| File name: | ProgramData.zip |
| Full analysis: | https://app.any.run/tasks/a04c79b8-19cb-4e18-8c1d-05b6d58c5d46 |
| Verdict: | Malicious activity |
| Analysis date: | August 13, 2024, 13:07:21 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 8215BE6CC9CD232DE0DF99D188DD0ADE |
| SHA1: | 6127400FA93F3652C8786E4E8B4F7F18DA4D060C |
| SHA256: | D180170D4EC50E90688C0034B81CBEE8DF4ACA18A8FC332FF5969CD2062F60E8 |
| SSDEEP: | 98304:OXdLTXlETf0S1eHFKCr2TN5k3eGXd3XdabwmFGhO85x4XveH4D9xD0yYJ7+hyC7P:s/6 |
MALICIOUS
Changes the login/logoff helper path in the registry
- svcr.exe (PID: 6364)
Disables the Shutdown in the Start menu
- svcr.exe (PID: 6364)
Changes the autorun value in the registry
- svcr.exe (PID: 6364)
Starts NET.EXE for service management
- cmd.exe (PID: 2152)
- cmd.exe (PID: 1692)
- cmd.exe (PID: 6080)
- net.exe (PID: 5104)
- net.exe (PID: 1060)
- net.exe (PID: 4824)
- cmd.exe (PID: 1488)
- net.exe (PID: 6792)
Creates or modifies Windows services
- svcr.exe (PID: 6364)
SUSPICIOUS
The process creates files with name similar to system file names
- WinRAR.exe (PID: 6404)
Reads security settings of Internet Explorer
- svcr.exe (PID: 6180)
- removelastfolders.exe (PID: 6176)
- alternateshell.exe (PID: 5880)
- logonsession.exe (PID: 5292)
- svcr.exe (PID: 1432)
- svcr.exe (PID: 7052)
- uninst.exe (PID: 5656)
Reads the date of Windows installation
- removelastfolders.exe (PID: 6176)
- alternateshell.exe (PID: 5880)
- logonsession.exe (PID: 5292)
- uninst.exe (PID: 5656)
- svcr.exe (PID: 7052)
Starts CMD.EXE for commands execution
- svcr.exe (PID: 6364)
Application launched itself
- svcr.exe (PID: 7052)
Executable content was dropped or overwritten
- svcr.exe (PID: 6364)
Drops the executable file immediately after the start
- svcr.exe (PID: 6364)
INFO
Reads mouse settings
- svcr.exe (PID: 6180)
- svcr.exe (PID: 7072)
- svcr.exe (PID: 6228)
- svcr.exe (PID: 1432)
- svcr.exe (PID: 7052)
- svcr.exe (PID: 6364)
Manual execution by a user
- svcr.exe (PID: 6180)
- removelastfolders.exe (PID: 6176)
- mspaint.exe (PID: 2268)
- alternateshell.exe (PID: 5880)
- logonsession.exe (PID: 5292)
- uninst.exe (PID: 5656)
Checks supported languages
- svcr.exe (PID: 6180)
- removelastfolders.exe (PID: 6176)
- svcr.exe (PID: 7072)
- alternateshell.exe (PID: 5880)
- svcr.exe (PID: 6228)
- logonsession.exe (PID: 5292)
- svcr.exe (PID: 1432)
- svcr.exe (PID: 7052)
- svcr.exe (PID: 6364)
- uninst.exe (PID: 5656)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6404)
Reads the computer name
- svcr.exe (PID: 6180)
- removelastfolders.exe (PID: 6176)
- alternateshell.exe (PID: 5880)
- logonsession.exe (PID: 5292)
- svcr.exe (PID: 1432)
- svcr.exe (PID: 7052)
- svcr.exe (PID: 6364)
- uninst.exe (PID: 5656)
Process checks computer location settings
- removelastfolders.exe (PID: 6176)
- alternateshell.exe (PID: 5880)
- logonsession.exe (PID: 5292)
- svcr.exe (PID: 7052)
- uninst.exe (PID: 5656)
Creates files or folders in the user directory
- svcr.exe (PID: 1432)
Creates files in the program directory
- svcr.exe (PID: 6364)
Create files in a temporary directory
- svcr.exe (PID: 6364)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:08:13 15:06:18 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | ProgramData/ |
Total processes
162
Monitored processes
32
Malicious processes
3
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 400 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 400 | sc config TermService depend= RPCSS | C:\Windows\SysWOW64\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 936 | C:\WINDOWS\system32\net1 STOP APSC | C:\Windows\SysWOW64\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Version: 10.0.19041.3636 (WinBuild.160101.0800) | |||||||||||||||
| 1060 | NET STOP APSC | C:\Windows\SysWOW64\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1432 | "C:\Users\admin\Desktop\ProgramData\ProgramData\svcr.exe" "logonsession.bin" "C:\Users\admin\Desktop\ProgramData\ProgramData\logonsession.exe" | C:\Users\admin\Desktop\ProgramData\ProgramData\svcr.exe | — | logonsession.exe | |||||||||||
User: admin Company: JWTS Integrity Level: MEDIUM Description: Application Runtime Exit code: 0 Version: 3, 3, 16, 1 | |||||||||||||||
| 1488 | C:\WINDOWS\system32\cmd.exe /c NET STOP APSC | C:\Windows\SysWOW64\cmd.exe | — | svcr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.19041.3636 (WinBuild.160101.0800) | |||||||||||||||
| 1692 | C:\WINDOWS\system32\cmd.exe /c NET STOP SVCE | C:\Windows\SysWOW64\cmd.exe | — | svcr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.19041.3636 (WinBuild.160101.0800) | |||||||||||||||
| 2044 | C:\WINDOWS\system32\cmd.exe /c sc config TermService depend= RPCSS | C:\Windows\SysWOW64\cmd.exe | — | svcr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) | |||||||||||||||
| 2152 | C:\WINDOWS\system32\cmd.exe /c NET STOP SVCM | C:\Windows\SysWOW64\cmd.exe | — | svcr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.19041.3636 (WinBuild.160101.0800) | |||||||||||||||
| 2268 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\Desktop\ProgramData\ProgramData\icon.ico" | C:\Windows\System32\mspaint.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
12 389
Read events
12 260
Write events
125
Delete events
4
Modification events
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\ProgramData.zip | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\ProgramData | |||
| (PID) Process: | (6404) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000200000003000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
7
Suspicious files
2
Text files
2
Unknown types
6
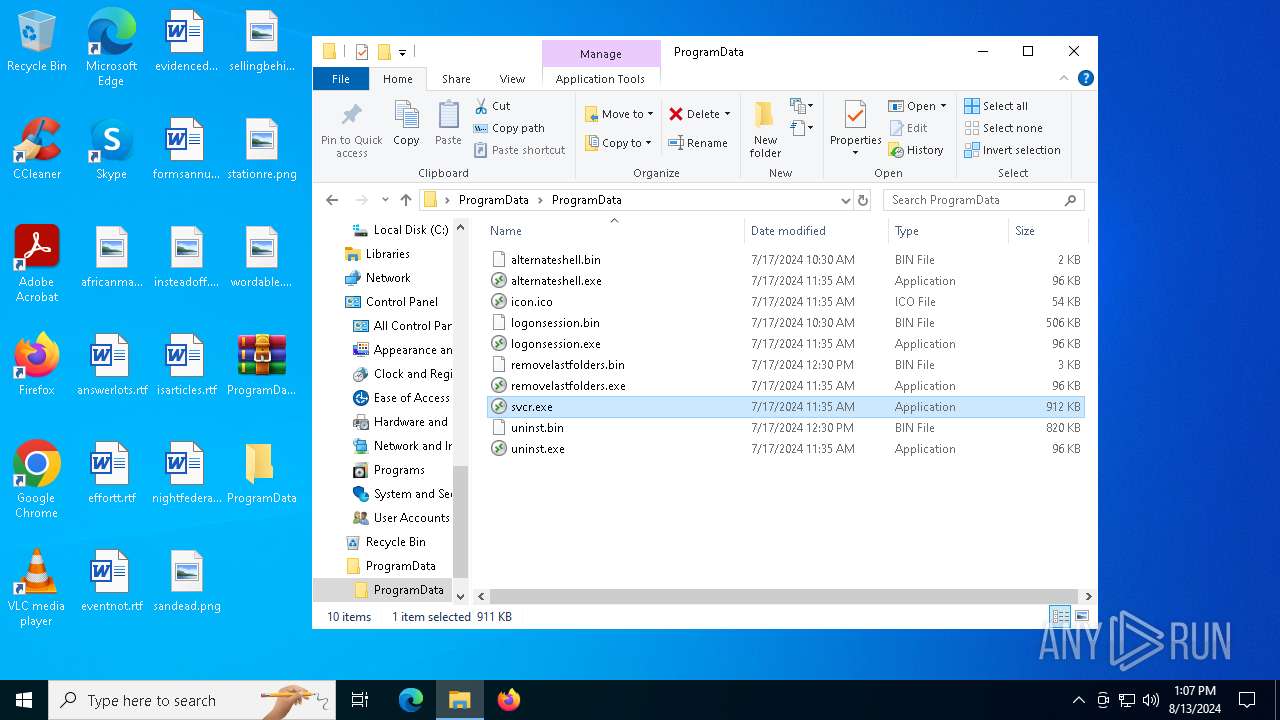
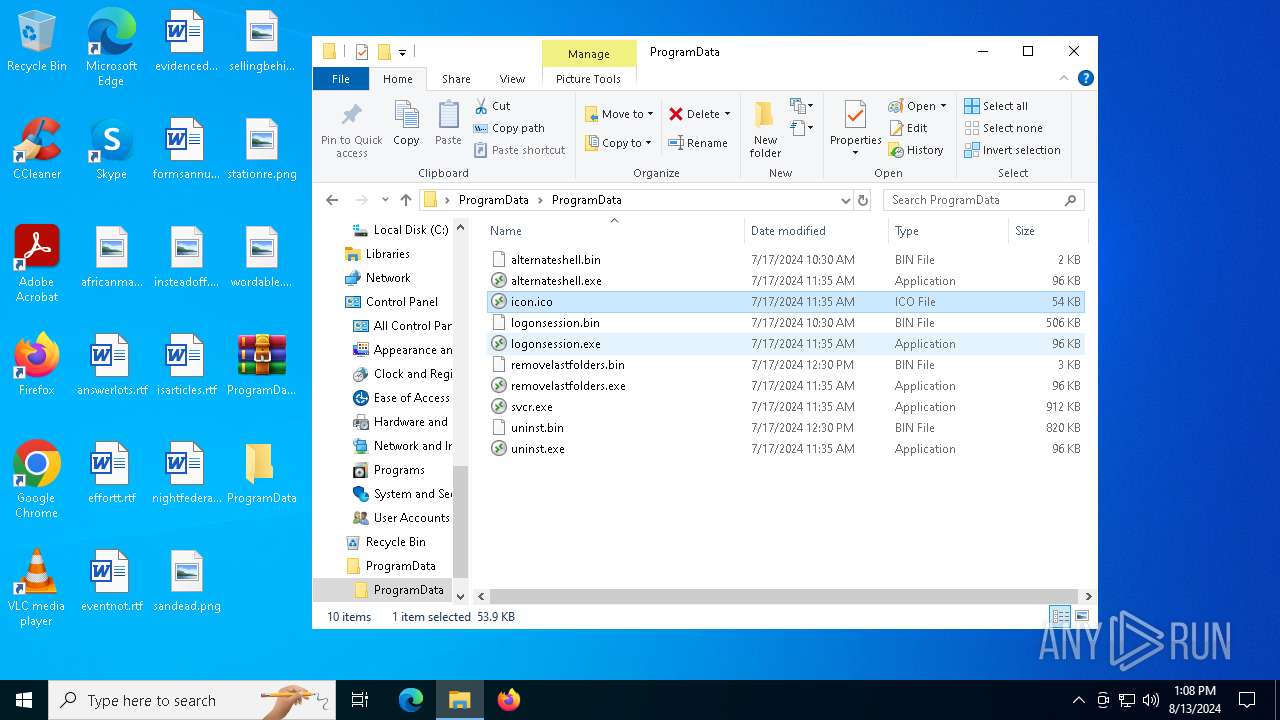
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6404 | WinRAR.exe | C:\Users\admin\Desktop\ProgramData\ProgramData\alternateshell.bin | a3x | |
MD5:AB932E6E4A549C20F58CF2DDDDA3D8C7 | SHA256:50FA5576F5EB4DC92FB264C47B1604007C864967A3E8444C0F762BDA773E6779 | |||
| 6404 | WinRAR.exe | C:\Users\admin\Desktop\ProgramData\ProgramData\logonsession.exe | executable | |
MD5:9EC3D89978C9A2EA2A7454D2913D79D2 | SHA256:7ACD2E8F32235743D25B48D9B679B553E60A6348E13EDD4F7EAB6AEE79FEFE2C | |||
| 6404 | WinRAR.exe | C:\Users\admin\Desktop\ProgramData\ProgramData\uninst.bin | a3x | |
MD5:7C339102759F647E5D6EA64605D873B9 | SHA256:F38CF49346590609AE16DE51EAA73FECD798AB00B763683590BEF04EEDB29033 | |||
| 6404 | WinRAR.exe | C:\Users\admin\Desktop\ProgramData\ProgramData\logonsession.bin | a3x | |
MD5:90BA3B6C847ABC2F6D0C7350E4F859D7 | SHA256:BF37FBAAAE5D697758D23CC717FF423D1093AE99BD4DCE919A8735B345737268 | |||
| 6404 | WinRAR.exe | C:\Users\admin\Desktop\ProgramData\ProgramData\removelastfolders.bin | a3x | |
MD5:E84169A715E34C4067940ED332361C7D | SHA256:1342E0E6019F6671E5C62F5295A99DFFAAE696C3DE2DC43719F960FE33A961F2 | |||
| 6404 | WinRAR.exe | C:\Users\admin\Desktop\ProgramData\ProgramData\removelastfolders.exe | executable | |
MD5:9EC3D89978C9A2EA2A7454D2913D79D2 | SHA256:7ACD2E8F32235743D25B48D9B679B553E60A6348E13EDD4F7EAB6AEE79FEFE2C | |||
| 6404 | WinRAR.exe | C:\Users\admin\Desktop\ProgramData\ProgramData\uninst.exe | executable | |
MD5:9EC3D89978C9A2EA2A7454D2913D79D2 | SHA256:7ACD2E8F32235743D25B48D9B679B553E60A6348E13EDD4F7EAB6AEE79FEFE2C | |||
| 6364 | svcr.exe | C:\ProgramData\removelastfolders.bin | a3x | |
MD5:E84169A715E34C4067940ED332361C7D | SHA256:1342E0E6019F6671E5C62F5295A99DFFAAE696C3DE2DC43719F960FE33A961F2 | |||
| 6404 | WinRAR.exe | C:\Users\admin\Desktop\ProgramData\ProgramData\alternateshell.exe | executable | |
MD5:9EC3D89978C9A2EA2A7454D2913D79D2 | SHA256:7ACD2E8F32235743D25B48D9B679B553E60A6348E13EDD4F7EAB6AEE79FEFE2C | |||
| 6404 | WinRAR.exe | C:\Users\admin\Desktop\ProgramData\ProgramData\svcr.exe | executable | |
MD5:0843004FB6F474DD6C69761BF1833DD4 | SHA256:7214D046DEE3CFBB7F4063F2D5F54ED453104602636A73625B5D5DEC385C5187 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
42
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4544 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6724 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6768 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3520 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3476 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3476 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5336 | SearchApp.exe | 2.23.209.130:443 | www.bing.com | Akamai International B.V. | GB | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |