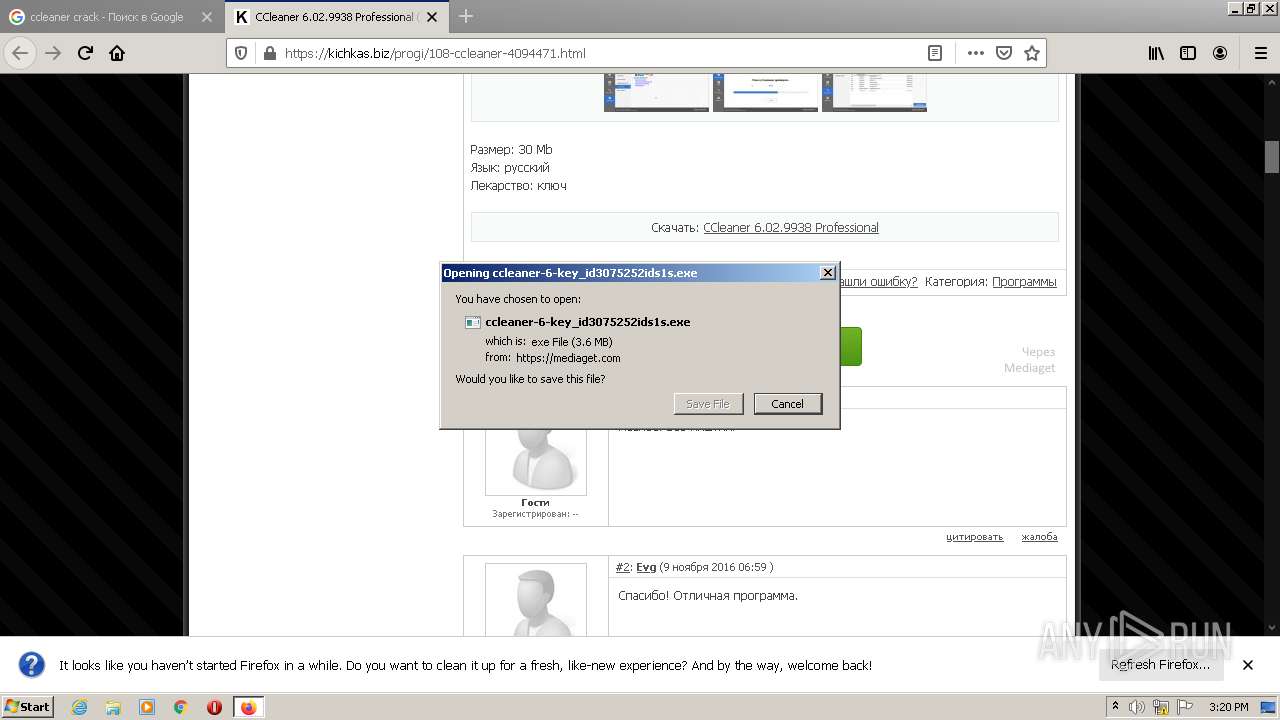
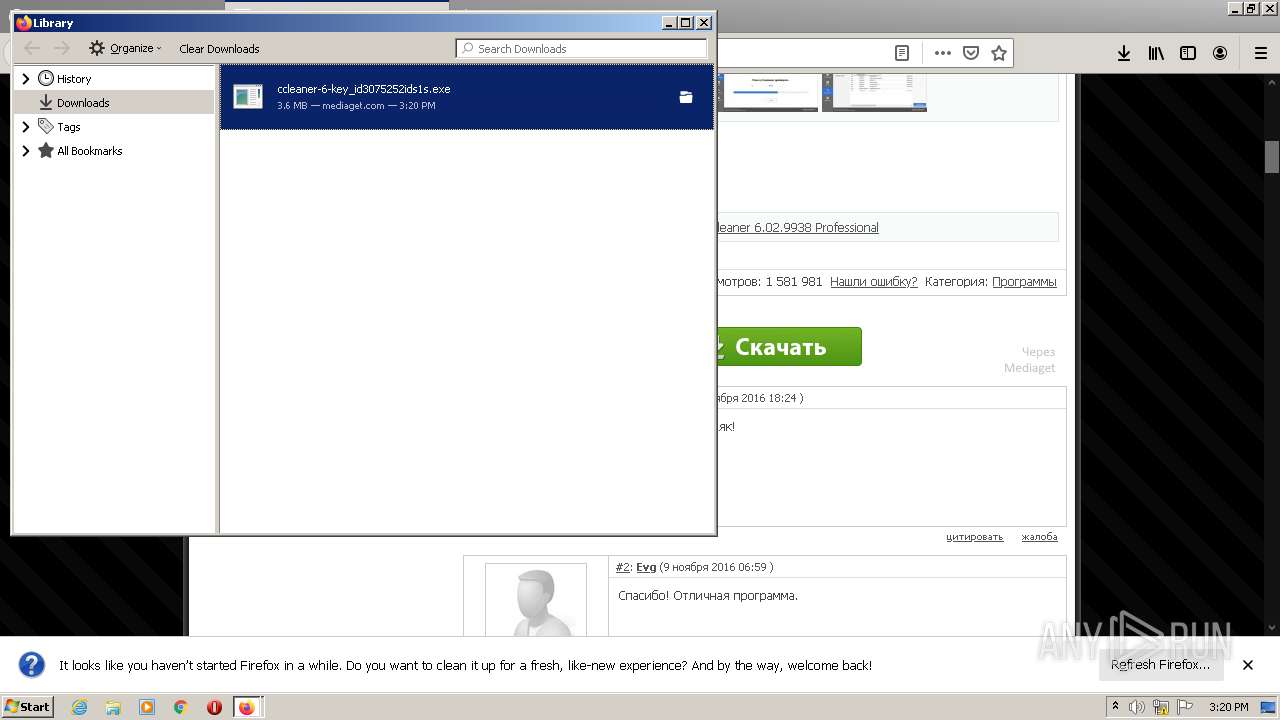
| URL: | https://www.google.com/ |
| Full analysis: | https://app.any.run/tasks/e56df576-ca50-4137-8387-b7b1ee69ff51 |
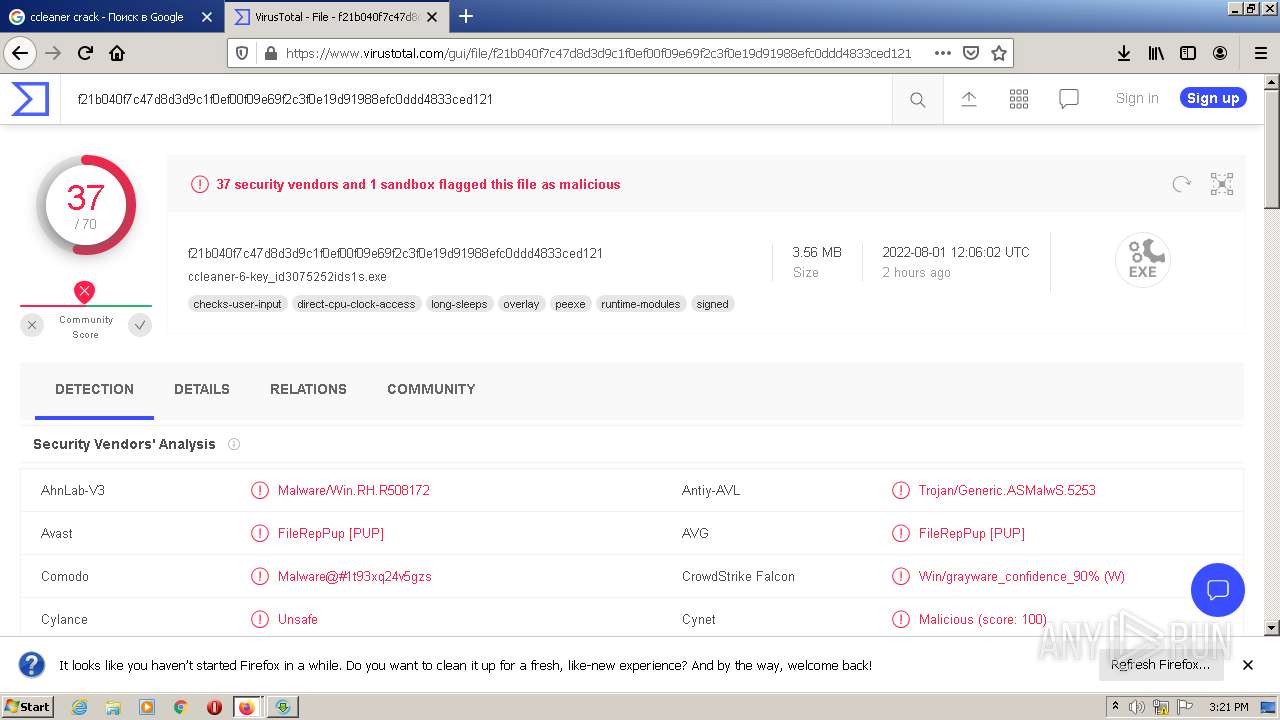
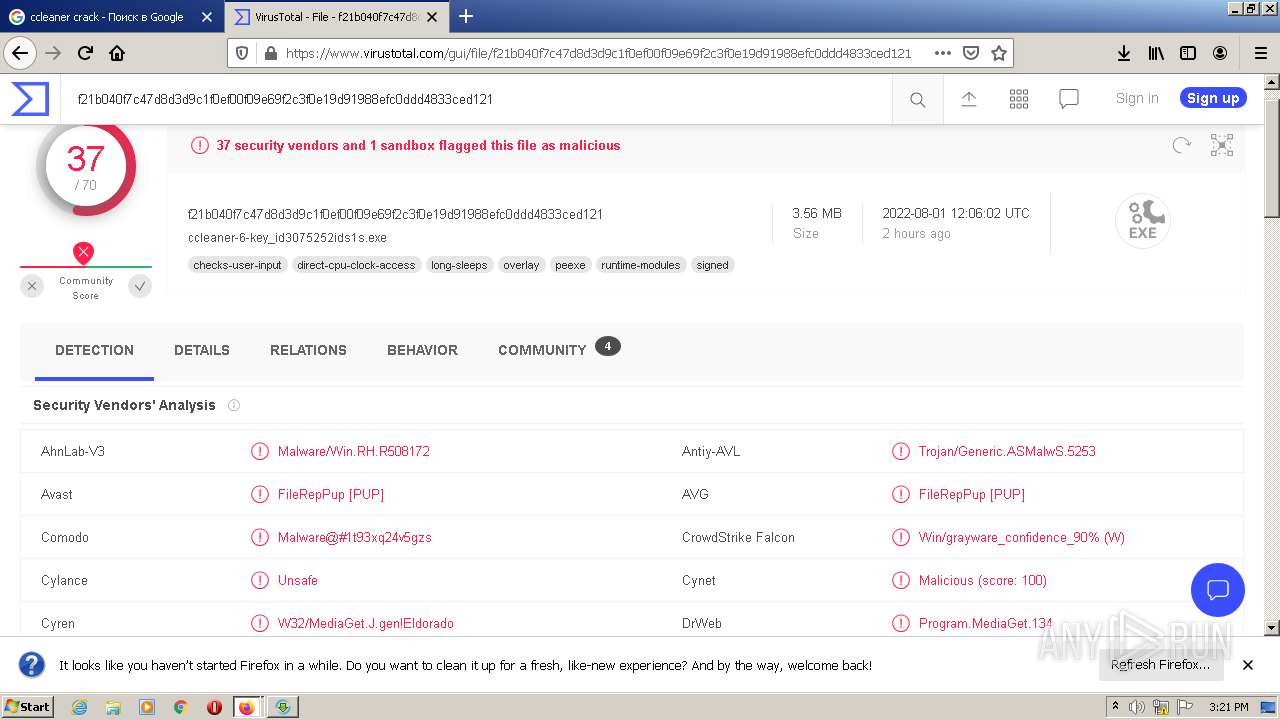
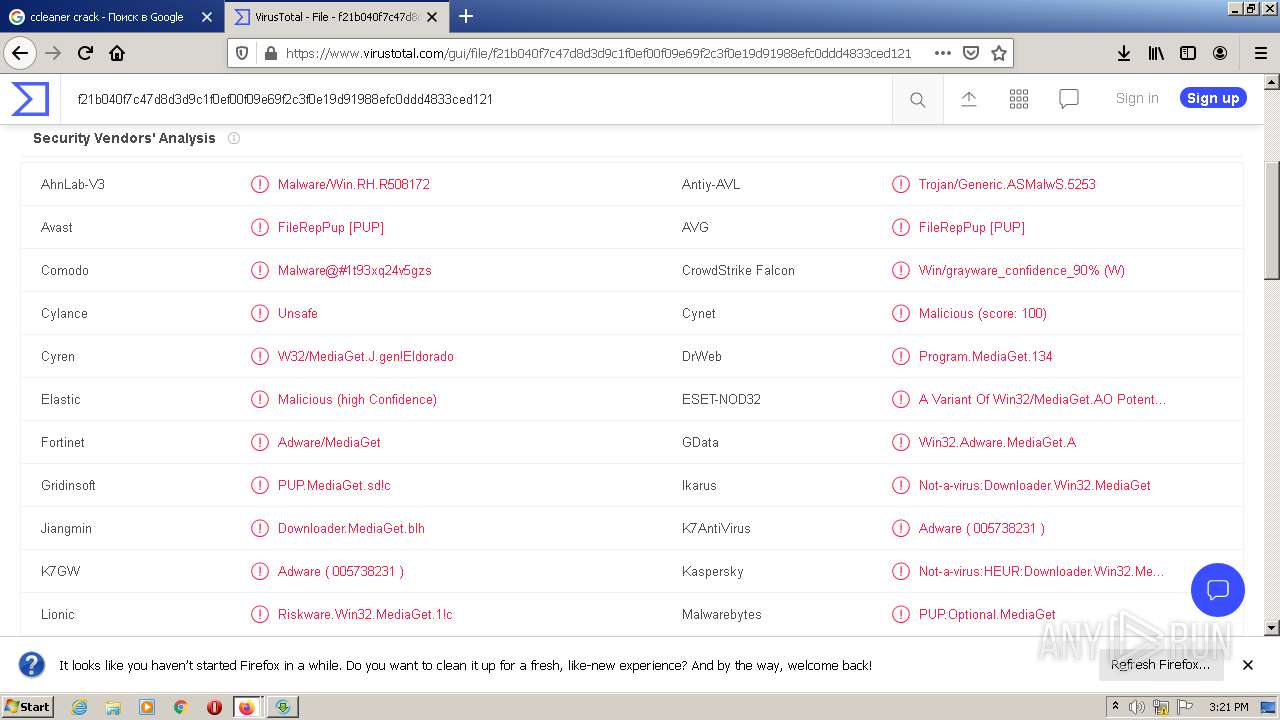
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | August 01, 2022, 14:19:01 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | D75277CDFFEF995A46AE59BDAEF1DB86 |
| SHA1: | 595C3CCE2409A55C13076F1BAC5EDEE529FC2E58 |
| SHA256: | D0E196A0C25D35DD0A84593CBAE0F38333AA58529936444EA26453EAB28DFC86 |
| SSDEEP: | 3:N8DSLIR:2OLIR |
MALICIOUS
Drops executable file immediately after starts
- firefox.exe (PID: 2780)
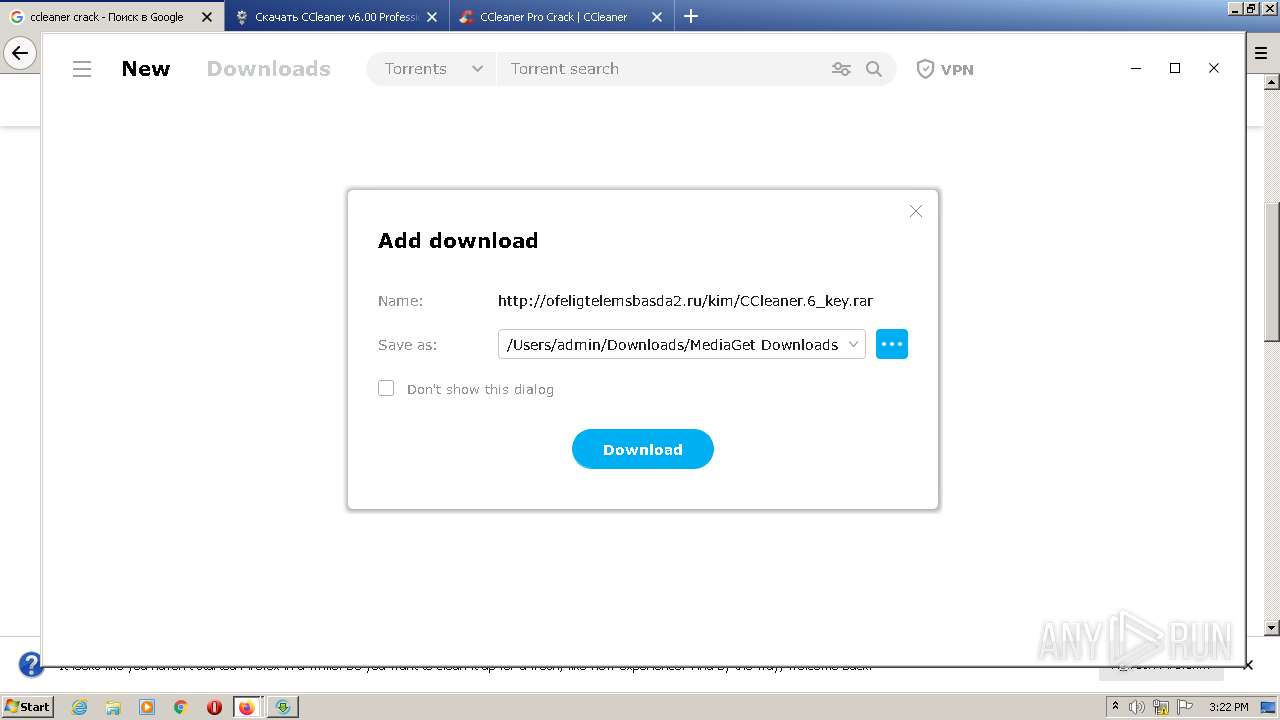
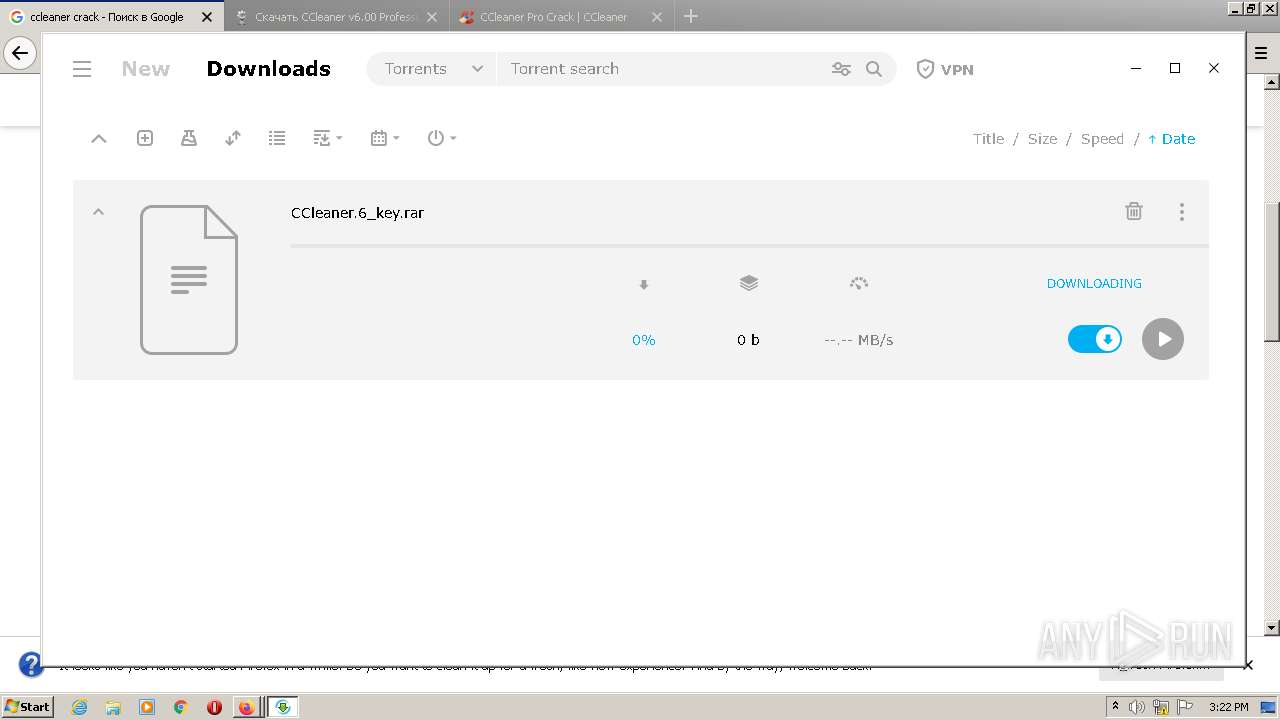
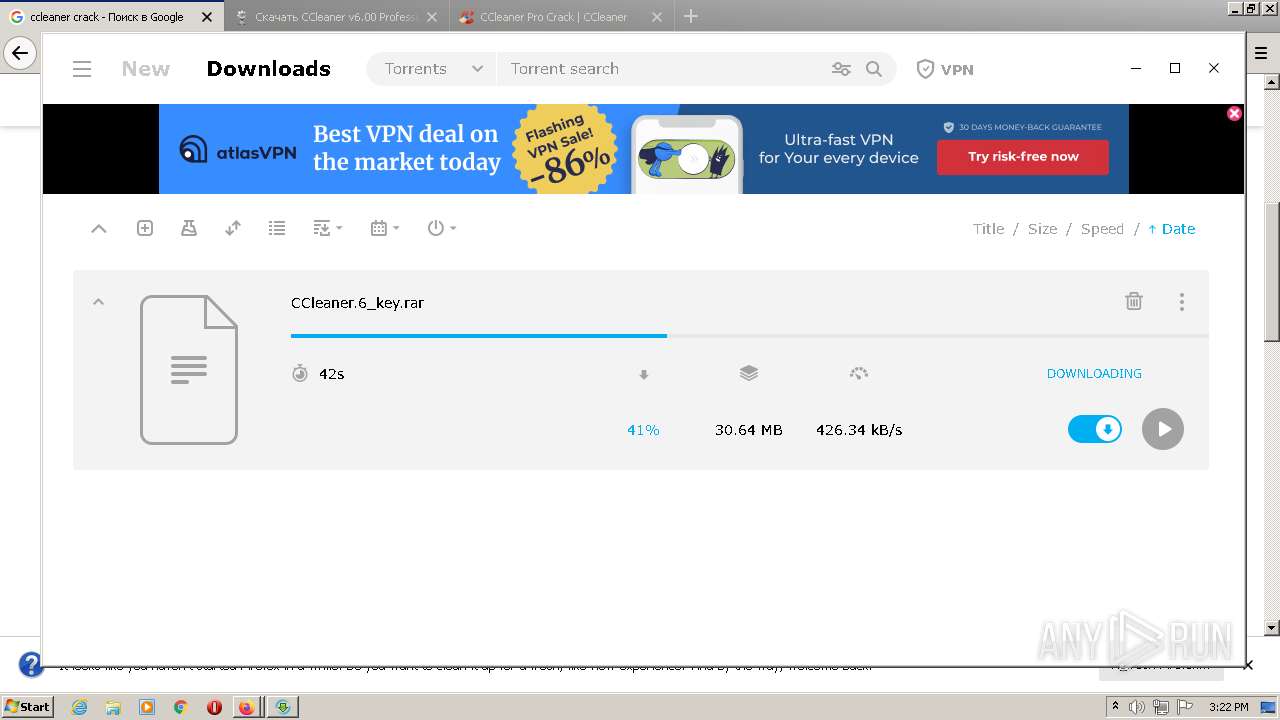
- ccleaner-6-key_id3075252ids1s.exe (PID: 2504)
- lum_inst.exe (PID: 2240)
- lum_inst.tmp (PID: 1552)
- net_updater32.exe (PID: 3692)
- antivirus360.exe (PID: 2344)
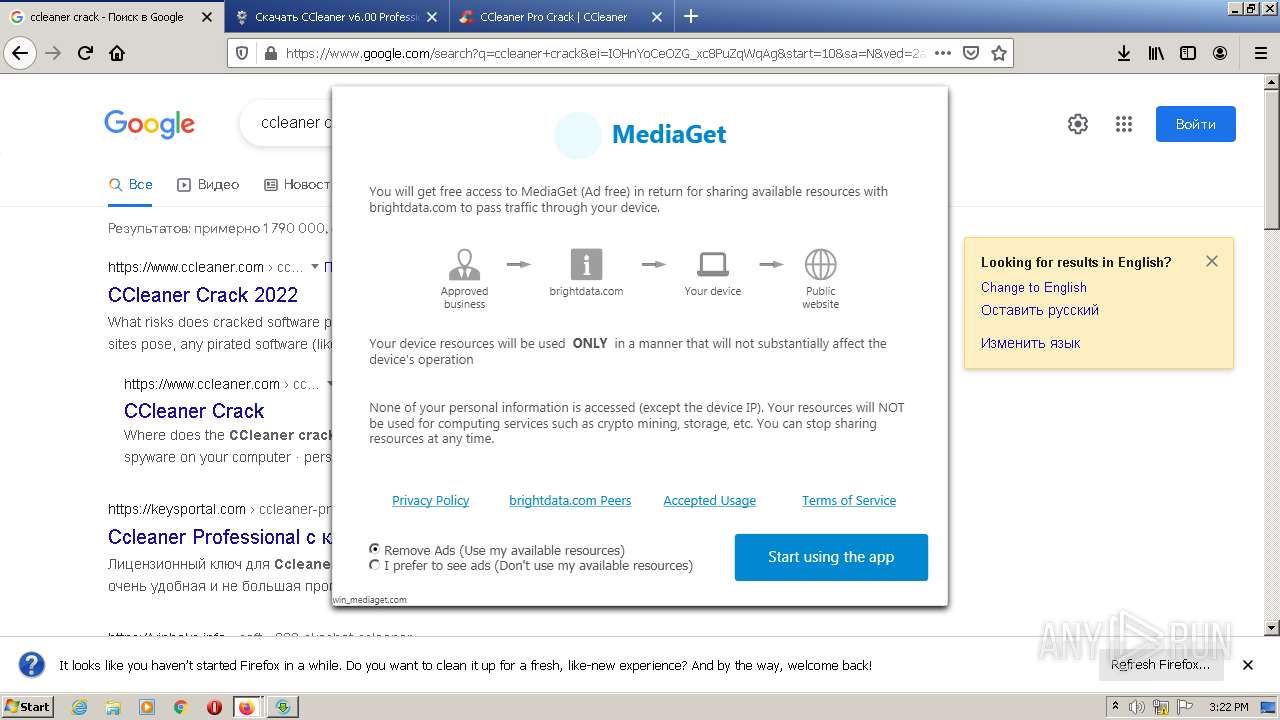
- mediaget.exe (PID: 2956)
- luminati-m-controller.exe (PID: 5256)
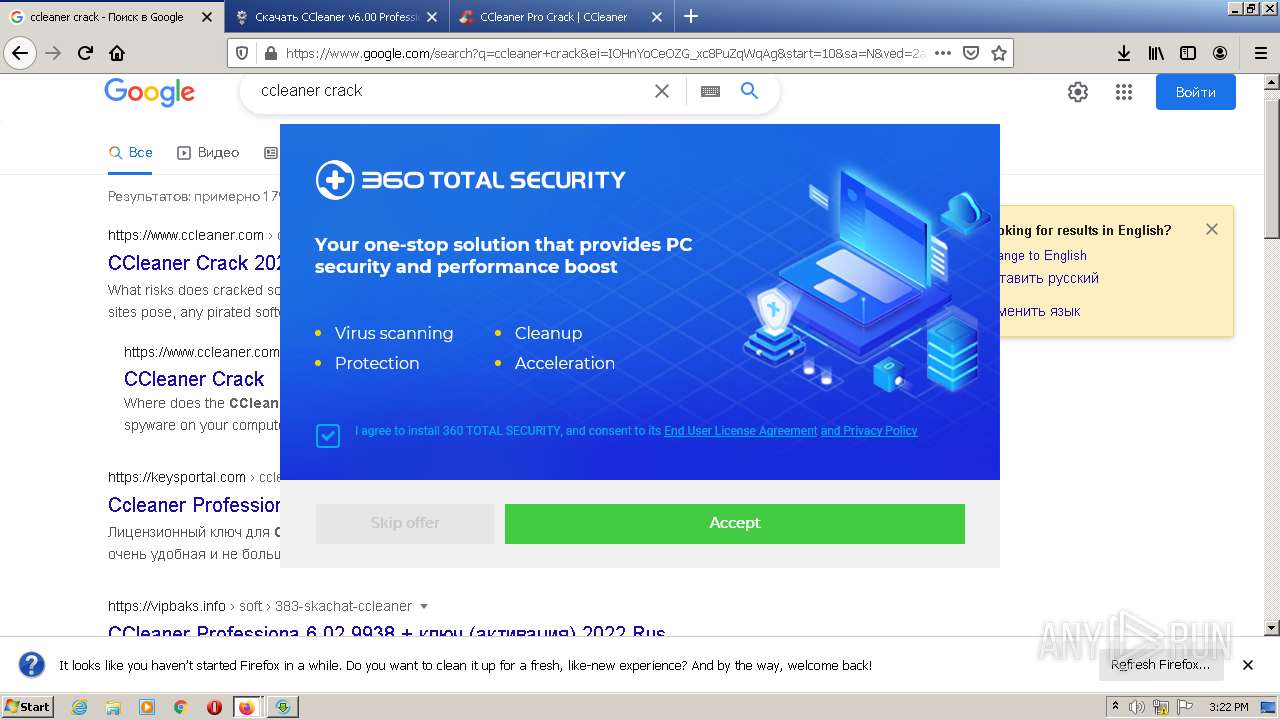
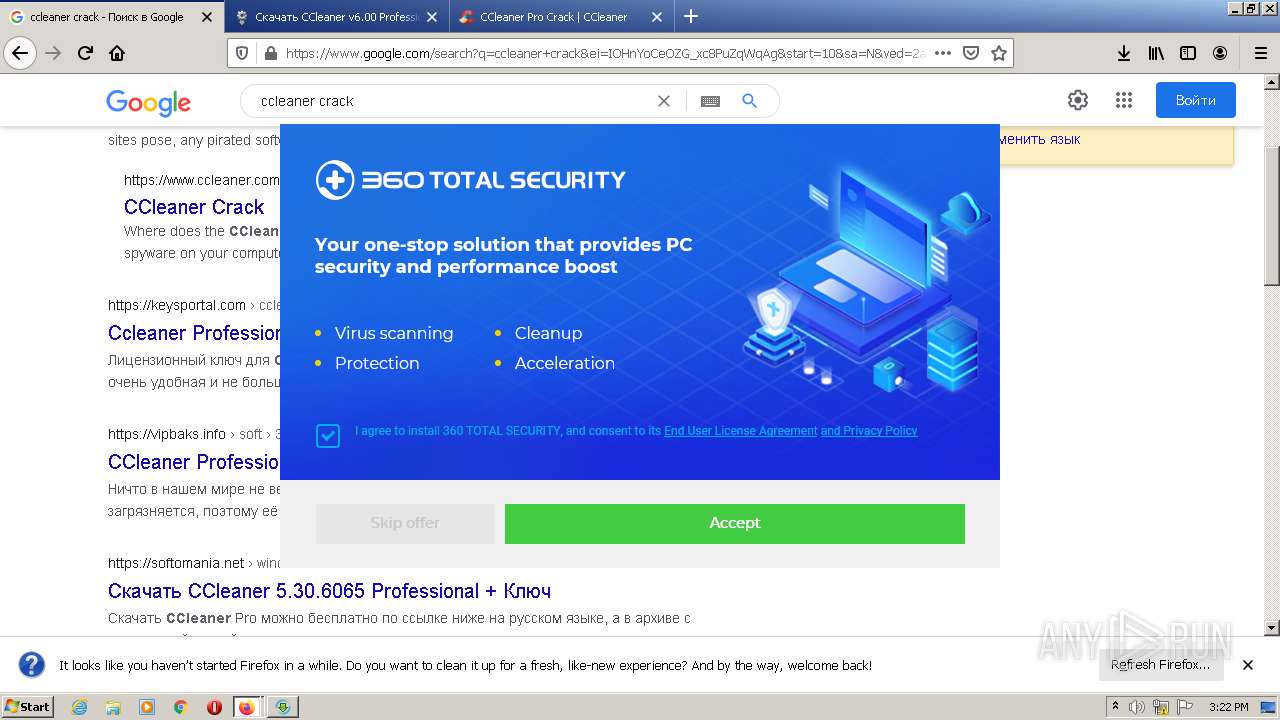
- 360TS_Setup.exe (PID: 4180)
- 360TS_Setup.exe (PID: 4928)
Application was dropped or rewritten from another process
- ccleaner-6-key_id3075252ids1s.exe (PID: 2208)
- ccleaner-6-key_id3075252ids1s.exe (PID: 2504)
- lum_inst.exe (PID: 2240)
- net_updater32.exe (PID: 3692)
- test_wpf.exe (PID: 3220)
- mediaget.exe (PID: 2956)
- mediaget_crashpad_handler.exe (PID: 280)
- QtWebEngineProcess.exe (PID: 3580)
- QtWebEngineProcess.exe (PID: 3348)
- QtWebEngineProcess.exe (PID: 3180)
- QtWebEngineProcess.exe (PID: 2540)
- QtWebEngineProcess.exe (PID: 4524)
- mediaget-admin-proxy.exe (PID: 4336)
- QtWebEngineProcess.exe (PID: 3140)
- antivirus360.exe (PID: 2344)
- luminati-m-controller.exe (PID: 5256)
- test_wpf.exe (PID: 5400)
Actions looks like stealing of personal data
- ccleaner-6-key_id3075252ids1s.exe (PID: 2504)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 444)
- net_updater32.exe (PID: 3692)
- mediaget.exe (PID: 2956)
- mediaget_crashpad_handler.exe (PID: 280)
- QtWebEngineProcess.exe (PID: 3580)
- QtWebEngineProcess.exe (PID: 3348)
- QtWebEngineProcess.exe (PID: 3180)
- QtWebEngineProcess.exe (PID: 3140)
- QtWebEngineProcess.exe (PID: 2540)
- QtWebEngineProcess.exe (PID: 4524)
- antivirus360.exe (PID: 2344)
- luminati-m-controller.exe (PID: 5256)
- 360TS_Setup.exe (PID: 4180)
- 360TS_Setup.exe (PID: 4928)
Changes settings of System certificates
- net_updater32.exe (PID: 3692)
- QtWebEngineProcess.exe (PID: 3580)
Changes the autorun value in the registry
- mediaget.exe (PID: 2956)
SUSPICIOUS
Executable content was dropped or overwritten
- firefox.exe (PID: 2780)
- ccleaner-6-key_id3075252ids1s.exe (PID: 2504)
- lum_inst.exe (PID: 2240)
- lum_inst.tmp (PID: 1552)
- net_updater32.exe (PID: 3692)
- antivirus360.exe (PID: 2344)
- mediaget.exe (PID: 2956)
- luminati-m-controller.exe (PID: 5256)
- 360TS_Setup.exe (PID: 4180)
- 360TS_Setup.exe (PID: 4928)
Drops a file with a compile date too recent
- firefox.exe (PID: 2780)
- ccleaner-6-key_id3075252ids1s.exe (PID: 2504)
- lum_inst.exe (PID: 2240)
- lum_inst.tmp (PID: 1552)
- net_updater32.exe (PID: 3692)
- antivirus360.exe (PID: 2344)
- mediaget.exe (PID: 2956)
- luminati-m-controller.exe (PID: 5256)
- 360TS_Setup.exe (PID: 4180)
- 360TS_Setup.exe (PID: 4928)
Reads the computer name
- ccleaner-6-key_id3075252ids1s.exe (PID: 2504)
- lum_inst.tmp (PID: 1552)
- net_updater32.exe (PID: 3692)
- test_wpf.exe (PID: 3220)
- mediaget.exe (PID: 2956)
- QtWebEngineProcess.exe (PID: 3580)
- antivirus360.exe (PID: 2344)
- luminati-m-controller.exe (PID: 5256)
- test_wpf.exe (PID: 5400)
- 360TS_Setup.exe (PID: 4180)
- 360TS_Setup.exe (PID: 4928)
Reads Microsoft Outlook installation path
- ccleaner-6-key_id3075252ids1s.exe (PID: 2504)
- iexplore.exe (PID: 5860)
Reads internet explorer settings
- ccleaner-6-key_id3075252ids1s.exe (PID: 2504)
Reads default file associations for system extensions
- firefox.exe (PID: 2780)
Checks supported languages
- ccleaner-6-key_id3075252ids1s.exe (PID: 2504)
- lum_inst.exe (PID: 2240)
- lum_inst.tmp (PID: 1552)
- net_updater32.exe (PID: 3692)
- test_wpf.exe (PID: 3220)
- mediaget.exe (PID: 2956)
- mediaget_crashpad_handler.exe (PID: 280)
- QtWebEngineProcess.exe (PID: 3580)
- QtWebEngineProcess.exe (PID: 3348)
- QtWebEngineProcess.exe (PID: 3180)
- antivirus360.exe (PID: 2344)
- QtWebEngineProcess.exe (PID: 2540)
- mediaget-admin-proxy.exe (PID: 4336)
- QtWebEngineProcess.exe (PID: 3140)
- QtWebEngineProcess.exe (PID: 4524)
- luminati-m-controller.exe (PID: 5256)
- test_wpf.exe (PID: 5400)
- 360TS_Setup.exe (PID: 4180)
- 360TS_Setup.exe (PID: 4928)
Creates a software uninstall entry
- ccleaner-6-key_id3075252ids1s.exe (PID: 2504)
Reads Windows owner or organization settings
- lum_inst.tmp (PID: 1552)
Reads the Windows organization settings
- lum_inst.tmp (PID: 1552)
Adds / modifies Windows certificates
- net_updater32.exe (PID: 3692)
- QtWebEngineProcess.exe (PID: 3580)
Reads Environment values
- net_updater32.exe (PID: 3692)
- mediaget.exe (PID: 2956)
- luminati-m-controller.exe (PID: 5256)
Creates files in the program directory
- net_updater32.exe (PID: 3692)
- 360TS_Setup.exe (PID: 4928)
- 360TS_Setup.exe (PID: 4180)
Changes default file association
- ccleaner-6-key_id3075252ids1s.exe (PID: 2504)
- mediaget.exe (PID: 2956)
Starts itself from another location
- 360TS_Setup.exe (PID: 4180)
Creates a directory in Program Files
- 360TS_Setup.exe (PID: 4928)
- 360TS_Setup.exe (PID: 4180)
INFO
Application launched itself
- firefox.exe (PID: 2620)
- firefox.exe (PID: 2780)
- iexplore.exe (PID: 5576)
Reads the computer name
- firefox.exe (PID: 2780)
- firefox.exe (PID: 324)
- firefox.exe (PID: 692)
- firefox.exe (PID: 2704)
- firefox.exe (PID: 2784)
- firefox.exe (PID: 3912)
- firefox.exe (PID: 3272)
- SearchProtocolHost.exe (PID: 444)
- firefox.exe (PID: 3080)
- firefox.exe (PID: 1104)
- WISPTIS.EXE (PID: 1520)
- WISPTIS.EXE (PID: 4440)
- iexplore.exe (PID: 5576)
- iexplore.exe (PID: 5860)
- firefox.exe (PID: 5664)
Checks supported languages
- firefox.exe (PID: 2620)
- firefox.exe (PID: 2780)
- firefox.exe (PID: 324)
- firefox.exe (PID: 692)
- firefox.exe (PID: 2704)
- firefox.exe (PID: 3912)
- firefox.exe (PID: 2784)
- firefox.exe (PID: 3272)
- SearchProtocolHost.exe (PID: 444)
- firefox.exe (PID: 3080)
- firefox.exe (PID: 1104)
- WISPTIS.EXE (PID: 1520)
- WISPTIS.EXE (PID: 4440)
- iexplore.exe (PID: 5860)
- firefox.exe (PID: 5664)
- iexplore.exe (PID: 5576)
Reads CPU info
- firefox.exe (PID: 2780)
Dropped object may contain Bitcoin addresses
- firefox.exe (PID: 2780)
- ccleaner-6-key_id3075252ids1s.exe (PID: 2504)
- iexplore.exe (PID: 5860)
- 360TS_Setup.exe (PID: 4928)
Reads the date of Windows installation
- firefox.exe (PID: 2780)
- iexplore.exe (PID: 5576)
Checks Windows Trust Settings
- firefox.exe (PID: 2780)
- net_updater32.exe (PID: 3692)
- iexplore.exe (PID: 5860)
- iexplore.exe (PID: 5576)
- 360TS_Setup.exe (PID: 4928)
Reads settings of System Certificates
- firefox.exe (PID: 2780)
- net_updater32.exe (PID: 3692)
- mediaget.exe (PID: 2956)
- QtWebEngineProcess.exe (PID: 3580)
- luminati-m-controller.exe (PID: 5256)
- iexplore.exe (PID: 5860)
- iexplore.exe (PID: 5576)
- 360TS_Setup.exe (PID: 4928)
Application was dropped or rewritten from another process
- lum_inst.tmp (PID: 1552)
Creates files in the program directory
- firefox.exe (PID: 2780)
Changes internet zones settings
- iexplore.exe (PID: 5576)
Reads internet explorer settings
- iexplore.exe (PID: 5860)
Changes settings of System certificates
- iexplore.exe (PID: 5860)
Adds / modifies Windows certificates
- iexplore.exe (PID: 5860)
Dropped object may contain TOR URL's
- 360TS_Setup.exe (PID: 4928)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
92
Monitored processes
38
Malicious processes
20
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 280 | C:\Users\admin\MediaGet2\mediaget_crashpad_handler.exe --no-rate-limit "--database=C:\Users\admin\AppData\Local\Media Get LLC\MediaGet2\crashdumps" "--metrics-dir=C:\Users\admin\AppData\Local\Media Get LLC\MediaGet2\crashdumps" "--attachment=C:/Users/admin/AppData/Local/Media Get LLC/MediaGet2/crashdumps/logs/log" "--attachment=C:\Users\admin\AppData\Local\Media Get LLC\MediaGet2\crashdumps\90f12523-0712-462c-3751-a6f03e96cf16.run\__sentry-event" "--attachment=C:\Users\admin\AppData\Local\Media Get LLC\MediaGet2\crashdumps\90f12523-0712-462c-3751-a6f03e96cf16.run\__sentry-breadcrumb1" "--attachment=C:\Users\admin\AppData\Local\Media Get LLC\MediaGet2\crashdumps\90f12523-0712-462c-3751-a6f03e96cf16.run\__sentry-breadcrumb2" --initial-client-data=0x3e8,0x3ec,0x3f0,0x3bc,0x3f4,0x689a7b7c,0x689a7b90,0x689a7ba0 | C:\Users\admin\MediaGet2\mediaget_crashpad_handler.exe | — | mediaget.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 324 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2780.0.807388694\491155416" -parentBuildID 20201112153044 -prefsHandle 1108 -prefMapHandle 892 -prefsLen 1 -prefMapSize 238726 -appdir "C:\Program Files\Mozilla Firefox\browser" - 2780 "\\.\pipe\gecko-crash-server-pipe.2780" 1192 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 444 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe3_ Global\UsGthrCtrlFltPipeMssGthrPipe3 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 692 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2780.6.516496537\375359636" -childID 1 -isForBrowser -prefsHandle 3032 -prefMapHandle 3028 -prefsLen 245 -prefMapSize 238726 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 2780 "\\.\pipe\gecko-crash-server-pipe.2780" 3044 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 1104 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2780.48.1659814251\346001451" -childID 7 -isForBrowser -prefsHandle 6748 -prefMapHandle 4064 -prefsLen 9812 -prefMapSize 238726 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 2780 "\\.\pipe\gecko-crash-server-pipe.2780" 6792 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 1520 | "C:\Windows\SYSTEM32\WISPTIS.EXE" /ManualLaunch; | C:\Windows\SYSTEM32\WISPTIS.EXE | — | net_updater32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Pen and Touch Input Component Exit code: 24 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1552 | "C:\Users\admin\AppData\Local\Temp\is-TH075.tmp\lum_inst.tmp" /SL5="$30136,2213707,121344,C:\Users\admin\AppData\Local\Temp\luminati\lum_inst.exe" /verysilent | C:\Users\admin\AppData\Local\Temp\is-TH075.tmp\lum_inst.tmp | lum_inst.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 100 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2208 | "C:\Users\admin\Downloads\ccleaner-6-key_id3075252ids1s.exe" | C:\Users\admin\Downloads\ccleaner-6-key_id3075252ids1s.exe | — | firefox.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 1.0 Modules
| |||||||||||||||
| 2240 | "C:\Users\admin\AppData\Local\Temp\luminati\lum_inst.exe" /verysilent | C:\Users\admin\AppData\Local\Temp\luminati\lum_inst.exe | ccleaner-6-key_id3075252ids1s.exe | ||||||||||||
User: admin Company: luminati Integrity Level: HIGH Description: luminati Setup Exit code: 100 Version: Modules
| |||||||||||||||
| 2344 | "C:\Users\admin\AppData\Local\Temp\antivirus360\antivirus360.exe" /s | C:\Users\admin\AppData\Local\Temp\antivirus360\antivirus360.exe | ccleaner-6-key_id3075252ids1s.exe | ||||||||||||
User: admin Company: Qihoo 360 Technology Co. Ltd. Integrity Level: HIGH Description: 360 Total Security Online Installer Exit code: 1 Version: 6, 6, 0, 1054 Modules
| |||||||||||||||
Total events
75 280
Read events
74 086
Write events
1 118
Delete events
76
Modification events
| (PID) Process: | (2620) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Launcher |
Value: F23E43D7D2000000 | |||
| (PID) Process: | (2780) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: 9B4843D7D2000000 | |||
| (PID) Process: | (2780) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 0 | |||
| (PID) Process: | (2780) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (2780) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableTelemetry |
Value: 1 | |||
| (PID) Process: | (2780) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableDefaultBrowserAgent |
Value: 0 | |||
| (PID) Process: | (2780) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|ServicesSettingsServer |
Value: https://firefox.settings.services.mozilla.com/v1 | |||
| (PID) Process: | (2780) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|SecurityContentSignatureRootHash |
Value: 97:E8:BA:9C:F1:2F:B3:DE:53:CC:42:A4:E6:57:7E:D6:4D:F4:93:C2:47:B4:14:FE:A0:36:81:8D:38:23:56:0E | |||
| (PID) Process: | (2780) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2780) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000003B010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A80164000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
584
Suspicious files
638
Text files
551
Unknown types
202
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2780 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 2780 | firefox.exe | C:\Users\admin\AppData\Local\Temp\mz_etilqs_wxh41v5377XCkpF | binary | |
MD5:— | SHA256:— | |||
| 2780 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 2780 | firefox.exe | C:\Users\admin\AppData\Local\Temp\mz_etilqs_OyEAZr2ToChtd51 | binary | |
MD5:— | SHA256:— | |||
| 2780 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionstore-backups\recovery.jsonlz4.tmp | jsonlz4 | |
MD5:— | SHA256:— | |||
| 2780 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionstore-backups\recovery.jsonlz4 | jsonlz4 | |
MD5:— | SHA256:— | |||
| 2780 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs.js | text | |
MD5:299A2B747C11E4BDA194E563FEA4A699 | SHA256:94EE461F62E8B4A0A65471A41E10C8C56722B73C0A019D76ACA7F5BAF109813E | |||
| 2780 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 2780 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\urlCache-current.bin | binary | |
MD5:994A33896BB41A278A315D0D796422B6 | SHA256:54EC50A20FFF8CC016710E49437CF6A11D3FE5EE7B28C185E4A9AAFEE2908B63 | |||
| 2780 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
101
TCP/UDP connections
357
DNS requests
397
Threats
26
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2780 | firefox.exe | POST | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gts1c3 | US | der | 472 b | whitelisted |
2780 | firefox.exe | POST | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gts1c3 | US | der | 472 b | whitelisted |
2780 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
2780 | firefox.exe | POST | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gts1c3 | US | der | 471 b | whitelisted |
2780 | firefox.exe | POST | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gts1c3 | US | der | 472 b | whitelisted |
2780 | firefox.exe | POST | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gts1c3 | US | der | 472 b | whitelisted |
2780 | firefox.exe | POST | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gts1c3 | US | der | 472 b | whitelisted |
2780 | firefox.exe | POST | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gts1c3 | US | der | 472 b | whitelisted |
2780 | firefox.exe | POST | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gts1c3 | US | der | 471 b | whitelisted |
2780 | firefox.exe | POST | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gts1c3 | US | der | 472 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2780 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | — | US | whitelisted |
2780 | firefox.exe | 142.250.74.196:443 | www.google.com | Google Inc. | US | whitelisted |
2780 | firefox.exe | 52.35.17.16:443 | location.services.mozilla.com | Amazon.com, Inc. | US | unknown |
— | — | 34.107.221.82:80 | detectportal.firefox.com | — | US | whitelisted |
2780 | firefox.exe | 143.204.215.37:443 | firefox.settings.services.mozilla.com | — | US | malicious |
2780 | firefox.exe | 142.250.186.74:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
2780 | firefox.exe | 52.33.84.190:443 | push.services.mozilla.com | Amazon.com, Inc. | US | unknown |
2780 | firefox.exe | 142.250.185.163:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
2780 | firefox.exe | 13.32.27.5:443 | content-signature-2.cdn.mozilla.net | Amazon.com, Inc. | US | suspicious |
2780 | firefox.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
detectportal.firefox.com |
| whitelisted |
www.google.com |
| malicious |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
firefox.settings.services.mozilla.com |
| whitelisted |
location.services.mozilla.com |
| whitelisted |
locprod2-elb-us-west-2.prod.mozaws.net |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
push.services.mozilla.com |
| whitelisted |
autopush.prod.mozaws.net |
| whitelisted |
content-signature-2.cdn.mozilla.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2780 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
2780 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
2780 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
2780 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
— | — | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
— | — | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
— | — | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
— | — | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
— | — | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
— | — | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
Process | Message |
|---|---|
mediaget.exe | AUTOSELECT OGL
|
mediaget.exe | > __thiscall Application::Application(int &,char *[])
|
mediaget.exe | os version: "6.1.7601v" __ os name: "Windows 7 Version 6.1 (Build 7601: SP 1)"
|
mediaget.exe | > int __thiscall Application::exec(void)
|
mediaget.exe | > __thiscall MediagetServerSettings::MediagetServerSettings(void)
|
mediaget.exe | INSTALL ID: "" _ OLD ID: ""
|
mediaget.exe | reseller - "" installId ""
|
mediaget.exe | > void __thiscall MediagetServerSettings::flushSettings(void)
|