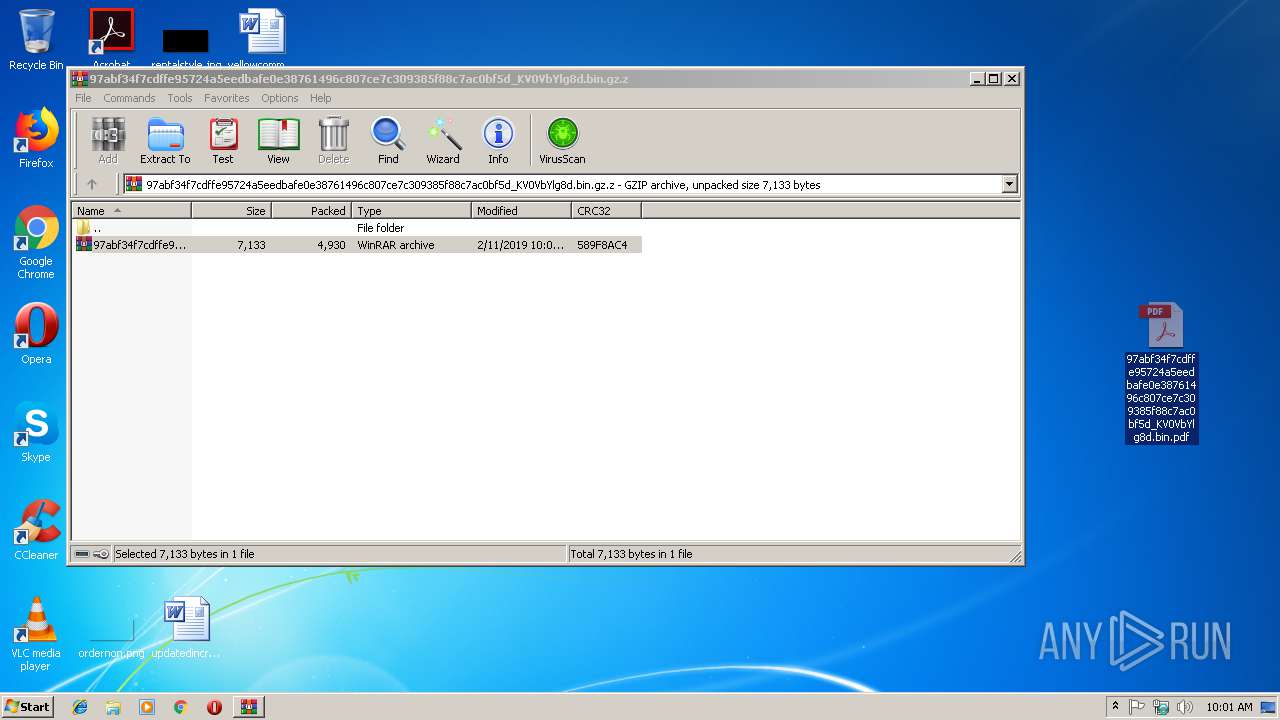
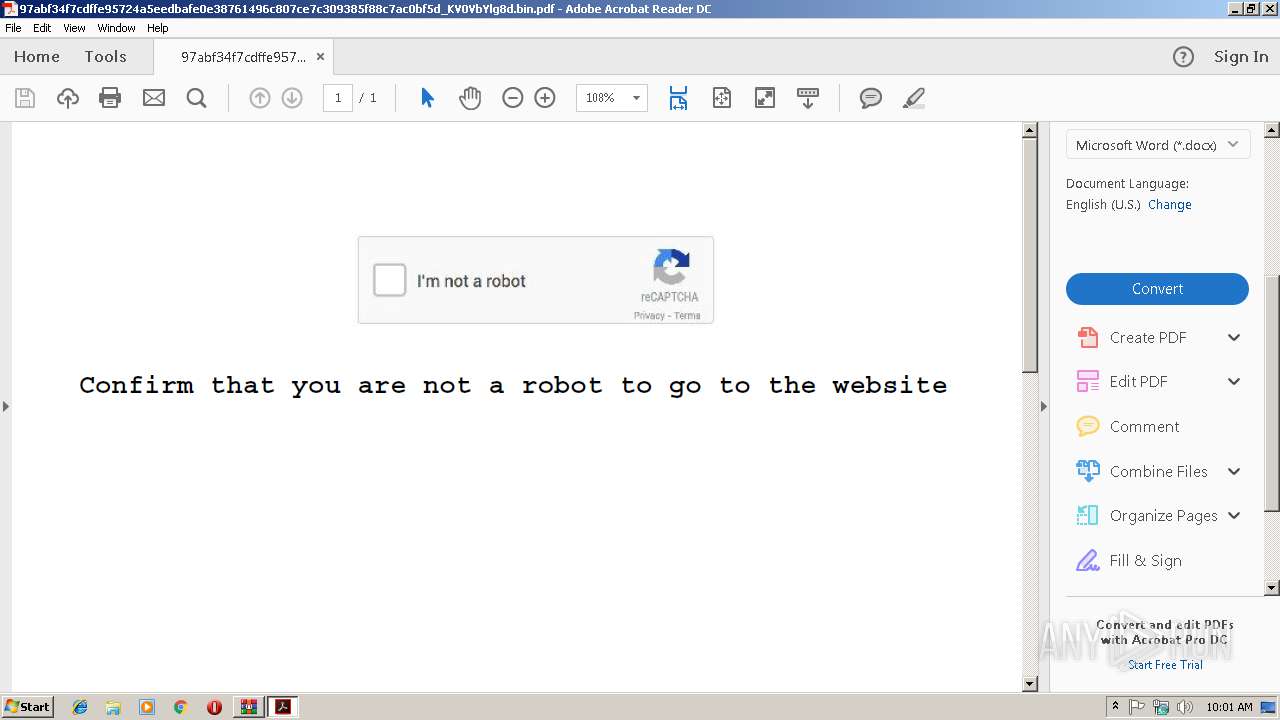
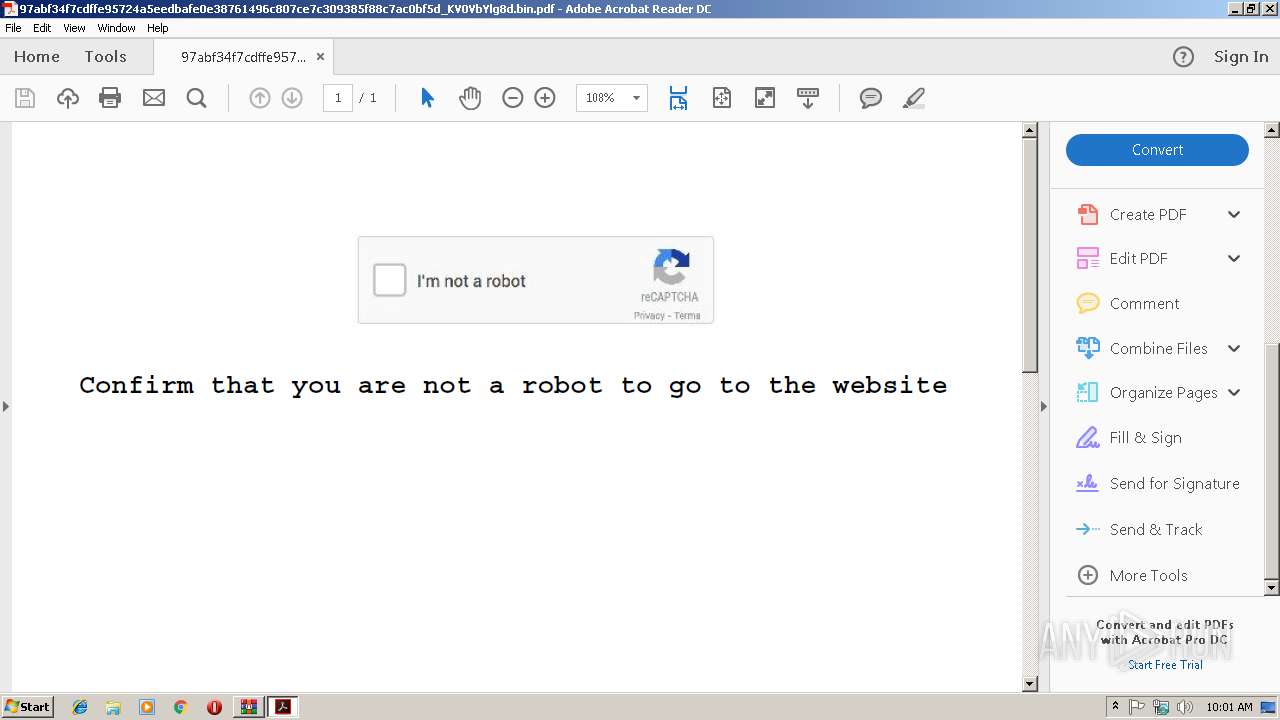
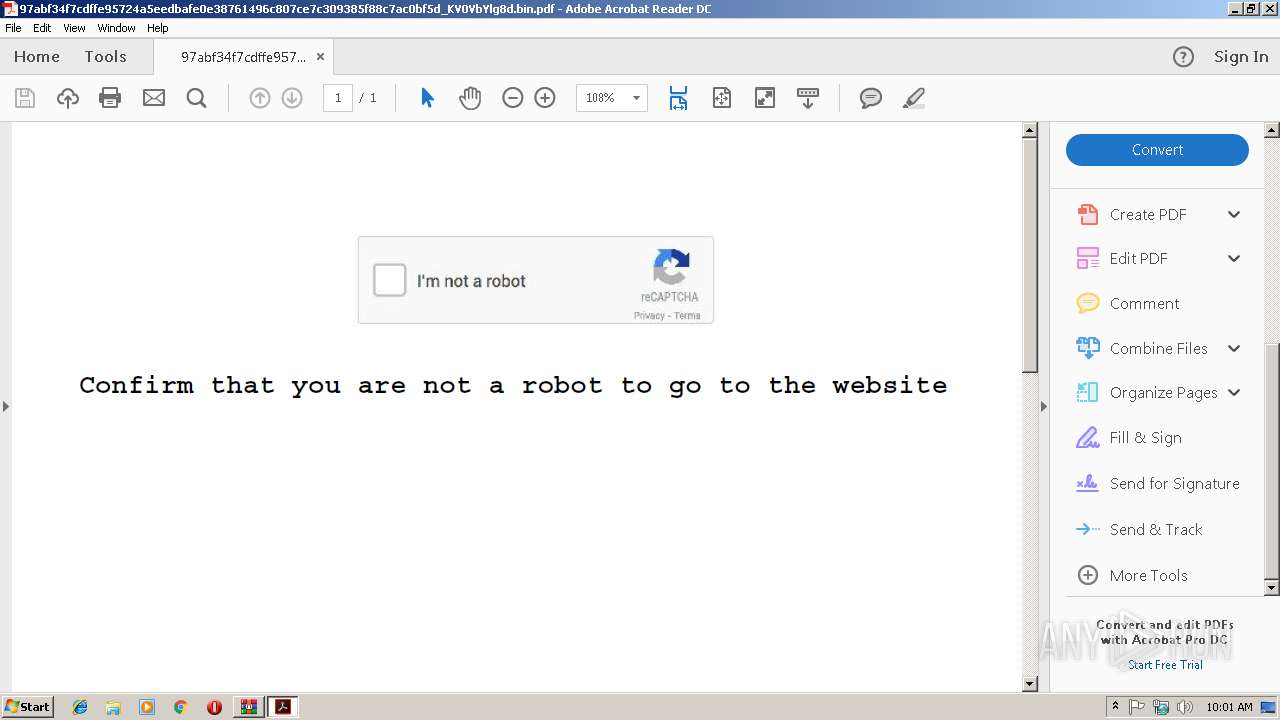
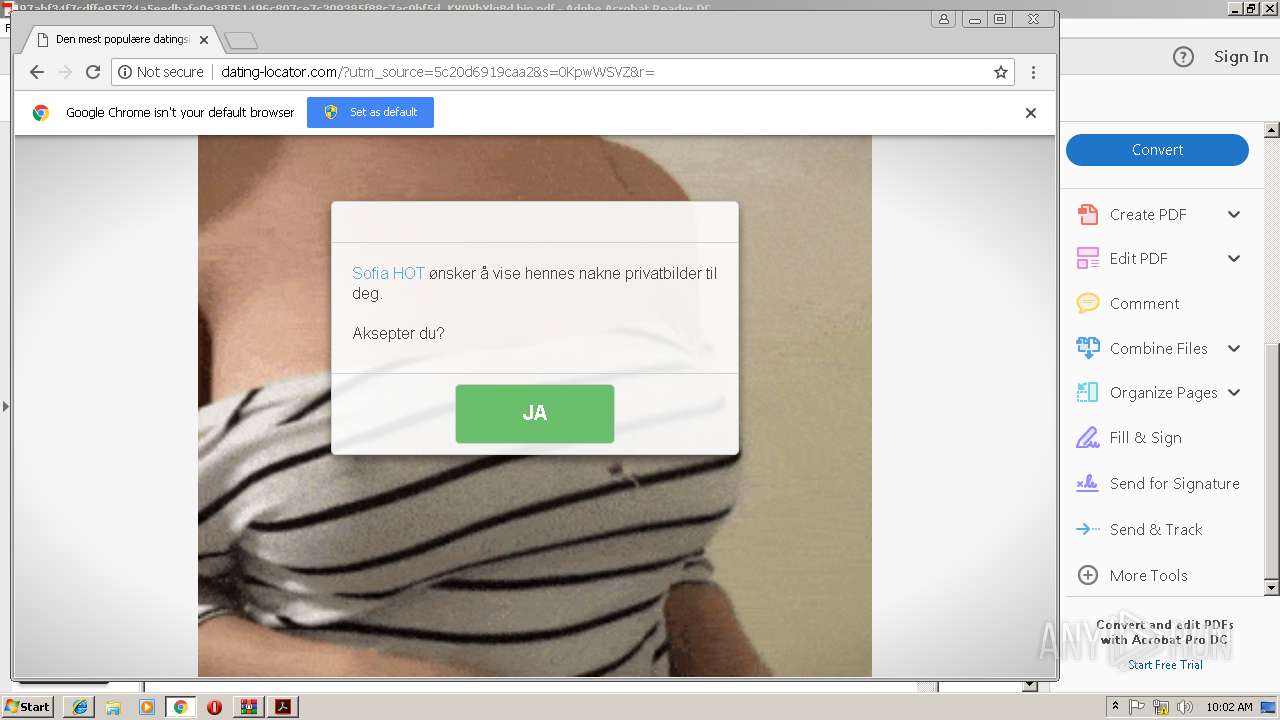
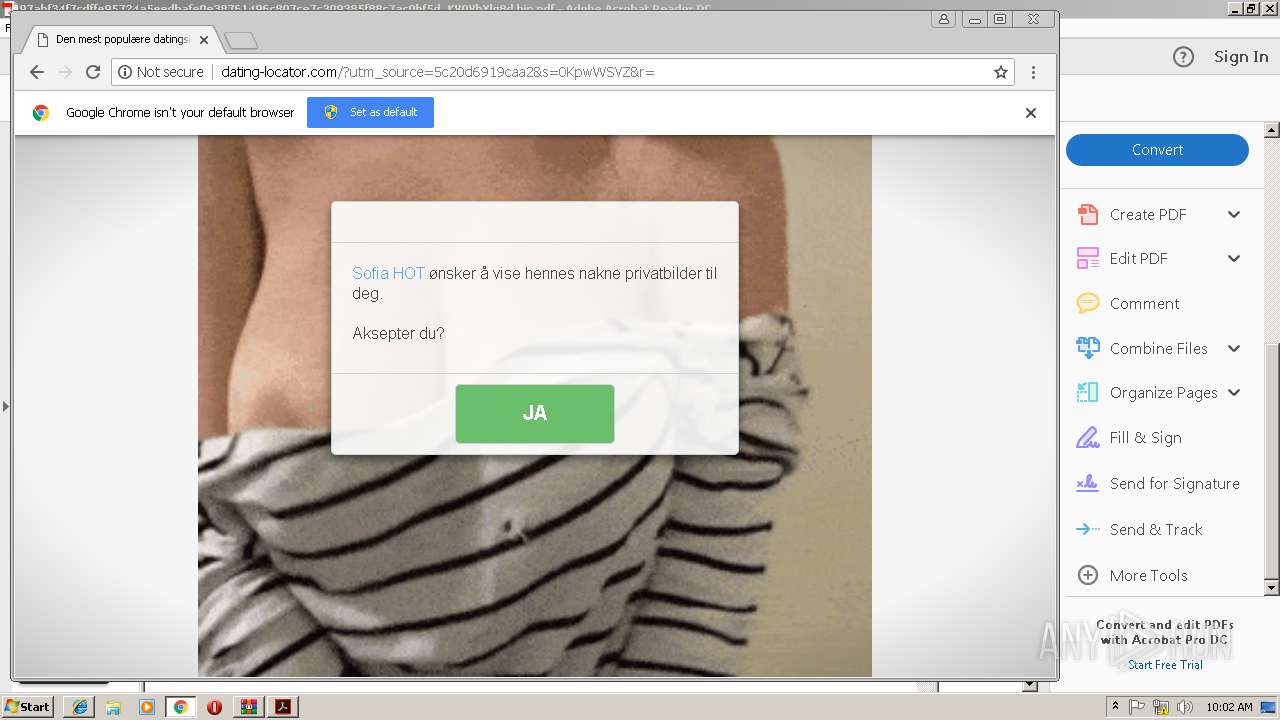
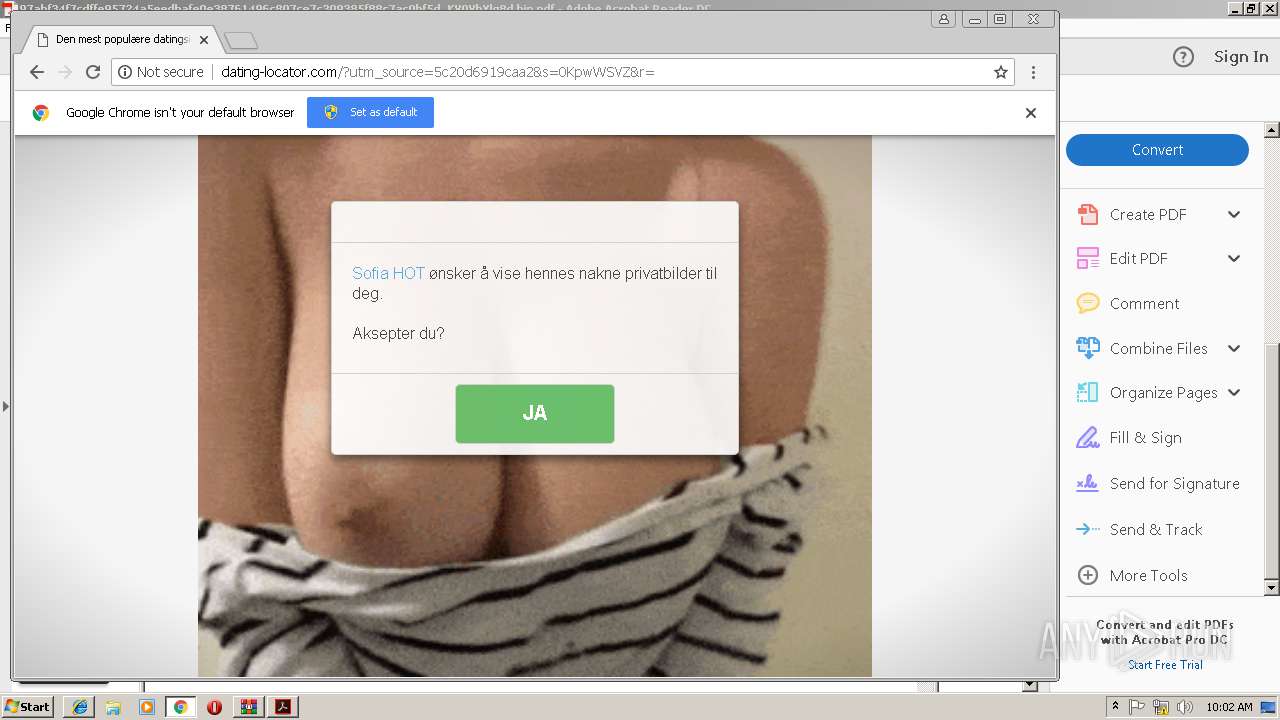
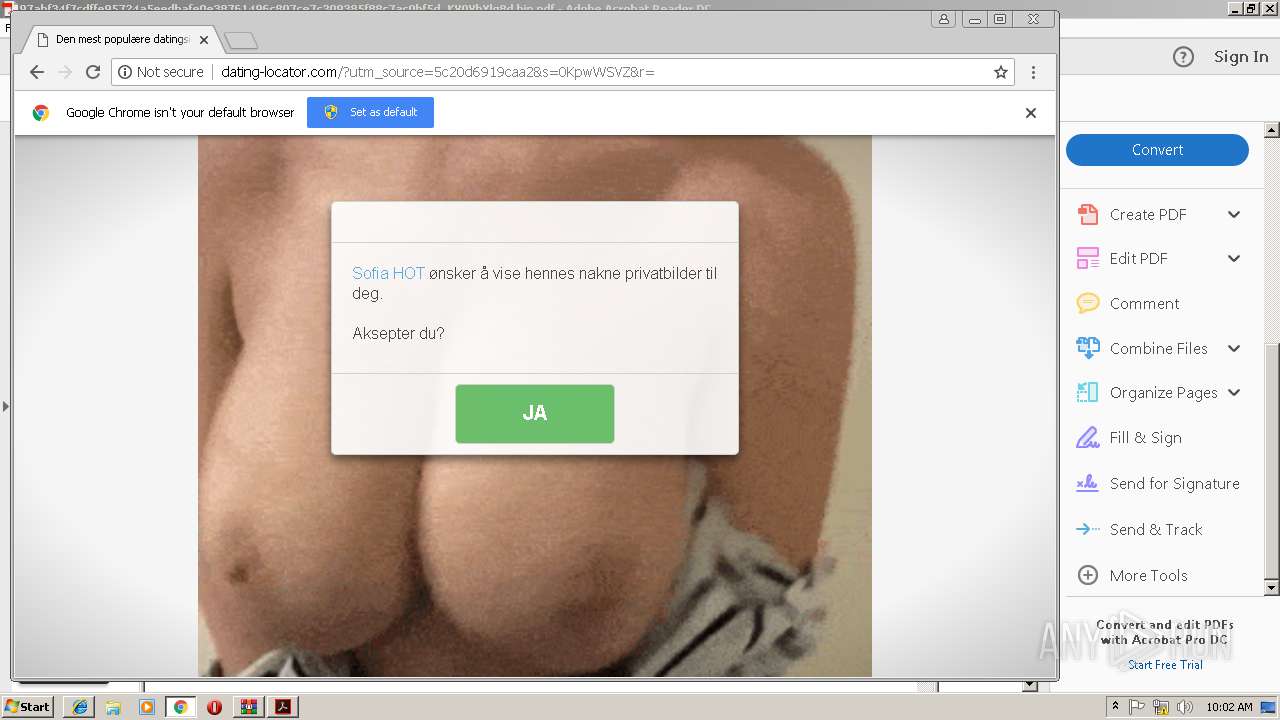
| File name: | 97abf34f7cdffe95724a5eedbafe0e38761496c807ce7c309385f88c7ac0bf5d_KV0VbYlg8d.bin.gz |
| Full analysis: | https://app.any.run/tasks/d2163532-9e6c-4f51-9dbc-071ffd2ae60e |
| Verdict: | Malicious activity |
| Analysis date: | February 11, 2019, 10:00:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/gzip |
| File info: | gzip compressed data, max compression, from Unix |
| MD5: | CEB84C5ABB70DE6266F402F024B9472E |
| SHA1: | BC8B7BED7809DE339EFF54945B676A9069C145ED |
| SHA256: | D152DEBABE6CC8C217835EC4EE6FB390941DE57603308751407C0A900AC914F2 |
| SSDEEP: | 96:3T63CssfmY6D7CM7cHGJNxKqnB3SdbYQEzC8R5OxzuN/XMCn53SOi8C5YyPs7:j6yUHD7CM7PriWoS5OtuN/XZ53LPhX7 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts Internet Explorer
- AcroRd32.exe (PID: 312)
Creates files in the program directory
- AdobeARM.exe (PID: 3500)
INFO
Application launched itself
- RdrCEF.exe (PID: 2260)
- chrome.exe (PID: 1396)
Creates files in the user directory
- AcroRd32.exe (PID: 312)
- iexplore.exe (PID: 3576)
Reads settings of System Certificates
- chrome.exe (PID: 1396)
Reads Internet Cache Settings
- iexplore.exe (PID: 3576)
Changes internet zones settings
- iexplore.exe (PID: 2892)
Reads internet explorer settings
- iexplore.exe (PID: 3576)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .z/gz/gzip | | | GZipped data (100) |
|---|
EXIF
ZIP
| Compression: | Deflated |
|---|---|
| Flags: | (none) |
| ModifyDate: | 0000:00:00 00:00:00 |
| ExtraFlags: | Maximum Compression |
| OperatingSystem: | Unix |
Total processes
51
Monitored processes
18
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
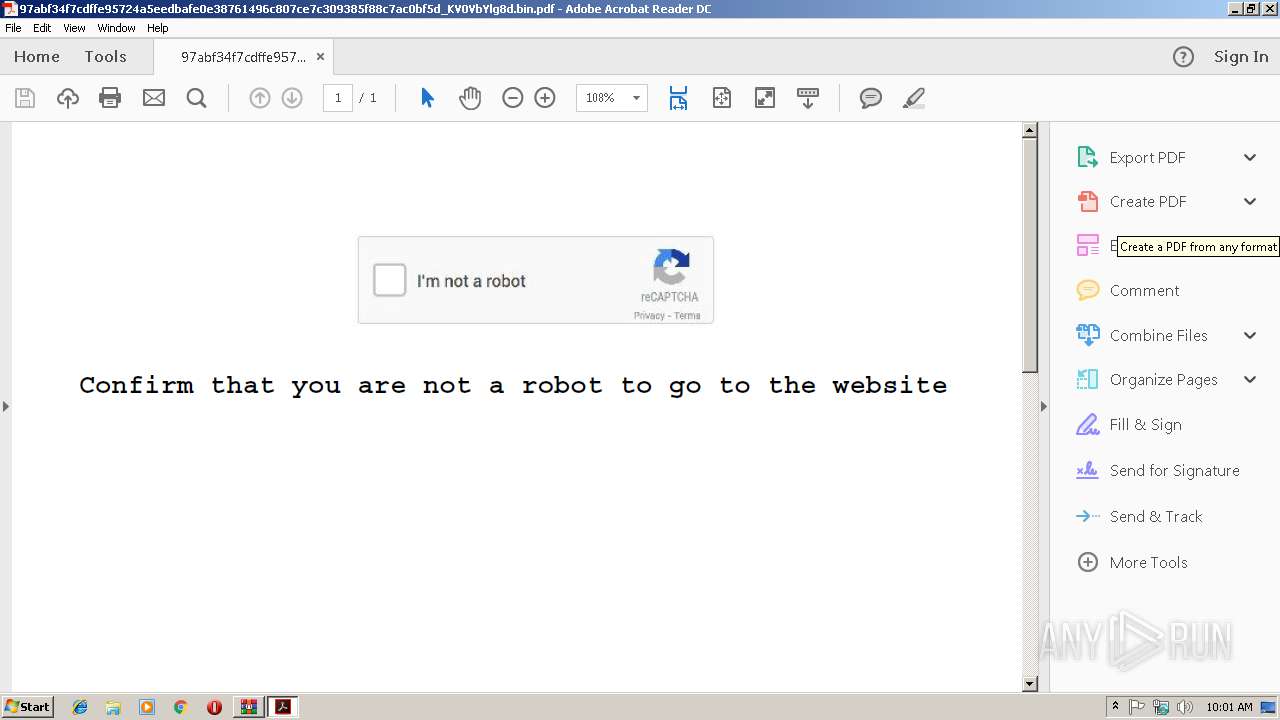
| 312 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" "C:\Users\admin\Desktop\97abf34f7cdffe95724a5eedbafe0e38761496c807ce7c309385f88c7ac0bf5d_KV0VbYlg8d.bin.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | explorer.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 0 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 340 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=68.0.3440.106 --initial-client-data=0x78,0x7c,0x80,0x74,0x84,0x6a4a00b0,0x6a4a00c0,0x6a4a00cc | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 992 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-direct-npapi-requests --disable-file-system --disable-notifications --disable-shared-workers --disable-direct-write --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.23.20053 Chrome/45.0.2454.85" --device-scale-factor=1 --enable-delegated-renderer --num-raster-threads=2 --gpu-rasterization-msaa-sample-count=8 --content-image-texture-target=3553 --video-image-texture-target=3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --channel="2260.1.1952725469\1440199978" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 1396 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2260 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --backgroundcolor=16448250 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 2308 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=956,14494040292142035522,12914418376964286807,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=B0180116E823A306F084B5765754116A --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=B0180116E823A306F084B5765754116A --renderer-client-id=6 --mojo-platform-channel-handle=3524 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2412 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=956,14494040292142035522,12914418376964286807,131072 --enable-features=PasswordImport --service-pipe-token=D7D64A1133672C09B9FB299DD69E821D --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=D7D64A1133672C09B9FB299DD69E821D --renderer-client-id=3 --mojo-platform-channel-handle=2084 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2748 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-direct-npapi-requests --disable-file-system --disable-notifications --disable-shared-workers --disable-direct-write --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.23.20053 Chrome/45.0.2454.85" --device-scale-factor=1 --enable-delegated-renderer --num-raster-threads=2 --gpu-rasterization-msaa-sample-count=8 --content-image-texture-target=3553 --video-image-texture-target=3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --channel="2260.0.807887772\1985370456" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 2884 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\Reader_sl.exe" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\Reader_sl.exe | — | AdobeARM.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat SpeedLauncher Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 2892 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | AcroRd32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 027
Read events
884
Write events
139
Delete events
4
Modification events
| (PID) Process: | (2968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2968) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\97abf34f7cdffe95724a5eedbafe0e38761496c807ce7c309385f88c7ac0bf5d_KV0VbYlg8d.bin.gz.z | |||
| (PID) Process: | (2968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3580) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
| (PID) Process: | (3580) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral |
| Operation: | write | Name: | bExpandRHPInViewer |
Value: 1 | |||
Executable files
0
Suspicious files
38
Text files
69
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3580 | AcroRd32.exe | C:\Users\admin\AppData\LocalLow\Adobe\Acrobat\DC\ReaderMessages-journal | — | |
MD5:— | SHA256:— | |||
| 3580 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9R1oimmt4_1801chq_2rg.tmp | — | |
MD5:— | SHA256:— | |||
| 3580 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9R1t8kbej_1801chr_2rg.tmp | — | |
MD5:— | SHA256:— | |||
| 3580 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9Rs9cnef_1801chs_2rg.tmp | — | |
MD5:— | SHA256:— | |||
| 3580 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9R2syt6w_1801cht_2rg.tmp | — | |
MD5:— | SHA256:— | |||
| 3580 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9R1xmtj9m_1801chu_2rg.tmp | — | |
MD5:— | SHA256:— | |||
| 2892 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2892 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3576 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@top.nov[1].txt | — | |
MD5:— | SHA256:— | |||
| 3576 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\ffehg_date-locator_com[1].txt | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
22
TCP/UDP connections
29
DNS requests
18
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3576 | iexplore.exe | GET | 302 | 91.215.153.90:80 | http://top.nov.ru/M9ccWt | BG | — | — | suspicious |
312 | AcroRd32.exe | GET | 304 | 2.16.186.33:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/278_15_23_20070.zip | unknown | — | — | whitelisted |
312 | AcroRd32.exe | GET | 304 | 2.16.186.33:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/280_15_23_20070.zip | unknown | — | — | whitelisted |
312 | AcroRd32.exe | GET | 304 | 2.16.186.33:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/277_15_23_20070.zip | unknown | — | — | whitelisted |
312 | AcroRd32.exe | GET | 304 | 2.16.186.33:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/message.zip | unknown | — | — | whitelisted |
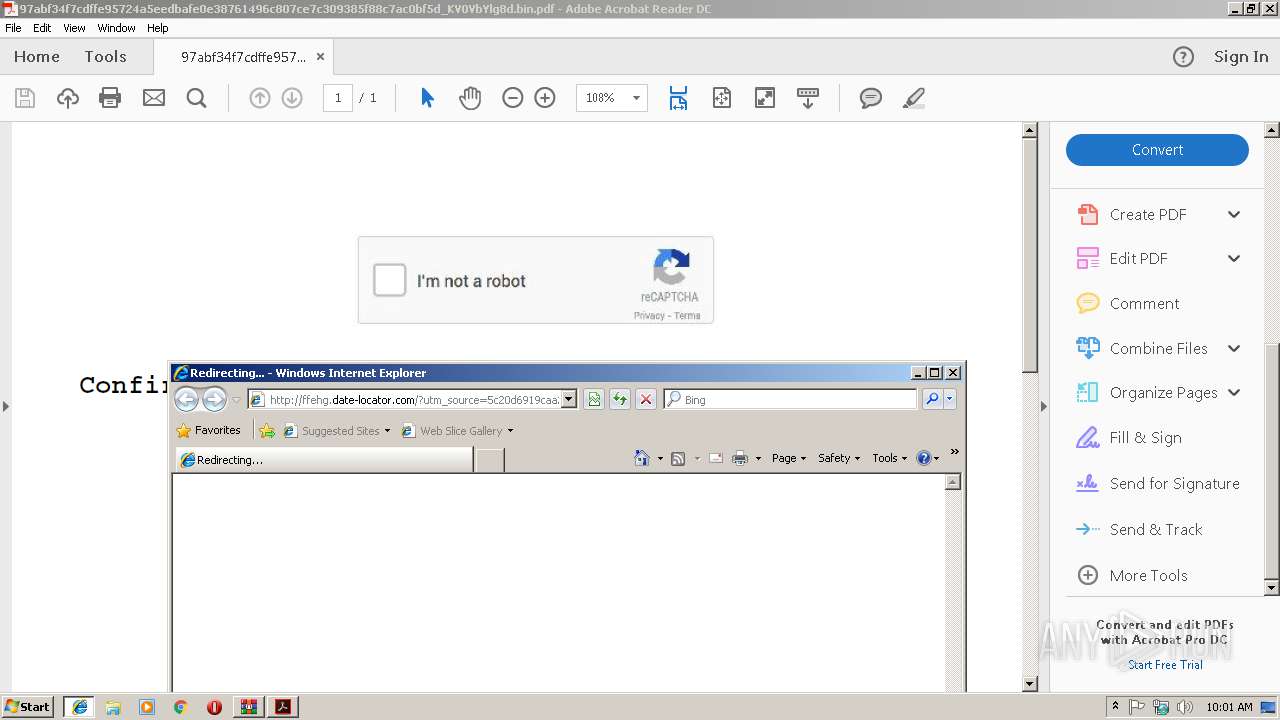
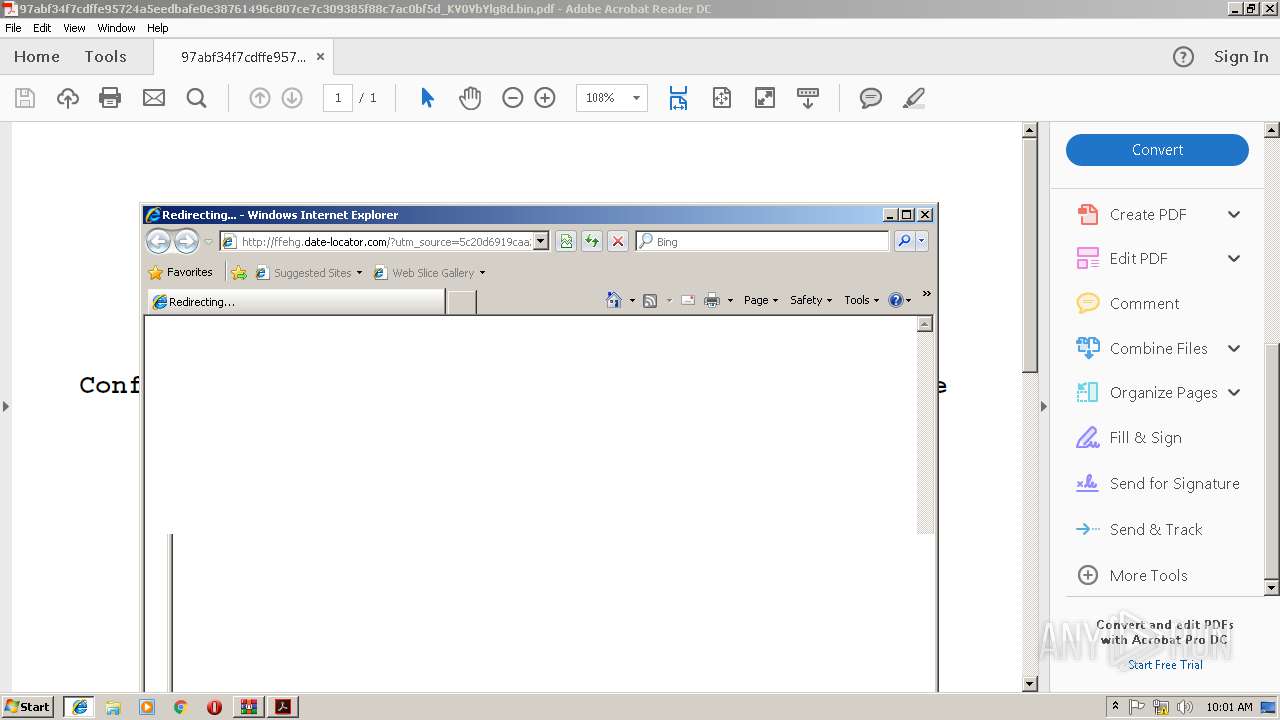
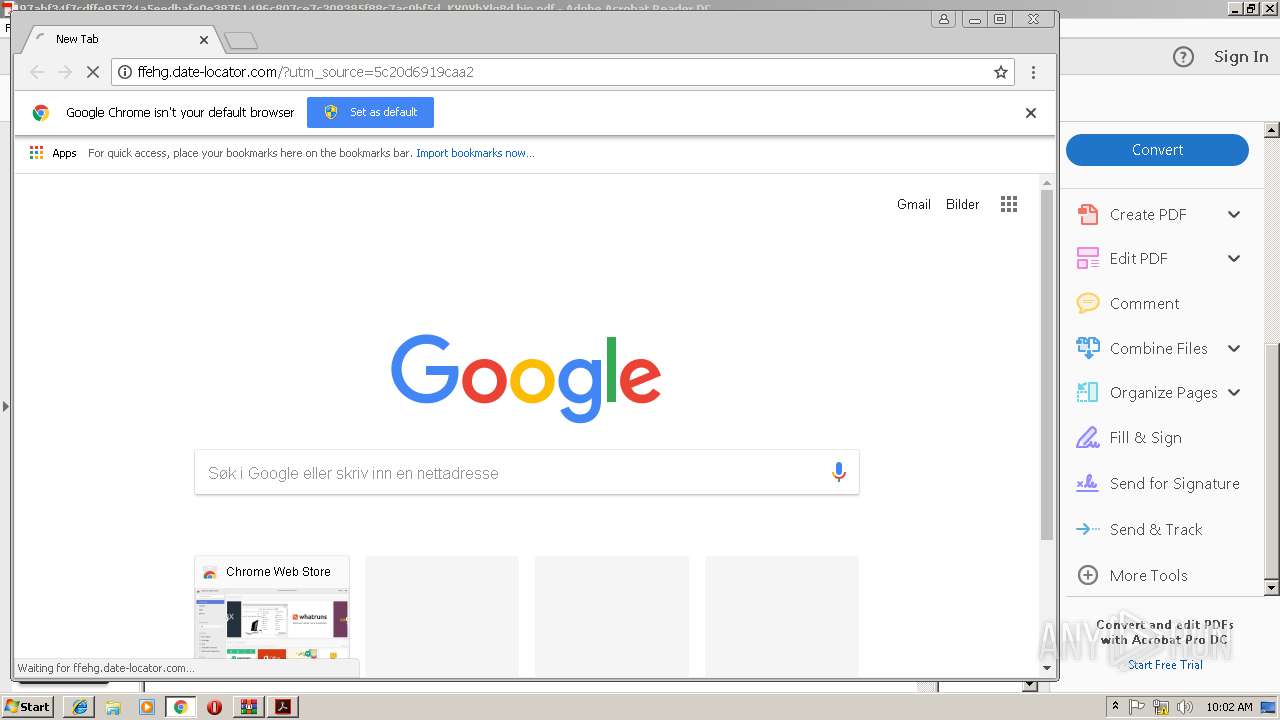
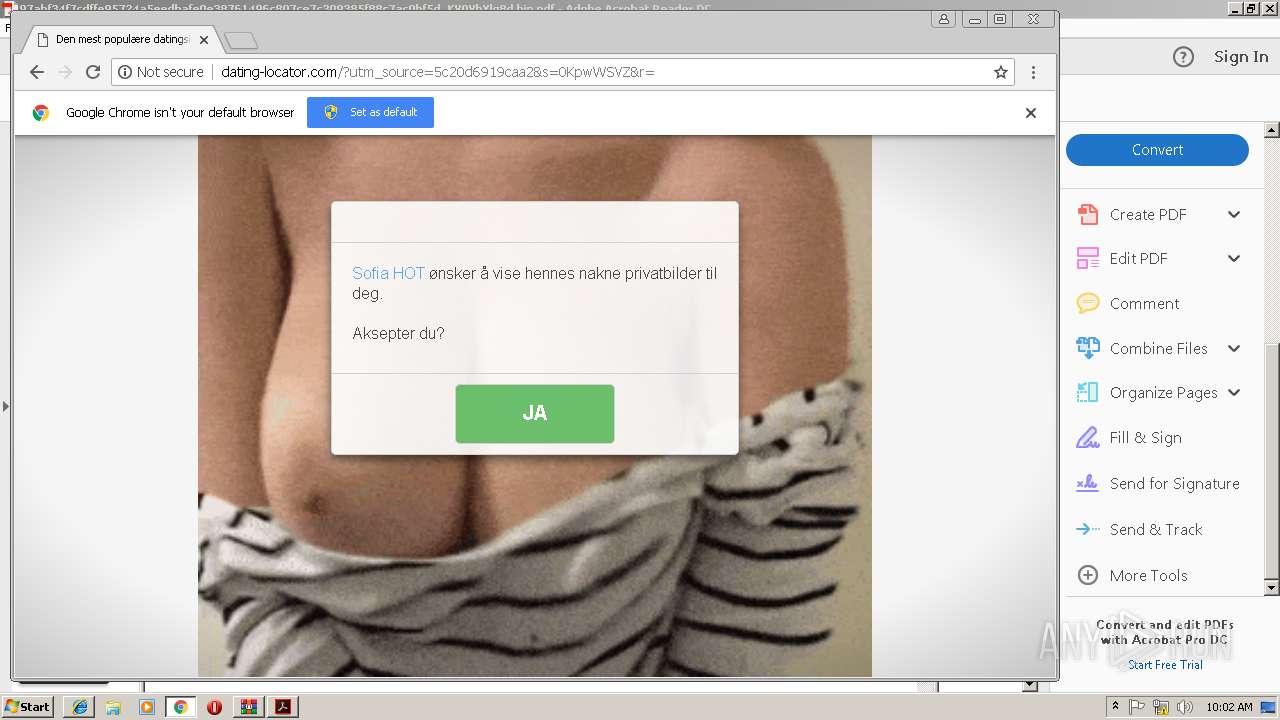
3576 | iexplore.exe | GET | 200 | 95.213.251.197:80 | http://ffehg.date-locator.com/?utm_source=5c20d6919caa2 | RU | html | 867 b | malicious |
1396 | chrome.exe | GET | 200 | 31.184.255.77:80 | http://ffehg.date-locator.com/?utm_source=5c20d6919caa2 | RU | html | 867 b | malicious |
2892 | iexplore.exe | GET | 404 | 95.213.251.197:80 | http://ffehg.date-locator.com/favicon.ico | RU | html | 245 b | malicious |
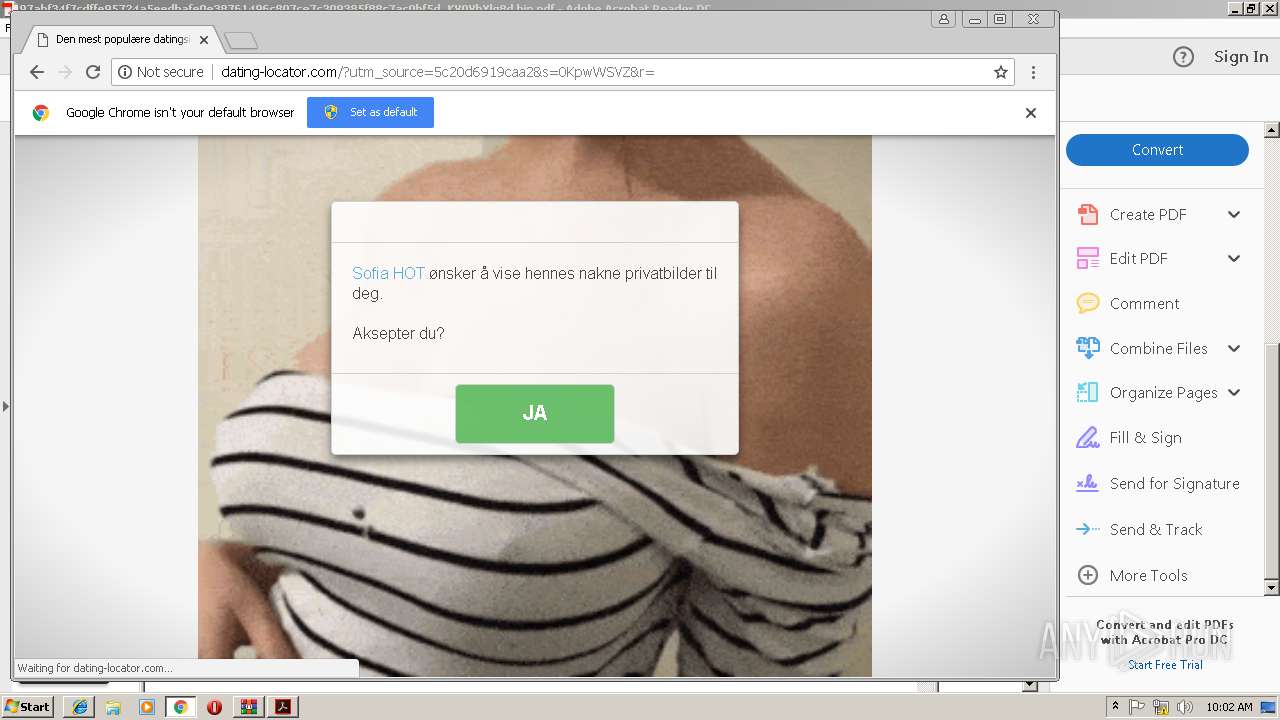
1396 | chrome.exe | GET | 200 | 95.213.251.197:80 | http://dating-locator.com/bundle/101/assets/css/back.css | RU | text | 99 b | malicious |
1396 | chrome.exe | GET | 200 | 95.213.251.197:80 | http://dating-locator.com/bundle/101/assets/css/css.css | RU | text | 270 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
312 | AcroRd32.exe | 2.18.233.74:443 | armmf.adobe.com | Akamai International B.V. | — | whitelisted |
312 | AcroRd32.exe | 2.16.186.33:80 | acroipm2.adobe.com | Akamai International B.V. | — | whitelisted |
3576 | iexplore.exe | 91.215.153.90:80 | top.nov.ru | ITL Company | BG | suspicious |
2892 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3576 | iexplore.exe | 95.213.251.197:80 | ffehg.date-locator.com | OOO Network of data-centers Selectel | RU | unknown |
2892 | iexplore.exe | 95.213.251.197:80 | ffehg.date-locator.com | OOO Network of data-centers Selectel | RU | unknown |
— | — | 2.18.233.74:443 | armmf.adobe.com | Akamai International B.V. | — | whitelisted |
— | — | 23.210.248.251:443 | ardownload2.adobe.com | Akamai International B.V. | NL | whitelisted |
1396 | chrome.exe | 216.58.205.227:443 | www.google.de | Google Inc. | US | whitelisted |
1396 | chrome.exe | 216.58.208.35:443 | www.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
acroipm2.adobe.com |
| whitelisted |
armmf.adobe.com |
| whitelisted |
www.bing.com |
| whitelisted |
top.nov.ru |
| suspicious |
ffehg.date-locator.com |
| malicious |
ardownload2.adobe.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
www.google.de |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3576 | iexplore.exe | Potentially Bad Traffic | ET CURRENT_EVENTS Possible Keitaro TDS Redirect |
1396 | chrome.exe | Misc activity | SUSPICIOUS [PTsecurity] JS obfuscation (obfuscator.io) |
1396 | chrome.exe | Misc activity | SUSPICIOUS [PTsecurity] Redirection JScript Obfuscated (seen Banload) |