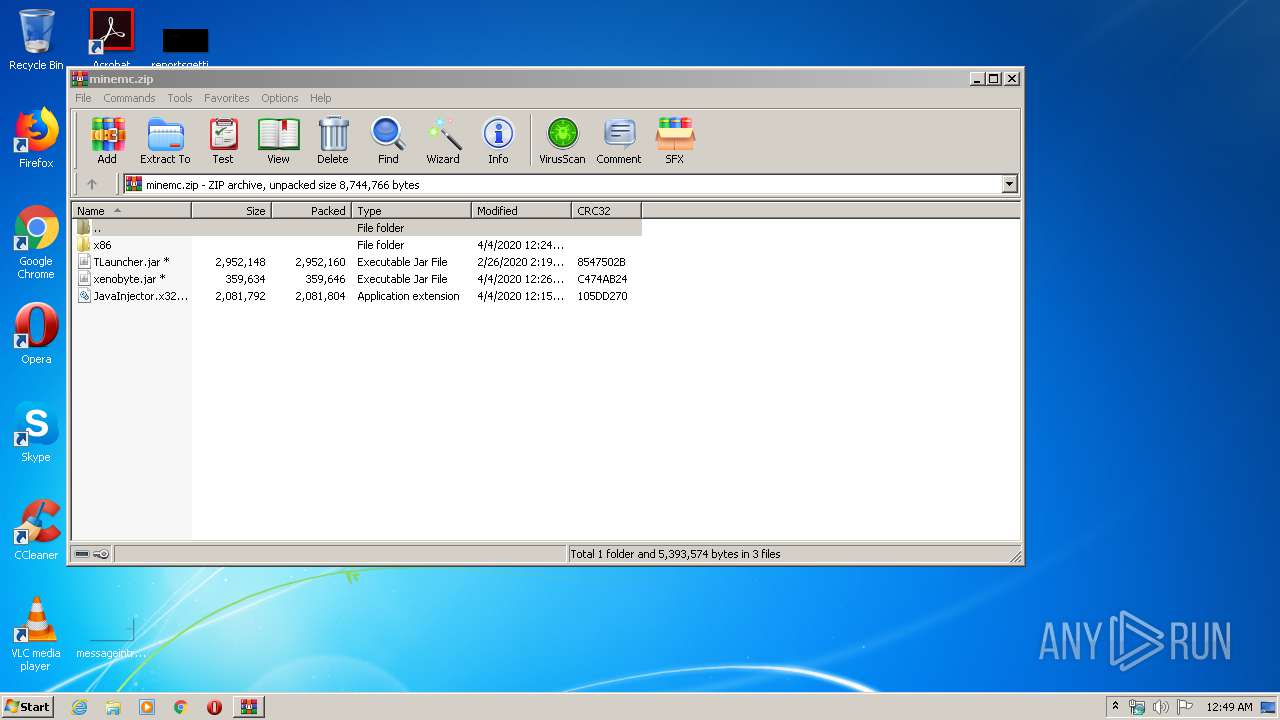
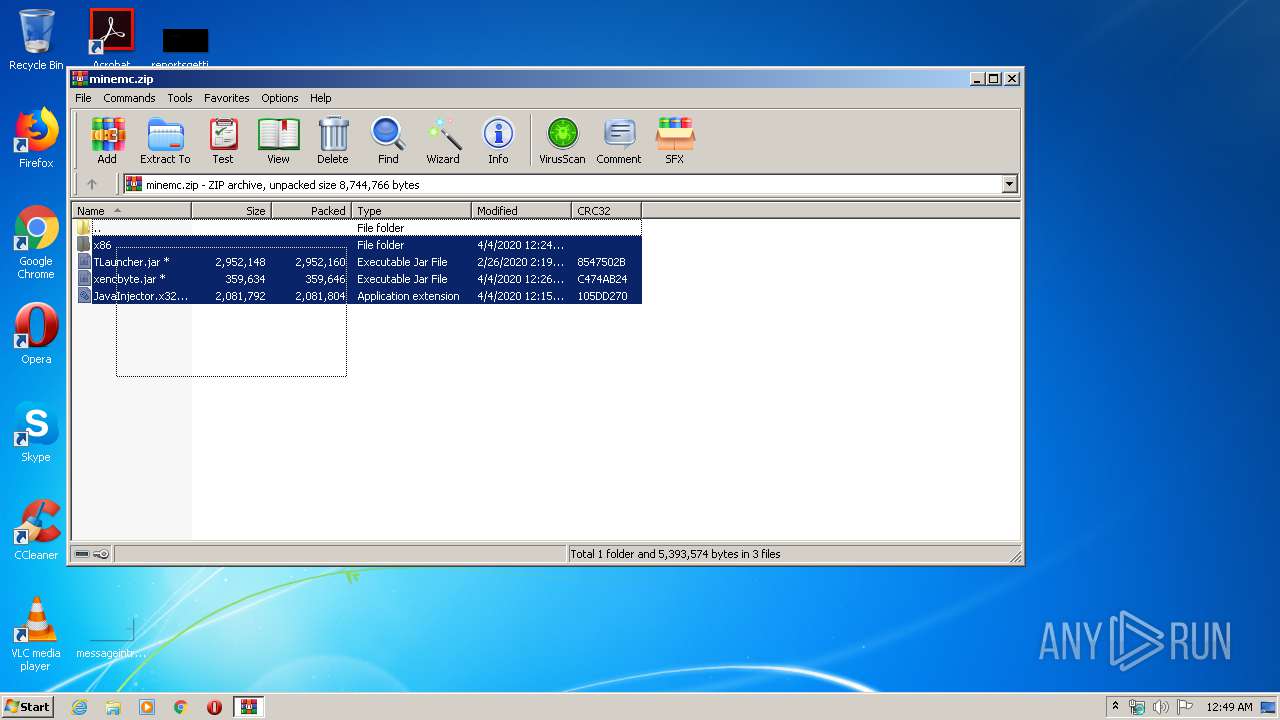
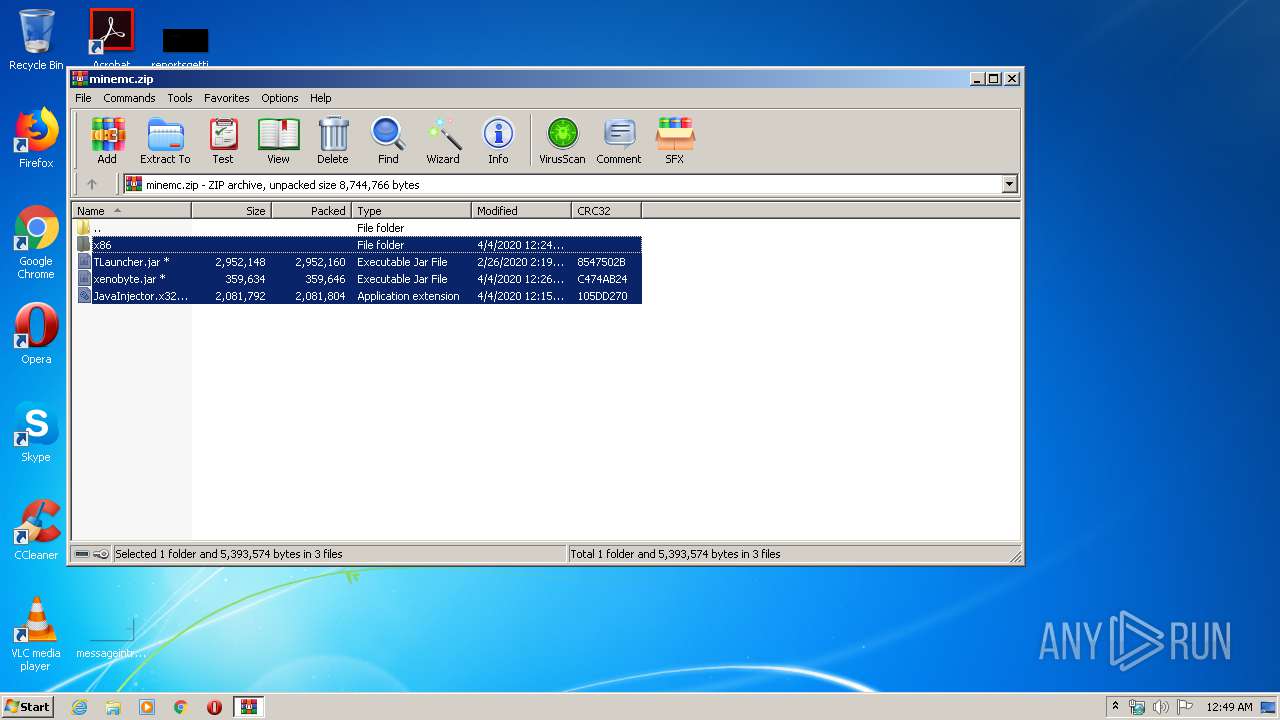
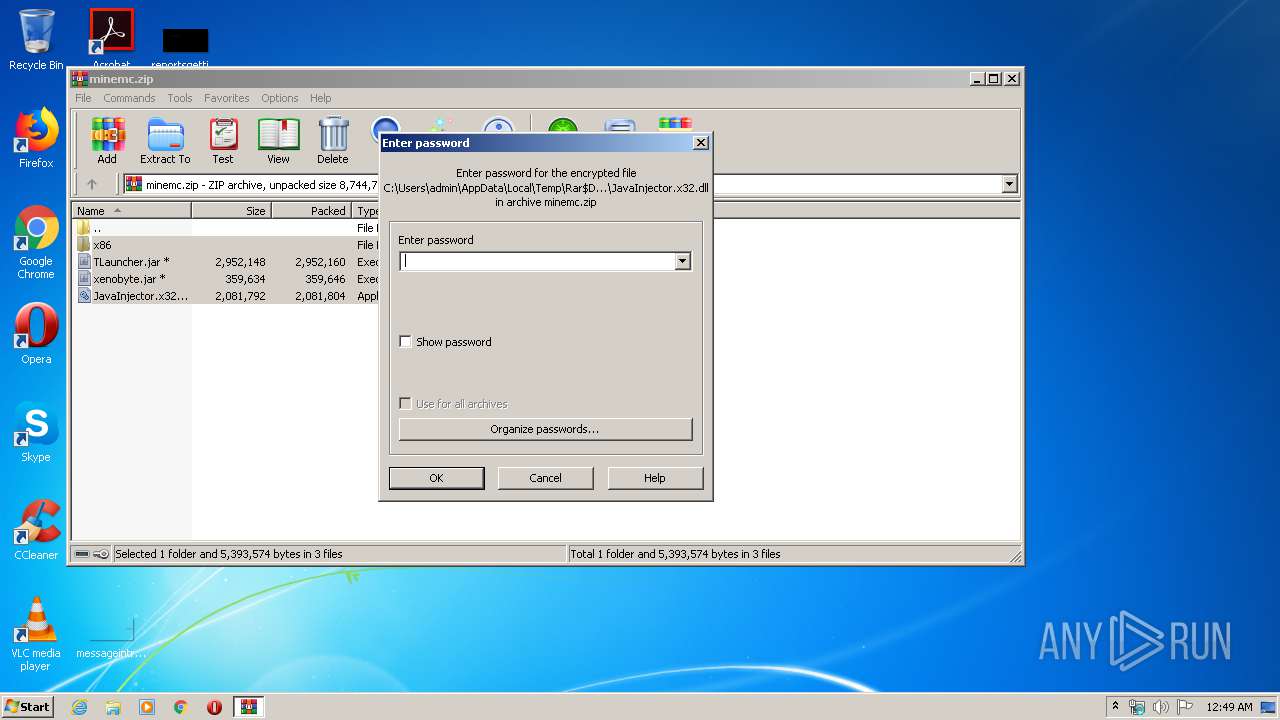
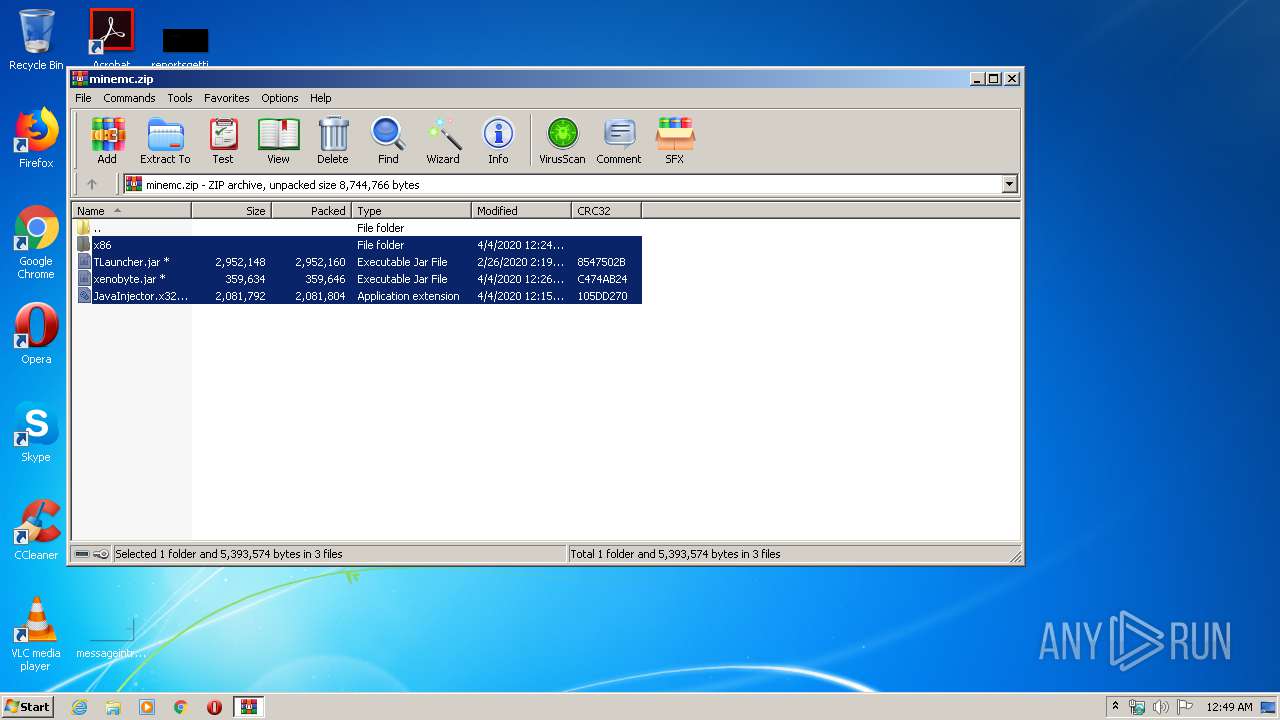
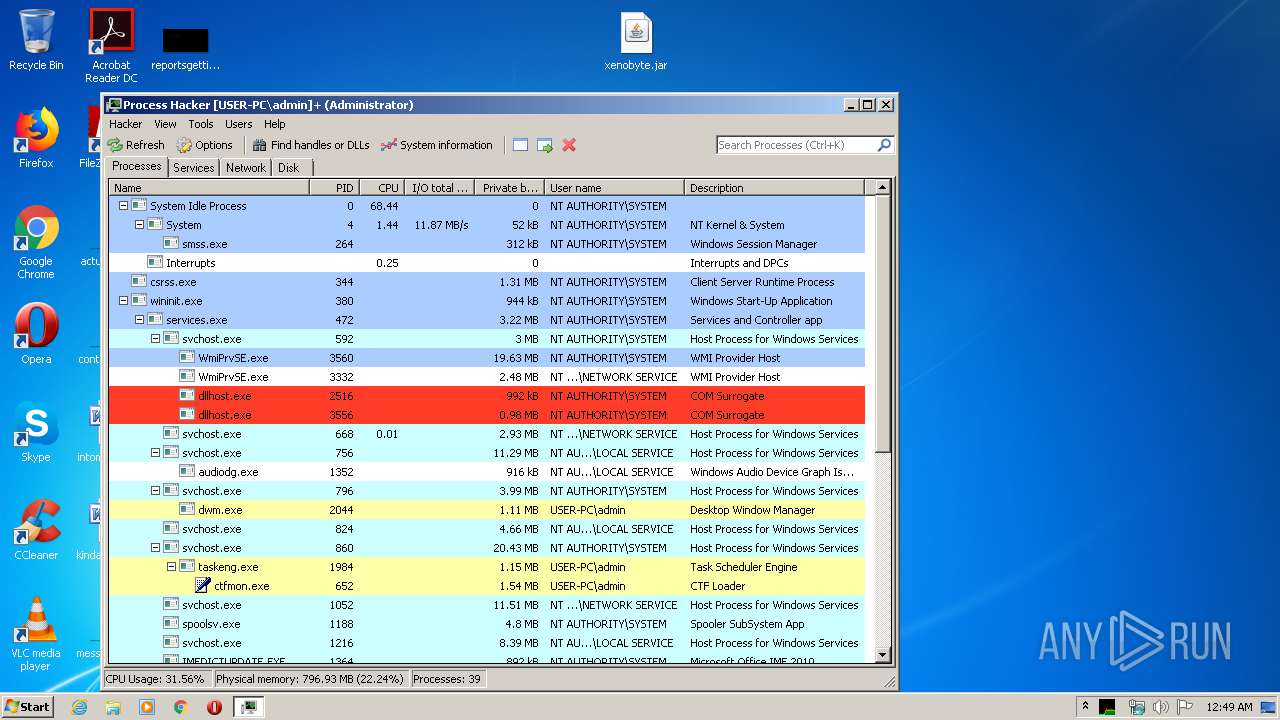
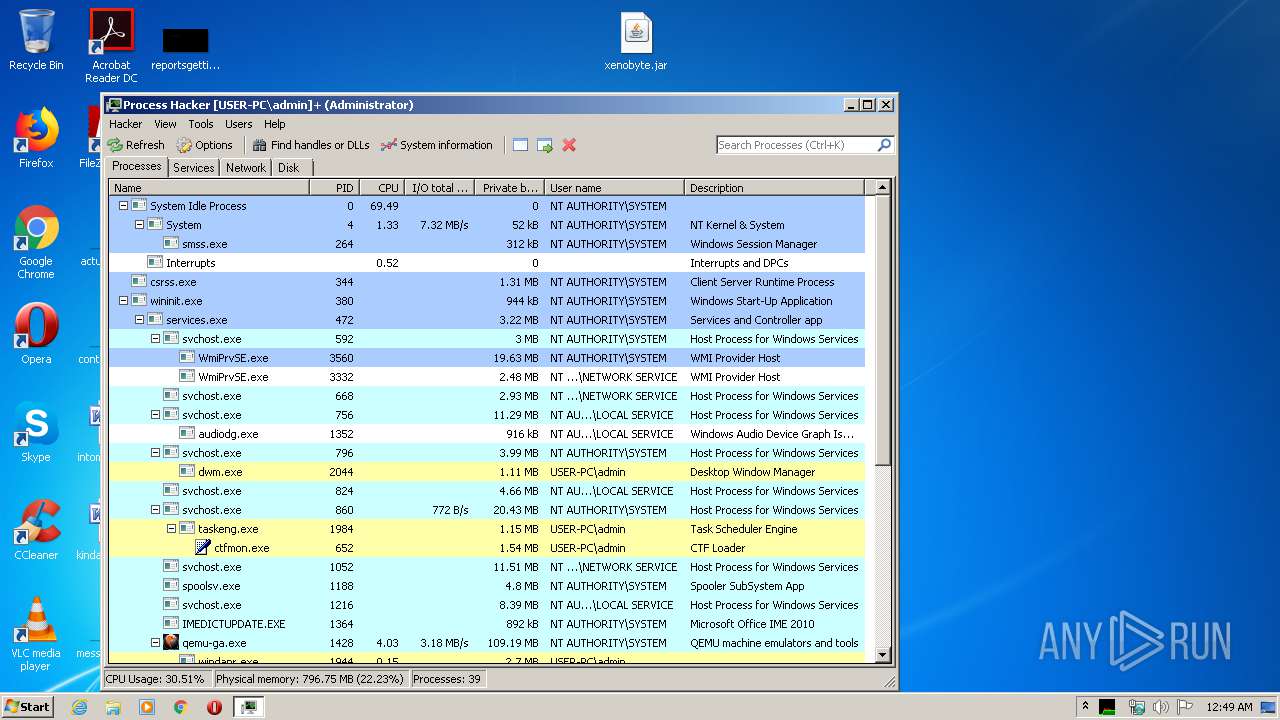
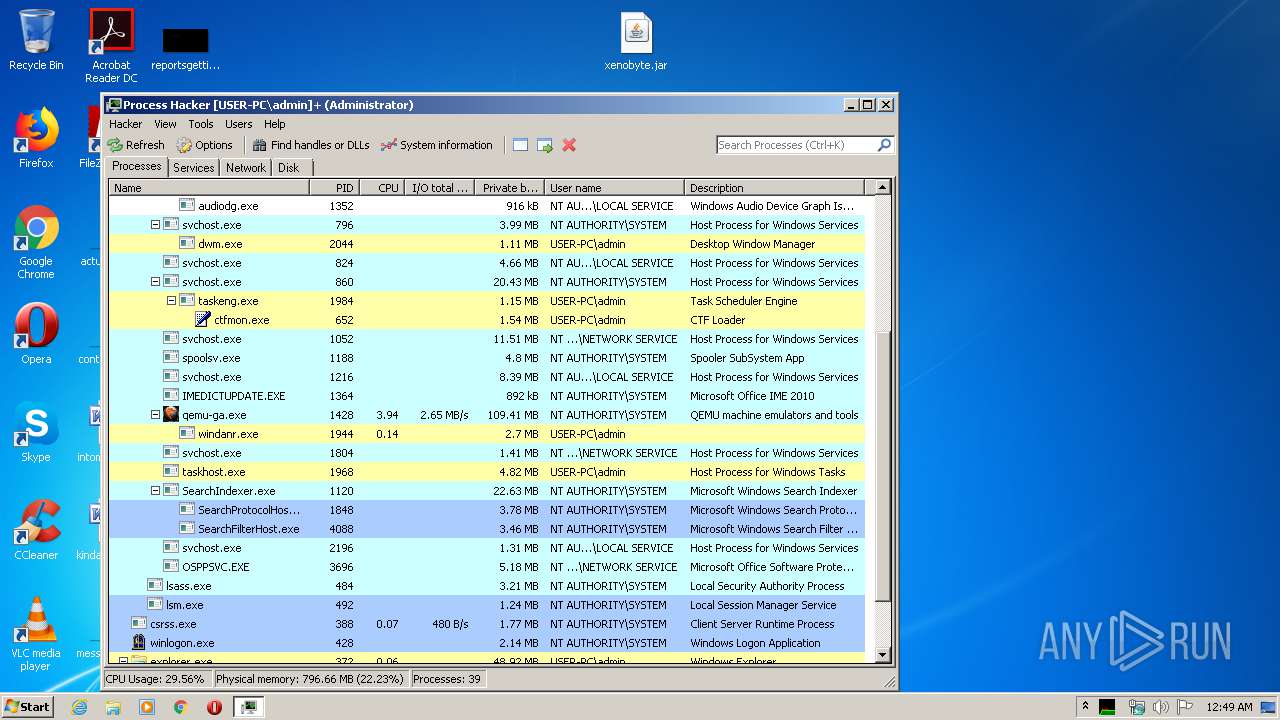
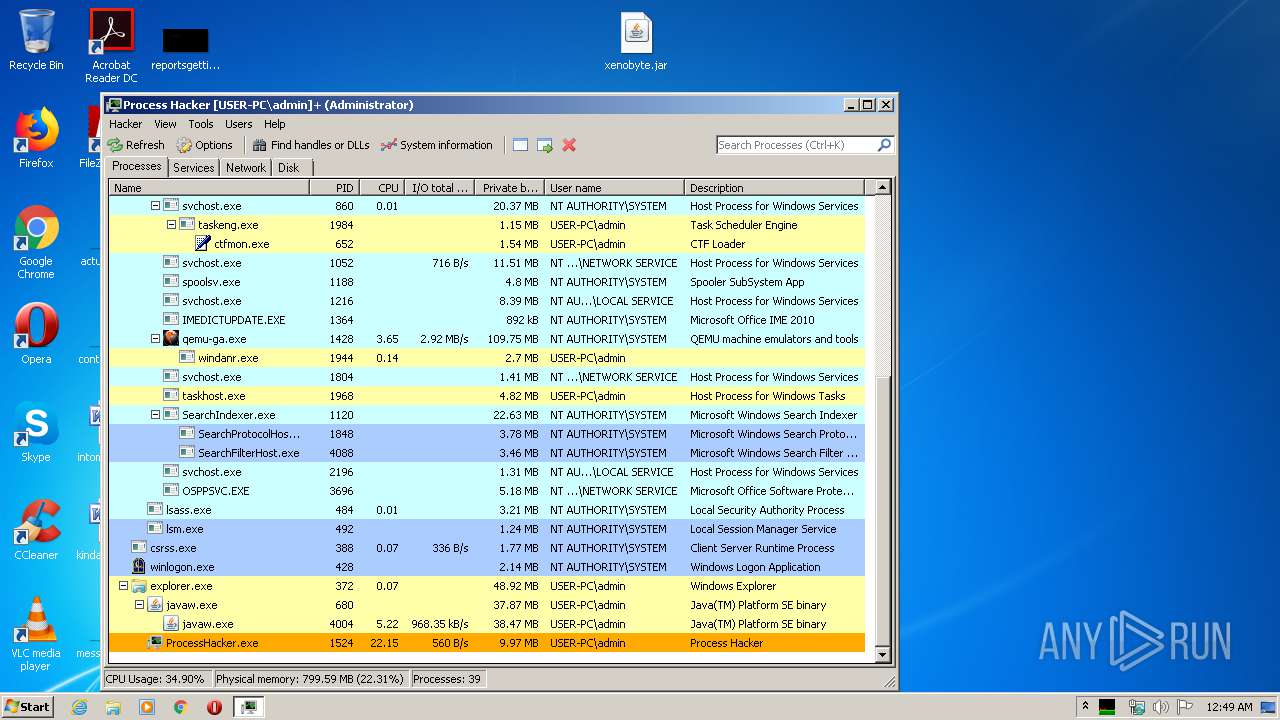
| URL: | https://yadi.sk/d/RDR-cwAcyDlSWQ |
| Full analysis: | https://app.any.run/tasks/24b82381-6f77-4cdf-8088-2d1834ff10d2 |
| Verdict: | Malicious activity |
| Analysis date: | April 02, 2020, 23:48:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | DB6817D401ABB04579F74D56AE4384A8 |
| SHA1: | 2E2B74677106567B898EC18F32B7AD088312E1C9 |
| SHA256: | D154C2FFF91ECAE7816EAB9FE0916DAA1E7F7A343E284A9373340F3B6A4E57B9 |
| SSDEEP: | 3:N8j4hvV0n:20T0n |
MALICIOUS
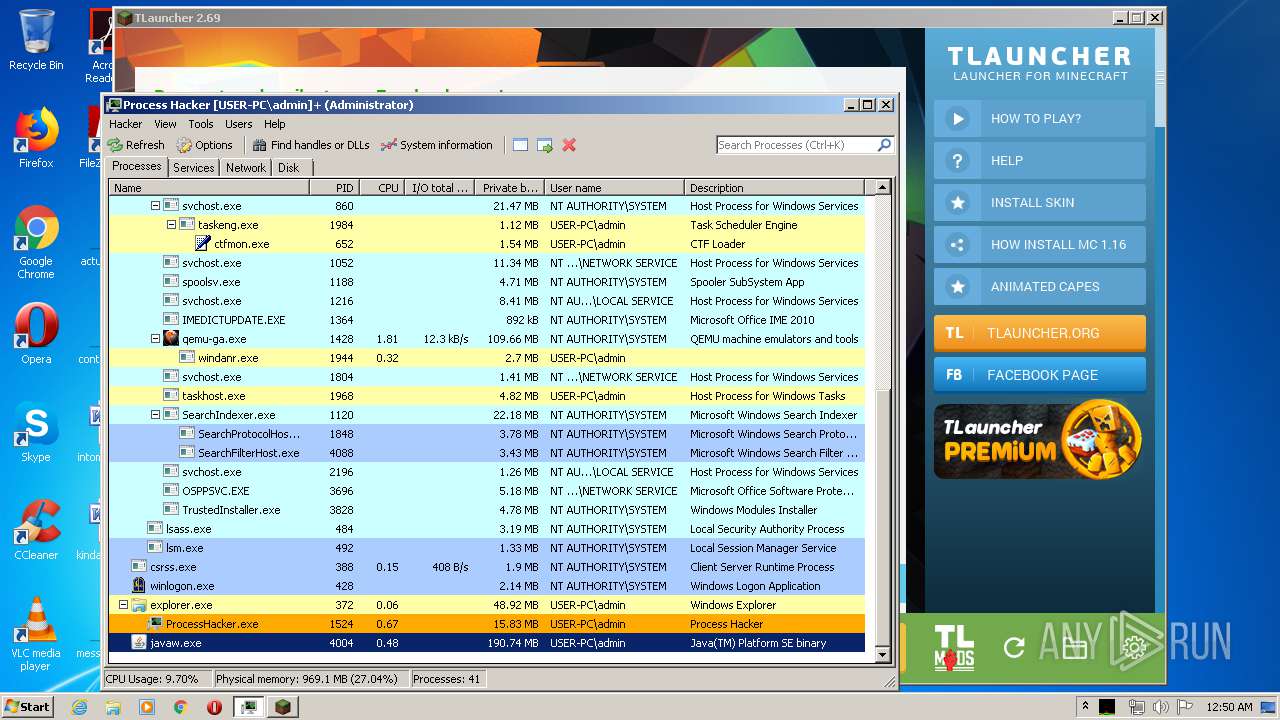
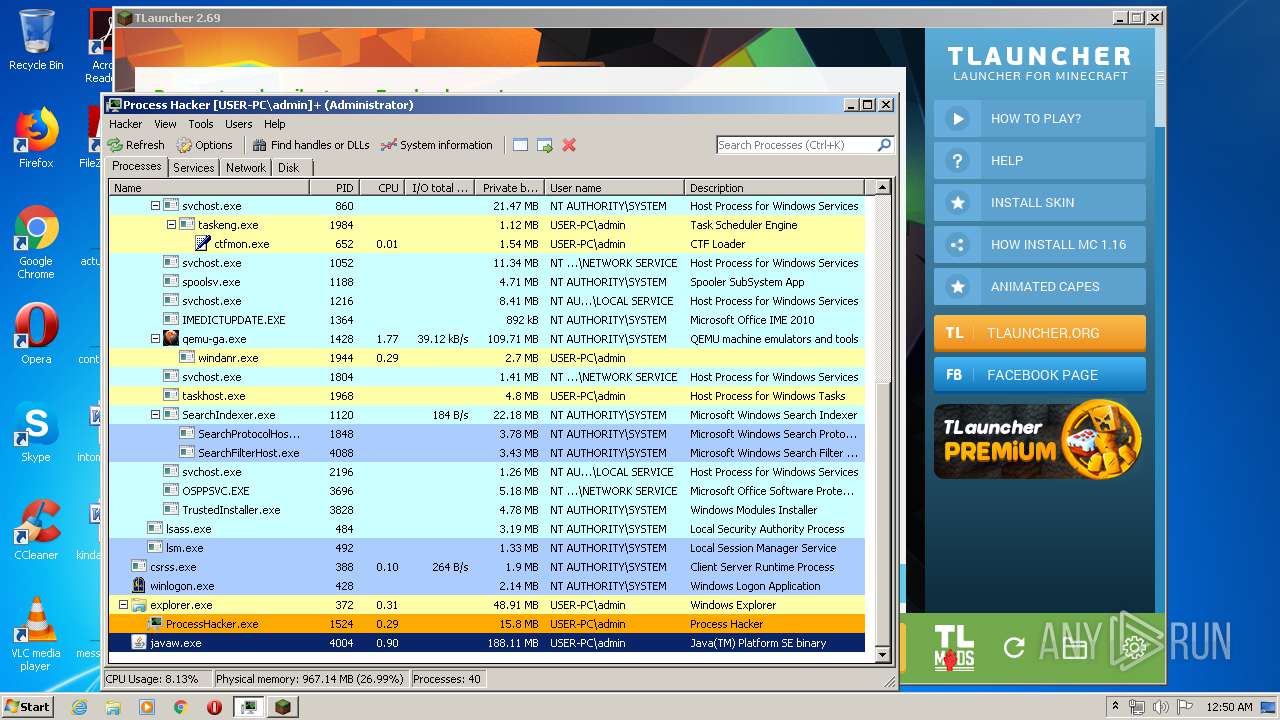
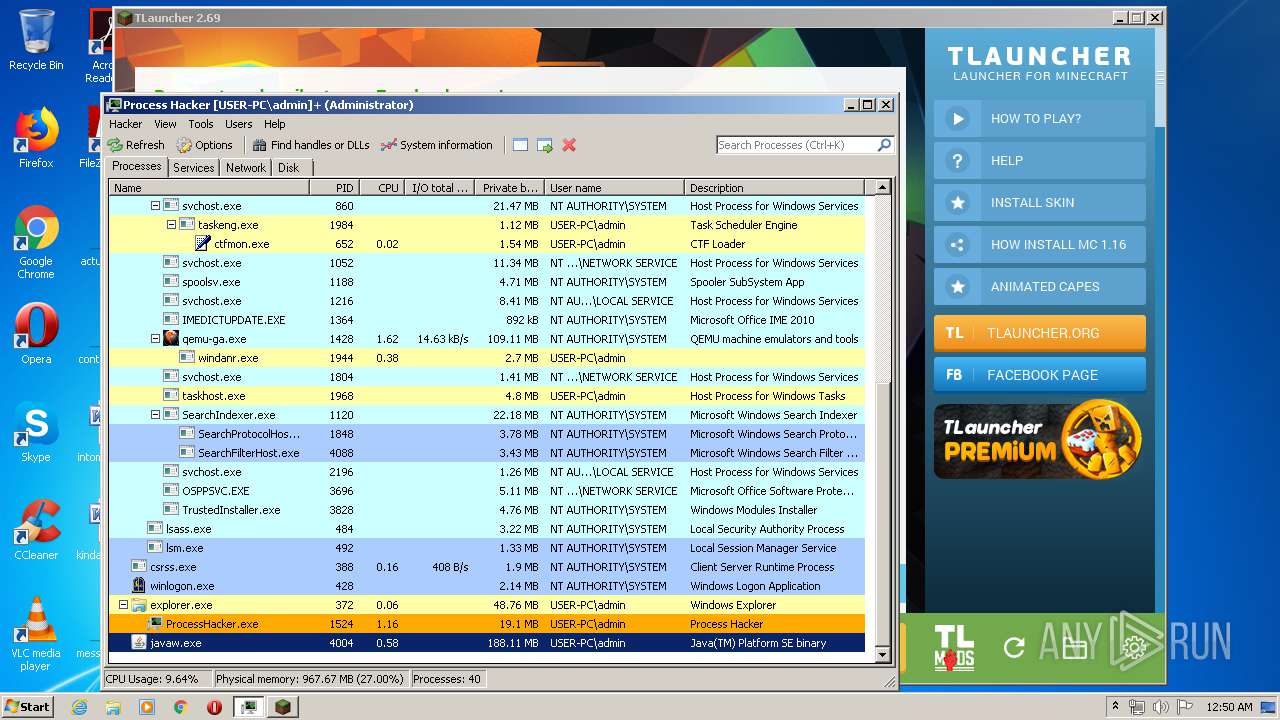
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 1848)
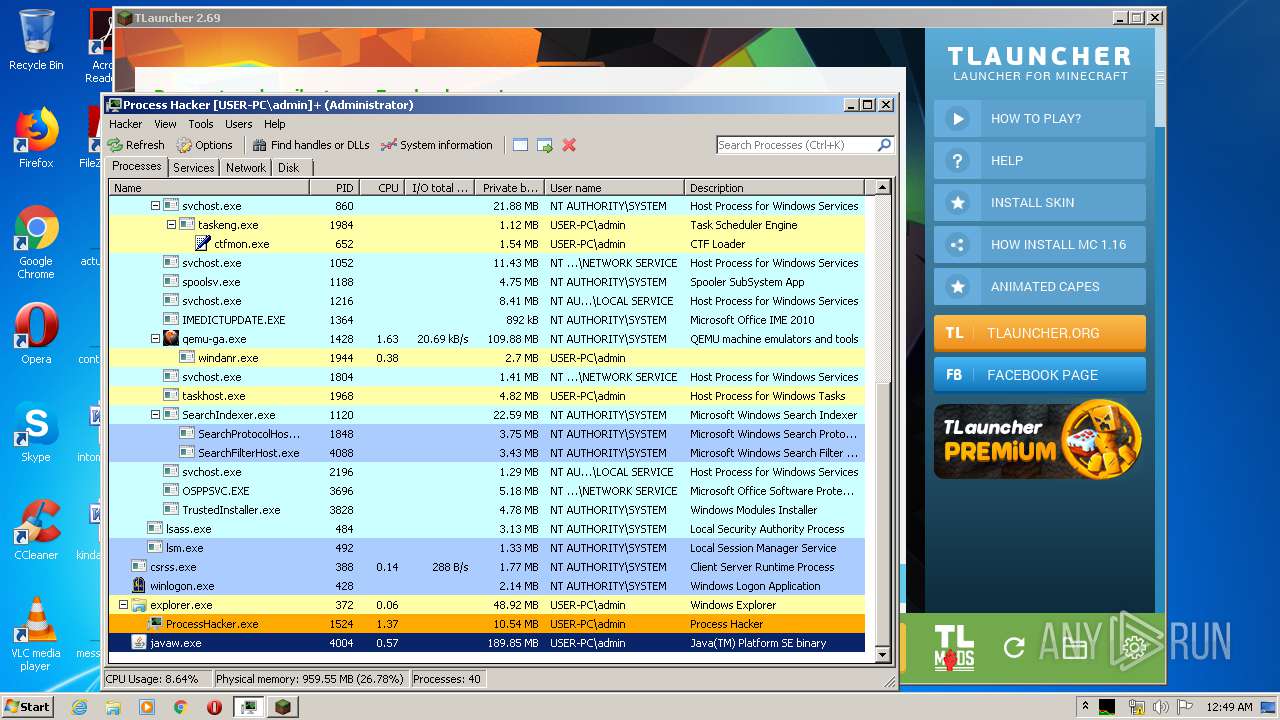
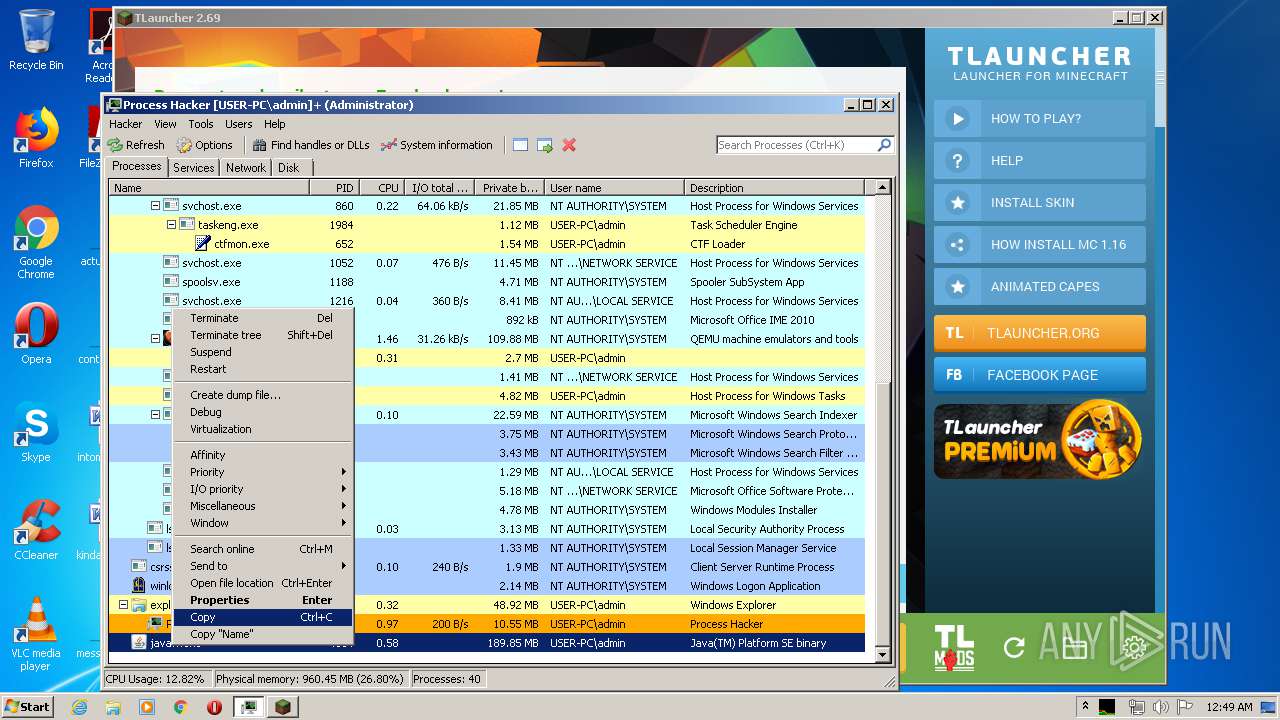
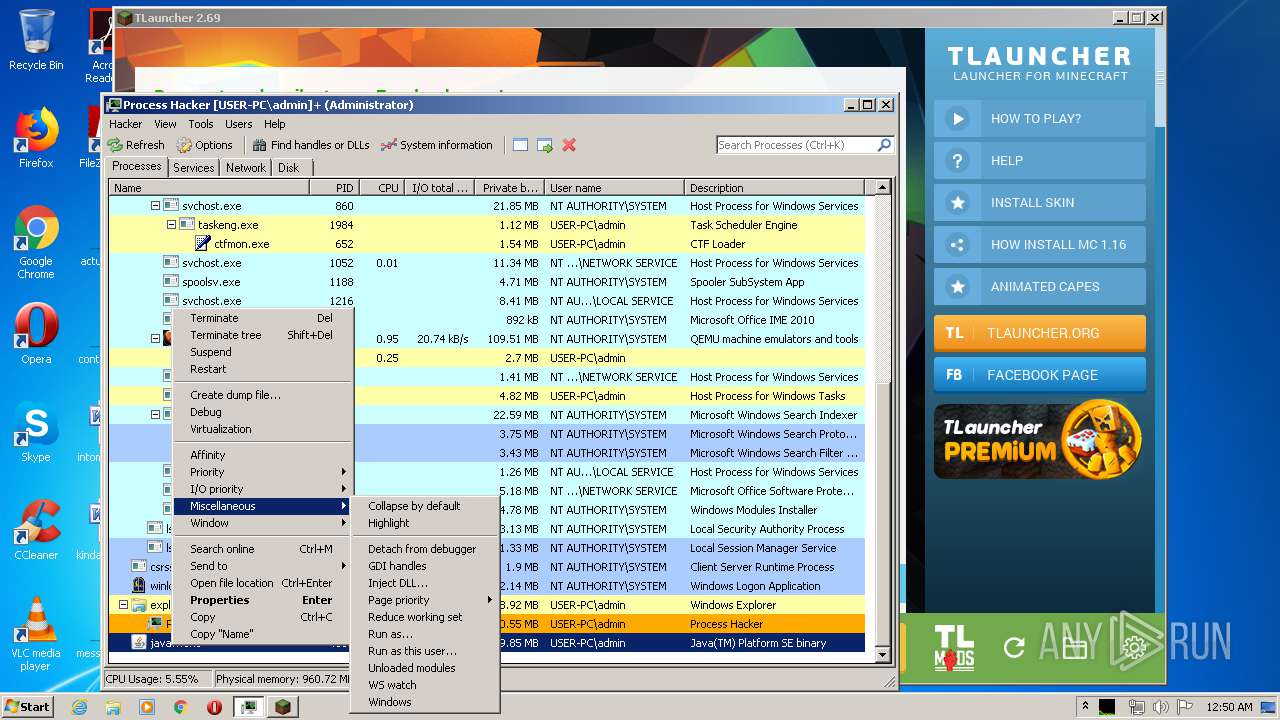
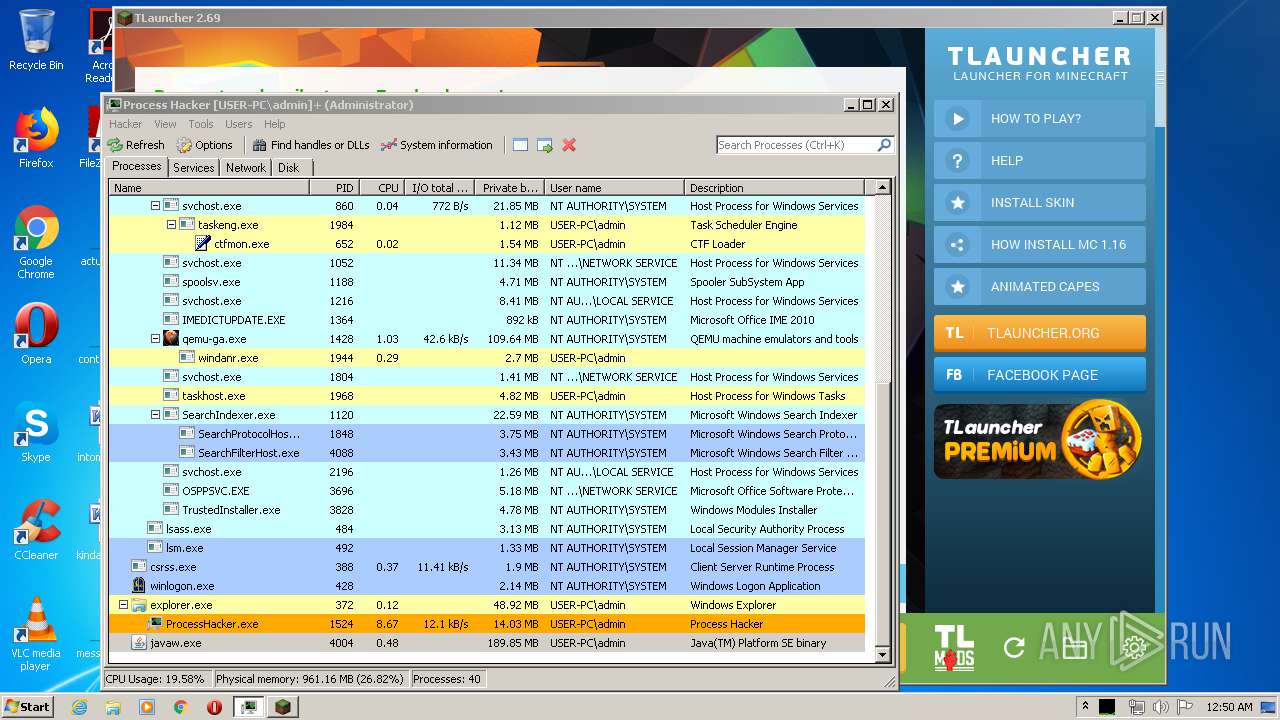
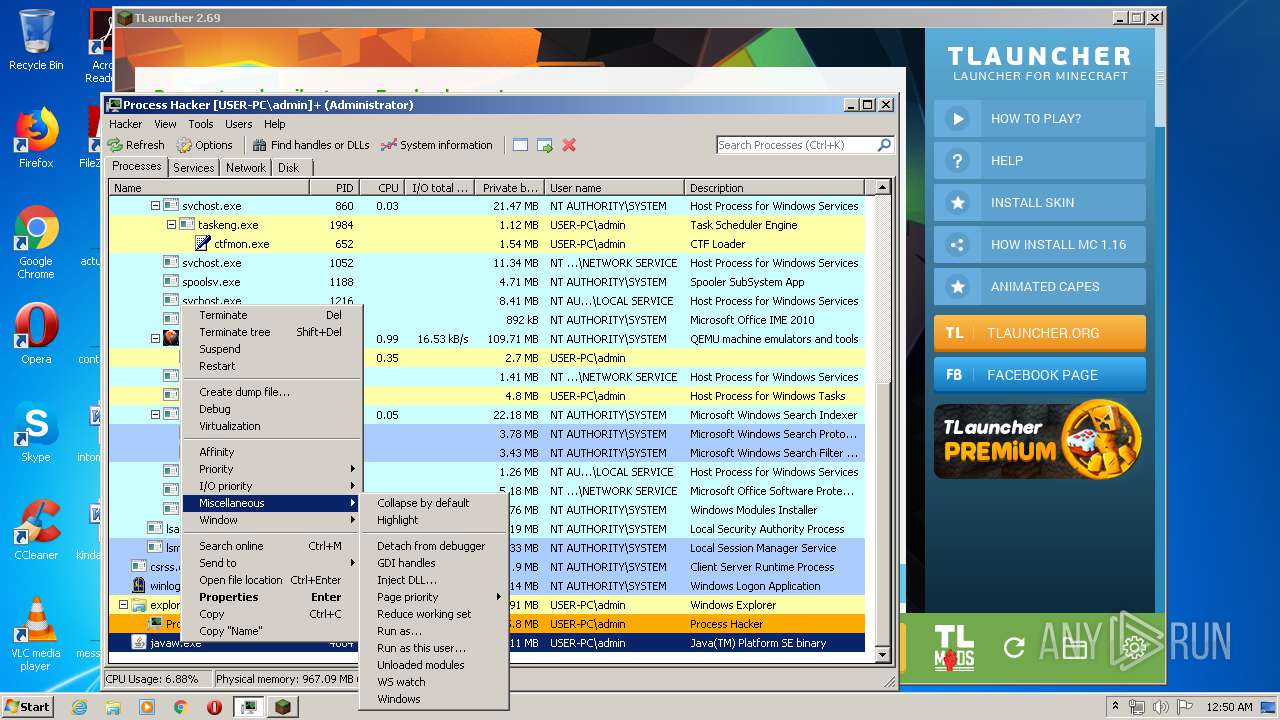
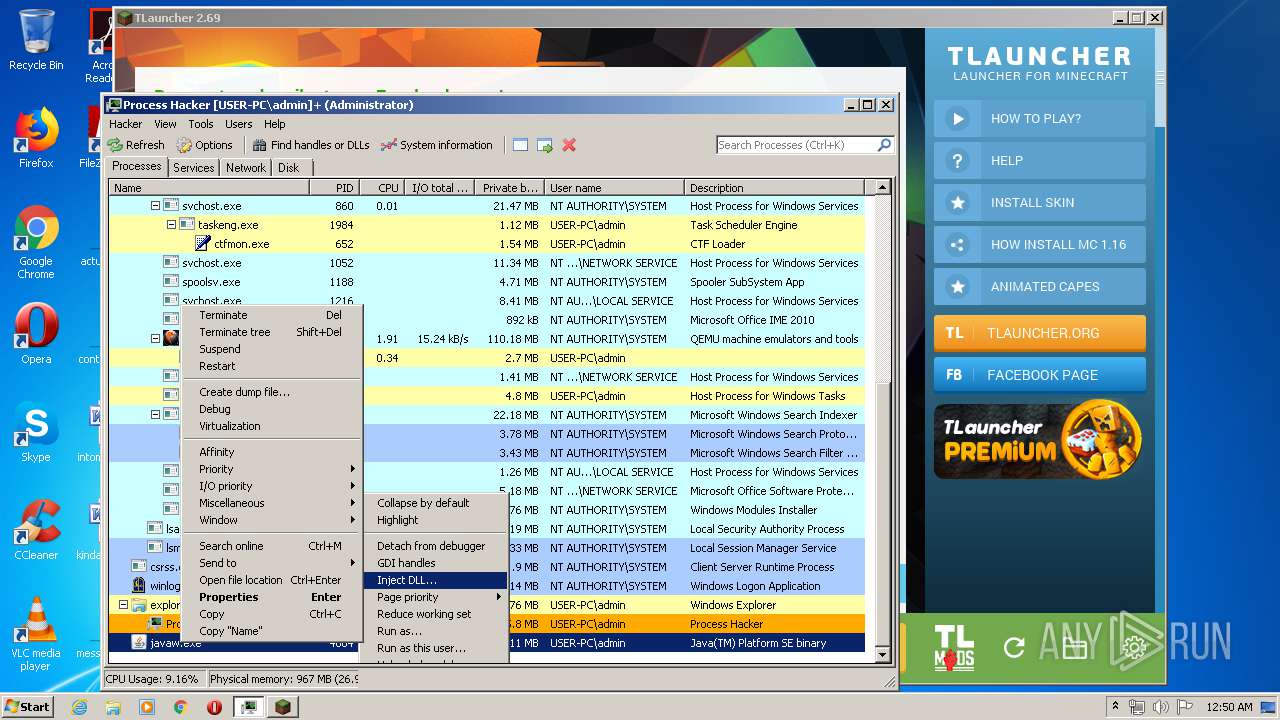
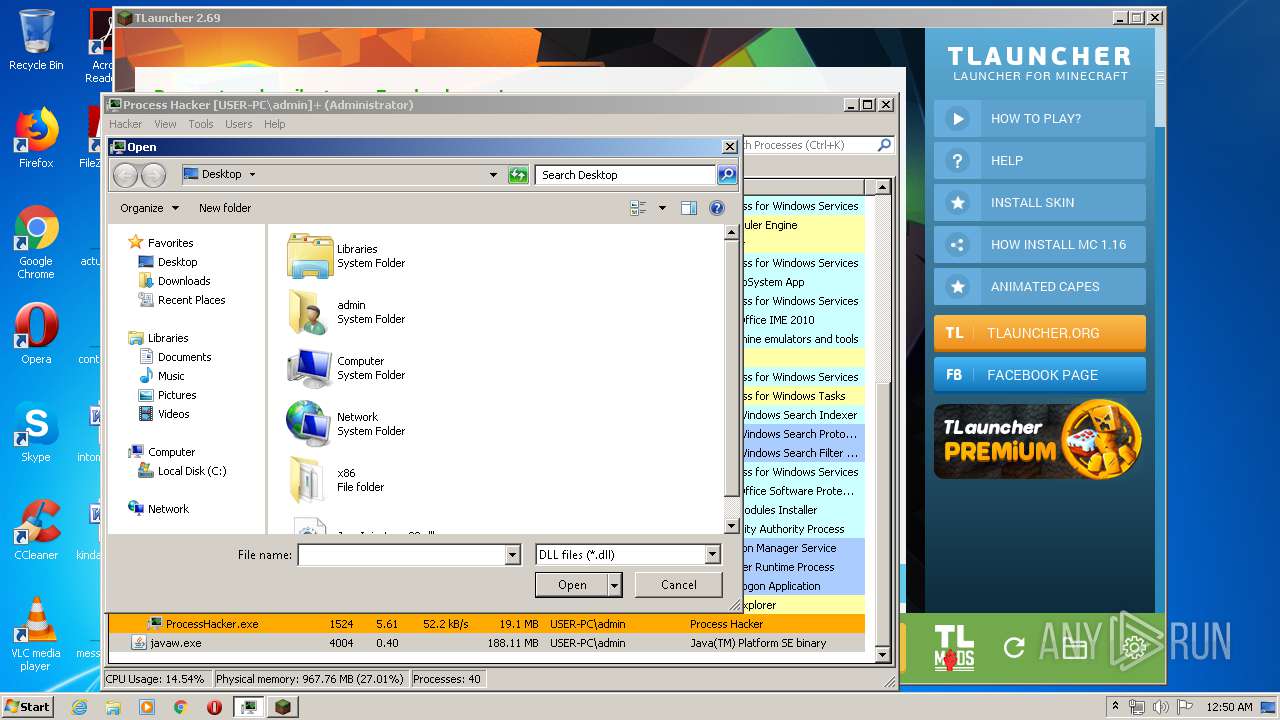
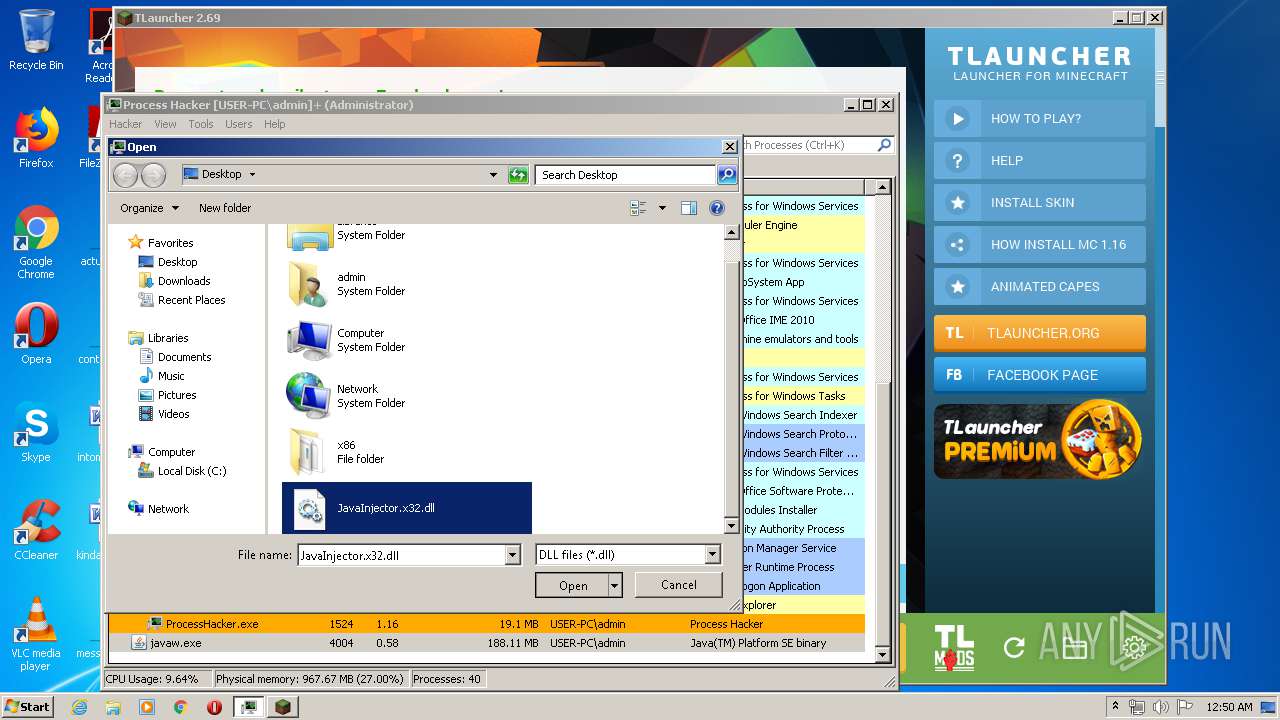
- ProcessHacker.exe (PID: 1524)
- javaw.exe (PID: 4004)
- javaw.exe (PID: 440)
Actions looks like stealing of personal data
- ProcessHacker.exe (PID: 1524)
- javaw.exe (PID: 4004)
Changes settings of System certificates
- ProcessHacker.exe (PID: 1524)
SUSPICIOUS
Starts CMD.EXE for commands execution
- javaw.exe (PID: 680)
- javaw.exe (PID: 4004)
Uses WMIC.EXE to obtain a system information
- cmd.exe (PID: 280)
- cmd.exe (PID: 540)
- cmd.exe (PID: 2744)
- cmd.exe (PID: 3620)
- cmd.exe (PID: 4040)
Starts application with an unusual extension
- cmd.exe (PID: 2744)
- cmd.exe (PID: 280)
- cmd.exe (PID: 540)
- cmd.exe (PID: 3620)
- cmd.exe (PID: 4040)
- cmd.exe (PID: 2336)
- cmd.exe (PID: 1332)
Executes JAVA applets
- javaw.exe (PID: 680)
- javaw.exe (PID: 4004)
Application launched itself
- javaw.exe (PID: 680)
- javaw.exe (PID: 4004)
Creates files in the user directory
- javaw.exe (PID: 680)
- dxdiag.exe (PID: 3508)
- ProcessHacker.exe (PID: 1524)
- javaw.exe (PID: 440)
- javaw.exe (PID: 4004)
Uses SYSTEMINFO.EXE to read environment
- cmd.exe (PID: 1332)
Connects to unusual port
- javaw.exe (PID: 4004)
Executable content was dropped or overwritten
- javaw.exe (PID: 4004)
Adds / modifies Windows certificates
- ProcessHacker.exe (PID: 1524)
INFO
Reads the hosts file
- chrome.exe (PID: 3964)
- chrome.exe (PID: 3568)
Manual execution by user
- javaw.exe (PID: 680)
- ProcessHacker.exe (PID: 1524)
Reads Internet Cache Settings
- chrome.exe (PID: 3568)
Application launched itself
- chrome.exe (PID: 3568)
Dropped object may contain Bitcoin addresses
- javaw.exe (PID: 4004)
Reads settings of System Certificates
- ProcessHacker.exe (PID: 1524)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
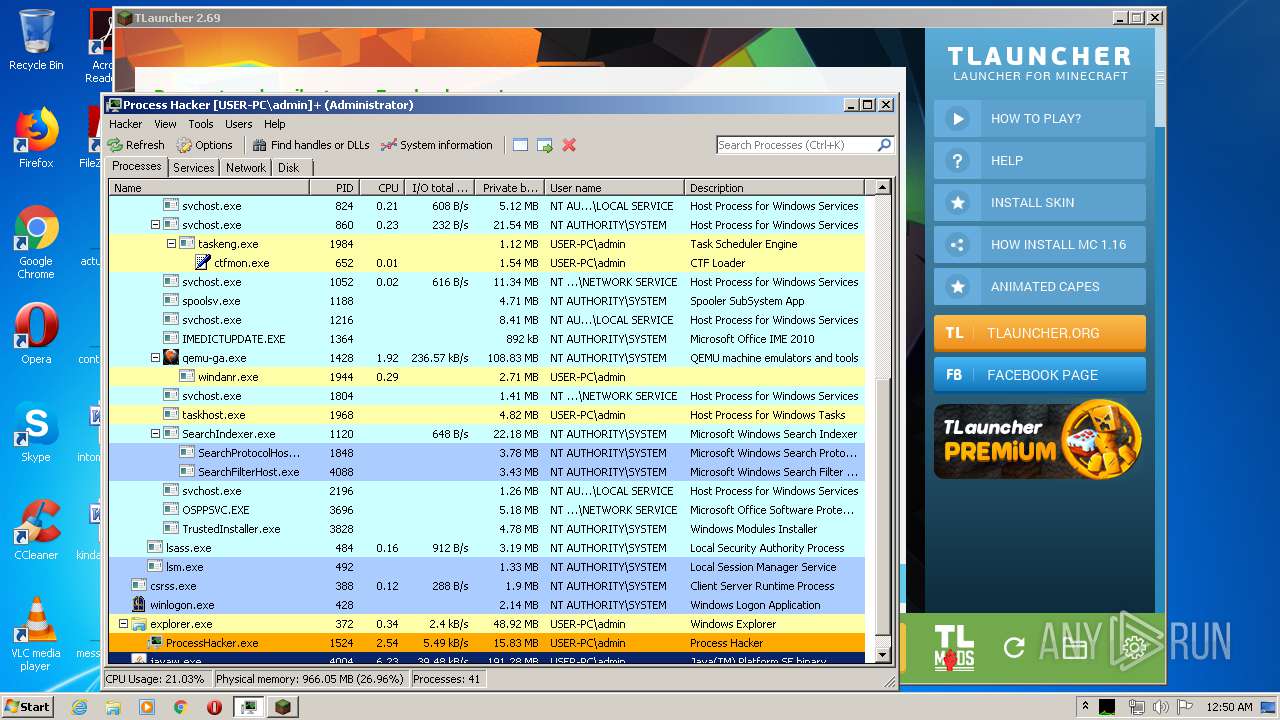
Total processes
101
Monitored processes
48
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 280 | cmd.exe /C chcp 437 & wmic os get osarchitecture | C:\Windows\system32\cmd.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
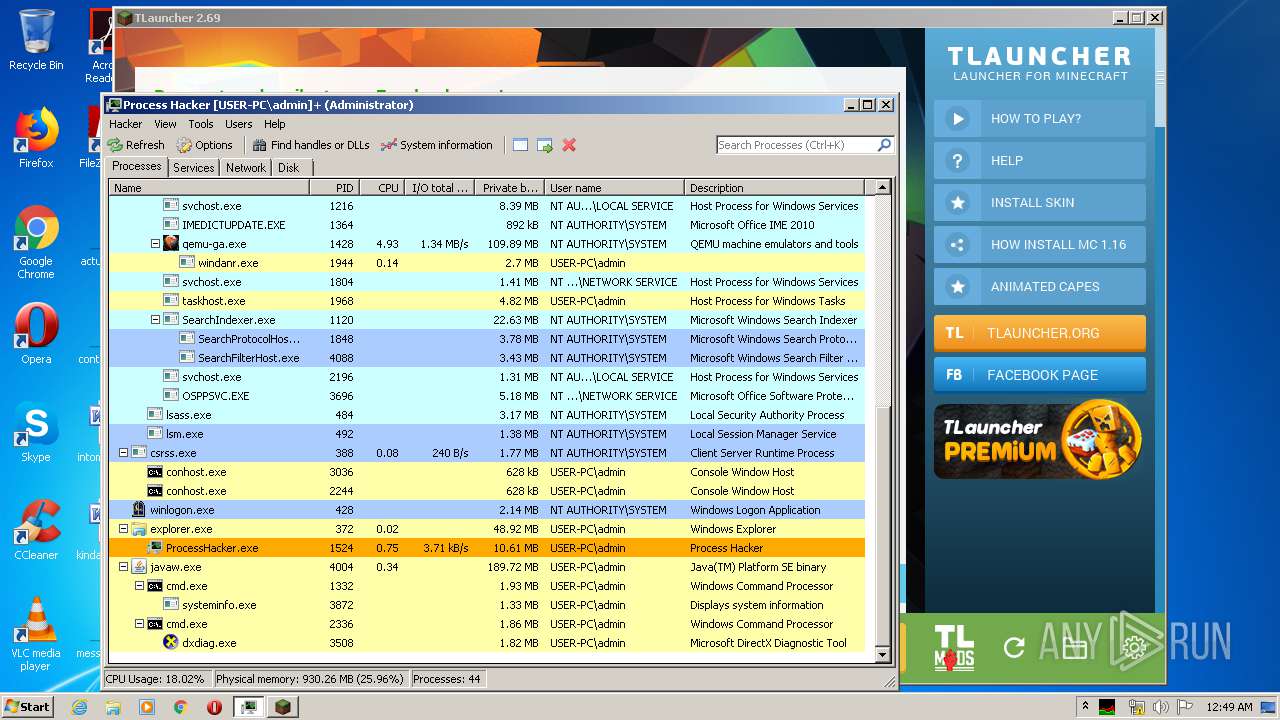
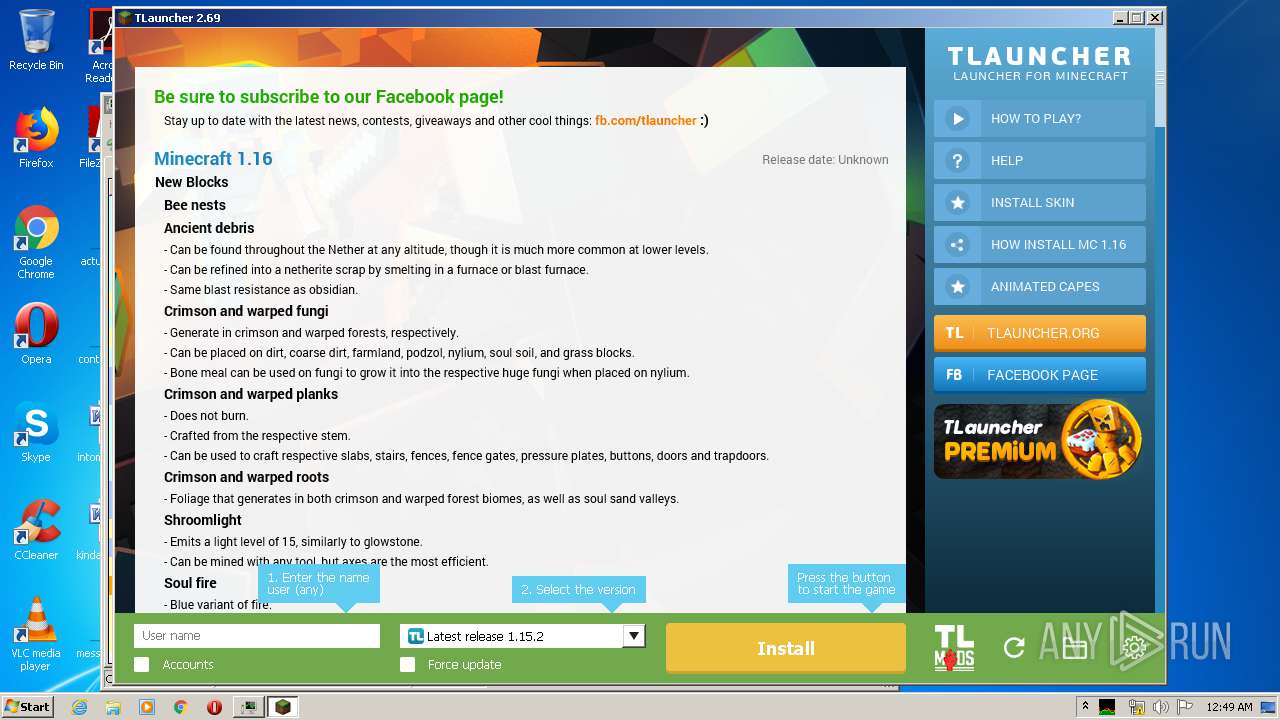
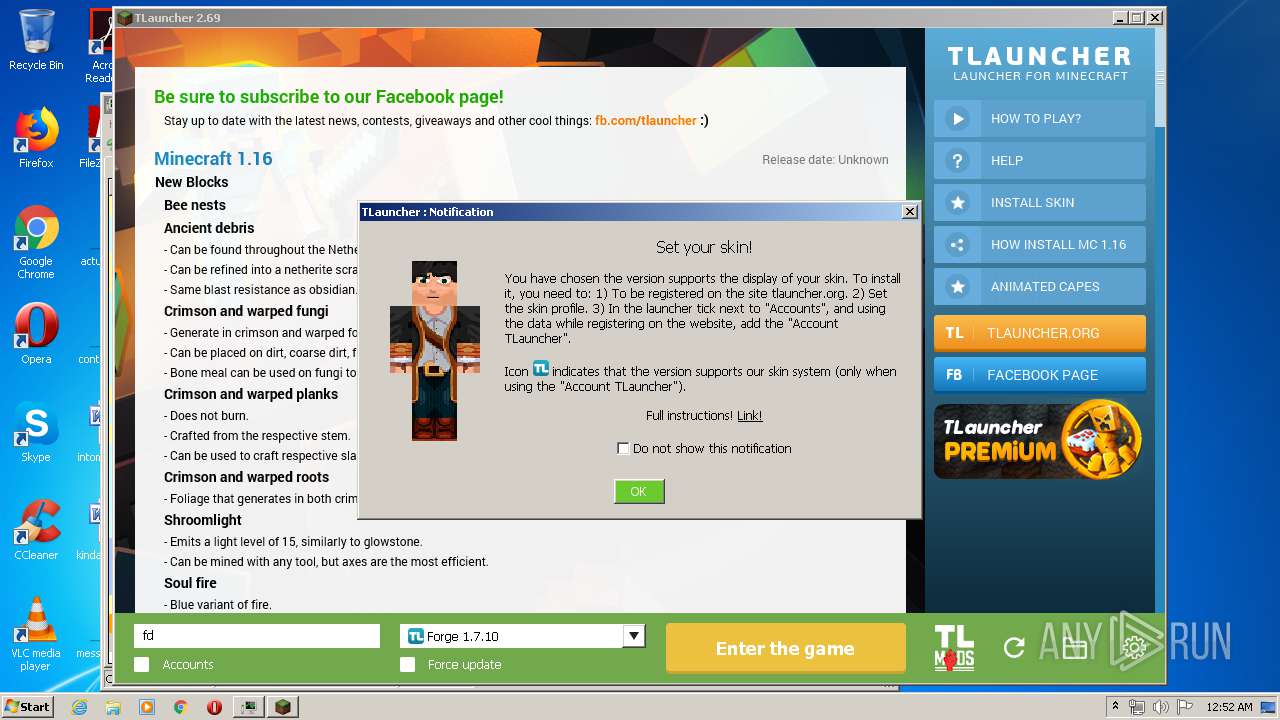
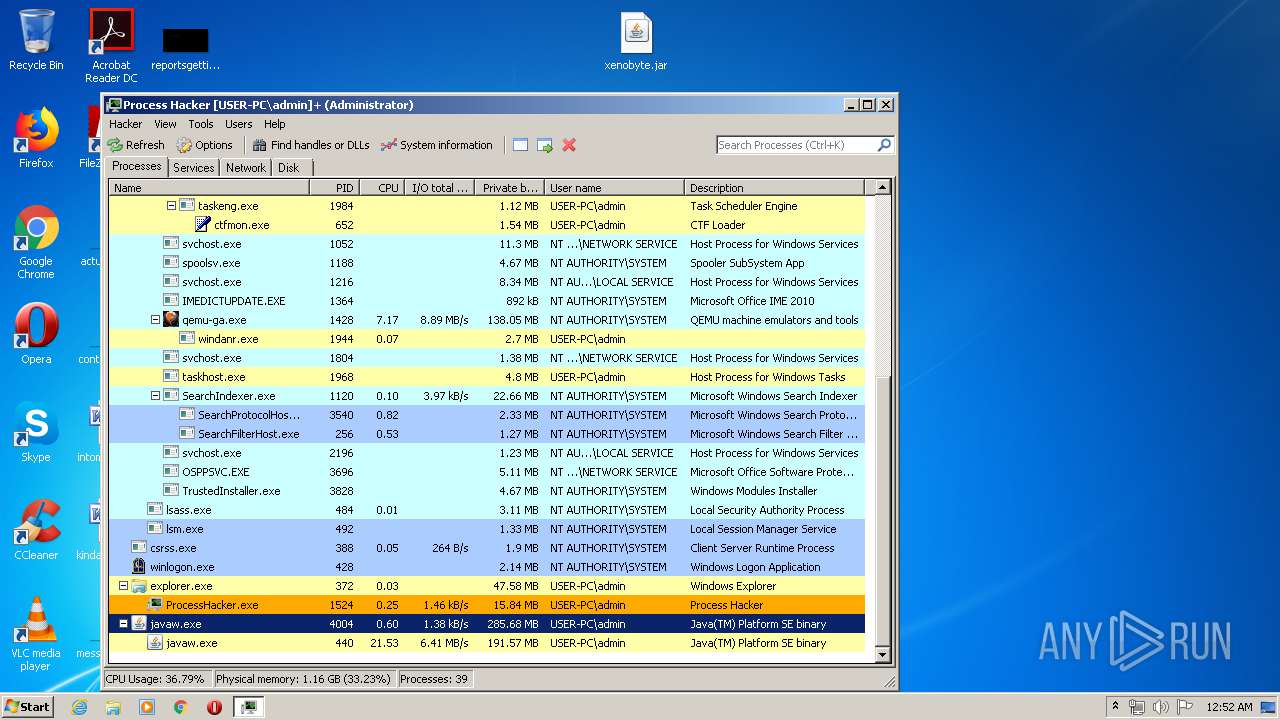
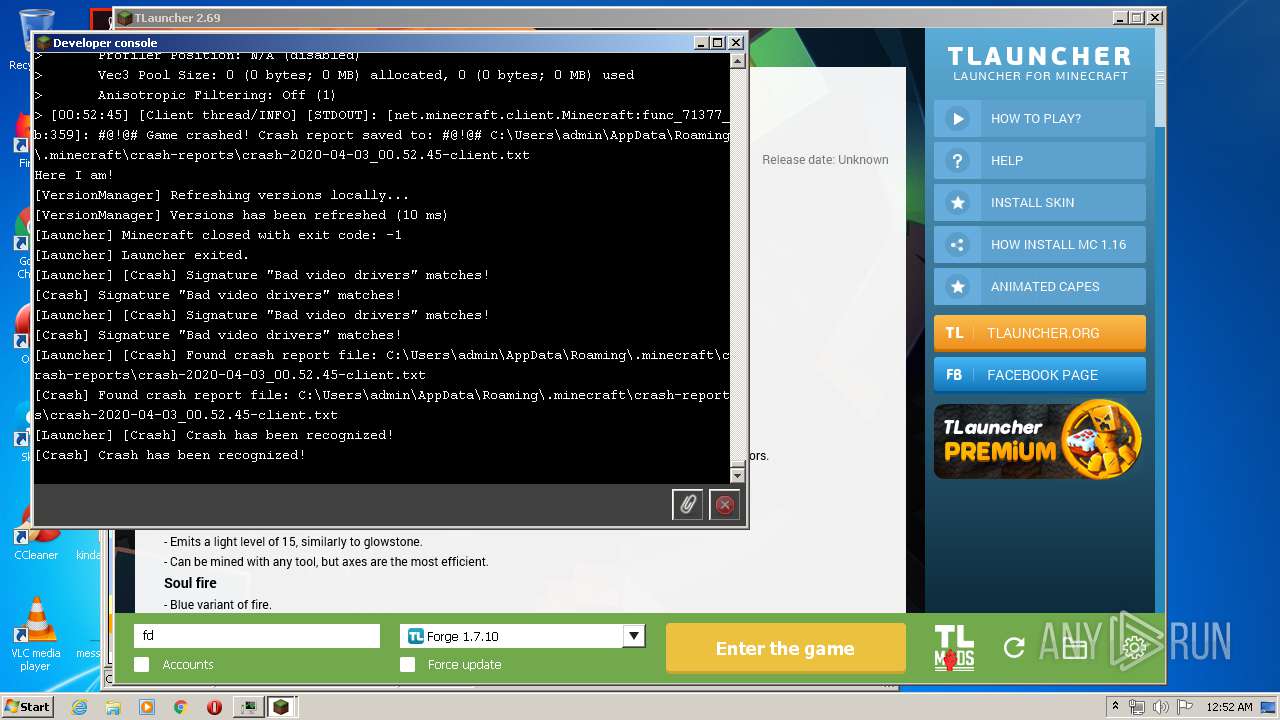
| 440 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -Djava.net.preferIPv4Stack=true -Xmn128M -Xmx1024M "-Djava.library.path=C:\Users\admin\AppData\Roaming\.minecraft\versions\Forge 1.7.10\natives" -cp "C:\Users\admin\AppData\Roaming\.minecraft\libraries\net\minecraftforge\forge\1.7.10-10.13.4.1614-1.7.10\forge-1.7.10-10.13.4.1614-1.7.10.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\net\minecraft\launchwrapper\1.12\launchwrapper-1.12.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\ow2\asm\asm-all\5.0.3\asm-all-5.0.3.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\com\typesafe\akka\akka-actor_2.11\2.3.3\akka-actor_2.11-2.3.3.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\com\typesafe\config\1.2.1\config-1.2.1.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\scala-lang\scala-actors-migration_2.11\1.1.0\scala-actors-migration_2.11-1.1.0.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\scala-lang\scala-compiler\2.11.1\scala-compiler-2.11.1.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\scala-lang\plugins\scala-continuations-library_2.11\1.0.2\scala-continuations-library_2.11-1.0.2.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\scala-lang\plugins\scala-continuations-plugin_2.11.1\1.0.2\scala-continuations-plugin_2.11.1-1.0.2.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\scala-lang\scala-library\2.11.1\scala-library-2.11.1.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\scala-lang\scala-parser-combinators_2.11\1.0.1\scala-parser-combinators_2.11-1.0.1.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\scala-lang\scala-reflect\2.11.1\scala-reflect-2.11.1.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\scala-lang\scala-swing_2.11\1.0.1\scala-swing_2.11-1.0.1.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\scala-lang\scala-xml_2.11\1.0.2\scala-xml_2.11-1.0.2.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\lzma\lzma\0.0.1\lzma-0.0.1.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\com\google\guava\guava\17.0\guava-17.0.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\tlauncher\netty\1.6\netty-1.6.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\com\mojang\realms\1.3.5\realms-1.3.5.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\apache\commons\commons-compress\1.8.1\commons-compress-1.8.1.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\apache\httpcomponents\httpclient\4.3.3\httpclient-4.3.3.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\commons-logging\commons-logging\1.1.3\commons-logging-1.1.3.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\apache\httpcomponents\httpcore\4.3.2\httpcore-4.3.2.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\java3d\vecmath\1.3.1\vecmath-1.3.1.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\net\sf\trove4j\trove4j\3.0.3\trove4j-3.0.3.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\com\ibm\icu\icu4j-core-mojang\51.2\icu4j-core-mojang-51.2.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\net\sf\jopt-simple\jopt-simple\4.5\jopt-simple-4.5.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\com\paulscode\codecjorbis\20101023\codecjorbis-20101023.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\com\paulscode\codecwav\20101023\codecwav-20101023.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\com\paulscode\libraryjavasound\20101123\libraryjavasound-20101123.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\com\paulscode\librarylwjglopenal\20100824\librarylwjglopenal-20100824.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\com\paulscode\soundsystem\20120107\soundsystem-20120107.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\io\netty\netty-all\4.0.10.Final\netty-all-4.0.10.Final.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\apache\commons\commons-lang3\3.3.2\commons-lang3-3.3.2.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\commons-io\commons-io\2.4\commons-io-2.4.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\commons-codec\commons-codec\1.9\commons-codec-1.9.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\net\java\jinput\jinput\2.0.5\jinput-2.0.5.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\net\java\jutils\jutils\1.0.0\jutils-1.0.0.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\com\google\code\gson\gson\2.2.4\gson-2.2.4.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\tlauncher\authlib\1.6.21\authlib-1.6.21.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\apache\logging\log4j\log4j-api\2.0-beta9\log4j-api-2.0-beta9.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\apache\logging\log4j\log4j-core\2.0-beta9\log4j-core-2.0-beta9.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\lwjgl\lwjgl\lwjgl\2.9.1\lwjgl-2.9.1.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\org\lwjgl\lwjgl\lwjgl_util\2.9.1\lwjgl_util-2.9.1.jar;C:\Users\admin\AppData\Roaming\.minecraft\libraries\tv\twitch\twitch\5.16\twitch-5.16.jar;C:\Users\admin\AppData\Roaming\.minecraft\versions\Forge 1.7.10\Forge 1.7.10.jar" -Dminecraft.applet.TargetDirectory=C:\Users\admin\AppData\Roaming\.minecraft -XX:+UseConcMarkSweepGC -Dfml.ignoreInvalidMinecraftCertificates=true -Dfml.ignorePatchDiscrepancies=true net.minecraft.launchwrapper.Launch --username fd --version "Forge 1.7.10" --gameDir C:\Users\admin\AppData\Roaming\.minecraft --assetsDir C:\Users\admin\AppData\Roaming\.minecraft\assets --assetIndex 1.7.10 --uuid 00000000-0000-0000-0000-000000000000 --accessToken null --userProperties [] --userType legacy --tweakClass cpw.mods.fml.common.launcher.FMLTweaker --width 925 --height 530 | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | — | javaw.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 4294967295 Version: 8.0.920.14 Modules
| |||||||||||||||
| 540 | cmd.exe /C chcp 437 & wmic os get osarchitecture | C:\Windows\system32\cmd.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
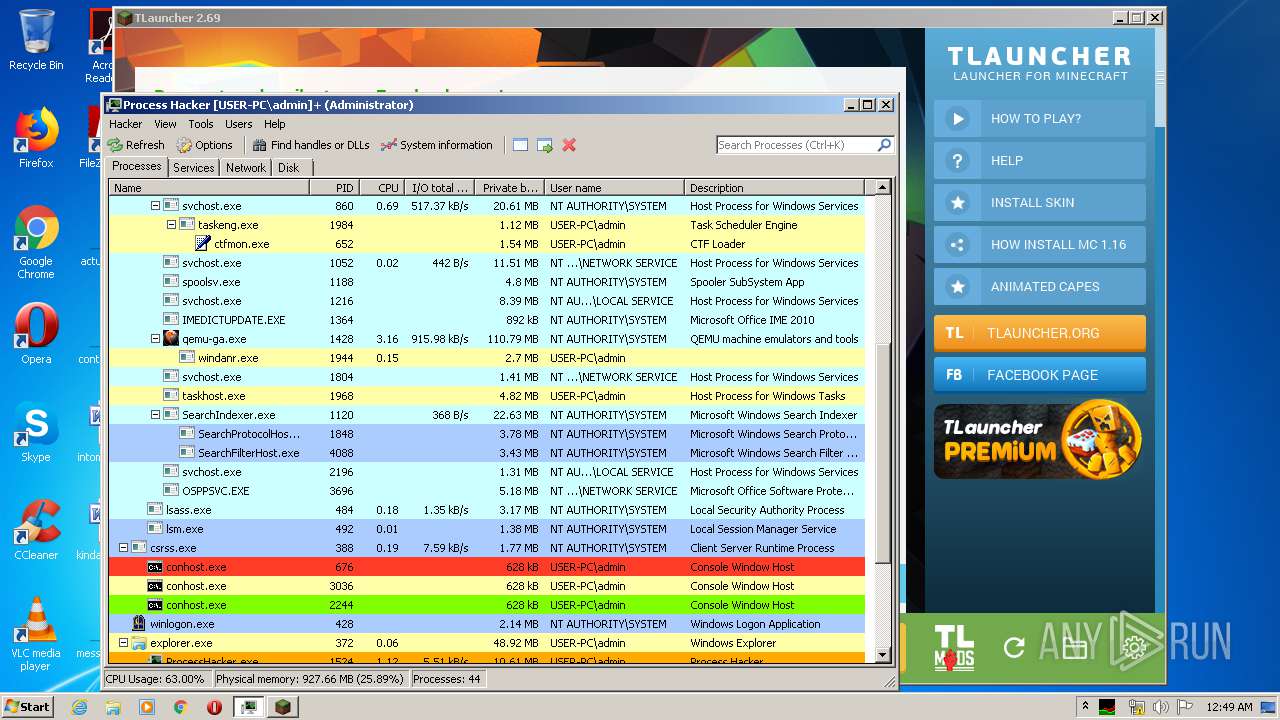
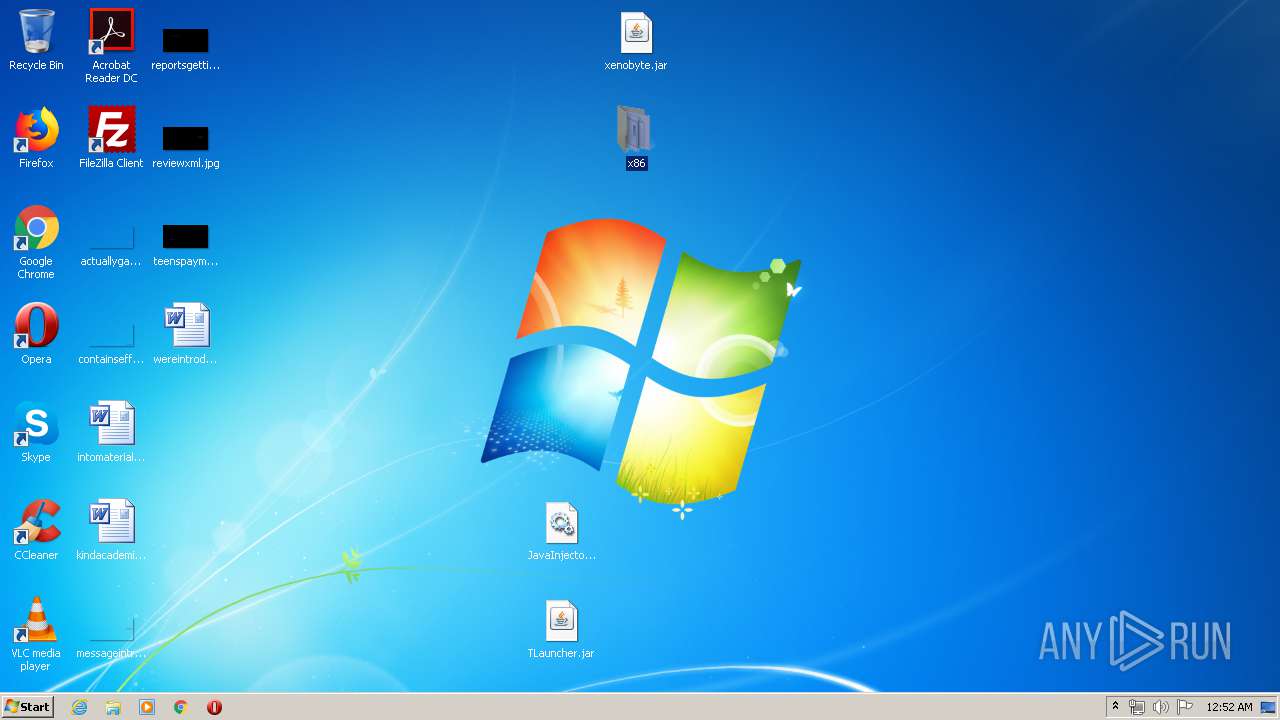
| 680 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -jar "C:\Users\admin\Desktop\TLauncher.jar" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | explorer.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 884 | wmic CPU get NAME | C:\Windows\System32\Wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 916 | wmic os get osarchitecture | C:\Windows\System32\Wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1332 | cmd.exe /C chcp 437 & systeminfo | C:\Windows\system32\cmd.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1440 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1000,7483782937906261148,14985180125037036720,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=11970029357780289933 --mojo-platform-channel-handle=4136 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
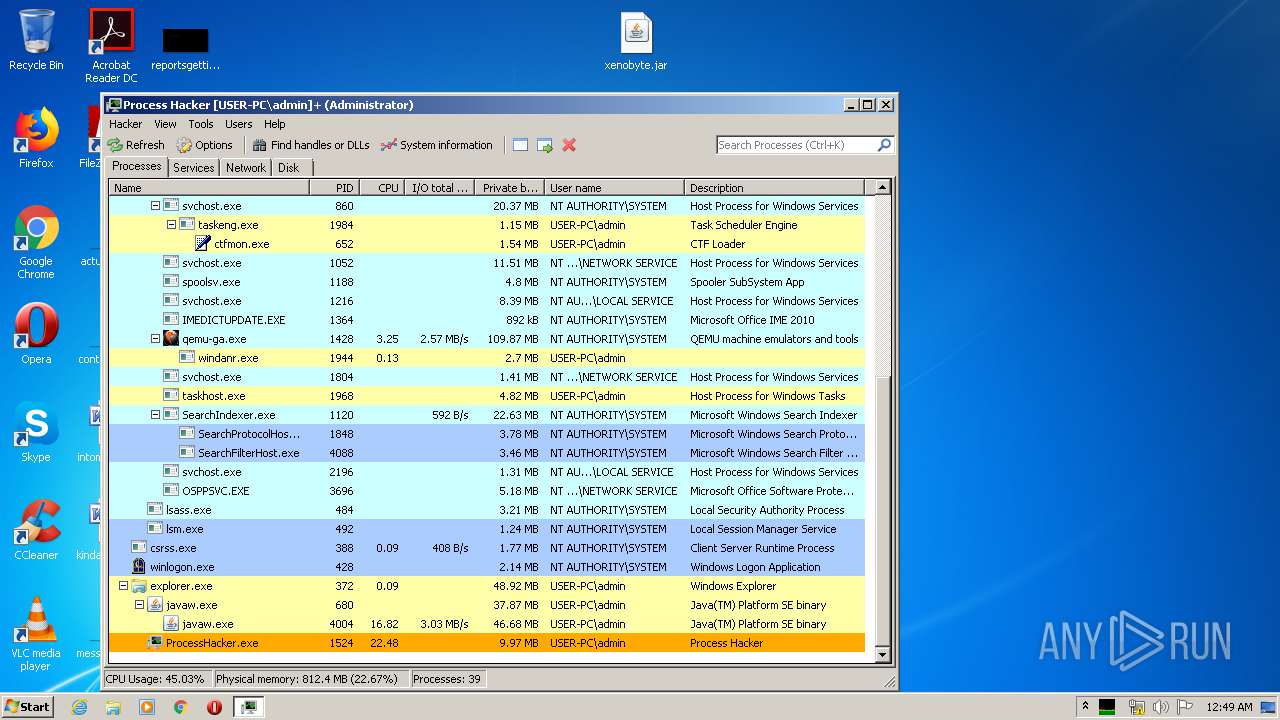
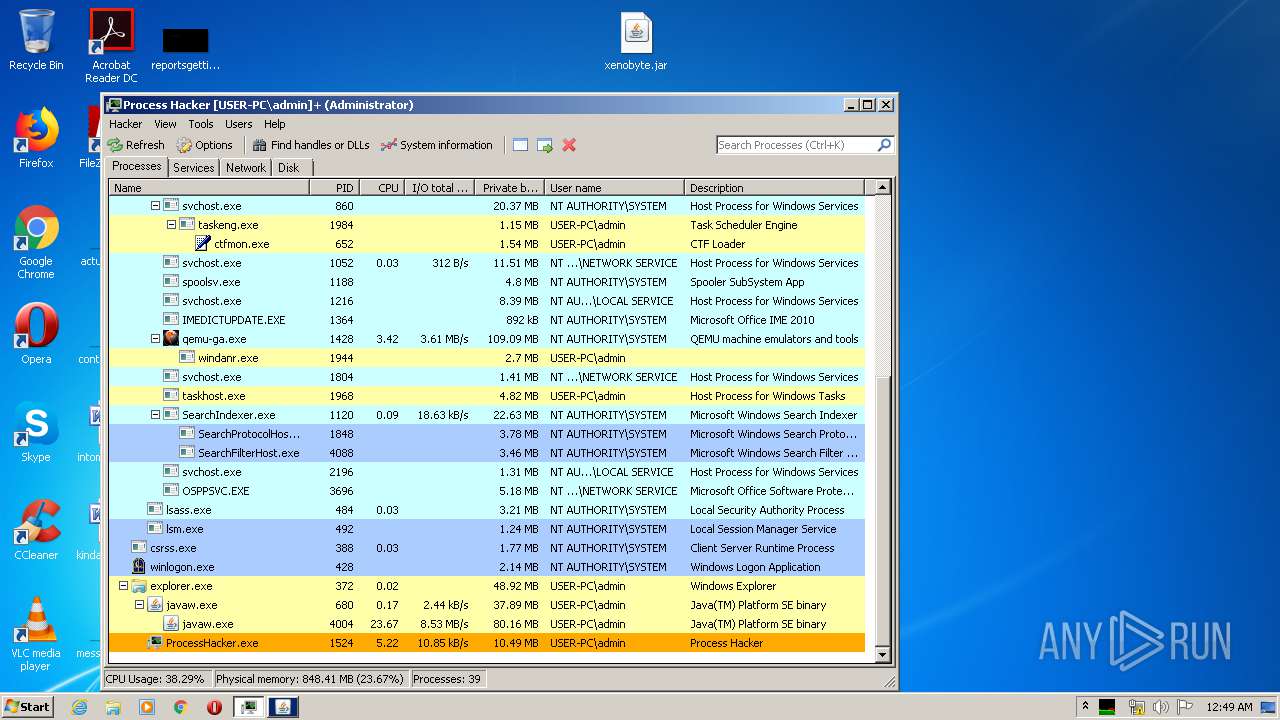
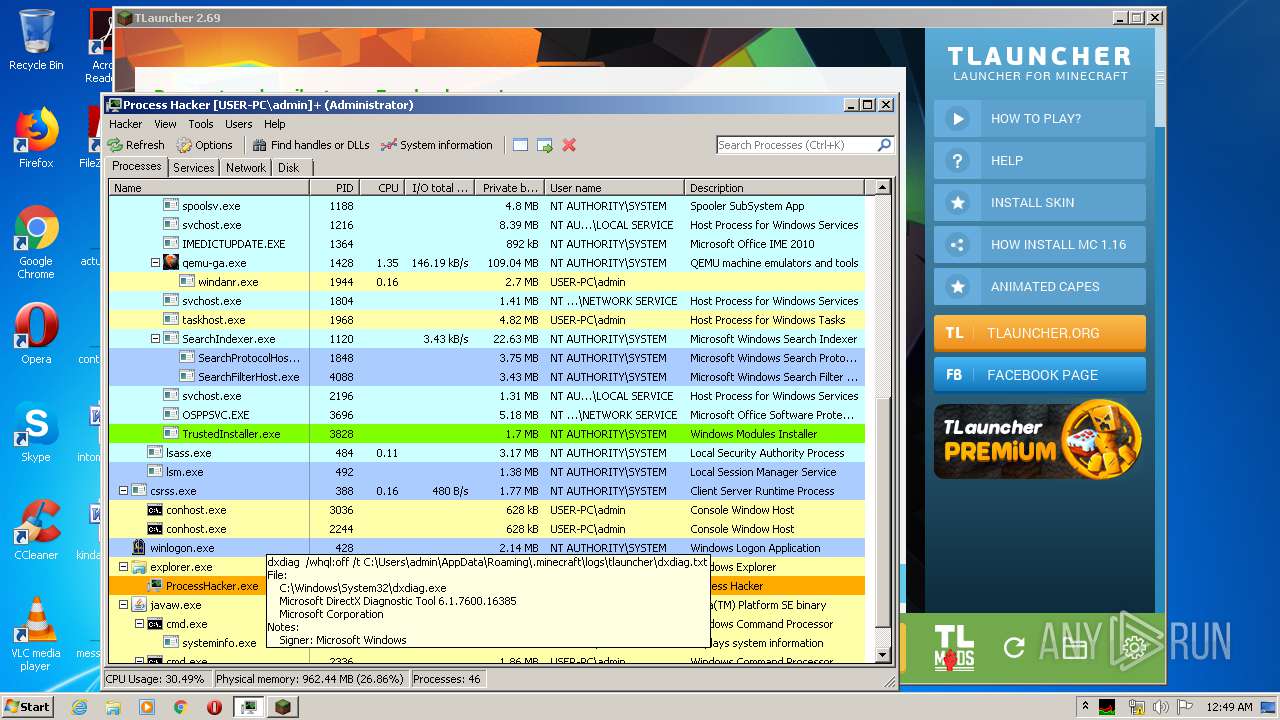
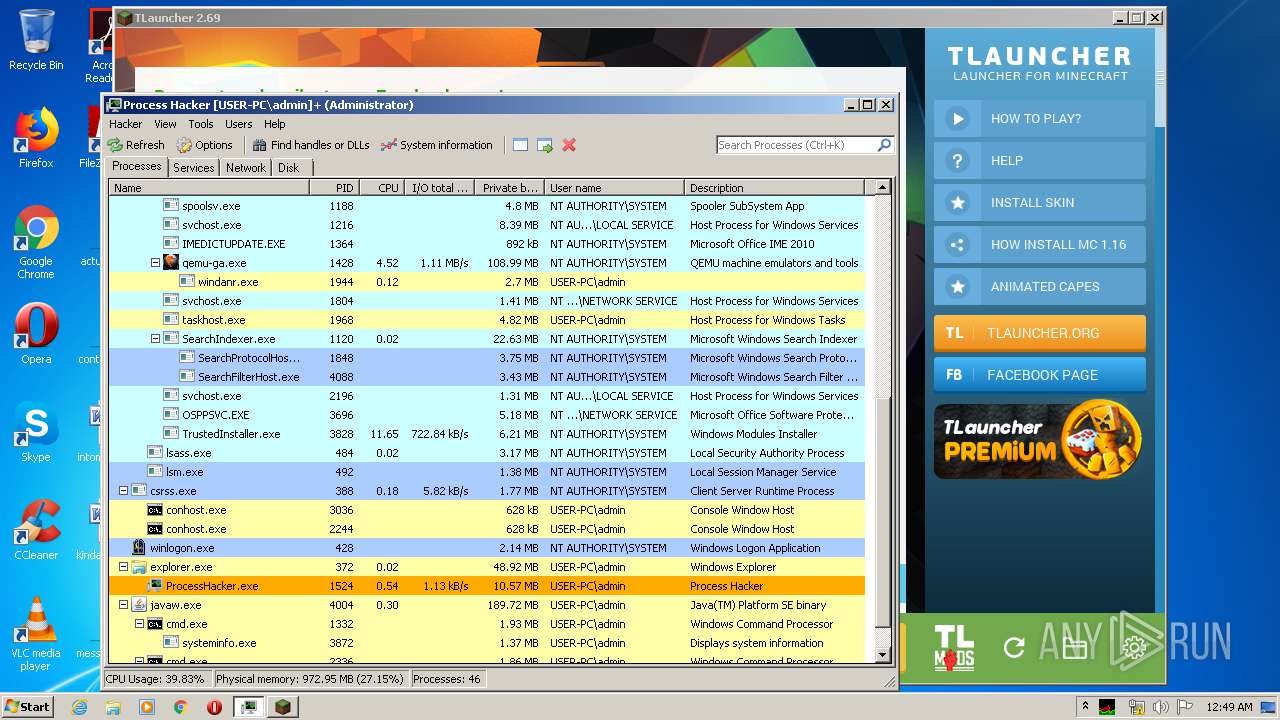
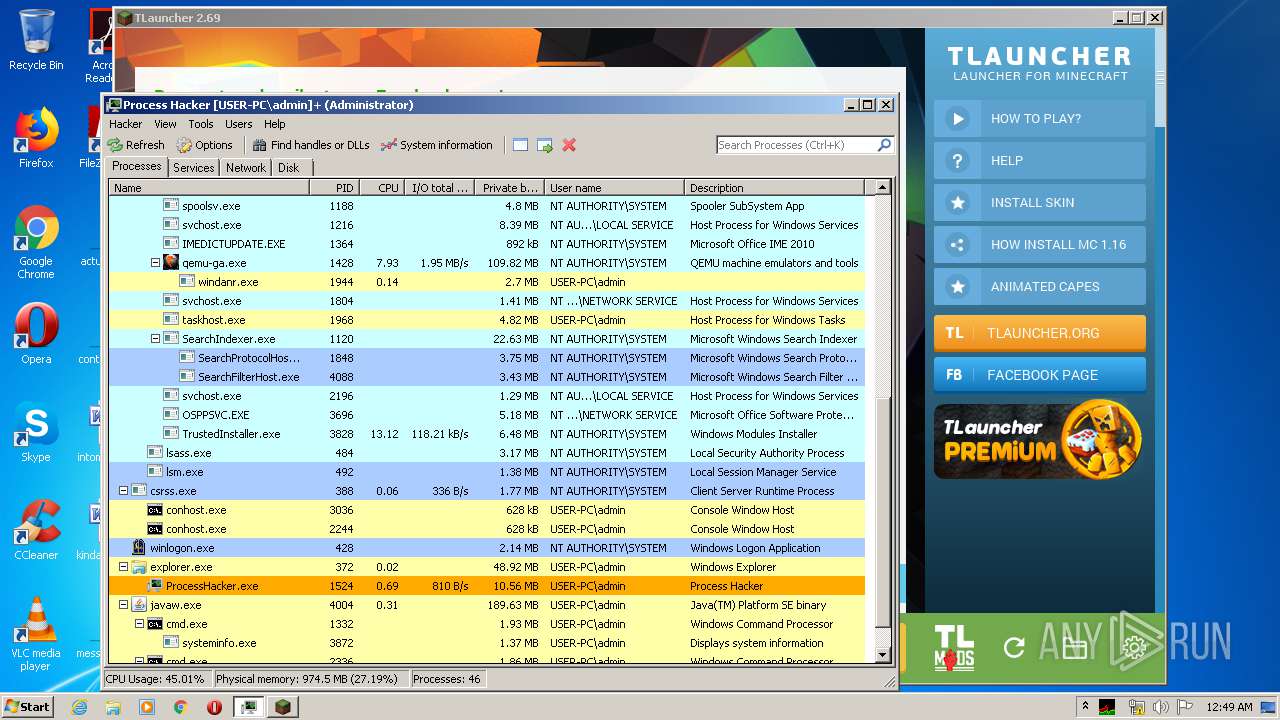
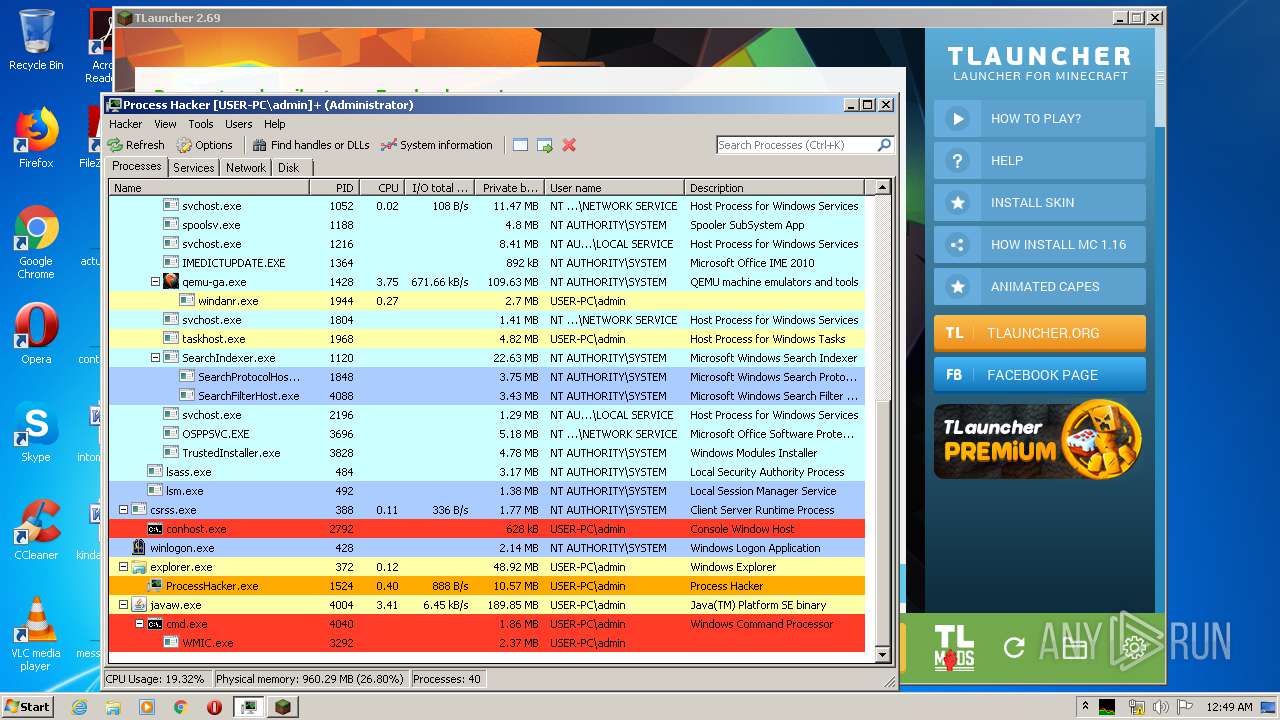
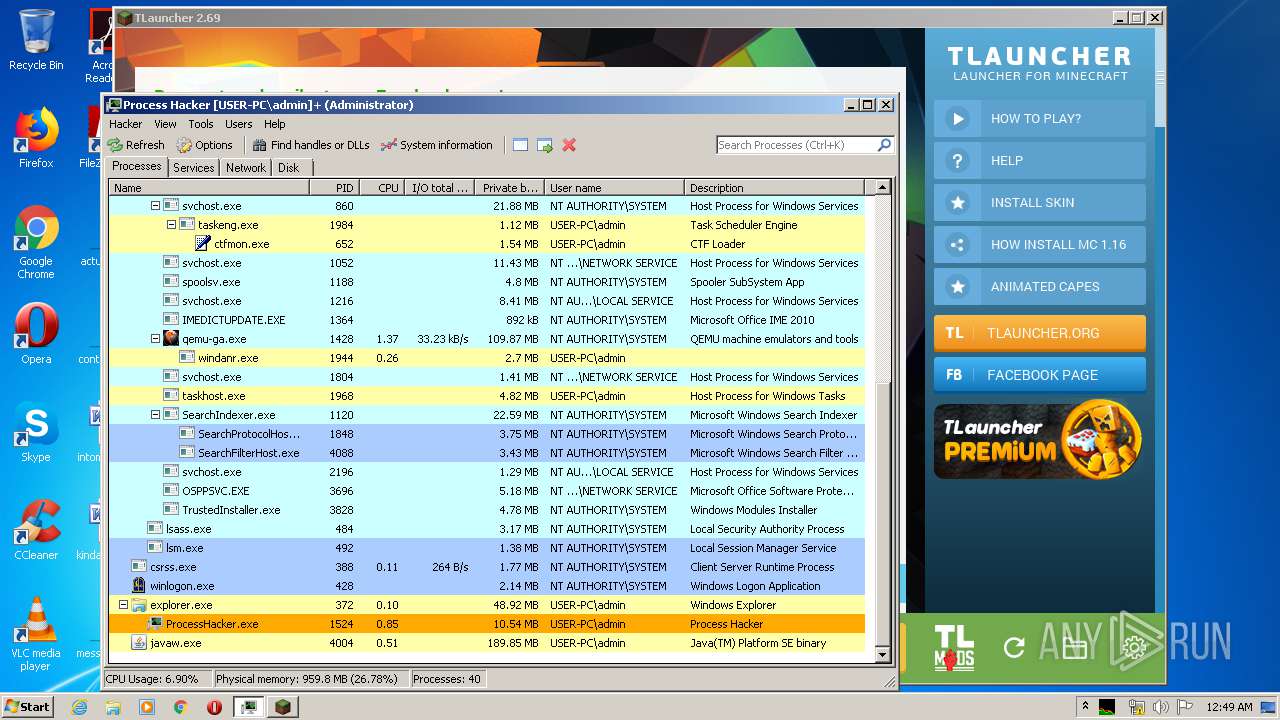
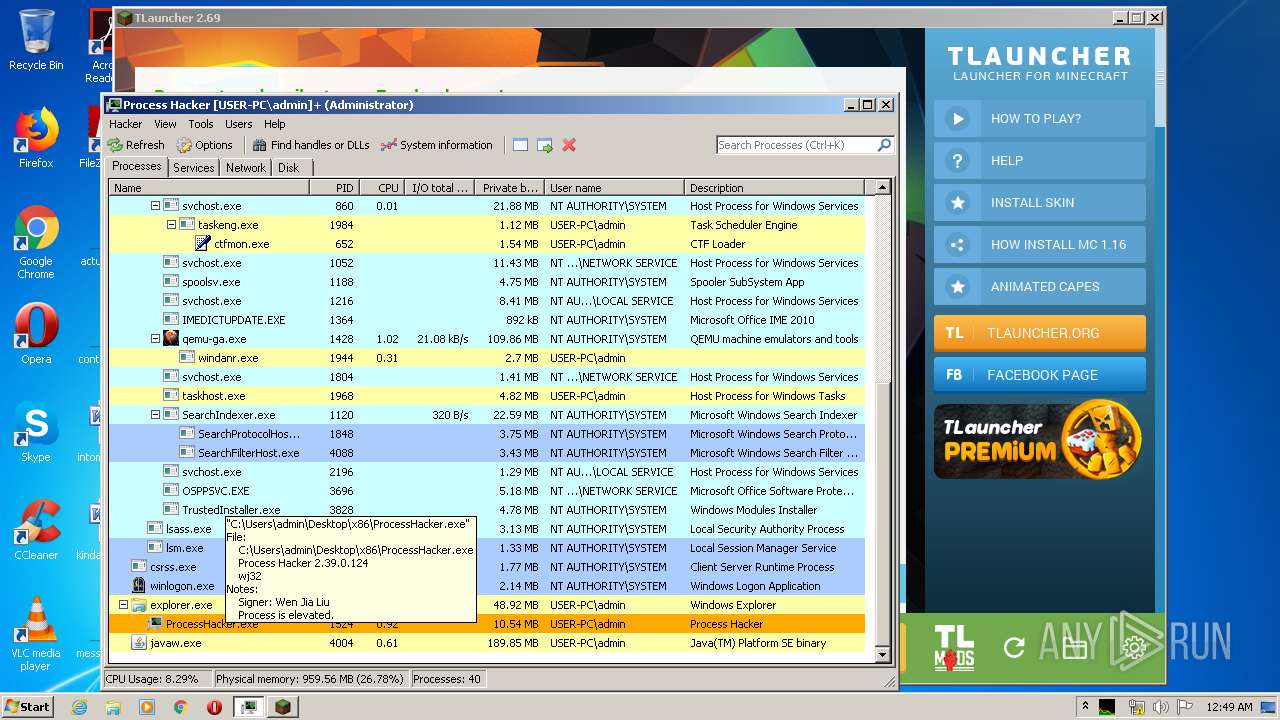
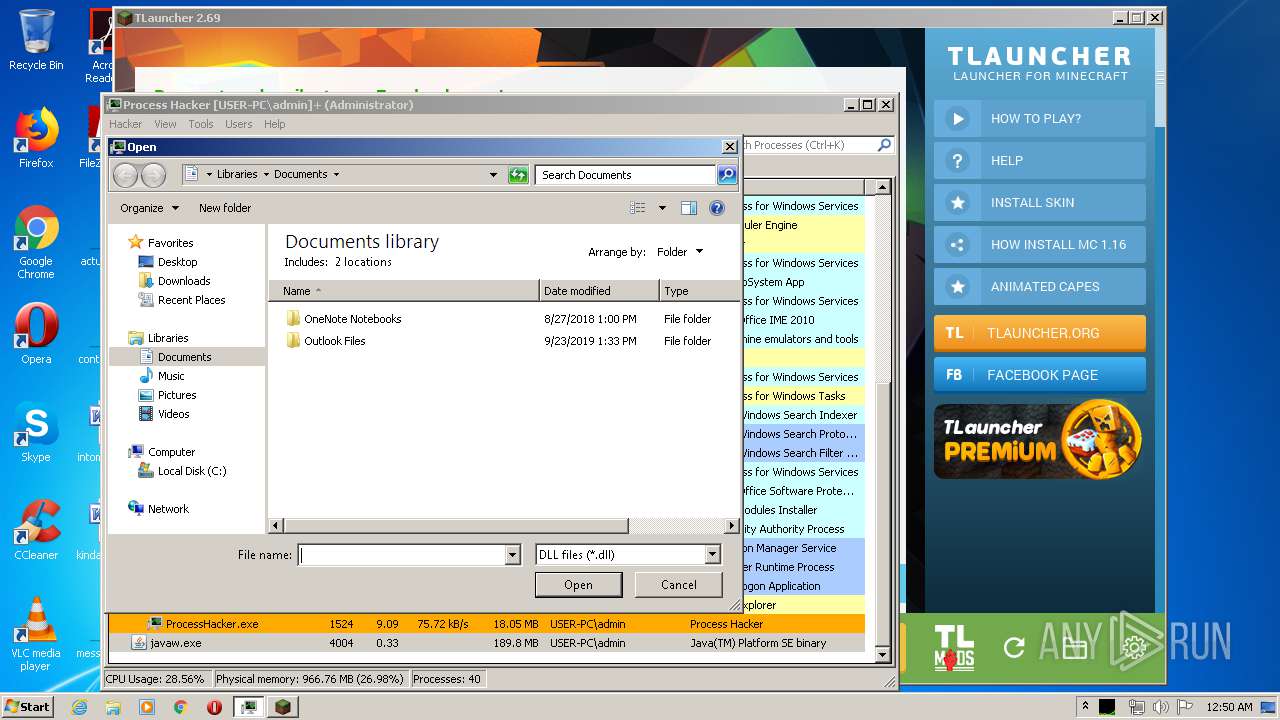
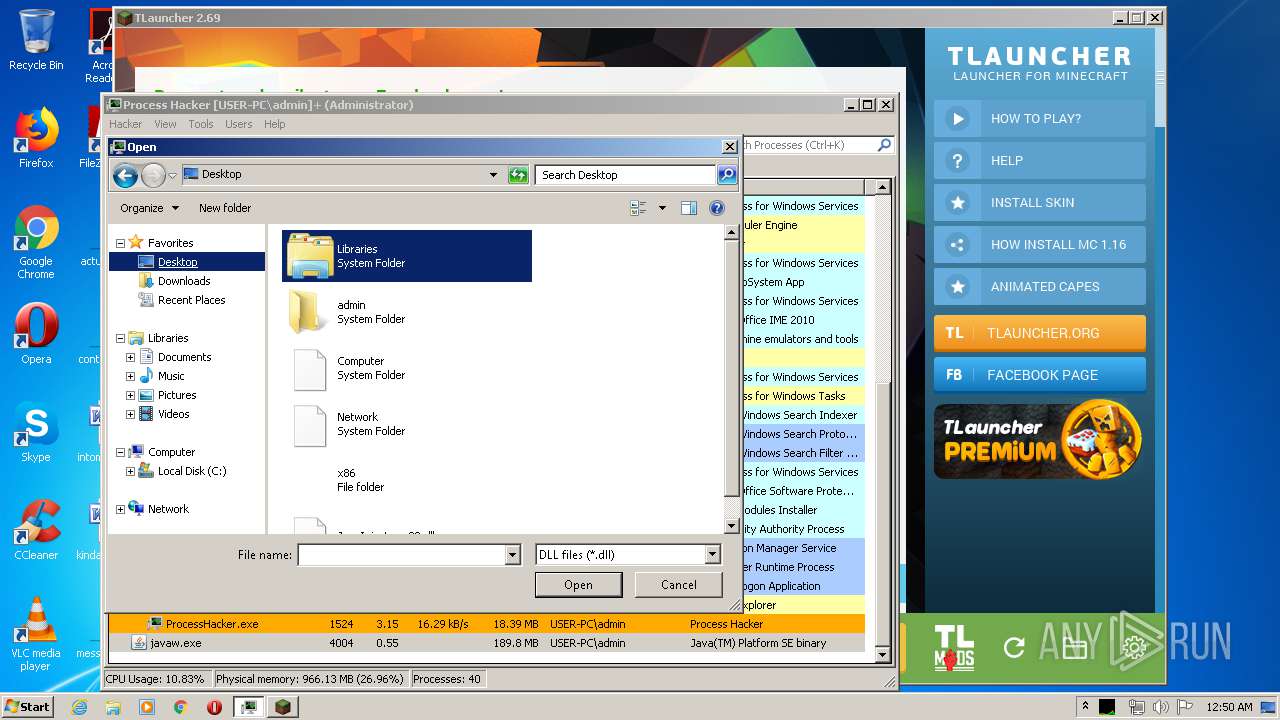
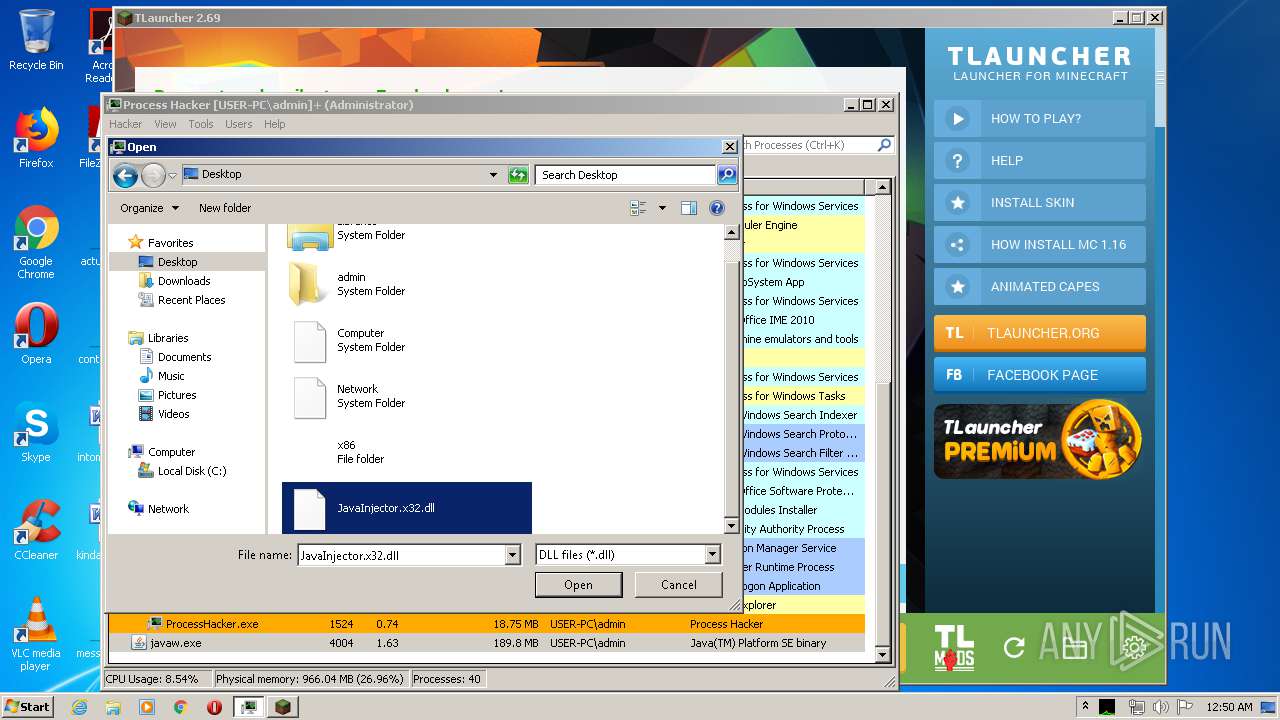
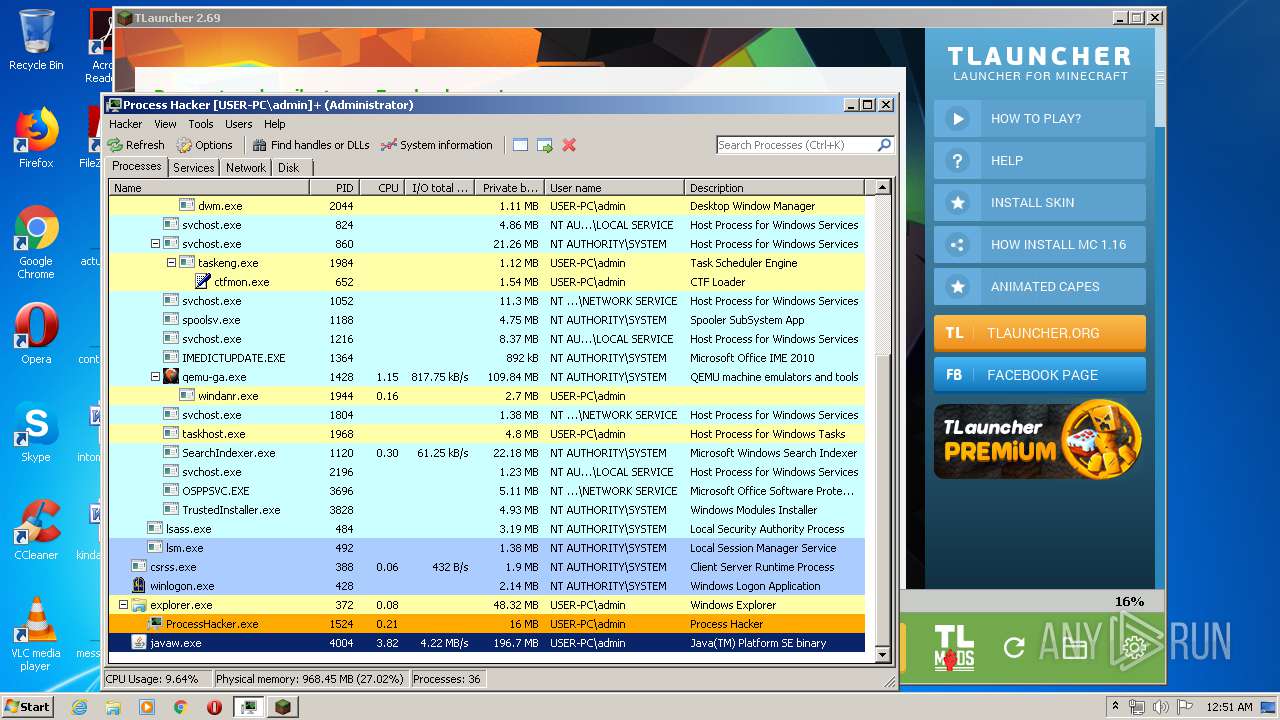
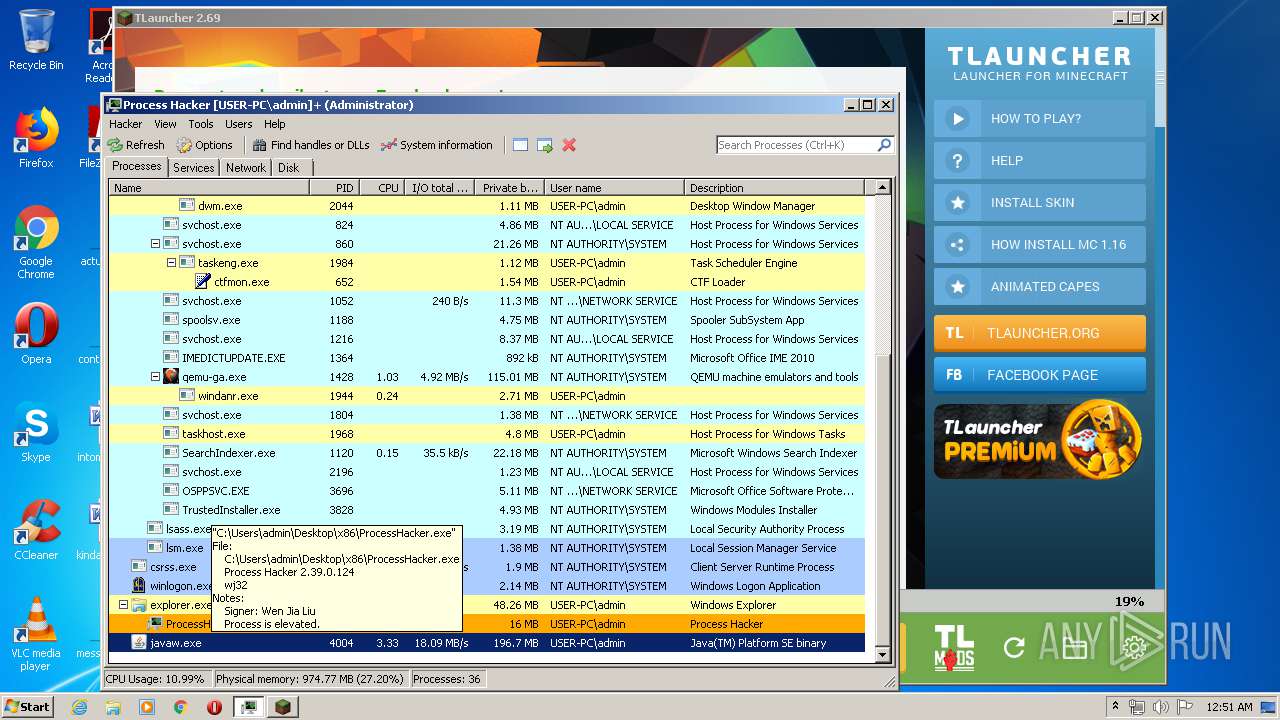
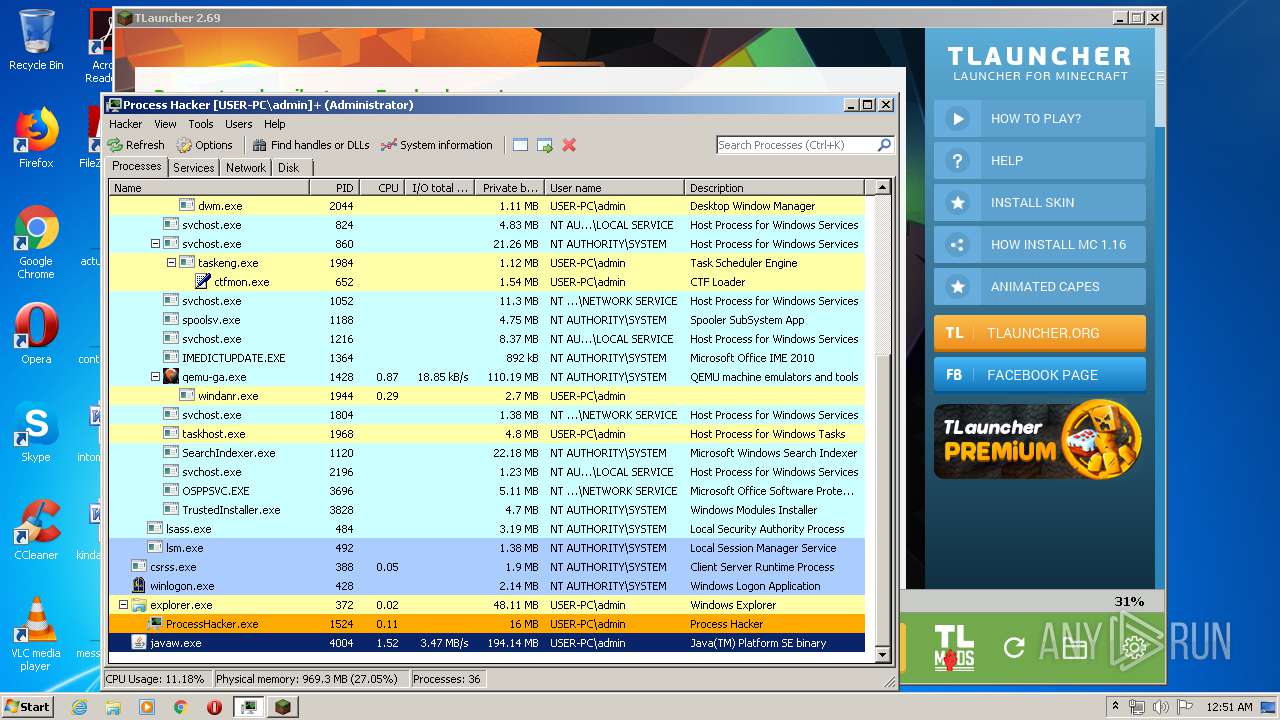
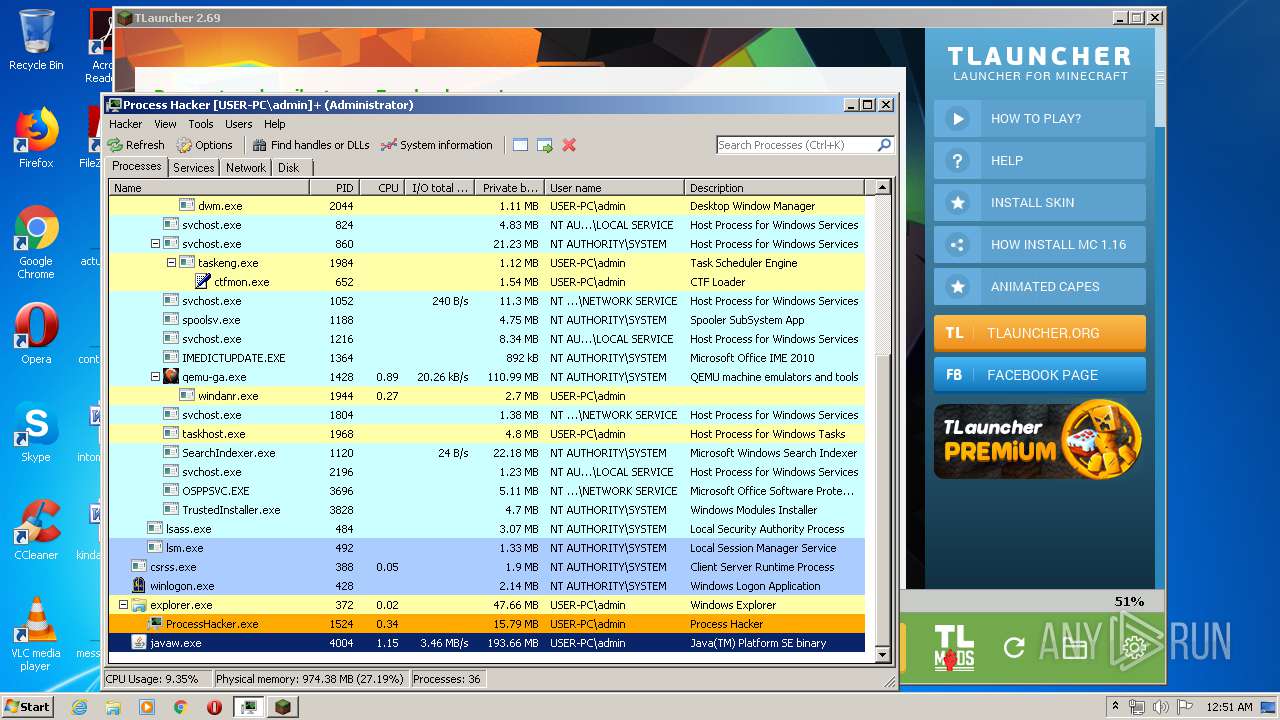
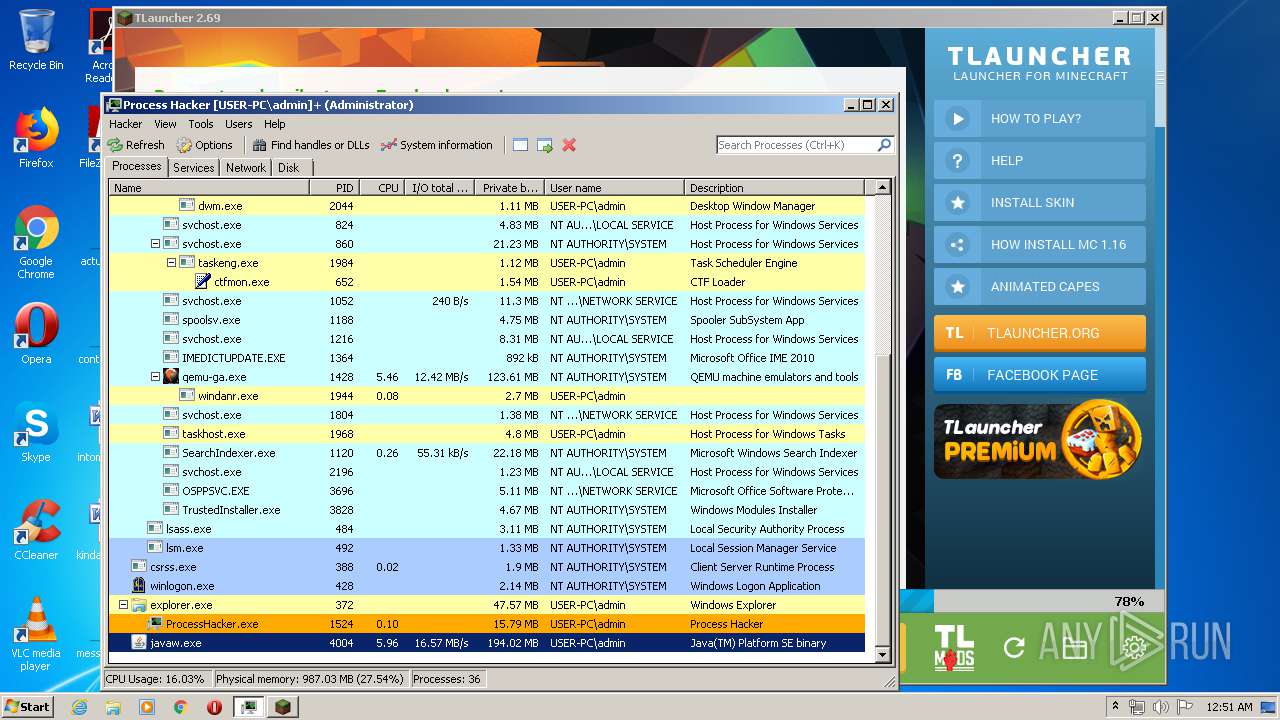
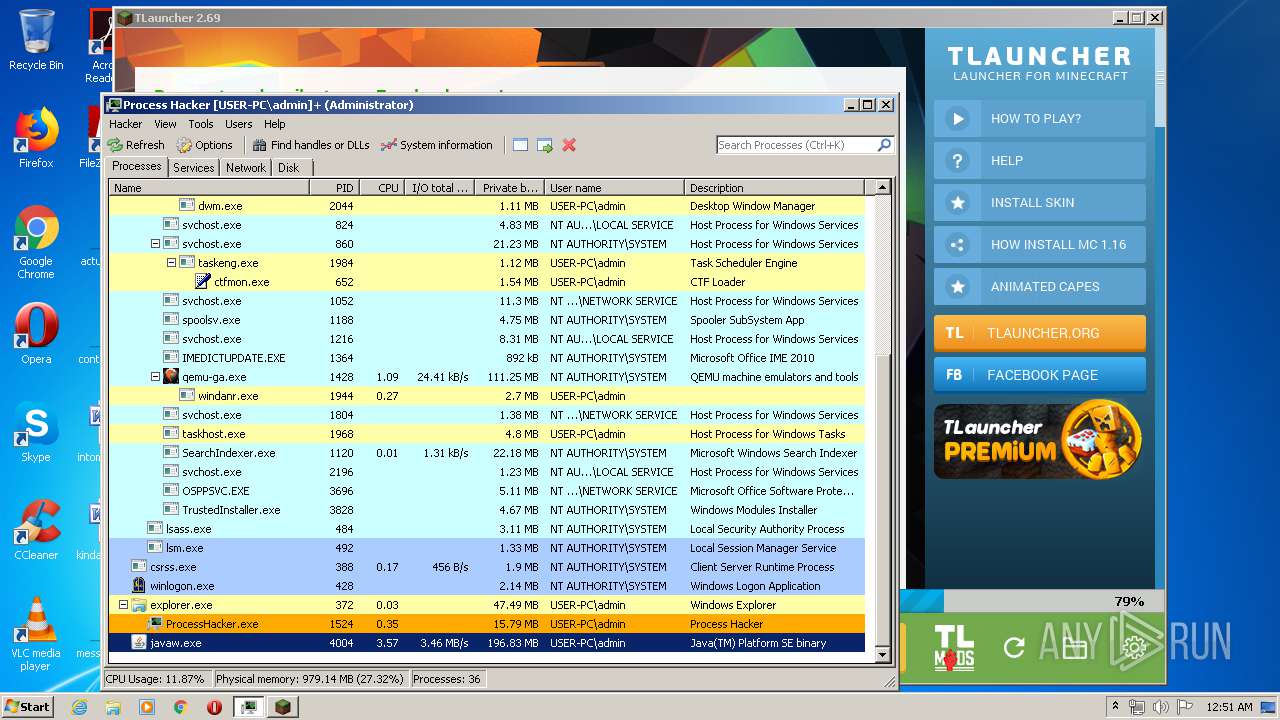
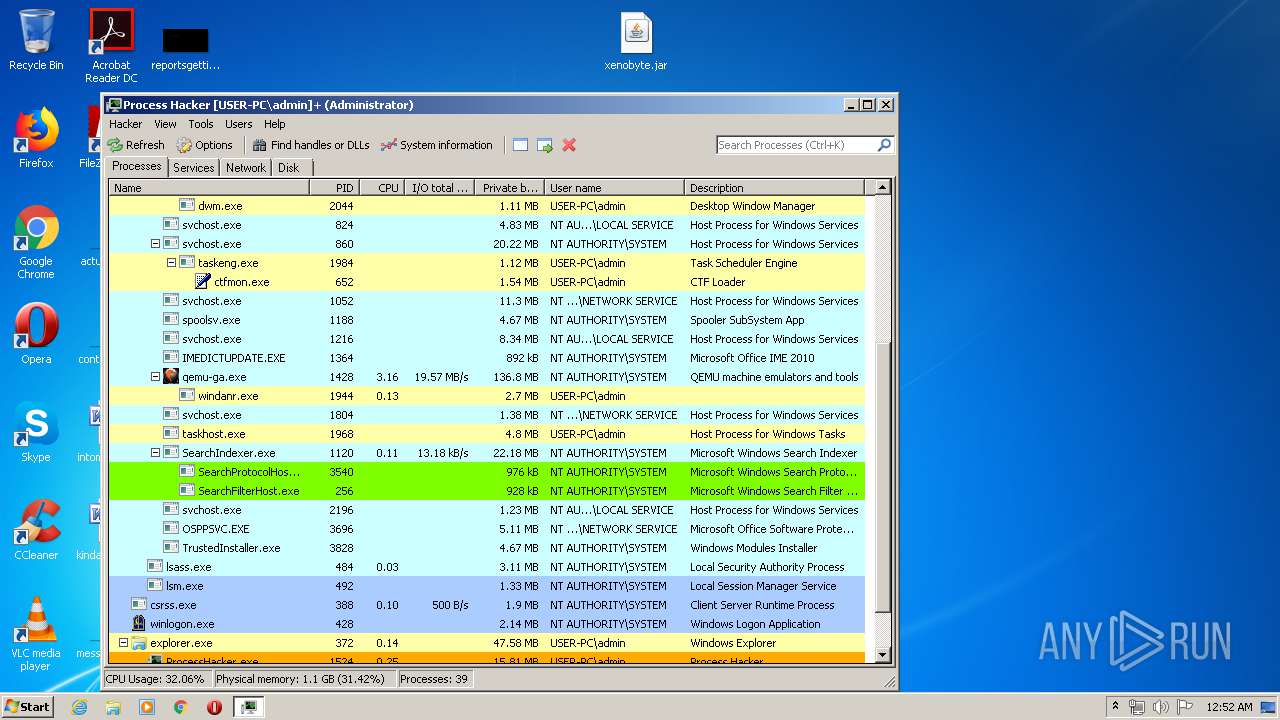
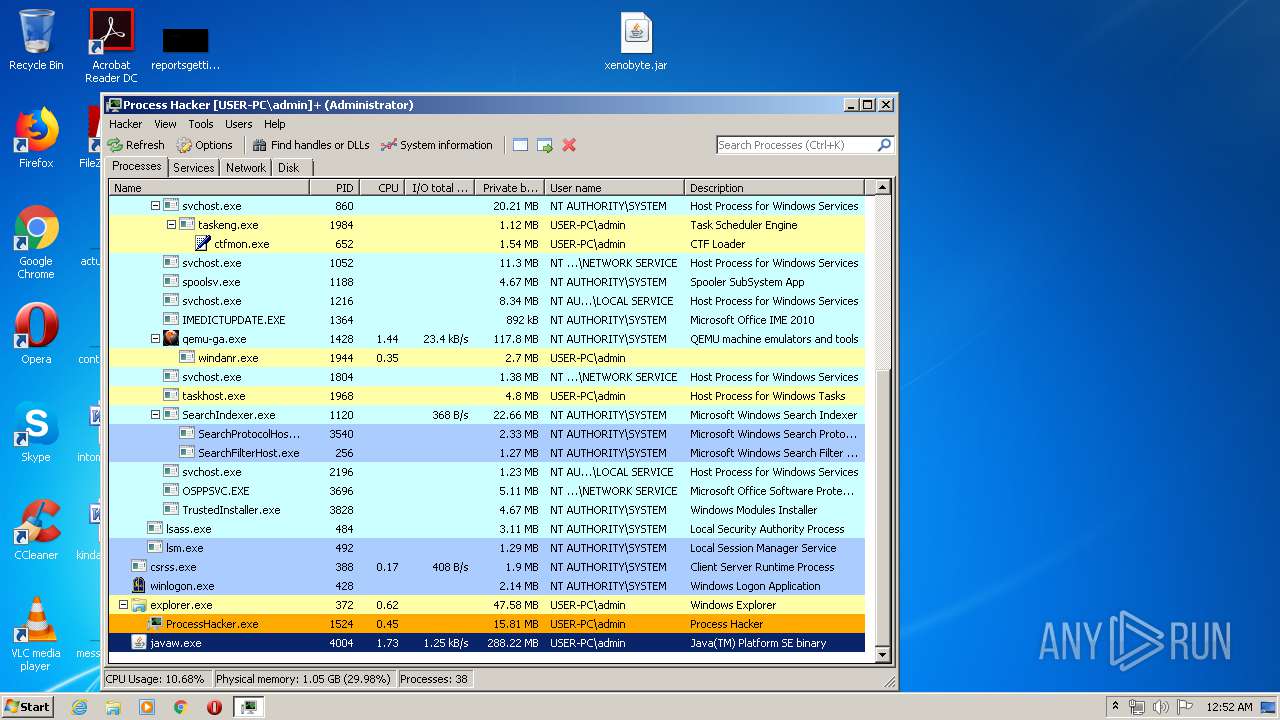
| 1524 | "C:\Users\admin\Desktop\x86\ProcessHacker.exe" | C:\Users\admin\Desktop\x86\ProcessHacker.exe | explorer.exe | ||||||||||||
User: admin Company: wj32 Integrity Level: HIGH Description: Process Hacker Exit code: 0 Version: 2.39.0.124 Modules
| |||||||||||||||
| 1756 | wmic os get osarchitecture | C:\Windows\System32\Wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
5 805
Read events
2 850
Write events
2 931
Delete events
24
Modification events
| (PID) Process: | (3568) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3568) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3568) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3568) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3472) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 3568-13230344925787500 |
Value: 259 | |||
| (PID) Process: | (3568) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3568) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3568) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3568) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3120-13213713943555664 |
Value: 0 | |||
| (PID) Process: | (3568) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
30
Suspicious files
130
Text files
330
Unknown types
587
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3568 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-5E8679DE-DF0.pma | — | |
MD5:— | SHA256:— | |||
| 3568 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3568 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\2dcd16cd-bd89-4694-8b41-dbf3a500e871.tmp | — | |
MD5:— | SHA256:— | |||
| 3568 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000028.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3568 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3568 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3568 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3568 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Last Tabs | binary | |
MD5:— | SHA256:— | |||
| 3568 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3568 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RFa6e3c1.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
772
TCP/UDP connections
125
DNS requests
76
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4004 | javaw.exe | HEAD | 200 | 104.20.50.26:80 | http://page.tlauncher.org/ | US | — | — | malicious |
4004 | javaw.exe | GET | 200 | 104.20.49.26:80 | http://img.tlauncher.org/update/downloads/configs/client/style_new_bes_fontov.css | US | text | 5.76 Kb | malicious |
4004 | javaw.exe | GET | 200 | 104.20.50.26:80 | http://page.tlauncher.org/update/downloads/configs/client/eng.html | US | html | 16.8 Kb | malicious |
3964 | chrome.exe | GET | 302 | 172.217.16.206:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOTRmQUFXVHlhaGJaUTdMLWtCSkNJUl9ZQQ/1.0.0.5_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | html | 519 b | whitelisted |
3964 | chrome.exe | GET | 302 | 172.217.16.206:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOWVmQUFXS041NV9ZVXlJVWwxbGc5TUM4dw/7519.422.0.3_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 524 b | whitelisted |
4004 | javaw.exe | GET | 200 | 104.20.50.26:80 | http://repo.tlauncher.org/update/lch/update_2.0.json?version=2.69&client=ae45734e-0711-46ab-aa73-b479a17346d4 | US | text | 7.69 Kb | whitelisted |
4004 | javaw.exe | GET | 200 | 104.20.50.26:80 | http://repo.tlauncher.org/update/downloads/configs/inner_servers.json | US | text | 3.63 Kb | whitelisted |
4004 | javaw.exe | GET | 200 | 104.20.49.26:80 | http://img.tlauncher.org/update/downloads/configs/client/images/tl-en-pe-news.png | US | image | 132 Kb | malicious |
4004 | javaw.exe | GET | 200 | 104.20.50.26:80 | http://repo.tlauncher.org/update/downloads/libraries/org/tlauncher/authlib/libraries-1.6.json | US | text | 83.1 Kb | whitelisted |
680 | javaw.exe | GET | 200 | 104.20.50.26:80 | http://repo.tlauncher.org/update/downloads/libraries/com/google/guava/guava/19.0/guava-19.0.jar | US | java | 2.20 Mb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3964 | chrome.exe | 172.217.18.3:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
3964 | chrome.exe | 178.154.131.215:443 | yastatic.net | YANDEX LLC | RU | whitelisted |
3964 | chrome.exe | 172.217.16.205:443 | accounts.google.com | Google Inc. | US | whitelisted |
3964 | chrome.exe | 87.250.250.90:443 | an.yandex.ru | YANDEX LLC | RU | whitelisted |
3964 | chrome.exe | 77.88.55.55:443 | yandex.ru | YANDEX LLC | RU | whitelisted |
3964 | chrome.exe | 87.250.250.114:443 | ysa-static.passport.yandex.ru | YANDEX LLC | RU | whitelisted |
3964 | chrome.exe | 87.250.250.50:443 | yadi.sk | YANDEX LLC | RU | whitelisted |
3964 | chrome.exe | 87.250.247.183:443 | avatars.mds.yandex.net | YANDEX LLC | RU | whitelisted |
3964 | chrome.exe | 212.11.152.206:443 | stats.mos.ru | Moscow Mayor's Office | RU | unknown |
3964 | chrome.exe | 81.222.128.215:443 | ssp.adriver.ru | PVimpelCom | RU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
yadi.sk |
| shared |
accounts.google.com |
| shared |
yastatic.net |
| whitelisted |
mc.yandex.ru |
| whitelisted |
disk.yandex.fr |
| shared |
disk.yandex.com |
| shared |
disk.yandex.ru |
| shared |
safebrowsing.googleapis.com |
| whitelisted |
an.yandex.ru |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
680 | javaw.exe | A Network Trojan was detected | ET INFO JAVA - Java Archive Download |
680 | javaw.exe | A Network Trojan was detected | ET INFO JAVA - Java Archive Download |
680 | javaw.exe | A Network Trojan was detected | ET INFO JAVA - Java Archive Download |
680 | javaw.exe | Potentially Bad Traffic | ET INFO JAR Size Under 30K Size - Potentially Hostile |