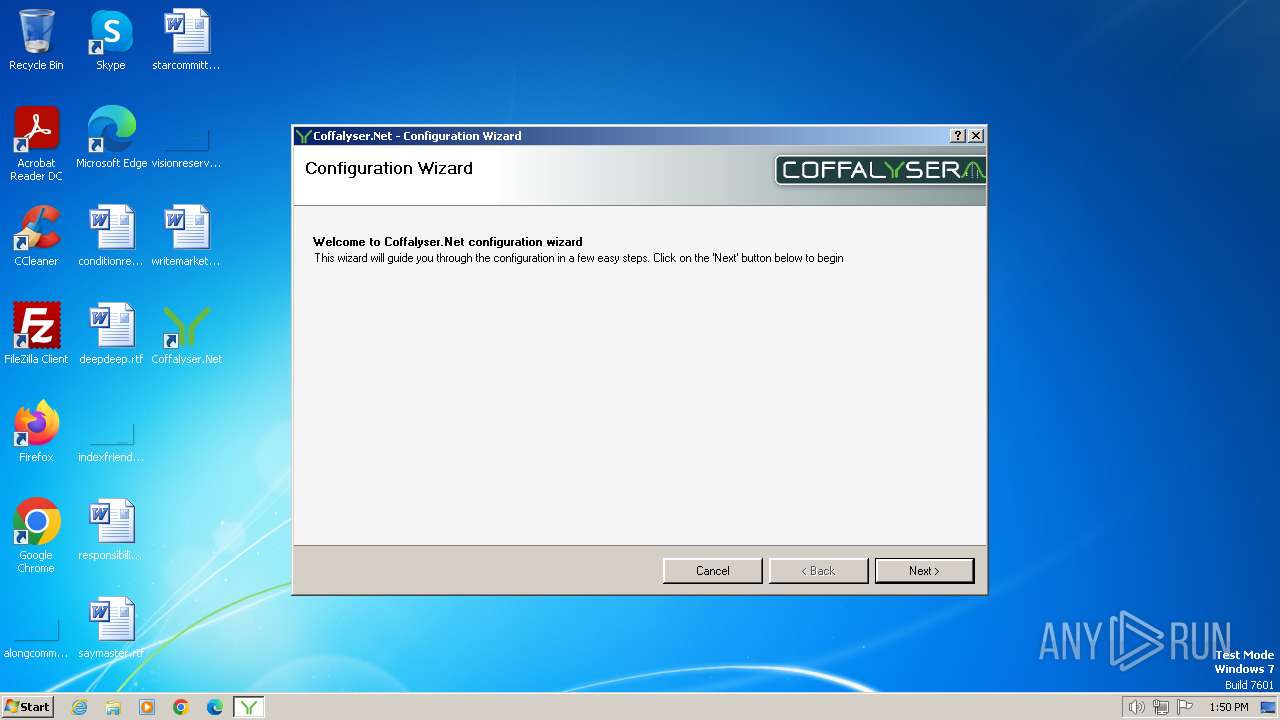
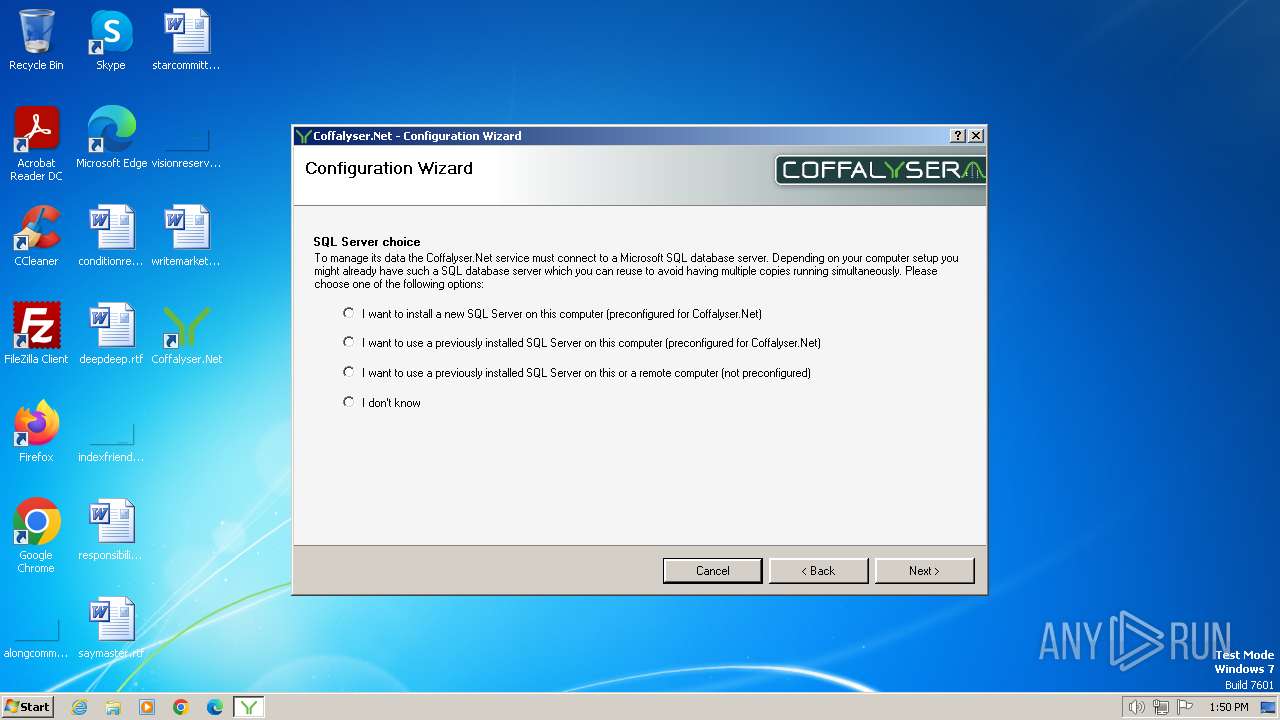
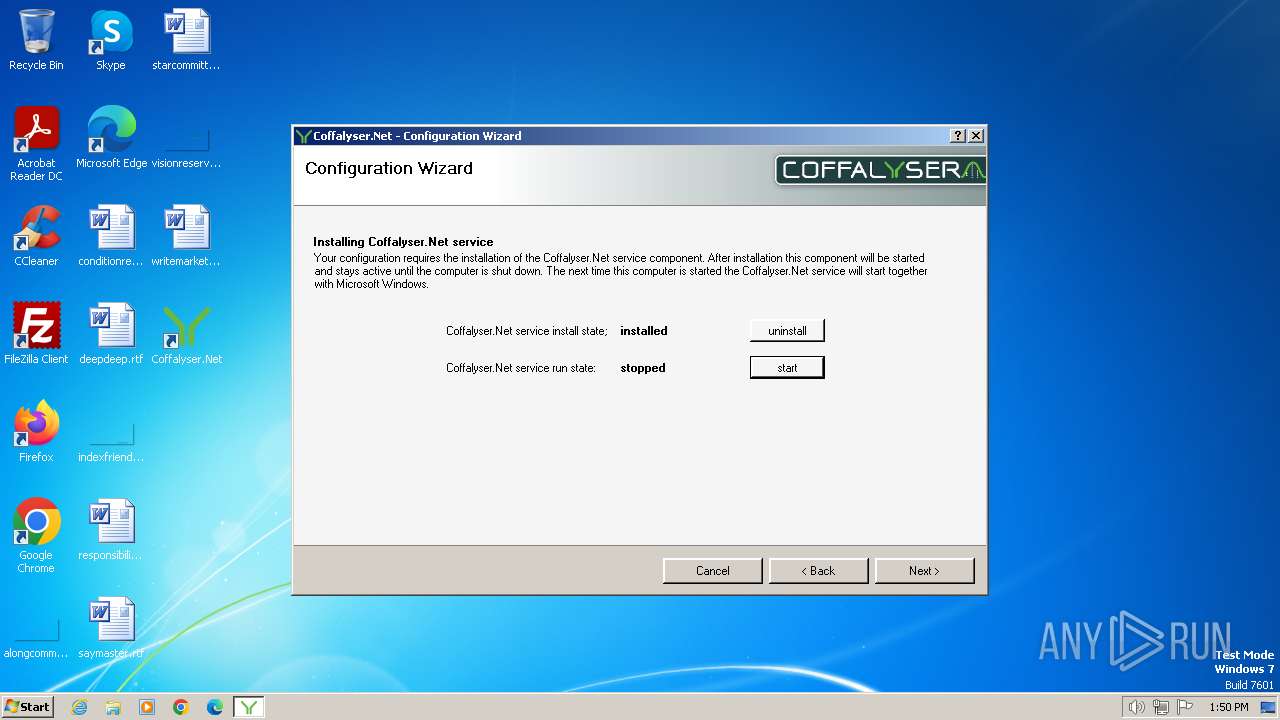
| File name: | Coffalyser.Net.msi |
| Full analysis: | https://app.any.run/tasks/99353b4b-c2a4-4300-b702-ed56c482e09b |
| Verdict: | Malicious activity |
| Analysis date: | June 23, 2024, 12:48:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Create Time/Date: Mon Jun 21 07:00:00 1999, Name of Creating Application: Windows Installer, Security: 1, Code page: 1252, Template: Intel;1033, Number of Pages: 200, Revision Number: {296F1FB1-689C-4183-839A-037E369E8A23}, Title: Coffalyser.Net, Author: MRC Holland, Number of Words: 2, Last Saved Time/Date: Mon Jan 29 18:59:19 2024, Last Printed: Mon Jan 29 18:59:19 2024 |
| MD5: | ADDD9D4F6F554012ABD98B0CFAEEEFE6 |
| SHA1: | 3C05DC5EF8F3C29D85D6C31AAD5D57377660660E |
| SHA256: | D15A9C675609D588840194282816C6E62446D4D7D9F581132B16018298D12C9D |
| SSDEEP: | 98304:fxOb0el1eMpCeUSJp35+MyuVWFRMe4e7XxzS4grMpPnIMAyW3Zo+nW6O+/PxlQip:5g2CoH |
MALICIOUS
Drops the executable file immediately after the start
- msiexec.exe (PID: 3392)
- msiexec.exe (PID: 3280)
Creates a writable file in the system directory
- CoffalyserServer.exe (PID: 660)
SUSPICIOUS
Process drops legitimate windows executable
- msiexec.exe (PID: 3392)
- msiexec.exe (PID: 3280)
Executes as Windows Service
- VSSVC.exe (PID: 2748)
- CoffalyserServer.exe (PID: 660)
- CoffalyserServer.exe (PID: 900)
- CoffalyserServer.exe (PID: 3900)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 3280)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 3084)
- CoffalyserClient.exe (PID: 3844)
- CoffalyserClient.exe (PID: 1180)
- CoffalyserClient.exe (PID: 4008)
- CoffalyserServer.exe (PID: 900)
- CoffalyserServer.exe (PID: 660)
- CoffalyserClient.exe (PID: 1944)
- CoffalyserClient.exe (PID: 3748)
- CoffalyserClient.exe (PID: 1488)
- CoffalyserServer.exe (PID: 3900)
Reads the Internet Settings
- CoffalyserClient.exe (PID: 3844)
- CoffalyserClient.exe (PID: 1180)
- CoffalyserClient.exe (PID: 4008)
- CoffalyserClient.exe (PID: 3748)
- CoffalyserClient.exe (PID: 1944)
- CoffalyserClient.exe (PID: 1488)
Application launched itself
- CoffalyserClient.exe (PID: 1180)
- CoffalyserClient.exe (PID: 3844)
- CoffalyserClient.exe (PID: 1944)
- CoffalyserClient.exe (PID: 1488)
INFO
Checks supported languages
- msiexec.exe (PID: 3280)
- msiexec.exe (PID: 3216)
- msiexec.exe (PID: 3084)
- CoffalyserClient.exe (PID: 3844)
- msiexec.exe (PID: 3336)
- CoffalyserClient.exe (PID: 4008)
- CoffalyserServer.exe (PID: 660)
- CoffalyserClient.exe (PID: 1180)
- CoffalyserSqlServerInstallationWizard.exe (PID: 3804)
- CoffalyserClient.exe (PID: 1488)
- CoffalyserServer.exe (PID: 900)
- CoffalyserClient.exe (PID: 1944)
- CoffalyserClient.exe (PID: 3748)
- CoffalyserServer.exe (PID: 3900)
Reads the computer name
- msiexec.exe (PID: 3216)
- msiexec.exe (PID: 3280)
- msiexec.exe (PID: 3084)
- CoffalyserClient.exe (PID: 3844)
- msiexec.exe (PID: 3336)
- CoffalyserClient.exe (PID: 1180)
- CoffalyserClient.exe (PID: 4008)
- CoffalyserServer.exe (PID: 660)
- CoffalyserServer.exe (PID: 900)
- CoffalyserSqlServerInstallationWizard.exe (PID: 3804)
- CoffalyserClient.exe (PID: 1488)
- CoffalyserClient.exe (PID: 1944)
- CoffalyserClient.exe (PID: 3748)
- CoffalyserServer.exe (PID: 3900)
Reads the machine GUID from the registry
- msiexec.exe (PID: 3216)
- msiexec.exe (PID: 3280)
- msiexec.exe (PID: 3084)
- CoffalyserClient.exe (PID: 3844)
- msiexec.exe (PID: 3336)
- CoffalyserClient.exe (PID: 1180)
- CoffalyserClient.exe (PID: 4008)
- CoffalyserServer.exe (PID: 900)
- CoffalyserSqlServerInstallationWizard.exe (PID: 3804)
- CoffalyserClient.exe (PID: 1488)
- CoffalyserServer.exe (PID: 660)
- CoffalyserClient.exe (PID: 1944)
- CoffalyserClient.exe (PID: 3748)
- CoffalyserServer.exe (PID: 3900)
Create files in a temporary directory
- msiexec.exe (PID: 3216)
- msiexec.exe (PID: 3280)
- msiexec.exe (PID: 3336)
Executable content was dropped or overwritten
- msiexec.exe (PID: 3392)
- msiexec.exe (PID: 3280)
Application launched itself
- msiexec.exe (PID: 3280)
Creates a software uninstall entry
- msiexec.exe (PID: 3280)
Creates files or folders in the user directory
- CoffalyserClient.exe (PID: 3844)
Reads Environment values
- CoffalyserServer.exe (PID: 900)
- CoffalyserClient.exe (PID: 4008)
- CoffalyserServer.exe (PID: 660)
- CoffalyserClient.exe (PID: 1488)
- CoffalyserClient.exe (PID: 3748)
- CoffalyserServer.exe (PID: 3900)
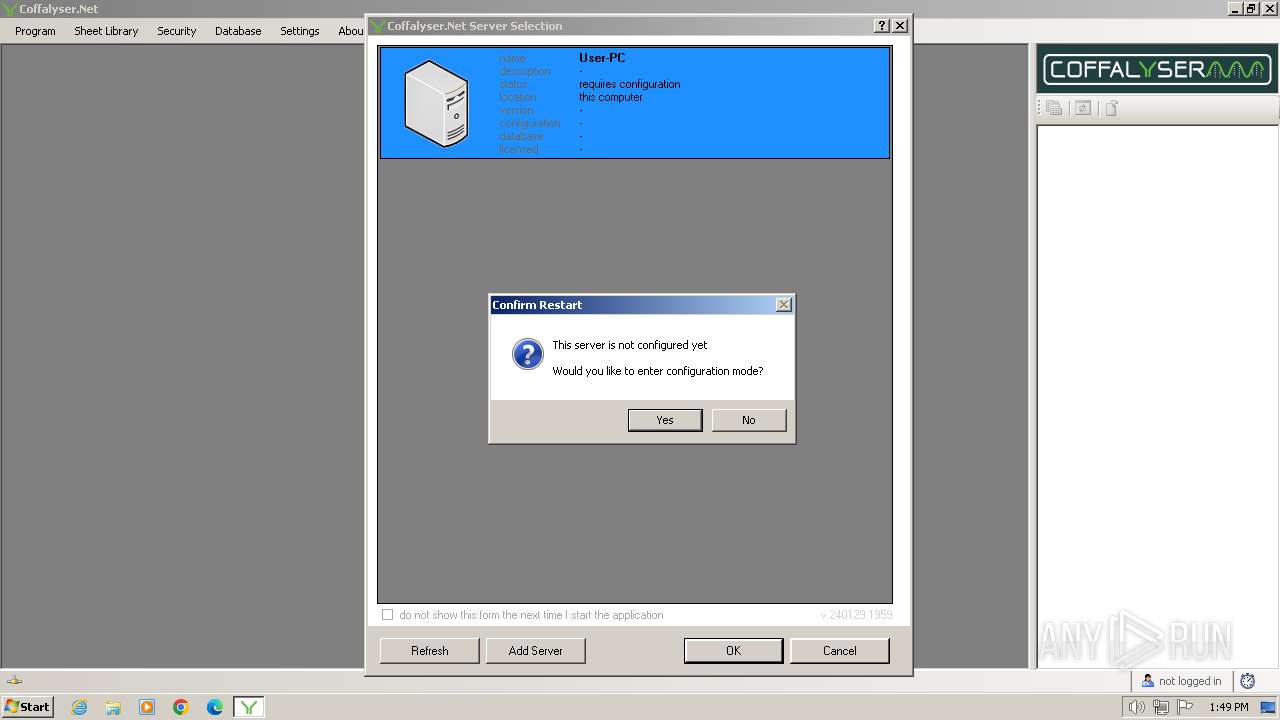
Manual execution by a user
- CoffalyserClient.exe (PID: 1488)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (90.2) |
|---|---|---|
| .msp | | | Windows Installer Patch (8.4) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CreateDate: | 1999:06:21 07:00:00 |
|---|---|
| Software: | Windows Installer |
| Security: | Password protected |
| CodePage: | Windows Latin 1 (Western European) |
| Template: | Intel;1033 |
| Pages: | 200 |
| RevisionNumber: | {296F1FB1-689C-4183-839A-037E369E8A23} |
| Title: | Coffalyser.Net |
| Subject: | - |
| Author: | MRC Holland |
| Keywords: | - |
| Comments: | - |
| Words: | 2 |
| ModifyDate: | 2024:01:29 18:59:19 |
| LastPrinted: | 2024:01:29 18:59:19 |
Total processes
62
Monitored processes
16
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 660 | "C:\Program Files\MRC-Holland\Coffalyser.Net\CoffalyserServer.exe" | C:\Program Files\MRC-Holland\Coffalyser.Net\CoffalyserServer.exe | services.exe | ||||||||||||
User: SYSTEM Company: MRC-Holland / Berg IT Solutions (BITS) Integrity Level: SYSTEM Description: CoffalyserServerEngine Exit code: 0 Version: 1.1.8794.35974 Modules
| |||||||||||||||
| 900 | "C:\Program Files\MRC-Holland\Coffalyser.Net\CoffalyserServer.exe" | C:\Program Files\MRC-Holland\Coffalyser.Net\CoffalyserServer.exe | services.exe | ||||||||||||
User: SYSTEM Company: MRC-Holland / Berg IT Solutions (BITS) Integrity Level: SYSTEM Description: CoffalyserServerEngine Exit code: 0 Version: 1.1.8794.35974 Modules
| |||||||||||||||
| 1180 | "C:\Program Files\MRC-Holland\Coffalyser.Net\CoffalyserClient.exe" /SERVICE_CONFIGURE | C:\Program Files\MRC-Holland\Coffalyser.Net\CoffalyserClient.exe | CoffalyserClient.exe | ||||||||||||
User: admin Company: MRC-Holland / Berg IT Solutions (BITS) Integrity Level: MEDIUM Description: CoffalyserClient Exit code: 999 Version: 1.1.8794.35975 Modules
| |||||||||||||||
| 1488 | "C:\Program Files\MRC-Holland\Coffalyser.Net\CoffalyserClient.exe" | C:\Program Files\MRC-Holland\Coffalyser.Net\CoffalyserClient.exe | explorer.exe | ||||||||||||
User: admin Company: MRC-Holland / Berg IT Solutions (BITS) Integrity Level: MEDIUM Description: CoffalyserClient Exit code: 999 Version: 1.1.8794.35975 Modules
| |||||||||||||||
| 1944 | "C:\Program Files\MRC-Holland\Coffalyser.Net\CoffalyserClient.exe" /SERVICE_CONFIGURE | C:\Program Files\MRC-Holland\Coffalyser.Net\CoffalyserClient.exe | CoffalyserClient.exe | ||||||||||||
User: admin Company: MRC-Holland / Berg IT Solutions (BITS) Integrity Level: MEDIUM Description: CoffalyserClient Exit code: 999 Version: 1.1.8794.35975 Modules
| |||||||||||||||
| 2748 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3084 | C:\Windows\system32\MsiExec.exe -Embedding 52CF33F18EC08FDC03ADD08771560E96 E Global\MSI0000 | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3216 | C:\Windows\system32\MsiExec.exe -Embedding 43C1A44685158C03D06434F5D986027D C | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3280 | C:\Windows\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3336 | C:\Windows\system32\MsiExec.exe -Embedding A7490FBBC74EB1744215E8C4D71981E8 | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
22 266
Read events
21 869
Write events
352
Delete events
45
Modification events
| (PID) Process: | (3280) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 400000000000000088BE20AE6BC5DA01D00C0000C00A0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3280) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 400000000000000088BE20AE6BC5DA01D00C0000C00A0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3280) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 75 | |||
| (PID) Process: | (3280) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 40000000000000009A53D8AE6BC5DA01D00C0000C00A0000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3280) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 40000000000000009A53D8AE6BC5DA01D00C0000840B0000E8030000010000000000000000000000660BD30121D15E4FAA659C3ED4C1812C0000000000000000 | |||
| (PID) Process: | (2748) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000A87ADFAE6BC5DA01BC0A000014040000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2748) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000A87ADFAE6BC5DA01BC0A0000FC080000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2748) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000A87ADFAE6BC5DA01BC0A0000180B0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2748) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000A87ADFAE6BC5DA01BC0A0000780B0000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2748) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 400000000000000002DDE1AE6BC5DA01BC0A0000780B0000E8030000000000000100000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
33
Suspicious files
17
Text files
28
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3280 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 3216 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\CFGE4BF.tmp | xml | |
MD5:2BE48F533744EFA173A2EDE37EA8031E | SHA256:02375FA63B79648ED6BB419C08F78BA9032EE22BA7170250E24427F47FDDFA4E | |||
| 3392 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIE461.tmp | executable | |
MD5:684F2D21637CB5835172EDAD55B6A8D9 | SHA256:DA1FE86141C446921021BB26B6FE2BD2D1BB51E3E614F46F8103FFAD8042F2C0 | |||
| 3392 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIE4CF.tmp | executable | |
MD5:684F2D21637CB5835172EDAD55B6A8D9 | SHA256:DA1FE86141C446921021BB26B6FE2BD2D1BB51E3E614F46F8103FFAD8042F2C0 | |||
| 3280 | msiexec.exe | C:\Windows\Installer\51ee9.msi | executable | |
MD5:ADDD9D4F6F554012ABD98B0CFAEEEFE6 | SHA256:D15A9C675609D588840194282816C6E62446D4D7D9F581132B16018298D12C9D | |||
| 3280 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DF5882610C1C6953A7.TMP | binary | |
MD5:E8B5231C88D23EFC406CD31B1130CB98 | SHA256:43A86BA6F652E63F63CC487A11C06C94B08A48C55AA098950197C6D5FDE92D40 | |||
| 3280 | msiexec.exe | C:\Windows\Installer\MSI2217.tmp | executable | |
MD5:684F2D21637CB5835172EDAD55B6A8D9 | SHA256:DA1FE86141C446921021BB26B6FE2BD2D1BB51E3E614F46F8103FFAD8042F2C0 | |||
| 3280 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:81222794E8E97774738BDEC3559184D4 | SHA256:D95644A8668A71EACEB67CE31073CD954E5CA9FDB1EFE1E775357777439AEFB2 | |||
| 3280 | msiexec.exe | C:\Windows\Installer\MSI24B8.tmp | binary | |
MD5:D501DD52C756266DB13AC2B4FE20BB77 | SHA256:6D3E17E0084538F93B721D7F9C6CE4883BDB9D5BFF6B1AF7FED6C64DCE31E0E3 | |||
| 3280 | msiexec.exe | C:\Program Files\MRC-Holland\Coffalyser.Net\PDFDocScoutImgAddon.dll | executable | |
MD5:2A2844B314B17CA6E7C7602EC66678A2 | SHA256:4A05EB5E0CCD269296E2AF6F241148C9829510E0C4A76D425AEC2C87DBB54050 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
14
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?fbe613066ac7852b | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 23.218.107.179:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 92.122.89.124:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1372 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2564 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1372 | svchost.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
1372 | svchost.exe | 23.218.107.179:80 | crl.microsoft.com | Akamai International B.V. | US | unknown |
1372 | svchost.exe | 92.122.89.124:80 | www.microsoft.com | Akamai International B.V. | NL | unknown |
— | — | 255.255.255.255:1231 | — | — | — | unknown |
1060 | svchost.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
CoffalyserClient.exe | CoffalyserClient.exe Information: 0 : |
CoffalyserClient.exe | skipped the text trace listener
|
CoffalyserClient.exe | CoffalyserClient.exe Warning: 0 : |
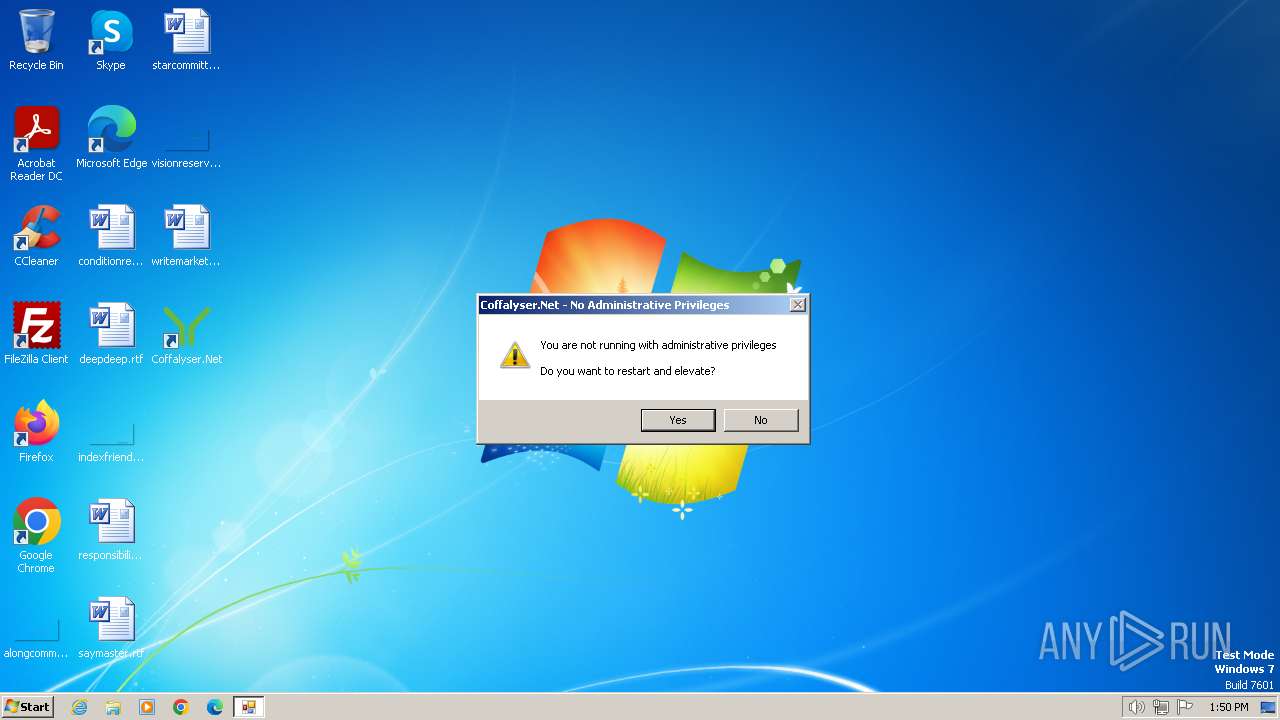
CoffalyserClient.exe | trying to restart the application (file name: C:\Program Files\MRC-Holland\Coffalyser.Net\CoffalyserClient.exe, verb: , arguments: /SERVICE_CONFIGURE)
|
CoffalyserClient.exe | CoffalyserClient.exe Information: 0 : |
CoffalyserClient.exe | skipped the text trace listener
|
CoffalyserClient.exe | CoffalyserClient.exe Warning: 0 : |
CoffalyserClient.exe | user requested the service configuration (with argument)
|
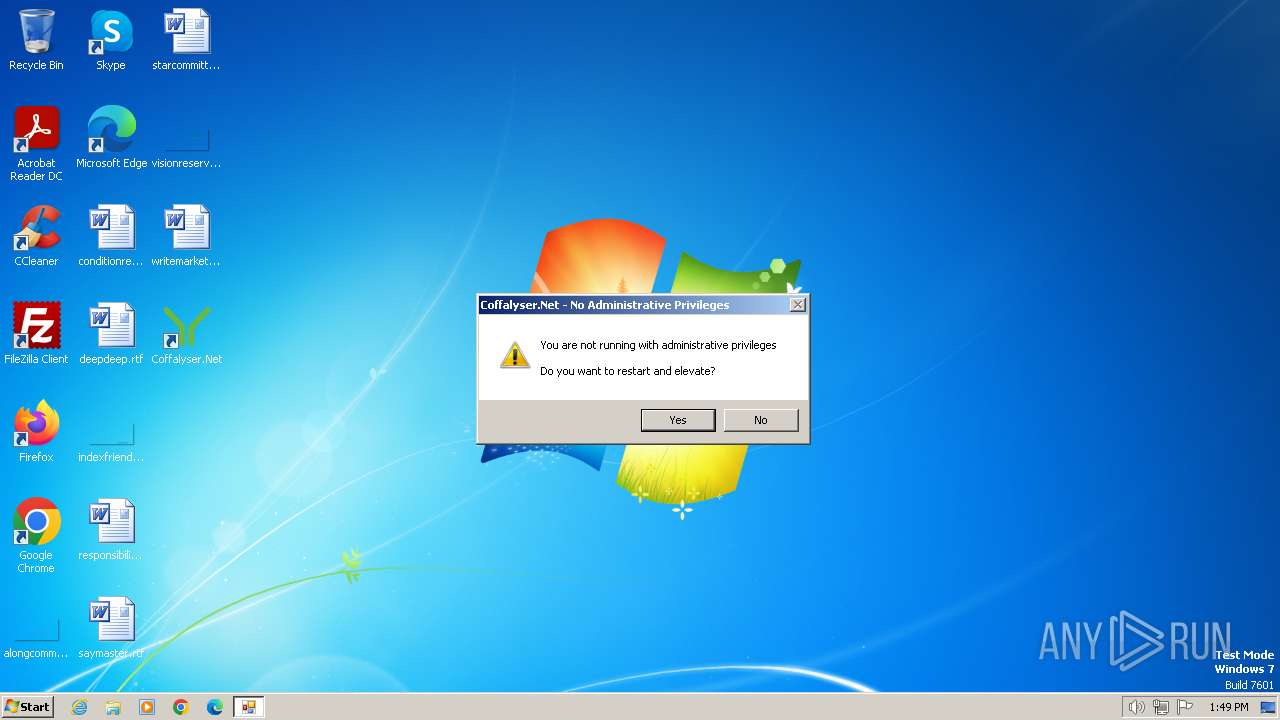
CoffalyserClient.exe | CoffalyserClient.exe Error: 0 : |
CoffalyserClient.exe | the service config requires administrative privileges which are not available
|