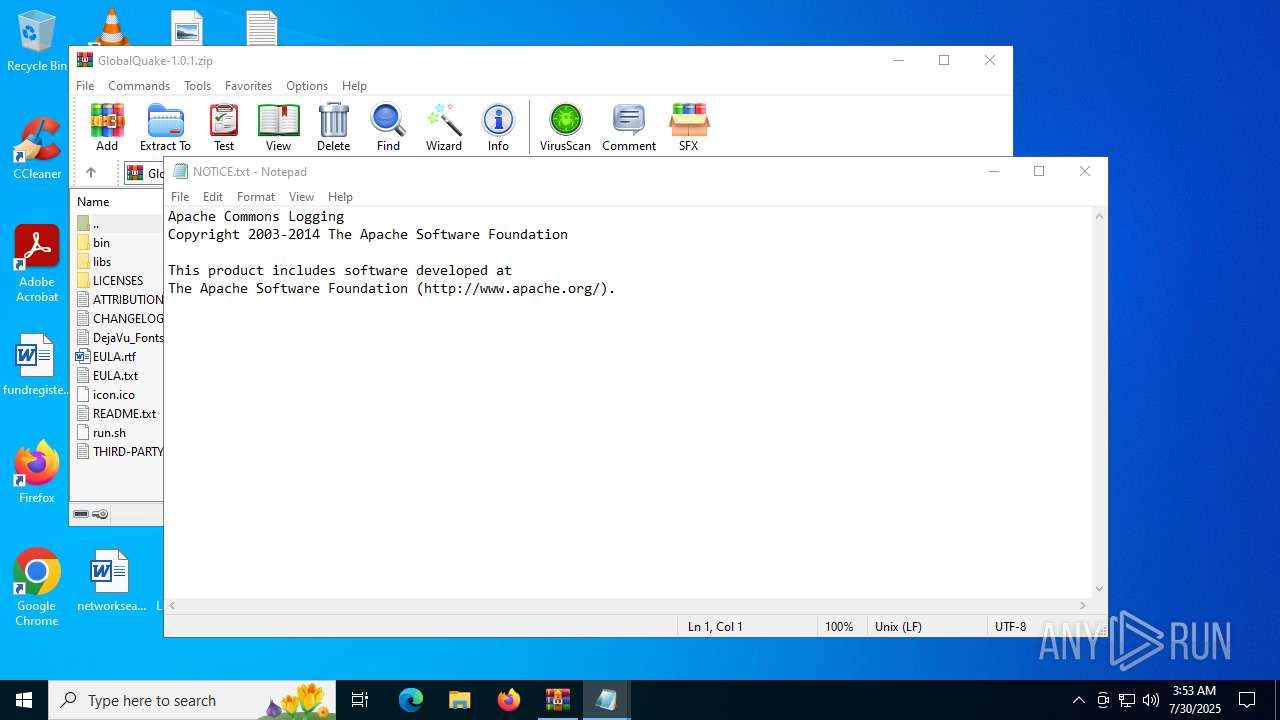
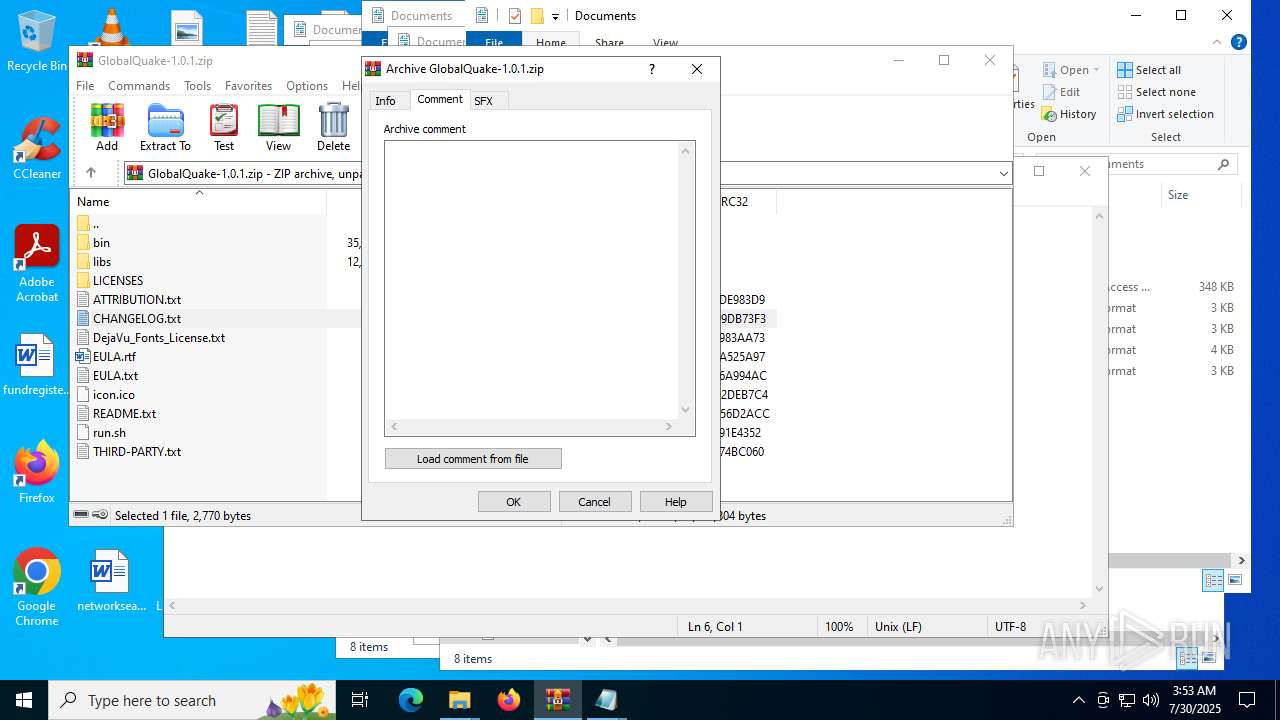
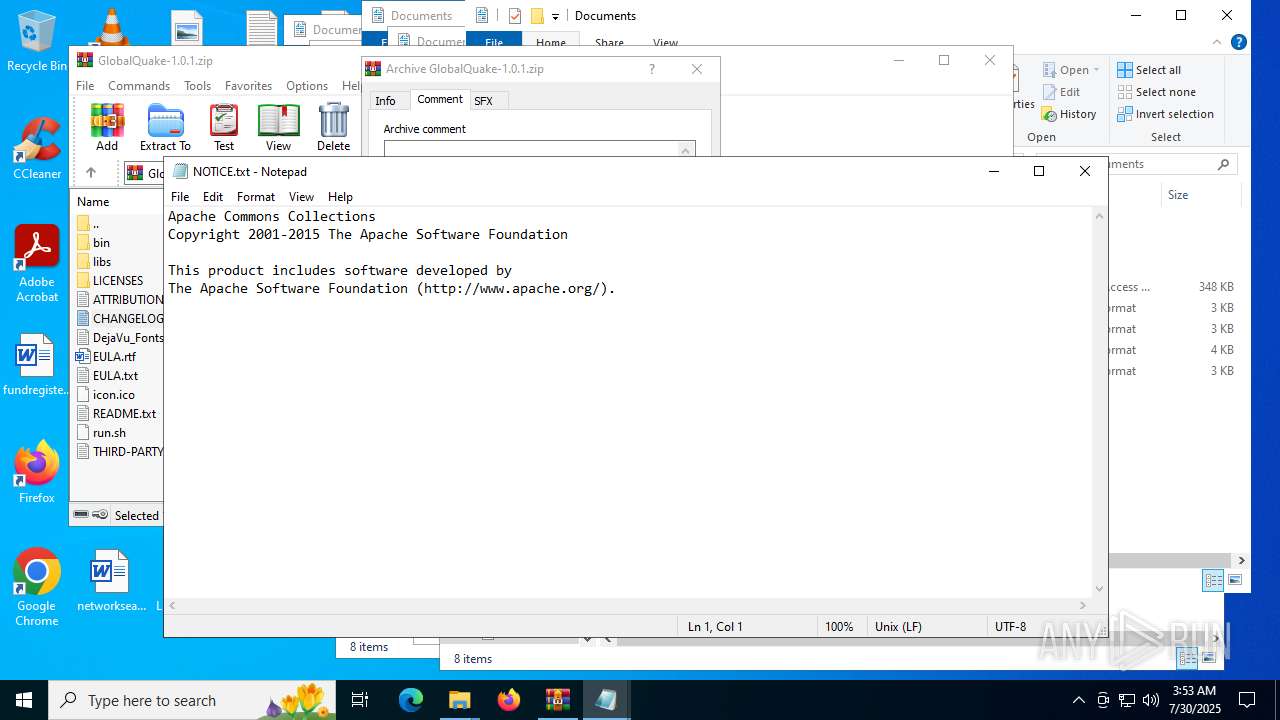
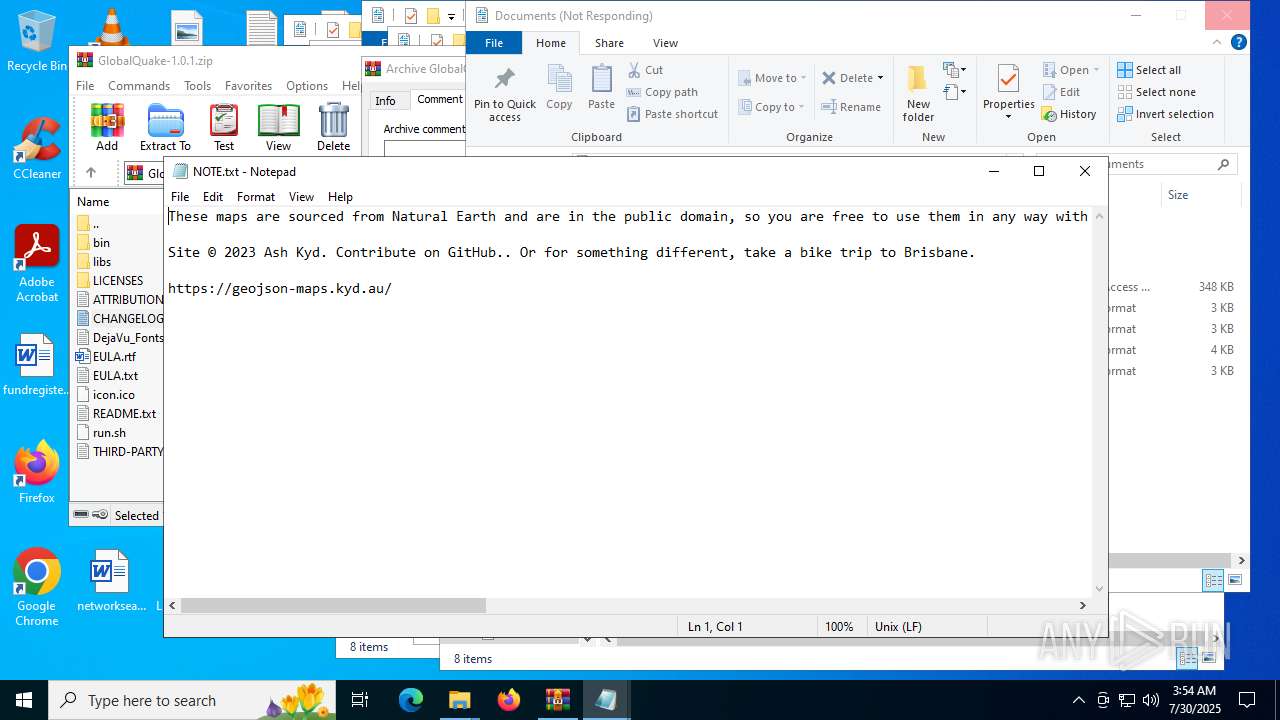
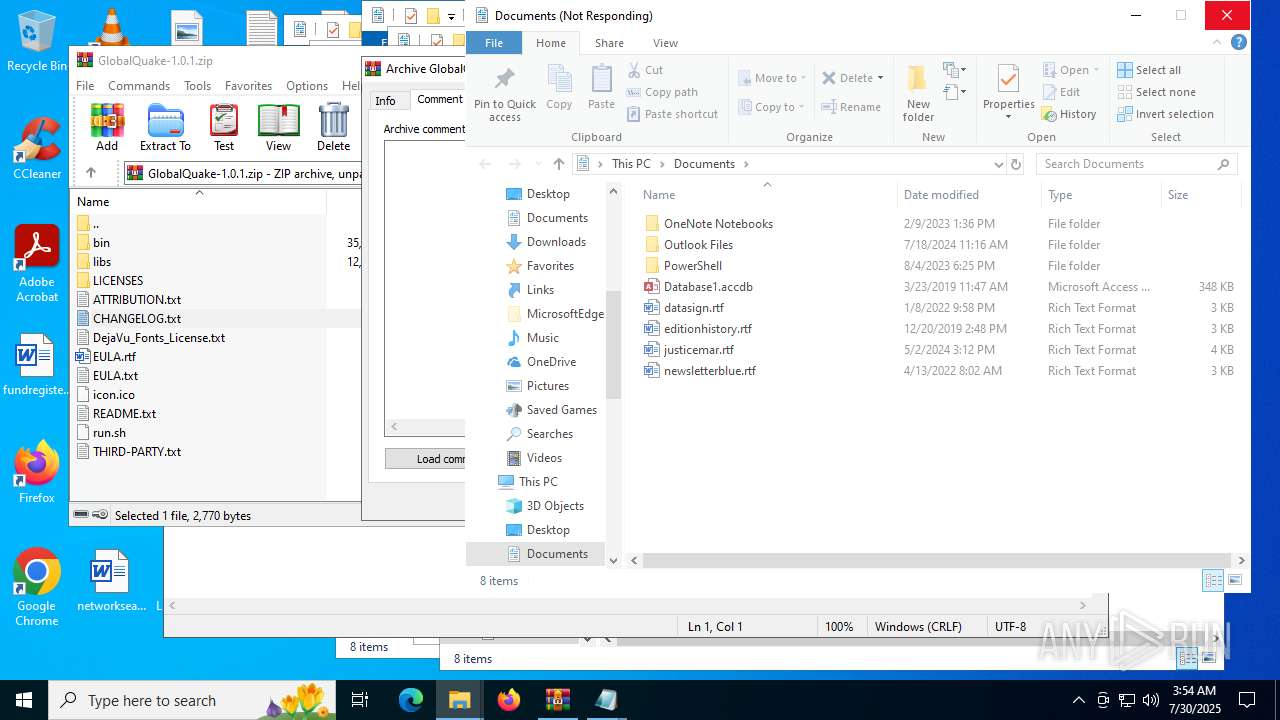
| File name: | GlobalQuake-1.0.1.zip |
| Full analysis: | https://app.any.run/tasks/1f1e3a4e-f3ec-46d4-991b-f539797ec4f0 |
| Verdict: | Malicious activity |
| Analysis date: | July 30, 2025, 03:52:36 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | EC6C175C6CF55AAD61649CFE4B8E5FF2 |
| SHA1: | 32504504BA0B083A96C7407F61F8552C50031380 |
| SHA256: | D14FD82AE7534F6C581B4ECF7F60A2898FD9594700C4A969EE453BDCB8EC4EC4 |
| SSDEEP: | 393216:9XlSuIBqr5OpIxSSpkWYyYYF+6xsY2a/XlhiHWArXT1T+8QnQIPG:9ZA4PkLAA6xR/XX65D12QT |
MALICIOUS
No malicious indicators.SUSPICIOUS
Generic archive extractor
- WinRAR.exe (PID: 5084)
INFO
Create files in a temporary directory
- javaw.exe (PID: 6016)
- javaw.exe (PID: 436)
- javaw.exe (PID: 2140)
- javaw.exe (PID: 2508)
- javaw.exe (PID: 1944)
- javaw.exe (PID: 6504)
- javaw.exe (PID: 4760)
- javaw.exe (PID: 3872)
- javaw.exe (PID: 3000)
- javaw.exe (PID: 7044)
Manual execution by a user
- notepad.exe (PID: 6636)
- notepad.exe (PID: 3100)
- javaw.exe (PID: 6016)
- javaw.exe (PID: 436)
- javaw.exe (PID: 2140)
- javaw.exe (PID: 7044)
- javaw.exe (PID: 3000)
- javaw.exe (PID: 1944)
- javaw.exe (PID: 2508)
- javaw.exe (PID: 3872)
- javaw.exe (PID: 6504)
- javaw.exe (PID: 4760)
- notepad.exe (PID: 7136)
- notepad.exe (PID: 7016)
- notepad.exe (PID: 6736)
- notepad.exe (PID: 7064)
- notepad.exe (PID: 6344)
- notepad.exe (PID: 5576)
Reads security settings of Internet Explorer
- notepad.exe (PID: 3100)
- notepad.exe (PID: 6636)
- notepad.exe (PID: 7016)
- notepad.exe (PID: 7136)
- notepad.exe (PID: 6736)
- notepad.exe (PID: 7064)
- notepad.exe (PID: 6344)
- notepad.exe (PID: 5576)
Application based on Java
- javaw.exe (PID: 6016)
- javaw.exe (PID: 436)
- javaw.exe (PID: 2140)
- javaw.exe (PID: 7044)
- javaw.exe (PID: 3000)
- javaw.exe (PID: 1944)
- javaw.exe (PID: 6504)
- javaw.exe (PID: 3872)
- javaw.exe (PID: 2508)
- javaw.exe (PID: 4760)
Checks supported languages
- javaw.exe (PID: 6016)
- javaw.exe (PID: 436)
- javaw.exe (PID: 2140)
- javaw.exe (PID: 7044)
- javaw.exe (PID: 3000)
- javaw.exe (PID: 2508)
- javaw.exe (PID: 1944)
- javaw.exe (PID: 6504)
- javaw.exe (PID: 3872)
- javaw.exe (PID: 4760)
Creates files in the program directory
- javaw.exe (PID: 6016)
Reads the software policy settings
- slui.exe (PID: 3944)
Checks proxy server information
- slui.exe (PID: 3944)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | 0x0800 |
| ZipCompression: | None |
| ZipModifyDate: | 2025:02:12 21:23:44 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | bin/ |
Total processes
149
Monitored processes
23
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 436 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -jar C:\Users\admin\Desktop\jackson-databind-2.17.2.jar | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | explorer.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 1 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 1036 | C:\WINDOWS\system32\icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\System32\icacls.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1944 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -jar C:\Users\admin\Desktop\commons-logging-1.2.jar | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | explorer.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 1 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 2140 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -jar C:\Users\admin\Desktop\slf4j-api-1.7.36.jar | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | explorer.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 1 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 2508 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -jar C:\Users\admin\Desktop\gson-2.11.0.jar | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | explorer.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 1 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 3000 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -jar C:\Users\admin\Desktop\tinylog-api-2.7.0.jar | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | explorer.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 1 Version: 8.0.2710.9 Modules
| |||||||||||||||
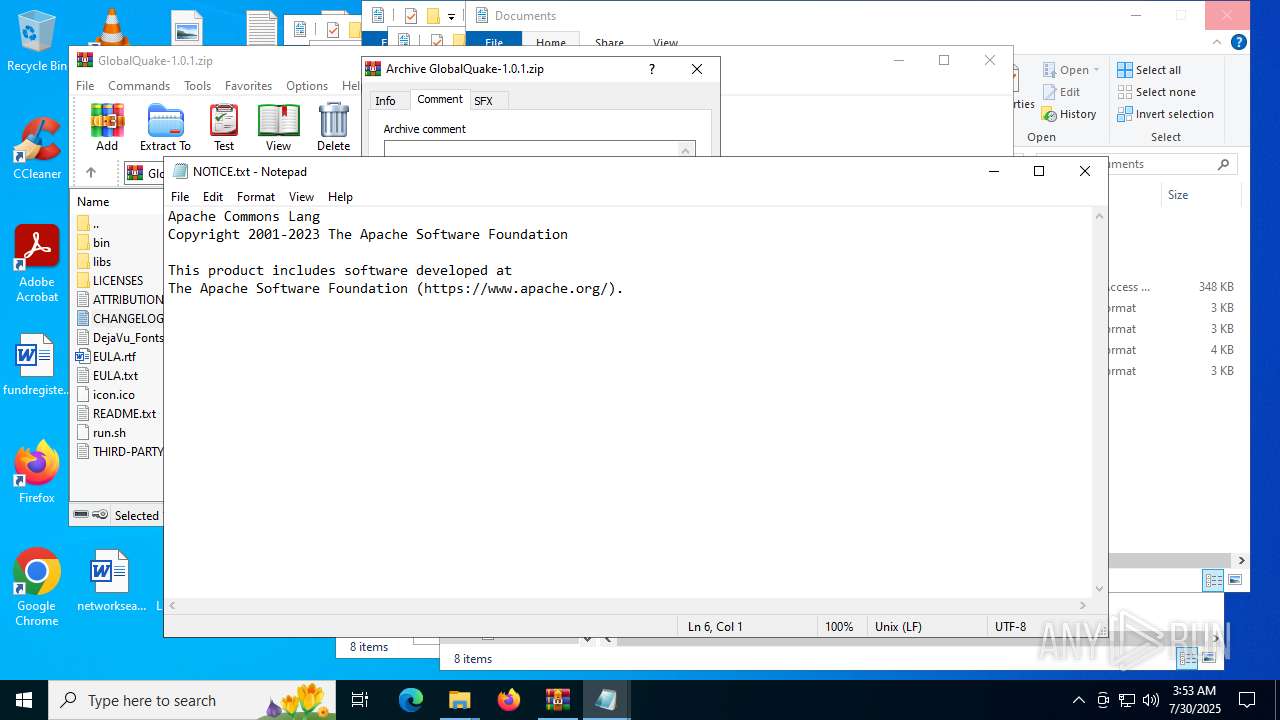
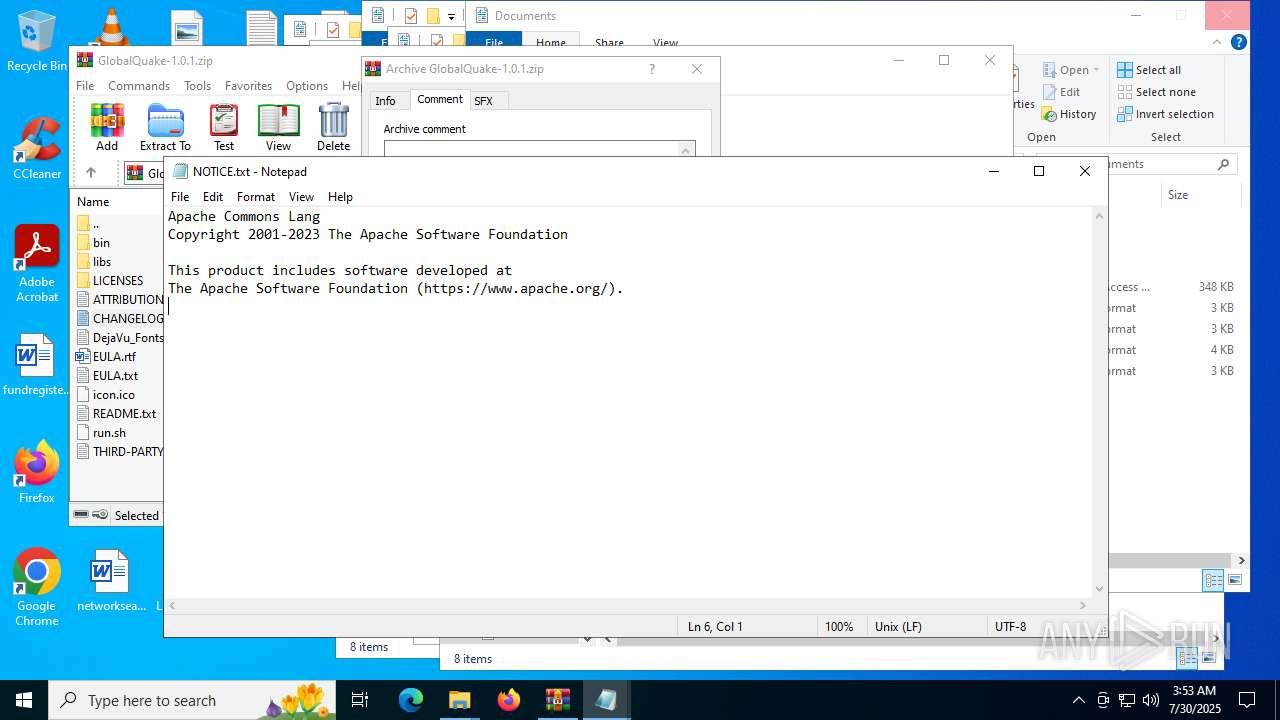
| 3100 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\NOTICE.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3872 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -jar C:\Users\admin\Desktop\httpcore-4.4.16.jar | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | explorer.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 1 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 3944 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4760 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -jar C:\Users\admin\Desktop\httpclient-4.5.14.jar | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | explorer.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 1 Version: 8.0.2710.9 Modules
| |||||||||||||||
Total events
7 516
Read events
7 506
Write events
10
Delete events
0
Modification events
| (PID) Process: | (5084) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5084) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5084) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5084) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\GlobalQuake-1.0.1.zip | |||
| (PID) Process: | (5084) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5084) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5084) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5084) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5084) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList |
| Operation: | write | Name: | ArcSort |
Value: 32 | |||
| (PID) Process: | (5084) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList |
| Operation: | write | Name: | ArcSort |
Value: 0 | |||
Executable files
0
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6016 | javaw.exe | C:\ProgramData\Oracle\Java\.oracle_jre_usage\17dfc292991c8061.timestamp | text | |
MD5:27E6C87A19EE906FA4BCCC60009EDB75 | SHA256:D8722FD53892C371E746F38F212A0B033C491B7821C2F8CF22D074BD5FCBA49F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
39
TCP/UDP connections
42
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 400 | 20.190.159.130:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 40.126.31.131:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 40.126.31.67:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 20.190.159.75:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |