| File name: | HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.7z |
| Full analysis: | https://app.any.run/tasks/087d1769-0dfd-4b0f-b10f-deafcb84d7d6 |
| Verdict: | Malicious activity |
| Analysis date: | May 10, 2025, 14:19:27 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 9D969F9301608AB539BB45D2CC61FBFE |
| SHA1: | 30F214D429CFC0D8646BB0A901E1D995D59F6C31 |
| SHA256: | D0C1B208CD6D69E0F1050BC1FDB3D0724C0D93CDC548160A38C2BAA1A291EAD0 |
| SSDEEP: | 3072:TSAtgZjhQNpndPbInY7Wh0KRlrZ9yZqfTmBRngU:TSEAFendTxjkrZEwm/gU |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 372)
Create files in the Startup directory
- HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe (PID: 1400)
SUSPICIOUS
Reads the Internet Settings
- HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe (PID: 1400)
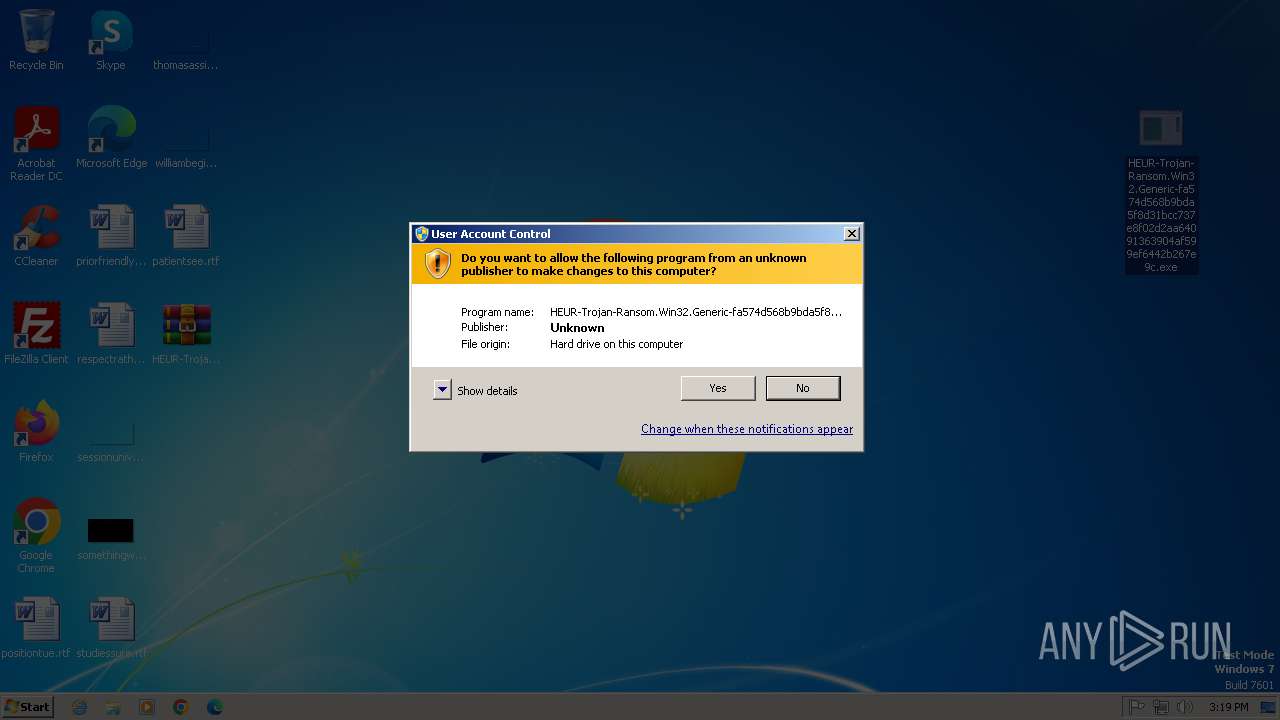
Executable content was dropped or overwritten
- HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe (PID: 1400)
Checks for external IP
- svchost.exe (PID: 1080)
- HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe (PID: 1400)
Possible usage of Discord/Telegram API has been detected (YARA)
- HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe (PID: 1400)
Executes as Windows Service
- VSSVC.exe (PID: 3696)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 372)
Checks supported languages
- HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe (PID: 1400)
Reads the computer name
- HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe (PID: 1400)
Manual execution by a user
- HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe (PID: 1400)
Reads the machine GUID from the registry
- HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe (PID: 1400)
Reads Environment values
- HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe (PID: 1400)
Disables trace logs
- HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe (PID: 1400)
Creates files or folders in the user directory
- HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe (PID: 1400)
Create files in a temporary directory
- HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe (PID: 1400)
Attempting to use instant messaging service
- HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe (PID: 1400)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(1400) HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe
Discord-Webhook-Tokens (1)889649878509170719/T-XddzgWh4gpqgWNHdXfhHrudt-sER4v8EdEVT3Moa7TIHvUpBdrAq6q-cx2bjRvsHG4
Discord-Info-Links
889649878509170719/T-XddzgWh4gpqgWNHdXfhHrudt-sER4v8EdEVT3Moa7TIHvUpBdrAq6q-cx2bjRvsHG4
Get Webhook Infohttps://discord.com/api/webhooks/889649878509170719/T-XddzgWh4gpqgWNHdXfhHrudt-sER4v8EdEVT3Moa7TIHvUpBdrAq6q-cx2bjRvsHG4
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2021:10:01 12:22:36+00:00 |
| ArchivedFileName: | HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe |
Total processes
44
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 372 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1080 | C:\Windows\system32\svchost.exe -k NetworkService | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1400 | "C:\Users\admin\Desktop\HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe" | C:\Users\admin\Desktop\HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe | explorer.exe | ||||||||||||
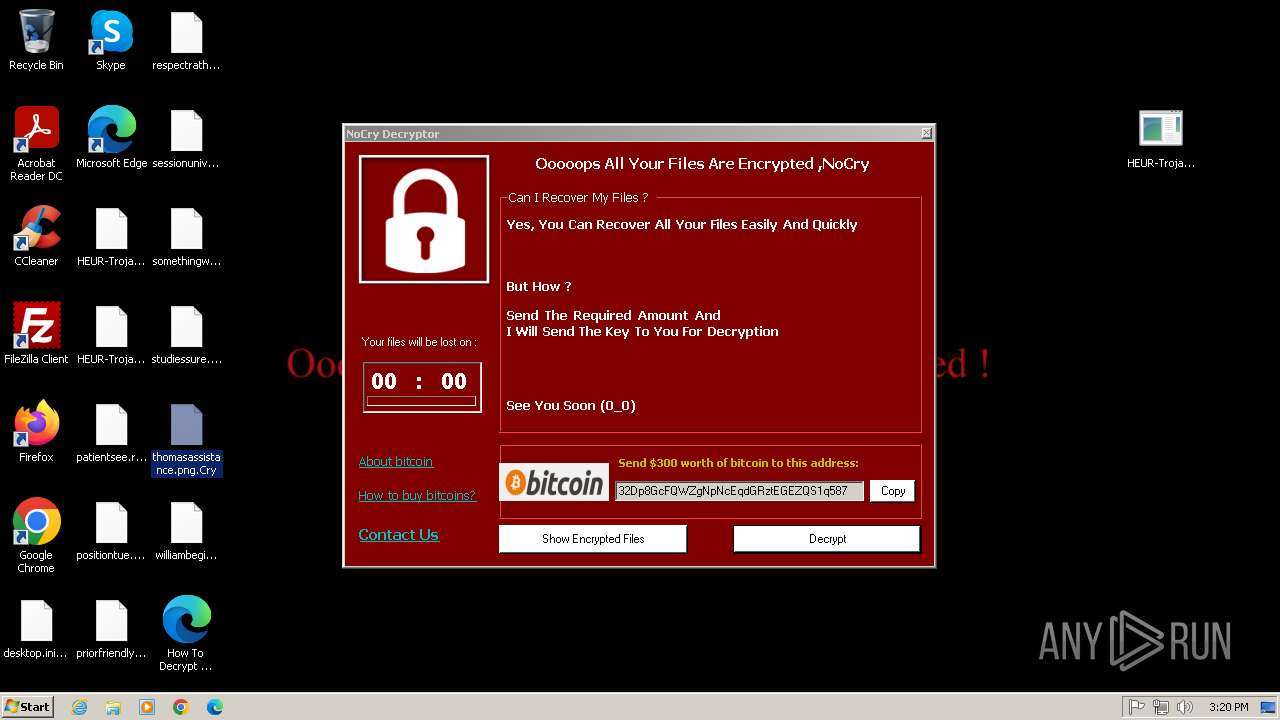
User: admin Integrity Level: HIGH Description: NoCry Version: 1.0.0.0 Modules
ims-api(PID) Process(1400) HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe Discord-Webhook-Tokens (1)889649878509170719/T-XddzgWh4gpqgWNHdXfhHrudt-sER4v8EdEVT3Moa7TIHvUpBdrAq6q-cx2bjRvsHG4 Discord-Info-Links 889649878509170719/T-XddzgWh4gpqgWNHdXfhHrudt-sER4v8EdEVT3Moa7TIHvUpBdrAq6q-cx2bjRvsHG4 Get Webhook Infohttps://discord.com/api/webhooks/889649878509170719/T-XddzgWh4gpqgWNHdXfhHrudt-sER4v8EdEVT3Moa7TIHvUpBdrAq6q-cx2bjRvsHG4 | |||||||||||||||
| 3000 | C:\Windows\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3696 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 357
Read events
2 222
Write events
135
Delete events
0
Modification events
| (PID) Process: | (372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (372) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.7z | |||
| (PID) Process: | (372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
2
Suspicious files
70
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1400 | HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe | C:\Users\admin\ntuser.dat.LOG1.Cry | binary | |
MD5:7D9C61FF2D62A55A64D13295E2651F35 | SHA256:D89C1C11A94305152C4B621806A00C7A911CA7ECE402919AD7C1CC0FA3C8CD49 | |||
| 1400 | HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe | C:\Users\admin\NTUSER.DAT.Cry | binary | |
MD5:7D9C61FF2D62A55A64D13295E2651F35 | SHA256:D89C1C11A94305152C4B621806A00C7A911CA7ECE402919AD7C1CC0FA3C8CD49 | |||
| 1400 | HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe | C:\Users\admin\Desktop\HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe.Cry | binary | |
MD5:2794301364AC509E425F7B7E4C023116 | SHA256:51A4E8F5E7EA8D380B9773AE071BF48A7CCD27FCFFEACA4B1EBDEE7C29D7E7A6 | |||
| 1400 | HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp.Cry | binary | |
MD5:48DAD25DEEC7FD6A8560FBDCF3A2F8F8 | SHA256:DD973FCF988F9747204DBABD312694109E0CC54D6A6B8CEED0FFE29BD27CC291 | |||
| 1400 | HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe | C:\Users\admin\NTUSER.DAT{6cced2f1-6e01-11de-8bed-001e0bcd1824}.TMContainer00000000000000000001.regtrans-ms.Cry | binary | |
MD5:7D9C61FF2D62A55A64D13295E2651F35 | SHA256:D89C1C11A94305152C4B621806A00C7A911CA7ECE402919AD7C1CC0FA3C8CD49 | |||
| 1400 | HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe | C:\Users\admin\ntuser.dat.LOG2.Cry | binary | |
MD5:7D9C61FF2D62A55A64D13295E2651F35 | SHA256:D89C1C11A94305152C4B621806A00C7A911CA7ECE402919AD7C1CC0FA3C8CD49 | |||
| 1400 | HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe | C:\Users\admin\NTUSER.DAT{6cced2f1-6e01-11de-8bed-001e0bcd1824}.TM.blf.Cry | binary | |
MD5:7D9C61FF2D62A55A64D13295E2651F35 | SHA256:D89C1C11A94305152C4B621806A00C7A911CA7ECE402919AD7C1CC0FA3C8CD49 | |||
| 1400 | HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe | C:\Users\admin\Contacts\admin.contact.Cry | binary | |
MD5:3B1443E3CA20FD4B09CB74071696DFA1 | SHA256:5F19192D1B3FAC37B1EF0FD10D7F05055199037BE2B42FCF013D91F4E71CDAB5 | |||
| 1400 | HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe | C:\Users\admin\Contacts\desktop.ini.Cry | binary | |
MD5:EB8EB8CBA248F5CE856FB40B2E24DF2B | SHA256:8E27E667EB178F814AD24B3FA4D5EFB28D3315793C9D675A8B253879BA649B65 | |||
| 1400 | HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe | C:\Users\admin\Desktop\desktop.ini.Cry | binary | |
MD5:7423446060F9FA88118ED3D2A6985501 | SHA256:70949AFAD7BFBC124E04B384B9E39D53A1D87D127EDED4AC6250964651CF1F15 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
6
DNS requests
3
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1400 | HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/line/?fields=hosting | unknown | — | — | whitelisted |
1400 | HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/csv/?fields=country,query | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
1400 | HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | whitelisted |
1400 | HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe | 162.159.135.232:443 | discord.com | CLOUDFLARENET | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
ip-api.com |
| whitelisted |
discord.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
1080 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
1400 | HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
1400 | HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External Hosting Lookup by ip-api |
1400 | HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |
1080 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
1400 | HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
1080 | svchost.exe | Misc activity | ET INFO Discord Chat Service Domain in DNS Lookup (discord .com) |
1400 | HEUR-Trojan-Ransom.Win32.Generic-fa574d568b9bda5f8d31bcc737e8f02d2aa64091363904af599ef6442b267e9c.exe | Misc activity | ET INFO Observed Discord Service Domain (discord .com) in TLS SNI |