| File name: | test.exe |
| Full analysis: | https://app.any.run/tasks/faa538ba-34b0-4bb1-833e-c4da6299d926 |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 19:23:19 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 7 sections |
| MD5: | 06C1DD22D2510A3303F1FA8C35BA7878 |
| SHA1: | A58A3A63628F7937A53FE4FA28477090E358C73D |
| SHA256: | D17C50F2AF14CD7C8F6FAB0F8E1F3C6645F6408888D37A4734C8C5F76C320DC9 |
| SSDEEP: | 98304:wD/lkMvqeLnc1ZaDPHUFK/uXbQx2UfuwiX8PHFC9uj8rhnoiWrIYqo7UJDZ2plic:VHKVtHTyMNUfi9W |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- test.exe (PID: 2716)
The process drops C-runtime libraries
- test.exe (PID: 2716)
Process drops legitimate windows executable
- test.exe (PID: 2716)
Application launched itself
- test.exe (PID: 2716)
- updater.exe (PID: 2188)
Process drops python dynamic module
- test.exe (PID: 2716)
Loads Python modules
- test.exe (PID: 1232)
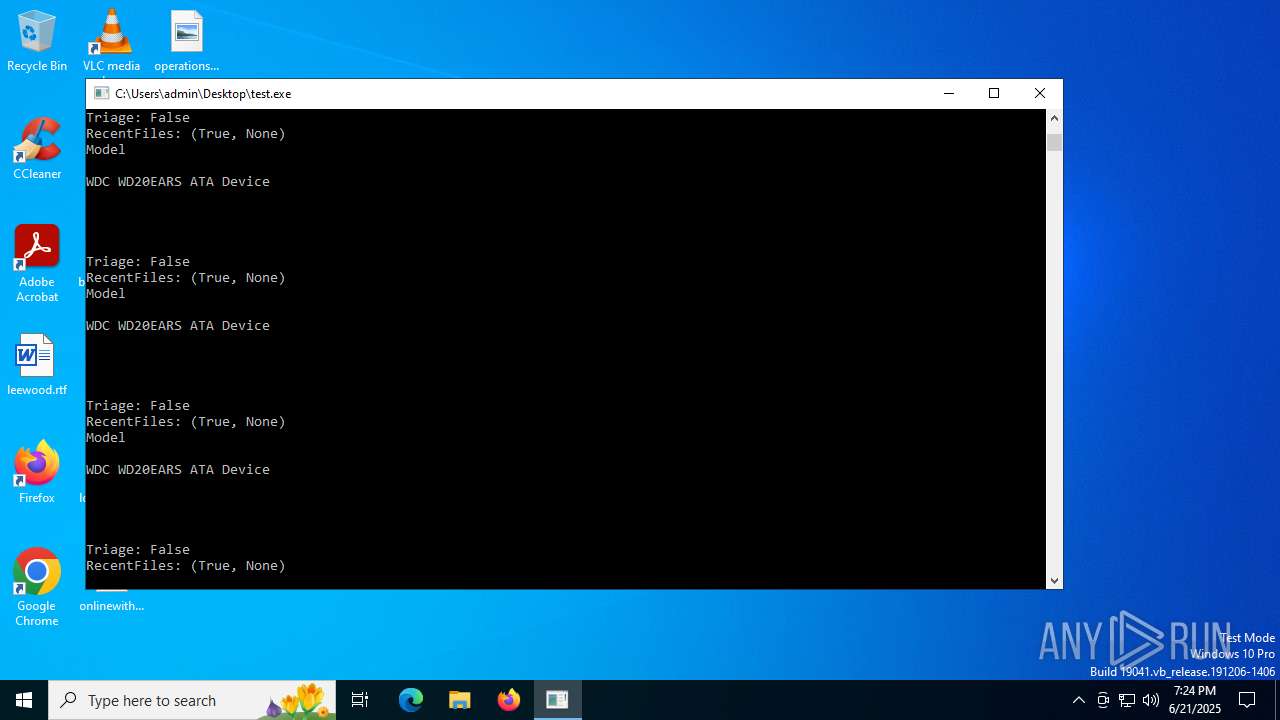
Uses WMIC.EXE to obtain physical disk drive information
- test.exe (PID: 1232)
The process executes via Task Scheduler
- updater.exe (PID: 2188)
INFO
Reads the computer name
- test.exe (PID: 2716)
- updater.exe (PID: 2188)
Checks supported languages
- test.exe (PID: 2716)
- test.exe (PID: 1232)
- updater.exe (PID: 2188)
- updater.exe (PID: 4692)
Create files in a temporary directory
- test.exe (PID: 2716)
The sample compiled with english language support
- test.exe (PID: 2716)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 5124)
- WMIC.exe (PID: 2524)
- WMIC.exe (PID: 5620)
- WMIC.exe (PID: 3620)
- WMIC.exe (PID: 6676)
- WMIC.exe (PID: 1204)
- WMIC.exe (PID: 5720)
- WMIC.exe (PID: 7072)
- WMIC.exe (PID: 6256)
- WMIC.exe (PID: 2668)
- WMIC.exe (PID: 6492)
- WMIC.exe (PID: 5528)
- WMIC.exe (PID: 2664)
- WMIC.exe (PID: 1136)
- WMIC.exe (PID: 3740)
- WMIC.exe (PID: 5724)
- WMIC.exe (PID: 432)
- WMIC.exe (PID: 4116)
- WMIC.exe (PID: 2708)
- WMIC.exe (PID: 4320)
- WMIC.exe (PID: 6892)
- WMIC.exe (PID: 4984)
- WMIC.exe (PID: 3588)
- WMIC.exe (PID: 6356)
- WMIC.exe (PID: 6840)
- WMIC.exe (PID: 3788)
- WMIC.exe (PID: 3048)
- WMIC.exe (PID: 1816)
- WMIC.exe (PID: 3580)
- WMIC.exe (PID: 5904)
- WMIC.exe (PID: 7116)
- WMIC.exe (PID: 888)
- WMIC.exe (PID: 5552)
- WMIC.exe (PID: 6160)
- WMIC.exe (PID: 1728)
- WMIC.exe (PID: 2076)
- WMIC.exe (PID: 3724)
- WMIC.exe (PID: 4168)
- WMIC.exe (PID: 2220)
- WMIC.exe (PID: 5060)
- WMIC.exe (PID: 1128)
- WMIC.exe (PID: 504)
- WMIC.exe (PID: 3652)
- WMIC.exe (PID: 4880)
- WMIC.exe (PID: 1100)
- WMIC.exe (PID: 4984)
- WMIC.exe (PID: 1688)
PyInstaller has been detected (YARA)
- test.exe (PID: 2716)
- test.exe (PID: 1232)
Reads the software policy settings
- slui.exe (PID: 6304)
Checks proxy server information
- slui.exe (PID: 6304)
Process checks whether UAC notifications are on
- updater.exe (PID: 2188)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:06:19 19:09:54+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.43 |
| CodeSize: | 179712 |
| InitializedDataSize: | 95232 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc650 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
184
Monitored processes
54
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 432 | wmic diskdrive get model | C:\Windows\System32\wbem\WMIC.exe | — | test.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 504 | wmic diskdrive get model | C:\Windows\System32\wbem\WMIC.exe | — | test.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 888 | wmic diskdrive get model | C:\Windows\System32\wbem\WMIC.exe | — | test.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1100 | wmic diskdrive get model | C:\Windows\System32\wbem\WMIC.exe | — | test.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1128 | wmic diskdrive get model | C:\Windows\System32\wbem\WMIC.exe | — | test.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1136 | wmic diskdrive get model | C:\Windows\System32\wbem\WMIC.exe | — | test.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1204 | wmic diskdrive get model | C:\Windows\System32\wbem\WMIC.exe | — | test.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1232 | "C:\Users\admin\Desktop\test.exe" | C:\Users\admin\Desktop\test.exe | — | test.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 1688 | wmic diskdrive get model | C:\Windows\System32\wbem\WMIC.exe | — | test.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1728 | wmic diskdrive get model | C:\Windows\System32\wbem\WMIC.exe | — | test.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
12 172
Read events
12 172
Write events
0
Delete events
0
Modification events
Executable files
50
Suspicious files
1
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2716 | test.exe | C:\Users\admin\AppData\Local\Temp\_MEI27162\_bz2.pyd | executable | |
MD5:057325E89B4DB46E6B18A52D1A691CAA | SHA256:5BA872CAA7FCEE0F4FB81C6E0201CEED9BD92A3624F16828DD316144D292A869 | |||
| 2716 | test.exe | C:\Users\admin\AppData\Local\Temp\_MEI27162\api-ms-win-core-console-l1-1-0.dll | executable | |
MD5:39852D24ACF76CF0B3A427F46663EFDF | SHA256:191E08DEA0AD5AC02E7E84669D9FFFA5AA67DC696E36077C5FA20D81C80B6A56 | |||
| 2716 | test.exe | C:\Users\admin\AppData\Local\Temp\_MEI27162\_decimal.pyd | executable | |
MD5:F465C15E7BACEAC920DC58A5FB922C1C | SHA256:F4A486A0CA6A53659159A404614C7E7EDCCB6BFBCDEB844F6CEE544436A826CB | |||
| 2716 | test.exe | C:\Users\admin\AppData\Local\Temp\_MEI27162\api-ms-win-core-debug-l1-1-0.dll | executable | |
MD5:A998282826D6091984D7D5F0BF476A31 | SHA256:263E038363527B7BED05110F37F7E5B95F82AAB9C0280C9C522CF7BFCE10FD7D | |||
| 2716 | test.exe | C:\Users\admin\AppData\Local\Temp\_MEI27162\api-ms-win-core-file-l2-1-0.dll | executable | |
MD5:4C9BF992AE40C7460A029B1046A7FB5E | SHA256:18655793B4D489F769327E3C8710ACED6B763C7873B6A8DC5AE6F28D228647F4 | |||
| 2716 | test.exe | C:\Users\admin\AppData\Local\Temp\_MEI27162\_socket.pyd | executable | |
MD5:69C4A9A654CF6D1684B73A431949B333 | SHA256:8DAEFAFF53E6956F5AEA5279A7C71F17D8C63E2B0D54031C3B9E82FCB0FB84DB | |||
| 2716 | test.exe | C:\Users\admin\AppData\Local\Temp\_MEI27162\VCRUNTIME140.dll | executable | |
MD5:862F820C3251E4CA6FC0AC00E4092239 | SHA256:36585912E5EAF83BA9FEA0631534F690CCDC2D7BA91537166FE53E56C221E153 | |||
| 2716 | test.exe | C:\Users\admin\AppData\Local\Temp\_MEI27162\_hashlib.pyd | executable | |
MD5:CF4120BAD9A7F77993DD7A95568D83D7 | SHA256:14765E83996FE6D50AEDC11BB41D7C427A3E846A6A6293A4A46F7EA7E3F14148 | |||
| 2716 | test.exe | C:\Users\admin\AppData\Local\Temp\_MEI27162\api-ms-win-core-handle-l1-1-0.dll | executable | |
MD5:F90E3B45C7942E3E30ECF1505253B289 | SHA256:7E45A1B997331F4D038F847F205904D6EC703DF7A8C5C660435697E318CED8FC | |||
| 2716 | test.exe | C:\Users\admin\AppData\Local\Temp\_MEI27162\api-ms-win-core-file-l1-1-0.dll | executable | |
MD5:E933CDD91FD5725873F57532F262F815 | SHA256:120C3AFED9CE2A981C61208757FCA0665F43926751EC8D0D13E10EF1096A0D48 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
32
TCP/UDP connections
49
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.24.77.22:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 184.24.77.22:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.24.77.22:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.190.159.129:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
— | — | POST | 200 | 20.190.159.73:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 16.7 Kb | whitelisted |
— | — | POST | 200 | 40.126.31.69:443 | https://login.live.com/RST2.srf | unknown | xml | 11.1 Kb | whitelisted |
— | — | POST | 200 | 40.126.31.3:443 | https://login.live.com/RST2.srf | unknown | xml | 11.1 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 184.24.77.22:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 184.24.77.22:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 184.24.77.22:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |