| File name: | System Destroyer Virus.zip |
| Full analysis: | https://app.any.run/tasks/dd43a469-ddb4-4c80-92c4-26def6c349ad |
| Verdict: | Malicious activity |
| Analysis date: | March 17, 2024, 20:06:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 922339F35F039C3C267C15084171F998 |
| SHA1: | 67C0D90CBE1E2E403F7D912218E5624F63D241D0 |
| SHA256: | D16C355CC672E2CE6514FB2D6A5EA4E85458ED38578FFAA691E091F2C51E9638 |
| SSDEEP: | 98304:O6eDDY4ORgLQLtD5aSmkRdc6597EnLrIC7UK11ydFLapZsLSFN/3UziDnzXTa24M:7JNEh |
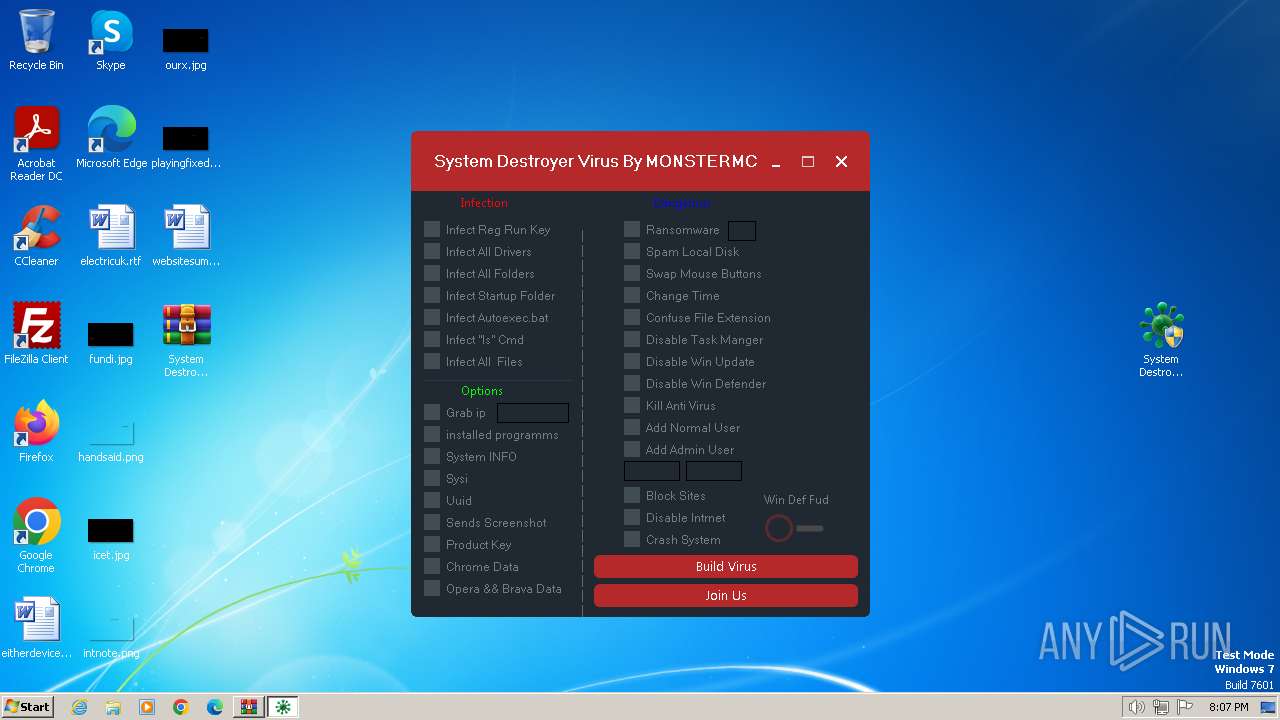
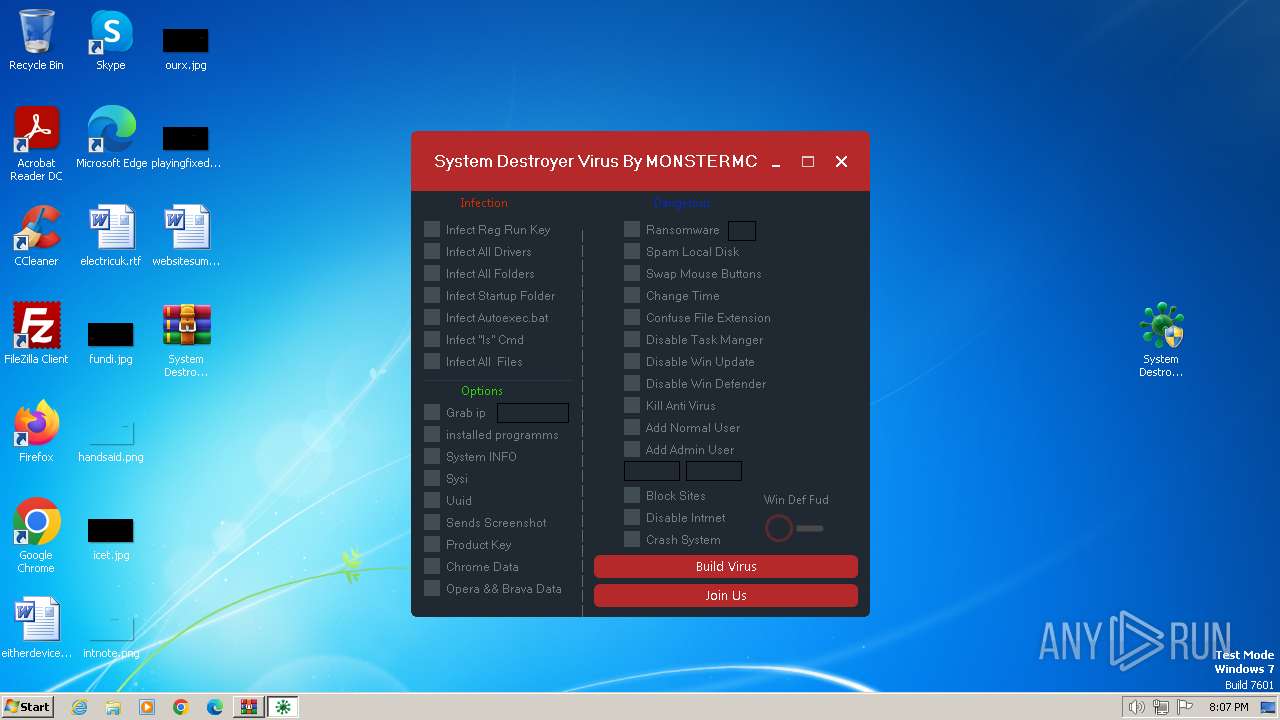
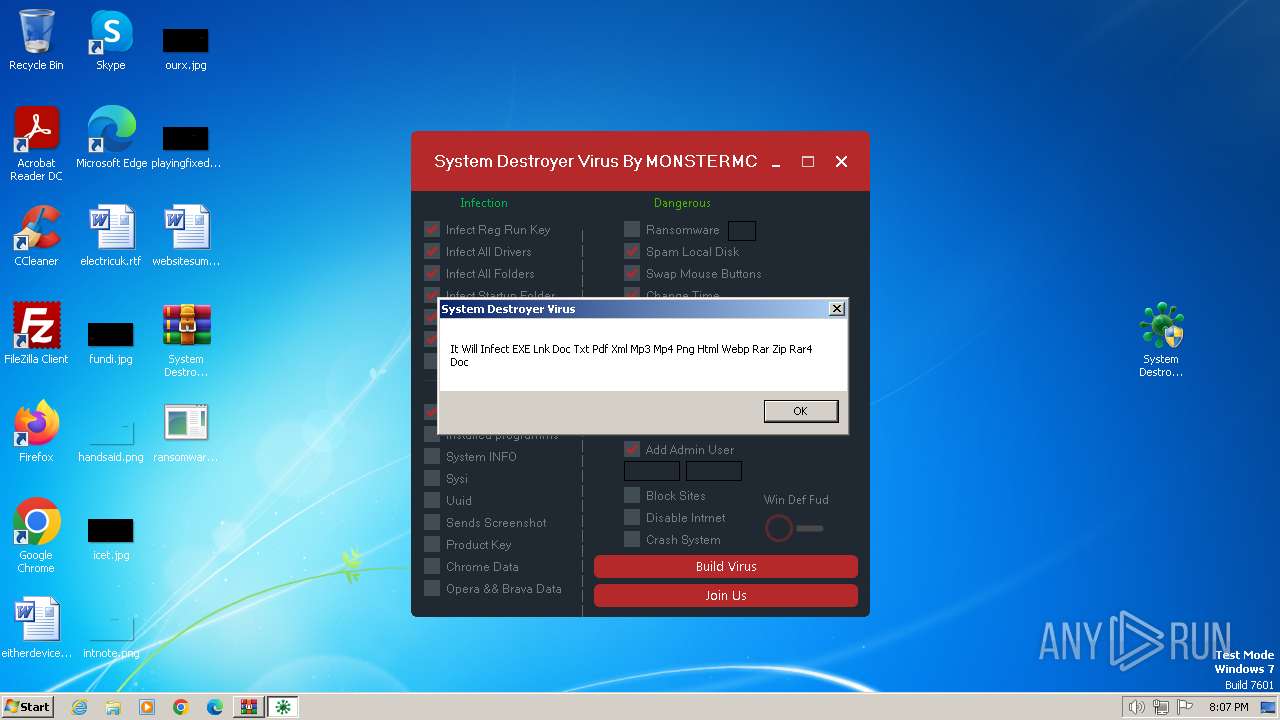
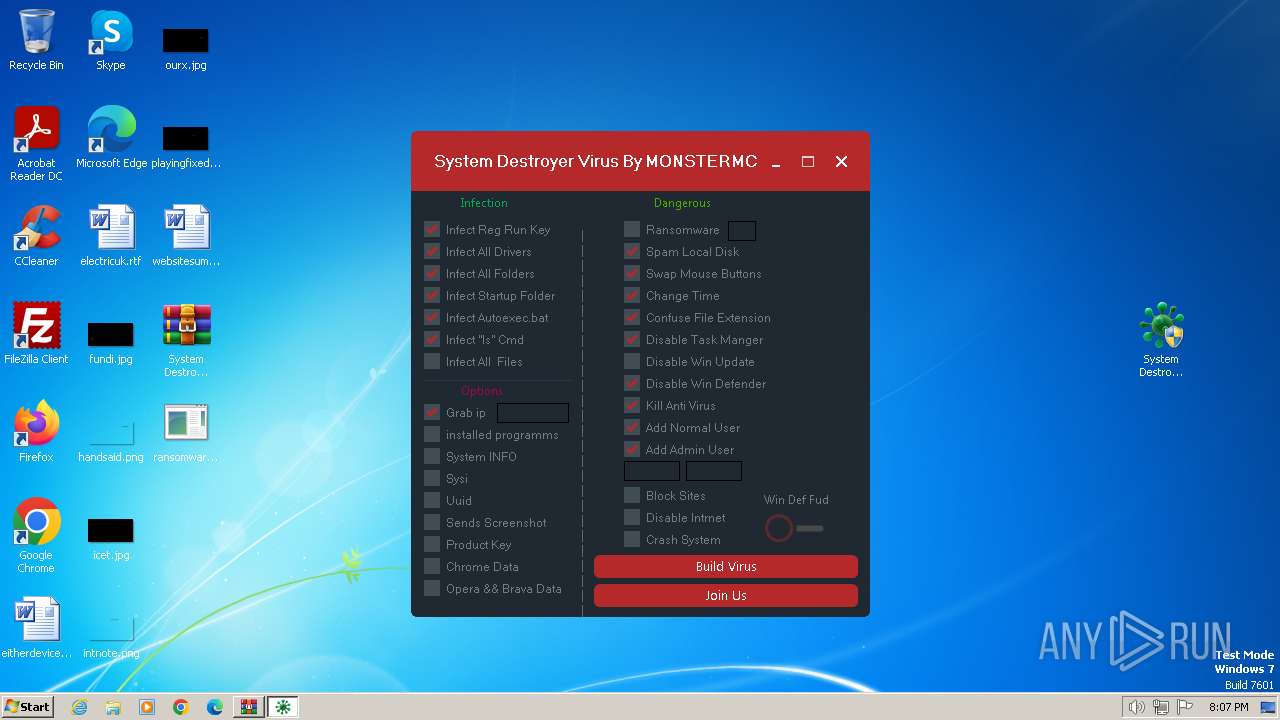
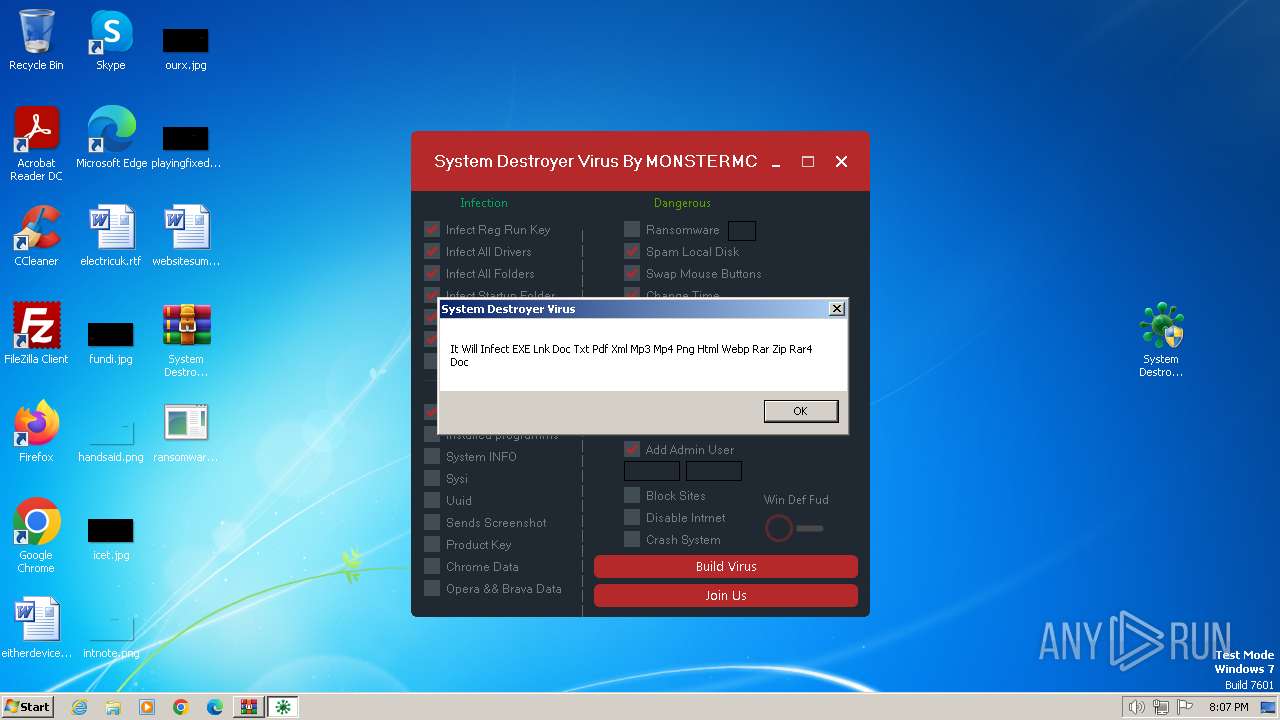
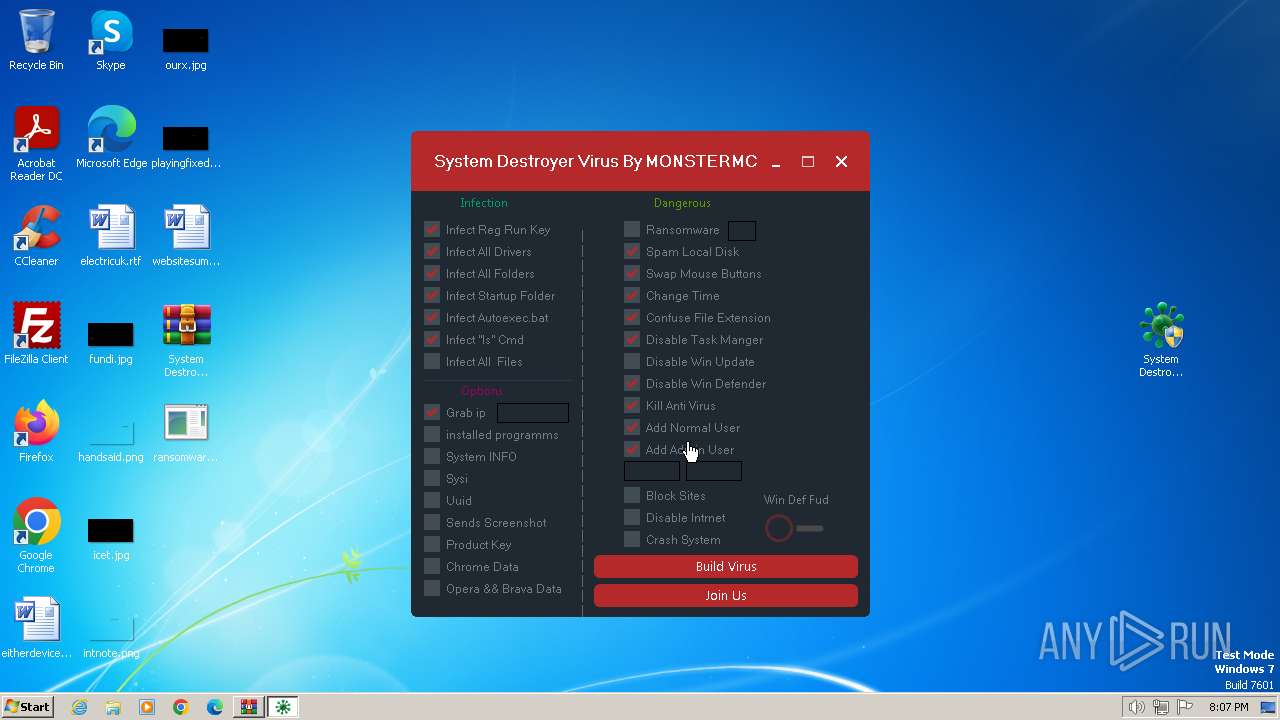
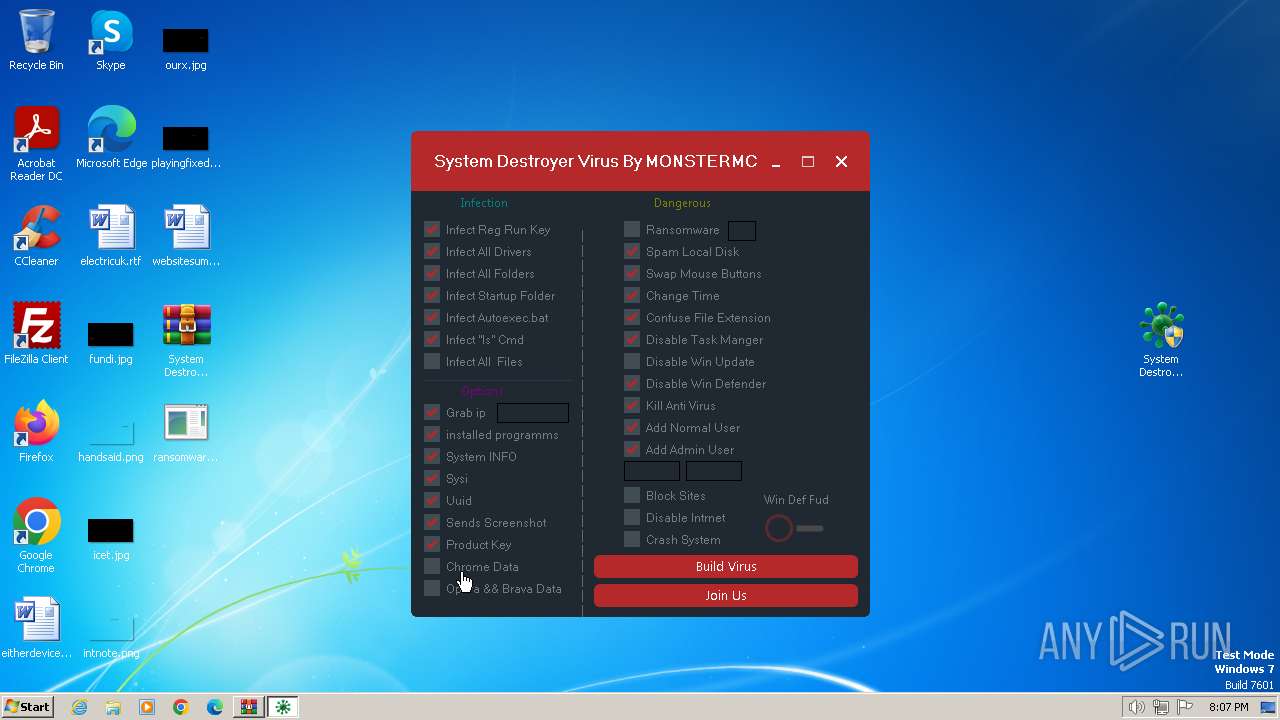
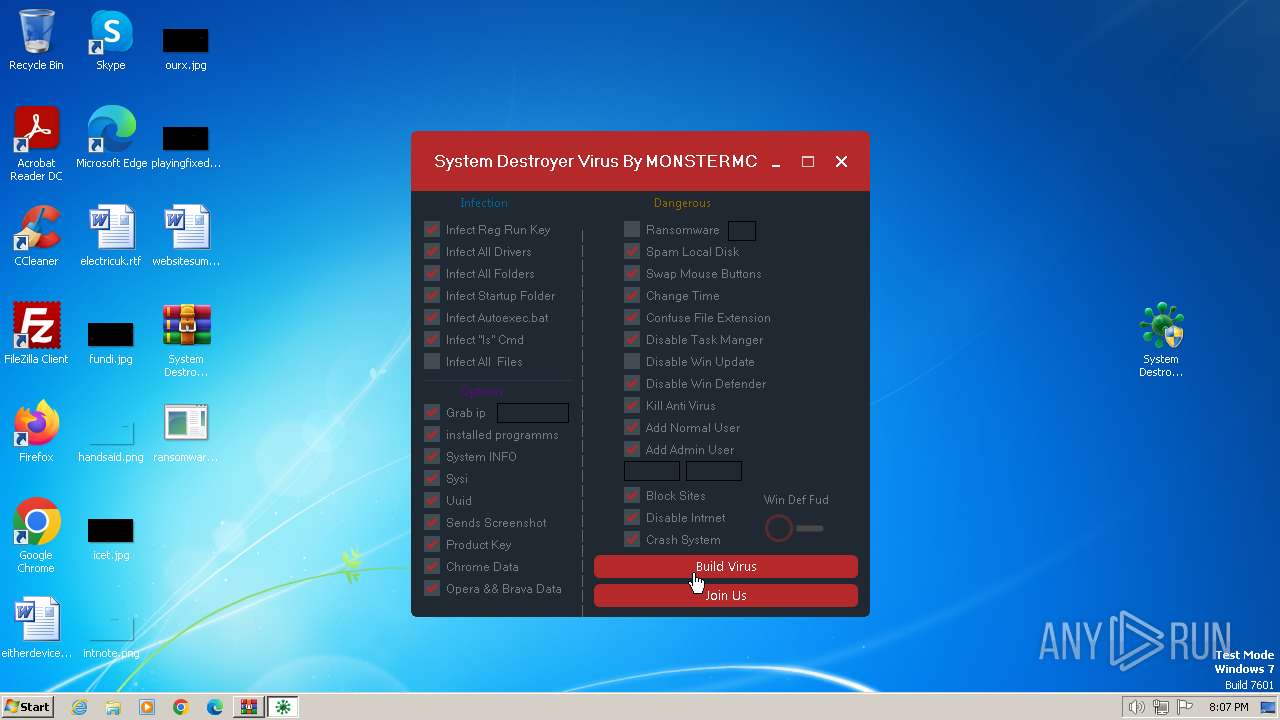
MALICIOUS
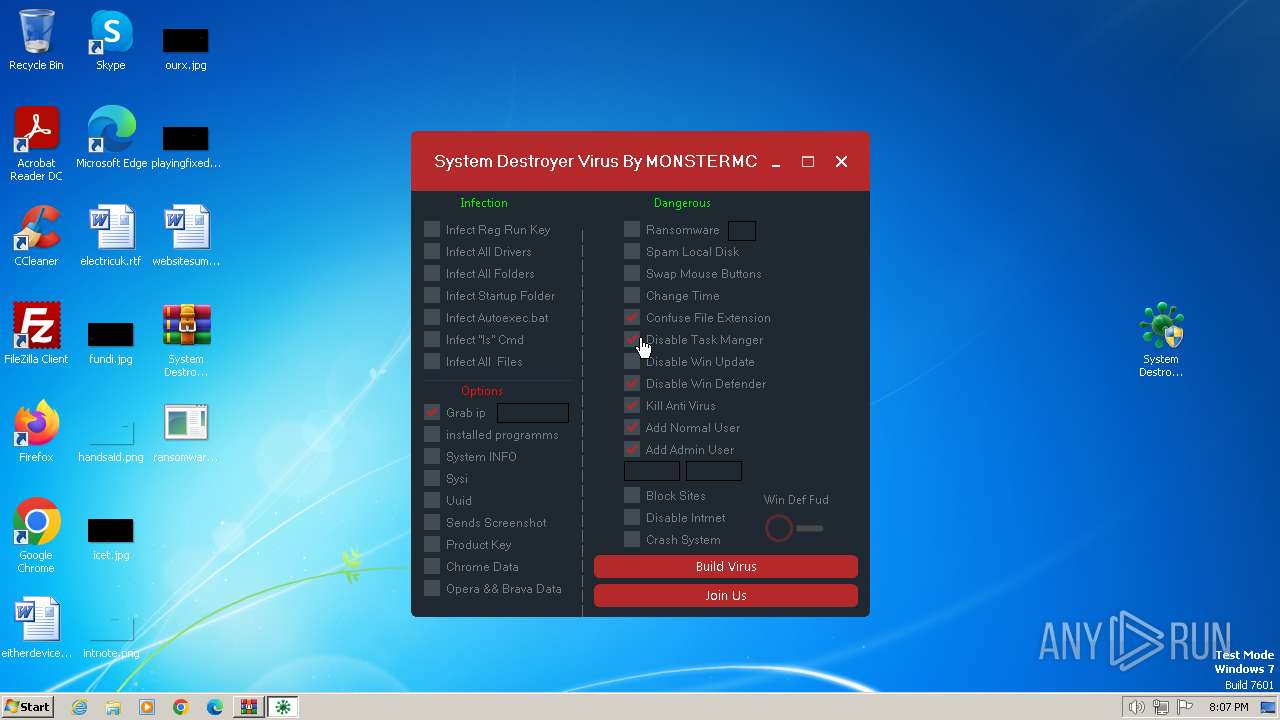
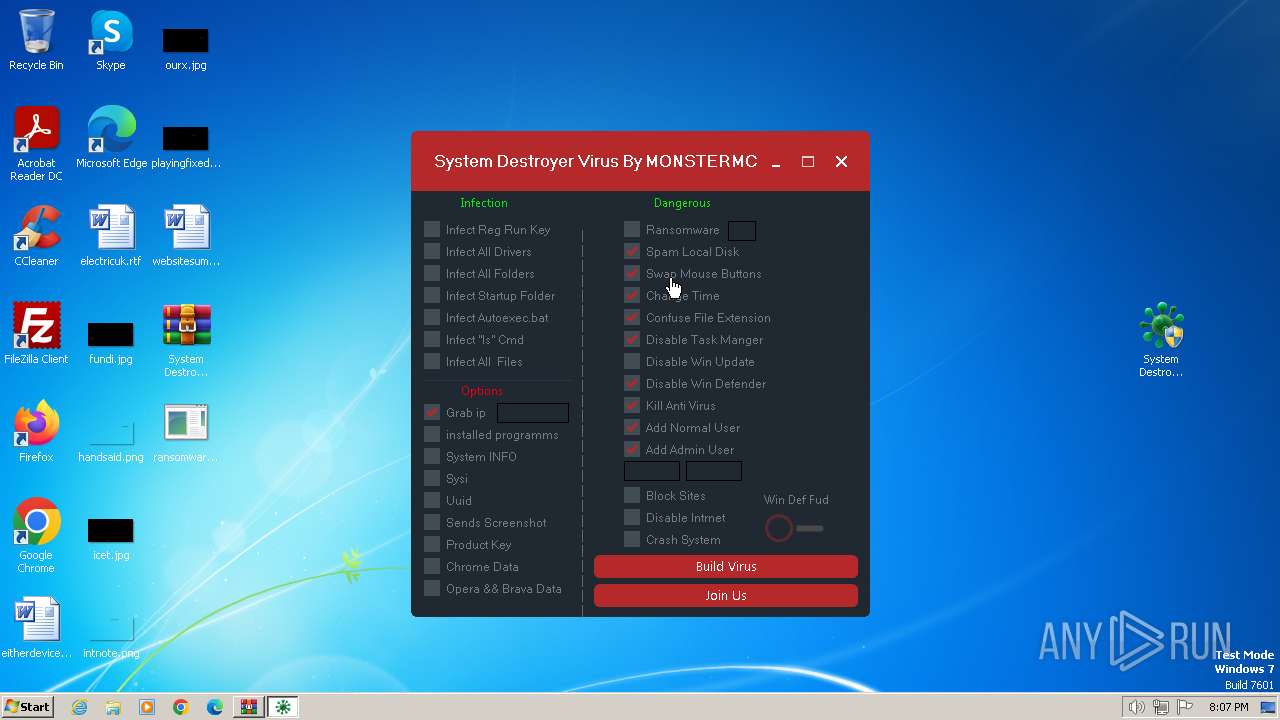
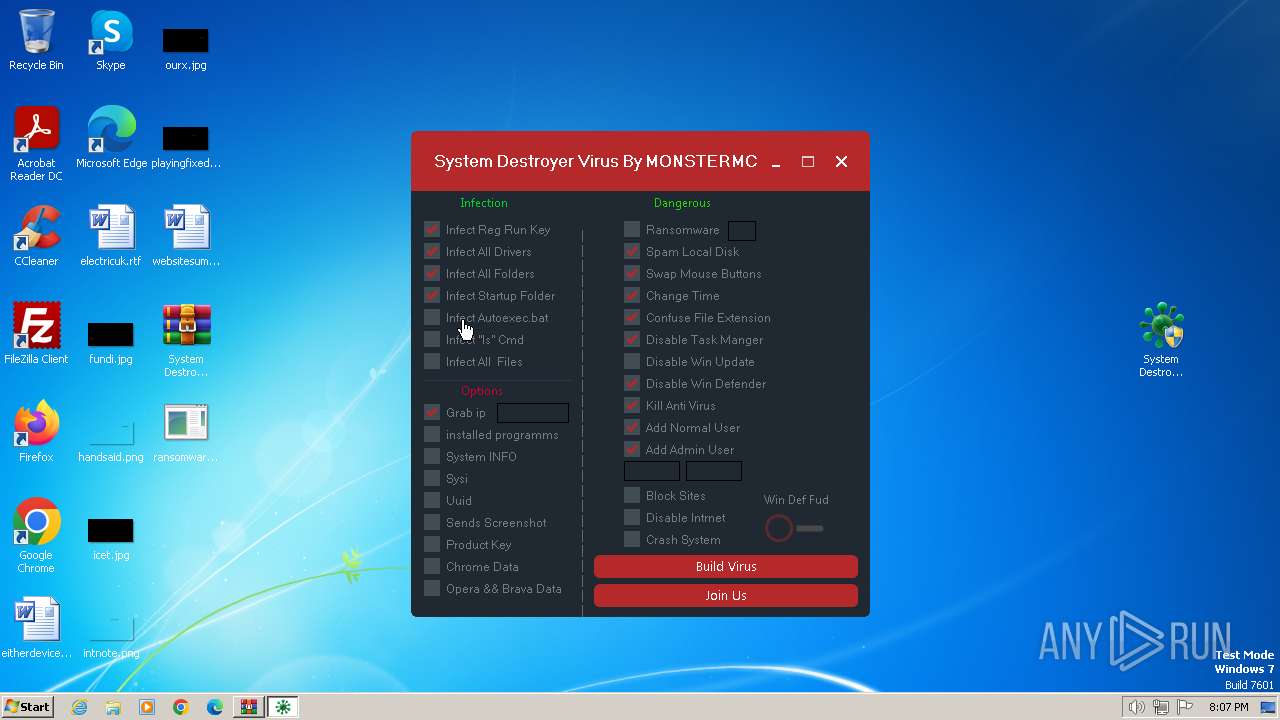
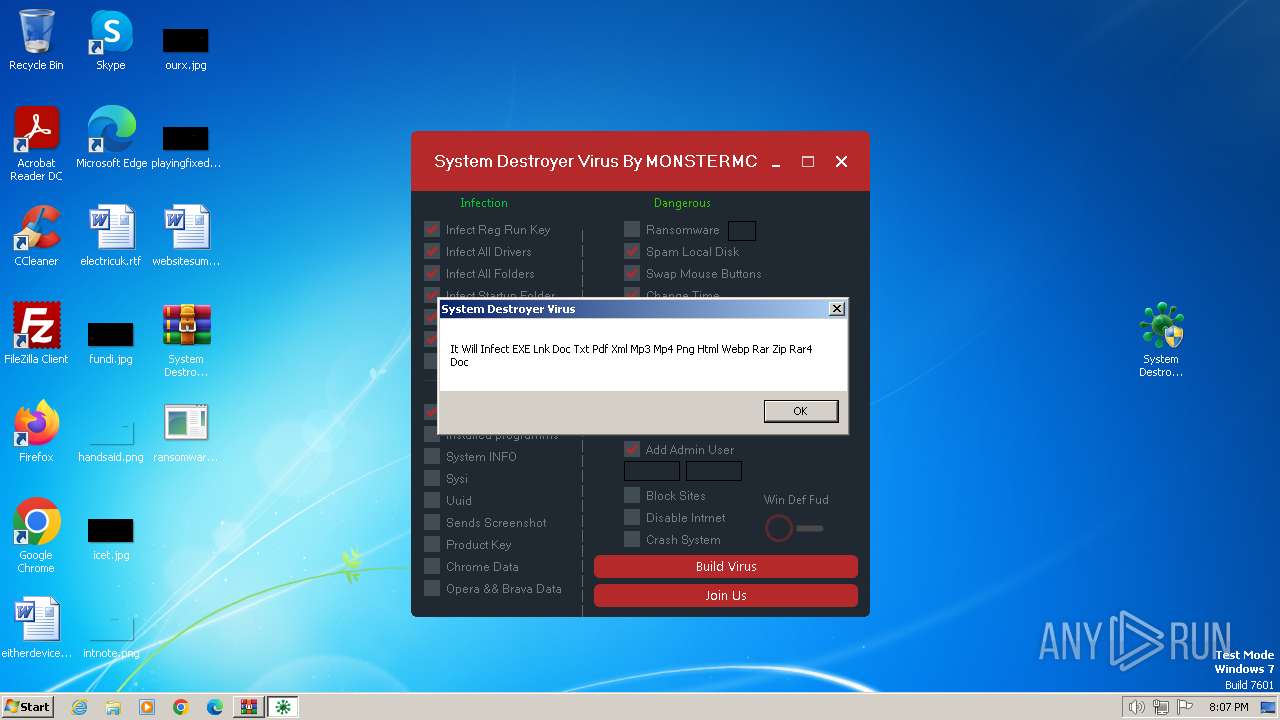
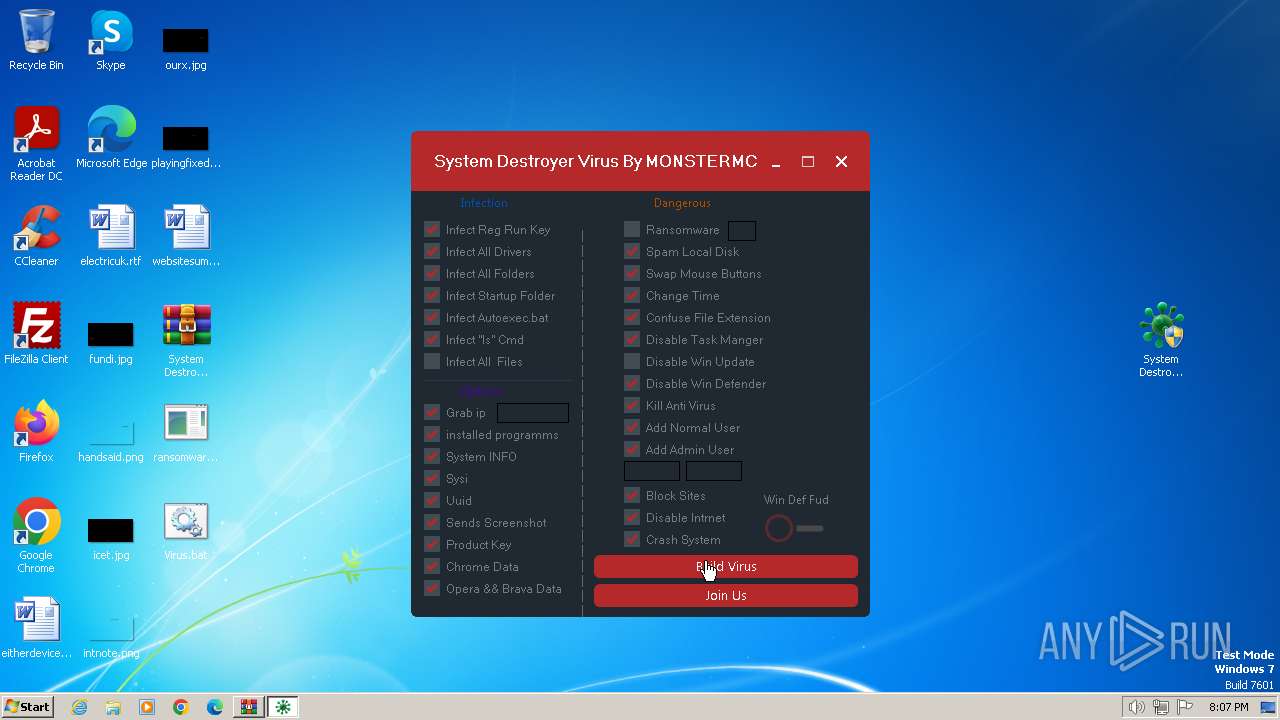
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1692)
Changes the autorun value in the registry
- reg.exe (PID: 2632)
Creates a writable file in the system directory
- cmd.exe (PID: 3984)
SUSPICIOUS
Reads the BIOS version
- System Destroyer Virus.exe (PID: 748)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 3984)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 3984)
Creates file in the systems drive root
- cmd.exe (PID: 3984)
INFO
Checks supported languages
- System Destroyer Virus.exe (PID: 748)
Manual execution by a user
- System Destroyer Virus.exe (PID: 1824)
- System Destroyer Virus.exe (PID: 748)
- cmd.exe (PID: 3984)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1692)
Process checks whether UAC notifications are on
- System Destroyer Virus.exe (PID: 748)
Reads the computer name
- System Destroyer Virus.exe (PID: 748)
Reads the machine GUID from the registry
- System Destroyer Virus.exe (PID: 748)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:10:13 03:07:56 |
| ZipCRC: | 0x1b37bcc6 |
| ZipCompressedSize: | 2409970 |
| ZipUncompressedSize: | 2439680 |
| ZipFileName: | System Destroyer Virus.exe |
Total processes
53
Monitored processes
6
Malicious processes
0
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 748 | "C:\Users\admin\Desktop\System Destroyer Virus.exe" | C:\Users\admin\Desktop\System Destroyer Virus.exe | explorer.exe | ||||||||||||
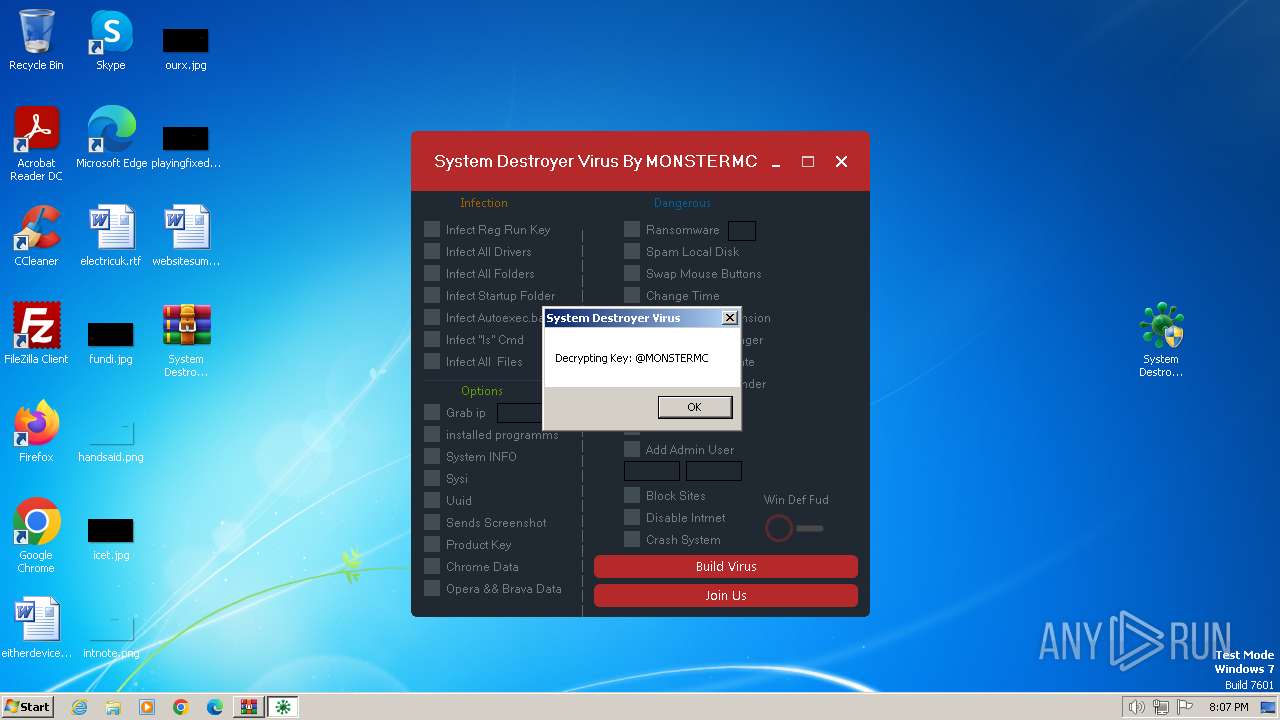
User: admin Company: My Telegram:@MONSTERMC Integrity Level: HIGH Description: System Destroyer Virus Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 840 | attrib +h C:\Users\admin\Desktop\Virus.bat | C:\Windows\System32\attrib.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1692 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\System Destroyer Virus.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1824 | "C:\Users\admin\Desktop\System Destroyer Virus.exe" | C:\Users\admin\Desktop\System Destroyer Virus.exe | — | explorer.exe | |||||||||||
User: admin Company: My Telegram:@MONSTERMC Integrity Level: MEDIUM Description: System Destroyer Virus Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2632 | reg add "hklm\Software\Microsoft\Windows\CurrentVersion\Run" /v "rundll32_26552_toolbar" /t "REG_SZ" /d C:\Users\admin\Desktop\Virus.bat /f | C:\Windows\System32\reg.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3984 | "C:\Windows\System32\cmd.exe" /C "C:\Users\admin\Desktop\Virus.bat" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
2 922
Read events
2 910
Write events
12
Delete events
0
Modification events
| (PID) Process: | (1692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1692) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (1692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (1692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\System Destroyer Virus.zip | |||
| (PID) Process: | (1692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
2
Suspicious files
1
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3984 | cmd.exe | C:\Windows\system32\PathHost | — | |
MD5:— | SHA256:— | |||
| 1692 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1692.750\System Destroyer Virus.exe | executable | |
MD5:452BFF8C8B53075B1AF79E3FA80EA966 | SHA256:A51CE89B49D7AF1B638055323249002785CB2FC8C2799C306D05FB7AC291FBF4 | |||
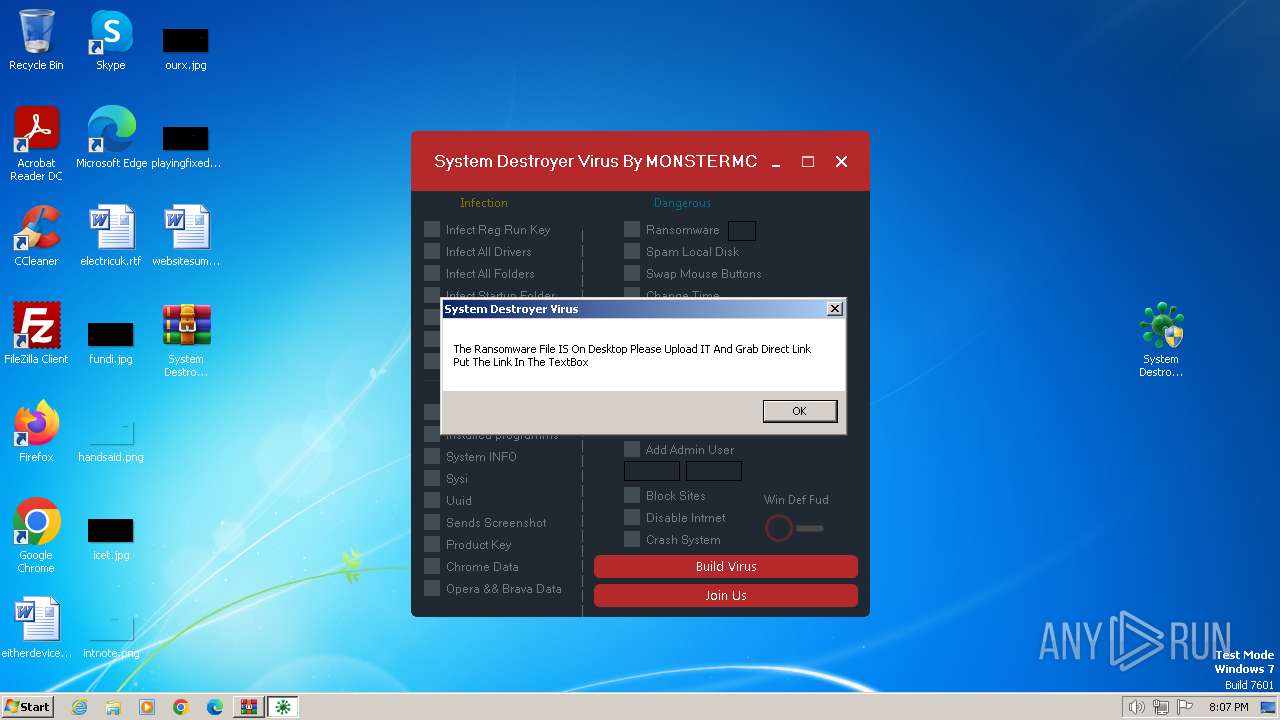
| 748 | System Destroyer Virus.exe | C:\Users\admin\Desktop\ransomware | compressed | |
MD5:F6183D188EE1F2867D7C13CAE5570F9F | SHA256:F0B7F041A66337A2D325A30F0DFE0C492686084015B479F64C2ABFB35204CE4E | |||
| 3984 | cmd.exe | C:\autorun.inf | text | |
MD5:9CC52BF4A1B9E598ADBE3B45EF67C0C1 | SHA256:3277EBE14439FF683F0485633465903BAD62AA6C6218221259FA145F7F4B806A | |||
| 748 | System Destroyer Virus.exe | C:\Users\admin\Desktop\Virus.bat | text | |
MD5:17294C16825DBC8A6C44D4787A8E7663 | SHA256:3121CA7FDC6FCE8802224D8B3445E3A3660A1B8534F03D1288C358AB4DE0EE56 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |