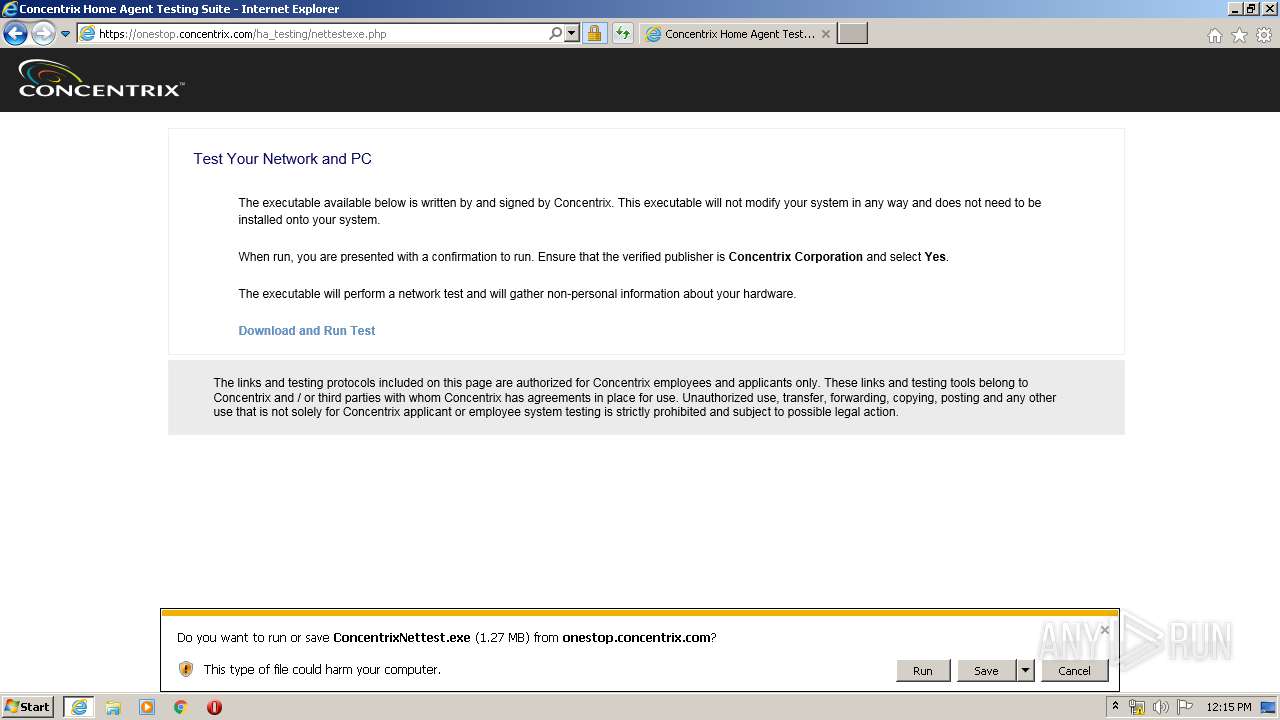
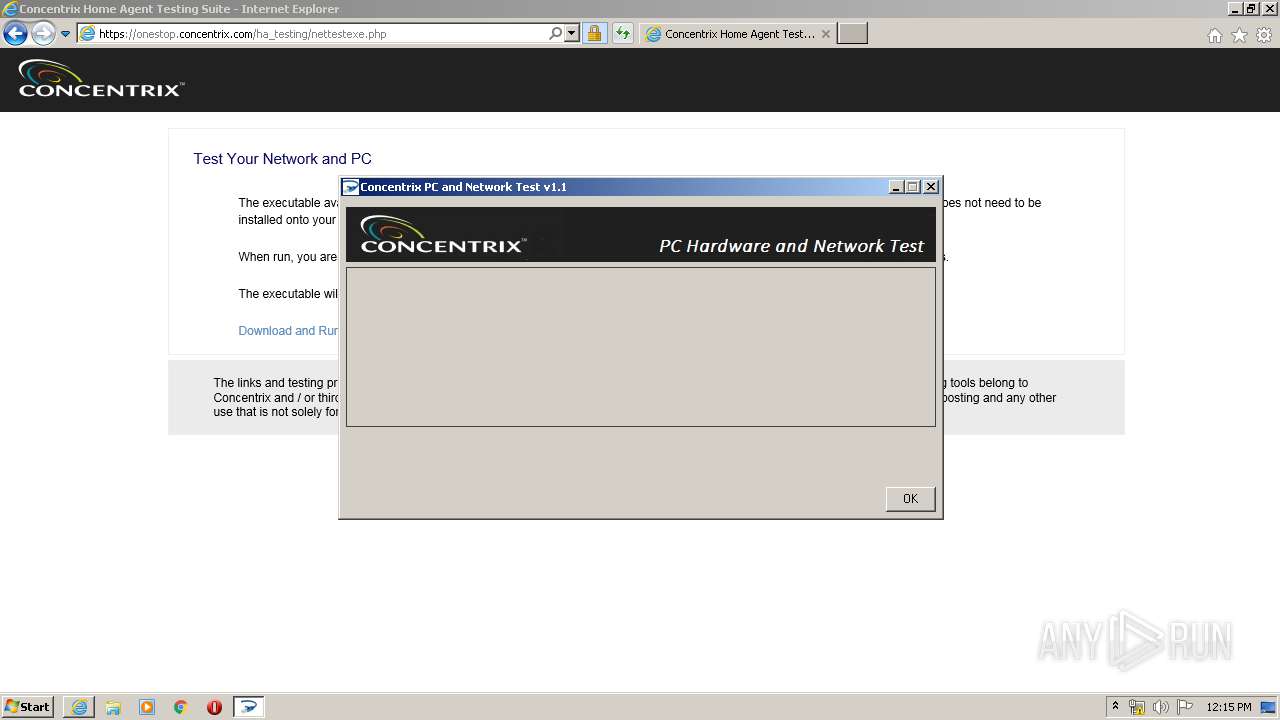
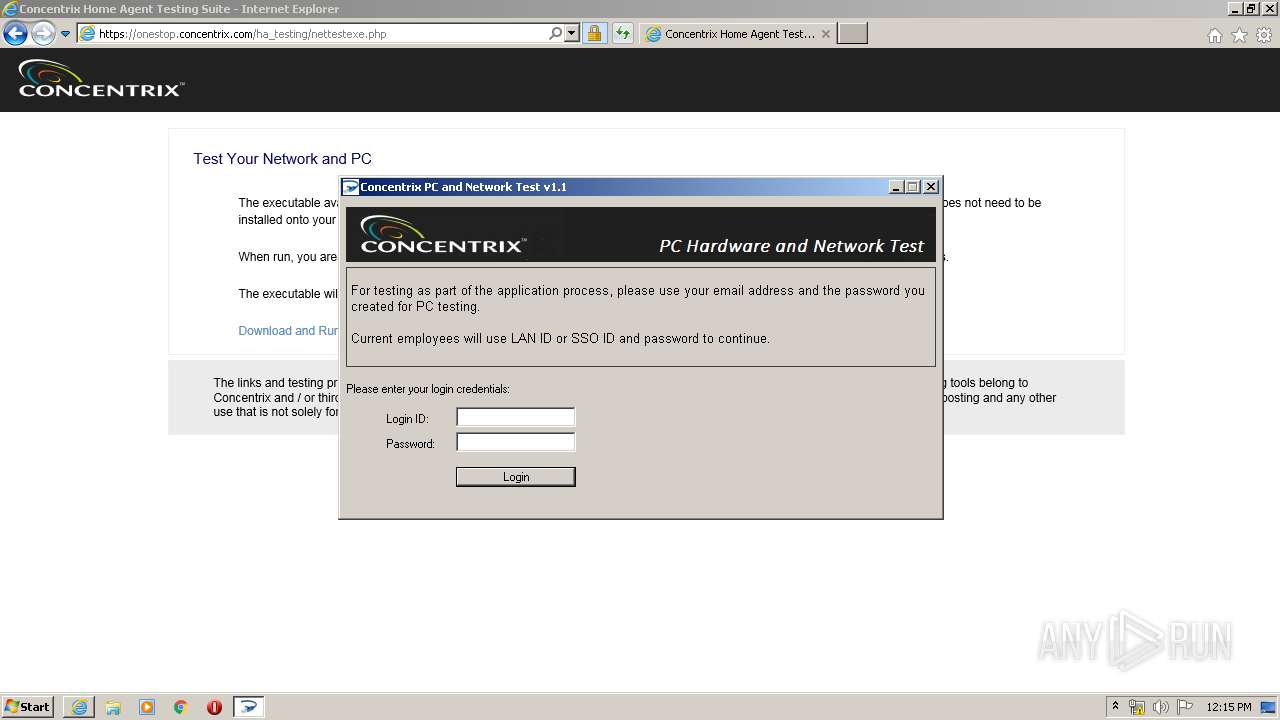
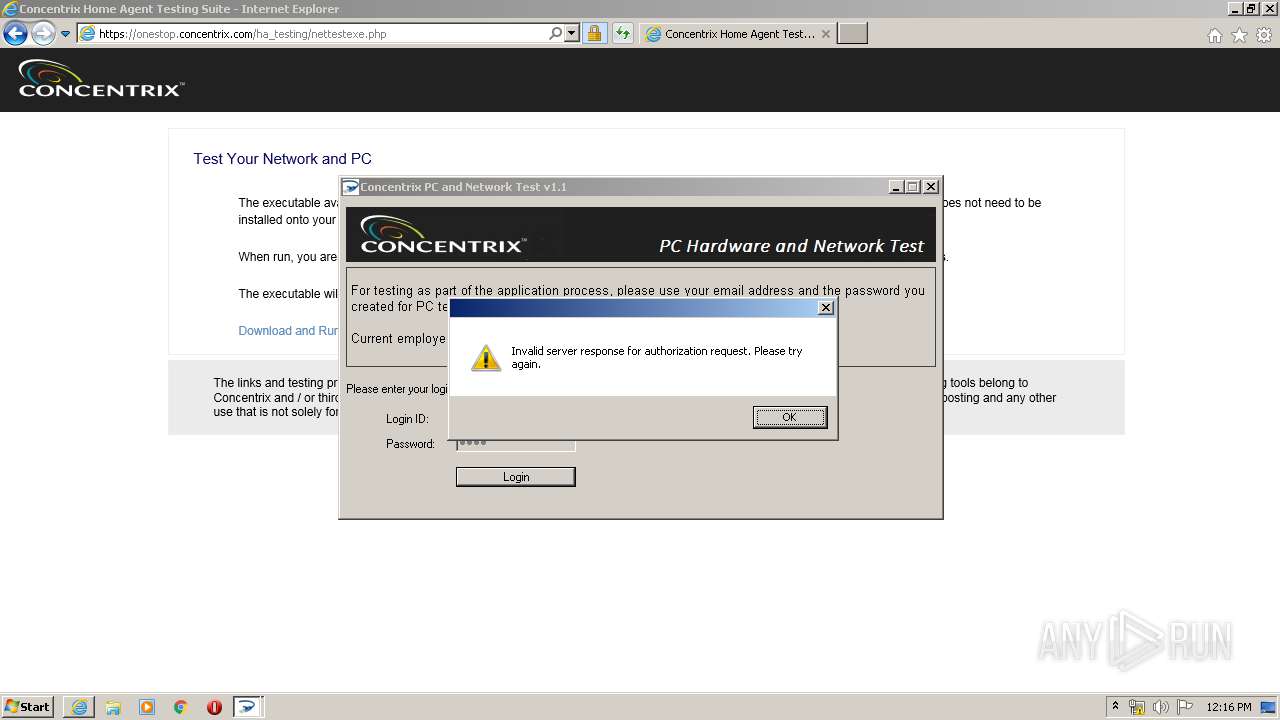
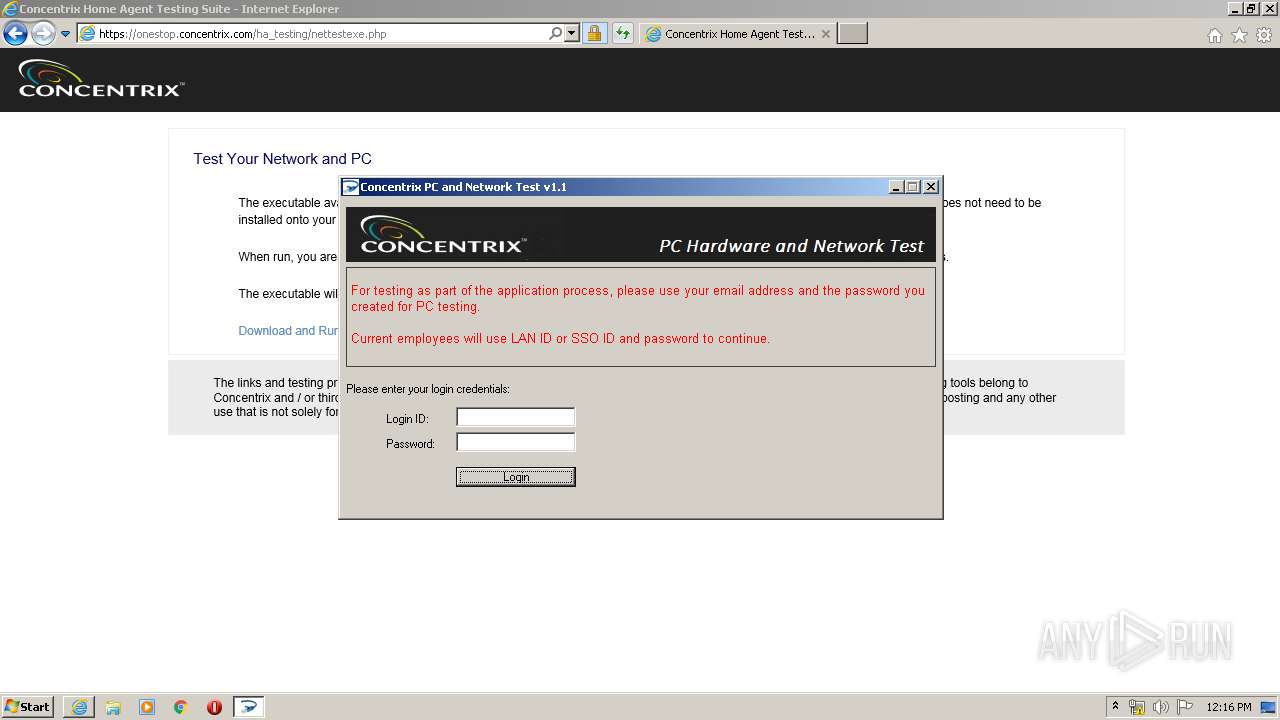
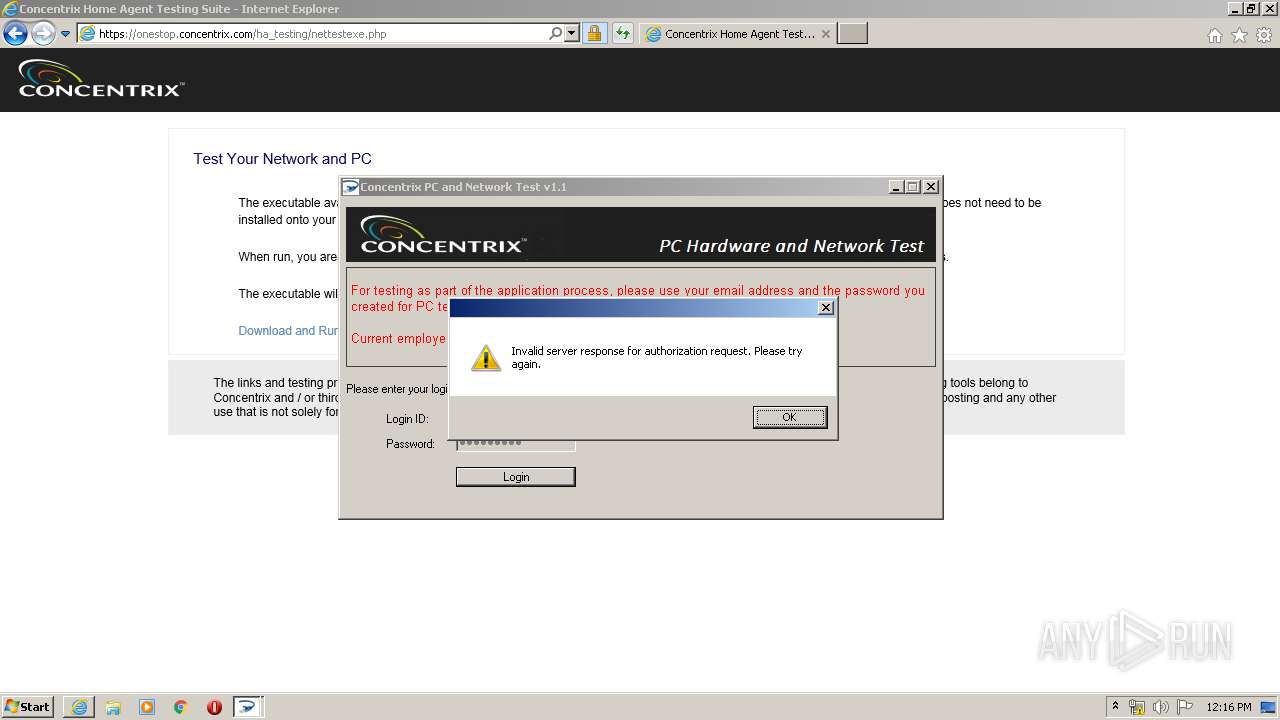
| URL: | https://onestop.concentrix.com/ha_testing/concentrixnettest.exe |
| Full analysis: | https://app.any.run/tasks/a2861cc8-b016-4c80-9f60-b429f0574c66 |
| Verdict: | Malicious activity |
| Analysis date: | April 07, 2020, 11:12:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 653C468836051183B0F1B29F21FCB51F |
| SHA1: | 4EE6ABBE145F784A2F460EA94B507D556CB20B58 |
| SHA256: | D0C69C32966B0F0345A1A1B9D6177FDA4A7C713F69FB08190CD0CB7242F4CD3A |
| SSDEEP: | 3:N8CzVQbcGTKNE6edyAIAwW0Cn:2ChOKWuK |
MALICIOUS
Application was dropped or rewritten from another process
- ConcentrixNettest.exe (PID: 3248)
Runs PING.EXE for delay simulation
- cmd.exe (PID: 2516)
Actions looks like stealing of personal data
- ConcentrixNettest.exe (PID: 3248)
SUSPICIOUS
Executable content was dropped or overwritten
- iexplore.exe (PID: 2804)
- iexplore.exe (PID: 3716)
Creates files in the user directory
- ConcentrixNettest.exe (PID: 3248)
Reads Internet Cache Settings
- ConcentrixNettest.exe (PID: 3248)
Starts CMD.EXE for commands execution
- ConcentrixNettest.exe (PID: 3248)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2516)
Uses TASKLIST.EXE to query information about running processes
- cmd.exe (PID: 2516)
INFO
Changes internet zones settings
- iexplore.exe (PID: 3716)
Reads internet explorer settings
- iexplore.exe (PID: 2804)
Drops Coronavirus (possible) decoy
- iexplore.exe (PID: 2804)
Reads Internet Cache Settings
- iexplore.exe (PID: 3716)
- iexplore.exe (PID: 2804)
Creates files in the user directory
- iexplore.exe (PID: 2804)
- iexplore.exe (PID: 3716)
Reads settings of System Certificates
- iexplore.exe (PID: 3716)
- iexplore.exe (PID: 2804)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3716)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3716)
Changes settings of System certificates
- iexplore.exe (PID: 3716)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
49
Monitored processes
8
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1692 | TASKKILL /F /FI "IMAGENAME EQ ConcentrixNettest.exe" | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1920 | TASKLIST /NH /FI "IMAGENAME EQ ConcentrixNettest.exe" | C:\Windows\system32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2364 | PING -n 2 127.0.0.1 | C:\Windows\system32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2516 | cmd /c C:\Users\admin\AppData\Local\Temp\ConcentrixNettest.bat | C:\Windows\system32\cmd.exe | — | ConcentrixNettest.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2804 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3716 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3068 | FIND /I "ConcentrixNettest.exe" | C:\Windows\system32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
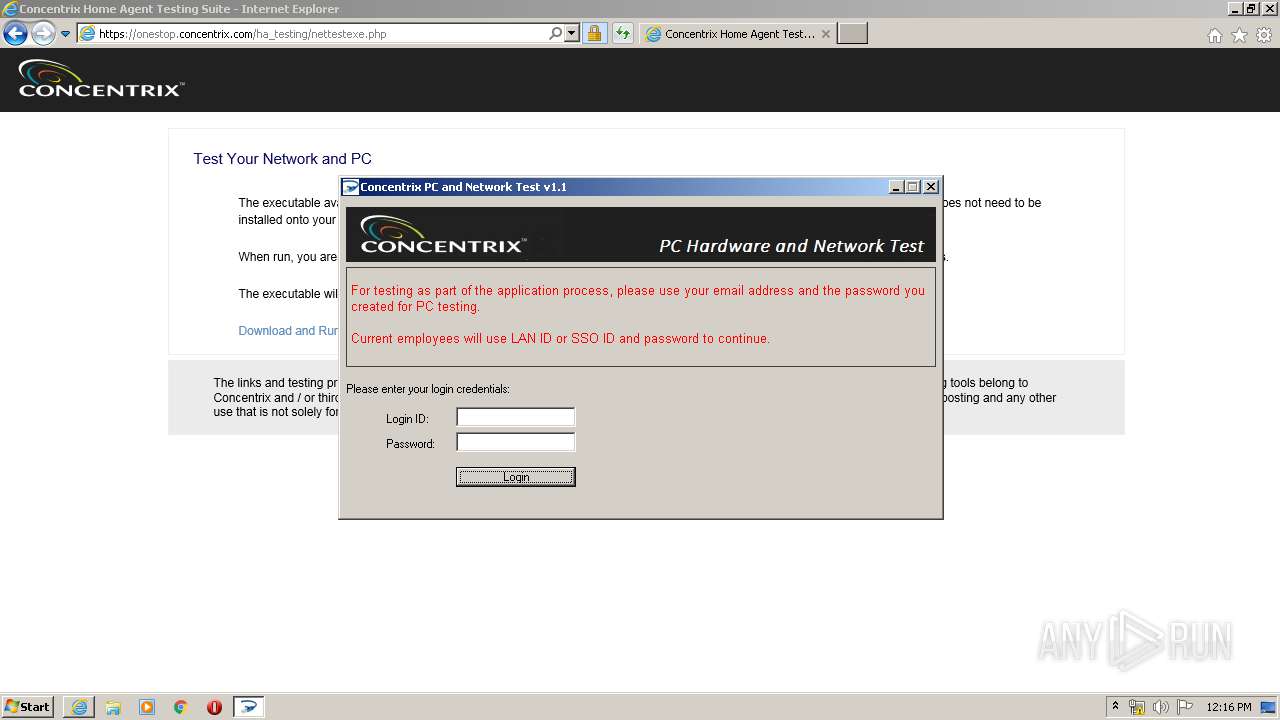
| 3248 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\ConcentrixNettest.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\ConcentrixNettest.exe | iexplore.exe | ||||||||||||
User: admin Company: Concentrix Integrity Level: MEDIUM Description: Concentrix PC and Network Test Exit code: 0 Version: 1.1 Modules
| |||||||||||||||
| 3716 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://onestop.concentrix.com/ha_testing/concentrixnettest.exe" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
5 727
Read events
1 003
Write events
3 199
Delete events
1 525
Modification events
| (PID) Process: | (3716) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 2500167688 | |||
| (PID) Process: | (3716) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30805197 | |||
| (PID) Process: | (3716) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3716) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3716) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3716) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3716) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3716) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A1000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3716) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3716) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
2
Suspicious files
108
Text files
88
Unknown types
64
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2804 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabF3ED.tmp | — | |
MD5:— | SHA256:— | |||
| 2804 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarF3EE.tmp | — | |
MD5:— | SHA256:— | |||
| 3716 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2804 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\redirect_page[1].htm | html | |
MD5:— | SHA256:— | |||
| 2804 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\223DE96EE265046957A660ED7C9DD9E7_EFF9B9BA98DEAA773F261FA85A0B1771 | binary | |
MD5:— | SHA256:— | |||
| 2804 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\0035920B3A7601994D78388FBD5F404F_6D902493C2B2B8366AEA1AE754B35C0B | der | |
MD5:— | SHA256:— | |||
| 3716 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\redirect_page[1].htm | html | |
MD5:— | SHA256:— | |||
| 2804 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\223DE96EE265046957A660ED7C9DD9E7_EFF9B9BA98DEAA773F261FA85A0B1771 | der | |
MD5:— | SHA256:— | |||
| 2804 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EB2C4AB8B68FFA4B7733A9139239A396_D76DB901EE986B889F30D8CC06229E2D | der | |
MD5:— | SHA256:— | |||
| 2804 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\0035920B3A7601994D78388FBD5F404F_6D902493C2B2B8366AEA1AE754B35C0B | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
66
TCP/UDP connections
142
DNS requests
42
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2804 | iexplore.exe | GET | 200 | 192.124.249.41:80 | http://ocsp.godaddy.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQdI2%2BOBkuXH93foRUj4a7lAr4rGwQUOpqFBxBnKLbv9r0FQW4gwZTaD94CAQc%3D | US | der | 1.69 Kb | whitelisted |
2804 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCEBPqKHBb9OztDDZjCYBhQzY%3D | US | der | 471 b | whitelisted |
2804 | iexplore.exe | GET | 200 | 192.124.249.41:80 | http://ocsp.godaddy.com//MEowSDBGMEQwQjAJBgUrDgMCGgUABBS2CA1fbGt26xPkOKX4ZguoUjM0TgQUQMK9J47MNIMwojPX%2B2yz8LQsgM4CCQDz3VZZSg0F6A%3D%3D | US | der | 1.74 Kb | whitelisted |
2804 | iexplore.exe | GET | 200 | 192.124.249.41:80 | http://ocsp.godaddy.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQdI2%2BOBkuXH93foRUj4a7lAr4rGwQUOpqFBxBnKLbv9r0FQW4gwZTaD94CAQc%3D | US | der | 1.69 Kb | whitelisted |
2804 | iexplore.exe | GET | 200 | 192.124.249.41:80 | http://ocsp.godaddy.com//MEowSDBGMEQwQjAJBgUrDgMCGgUABBS2CA1fbGt26xPkOKX4ZguoUjM0TgQUQMK9J47MNIMwojPX%2B2yz8LQsgM4CCQDz3VZZSg0F6A%3D%3D | US | der | 1.74 Kb | whitelisted |
2804 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCEBPqKHBb9OztDDZjCYBhQzY%3D | US | der | 471 b | whitelisted |
2804 | iexplore.exe | GET | 200 | 206.126.172.177:80 | http://www.convergysworkathome.com/redirect_page.html | US | html | 490 b | suspicious |
2804 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCEBPqKHBb9OztDDZjCYBhQzY%3D | US | der | 471 b | whitelisted |
3716 | iexplore.exe | GET | 302 | 206.126.172.177:80 | http://www.convergysworkathome.com/favicon.ico | US | html | 237 b | suspicious |
2804 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCEBPqKHBb9OztDDZjCYBhQzY%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2804 | iexplore.exe | 192.124.249.41:80 | ocsp.godaddy.com | Sucuri | US | suspicious |
2804 | iexplore.exe | 206.126.172.177:443 | onestop.concentrix.com | Convergys Corp. | US | suspicious |
2804 | iexplore.exe | 206.126.172.177:80 | onestop.concentrix.com | Convergys Corp. | US | suspicious |
3716 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3716 | iexplore.exe | 206.126.172.177:80 | onestop.concentrix.com | Convergys Corp. | US | suspicious |
2804 | iexplore.exe | 54.172.182.166:80 | www.concentrix.com | Amazon.com, Inc. | US | unknown |
2804 | iexplore.exe | 108.161.188.228:443 | 1cfrbv1cz8j13t7nr4n67ss1-wpengine.netdna-ssl.com | netDNA | US | unknown |
2804 | iexplore.exe | 172.217.18.106:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
2804 | iexplore.exe | 54.172.182.166:443 | www.concentrix.com | Amazon.com, Inc. | US | unknown |
2804 | iexplore.exe | 151.139.128.14:80 | ocsp.usertrust.com | Highwinds Network Group, Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
onestop.concentrix.com |
| suspicious |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.godaddy.com |
| whitelisted |
www.convergysworkathome.com |
| suspicious |
www.concentrix.com |
| unknown |
1cfrbv1cz8j13t7nr4n67ss1-wpengine.netdna-ssl.com |
| unknown |
fonts.googleapis.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3248 | ConcentrixNettest.exe | Potential Corporate Privacy Violation | ET POLICY Autoit Windows Automation tool User-Agent in HTTP Request - Possibly Hostile |