| download: | MalwareDatabase |
| Full analysis: | https://app.any.run/tasks/58d1e9f7-e89b-42a4-b062-71bbf97bea7b |
| Verdict: | Malicious activity |
| Analysis date: | November 29, 2020, 19:19:52 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, UTF-8 Unicode text, with very long lines |
| MD5: | 8855EF2CE723DF76F668BBB5C48310B1 |
| SHA1: | 7BFB7E31D4BCE78C6A5B9C63034FBCE02BCB8E17 |
| SHA256: | D1A9709A0D29090F7EE21035CE57B5996B05F65527995845A7D20B29C31E267E |
| SSDEEP: | 3072:KYsDuqynwzbWadYVadYmadYb3M/GS0unY8etLZ0WLdEQD2ZtdAiC6UjF7rTBFZfI:0DuqynwzbWaqVaqmaqb3M/GS0unY8etO |
MALICIOUS
Application was dropped or rewritten from another process
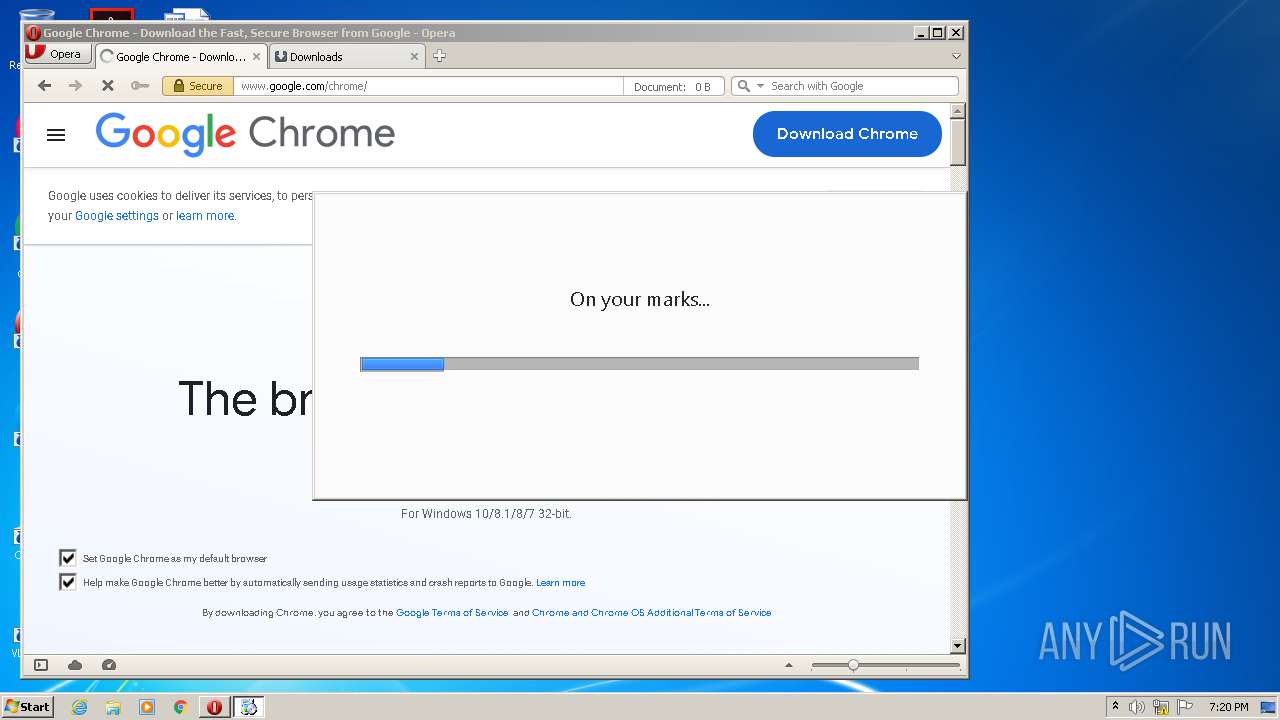
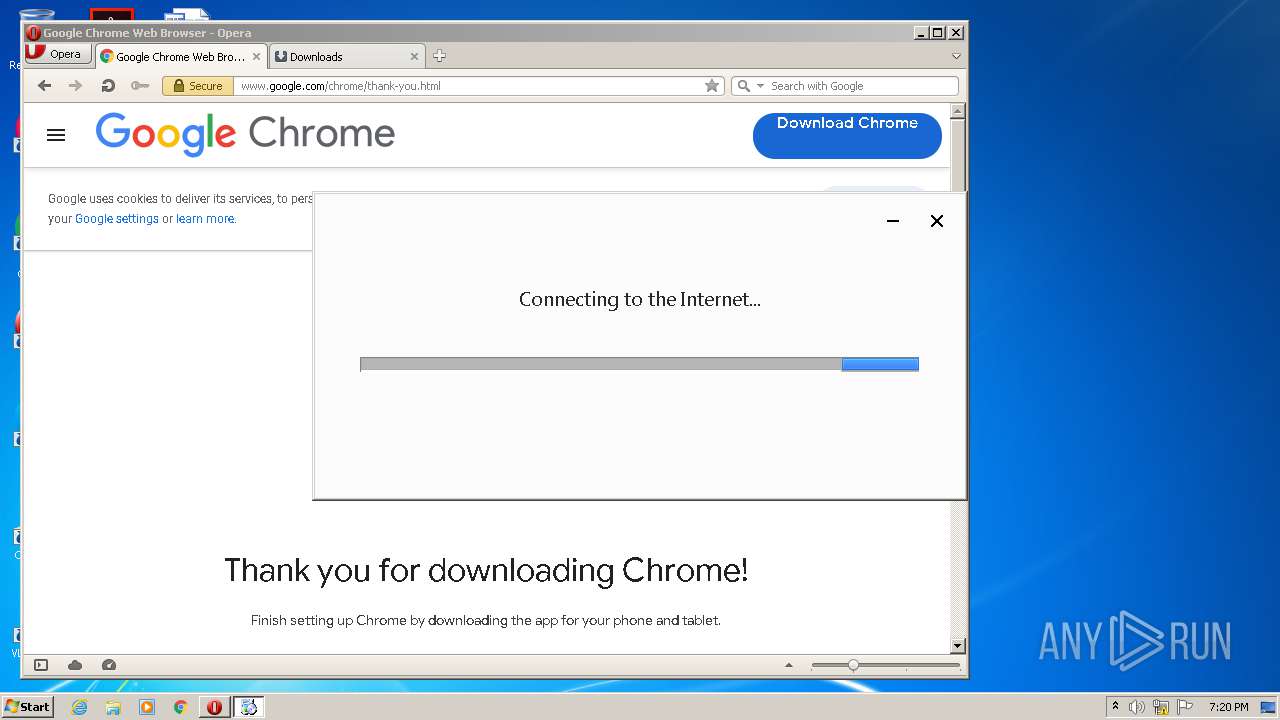
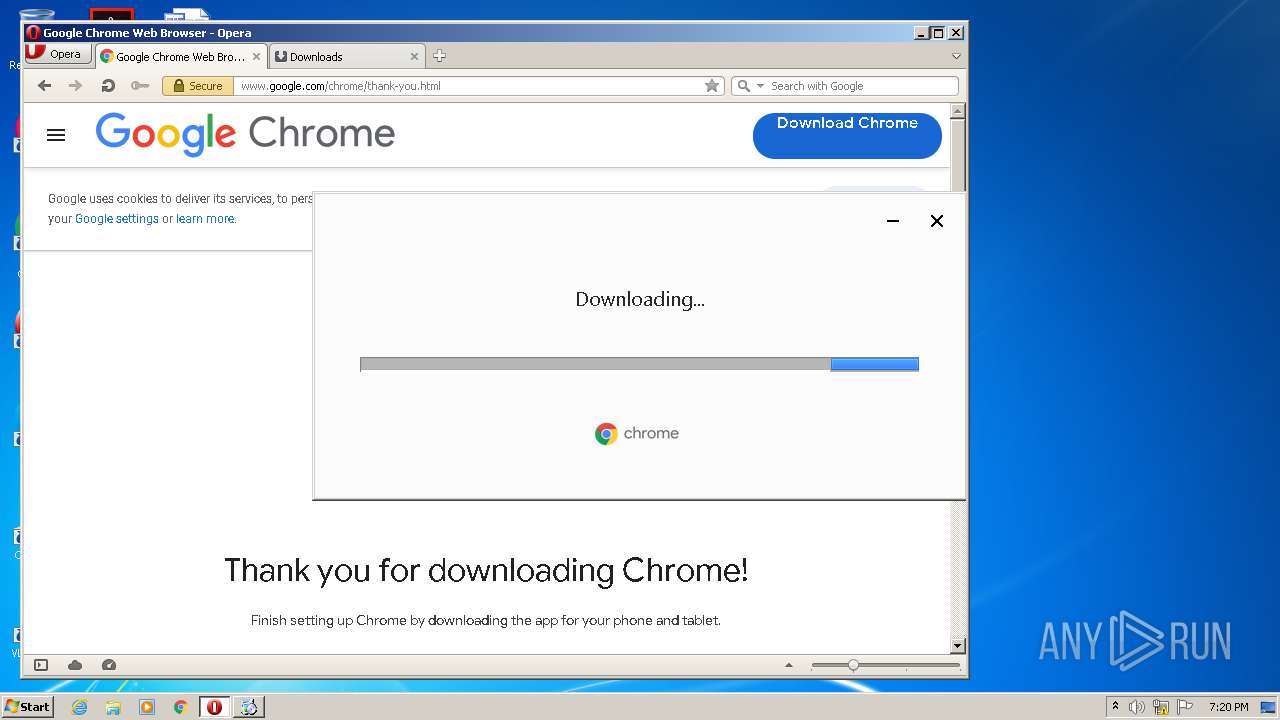
- ChromeSetup.exe (PID: 4052)
- GoogleUpdateSetup.exe (PID: 1540)
- GoogleUpdate.exe (PID: 2252)
- GoogleUpdate.exe (PID: 2864)
Drops executable file immediately after starts
- ChromeSetup.exe (PID: 4052)
- GoogleUpdateSetup.exe (PID: 1540)
- GoogleUpdate.exe (PID: 2864)
Loads dropped or rewritten executable
- GoogleUpdate.exe (PID: 2252)
- GoogleUpdate.exe (PID: 2864)
- GoogleUpdate.exe (PID: 2248)
- GoogleUpdate.exe (PID: 984)
- GoogleUpdate.exe (PID: 2608)
- GoogleUpdate.exe (PID: 2204)
- GoogleUpdate.exe (PID: 3100)
Loads the Task Scheduler COM API
- GoogleUpdate.exe (PID: 2864)
Changes settings of System certificates
- GoogleUpdate.exe (PID: 2608)
SUSPICIOUS
Executable content was dropped or overwritten
- Opera.exe (PID: 3068)
- ChromeSetup.exe (PID: 4052)
- GoogleUpdateSetup.exe (PID: 1540)
- GoogleUpdate.exe (PID: 2864)
Creates files in the program directory
- GoogleUpdateSetup.exe (PID: 1540)
- GoogleUpdate.exe (PID: 2864)
Drops a file that was compiled in debug mode
- Opera.exe (PID: 3068)
- ChromeSetup.exe (PID: 4052)
- GoogleUpdateSetup.exe (PID: 1540)
- GoogleUpdate.exe (PID: 2864)
Creates a directory in Program Files
- GoogleUpdateSetup.exe (PID: 1540)
- GoogleUpdate.exe (PID: 2864)
Disables SEHOP
- GoogleUpdate.exe (PID: 2864)
Creates COM task schedule object
- GoogleUpdate.exe (PID: 2248)
Executed as Windows Service
- GoogleUpdate.exe (PID: 3100)
Adds / modifies Windows certificates
- GoogleUpdate.exe (PID: 2608)
INFO
Creates files in the user directory
- Opera.exe (PID: 3068)
Dropped object may contain Bitcoin addresses
- Opera.exe (PID: 3068)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
EXIF
HTML
| viewport: | width=device-width |
|---|---|
| Title: | GitHub - Endermanch/MalwareDatabase: This repository is one of a few malware collections on the GitHub. |
| Description: | This repository is one of a few malware collections on the GitHub. - Endermanch/MalwareDatabase |
| appleItunesApp: | app-id=1477376905 |
| twitterImageSrc: | https://avatars1.githubusercontent.com/u/44542704?s=400&v=4 |
| twitterSite: | @github |
| twitterCard: | summary |
| twitterTitle: | Endermanch/MalwareDatabase |
| twitterDescription: | This repository is one of a few malware collections on the GitHub. - Endermanch/MalwareDatabase |
| requestId: | 21EF:9832:279029:3355AD:5FC3F458 |
| htmlSafeNonce: | 28dd6edb6a1066203f37a64938f89e0cc752431da669c82b56ff31d2f66023ad |
| visitorPayload: | eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiIyMUVGOjk4MzI6Mjc5MDI5OjMzNTVBRDo1RkMzRjQ1OCIsInZpc2l0b3JfaWQiOiIyOTI3MzY4MjI2NDQwMjQ5NTI2IiwicmVnaW9uX2VkZ2UiOiJmcmEiLCJyZWdpb25fcmVuZGVyIjoiZnJhIn0= |
| visitorHmac: | e1e27887a8d15e708769e40ec7363b880f78fc696c45eb20c3f0bdca29c49a84 |
| cookieConsentRequired: | |
| hovercardSubjectTag: | repository:155052331 |
| githubKeyboardShortcuts: | repository |
| googleSiteVerification: | GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc |
| octolyticsHost: | collector.githubapp.com |
| octolyticsAppId: | github |
| octolyticsEventUrl: | https://collector.githubapp.com/github-external/browser_event |
| analyticsLocation: | /<user-name>/<repo-name> |
| optimizelyDatafile: | {"version": "4", "rollouts": [], "typedAudiences": [], "anonymizeIP": true, "projectId": "16737760170", "variables": [], "featureFlags": [], "experiments": [{"status": "Running", "audienceIds": [], "variations": [{"variables": [], "id": "18630402174", "key": "launchpad"}, {"variables": [], "id": "18866331456", "key": "control"}], "id": "18651193356", "key": "_features_redesign_rollout", "layerId": "18645992876", "trafficAllocation": [{"entityId": "18630402174", "endOfRange": 500}, {"entityId": "18866331456", "endOfRange": 1000}, {"entityId": "18630402174", "endOfRange": 5000}, {"entityId": "18630402174", "endOfRange": 5500}, {"entityId": "18866331456", "endOfRange": 10000}], "forcedVariations": {"143327983.1601483920": "launchpad", "1955030087.1562868941": "launchpad", "1983887325.1550021416": "launchpad", "1947530619.1600461583": "launchpad"}}, {"status": "Running", "audienceIds": [], "variations": [{"variables": [], "id": "19136700362", "key": "show_plans"}, {"variables": [], "id": "19157700511", "key": "control"}], "id": "19062314978", "key": "account_billing_plans", "layerId": "19068014945", "trafficAllocation": [{"entityId": "19136700362", "endOfRange": 5000}, {"entityId": "19157700511", "endOfRange": 10000}], "forcedVariations": {"1238720267648ea2c88a74b410aa3c5c": "show_plans", "c4abf59d1620c671458b2a74df2a2410": "control"}}], "audiences": [{"conditions": "[\"or\", {\"match\": \"exact\", \"name\": \"$opt_dummy_attribute\", \"type\": \"custom_attribute\", \"value\": \"$opt_dummy_value\"}]", "id": "$opt_dummy_audience", "name": "Optimizely-Generated Audience for Backwards Compatibility"}], "groups": [], "attributes": [{"id": "16822470375", "key": "user_id"}, {"id": "17143601254", "key": "spammy"}, {"id": "18175660309", "key": "organization_plan"}, {"id": "18813001570", "key": "is_logged_in"}, {"id": "19073851829", "key": "geo"}], "botFiltering": false, "accountId": "16737760170", "events": [{"experimentIds": [], "id": "17911811441", "key": "hydro_click.dashboard.teacher_toolbox_cta"}, {"experimentIds": [], "id": "18124116703", "key": "submit.organizations.complete_sign_up"}, {"experimentIds": [], "id": "18145892387", "key": "no_metric.tracked_outside_of_optimizely"}, {"experimentIds": [], "id": "18178755568", "key": "click.org_onboarding_checklist.add_repo"}, {"experimentIds": [], "id": "18180553241", "key": "submit.repository_imports.create"}, {"experimentIds": [], "id": "18186103728", "key": "click.help.learn_more_about_repository_creation"}, {"experimentIds": [], "id": "18188530140", "key": "test_event.do_not_use_in_production"}, {"experimentIds": [], "id": "18191963644", "key": "click.empty_org_repo_cta.transfer_repository"}, {"experimentIds": [], "id": "18195612788", "key": "click.empty_org_repo_cta.import_repository"}, {"experimentIds": [], "id": "18210945499", "key": "click.org_onboarding_checklist.invite_members"}, {"experimentIds": [], "id": "18211063248", "key": "click.empty_org_repo_cta.create_repository"}, {"experimentIds": [], "id": "18215721889", "key": "click.org_onboarding_checklist.update_profile"}, {"experimentIds": [], "id": "18224360785", "key": "click.org_onboarding_checklist.dismiss"}, {"experimentIds": [], "id": "18234832286", "key": "submit.organization_activation.complete"}, {"experimentIds": [], "id": "18252392383", "key": "submit.org_repository.create"}, {"experimentIds": [], "id": "18257551537", "key": "submit.org_member_invitation.create"}, {"experimentIds": [], "id": "18259522260", "key": "submit.organization_profile.update"}, {"experimentIds": [], "id": "18564603625", "key": "view.classroom_select_organization"}, {"experimentIds": [], "id": "18568612016", "key": "click.classroom_sign_in_click"}, {"experimentIds": [], "id": "18572592540", "key": "view.classroom_name"}, {"experimentIds": [], "id": "18574203855", "key": "click.classroom_create_organization"}, {"experimentIds": [], "id": "18582053415", "key": "click.classroom_select_organization"}, {"experimentIds": [], "id": "18589463420", "key": "click.classroom_create_classroom"}, {"experimentIds": [], "id": "18591323364", "key": "click.classroom_create_first_classroom"}, {"experimentIds": [], "id": "18591652321", "key": "click.classroom_grant_access"}, {"experimentIds": [], "id": "18607131425", "key": "view.classroom_creation"}, {"experimentIds": [], "id": "18831680583", "key": "upgrade_account_plan"}, {"experimentIds": [], "id": "19064064515", "key": "click.signup"}, {"experimentIds": [], "id": "19075373687", "key": "click.view_account_billing_page"}, {"experimentIds": [], "id": "19077355841", "key": "click.dismiss_signup_prompt"}, {"experimentIds": ["19062314978"], "id": "19079713938", "key": "click.contact_sales"}, {"experimentIds": ["19062314978"], "id": "19120963070", "key": "click.compare_account_plans"}, {"experimentIds": ["19062314978"], "id": "19151690317", "key": "click.upgrade_account_cta"}], "revision": "338"} |
Total processes
47
Monitored processes
11
Malicious processes
9
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 984 | "C:\Program Files\Google\Update\GoogleUpdate.exe" /regsvc | C:\Program Files\Google\Update\GoogleUpdate.exe | — | GoogleUpdate.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: HIGH Description: Google Installer Exit code: 0 Version: 1.3.33.23 Modules
| |||||||||||||||
| 1540 | "C:\Users\admin\AppData\Local\Temp\GUM4451.tmp\GoogleUpdateSetup.exe" /installsource taggedmi /install "appguid={8A69D345-D564-463C-AFF1-A69D9E530F96}&iid={BF5A988F-2216-5AAF-4C18-8E1B292750E6}&lang=en&browser=0&usagestats=1&appname=Google%20Chrome&needsadmin=prefers&ap=stable-arch_x86-statsdef_1&brand=BNSD&installdataindex=defaultbrowser" /installelevated /nomitag | C:\Users\admin\AppData\Local\Temp\GUM4451.tmp\GoogleUpdateSetup.exe | GoogleUpdate.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: HIGH Description: Google Update Setup Exit code: 0 Version: 1.3.36.32 Modules
| |||||||||||||||
| 1908 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\MalwareDatabase | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2204 | "C:\Program Files\Google\Update\GoogleUpdate.exe" /handoff "appguid={8A69D345-D564-463C-AFF1-A69D9E530F96}&iid={BF5A988F-2216-5AAF-4C18-8E1B292750E6}&lang=en&browser=0&usagestats=1&appname=Google%20Chrome&needsadmin=prefers&ap=stable-arch_x86-statsdef_1&brand=BNSD&installdataindex=defaultbrowser" /installsource taggedmi /sessionid "{0C1C5701-CDCB-43C6-A355-9C3251213489}" | C:\Program Files\Google\Update\GoogleUpdate.exe | — | GoogleUpdate.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: HIGH Description: Google Installer Exit code: 0 Version: 1.3.33.23 Modules
| |||||||||||||||
| 2248 | "C:\Program Files\Google\Update\GoogleUpdate.exe" /regserver | C:\Program Files\Google\Update\GoogleUpdate.exe | — | GoogleUpdate.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: HIGH Description: Google Installer Exit code: 0 Version: 1.3.33.23 Modules
| |||||||||||||||
| 2252 | C:\Users\admin\AppData\Local\Temp\GUM4451.tmp\GoogleUpdate.exe /installsource taggedmi /install "appguid={8A69D345-D564-463C-AFF1-A69D9E530F96}&iid={BF5A988F-2216-5AAF-4C18-8E1B292750E6}&lang=en&browser=0&usagestats=1&appname=Google%20Chrome&needsadmin=prefers&ap=stable-arch_x86-statsdef_1&brand=BNSD&installdataindex=defaultbrowser" | C:\Users\admin\AppData\Local\Temp\GUM4451.tmp\GoogleUpdate.exe | — | ChromeSetup.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Installer Exit code: 0 Version: 1.3.36.31 Modules
| |||||||||||||||
| 2608 | "C:\Program Files\Google\Update\GoogleUpdate.exe" /ping PD94bWwgdmVyc2lvbj0iMS4wIiBlbmNvZGluZz0iVVRGLTgiPz48cmVxdWVzdCBwcm90b2NvbD0iMy4wIiB1cGRhdGVyPSJPbWFoYSIgdXBkYXRlcnZlcnNpb249IjEuMy4zNi4zMiIgc2hlbGxfdmVyc2lvbj0iMS4zLjMzLjIzIiBpc21hY2hpbmU9IjEiIHNlc3Npb25pZD0iezBDMUM1NzAxLUNEQ0ItNDNDNi1BMzU1LTlDMzI1MTIxMzQ4OX0iIHVzZXJpZD0iezQxOUQ5QUNELUU0MTctNEExQi1BMkQwLUVFQjREMTNFRDQ2OH0iIGluc3RhbGxzb3VyY2U9InRhZ2dlZG1pIiByZXF1ZXN0aWQ9IntCODU2OEZDOS0xMzkxLTRGMDMtQjhGOS0zQzUzRjU1NEI0NEV9IiBkZWR1cD0iY3IiIGRvbWFpbmpvaW5lZD0iMCI-PGh3IHBoeXNtZW1vcnk9IjMiIHNzZT0iMSIgc3NlMj0iMSIgc3NlMz0iMSIgc3NzZTM9IjEiIHNzZTQxPSIxIiBzc2U0Mj0iMSIgYXZ4PSIxIi8-PG9zIHBsYXRmb3JtPSJ3aW4iIHZlcnNpb249IjYuMS43NjAxLjAiIHNwPSJTZXJ2aWNlIFBhY2sgMSIgYXJjaD0ieDg2Ii8-PGFwcCBhcHBpZD0iezQzMEZENEQwLUI3MjktNEY2MS1BQTM0LTkxNTI2NDgxNzk5RH0iIHZlcnNpb249IjEuMy4zNC4xMSIgbmV4dHZlcnNpb249IjEuMy4zNi4zMiIgbGFuZz0iZW4iIGJyYW5kPSJCTlNEIiBjbGllbnQ9IiIgaWlkPSJ7QkY1QTk4OEYtMjIxNi01QUFGLTRDMTgtOEUxQjI5Mjc1MEU2fSI-PGV2ZW50IGV2ZW50dHlwZT0iMiIgZXZlbnRyZXN1bHQ9IjEiIGVycm9yY29kZT0iMCIgZXh0cmFjb2RlMT0iMCIgaW5zdGFsbF90aW1lX21zPSIxODA3Ii8-PC9hcHA-PC9yZXF1ZXN0Pg | C:\Program Files\Google\Update\GoogleUpdate.exe | GoogleUpdate.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: HIGH Description: Google Installer Exit code: 0 Version: 1.3.33.23 Modules
| |||||||||||||||
| 2864 | "C:\Program Files\Google\Temp\GUM48D5.tmp\GoogleUpdate.exe" /installsource taggedmi /install "appguid={8A69D345-D564-463C-AFF1-A69D9E530F96}&iid={BF5A988F-2216-5AAF-4C18-8E1B292750E6}&lang=en&browser=0&usagestats=1&appname=Google%20Chrome&needsadmin=prefers&ap=stable-arch_x86-statsdef_1&brand=BNSD&installdataindex=defaultbrowser" /installelevated | C:\Program Files\Google\Temp\GUM48D5.tmp\GoogleUpdate.exe | GoogleUpdateSetup.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: HIGH Description: Google Installer Exit code: 0 Version: 1.3.36.31 Modules
| |||||||||||||||
| 3068 | "C:\Program Files\Opera\Opera.exe" "C:\Users\admin\AppData\Local\Temp\MalwareDatabase" | C:\Program Files\Opera\Opera.exe | rundll32.exe | ||||||||||||
User: admin Company: Opera Software Integrity Level: MEDIUM Description: Opera Internet Browser Exit code: 0 Version: 1748 Modules
| |||||||||||||||
| 3100 | "C:\Program Files\Google\Update\GoogleUpdate.exe" /svc | C:\Program Files\Google\Update\GoogleUpdate.exe | services.exe | ||||||||||||
User: SYSTEM Company: Google Inc. Integrity Level: SYSTEM Description: Google Installer Exit code: 0 Version: 1.3.33.23 Modules
| |||||||||||||||
Total events
2 715
Read events
1 531
Write events
1 058
Delete events
126
Modification events
| (PID) Process: | (1908) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe |
Value: Adobe Acrobat Reader DC | |||
| (PID) Process: | (1908) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\eHome\ehshell.exe |
Value: Windows Media Center | |||
| (PID) Process: | (1908) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\mspaint.exe |
Value: Paint | |||
| (PID) Process: | (1908) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\NOTEPAD.EXE |
Value: Notepad | |||
| (PID) Process: | (1908) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\PROGRA~1\MICROS~1\Office14\OIS.EXE |
Value: Microsoft Office 2010 | |||
| (PID) Process: | (1908) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Opera\Opera.exe |
Value: Opera Internet Browser | |||
| (PID) Process: | (1908) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Windows Photo Viewer\PhotoViewer.dll |
Value: Windows Photo Viewer | |||
| (PID) Process: | (1908) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\VideoLAN\VLC\vlc.exe |
Value: VLC media player | |||
| (PID) Process: | (1908) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE |
Value: Microsoft Word | |||
| (PID) Process: | (1908) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
210
Suspicious files
134
Text files
356
Unknown types
26
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3068 | Opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\oprC9A3.tmp | — | |
MD5:— | SHA256:— | |||
| 3068 | Opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\oprC9A4.tmp | — | |
MD5:— | SHA256:— | |||
| 3068 | Opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\oprC9E3.tmp | — | |
MD5:— | SHA256:— | |||
| 3068 | Opera.exe | C:\Users\admin\AppData\Local\Opera\Opera\cache\sesn\opr00001.tmp | — | |
MD5:— | SHA256:— | |||
| 3068 | Opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\7XRX1QHKM7OVL5PKWOVC.temp | — | |
MD5:— | SHA256:— | |||
| 3068 | Opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\tasks.xml | xml | |
MD5:— | SHA256:— | |||
| 3068 | Opera.exe | C:\Users\admin\AppData\Local\Opera\Opera\cache\sesn\opr00003.tmp | image | |
MD5:— | SHA256:— | |||
| 3068 | Opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opssl6.dat | binary | |
MD5:— | SHA256:— | |||
| 3068 | Opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\oprD5CB.tmp | — | |
MD5:— | SHA256:— | |||
| 3068 | Opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\operaprefs.ini | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
67
TCP/UDP connections
348
DNS requests
103
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3068 | Opera.exe | GET | 301 | 23.67.137.78:80 | http://www.amazon.com/exec/obidos/redirect-home/opera-20 | NL | — | — | whitelisted |
3068 | Opera.exe | GET | 301 | 23.67.137.78:80 | http://www.amazon.com/exec/obidos/redirect-home/opera-20 | NL | — | — | whitelisted |
3068 | Opera.exe | GET | 200 | 93.184.220.29:80 | http://crl4.digicert.com/DigiCertHighAssuranceEVRootCA.crl | US | der | 592 b | whitelisted |
3068 | Opera.exe | GET | 302 | 185.26.182.110:80 | http://redir.opera.com/speeddials/amazon/ | unknown | html | 319 b | whitelisted |
3068 | Opera.exe | GET | 302 | 185.26.182.110:80 | http://redir.opera.com/speeddials/amazon/ | unknown | html | 319 b | whitelisted |
3068 | Opera.exe | GET | 200 | 93.184.220.29:80 | http://crl4.digicert.com/DigiCertGlobalRootG2.crl | US | der | 828 b | whitelisted |
3068 | Opera.exe | GET | 200 | 65.9.70.133:80 | http://crl.rootca1.amazontrust.com/rootca1.crl | US | der | 439 b | whitelisted |
3068 | Opera.exe | GET | 200 | 65.9.70.190:80 | http://s.ss2.us/r.crl | US | der | 434 b | whitelisted |
3068 | Opera.exe | GET | 200 | 93.184.220.29:80 | http://s.symcb.com/pca3-g5.crl | US | der | 834 b | whitelisted |
3068 | Opera.exe | GET | 200 | 65.9.70.42:80 | http://crl.rootg2.amazontrust.com/rootg2.crl | US | der | 608 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3068 | Opera.exe | 185.199.109.154:443 | github.githubassets.com | GitHub, Inc. | NL | suspicious |
3068 | Opera.exe | 185.26.182.93:443 | certs.opera.com | Opera Software AS | — | whitelisted |
3068 | Opera.exe | 151.101.0.133:443 | avatars2.githubusercontent.com | Fastly | US | malicious |
— | — | 185.199.109.154:443 | github.githubassets.com | GitHub, Inc. | NL | suspicious |
3068 | Opera.exe | 93.184.220.29:80 | crl4.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3068 | Opera.exe | 185.26.182.110:80 | redir.opera.com | Opera Software AS | — | unknown |
3068 | Opera.exe | 82.145.216.16:80 | sitecheck2.opera.com | Opera Software AS | — | suspicious |
3068 | Opera.exe | 151.101.1.16:443 | images-na.ssl-images-amazon.com | Fastly | US | suspicious |
3068 | Opera.exe | 151.101.193.16:443 | images-na.ssl-images-amazon.com | Fastly | US | suspicious |
3068 | Opera.exe | 23.67.137.78:80 | www.amazon.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
github.githubassets.com |
| whitelisted |
avatars2.githubusercontent.com |
| whitelisted |
camo.githubusercontent.com |
| shared |
avatars3.githubusercontent.com |
| whitelisted |
avatars0.githubusercontent.com |
| whitelisted |
avatars1.githubusercontent.com |
| whitelisted |
certs.opera.com |
| whitelisted |
crl4.digicert.com |
| whitelisted |
redir.opera.com |
| whitelisted |
sitecheck2.opera.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3068 | Opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
3068 | Opera.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
3068 | Opera.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
— | — | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
— | — | Misc activity | ET INFO EXE - Served Attached HTTP |
1 ETPRO signatures available at the full report