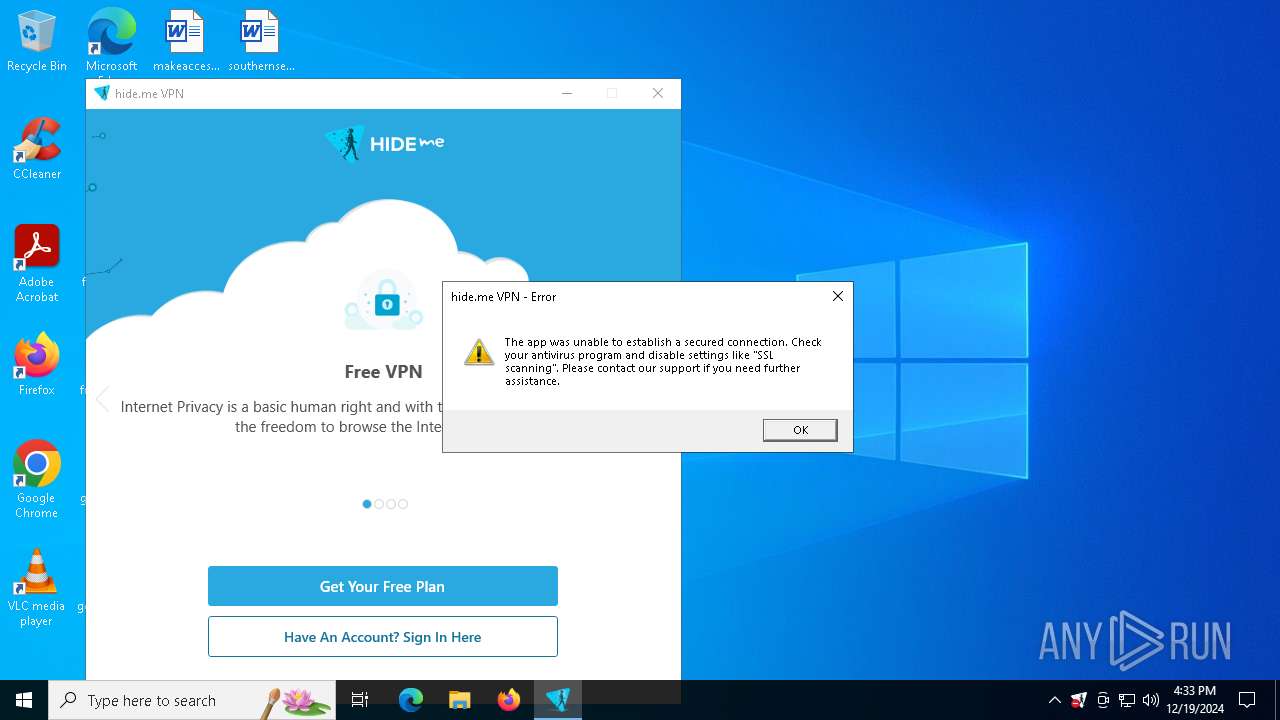
| File name: | Hide.me-Setup-3.17.3.exe |
| Full analysis: | https://app.any.run/tasks/24e2aa25-2aab-4f96-896e-cda766f665a4 |
| Verdict: | Malicious activity |
| Analysis date: | December 19, 2024, 16:32:26 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 11 sections |
| MD5: | 76D02F6B9E7681C05F4E9EFD82543C8C |
| SHA1: | 5EA89EE60CD61DB9C5B82F612D9E771FBCED5127 |
| SHA256: | D1853A77142B349187FBDC32EC529739627AE9B4512119E5E5F899B6B0A11142 |
| SSDEEP: | 196608:x9XYdnDkTLUlgWxTlOYPoD9jfmKJfk18kA:UdnIUmgT8fHfk18kA |
MALICIOUS
Create files in the Startup directory
- Hide.me-Setup-3.17.3.tmp (PID: 4444)
SUSPICIOUS
Reads security settings of Internet Explorer
- Hide.me-Setup-3.17.3.tmp (PID: 4996)
- hidemesvc.exe (PID: 6576)
Executable content was dropped or overwritten
- Hide.me-Setup-3.17.3.exe (PID: 4528)
- Hide.me-Setup-3.17.3.exe (PID: 3620)
- Hide.me-Setup-3.17.3.tmp (PID: 4444)
- drvinst.exe (PID: 6156)
- drvinst.exe (PID: 6520)
- hidemesvc.exe (PID: 6700)
Reads the Windows owner or organization settings
- Hide.me-Setup-3.17.3.tmp (PID: 4444)
- msiexec.exe (PID: 5460)
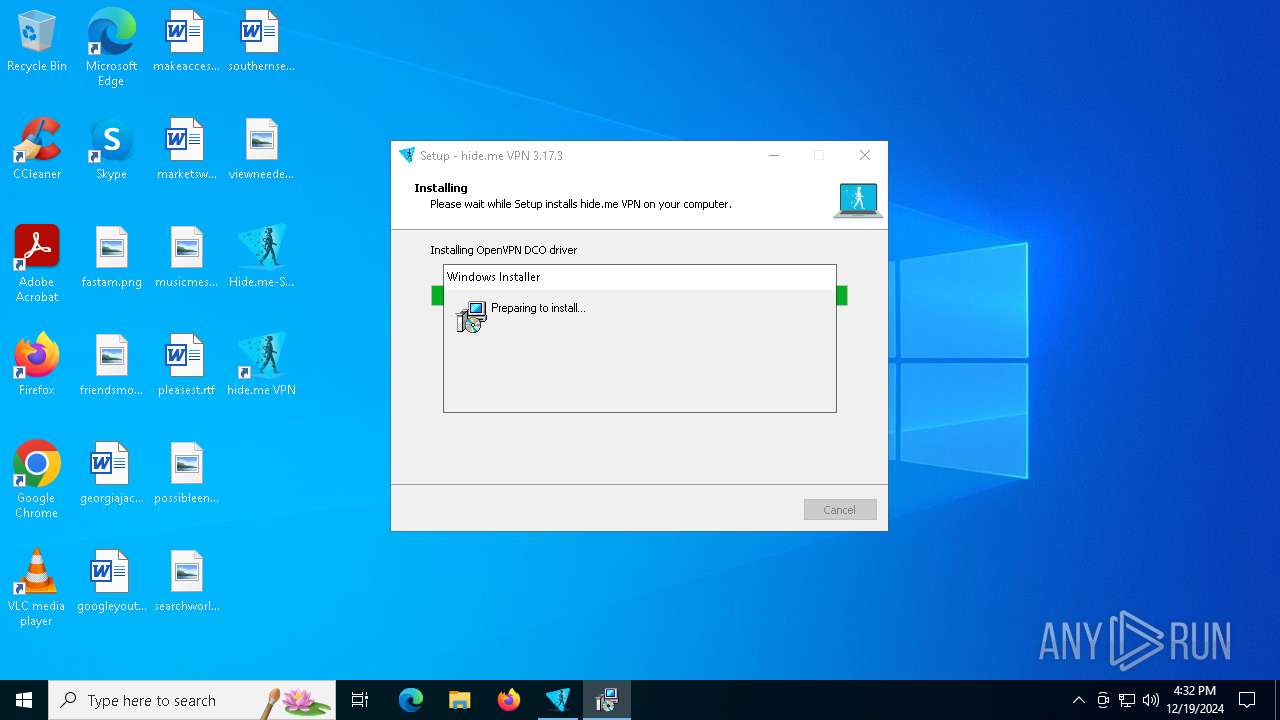
Drops a system driver (possible attempt to evade defenses)
- Hide.me-Setup-3.17.3.tmp (PID: 4444)
- msiexec.exe (PID: 5460)
- drvinst.exe (PID: 6156)
- msiexec.exe (PID: 6476)
- drvinst.exe (PID: 6520)
- hidemesvc.exe (PID: 6700)
Process drops legitimate windows executable
- Hide.me-Setup-3.17.3.tmp (PID: 4444)
The process drops C-runtime libraries
- Hide.me-Setup-3.17.3.tmp (PID: 4444)
Executes as Windows Service
- VSSVC.exe (PID: 2008)
- hidemesvc.exe (PID: 6700)
Creates files in the driver directory
- msiexec.exe (PID: 6476)
- drvinst.exe (PID: 6520)
- drvinst.exe (PID: 6156)
Checks Windows Trust Settings
- drvinst.exe (PID: 6520)
- hidemesvc.exe (PID: 6576)
Uses powercfg.exe to modify the power settings
- hidemesvc.exe (PID: 6700)
INFO
Create files in a temporary directory
- Hide.me-Setup-3.17.3.exe (PID: 3620)
- Hide.me-Setup-3.17.3.exe (PID: 4528)
Checks supported languages
- Hide.me-Setup-3.17.3.exe (PID: 3620)
- Hide.me-Setup-3.17.3.tmp (PID: 4996)
- Hide.me-Setup-3.17.3.exe (PID: 4528)
- Hide.me-Setup-3.17.3.tmp (PID: 4444)
- msiexec.exe (PID: 5460)
- msiexec.exe (PID: 1684)
- drvinst.exe (PID: 6156)
- msiexec.exe (PID: 6424)
- drvinst.exe (PID: 6520)
- Hide.me.exe (PID: 6820)
- hidemesvc.exe (PID: 6576)
- hidemesvc.exe (PID: 6700)
Reads the computer name
- Hide.me-Setup-3.17.3.tmp (PID: 4996)
- Hide.me-Setup-3.17.3.exe (PID: 3620)
- Hide.me-Setup-3.17.3.tmp (PID: 4444)
- msiexec.exe (PID: 5460)
- msiexec.exe (PID: 1684)
- drvinst.exe (PID: 6520)
- hidemesvc.exe (PID: 6576)
- Hide.me.exe (PID: 6820)
Process checks computer location settings
- Hide.me-Setup-3.17.3.tmp (PID: 4996)
Creates files in the program directory
- Hide.me-Setup-3.17.3.tmp (PID: 4444)
- hidemesvc.exe (PID: 6576)
- hidemesvc.exe (PID: 6700)
The sample compiled with english language support
- Hide.me-Setup-3.17.3.tmp (PID: 4444)
- msiexec.exe (PID: 5460)
- msiexec.exe (PID: 6476)
- drvinst.exe (PID: 6520)
- drvinst.exe (PID: 6156)
- hidemesvc.exe (PID: 6700)
Creates files or folders in the user directory
- Hide.me-Setup-3.17.3.tmp (PID: 4444)
- hidemesvc.exe (PID: 6700)
Creates a software uninstall entry
- Hide.me-Setup-3.17.3.tmp (PID: 4444)
- msiexec.exe (PID: 5460)
Executable content was dropped or overwritten
- msiexec.exe (PID: 5460)
- msiexec.exe (PID: 6476)
Manages system restore points
- SrTasks.exe (PID: 2612)
- SrTasks.exe (PID: 6348)
Application launched itself
- msiexec.exe (PID: 5460)
Reads the software policy settings
- drvinst.exe (PID: 6520)
- drvinst.exe (PID: 6156)
- hidemesvc.exe (PID: 6576)
- Hide.me.exe (PID: 6820)
Reads the machine GUID from the registry
- drvinst.exe (PID: 6520)
- drvinst.exe (PID: 6156)
- hidemesvc.exe (PID: 6576)
- hidemesvc.exe (PID: 6700)
- Hide.me.exe (PID: 6820)
Checks proxy server information
- hidemesvc.exe (PID: 6576)
The process uses the downloaded file
- hidemesvc.exe (PID: 6576)
Sends debugging messages
- hidemesvc.exe (PID: 6700)
Disables trace logs
- hidemesvc.exe (PID: 6700)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (67.7) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (25.6) |
| .exe | | | Win32 Executable (generic) (2.7) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
| .exe | | | Generic Win/DOS Executable (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:07:12 07:26:53+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 685056 |
| InitializedDataSize: | 171520 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa83bc |
| OSVersion: | 6.1 |
| ImageVersion: | - |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.17.3.0 |
| ProductVersionNumber: | 3.17.3.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | eVenture Limited |
| FileDescription: | hide.me VPN Setup |
| FileVersion: | 3.17.3 |
| LegalCopyright: | |
| OriginalFileName: | |
| ProductName: | hide.me VPN |
| ProductVersion: | 3.17.3 |
Total processes
148
Monitored processes
25
Malicious processes
9
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1536 | C:\Windows\System32\MsiExec.exe -Embedding F20B570A94A99B9642E7037E8F7C4B4F E Global\MSI0000 | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1684 | C:\Windows\System32\MsiExec.exe -Embedding 7E9E3550A93335E0F74AF7C0C3395852 | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2008 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2612 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 2147942487 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3568 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3620 | "C:\Users\admin\Desktop\Hide.me-Setup-3.17.3.exe" /SPAWNWND=$402D2 /NOTIFYWND=$901FA | C:\Users\admin\Desktop\Hide.me-Setup-3.17.3.exe | Hide.me-Setup-3.17.3.tmp | ||||||||||||
User: admin Company: eVenture Limited Integrity Level: HIGH Description: hide.me VPN Setup Exit code: 0 Version: 3.17.3 Modules
| |||||||||||||||
| 4444 | "C:\Users\admin\AppData\Local\Temp\is-O2RBE.tmp\Hide.me-Setup-3.17.3.tmp" /SL5="$60224,14933946,857600,C:\Users\admin\Desktop\Hide.me-Setup-3.17.3.exe" /SPAWNWND=$402D2 /NOTIFYWND=$901FA | C:\Users\admin\AppData\Local\Temp\is-O2RBE.tmp\Hide.me-Setup-3.17.3.tmp | Hide.me-Setup-3.17.3.exe | ||||||||||||
User: admin Company: eVenture Limited Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 4528 | "C:\Users\admin\Desktop\Hide.me-Setup-3.17.3.exe" | C:\Users\admin\Desktop\Hide.me-Setup-3.17.3.exe | explorer.exe | ||||||||||||
User: admin Company: eVenture Limited Integrity Level: MEDIUM Description: hide.me VPN Setup Exit code: 0 Version: 3.17.3 Modules
| |||||||||||||||
| 4652 | "C:\WINDOWS\system32\msiexec.exe" /x "{6A3B09CD-8B4A-4A66-9C90-833023E463E9}" /passive | C:\Windows\SysWOW64\msiexec.exe | — | Hide.me-Setup-3.17.3.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 1605 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4976 | "C:\WINDOWS\system32\msiexec.exe" /i "C:\Program Files (x86)\hide.me VPN\OpenVPN\drivers\ovpn-dco-x64.msi" /passive | C:\Windows\SysWOW64\msiexec.exe | — | Hide.me-Setup-3.17.3.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
25 611
Read events
25 012
Write events
561
Delete events
38
Modification events
| (PID) Process: | (4444) Hide.me-Setup-3.17.3.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{0E00BDA5-7998-4889-BE4B-39A4BBD2EDFB}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.3.3 | |||
| (PID) Process: | (4444) Hide.me-Setup-3.17.3.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{0E00BDA5-7998-4889-BE4B-39A4BBD2EDFB}_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files (x86)\hide.me VPN | |||
| (PID) Process: | (4444) Hide.me-Setup-3.17.3.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{0E00BDA5-7998-4889-BE4B-39A4BBD2EDFB}_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files (x86)\hide.me VPN\ | |||
| (PID) Process: | (4444) Hide.me-Setup-3.17.3.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{0E00BDA5-7998-4889-BE4B-39A4BBD2EDFB}_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: hide.me VPN | |||
| (PID) Process: | (4444) Hide.me-Setup-3.17.3.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{0E00BDA5-7998-4889-BE4B-39A4BBD2EDFB}_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
| (PID) Process: | (4444) Hide.me-Setup-3.17.3.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{0E00BDA5-7998-4889-BE4B-39A4BBD2EDFB}_is1 |
| Operation: | write | Name: | Inno Setup: Language |
Value: en | |||
| (PID) Process: | (4444) Hide.me-Setup-3.17.3.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{0E00BDA5-7998-4889-BE4B-39A4BBD2EDFB}_is1 |
| Operation: | write | Name: | DisplayName |
Value: hide.me VPN 3.17.3 | |||
| (PID) Process: | (4444) Hide.me-Setup-3.17.3.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{0E00BDA5-7998-4889-BE4B-39A4BBD2EDFB}_is1 |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files (x86)\hide.me VPN\unins000.exe | |||
| (PID) Process: | (4444) Hide.me-Setup-3.17.3.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{0E00BDA5-7998-4889-BE4B-39A4BBD2EDFB}_is1 |
| Operation: | write | Name: | UninstallString |
Value: "C:\Program Files (x86)\hide.me VPN\unins000.exe" | |||
| (PID) Process: | (4444) Hide.me-Setup-3.17.3.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{0E00BDA5-7998-4889-BE4B-39A4BBD2EDFB}_is1 |
| Operation: | write | Name: | QuietUninstallString |
Value: "C:\Program Files (x86)\hide.me VPN\unins000.exe" /SILENT | |||
Executable files
128
Suspicious files
147
Text files
33
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4444 | Hide.me-Setup-3.17.3.tmp | C:\Program Files (x86)\hide.me VPN\is-D6LIQ.tmp | executable | |
MD5:EB9CCEA99B956BC3FAE6FC5A5EBC6E21 | SHA256:67366BEBFA49AF883AC25176E15FA4DEB3A947A9F307AE352EAD94936D6AA406 | |||
| 4444 | Hide.me-Setup-3.17.3.tmp | C:\Program Files (x86)\hide.me VPN\is-378H0.tmp | executable | |
MD5:7DF949770C6AFC2C36F0A5D961087548 | SHA256:F6B44BF917C89A3C36C4B5C85D0CFDF323697B0957191053B882EB5A92B99A89 | |||
| 4444 | Hide.me-Setup-3.17.3.tmp | C:\Users\admin\AppData\Local\Temp\is-R4EHE.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 4444 | Hide.me-Setup-3.17.3.tmp | C:\Program Files (x86)\hide.me VPN\unins000.exe | executable | |
MD5:EB9CCEA99B956BC3FAE6FC5A5EBC6E21 | SHA256:67366BEBFA49AF883AC25176E15FA4DEB3A947A9F307AE352EAD94936D6AA406 | |||
| 4444 | Hide.me-Setup-3.17.3.tmp | C:\Program Files (x86)\hide.me VPN\CodeKicker.BBCode.dll | executable | |
MD5:7DF949770C6AFC2C36F0A5D961087548 | SHA256:F6B44BF917C89A3C36C4B5C85D0CFDF323697B0957191053B882EB5A92B99A89 | |||
| 3620 | Hide.me-Setup-3.17.3.exe | C:\Users\admin\AppData\Local\Temp\is-O2RBE.tmp\Hide.me-Setup-3.17.3.tmp | executable | |
MD5:2E9F9B1ABBB8D8D3D405ADFFEA3017B9 | SHA256:687295EEF5E866CC1D3CD057394C3280FB7699C8899F48804CB74C4DCE13F5CA | |||
| 4444 | Hide.me-Setup-3.17.3.tmp | C:\Program Files (x86)\hide.me VPN\is-MKTS8.tmp | executable | |
MD5:AEB2194B5C7D9046FBADA34954B2242F | SHA256:C3979C23F9F89E9FEEB89D0E9ED53511A9016AB304EABFBF652969B6C5AB568C | |||
| 4444 | Hide.me-Setup-3.17.3.tmp | C:\Users\admin\AppData\Local\Temp\is-R4EHE.tmp\idp.dll | executable | |
MD5:55C310C0319260D798757557AB3BF636 | SHA256:54E7E0AD32A22B775131A6288F083ED3286A9A436941377FC20F85DD9AD983ED | |||
| 4444 | Hide.me-Setup-3.17.3.tmp | C:\Program Files (x86)\hide.me VPN\is-1B1PO.tmp | executable | |
MD5:210C1D906BFAC28272F6714776F6DB99 | SHA256:FD8D832125EE22755BF82F11495CD2CAAC02C418202560756E5B554E3E6A22C3 | |||
| 4444 | Hide.me-Setup-3.17.3.tmp | C:\Program Files (x86)\hide.me VPN\ComLib.dll | executable | |
MD5:AEB2194B5C7D9046FBADA34954B2242F | SHA256:C3979C23F9F89E9FEEB89D0E9ED53511A9016AB304EABFBF652969B6C5AB568C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
21
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.194:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.23.9.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6576 | hidemesvc.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
3040 | svchost.exe | GET | 200 | 23.48.23.194:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAV2do6CXHS9PJ6aGicg1DY%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3040 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.212.110.209:443 | www.bing.com | Akamai International B.V. | CZ | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.194:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3040 | svchost.exe | 23.48.23.194:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.23.9.218:80 | www.microsoft.com | AKAMAI-AS | CZ | whitelisted |
3040 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
dns.msftncsi.com |
| whitelisted |
api.hide.me |
| unknown |
sentry.thevpncompany.net |
| unknown |
self.events.data.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
hidemesvc.exe | Corrected RASENTRY size -> Prev: 5680. New: 6724
|
hidemesvc.exe | Corrected RASENTRY size -> Prev: 5680. New: 6724
|
hidemesvc.exe | Corrected RASENTRY size -> Prev: 5680. New: 6724
|
hidemesvc.exe | Corrected RASENTRY size -> Prev: 5680. New: 6724
|
hidemesvc.exe | Corrected RASENTRY size -> Prev: 5680. New: 6724
|
hidemesvc.exe | Corrected RASENTRY size -> Prev: 5680. New: 6724
|