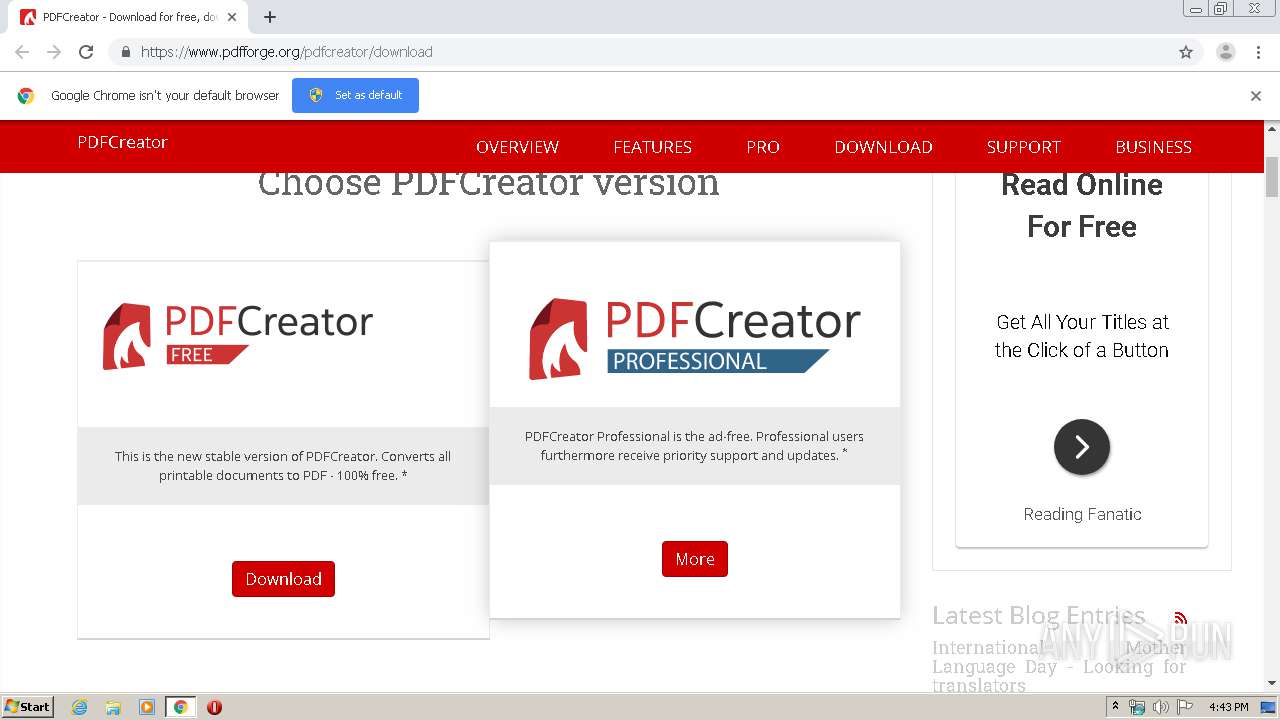
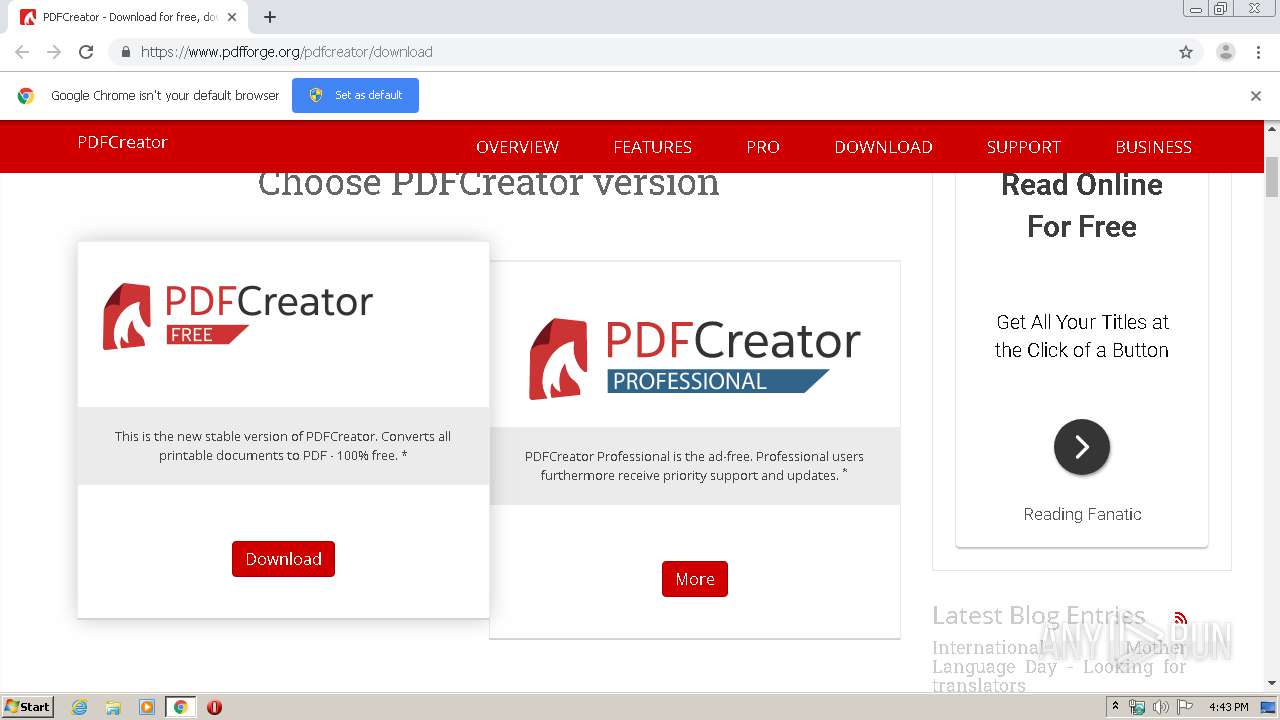
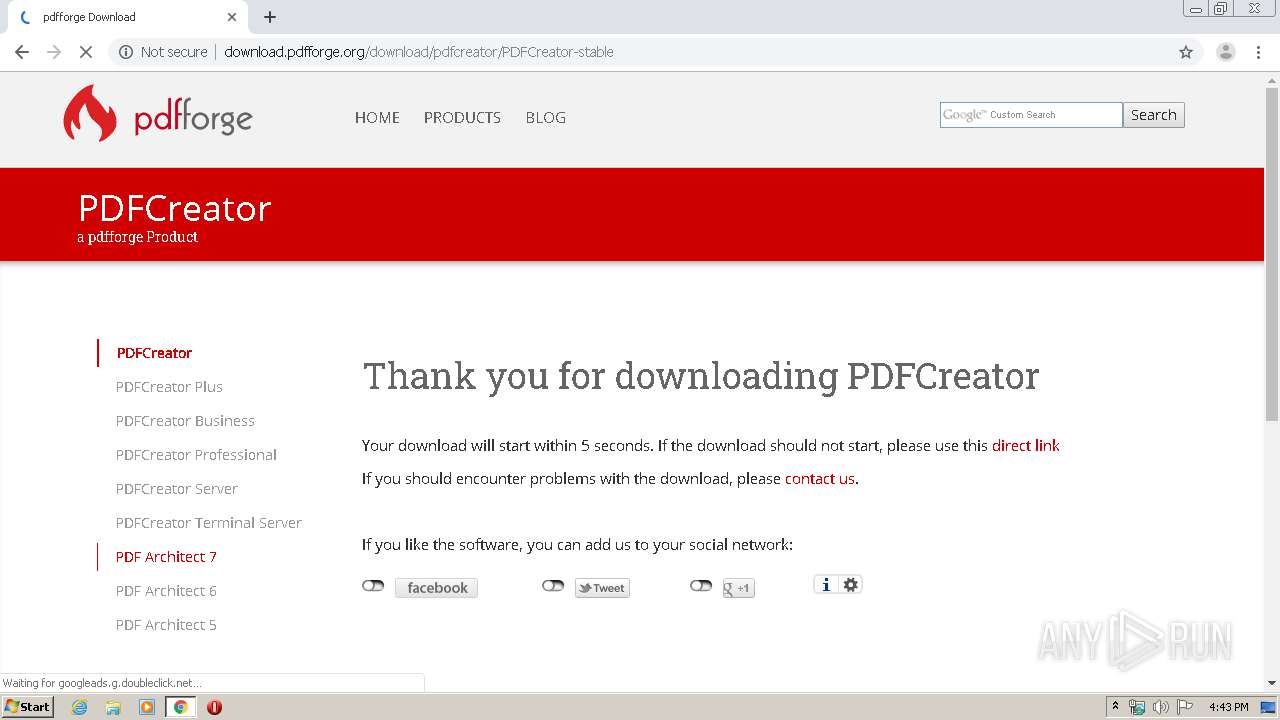
| URL: | https://www.pdfforge.org/pdfcreator/download |
| Full analysis: | https://app.any.run/tasks/7c4da78e-020f-4a3d-abbe-f314b91b22cf |
| Verdict: | Malicious activity |
| Analysis date: | March 26, 2020, 16:43:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 5A3FD0149276A2A45424EC348C79C39C |
| SHA1: | EBBFE4C22A3FA84922168BF3BBA19460155052DD |
| SHA256: | D11FD0427142E8613A2D353E68983C694323E766CF756996EC6A711E29D220BF |
| SSDEEP: | 3:N8DSLTKSFScaFJp:2OLTKSFuFz |
MALICIOUS
Application was dropped or rewritten from another process
- PDFCreator-4_0_3-Setup.exe (PID: 1460)
- PDFCreator-4_0_3-Setup.exe (PID: 3244)
- 7z.exe (PID: 2704)
- PDFCreatorSetup.exe (PID: 1604)
- PrinterHelper.exe (PID: 3812)
- setuphelper.exe (PID: 3708)
- architect-setup.exe (PID: 1296)
- setuphelper.exe (PID: 440)
- PDF_Architect_7_Installer.exe (PID: 3064)
- PDFCreator.exe (PID: 3576)
- PDFCreator.exe (PID: 3444)
- stats-com.exe (PID: 3476)
- gswin32c.exe (PID: 2524)
- ws.exe (PID: 2080)
- updater-ws.exe (PID: 3440)
Loads dropped or rewritten executable
- PDFCreatorSetup.exe (PID: 1604)
- rundll32.exe (PID: 3788)
- rundll32.exe (PID: 3112)
- rundll32.exe (PID: 3640)
- rundll32.exe (PID: 748)
- rundll32.exe (PID: 3388)
- setuphelper.exe (PID: 3708)
- rundll32.exe (PID: 1676)
- rundll32.exe (PID: 2692)
- setuphelper.exe (PID: 440)
- RegAsm.exe (PID: 3060)
- RegAsm.exe (PID: 2436)
- spoolsv.exe (PID: 1188)
- PrinterHelper.exe (PID: 3812)
- PDFCreator.exe (PID: 3576)
- regsvr32.exe (PID: 2412)
- architect-setup.exe (PID: 1296)
- DllHost.exe (PID: 1712)
- WINWORD.EXE (PID: 2588)
- PDFCreator.exe (PID: 3444)
- gswin32c.exe (PID: 2524)
- MsiExec.exe (PID: 952)
- stats-com.exe (PID: 3476)
- ws.exe (PID: 2080)
- updater-ws.exe (PID: 3440)
- MsiExec.exe (PID: 2060)
- explorer.exe (PID: 372)
- svchost.exe (PID: 860)
- DllHost.exe (PID: 4056)
Changes settings of System certificates
- PDFCreatorSetup.exe (PID: 1604)
- architect-setup.exe (PID: 1296)
- PDFCreator-4_0_3-Setup.exe (PID: 1460)
Registers / Runs the DLL via REGSVR32.EXE
- architect-setup.exe (PID: 1296)
SUSPICIOUS
Executable content was dropped or overwritten
- chrome.exe (PID: 3792)
- chrome.exe (PID: 3144)
- PDFCreator-4_0_3-Setup.exe (PID: 1460)
- 7z.exe (PID: 2704)
- rundll32.exe (PID: 3640)
- rundll32.exe (PID: 748)
- rundll32.exe (PID: 1676)
- rundll32.exe (PID: 3388)
- msiexec.exe (PID: 2108)
- PDFCreatorSetup.exe (PID: 1604)
- spoolsv.exe (PID: 1188)
- architect-setup.exe (PID: 1296)
- PrinterHelper.exe (PID: 3812)
Modifies files in Chrome extension folder
- chrome.exe (PID: 3144)
Reads Environment values
- PDFCreatorSetup.exe (PID: 1604)
- PDFCreator.exe (PID: 3576)
Adds / modifies Windows certificates
- PDFCreatorSetup.exe (PID: 1604)
- architect-setup.exe (PID: 1296)
- PDFCreator-4_0_3-Setup.exe (PID: 1460)
Uses RUNDLL32.EXE to load library
- MsiExec.exe (PID: 1156)
- MsiExec.exe (PID: 4064)
Creates COM task schedule object
- RegAsm.exe (PID: 3060)
- RegAsm.exe (PID: 2436)
- regsvr32.exe (PID: 2412)
- MsiExec.exe (PID: 3476)
- MsiExec.exe (PID: 952)
- MsiExec.exe (PID: 2060)
Creates files in the program directory
- RegAsm.exe (PID: 3060)
- PDFCreatorSetup.exe (PID: 1604)
- architect-setup.exe (PID: 1296)
Creates files in the Windows directory
- PrinterHelper.exe (PID: 3812)
- spoolsv.exe (PID: 1188)
Removes files from Windows directory
- spoolsv.exe (PID: 1188)
- PrinterHelper.exe (PID: 3812)
Searches for installed software
- PDFCreatorSetup.exe (PID: 1604)
- PDFCreator.exe (PID: 3576)
Starts itself from another location
- architect-setup.exe (PID: 1296)
Reads Internet Cache Settings
- architect-setup.exe (PID: 1296)
Executed via COM
- DllHost.exe (PID: 1712)
Starts Microsoft Office Application
- PDFCreator.exe (PID: 3576)
Creates files in the user directory
- explorer.exe (PID: 372)
Executed as Windows Service
- vssvc.exe (PID: 4072)
Modifies the open verb of a shell class
- msiexec.exe (PID: 2108)
Changes IE settings (feature browser emulation)
- AcroRd32.exe (PID: 1388)
Creates a software uninstall entry
- architect-setup.exe (PID: 1296)
INFO
Reads the hosts file
- chrome.exe (PID: 3792)
- chrome.exe (PID: 3144)
- RdrCEF.exe (PID: 3552)
Reads Internet Cache Settings
- chrome.exe (PID: 3144)
Application launched itself
- chrome.exe (PID: 3144)
- msiexec.exe (PID: 2108)
- RdrCEF.exe (PID: 3552)
Dropped object may contain Bitcoin addresses
- 7z.exe (PID: 2704)
- msiexec.exe (PID: 2108)
- architect-setup.exe (PID: 1296)
Reads settings of System Certificates
- PDFCreator-4_0_3-Setup.exe (PID: 1460)
- PDFCreatorSetup.exe (PID: 1604)
- chrome.exe (PID: 3792)
- PrinterHelper.exe (PID: 3812)
- PDFCreator.exe (PID: 3576)
- architect-setup.exe (PID: 1296)
Loads dropped or rewritten executable
- MsiExec.exe (PID: 1156)
- MsiExec.exe (PID: 4064)
Creates a software uninstall entry
- msiexec.exe (PID: 2108)
Creates files in the program directory
- msiexec.exe (PID: 2108)
Manual execution by user
- PDFCreator.exe (PID: 3576)
Creates files in the user directory
- WINWORD.EXE (PID: 2588)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2588)
Low-level read access rights to disk partition
- vssvc.exe (PID: 4072)
Searches for installed software
- msiexec.exe (PID: 2108)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
122
Monitored processes
76
Malicious processes
25
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1000,17520006566804599063,14212101678021356474,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=1480792801777221921 --mojo-platform-channel-handle=3468 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 372 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 440 | "C:\Program Files\PDFCreator\setuphelper.exe" /ComInterface=Register | C:\Program Files\PDFCreator\setuphelper.exe | — | rundll32.exe | |||||||||||
User: SYSTEM Company: pdfforge Integrity Level: SYSTEM Description: SetupHelper Exit code: 0 Version: 1.2.0.0 Modules
| |||||||||||||||
| 748 | rundll32.exe "C:\Windows\Installer\MSI17D1.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_11016421 13 PDFCreator_setup!pdfforge.PDFCreator.Setup.Builder.Features.FreewareExclusiveFeaturesBuilder.CheckInstall | C:\Windows\system32\rundll32.exe | MsiExec.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 860 | C:\Windows\system32\svchost.exe -k netsvcs | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 952 | "C:\Windows\system32\MsiExec.exe" /Y "C:\Program Files\PDF Architect 7\preview-handler.dll" | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 956 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1000,17520006566804599063,14212101678021356474,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=3168560508315394261 --renderer-client-id=10 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3628 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1028 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-direct-npapi-requests --disable-file-system --disable-notifications --disable-shared-workers --disable-direct-write --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.23.20053 Chrome/45.0.2454.85" --device-scale-factor=1 --enable-delegated-renderer --num-raster-threads=2 --gpu-rasterization-msaa-sample-count=8 --content-image-texture-target=3553 --video-image-texture-target=3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --channel="3552.1.187177326\1564431828" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 1064 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1000,17520006566804599063,14212101678021356474,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=10761118126215875916 --mojo-platform-channel-handle=3612 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1156 | C:\Windows\system32\MsiExec.exe -Embedding 863CDC24A074810342479620AA56E199 | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
19 510
Read events
11 528
Write events
7 538
Delete events
444
Modification events
| (PID) Process: | (3144) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3144) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3144) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3144) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3144) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1920) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 3144-13229714613725625 |
Value: 259 | |||
| (PID) Process: | (3144) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3144) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3144) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3120-13213713943555664 |
Value: 0 | |||
| (PID) Process: | (3144) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
255
Suspicious files
222
Text files
695
Unknown types
82
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3144 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-5E7CDBB6-C48.pma | — | |
MD5:— | SHA256:— | |||
| 3144 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\77d387d3-a9ef-417c-b3e8-5d05579a8eb3.tmp | — | |
MD5:— | SHA256:— | |||
| 3144 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000028.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3144 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\EventDB\LOG.old~RFa66d39.TMP | text | |
MD5:— | SHA256:— | |||
| 3144 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3144 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3144 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 860 | svchost.exe | C:\Windows\appcompat\programs\RecentFileCache.bcf | txt | |
MD5:— | SHA256:— | |||
| 3144 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3144 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
36
TCP/UDP connections
146
DNS requests
71
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3792 | chrome.exe | GET | 200 | 216.239.36.21:80 | http://download.pdfforge.org/styles/overwrite.css | US | text | 1.53 Kb | malicious |
3792 | chrome.exe | GET | 200 | 216.239.36.21:80 | http://download.pdfforge.org/styles/screen.css | US | text | 42.4 Kb | malicious |
3792 | chrome.exe | GET | 200 | 216.239.36.21:80 | http://download.pdfforge.org/scripts/vendor/modernizr.js | US | html | 4.95 Kb | malicious |
3792 | chrome.exe | GET | 200 | 216.239.36.21:80 | http://download.pdfforge.org/images/socialprivacy/dummy_facebook.png | US | image | 1.83 Kb | malicious |
3792 | chrome.exe | GET | 200 | 216.239.36.21:80 | http://download.pdfforge.org/download/pdfcreator/PDFCreator-stable | US | html | 18.3 Kb | malicious |
3792 | chrome.exe | GET | 200 | 216.239.36.21:80 | http://download.pdfforge.org/images/base/en_logo.png | US | image | 11.3 Kb | malicious |
3792 | chrome.exe | GET | 200 | 216.239.36.21:80 | http://download.pdfforge.org/scripts/main.min.js?v=2 | US | text | 4.53 Kb | malicious |
3792 | chrome.exe | GET | 200 | 216.58.210.2:80 | http://pagead2.googlesyndication.com/pagead/js/adsbygoogle.js | US | text | 38.1 Kb | whitelisted |
3792 | chrome.exe | GET | 200 | 216.239.36.21:80 | http://download.pdfforge.org/scripts/vendor/adsense_cse.js | US | text | 1.01 Kb | malicious |
3792 | chrome.exe | GET | 200 | 216.239.36.21:80 | http://download.pdfforge.org/images/socialprivacy/dummy_twitter.png | US | image | 1.31 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3792 | chrome.exe | 216.58.207.67:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
3792 | chrome.exe | 178.33.77.135:443 | www.pdfforge.org | OVH SAS | FR | suspicious |
3792 | chrome.exe | 172.217.22.77:443 | accounts.google.com | Google Inc. | US | whitelisted |
3792 | chrome.exe | 172.217.18.106:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3792 | chrome.exe | 172.217.21.234:443 | maps.googleapis.com | Google Inc. | US | whitelisted |
3792 | chrome.exe | 172.217.18.10:443 | ajax.googleapis.com | Google Inc. | US | whitelisted |
3792 | chrome.exe | 216.58.210.2:443 | pagead2.googlesyndication.com | Google Inc. | US | whitelisted |
3792 | chrome.exe | 46.105.202.131:443 | cdn.pdfforge.org | OVH SAS | FR | suspicious |
3792 | chrome.exe | 216.58.206.14:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
3792 | chrome.exe | 216.58.206.2:443 | adservice.google.de | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.pdfforge.org |
| unknown |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
fonts.googleapis.com |
| whitelisted |
maps.googleapis.com |
| whitelisted |
ajax.googleapis.com |
| whitelisted |
pagead2.googlesyndication.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
cdn.pdfforge.org |
| suspicious |
static.pdfforge.org |
| suspicious |
Threats
Process | Message |
|---|---|
gswin32c.exe | RRANTY: see the file PUBLIC for details.
|
gswin32c.exe | GPL Ghostscript 9.25 (2018-09-13)
Copyright (C) 2018 Artifex Software, Inc. All rights reserved.
This software comes with NO WA |
gswin32c.exe | Loading NimbusMonoPS-Regular font from %rom%Resource/Font/NimbusMonoPS-Regular... |
gswin32c.exe | 4508436 3088464 1801504 501472 1 done.
|
gswin32c.exe | %%[ ProductName: GPL Ghostscript ]%%
|
gswin32c.exe | Loading NimbusRoman-Regular font from %rom%Resource/Font/NimbusRoman-Regular... |
gswin32c.exe | 4614532 3294236 2337576 1001352 2 done.
|
gswin32c.exe | %%[Page: 1]%%
%%[LastPage]%%
|