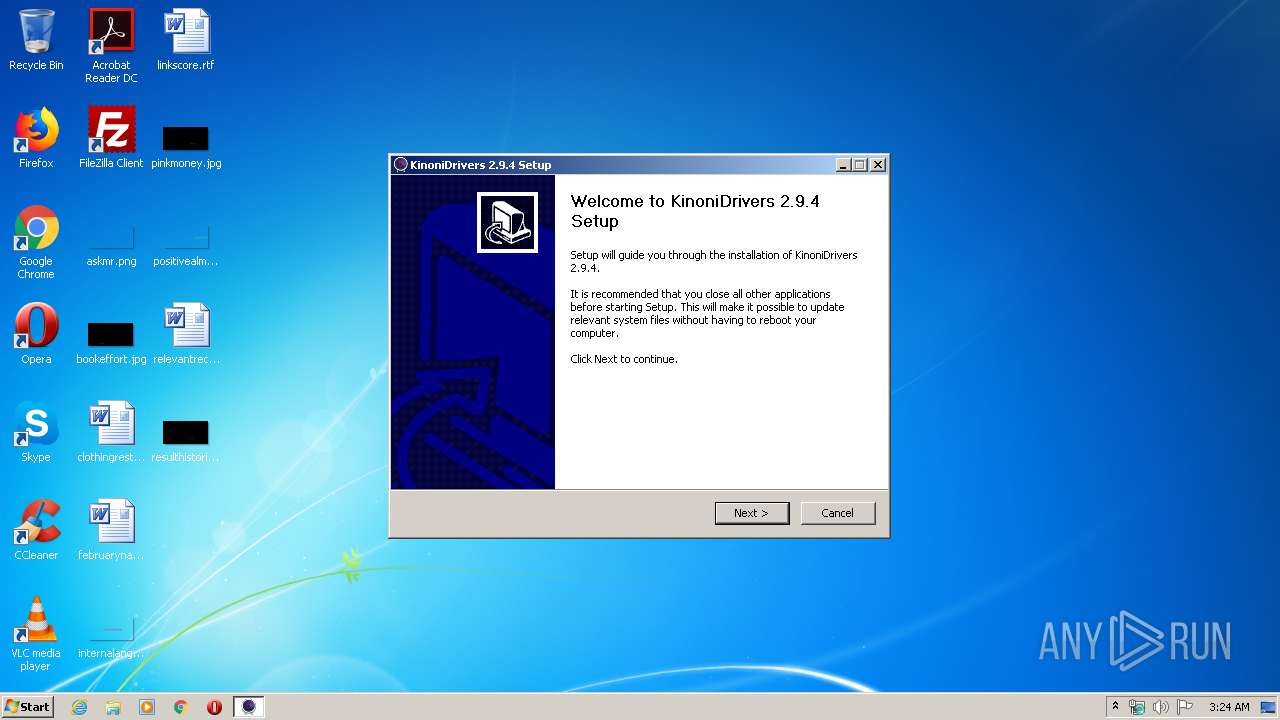
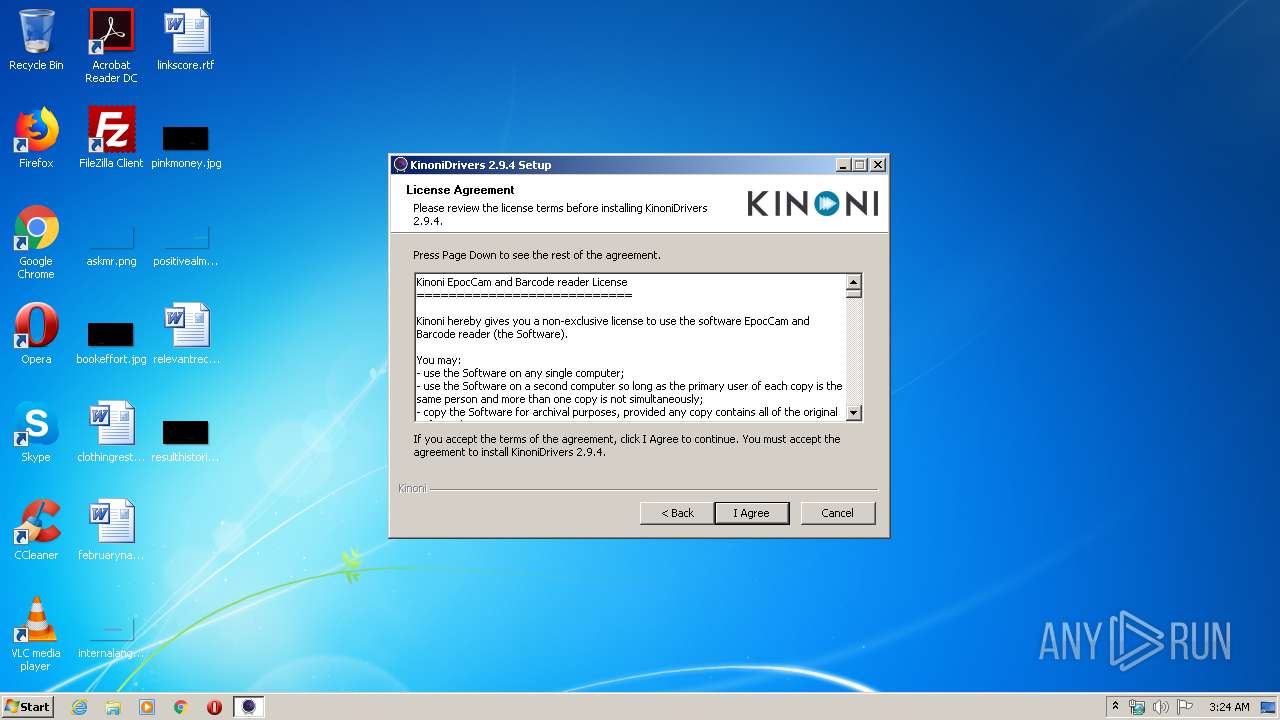
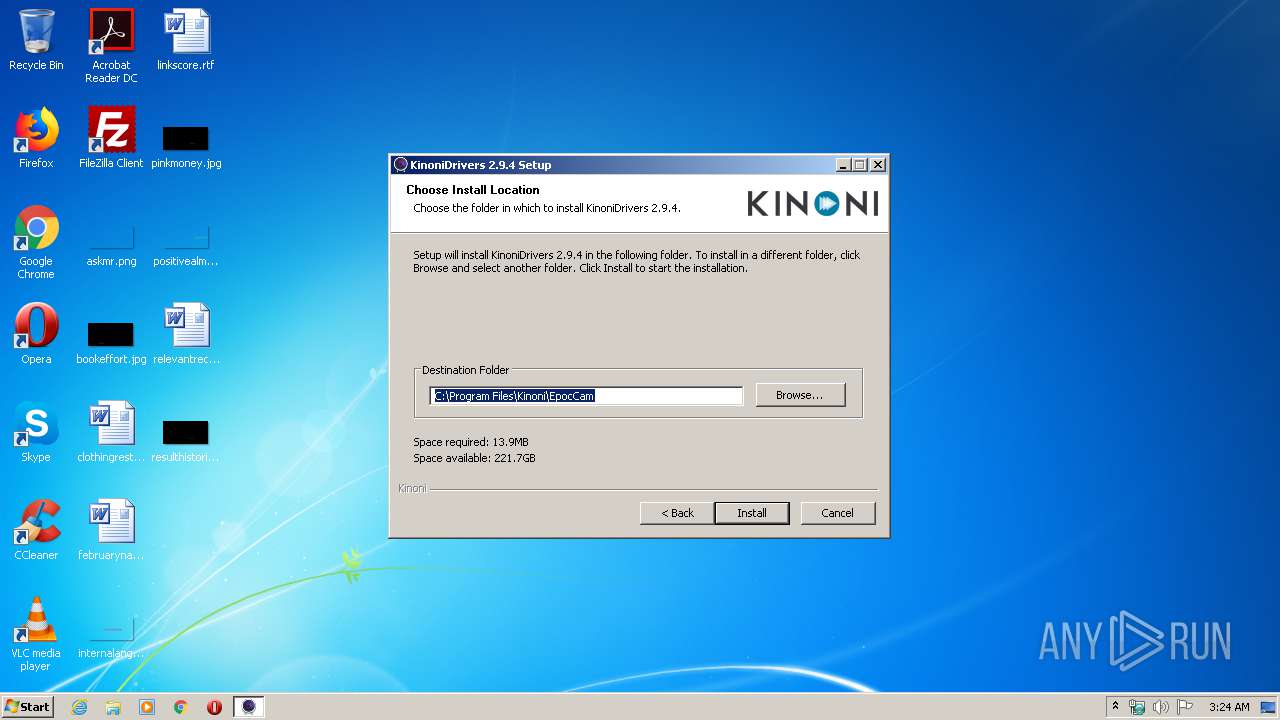
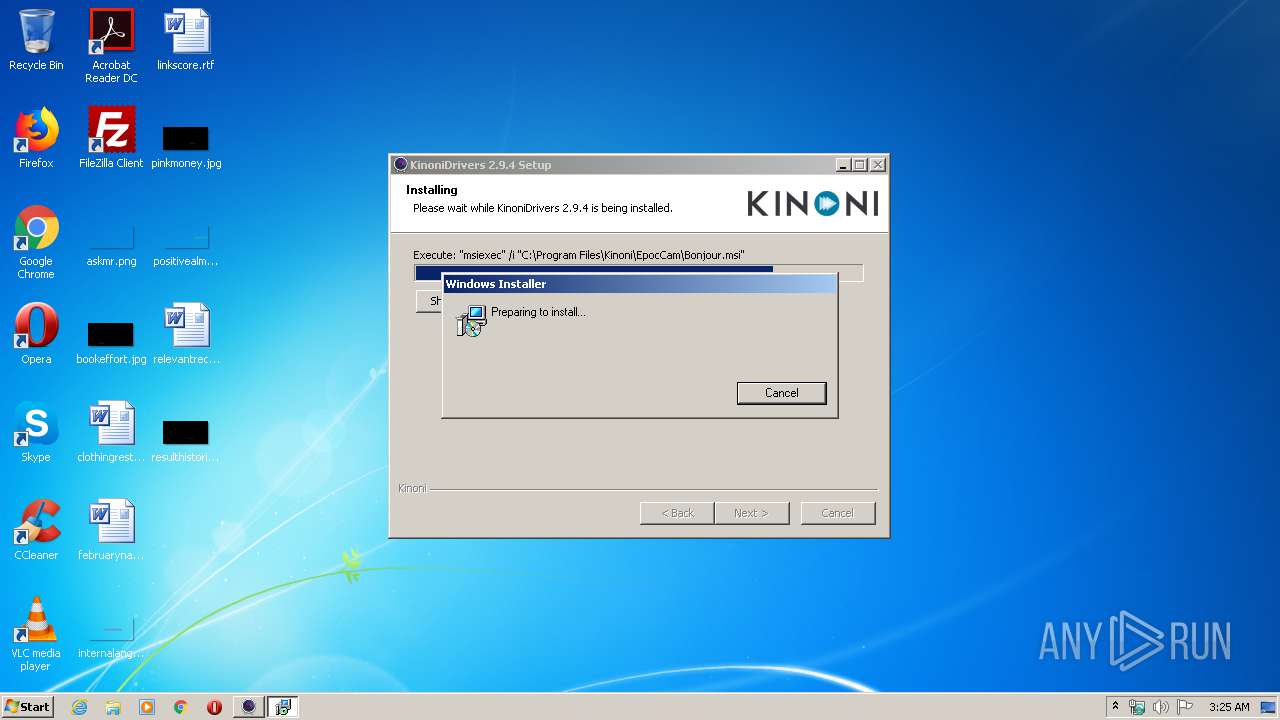
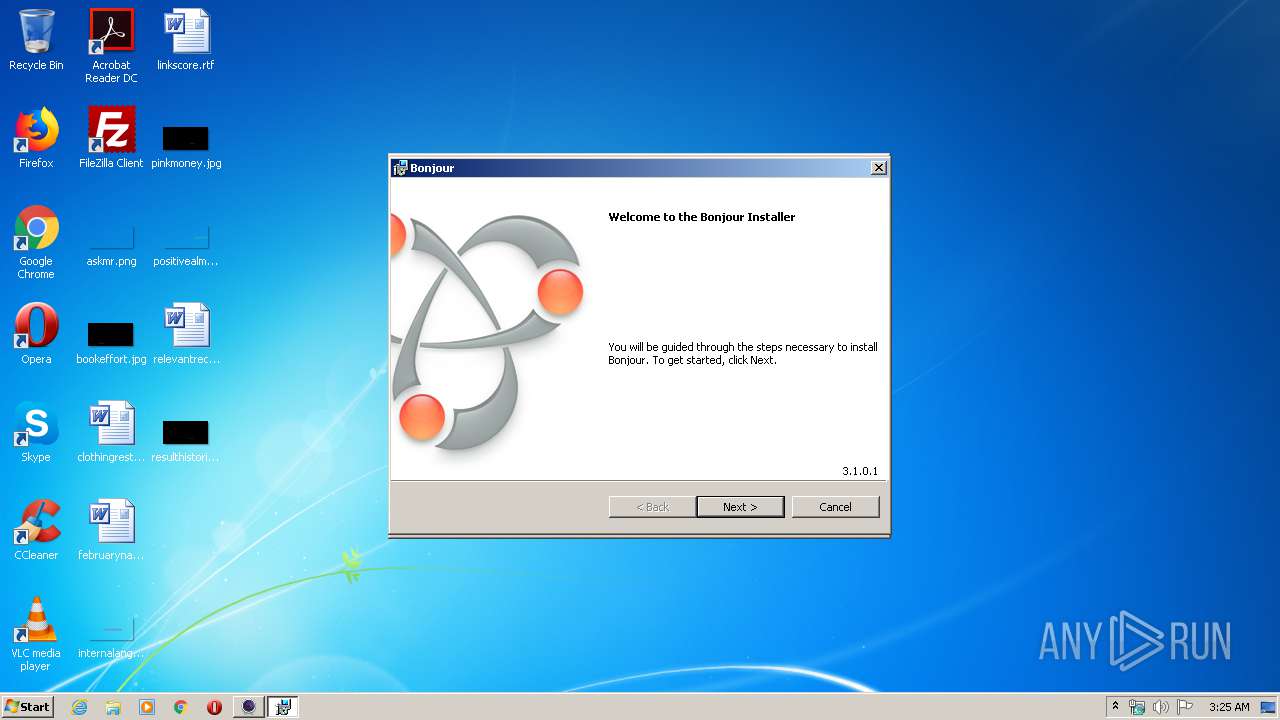
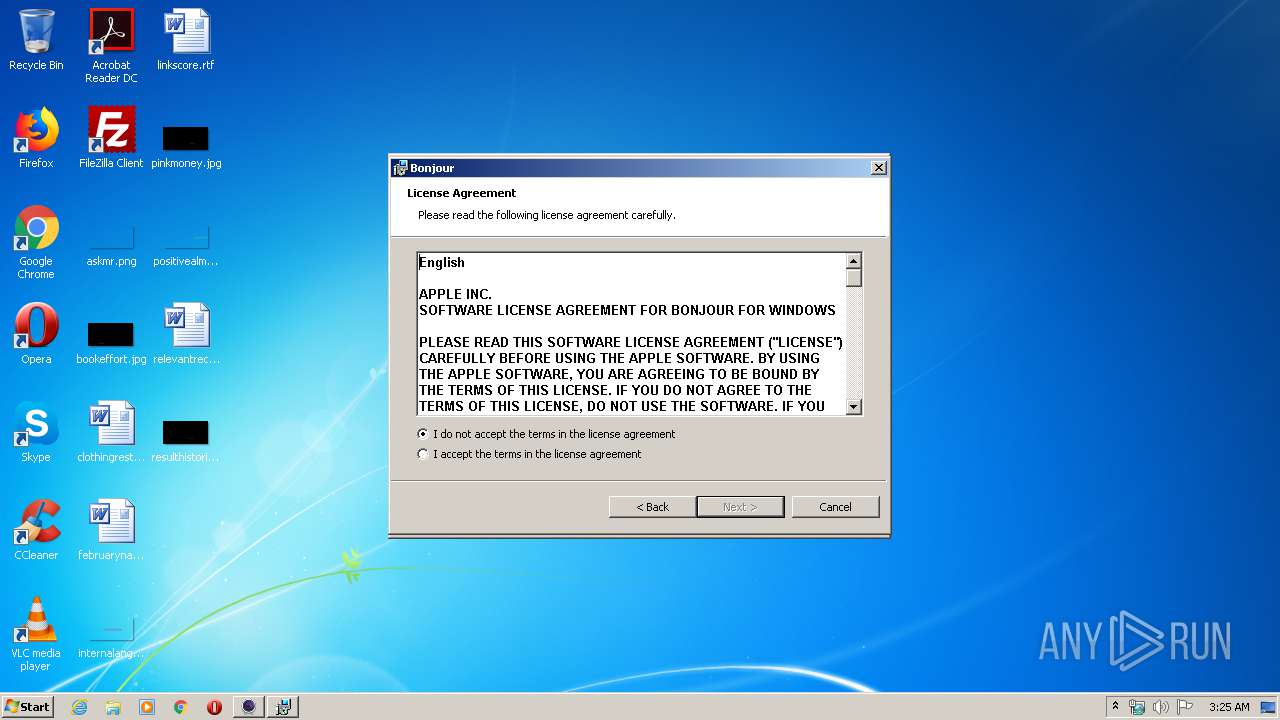
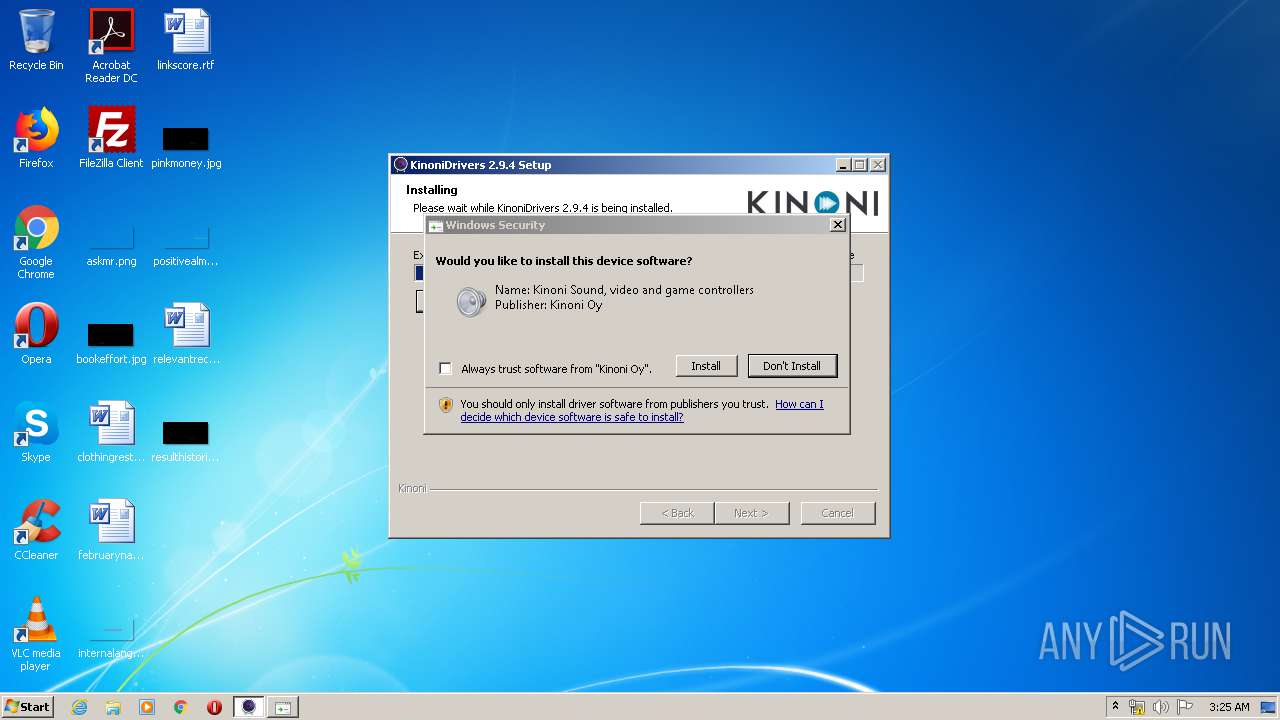
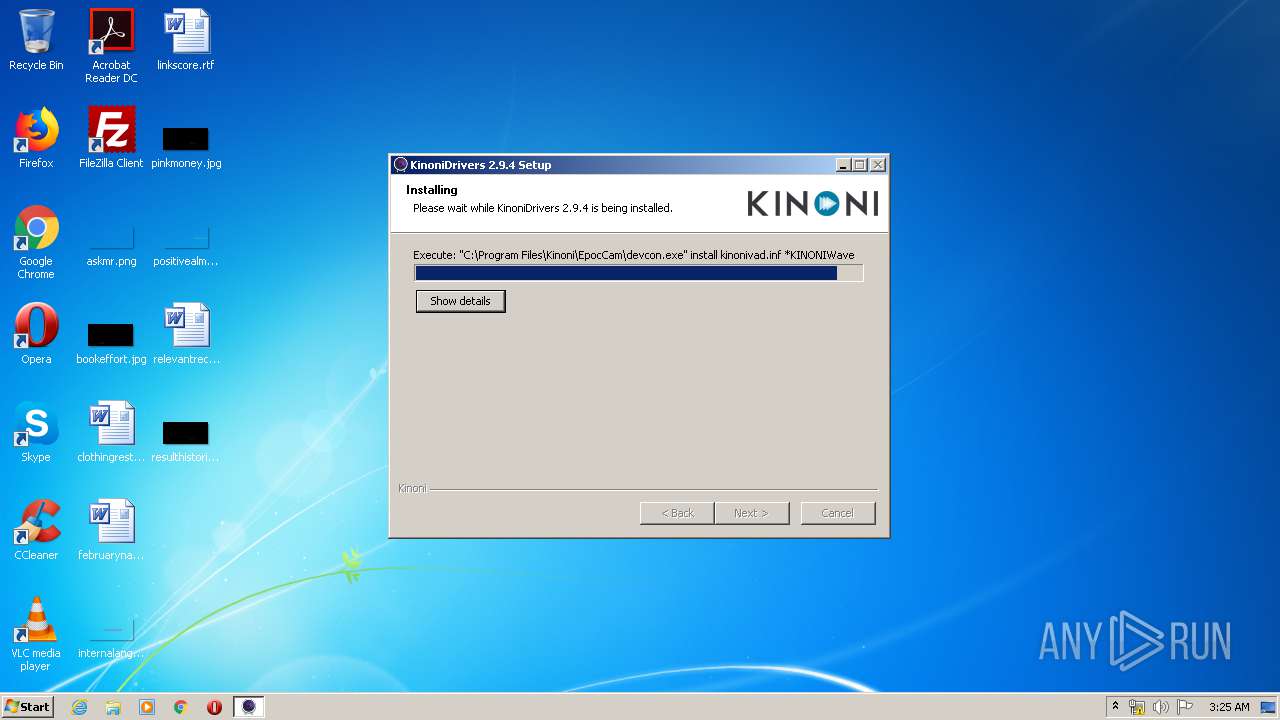
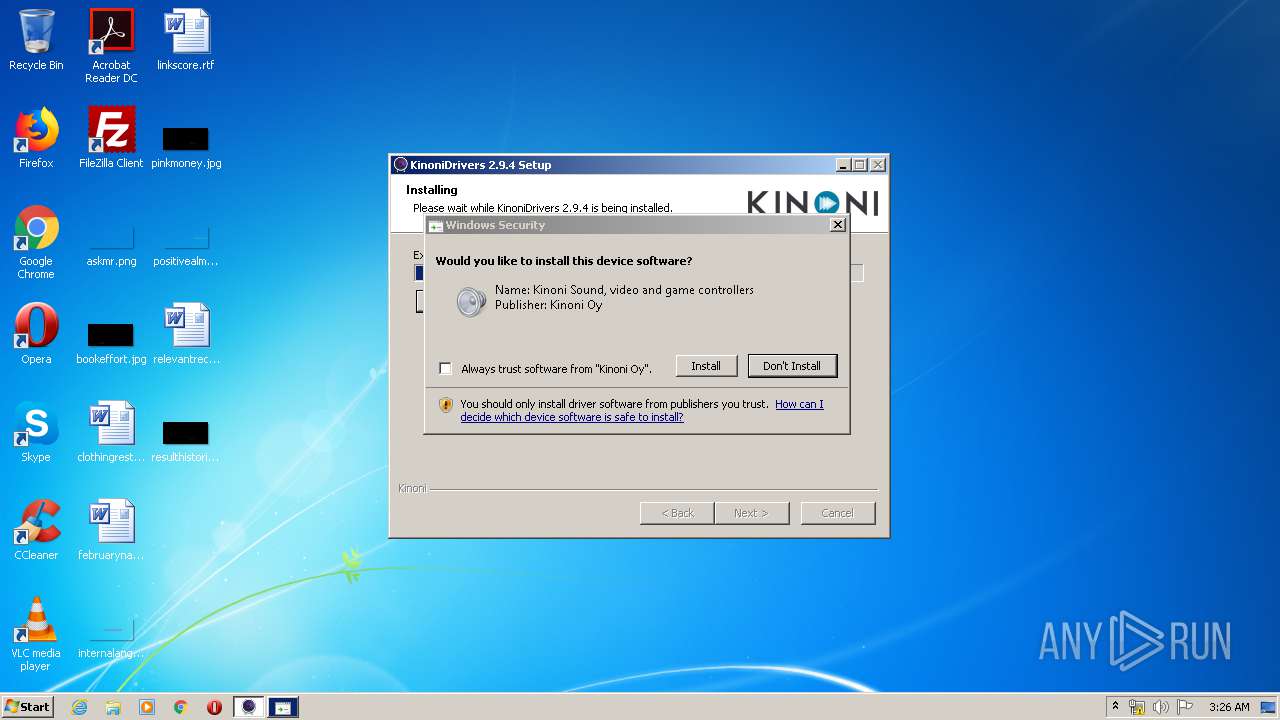
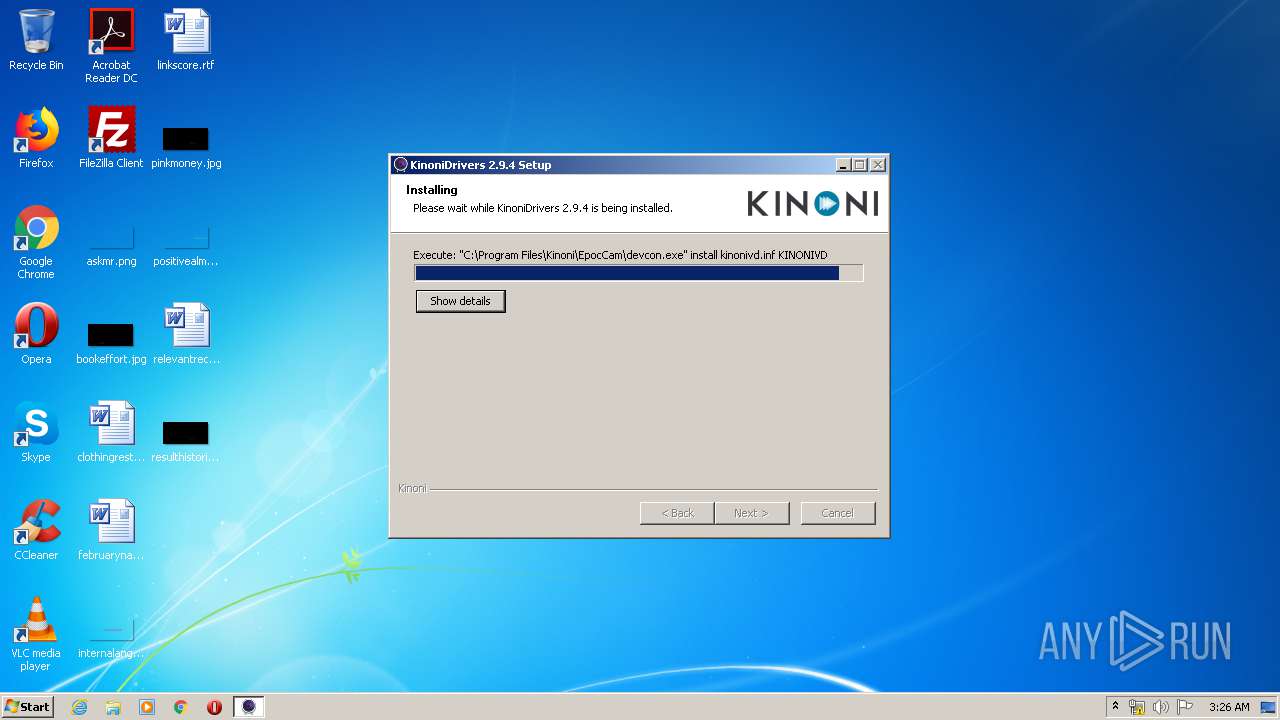
| download: | EpocCamInstaller294.exe |
| Full analysis: | https://app.any.run/tasks/a54595e3-1237-4d69-9014-9c9f1f4fea11 |
| Verdict: | Malicious activity |
| Analysis date: | March 31, 2020, 02:24:26 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 9BF80A3A306ADBA93C9F566F229356E7 |
| SHA1: | ADD851CD0C246D6BB7B511C8AA3326FA2B1BE2A7 |
| SHA256: | D0CC7DD1C4E7DFD70BD1C764CBA973BE677901BF2FCDF3FF9434D3180A3F3532 |
| SSDEEP: | 98304:hV98wuHASmAZS84ZG43oR6b35aSGFysUe:Xkgz84B7psF6e |
MALICIOUS
Application was dropped or rewritten from another process
- nsA7F3.tmp (PID: 1944)
- nsA8DF.tmp (PID: 3324)
- mDNSResponder.exe (PID: 3480)
- devcon.exe (PID: 2716)
- devcon.exe (PID: 3748)
- devcon.exe (PID: 1948)
- devcon.exe (PID: 3248)
- ns1C17.tmp (PID: 2520)
- KinoniSvc.exe (PID: 2428)
- ns1DBE.tmp (PID: 3300)
- KinoniSvc.exe (PID: 1456)
Loads dropped or rewritten executable
- MsiExec.exe (PID: 2900)
- EpocCamInstaller294.exe (PID: 2916)
- iexplore.exe (PID: 2492)
- KinoniSvc.exe (PID: 1456)
- iexplore.exe (PID: 3012)
- svchost.exe (PID: 1052)
Changes settings of System certificates
- devcon.exe (PID: 2716)
- devcon.exe (PID: 3248)
- msiexec.exe (PID: 3028)
SUSPICIOUS
Executable content was dropped or overwritten
- EpocCamInstaller294.exe (PID: 2916)
- msiexec.exe (PID: 2636)
- devcon.exe (PID: 2716)
- DrvInst.exe (PID: 304)
- DrvInst.exe (PID: 2712)
- DrvInst.exe (PID: 3612)
- devcon.exe (PID: 3248)
- DrvInst.exe (PID: 1724)
Starts CMD.EXE for commands execution
- nsA7F3.tmp (PID: 1944)
- nsA8DF.tmp (PID: 3324)
- ns1C17.tmp (PID: 2520)
- ns1DBE.tmp (PID: 3300)
Starts Microsoft Installer
- EpocCamInstaller294.exe (PID: 2916)
Starts SC.EXE for service management
- cmd.exe (PID: 2664)
- cmd.exe (PID: 3040)
- cmd.exe (PID: 2288)
Executed as Windows Service
- vssvc.exe (PID: 1836)
- mDNSResponder.exe (PID: 3480)
- KinoniSvc.exe (PID: 1456)
Creates COM task schedule object
- msiexec.exe (PID: 2636)
Adds / modifies Windows certificates
- devcon.exe (PID: 2716)
- devcon.exe (PID: 3248)
- msiexec.exe (PID: 3028)
Creates files in the Windows directory
- msiexec.exe (PID: 2636)
- DrvInst.exe (PID: 304)
- svchost.exe (PID: 1052)
- DrvInst.exe (PID: 2712)
- DrvInst.exe (PID: 3612)
- DrvInst.exe (PID: 1724)
Executed via COM
- DrvInst.exe (PID: 304)
- DrvInst.exe (PID: 2712)
- DrvInst.exe (PID: 3612)
- DrvInst.exe (PID: 1724)
- DllHost.exe (PID: 1812)
Removes files from Windows directory
- DrvInst.exe (PID: 304)
- svchost.exe (PID: 1052)
- DrvInst.exe (PID: 2712)
- DrvInst.exe (PID: 3612)
- DrvInst.exe (PID: 1724)
Creates files in the driver directory
- DrvInst.exe (PID: 304)
- DrvInst.exe (PID: 2712)
- DrvInst.exe (PID: 3612)
- DrvInst.exe (PID: 1724)
Uses RUNDLL32.EXE to load library
- DrvInst.exe (PID: 304)
- DrvInst.exe (PID: 3612)
Starts Internet Explorer
- EpocCamInstaller294.exe (PID: 2916)
Creates a software uninstall entry
- EpocCamInstaller294.exe (PID: 2916)
Reads Internet Cache Settings
- DllHost.exe (PID: 1812)
Starts application with an unusual extension
- EpocCamInstaller294.exe (PID: 2916)
Creates files in the program directory
- EpocCamInstaller294.exe (PID: 2916)
INFO
Reads settings of System Certificates
- msiexec.exe (PID: 3028)
- iexplore.exe (PID: 2492)
- iexplore.exe (PID: 3012)
Low-level read access rights to disk partition
- vssvc.exe (PID: 1836)
Loads dropped or rewritten executable
- MsiExec.exe (PID: 3424)
- MsiExec.exe (PID: 3576)
Searches for installed software
- msiexec.exe (PID: 2636)
- DrvInst.exe (PID: 304)
- DrvInst.exe (PID: 3612)
Creates a software uninstall entry
- msiexec.exe (PID: 2636)
Creates files in the program directory
- msiexec.exe (PID: 2636)
Application launched itself
- msiexec.exe (PID: 2636)
- iexplore.exe (PID: 2492)
Changes settings of System certificates
- DrvInst.exe (PID: 3612)
- iexplore.exe (PID: 3012)
Reads Internet Cache Settings
- iexplore.exe (PID: 2492)
- iexplore.exe (PID: 3012)
Changes internet zones settings
- iexplore.exe (PID: 2492)
Creates files in the user directory
- iexplore.exe (PID: 3012)
- iexplore.exe (PID: 2492)
Reads internet explorer settings
- iexplore.exe (PID: 3012)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3012)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:12:11 22:50:45+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 24576 |
| InitializedDataSize: | 118784 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x32bf |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.9.4.0 |
| ProductVersionNumber: | 2.9.4.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | ASCII |
| Comments: | Kinoni Driver Installer |
| CompanyName: | Kinoni |
| FileDescription: | Kinoni Driver Installer |
| FileVersion: | 2.9.4 |
| LegalCopyright: | Copyright Kinoni |
| ProductName: | Kinoni Driver Installer |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 11-Dec-2016 21:50:45 |
| Detected languages: |
|
| Comments: | Kinoni Driver Installer |
| CompanyName: | Kinoni |
| FileDescription: | Kinoni Driver Installer |
| FileVersion: | 2.9.4 |
| LegalCopyright: | Copyright Kinoni |
| ProductName: | Kinoni Driver Installer |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000D8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 11-Dec-2016 21:50:45 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00005E59 | 0x00006000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.42419 |
.rdata | 0x00007000 | 0x00001246 | 0x00001400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.0004 |
.data | 0x00009000 | 0x0001A818 | 0x00000400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.21193 |
.ndata | 0x00024000 | 0x00009000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rsrc | 0x0002D000 | 0x00004D00 | 0x00004E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.47437 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.28813 | 1070 | UNKNOWN | English - United States | RT_MANIFEST |
102 | 2.71813 | 180 | UNKNOWN | English - United States | RT_DIALOG |
103 | 1.7815 | 20 | UNKNOWN | English - United States | RT_GROUP_ICON |
105 | 2.68372 | 512 | UNKNOWN | English - United States | RT_DIALOG |
106 | 2.91148 | 248 | UNKNOWN | English - United States | RT_DIALOG |
111 | 2.89887 | 238 | UNKNOWN | English - United States | RT_DIALOG |
202 | 2.63447 | 160 | UNKNOWN | English - United States | RT_DIALOG |
203 | 2.47654 | 268 | UNKNOWN | English - United States | RT_DIALOG |
205 | 2.62576 | 492 | UNKNOWN | English - United States | RT_DIALOG |
206 | 2.86626 | 228 | UNKNOWN | English - United States | RT_DIALOG |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
ole32.dll |
Total processes
80
Monitored processes
37
Malicious processes
10
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{56bd0b9d-474b-3af0-6e8e-79196cf9cb15}\kinonivad.inf" "0" "6262814e7" "000005AC" "WinSta0\Default" "000003FC" "208" "c:\program files\kinoni\epoccam" | C:\Windows\system32\DrvInst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 376 | sc.exe delete KinoniSvc | C:\Windows\system32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1052 | C:\Windows\system32\svchost.exe -k NetworkService | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1456 | "C:\Program Files\Kinoni\EpocCam\KinoniSvc.exe" | C:\Program Files\Kinoni\EpocCam\KinoniSvc.exe | services.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Modules
| |||||||||||||||
| 1724 | DrvInst.exe "2" "211" "ROOT\MEDIA\0001" "C:\Windows\INF\oem5.inf" "kinonivd.inf:AvsCamera.Device.NTx86:AvsCamera:21.37.17.102:kinonivd" "6baffe4eb" "000003BC" "000005D4" "000005C8" | C:\Windows\system32\DrvInst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1812 | C:\Windows\system32\DllHost.exe /Processid:{F9717507-6651-4EDB-BFF7-AE615179BCCF} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1828 | sc.exe start KinoniSvc | C:\Windows\system32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1836 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1944 | "C:\Users\admin\AppData\Local\Temp\nsb720D.tmp\nsA7F3.tmp" C:\Windows\system32\cmd.exe /C sc.exe stop KinoniSvc | C:\Users\admin\AppData\Local\Temp\nsb720D.tmp\nsA7F3.tmp | — | EpocCamInstaller294.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1060 Modules
| |||||||||||||||
| 1948 | "C:\Program Files\Kinoni\EpocCam\devcon.exe" remove KINONIVD | C:\Program Files\Kinoni\EpocCam\devcon.exe | — | EpocCamInstaller294.exe | |||||||||||
User: admin Company: Windows (R) Win 7 DDK provider Integrity Level: HIGH Description: Windows Setup API Exit code: 0 Version: 6.1.7600.16385 built by: WinDDK Modules
| |||||||||||||||
Total events
5 147
Read events
2 572
Write events
2 555
Delete events
20
Modification events
| (PID) Process: | (3028) msiexec.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3028) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\CDD4EEAE6000AC7F40C3802C171E30148030C072 |
| Operation: | write | Name: | Blob |
Value: 0F0000000100000014000000391BE92883D52509155BFEAE27B9BD340170B76B030000000100000014000000CDD4EEAE6000AC7F40C3802C171E30148030C0720B000000010000004A0000004D006900630072006F0073006F0066007400200052006F006F007400200043006500720074006900660069006300610074006500200041007500740068006F007200690074007900000069000000010000000E000000300C060A2B0601040182373C030220000000010000009D0500003082059930820381A003020102021079AD16A14AA0A5AD4C7358F407132E65300D06092A864886F70D0101050500305F31133011060A0992268993F22C6401191603636F6D31193017060A0992268993F22C64011916096D6963726F736F6674312D302B060355040313244D6963726F736F667420526F6F7420436572746966696361746520417574686F72697479301E170D3031303530393233313932325A170D3231303530393233323831335A305F31133011060A0992268993F22C6401191603636F6D31193017060A0992268993F22C64011916096D6963726F736F6674312D302B060355040313244D6963726F736F667420526F6F7420436572746966696361746520417574686F7269747930820222300D06092A864886F70D01010105000382020F003082020A0282020100F35DFA8067D45AA7A90C2C9020D035083C7584CDB707899C89DADECEC360FA91685A9E94712918767CC2E0C82576940E58FA043436E6DFAFF780BAE9580B2B93E59D05E3772291F734643C22911D5EE10990BC14FEFC755819E179B70792A3AE885908D89F07CA0358FC68296D32D7D2A8CB4BFCE10B48324FE6EBB8AD4FE45C6F139499DB95D575DBA81AB79491B4775BF5480C8F6A797D1470047D6DAF90F5DA70D847B7BF9B2F6CE705B7E11160AC7991147CC5D6A6E4E17ED5C37EE592D23C00B53682DE79E16DF3B56EF89F33C9CB527D739836DB8BA16BA295979BA3DEC24D26FF0696672506C8E7ACE4EE1233953199C835084E34CA7953D5B5BE6332594036C0A54E044D3DDB5B0733E458BFEF3F5364D842593557FD0F457C24044D9ED6387411972290CE684474926FD54B6FB086E3C73642A0D0FCC1C05AF9A361B9304771960A16B091C04295EF107F286AE32A1FB1E4CD033F777104C720FC490F1D4588A4D7CB7E88AD8E2DEC45DBC45104C92AFCEC869E9A11975BDECE5388E6E2B7FDAC95C22840DBEF0490DF813339D9B245A5238706A5558931BB062D600E41187D1F2EB597CB11EB15D524A594EF151489FD4B73FA325BFCD13300F95962700732EA2EAB402D7BCADD21671B30998F16AA23A841D1B06E119B36C4DE40749CE15865C1601E7A5B38C88FBB04267CD41640E5B66B6CAA86FD00BFCEC1350203010001A351304F300B0603551D0F0404030201C6300F0603551D130101FF040530030101FF301D0603551D0E041604140EAC826040562797E52513FC2AE10A539559E4A4301006092B06010401823715010403020100300D06092A864886F70D01010505000382020100C5114D033A60DD5D5211778FB2BB36C8B205BFB4B7A8D8209D5C1303B61C22FA061335B6C863D49A476F2657D255F104B1265FD6A95068A0BCD2B86ECCC3E9ACDF19CD78AC5974AC663436C41B3E6C384C330E30120DA326FE515300FFAF5A4E840D0F1FE46D052E4E854B8D6C336F54D264ABBF50AF7D7A39A037ED63030FFC1306CE1636D4543B951B51623AE54D17D40539929A27A85BAABDECBBBEE3208960716C56B3A513D06D0E237E9503ED683DF2D863B86B4DB6E830B5E1CA944BF7A2AA5D9930B23DA7C2516C28200124272B4B00B79D116B70BEB21082BC0C9B68D08D3B2487AA9928729D335F5990BDF5DE939E3A625A3439E288551DB906B0C1896B2DD769C319123684D0C9A0DAFF2F6978B2E57ADAEBD70CC0F7BD6317B8391338A2365B7BF285566A1D6462C138E2AABF5166A294F5129C6622106BF2B730922DF229F03D3B144368A2F19C2937CBCE3820256D7C67F37E24122403088147ECA59E97F518D7CFBBD5EF7696EFFDCEDB569D95A042F99758E1D73122D35F59E63E6E2200EA4384B625DBD9F3085668C0646B1D7CECB693A262576E2ED8E7588FC4314926DDDE293587F53071705B143C69BD89127DEB2EA3FED87F9E825A520A2BC1432BD930889FC810FB898DE6A18575337E6C9EDB7313646269A52F7DCA966D9FF8044D30923D6E211421C93DE0C3FD8A6B9D4AFDD1A19D9943773FB0DA | |||
| (PID) Process: | (3028) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\A43489159A520F0D93D032CCAF37E7FE20A8B419 |
| Operation: | write | Name: | Blob |
Value: 0F00000001000000100000008B3C3087B7056F5EC5DDBA91A1B901F069000000010000000E000000300C060A2B0601040182373C03020B00000001000000320000004D006900630072006F0073006F0066007400200052006F006F007400200041007500740068006F0072006900740079000000030000000100000014000000A43489159A520F0D93D032CCAF37E7FE20A8B41920000000010000001604000030820412308202FAA003020102020F00C1008B3C3C8811D13EF663ECDF40300D06092A864886F70D01010405003070312B3029060355040B1322436F70797269676874202863292031393937204D6963726F736F667420436F72702E311E301C060355040B13154D6963726F736F667420436F72706F726174696F6E3121301F060355040313184D6963726F736F667420526F6F7420417574686F72697479301E170D3937303131303037303030305A170D3230313233313037303030305A3070312B3029060355040B1322436F70797269676874202863292031393937204D6963726F736F667420436F72702E311E301C060355040B13154D6963726F736F667420436F72706F726174696F6E3121301F060355040313184D6963726F736F667420526F6F7420417574686F7269747930820122300D06092A864886F70D01010105000382010F003082010A0282010100A902BDC170E63BF24E1B289F97785E30EAA2A98D255FF8FE954CA3B7FE9DA2203E7C51A29BA28F60326BD1426479EEAC76C954DAF2EB9C861C8F9F8466B3C56B7A6223D61D3CDE0F0192E896C4BF2D669A9A682699D03A2CBF0CB55826C146E70A3E38962CA92839A8EC498342E3840FBB9A6C5561AC827CA1602D774CE999B4643B9A501C310824149FA9E7912B18E63D986314605805659F1D375287F7A7EF9402C61BD3BF5545B38980BF3AEC54944EAEFDA77A6D744EAF18CC96092821005790606937BB4B12073C56FF5BFBA4660A08A6D2815657EFB63B5E16817704DAF6BEAE8095FEB0CD7FD6A71A725C3CCABCF008A32230B30685C9B320771385DF0203010001A381A83081A53081A20603551D0104819A30819780105BD070EF69729E23517E14B24D8EFFCBA1723070312B3029060355040B1322436F70797269676874202863292031393937204D6963726F736F667420436F72702E311E301C060355040B13154D6963726F736F667420436F72706F726174696F6E3121301F060355040313184D6963726F736F667420526F6F7420417574686F72697479820F00C1008B3C3C8811D13EF663ECDF40300D06092A864886F70D0101040500038201010095E80BC08DF3971835EDB80124D87711F35C60329F9E0BCB3E0591888FC93AE621F2F057932CB5A047C862EFFCD7CC3B3B5AA9365469FE246D3FC9CCAADE057CDD318D3D9F10706ABBFE124F1869C0FCD043E3115A204FEA627BAFAA19C82B37252DBE65A1128A250F63A3F7541CF921C9D615F352AC6E433207FD8217F8E5676C0D51F6BDF152C7BDE7C430FC203109881D95291A4DD51D02A5F180E003B45BF4B1DDC857EE6549C75254B6B4032812FF90D6F0088F7EB897C5AB372CE47AE4A877E376A000D06A3FC1D2368AE04112A8356A1B6ADB35E1D41C04E4A84504C85A33386E4D1C0D62B70AA28CD3D5543F46CD1C55A670DB123A8793759FA7D2A0 | |||
| (PID) Process: | (3028) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\7F88CD7223F3C813818C994614A89C99FA3B5247 |
| Operation: | write | Name: | Blob |
Value: 0F0000000100000010000000D67576F5521D1CCAB52E9215E0F9F7430B00000001000000400000004D006900630072006F0073006F00660074002000410075007400680065006E007400690063006F0064006500280074006D002900200052006F006F0074000000090000000100000016000000301406082B0601050507030406082B060105050703030300000001000000140000007F88CD7223F3C813818C994614A89C99FA3B52472000000001000000DA030000308203D6308202BEA003020102020101300D06092A864886F70D01010405003050310B3009060355040613025553310D300B060355040A13044D53465431323030060355040313294D6963726F736F66742041757468656E7469636F646528746D2920526F6F7420417574686F72697479301E170D3935303130313038303030315A170D3939313233313233353935395A3050310B3009060355040613025553310D300B060355040A13044D53465431323030060355040313294D6963726F736F66742041757468656E7469636F646528746D2920526F6F7420417574686F7269747930820122300D06092A864886F70D01010105000382010F003082010A0282010100DF08BAE33F6E649BF589AF28964A078F1B2E8B3E1DFCB88069A3A1CEDBDFB08E6C8976294FCA603539AD7232E00BAE293D4C16D94B3C9DDAC5D3D109C92C6FA6C2605345DD4BD155CD031CD2595624F3E578D807CCD8B31F903FC01A71501D2DA712086D7CB0866CC7BA853207E1616FAF03C56DE5D6A18F36F6C10BD13E69974872C97FA4C8C24A4C7EA1D194A6D7DCEB05462EB818B4571D8649DB694A2C21F55E0F542D5A43A97A7E6A8E504D2557A1BF1B1505437B2C058DBD3D038C93227D63EA0A5705060ADB6198652D4749A8E7E656755CB8640863A9304066B2F9B6E334E86730E1430B87FFC9BE72105E23F09BA74865BF09887BCD72BC2E799B7B0203010001A381BA3081B7300D0603551D0A040630040302078030320603550403042B13294D6963726F736F66742041757468656E7469636F646528746D2920526F6F7420417574686F7269747930720603551D01046B306980101A1BE75B9FFD8C2AC339AE0C622E5332A1523050310B3009060355040613025553310D300B060355040A13044D53465431323030060355040313294D6963726F736F66742041757468656E7469636F646528746D2920526F6F7420417574686F72697479820101300D06092A864886F70D010104050003820101002DC9E2F6129E5D5667FAFA4B9A7EDC29565C80140228856E26F3CD58DA5080C5F819B3A67CE29D6B5F3B8F2274E61804FC4740D87A3F3066F012A4D1EB1DE7B6F498AB5322865158EE230976E41D455C4BFF4CE302500113CC41A45297D486D5C4FE8383657DEABEA2683BC1B12998BFA2A5FC9DD384EE701750F30BFA3CEFA9278B91B448C845A0E101424B4476041CC219A28E6B2098C4DD02ACB4D2A20E8D5DB9368E4A1B5D6C1AE2CB007F10F4B295EFE3E8FFA17358A9752CA2499585FECCDA448AC21244D244C8A5A21FA95A8E56C2C37BCF4260DC821FFBCE74067ED6F1AC196A4F745CC51566316CC16271910F595B7D2A821ADFB1B4D81D37DE0D0F | |||
| (PID) Process: | (3028) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\3B1EFD3A66EA28B16697394703A72CA340A05BD5 |
| Operation: | write | Name: | Blob |
Value: 0F000000010000002000000008FBA831C08544208F5208686B991CA1B2CFC510E7301784DDF1EB5BF039323969000000010000000E000000300C060A2B0601040182373C03020B00000001000000540000004D006900630072006F0073006F0066007400200052006F006F007400200043006500720074006900660069006300610074006500200041007500740068006F0072006900740079002000320030003100300000000300000001000000140000003B1EFD3A66EA28B16697394703A72CA340A05BD52000000001000000F1050000308205ED308203D5A003020102021028CC3A25BFBA44AC449A9B586B4339AA300D06092A864886F70D01010B0500308188310B3009060355040613025553311330110603550408130A57617368696E67746F6E3110300E060355040713075265646D6F6E64311E301C060355040A13154D6963726F736F667420436F72706F726174696F6E31323030060355040313294D6963726F736F667420526F6F7420436572746966696361746520417574686F726974792032303130301E170D3130303632333231353732345A170D3335303632333232303430315A308188310B3009060355040613025553311330110603550408130A57617368696E67746F6E3110300E060355040713075265646D6F6E64311E301C060355040A13154D6963726F736F667420436F72706F726174696F6E31323030060355040313294D6963726F736F667420526F6F7420436572746966696361746520417574686F72697479203230313030820222300D06092A864886F70D01010105000382020F003082020A0282020100B9089E28E4E4EC064E5068B341C57BEBAEB68EAF81BA22441F6534694CBE704017F2167BE279FD86ED0D39F41BA8AD92901ECB3D768F5AD9B591102E3C058D8A6D2454E71FED56AD83B4509C15A51774885920FC08C58476D368D46F2878CE5CB8F3509044FFE3635FBEA19A2C961504D607FE1E8421E0423111C4283694CF50A4629EC9D6AB7100B25B0CE696D40A2496F5FFC6D5B71BD7CBB72162AF12DCA15D37E31AFB1A4698C09BC0E7631F2A0893027E1E6A8EF29F1889E42285A2B1845740FFF50ED86F9CEDE2453101CD17E97FB08145E3AA214026A172AAA74F3C01057EEE8358B15E06639962917882B70D930C246AB41BDB27EC5F95043F934A30F59718B3A7F919A793331D01C8DB22525CD725C946F9A2FB875943BE9B62B18D2D86441A46AC78617E3009FAAE89C4412A2266039139459CC78B0CA8CA0D2FFB52EA0CF76333239DFEB01FAD67D6A75003C6047063B52CB1865A43B7FBAEF96E296E21214126068CC9C3EEB0C28593A1B985D9E6326C4B4C3FD65DA3E5B59D77C39CC055B77400E3B838AB839750E19A42241DC6C0A330D11A5AC85234F773F1C7181F33AD7AECCB4160F3239420C24845AC5C51C62E80C2E27715BD8587ED369D9691EE00B5A370EC9FE38D80688376BAAF5D70522216E266FBBAB3C5C2F73E2F77A6CADEC1A6C6484CC3375123D327D7B84E7096F0A14476AF78CF9AE166130203010001A351304F300B0603551D0F040403020186300F0603551D130101FF040530030101FF301D0603551D0E04160414D5F656CB8FE8A25C6268D13D94905BD7CE9A18C4301006092B06010401823715010403020100300D06092A864886F70D01010B05000382020100ACA5968CBFBBAEA6F6D7718743315688FD1C32715B35B7D4F091F2AF37E214F1F30226053E16147F14BAB84FFB89B2B2E7D409CC6DB95B3B64657066B7F2B15ADF1A02F3F551B8676D79F3BF567BE484B92B1E9B409C2634F947189869D81CD7B6D1BF8F61C267C4B5EF60438E101B3649E420CAADA7C1B1276509F8CDF55B2AD08433F3EF1FF2F59C0B589337A075A0DE72DE6C752A6622F58C0630569F40B930AA40771582D78BECC0D3B2BD83C5770C1EAEAF1953A04D79719F0FAF30CE67F9D62CCC22417A07F2974218CE59791055DE6F10E4B8DA836640160968235B972E269A02BB578CC5B8BA69623280899EA1FDC0927C7B2B3319842A63C5006862FA9F478D997A453AA7E9EDEE6942B5F3819B4756107BFC7036841873EAEFF9974D9E3323DD260BBA2AB73F44DC8327FFBD61592B11B7CA4FDBC58B0C1C31AE32F8F8B942F77FDC619A76B15A04E1113D6645B71871BEC92485D6F3D4BA41345D122D25B98DA613486D4BB0077D99930961817457268AAB69E3E4D9C788CC24D8EC52245C1EBC9114E296DEEB0ADA9EDD5FB35BDBD482ECC620508725403AFBC7EECDFE33E56EC3840955032539C0E9355D6531A8F6BFA009CD29C7B336322EDC95F383C15ACF8B8DF6EAB321F8A4ED1E310EB64C11AB600BA412232217A3366482910412E0AB6F1ECB500561B440FF598671D1D533697CA9738A38D7640CF169 | |||
| (PID) Process: | (3028) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\245C97DF7514E7CF2DF8BE72AE957B9E04741E85 |
| Operation: | write | Name: | Blob |
Value: 0F00000001000000100000009DF0D13100123AECA770130F4AD8D209030000000100000014000000245C97DF7514E7CF2DF8BE72AE957B9E04741E8509000000010000000C000000300A06082B060105050703080B00000001000000320000004D006900630072006F0073006F00660074002000540069006D0065007300740061006D007000200052006F006F00740000002000000001000000B1020000308202AD30820216020101300D06092A864886F70D010104050030819E3120301E060355040A13174D6963726F736F6674205472757374204E6574776F726B311E301C060355040B13154D6963726F736F667420436F72706F726174696F6E312D302B060355040B13244D6963726F736F66742054696D65205374616D70696E67205365727669636520526F6F74312B3029060355040B1322436F70797269676874202863292031393937204D6963726F736F667420436F72702E301E170D3937303531333136313235395A170D3939313233303233353935395A30819E3120301E060355040A13174D6963726F736F6674205472757374204E6574776F726B311E301C060355040B13154D6963726F736F667420436F72706F726174696F6E312D302B060355040B13244D6963726F736F66742054696D65205374616D70696E67205365727669636520526F6F74312B3029060355040B1322436F70797269676874202863292031393937204D6963726F736F667420436F72702E30819F300D06092A864886F70D010101050003818D0030818902818100B75A38F51F37CCA943C4DC2418BEF28552B41D5B5F18B90B8F4B6DA8FFCD40506CD3A0D35C47C2B9F786E4CD7D350569371FAF3DDD1FFD8F1534C2C479CC59748A6F8C0EC3E811EB8438479853E1F10C0DE4010CF01B1E20DA2A7A3DC215528E8AFF7B32BF581E25988326CB8AC9C4071424BC499ED77AB3871A2533BC6D08470203010001300D06092A864886F70D010104050003818100505BC56B6F8D525B0DC9BDAC347398CA0A87CAAE4C4ABA14A4EB52709521E0B5A1604EF743025101AF1E3A70CEBF18B686289967EB08E897405C1682FDB825FB366F6F763EC54C8EE2A751FACAC163BA5E8324470B9372F6449ACEA7953A8F50109E1DB15916ABCF3EDF838BC7FAC36BDC649F402B1F452404AE492FF6DF0C91 | |||
| (PID) Process: | (3028) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\18F7C1FCC3090203FD5BAA2F861A754976C8DD25 |
| Operation: | write | Name: | Blob |
Value: 0F000000010000001000000065FC47520F66383962EC0B7B88A0821D03000000010000001400000018F7C1FCC3090203FD5BAA2F861A754976C8DD2509000000010000000C000000300A06082B060105050703080B000000010000003400000056006500720069005300690067006E002000540069006D00650020005300740061006D00700069006E00670020004300410000002000000001000000C0020000308202BC3082022502104A19D2388C82591CA55D735F155DDCA3300D06092A864886F70D010104050030819E311F301D060355040A1316566572695369676E205472757374204E6574776F726B31173015060355040B130E566572695369676E2C20496E632E312C302A060355040B1323566572695369676E2054696D65205374616D70696E67205365727669636520526F6F7431343032060355040B132B4E4F204C494142494C4954592041434345505445442C20286329393720566572695369676E2C20496E632E301E170D3937303531323030303030305A170D3034303130373233353935395A30819E311F301D060355040A1316566572695369676E205472757374204E6574776F726B31173015060355040B130E566572695369676E2C20496E632E312C302A060355040B1323566572695369676E2054696D65205374616D70696E67205365727669636520526F6F7431343032060355040B132B4E4F204C494142494C4954592041434345505445442C20286329393720566572695369676E2C20496E632E30819F300D06092A864886F70D010101050003818D0030818902818100D32E20F0687C2C2D2E811CB106B2A70BB7110D57DA53D875E3C9332AB2D4F6095B34F3E990FE090CD0DB1B5AB9CDE7F688B19DC08725EB7D5810736A78CB7115FDC658F629AB585E9604FD2D621158811CCA7194D522582FD5CC14058436BA94AAB44D4AE9EE3B22AD56997E219C6C86C04A47976AB4A636D5FC092DD3B4399B0203010001300D06092A864886F70D01010405000381810061550E3E7BC792127E11108E22CCD4B3132B5BE844E40B789EA47EF3A707721EE259EFCC84E389944CDB4E61EFB3A4FB463D50340B9F7056F68E2A7F17CEE563BF796907732EB095288AF5EDAAA9D25DCD0ACA10098FCEB3AF2896C479298492DCFFBA674248A69010E4BF61F89C53E593D1733FF8FD9D4F84AC55D1FD116363 | |||
| (PID) Process: | (3028) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\FFBDCDE782C8435E3C6F26865CCAA83A455BC30A |
| Operation: | write | Name: | Blob |
Value: 0F000000010000002000000091655B012CB919746D6127AA24E54BA90B2F15A01927DC1DC88E54365D126363030000000100000014000000FFBDCDE782C8435E3C6F26865CCAA83A455BC30A1D00000001000000100000008229307CFB16C4A269DB1E9BB9FAE94D140000000100000014000000EE6B493C7A3F0DE3B109B78AC8AB199F733350E7090000000100000020000000301E06082B0601050507030206082B0601050507030406082B06010505070301620000000100000020000000D40E9C86CD8FE468C1776959F49EA774FA548684B6C406F3909261F4DCE2575C0B000000010000002E0000005400720075007300740043006F007200200052006F006F00740043006500720074002000430041002D00310000002000000001000000340400003082043030820318A003020102020900DA9BEC71F303B019300D06092A864886F70D01010B05003081A4310B3009060355040613025041310F300D06035504080C0650616E616D613114301206035504070C0B50616E616D61204369747931243022060355040A0C1B5472757374436F722053797374656D7320532E20646520522E4C2E31273025060355040B0C1E5472757374436F7220436572746966696361746520417574686F72697479311F301D06035504030C165472757374436F7220526F6F74436572742043412D31301E170D3136303230343132333231365A170D3239313233313137323331365A3081A4310B3009060355040613025041310F300D06035504080C0650616E616D613114301206035504070C0B50616E616D61204369747931243022060355040A0C1B5472757374436F722053797374656D7320532E20646520522E4C2E31273025060355040B0C1E5472757374436F7220436572746966696361746520417574686F72697479311F301D06035504030C165472757374436F7220526F6F74436572742043412D3130820122300D06092A864886F70D01010105000382010F003082010A0282010100BF8EB795E2C226126B3319C740580AAB59AA8D00A3FC80C7507B8ED42026BA3212D8235449251022989D46D2C1C99E4E1B2E2C0E38F31A25681CA65A05E61E8B48BF9896743E69CAE9B578A506BCD5005E090AF2277A52FC2DD5B1EAB4896124F31A13DBA9CF52ED0C24BAB99EEC7E0074FA93AD6C2992AE51B4BBD357BFB3F3A88D9CF4244B2AD6999EF49EFEC07E423AE70B9553DAB7680E904CFB703F8F4A2C94F326DD6369A994D8104EC5470890991B174DB96C6EEF6095118E2180B5BDA073D8D0B277C445EA5A26FB667676F8061F616D0F55C583B71056720607A5F3B11A0305640E9D5A8AD686701B24DEFE288A2BD06AB0FC7AA2DCB2790E8B650F0203010001A3633061301D0603551D0E04160414EE6B493C7A3F0DE3B109B78AC8AB199F733350E7301F0603551D23041830168014EE6B493C7A3F0DE3B109B78AC8AB199F733350E7300F0603551D130101FF040530030101FF300E0603551D0F0101FF040403020186300D06092A864886F70D01010B050003820101002518D4918F13EE8F1E1D1153DA2D442919A01E6B319E4D0E9EAD3D5C416F952B24A179983A3836FBBB669E48FF9090EF3DD4B89BB487753F209BCE72CFA155C14D64A21906A107330C0B29E5F1EAABA3ECB50A7490C77D72F2D75C9F91EF918BB7DCED66A2CF8E663BBC9F3A02E027DD1698C095D40AA4E4819A7594359C905F883706AD59950AB0D167D319CA89E7325A361C3E82A85A93BEC6D06491B6CFD9B618CFDB7ED265A3A6C48E1731C1FB7E76DBD385E358B2777A763B6C2F501CE7DBF667791FF582959A07A714AF8FDC28216709D2D64D5A1C191C8E775CC394243D326B4B7ED4789483BE374DCE5FC71E4E3CE08933950B0FA532D63C5A792C19 | |||
| (PID) Process: | (3028) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\FFB7E08F66E1D0C2582F0245C4970292A46E8803 |
| Operation: | write | Name: | Blob |
Value: 0F00000001000000200000004E3F084ED3C4B0D20C5D5E2E1D33F6096C65162DE9D58F866D8BC6B79EDC39FB030000000100000014000000FFB7E08F66E1D0C2582F0245C4970292A46E88031D000000010000001000000054ECC7F7A10FC6E709B361B583617D40140000000100000014000000D5A8510E7930725EB4AC160DD3B5EBEAC14BDC3A620000000100000020000000C2157309D9AEE17BF34F4DF5E88DBAEBA57E0361EB814CBC239F4D54D329A38D090000000100000042000000304006082B0601050507030106082B0601050507030206082B0601050507030406082B06010505070308060A2B0601040182370A0304060A2B0601040182370A030C0B000000010000007200000046005101740061006E00FA007300ED0074007600E1006E0079006B00690061006400F30020002D0020004B006F0072006D00E1006E0079007A00610074006900200048006900740065006C0065007300ED007400E9007300200053007A006F006C006700E1006C00740061007400F30000002000000001000000440600003082064030820428A003020102020874F860F1E8A38F41300D06092A864886F70D01010B05003081AB310B30090603550406130248553111300F06035504070C084275646170657374313C303A060355040A0C334E49535A204E656D7A65746920496E666F6B6F6D6D756E696BC3A16369C3B37320537A6F6C67C3A16C746174C3B3205A72742E314B304906035504030C4246C59174616EC3BA73C3AD7476C3A16E796B696164C3B3202D204B6F726DC3A16E797A61746920486974656C6573C3AD74C3A97320537A6F6C67C3A16C746174C3B3301E170D3133303931333130323730345A170D3333303931333130323730345A3081AB310B30090603550406130248553111300F06035504070C084275646170657374313C303A060355040A0C334E49535A204E656D7A65746920496E666F6B6F6D6D756E696BC3A16369C3B37320537A6F6C67C3A16C746174C3B3205A72742E314B304906035504030C4246C59174616EC3BA73C3AD7476C3A16E796B696164C3B3202D204B6F726DC3A16E797A61746920486974656C6573C3AD74C3A97320537A6F6C67C3A16C746174C3B330820222300D06092A864886F70D01010105000382020F003082020A0282020100B542A56448DB64A537F82CB8990251B9A228C4FB7004C4D96C8A86F70F8917A484C22E6C4EF5FF44EF5B430E897F3735A55BC8E4235BAF199C5BEDACD6002EDB63CAC354D8AF67D4CB6044A24FCFA4DEFC1F316656B7E1DD388A53FCCF23158B8A87FD0930E59847040E1669AF0905BCC7D490458F6863BE825837FBD84C6FA5AC157775A58864385CD2650F5305CE9430976F7A81E9649812D11E4A9FC1F317DB19361039B801B3B7784DB50C7B5EAA4E9DB9CD5D38FF7F49FEB748AF03426CBE641B61F9CE6B7A9B507100F35797C501741BABC926596C7ABF0A976796B580454801469C4014E46138215B8964E2053613A02ACEDB8804864435DC933459576AED5363FA8BC218163CF471C73E0C1A11E4CE0F20C31723ABA37F1355ACB4FF96D8C02F7A099BDB1C968DA68CFCA16AA66BD10C9D31AC9A31FA52F98939FA2F53F3E9912E508EAAB8A425AF1B8BD96A5288570AC30B9A719FBCCA458AE9B9D595C1B6C2CED10D694A363CAE8DACCB75F69021C30997CE2D1276625EEB0E8F725F2B9BB0C90A15F3FECFF744844601FDCF66ECD030977C6DACD138C1467207170E3EFB30E6CB34D5B5731345210E1D196B4816DAE891A906D0E83D6FFA8CD1B8F59903F1EBD8B569BBB8894F5202A77E3EDBECC5970695FB53EBE0D3E7C88F8899FF2EB797997D84F351FD8E8343DEF3AFE03374C4151C2917A74973DCC04EDD0203010001A3663064301D0603551D0E04160414D5A8510E7930725EB4AC160DD3B5EBEAC14BDC3A30120603551D130101FF040830060101FF020103301F0603551D23041830168014D5A8510E7930725EB4AC160DD3B5EBEAC14BDC3A300E0603551D0F0101FF040403020106300D06092A864886F70D01010B0500038202010061F6644EEA7B97C2C202D95932806D8292A2FA4D8273665A9D82D2556230F820CDA7D389C1C673C4D85D493DCEBE0C7A1DC8696C3DFAEF00F6819A8D3B554F0C9D56D9A7E64DE66BB0A2B5A0FEDF5D835BAB11F26B18AFAB66DB1BC94B1AF744DDF19C82AC9A5EA8A8A8319EDE9CC142228CC41384E52C43061B296933D7E007021FABEE499ED7C388AE591B97CBF81B656001CC6DE140202D4B2101EC1E2CB1816BDEC68CF534B08CC39BDE583E114DE8484C8796EE5A474B426F9EE8834882B99AE93C44F9519354AB9445F9A895AEA68879F5E692A858222ED4944C18BAADFDA7855A82136ABDAE5BC02C195DD893C0DD75403369D94E260A3687A4010CE1DFAD0C19185F88CA35B10A7B810766F97F0F2D6D198AE4E483BB431D5E4FD2E12938C11FF55CA35460EBF843DEE695049987E1CBA9243A792D1A70659F11275D382E450D5BF811592E0E35136AD7A75404FE52F84C15E603995CB287FCAA4608F8D36807601C2F2752759302D8DDD3B187D4FD99767CC1FC03AAEFC782497AFAFA4BDA87DB059F58E26FBE63FA1AA334C1CFBA4C22000705805F05E6017357D491E1D061EF8628E37DCCCA3297E3B36DBCBFF009A02DC40054336D0587F487241D85CDDEC33B37A0E508AFE38B011DB81D3663A210E1252B6C52E01DC6C7F66D9DE0C722E4DDB0862EA6A3986533207656DB67F0C65E4382C20A6D64D5DE8C6C | |||
| (PID) Process: | (3028) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\FEB8C432DCF9769ACEAE3DD8908FFD288665647D |
| Operation: | write | Name: | Blob |
Value: 0F0000000100000014000000CF5C65CD58EBB3D31A6618C3D42BE79BB5DE72E8030000000100000014000000FEB8C432DCF9769ACEAE3DD8908FFD288665647D6800000001000000080000000080D10BBAC7D3017E00000001000000080000000000DC6F269AD3011D00000001000000100000007BFEBE9D00E942574DF1E0052D4409CD140000000100000014000000354AF54DAF3FD78238ACAB716517758C9D5593E6620000000100000020000000A22DBA681E97376E2D397D728AAE3A9B6296B9FDBA60BC2E11F647F2C675FB3753000000010000002400000030223020060A2A83088C9B1B6485510130123010060A2B0601040182373C0101030200C0090000000100000034000000303206082B0601050507030106082B0601050507030206082B0601050507030306082B0601050507030406082B060105050703080B00000001000000360000005300450043004F004D002000540072007500730074002000530079007300740065006D007300200043004F0020004C005400440000002000000001000000810300003082037D30820265A003020102020100300D06092A864886F70D01010505003060310B3009060355040613024A5031253023060355040A131C5345434F4D2054727573742053797374656D7320434F2E2C4C54442E312A3028060355040B1321536563757269747920436F6D6D756E69636174696F6E20455620526F6F74434131301E170D3037303630363032313233325A170D3337303630363032313233325A3060310B3009060355040613024A5031253023060355040A131C5345434F4D2054727573742053797374656D7320434F2E2C4C54442E312A3028060355040B1321536563757269747920436F6D6D756E69636174696F6E20455620526F6F7443413130820122300D06092A864886F70D01010105000382010F003082010A0282010100BC7FEC579B24E0FE9CBA4279A9888AFA80E0F5072943EA8E0A34368D1CFAA7B53978FF9775F72FE4AA6B048444CAA6E2688EFD5550620FA4710ECE07382D428550AD3C966F8BD5A20ECFDE49893DD6642E38E51E6CB5578A9EEF480ECD7A69168744B590E4069DAEA104975879EF204A826B8C22BFEC1F0FE98471EDF10EE4B81813CC56365DD19A1E516B396E607688340BF3B3D1B09DCA61E2641DC14607B863DD1E3365B38E0955523DB5BDFF07EBAD6155182CA969984AAA40C53314657400F991DEAF0348C54054DC0F84906820C59296DC2EE50245AAC05F54F86DEA49CF5D6C4BAFEF9AC2565CC63556426A305FC2ABF6E23D3FB3C9118F314CD79F490203010001A3423040301D0603551D0E04160414354AF54DAF3FD78238ACAB716517758C9D5593E6300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF300D06092A864886F70D01010505000382010100A887E9ECF840675DC3C166C7404B97FC8713905AC4EFA0CA5F8BB7A7B7F1D6B564B78AB3B81BCCDAFBAC668841CEE8FCE4DB1E88A6ED27501B0230244679FE048770974073D1C0C157199A69A52799AB9D6284F651C12CC92315D828B7AB2513B546E18602FF268CC488921D56FE1967F255E480A36B9CAB77E151710D20DB109ADBBD767907779928AD9A5EDAB14F442C358EA596C7FD83F058C679D6987CA88DFE863E071692E17BE71DEC33767E422E4A85F9918968840381A59B9ABEE337C554AB563B182D41A40CF842DB99A0E0726FBB5DE1164F530A64F94EF4BF4E54BD786C88EABF9C1324C27069A27F0FC83CAD08C9B09840A32AE78883ED778F74 | |||
Executable files
46
Suspicious files
73
Text files
417
Unknown types
53
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2916 | EpocCamInstaller294.exe | C:\Users\admin\AppData\Local\Temp\nsb720D.tmp\nsA8DF.tmp | — | |
MD5:— | SHA256:— | |||
| 2916 | EpocCamInstaller294.exe | C:\Users\admin\AppData\Local\Temp\nsb720D.tmp\ioSpecial.ini | text | |
MD5:— | SHA256:— | |||
| 2916 | EpocCamInstaller294.exe | C:\Users\admin\AppData\Local\Temp\nsb720D.tmp\modern-header.bmp | image | |
MD5:— | SHA256:— | |||
| 3028 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIB677.tmp | — | |
MD5:— | SHA256:— | |||
| 2916 | EpocCamInstaller294.exe | C:\Program Files\Kinoni\EpocCam\EpocCamTest.exe | executable | |
MD5:— | SHA256:— | |||
| 2916 | EpocCamInstaller294.exe | C:\Program Files\Kinoni\EpocCam\swresample-3.dll | executable | |
MD5:— | SHA256:— | |||
| 2636 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 1052 | svchost.exe | C:\Windows\System32\catroot2\{127D0A1D-4EF2-11D1-8608-00C04FC295EE}\catdb | — | |
MD5:— | SHA256:— | |||
| 1052 | svchost.exe | C:\Windows\system32\CatRoot2\{127D0A1D-4EF2-11D1-8608-00C04FC295EE}\catdb | — | |
MD5:— | SHA256:— | |||
| 1052 | svchost.exe | C:\Windows\System32\catroot2\{F750E6C3-38EE-11D1-85E5-00C04FC295EE}\catdb | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
116
TCP/UDP connections
44
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3012 | iexplore.exe | GET | 301 | 172.217.23.174:80 | http://www.youtube.com/embed/h4jb7o27LdM | US | — | — | whitelisted |
3012 | iexplore.exe | GET | 200 | 84.34.147.59:80 | http://www.kinoni.com/images/debutlink.png | FI | image | 19.9 Kb | unknown |
3012 | iexplore.exe | GET | 200 | 84.34.147.59:80 | http://www.kinoni.com/images/head_bar_bg.png | FI | image | 183 b | unknown |
3012 | iexplore.exe | GET | 200 | 84.34.147.59:80 | http://www.kinoni.com/images/header_thin_bg_blue.jpg | FI | image | 14.8 Kb | unknown |
3012 | iexplore.exe | GET | 200 | 84.34.147.59:80 | http://www.kinoni.com/images/head_bar_shadow.png | FI | image | 476 b | unknown |
3012 | iexplore.exe | GET | 200 | 84.34.147.59:80 | http://www.kinoni.com/thankyou.html | FI | html | 1.50 Kb | unknown |
3012 | iexplore.exe | GET | 200 | 84.34.147.59:80 | http://www.kinoni.com/style.css | FI | html | 16.2 Kb | unknown |
3012 | iexplore.exe | GET | 200 | 84.34.147.59:80 | http://www.kinoni.com/css/shThemeDefault.css | FI | text | 1.15 Kb | unknown |
3012 | iexplore.exe | GET | 200 | 84.34.147.59:80 | http://www.kinoni.com/js/general.js | FI | text | 924 b | unknown |
3012 | iexplore.exe | GET | 200 | 152.199.19.161:80 | http://kinoconsole.kinoni.com/kinoni_main_website/images/kinonilogo_darkbg.png | US | image | 34.0 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3012 | iexplore.exe | 84.34.147.59:80 | www.kinoni.com | AinaCom Oy | FI | unknown |
3012 | iexplore.exe | 152.199.19.161:80 | kinoconsole.kinoni.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3012 | iexplore.exe | 172.217.23.174:80 | www.youtube.com | Google Inc. | US | whitelisted |
3012 | iexplore.exe | 216.58.208.46:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
3012 | iexplore.exe | 172.217.23.174:443 | www.youtube.com | Google Inc. | US | whitelisted |
3012 | iexplore.exe | 172.217.23.131:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
2492 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3012 | iexplore.exe | 64.233.184.156:443 | stats.g.doubleclick.net | Google Inc. | US | whitelisted |
3012 | iexplore.exe | 172.217.22.98:443 | googleads.g.doubleclick.net | Google Inc. | US | whitelisted |
3012 | iexplore.exe | 172.217.22.35:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.kinoni.com |
| unknown |
kinoconsole.kinoni.com |
| malicious |
www.google-analytics.com |
| whitelisted |
www.youtube.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
stats.g.doubleclick.net |
| whitelisted |
googleads.g.doubleclick.net |
| whitelisted |
static.doubleclick.net |
| whitelisted |