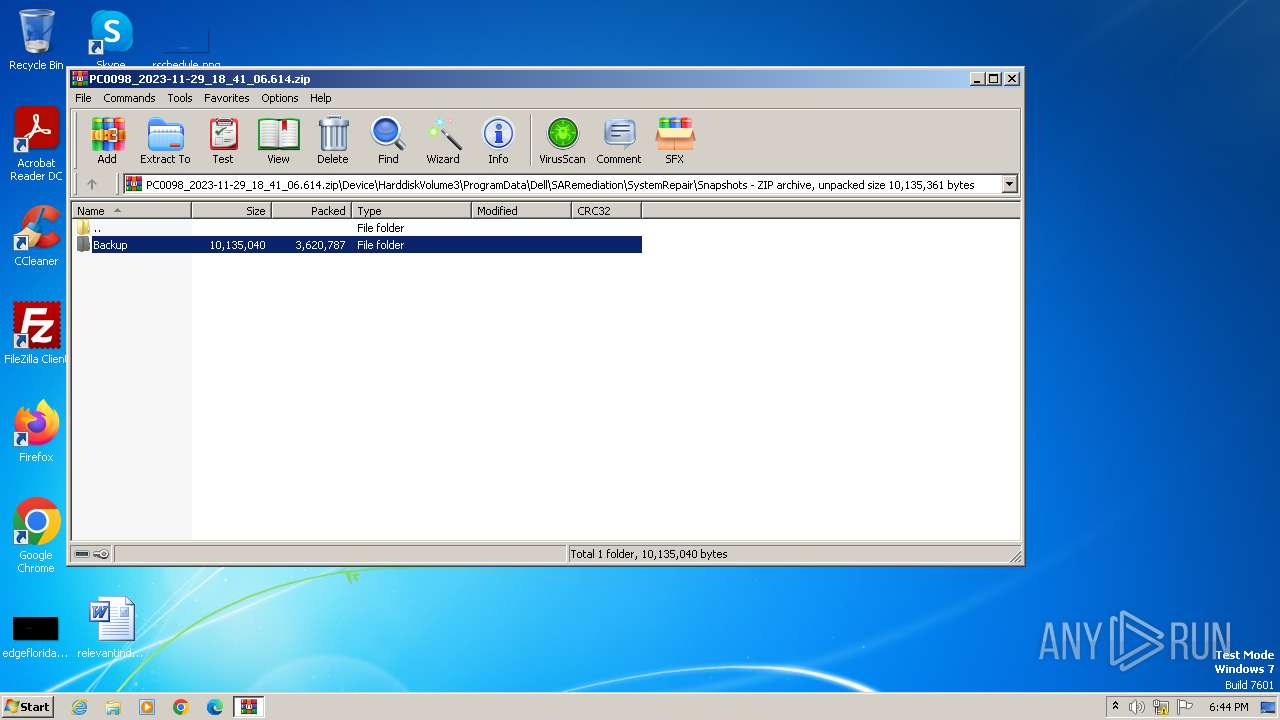
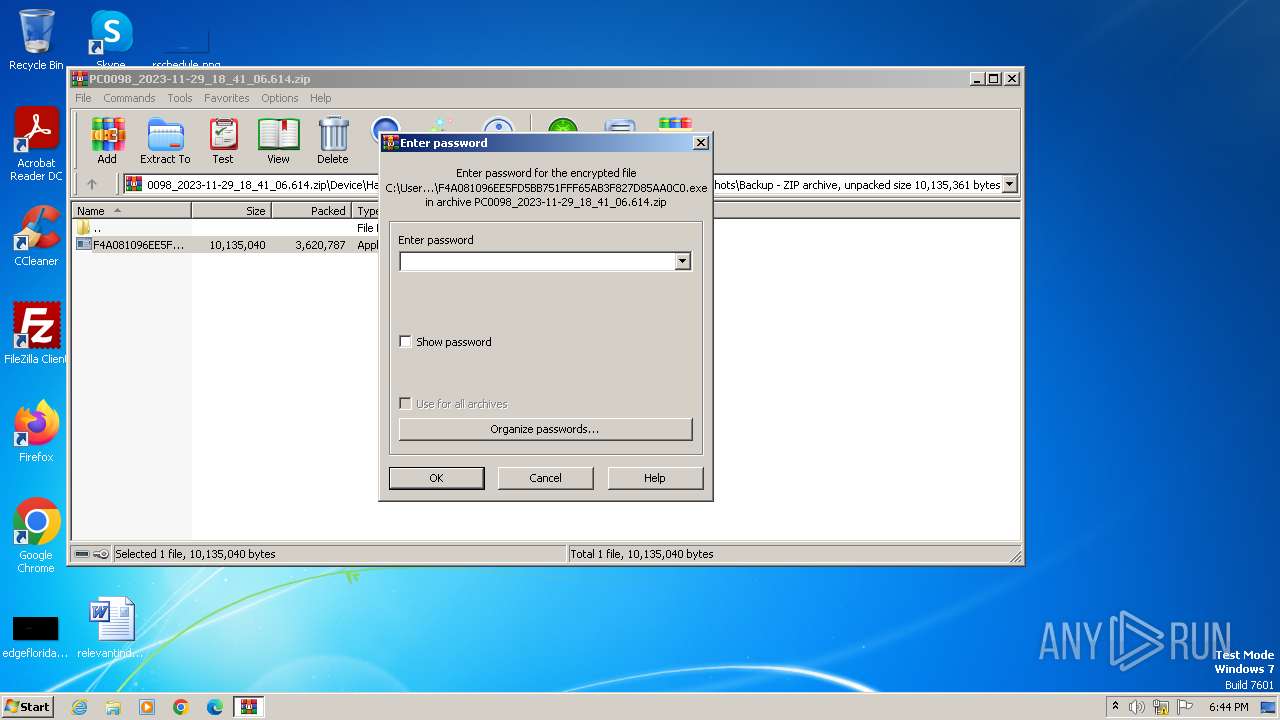
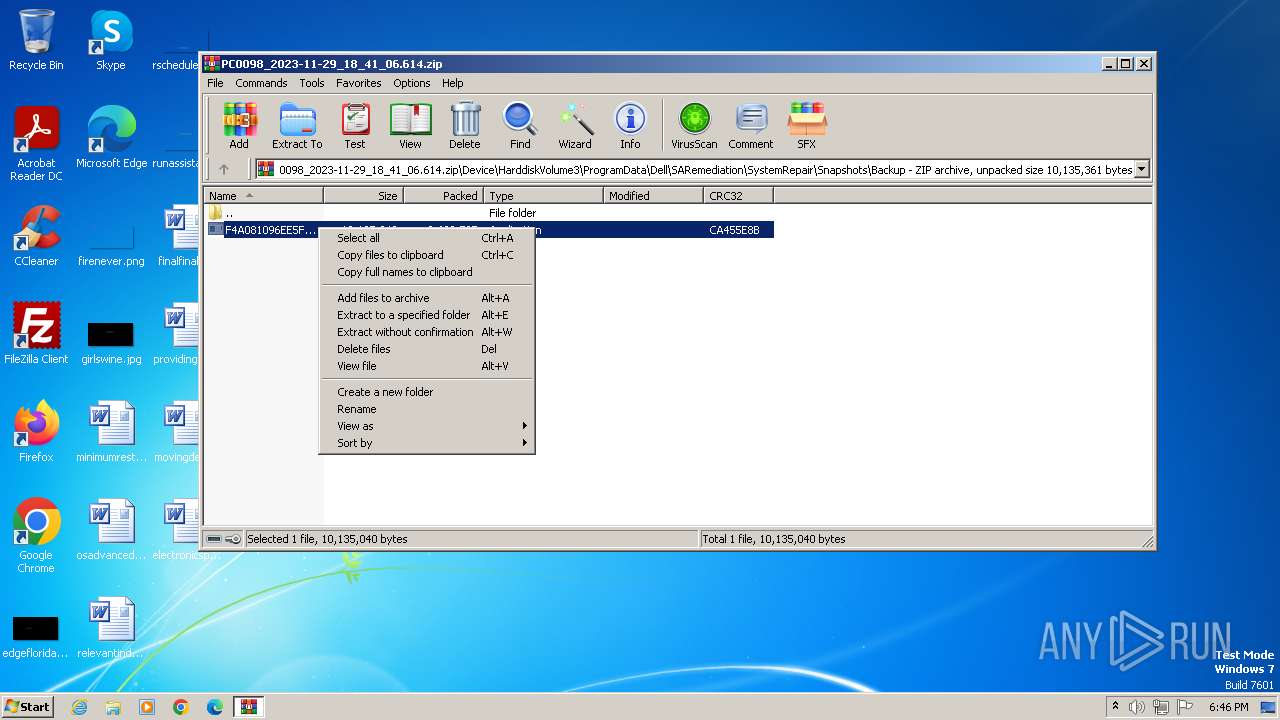
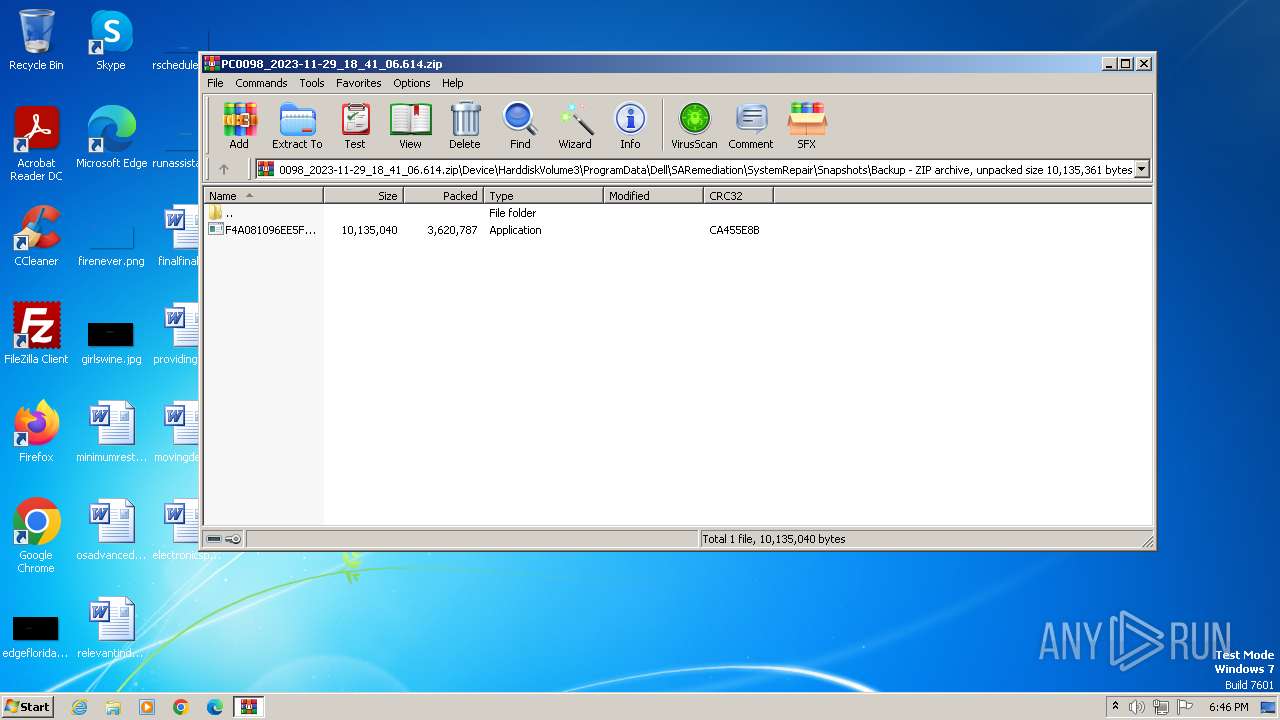
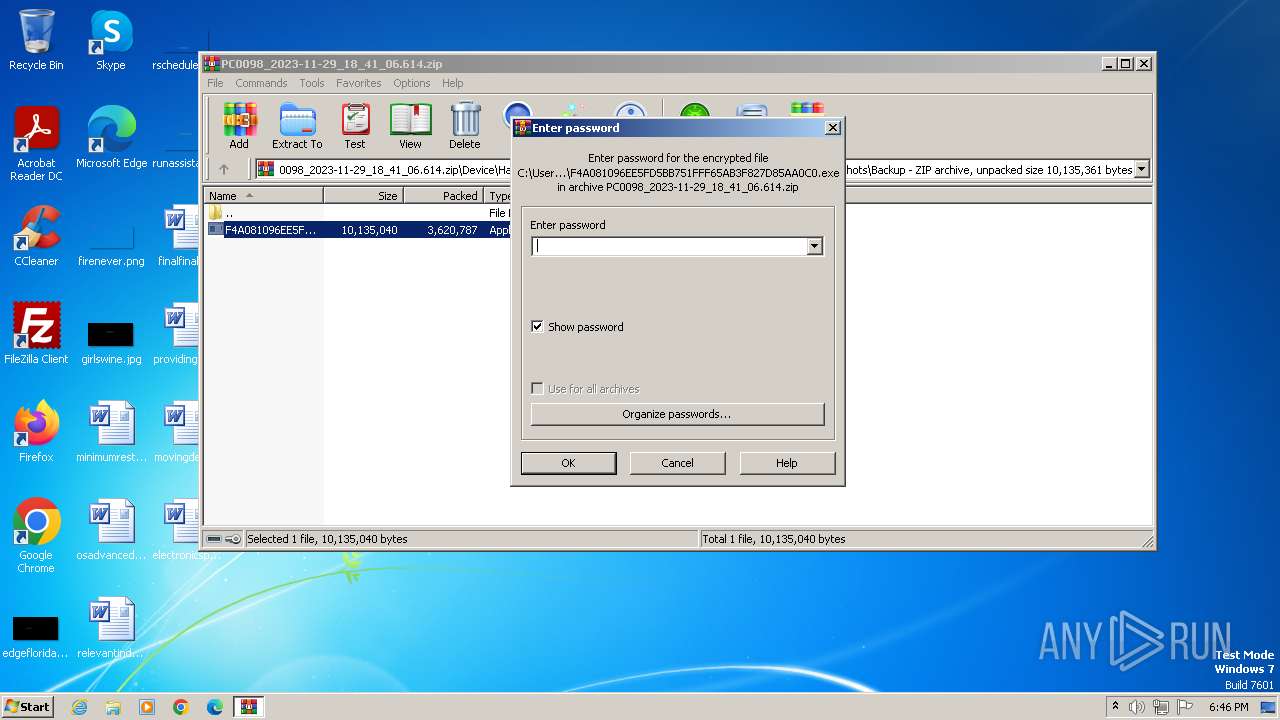
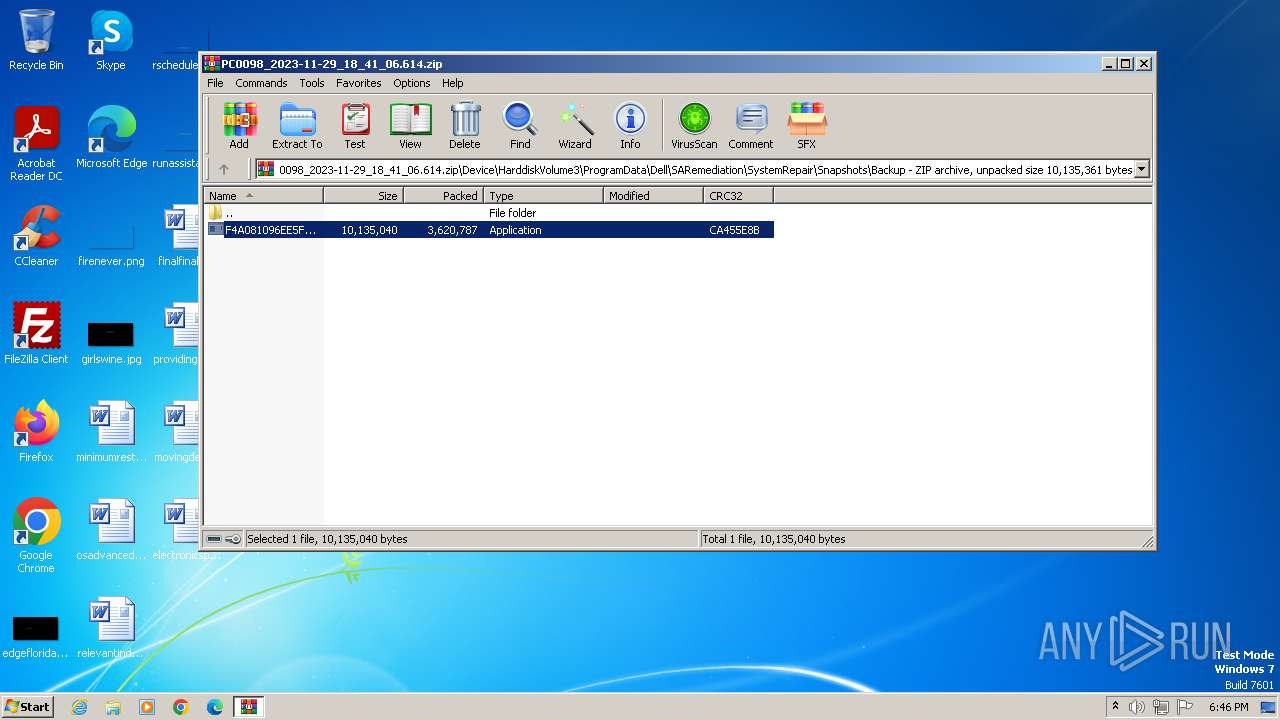
| File name: | PC0098_2023-11-29_18_41_06.614.zip |
| Full analysis: | https://app.any.run/tasks/d589ea11-55f3-4472-8d5d-5c79b1d48747 |
| Verdict: | Malicious activity |
| Analysis date: | November 29, 2023, 18:44:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v4.5 to extract |
| MD5: | DF5260F2958F1C644244CBE8F3C332CC |
| SHA1: | 7DEFD7DA103199EC077892013B76FC759A04CA03 |
| SHA256: | D15A219608ED0FFAA28928A78CDBE1D05AEE693C33D8FE2A855075647D8CE0A9 |
| SSDEEP: | 98304:36qy2V6mZEnPdET6Z9nDCHvkPihoZC7U3eKhw8F89J8l3Z/n8YrI9kwM3Cy9r+BC:ElXF |
MALICIOUS
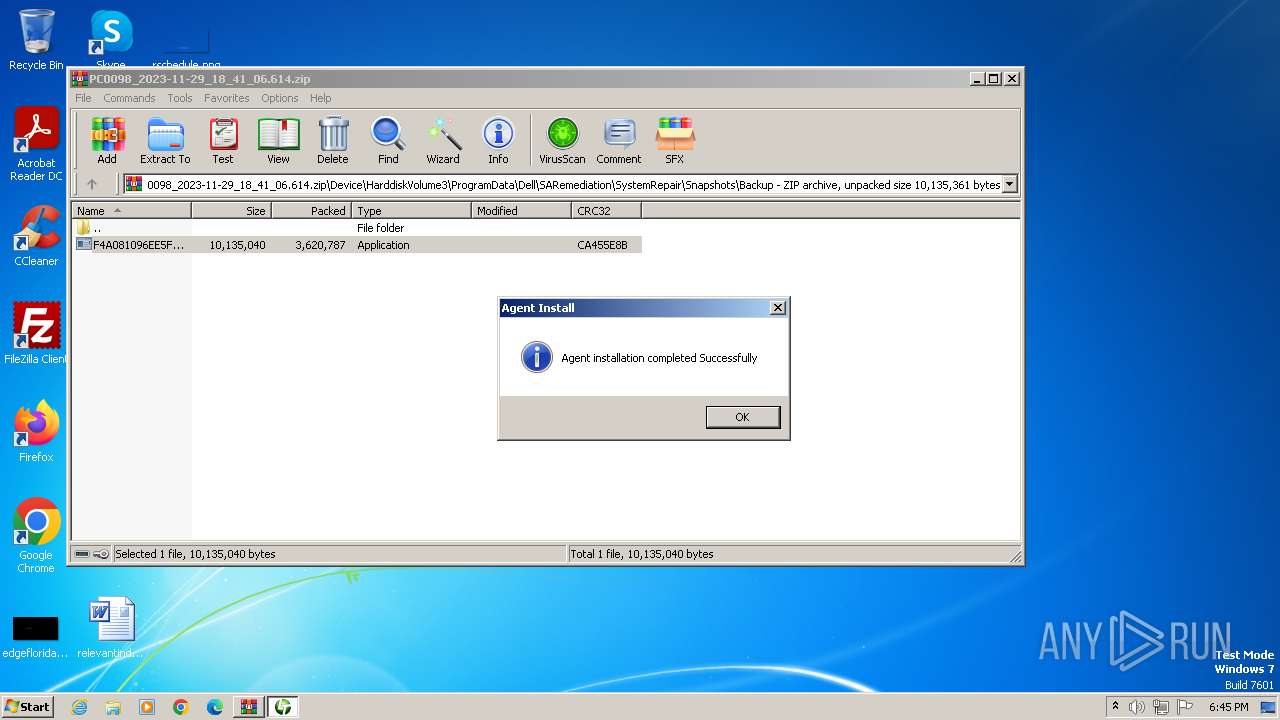
Drops the executable file immediately after the start
- F4A081096EE5FD5BB751FFF65AB3F827D85AA0C0.exe (PID: 924)
- LTSVC.exe (PID: 2760)
Creates a writable file in the system directory
- LTSVC.exe (PID: 2760)
Create files in the Startup directory
- LTSVC.exe (PID: 2760)
Starts NET.EXE for service management
- cmd.exe (PID: 3972)
- net.exe (PID: 3400)
- net.exe (PID: 2456)
- cmd.exe (PID: 3272)
- LTSVC.exe (PID: 2760)
- net.exe (PID: 128)
- net.exe (PID: 1864)
- net.exe (PID: 2944)
- cmd.exe (PID: 3540)
- net.exe (PID: 2052)
- net.exe (PID: 2480)
Registers / Runs the DLL via REGSVR32.EXE
- LTSVC.exe (PID: 2760)
SUSPICIOUS
Reads the Internet Settings
- F4A081096EE5FD5BB751FFF65AB3F827D85AA0C0.exe (PID: 924)
The process creates files with name similar to system file names
- F4A081096EE5FD5BB751FFF65AB3F827D85AA0C0.exe (PID: 924)
Reads security settings of Internet Explorer
- installutil.exe (PID: 2432)
Checks Windows Trust Settings
- LTSVC.exe (PID: 2760)
- installutil.exe (PID: 2432)
- LTSVC.exe (PID: 1644)
Creates or modifies Windows services
- installutil.exe (PID: 2432)
Reads settings of System Certificates
- installutil.exe (PID: 2432)
Executes as Windows Service
- LTSVC.exe (PID: 2760)
- LTSVC.exe (PID: 1644)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- cmd.exe (PID: 4080)
- cmd.exe (PID: 3900)
- cmd.exe (PID: 284)
- cmd.exe (PID: 1752)
- cmd.exe (PID: 3764)
Uses ICACLS.EXE to modify access control lists
- LTSVC.exe (PID: 2760)
Drops a system driver (possible attempt to evade defenses)
- LTSVC.exe (PID: 2760)
Starts CMD.EXE for commands execution
- LTSVC.exe (PID: 2760)
Executing commands from a ".bat" file
- LTSVC.exe (PID: 2760)
INFO
Reads the computer name
- wmpnscfg.exe (PID: 2848)
- F4A081096EE5FD5BB751FFF65AB3F827D85AA0C0.exe (PID: 924)
- LTSVC.exe (PID: 2760)
- installutil.exe (PID: 2432)
- LTSVC.exe (PID: 1644)
Checks supported languages
- wmpnscfg.exe (PID: 2848)
- F4A081096EE5FD5BB751FFF65AB3F827D85AA0C0.exe (PID: 924)
- installutil.exe (PID: 2432)
- LTSVC.exe (PID: 2760)
- LTSVC.exe (PID: 1644)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 2848)
- F4A081096EE5FD5BB751FFF65AB3F827D85AA0C0.exe (PID: 924)
- LTSVC.exe (PID: 2760)
- installutil.exe (PID: 2432)
- LTSVC.exe (PID: 1644)
Manual execution by a user
- wmpnscfg.exe (PID: 2848)
Reads Environment values
- F4A081096EE5FD5BB751FFF65AB3F827D85AA0C0.exe (PID: 924)
- LTSVC.exe (PID: 2760)
- LTSVC.exe (PID: 1644)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 888)
Create files in a temporary directory
- F4A081096EE5FD5BB751FFF65AB3F827D85AA0C0.exe (PID: 924)
- installutil.exe (PID: 2432)
Creates files in the program directory
- LTSVC.exe (PID: 2760)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0801 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCRC: | 0xca455e8b |
| ZipCompressedSize: | 3620787 |
| ZipUncompressedSize: | 10135040 |
| ZipFileName: | Device/HarddiskVolume3/ProgramData/Dell/SARemediation/SystemRepair/Snapshots/Backup/F4A081096EE5FD5BB751FFF65AB3F827D85AA0C0.exe |
Total processes
94
Monitored processes
41
Malicious processes
5
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | net start LTService | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 148 | ping localhost | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 284 | "CMD.exe" /c netsh advfirewall firewall Delete rule name="Allow Local Redir" | C:\Windows\System32\cmd.exe | — | LTSVC.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 536 | ping localhost | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 888 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\PC0098_2023-11-29_18_41_06.614.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 924 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb888.47767\Device\HarddiskVolume3\ProgramData\Dell\SARemediation\SystemRepair\Snapshots\Backup\F4A081096EE5FD5BB751FFF65AB3F827D85AA0C0.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb888.47767\Device\HarddiskVolume3\ProgramData\Dell\SARemediation\SystemRepair\Snapshots\Backup\F4A081096EE5FD5BB751FFF65AB3F827D85AA0C0.exe | WinRAR.exe | ||||||||||||
User: admin Company: LabTech Software Integrity Level: HIGH Description: LTSilent Exit code: 0 Version: 100.332.5505.17848 Modules
| |||||||||||||||
| 1248 | netsh advfirewall firewall Delete rule name="Allow Local Redir" | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1644 | "C:\Windows\LTSvc\LTSVC.exe" -sLTService | C:\Windows\LTSvc\LTSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: LabTech Software Integrity Level: SYSTEM Description: LabTech Service Exit code: 0 Version: 100.332.5505.17847 Modules
| |||||||||||||||
| 1752 | "CMD.exe" /c netsh advfirewall firewall Delete rule name="Allow Tunnel StunRelay" | C:\Windows\System32\cmd.exe | — | LTSVC.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1856 | C:\Windows\system32\net1 start LTService | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
19 473
Read events
19 150
Write events
320
Delete events
3
Modification events
| (PID) Process: | (888) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (888) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (888) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (888) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (888) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (888) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (888) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (888) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2848) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{2BEAD2BD-3336-4650-9DF0-7539C2C034CC}\{222FC10C-194C-43E0-9DBE-87C7FEE93C3B} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2848) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{2BEAD2BD-3336-4650-9DF0-7539C2C034CC} |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
16
Suspicious files
12
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 888 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb888.47767\Device\HarddiskVolume3\ProgramData\Dell\SARemediation\SystemRepair\Snapshots\Backup\F4A081096EE5FD5BB751FFF65AB3F827D85AA0C0.exe | executable | |
MD5:4E668643C2152718259E27EA1C1E9BEC | SHA256:3B189EC6B9EBE1228DE113C0FA40B7D69220F13AB8F98480E40C23751776C780 | |||
| 924 | F4A081096EE5FD5BB751FFF65AB3F827D85AA0C0.exe | C:\Windows\LTSvc\cpuidsdk.dll | executable | |
MD5:123E7C9DBD1F96F14A2469D80E69492F | SHA256:B9D02CC345108F02731AC2BC924FC9FBC9384632A5123B5AE8E20A22AC717811 | |||
| 924 | F4A081096EE5FD5BB751FFF65AB3F827D85AA0C0.exe | C:\Windows\LTSvc\Interop.WODVPNCOMLib.dll | executable | |
MD5:45C0B448A5795DF48AFD0885C9D58D24 | SHA256:3322BD0B66E00AB89DEA46CA81A4661CCB6E7ADFFC3D5BD28FB308F950298297 | |||
| 924 | F4A081096EE5FD5BB751FFF65AB3F827D85AA0C0.exe | C:\Windows\LTSvc\nsoftware.IPWorksSSH.dll | executable | |
MD5:3EEE3A5FE8BCC66D2CF519BF9D540F68 | SHA256:9C3DE4F8DBEDAD6D6FC528E3EDB27FE91FFCAED3A6F7F665D899E9316BC23B33 | |||
| 924 | F4A081096EE5FD5BB751FFF65AB3F827D85AA0C0.exe | C:\Windows\LTSvc\Interfaces.dll | executable | |
MD5:2304C5AE2CC8D48A8BC4505A7DF43A9C | SHA256:83CF4768671168D558A2B616847A4AFCD6260B54413FF24D764451A45F748F53 | |||
| 888 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb888.47767\manifest.json | text | |
MD5:BB66E33C8D794DCFA68ED500AD2EB2AB | SHA256:765324C001AD3A3E4A7B9DFC2DF8812448CC114D42A7D5AA474728FE95D470F1 | |||
| 924 | F4A081096EE5FD5BB751FFF65AB3F827D85AA0C0.exe | C:\Windows\LTSvc\LTSVC.exe | executable | |
MD5:8B6411DA19A9798E11E203AFFEBAE2E7 | SHA256:01D252FDF2FD638C9010B4552420C6F861F7573291AA45E77FB2ABC980B81A57 | |||
| 924 | F4A081096EE5FD5BB751FFF65AB3F827D85AA0C0.exe | C:\Windows\LTSvc\LTTray.exe | executable | |
MD5:BF87FA5FFEB414D73BA6E7A5C8BF0D2D | SHA256:15BC843A229AECBA32E526186FE3741DF18C210A887ED7E3ADE1B0D3D5E6FB34 | |||
| 2432 | installutil.exe | C:\Windows\LTSvc\LTSVC.InstallLog | text | |
MD5:ECAE64ECC84C210520E4E71A5F8E6CEE | SHA256:836053C64BB1502E6E8BB83AEC7A5CB2E189590A70F1F23CBA64464249B7AFA4 | |||
| 924 | F4A081096EE5FD5BB751FFF65AB3F827D85AA0C0.exe | C:\Windows\LTSvc\ICSharpCode.SharpZipLib.dll | executable | |
MD5:555A3998407435703F9C14350A929846 | SHA256:BC02A4FE45FC5E83AD07220120DF2F841FE6D17391D3FFEBBE8CB21393CADBAE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
10
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2760 | LTSVC.exe | GET | 200 | 152.199.19.74:80 | http://ocsp.verisign.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS56bKHAoUD%2BOyl%2B0LhPg9JxyQm4gQUf9Nlp8Ld7LvwMAnzQzn6Aq8zMTMCEFIA5aolVvwahu2WydRLM8c%3D | unknown | binary | 5 b | unknown |
1080 | svchost.exe | GET | 200 | 184.24.77.202:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?8c278ce706dba7cc | unknown | compressed | 4.66 Kb | unknown |
2760 | LTSVC.exe | GET | 200 | 152.199.19.74:80 | http://ocsp.verisign.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS56bKHAoUD%2BOyl%2B0LhPg9JxyQm4gQUf9Nlp8Ld7LvwMAnzQzn6Aq8zMTMCEFIA5aolVvwahu2WydRLM8c%3D | unknown | binary | 5 b | unknown |
2760 | LTSVC.exe | GET | 200 | 184.24.77.202:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e066062f7f0bb17c | unknown | compressed | 4.66 Kb | unknown |
2760 | LTSVC.exe | GET | 200 | 192.229.221.95:80 | http://crl.verisign.com/pca3-g5.crl | unknown | binary | 834 b | unknown |
2760 | LTSVC.exe | GET | 200 | 152.199.19.74:80 | http://ocsp.verisign.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTSqZMG5M8TA9rdzkbCnNwuMAd5VgQUz5mp6nsm9EvJjo%2FX8AUm7%2BPSp50CECjIFSgOcuwQMusYMOo9RJ0%3D | unknown | binary | 1.51 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
868 | svchost.exe | 95.101.148.135:80 | — | Akamai International B.V. | NL | unknown |
868 | svchost.exe | 104.122.25.135:80 | armmf.adobe.com | AKAMAI-AS | DE | unknown |
2760 | LTSVC.exe | 184.24.77.202:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
2760 | LTSVC.exe | 152.199.19.74:80 | ocsp.verisign.com | EDGECAST | US | unknown |
2760 | LTSVC.exe | 192.229.221.95:80 | crl.verisign.com | EDGECAST | US | whitelisted |
1080 | svchost.exe | 184.24.77.202:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
armmf.adobe.com |
| whitelisted |
labtech.wpc.net |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.verisign.com |
| whitelisted |
crl.verisign.com |
| whitelisted |