| File name: | income_tax_and_benefit_return_2021.docx |
| Full analysis: | https://app.any.run/tasks/bd0d414f-64ce-463d-a958-cace2d3f3118 |
| Verdict: | Malicious activity |
| Analysis date: | February 17, 2024, 23:35:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| MIME: | application/octet-stream |
| File info: | Microsoft OOXML |
| MD5: | 55998CB43459159A5ED4511F00FF3FC8 |
| SHA1: | 9BEC2182CC5B41FE8783BB7AB6E577BAC5C19F04 |
| SHA256: | D0E1F97DBE2D0AF9342E64D460527B088D85F96D38B1D1D4AA610C0987DCA745 |
| SSDEEP: | 384:Q6UDg00MWEg9fPCPyH111/elBqhveoNHfn5yAehqbhtgyhdCxi556BjsbIwRq:QcMWE04uebyvNv5yHcttg6dwc5YQb5w |
MALICIOUS
CVE-2022-30190 detected
- WINWORD.EXE (PID: 3700)
SUSPICIOUS
No suspicious indicators.INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docx | | | Word Microsoft Office Open XML Format document (52.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (38.8) |
| .zip | | | ZIP compressed archive (8.8) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0x1e3c81b4 |
| ZipCompressedSize: | 358 |
| ZipUncompressedSize: | 1416 |
| ZipFileName: | [Content_Types].xml |
XML
| Template: | Normal |
|---|---|
| TotalEditTime: | 34 minutes |
| Pages: | 1 |
| Words: | 206 |
| Characters: | 1176 |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 9 |
| Paragraphs: | 2 |
| ScaleCrop: | No |
| Company: | Consumers Association |
| LinksUpToDate: | No |
| CharactersWithSpaces: | 1380 |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 16 |
| LastModifiedBy: | user |
| RevisionNumber: | 6 |
| CreateDate: | 2013:10:31 15:25:00Z |
| ModifyDate: | 2021:08:31 16:47:00Z |
XMP
| Title: | - |
|---|---|
| Subject: | - |
| Creator: | Michele Eykelbosch |
| Description: | - |
| Language: | en-US |
Total processes
39
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3700 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\income_tax_and_benefit_return_2021.docx" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
7 850
Read events
7 022
Write events
577
Delete events
251
Modification events
| (PID) Process: | (3700) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | <a' |
Value: 3C612700740E0000010000000000000000000000 | |||
| (PID) Process: | (3700) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3700) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3700) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3700) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3700) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3700) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3700) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3700) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3700) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
8
Text files
1
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3700 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRED9C.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3700 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:280D2B65A6285DCE35099F1721B7999D | SHA256:9C481BFD497634B56792F1F82F7323677D76F0ECD94EC28D527714D4DEF38B52 | |||
| 3700 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\msoDF6.tmp | document | |
MD5:F3DA6C44C0957CC125BFF6FE29A91C86 | SHA256:A57BE71B4AD5544DE6EB9FACC52700A44F54A095C9B2CC16721818F5B5B22DAF | |||
| 3700 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\LocalCacheFileEditManager\FSF-{0E1EEE64-E8C6-4E2A-9759-63CF07FD8988}.FSF | binary | |
MD5:D471A0BB5F0B8A9AC834E0172491B7F9 | SHA256:418B6AE0A39787583DCD77DA0ED040F8C3DDA03410E71D04C235EE6E736F298F | |||
| 3700 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\2408C799.dat | binary | |
MD5:07FFEFF17A8A1A1209AB3C2690D569D4 | SHA256:57CFA30BB860B95B7012ED62427025959B671D270AAF67FC406FBC3C4F3C48D4 | |||
| 3700 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\FSF-CTBL.FSF | binary | |
MD5:D471A0BB5F0B8A9AC834E0172491B7F9 | SHA256:418B6AE0A39787583DCD77DA0ED040F8C3DDA03410E71D04C235EE6E736F298F | |||
| 3700 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\345DD7F8.wmf | binary | |
MD5:C4E6B3035AC3828D375E5479E8485D0D | SHA256:591890CBBED60EF32252835A3F13362E9204F1088E5EFA9E164A3526B612C4D7 | |||
| 3700 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\LocalCacheFileEditManager\FSD-CNRY.FSD | binary | |
MD5:39429B01CC4882AC1E2C66F625FF69AA | SHA256:D0C3966F7BFFC9E7D48CAAFFB45426E1EE65DD7DF172516B9EC6A20FE79217FA | |||
| 3700 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{D51C7DFA-B3E7-4CC1-8F70-2191749C8254} | binary | |
MD5:39429B01CC4882AC1E2C66F625FF69AA | SHA256:D0C3966F7BFFC9E7D48CAAFFB45426E1EE65DD7DF172516B9EC6A20FE79217FA | |||
| 3700 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$come_tax_and_benefit_return_2021.docx | binary | |
MD5:BD6D41709BF8D7AA5D0E2C6D2E9673BF | SHA256:5A5EB8DD117C96C803F84125C89A14BC0EA1E90E57822B17DDFA269A1E704439 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
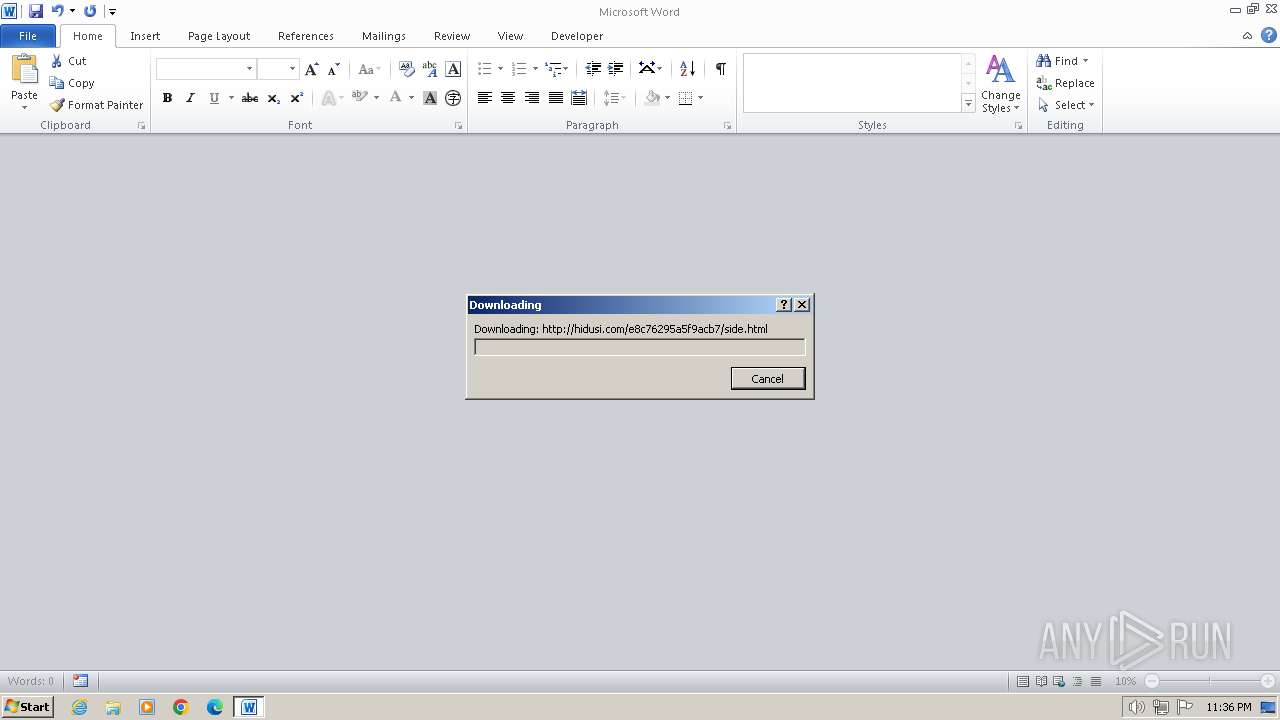
hidusi.com |
| unknown |