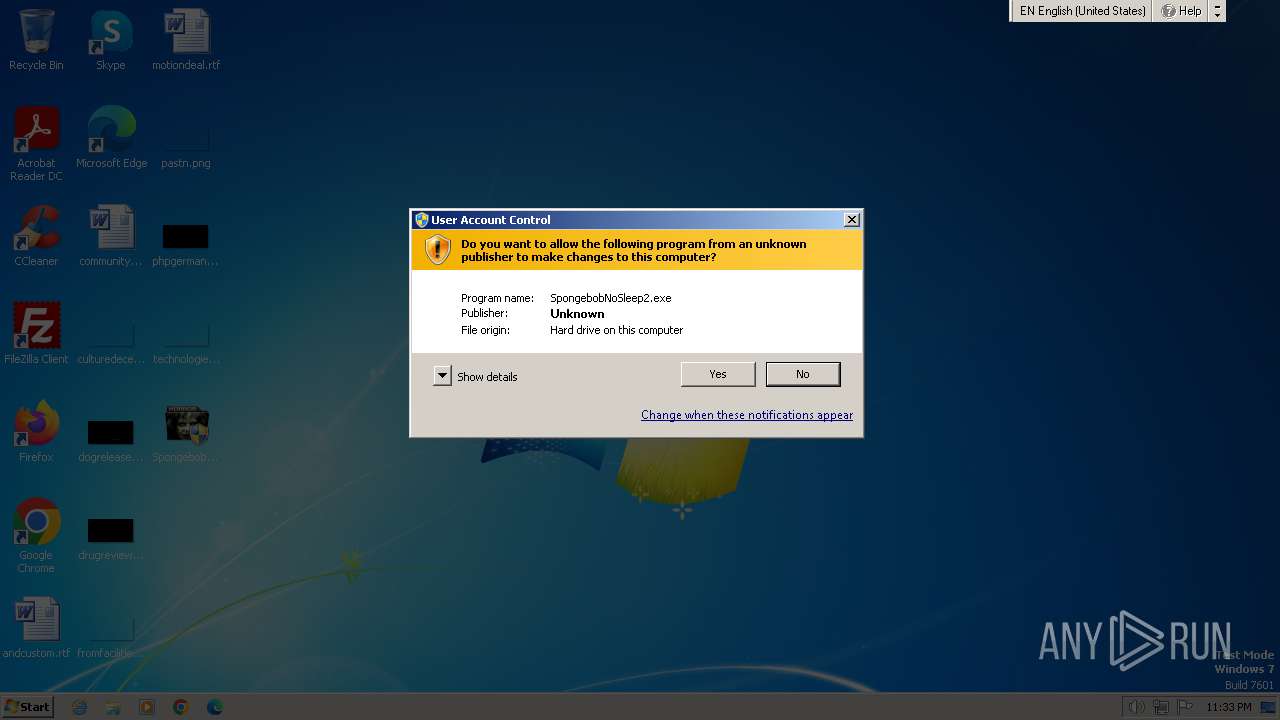
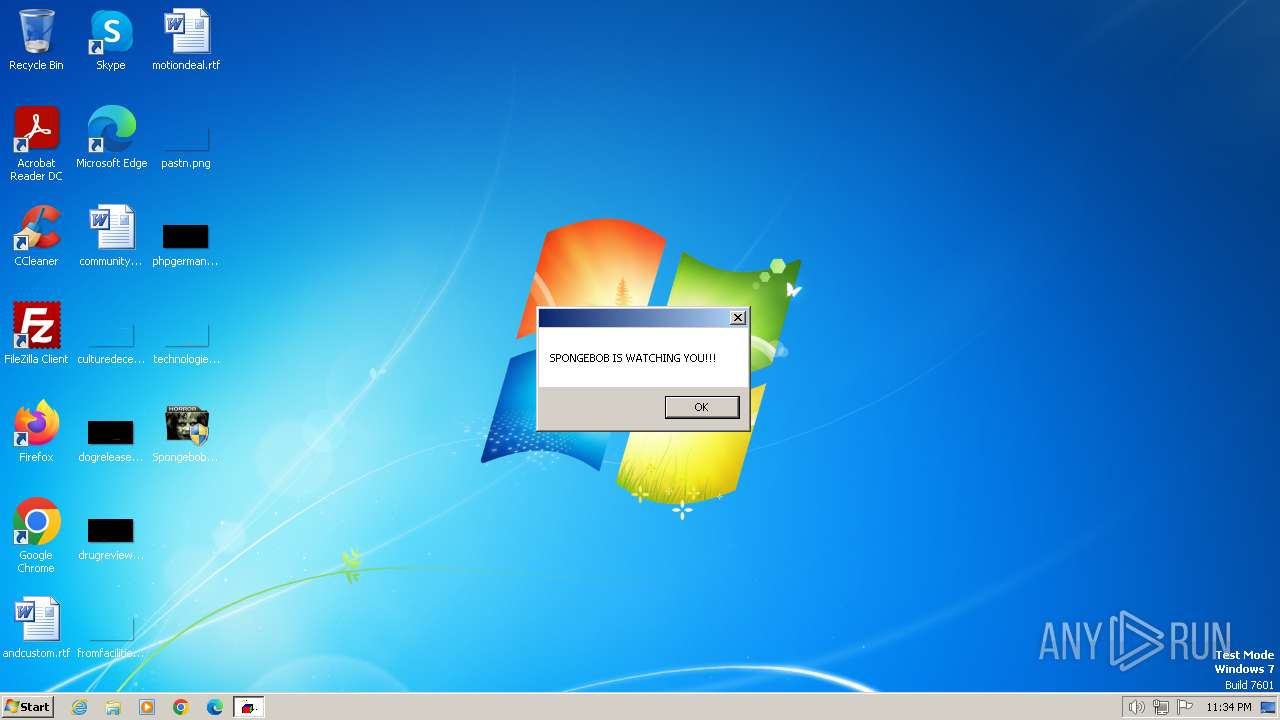
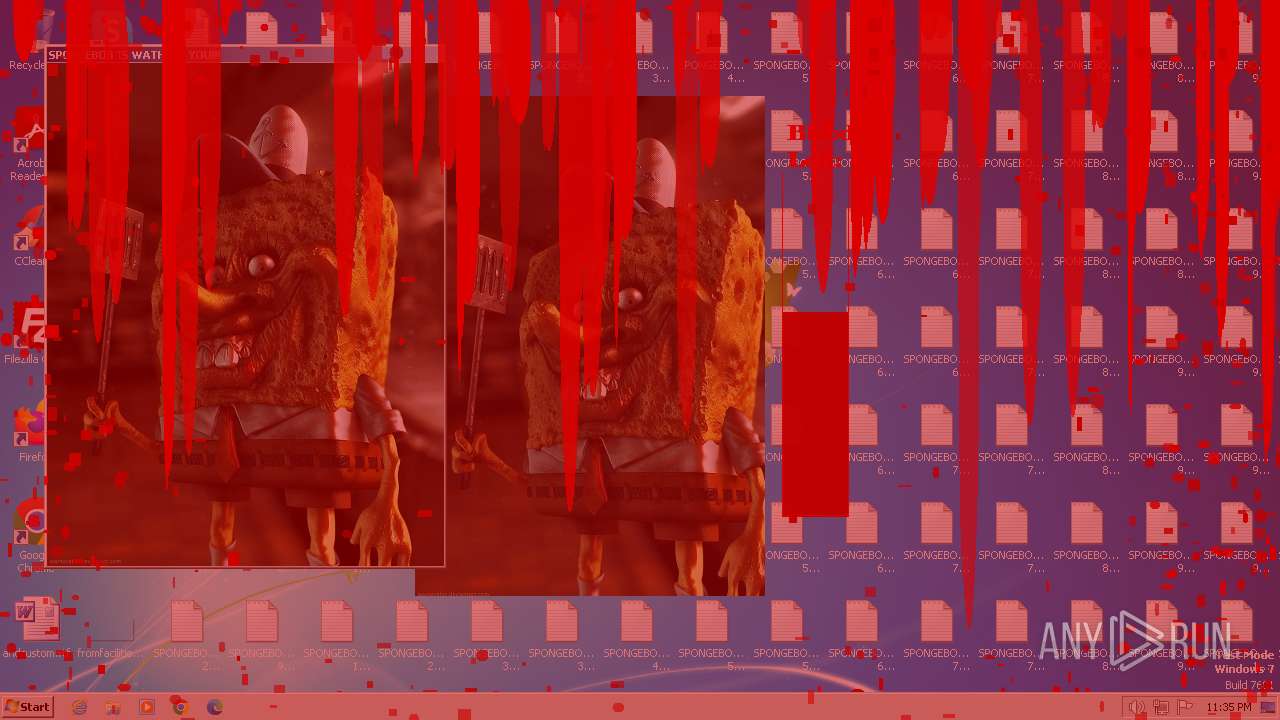
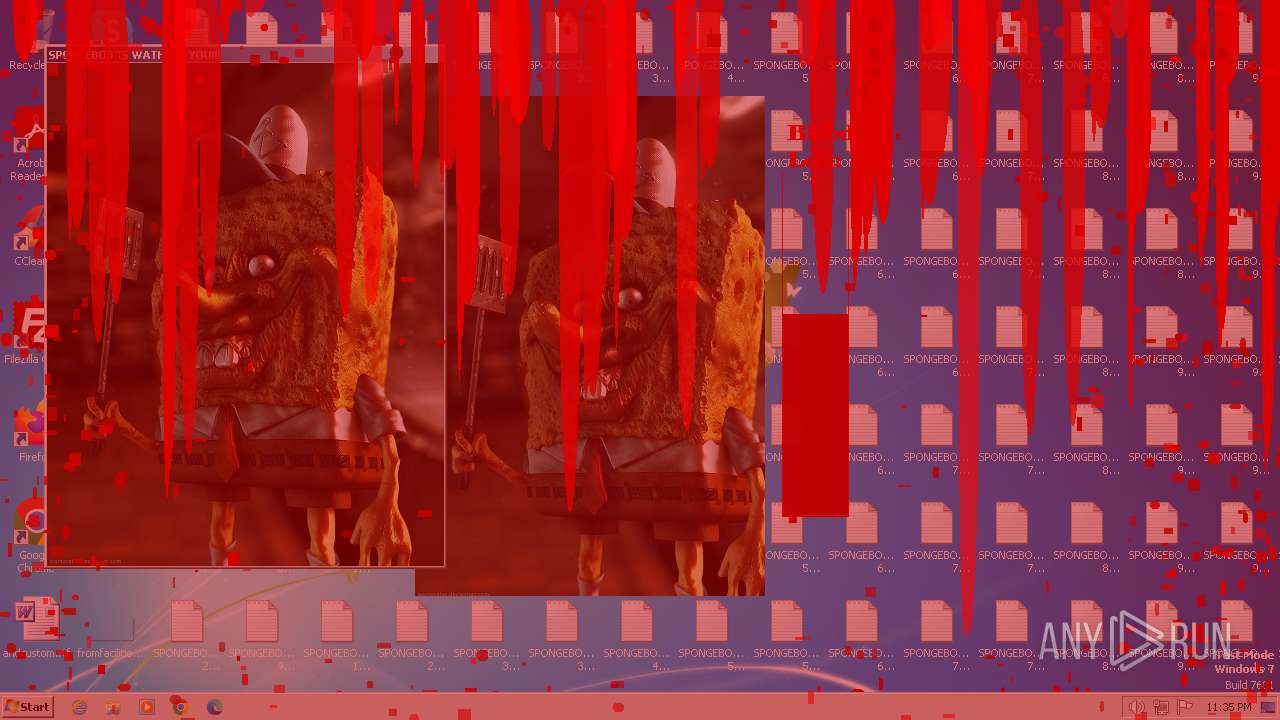
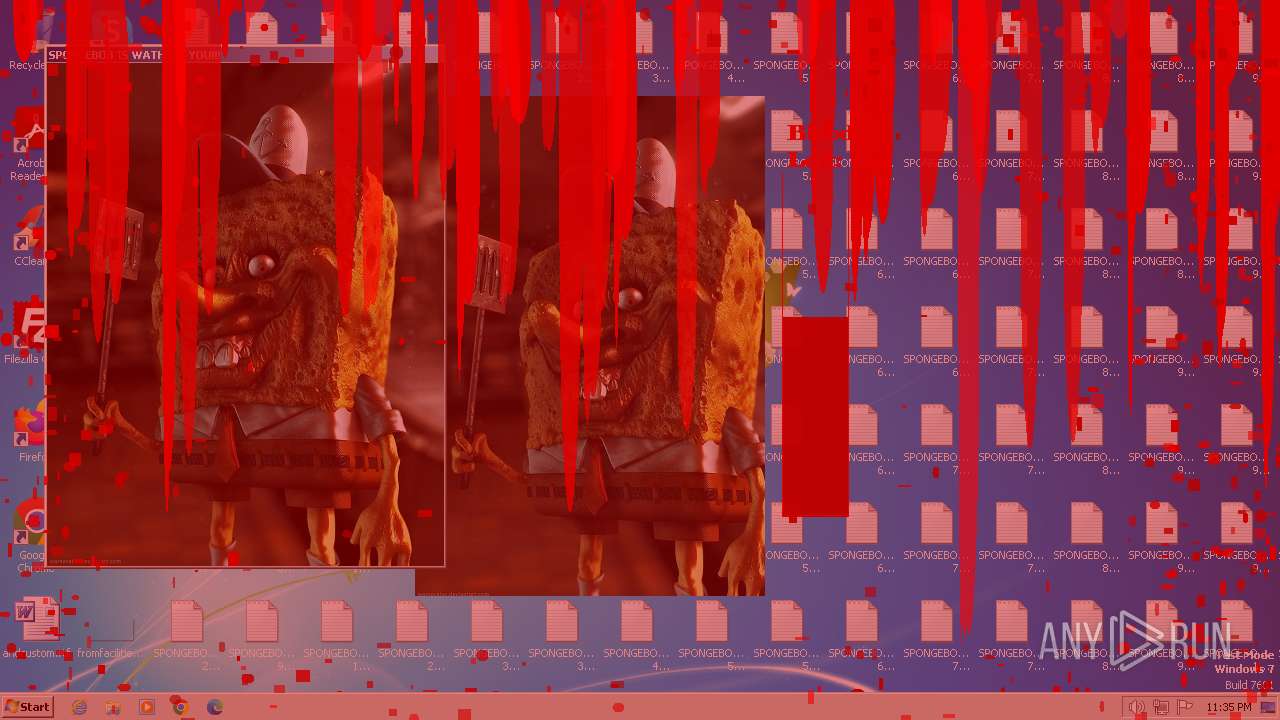
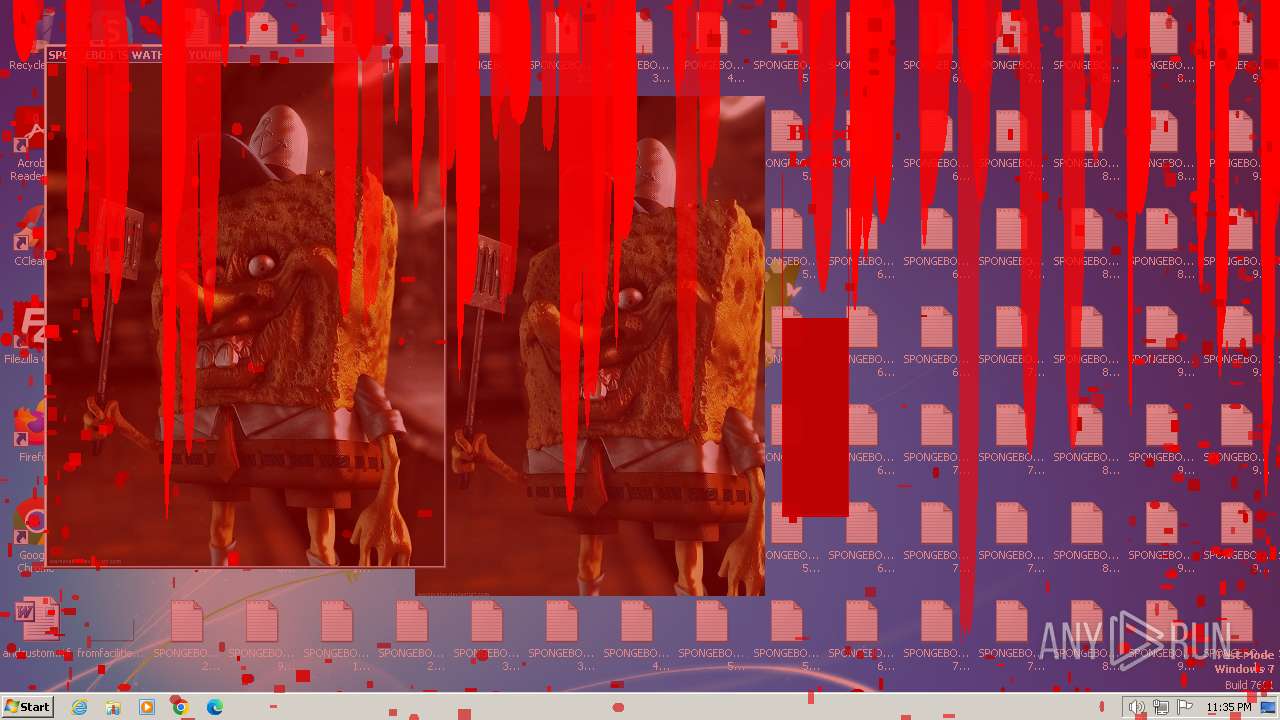
| File name: | SpongebobNoSleep2.exe |
| Full analysis: | https://app.any.run/tasks/d58e55b1-1485-4641-a875-6a4ed87b050e |
| Verdict: | Malicious activity |
| Analysis date: | June 24, 2024, 22:33:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | B05FBD1BFD40E5632C36341D1F4CAE47 |
| SHA1: | 383DF2DFD995236DB0C5ABCF84D867F2117215E7 |
| SHA256: | D090C4B65F8F3145301E612F6007996C2408A140FBFD09B608CEE3D4A273FF26 |
| SSDEEP: | 196608:HB5HVbnvf/tlSZSKWdPcYpdo5V30UsnzKTFQCZ+nE2bZq3WFGuUa:DVrnVlitW0MowTnzwFv+ZqGFdl |
MALICIOUS
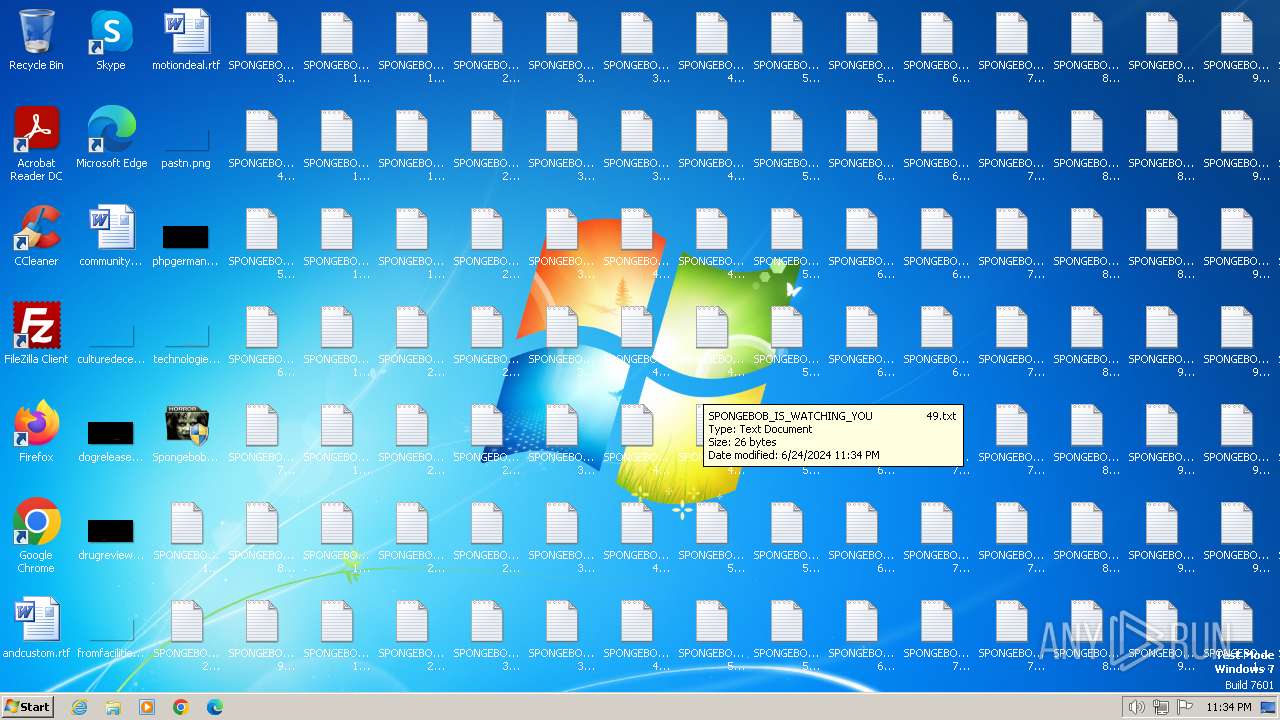
Drops the executable file immediately after the start
- SpongebobNoSleep2.exe (PID: 3128)
- cmd.exe (PID: 3152)
Gets path to any of the special folders (SCRIPT)
- wscript.exe (PID: 3164)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 3164)
Changes the login/logoff helper path in the registry
- gdifuncs.exe (PID: 4032)
Task Manager has been disabled (taskmgr)
- gdifuncs.exe (PID: 4032)
Disables Windows Defender
- gdifuncs.exe (PID: 4032)
Modify registry editing tools (regedit)
- gdifuncs.exe (PID: 4032)
Disables the Run the Start menu
- gdifuncs.exe (PID: 4032)
SUSPICIOUS
Reads security settings of Internet Explorer
- SpongebobNoSleep2.exe (PID: 3128)
Executable content was dropped or overwritten
- SpongebobNoSleep2.exe (PID: 3128)
- cmd.exe (PID: 3152)
The process executes VB scripts
- SpongebobNoSleep2.exe (PID: 3128)
Reads the Internet Settings
- SpongebobNoSleep2.exe (PID: 3128)
- wscript.exe (PID: 3164)
Runs WScript without displaying logo
- wscript.exe (PID: 3164)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 3164)
Writes binary data to a Stream object (SCRIPT)
- wscript.exe (PID: 3164)
Runs shell command (SCRIPT)
- wscript.exe (PID: 3164)
Executing commands from ".cmd" file
- wscript.exe (PID: 3164)
Uses RUNDLL32.EXE to load library
- cmd.exe (PID: 3152)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 3164)
Creates file in the systems drive root
- cmd.exe (PID: 3152)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 3152)
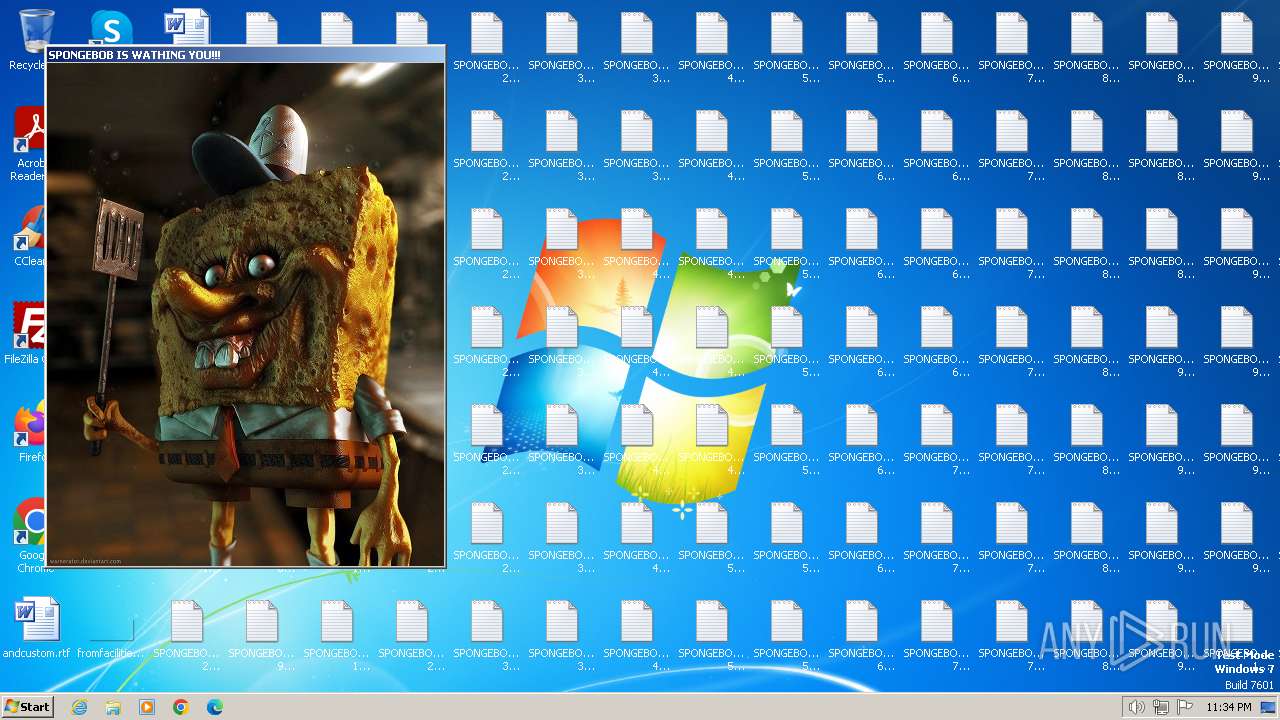
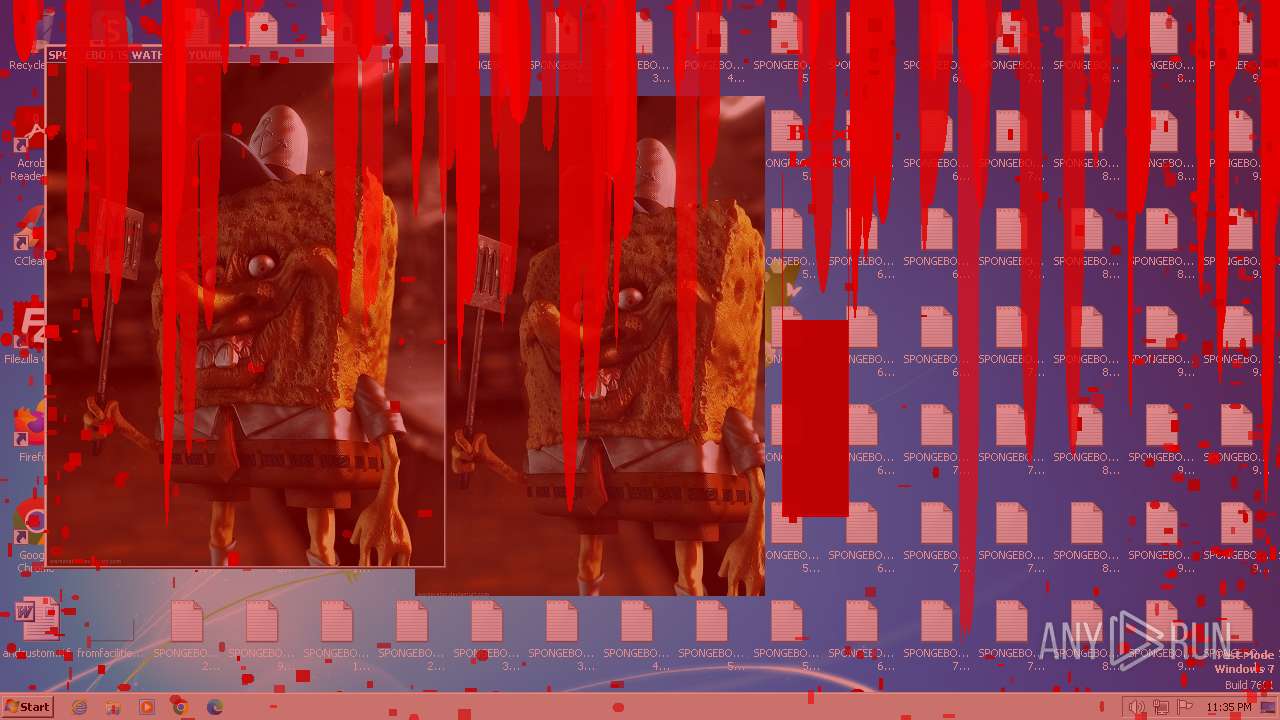
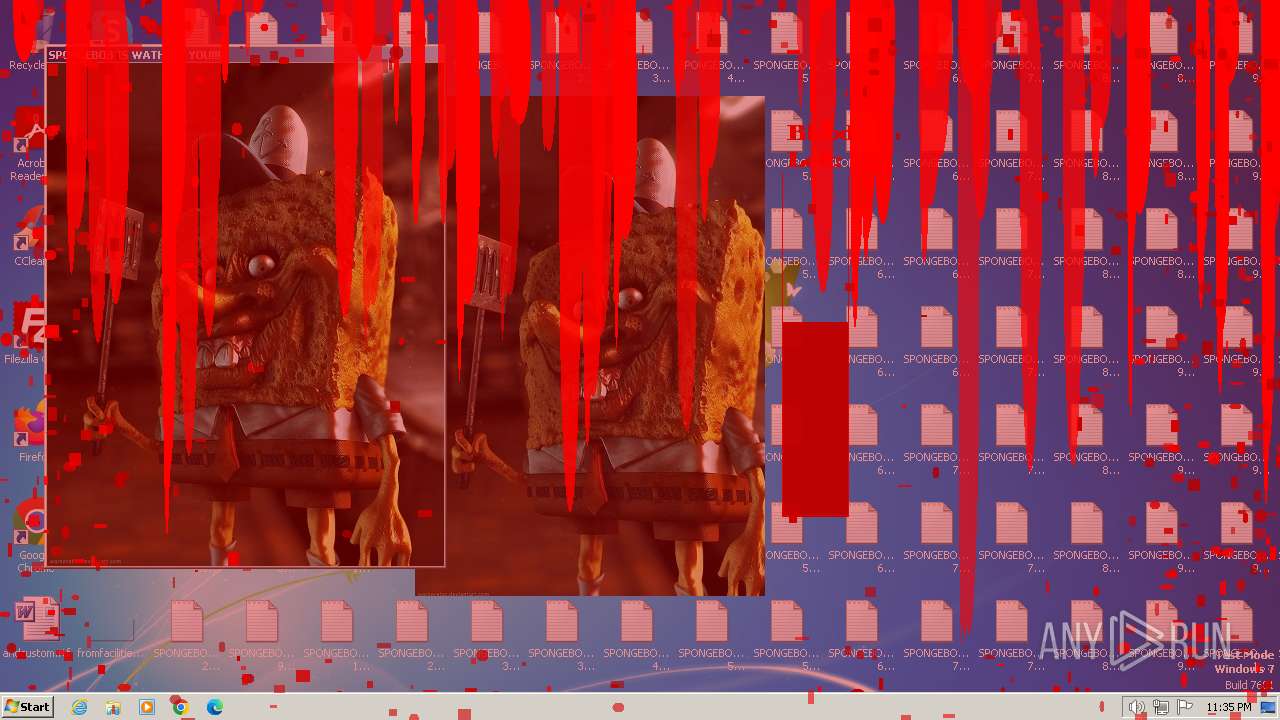
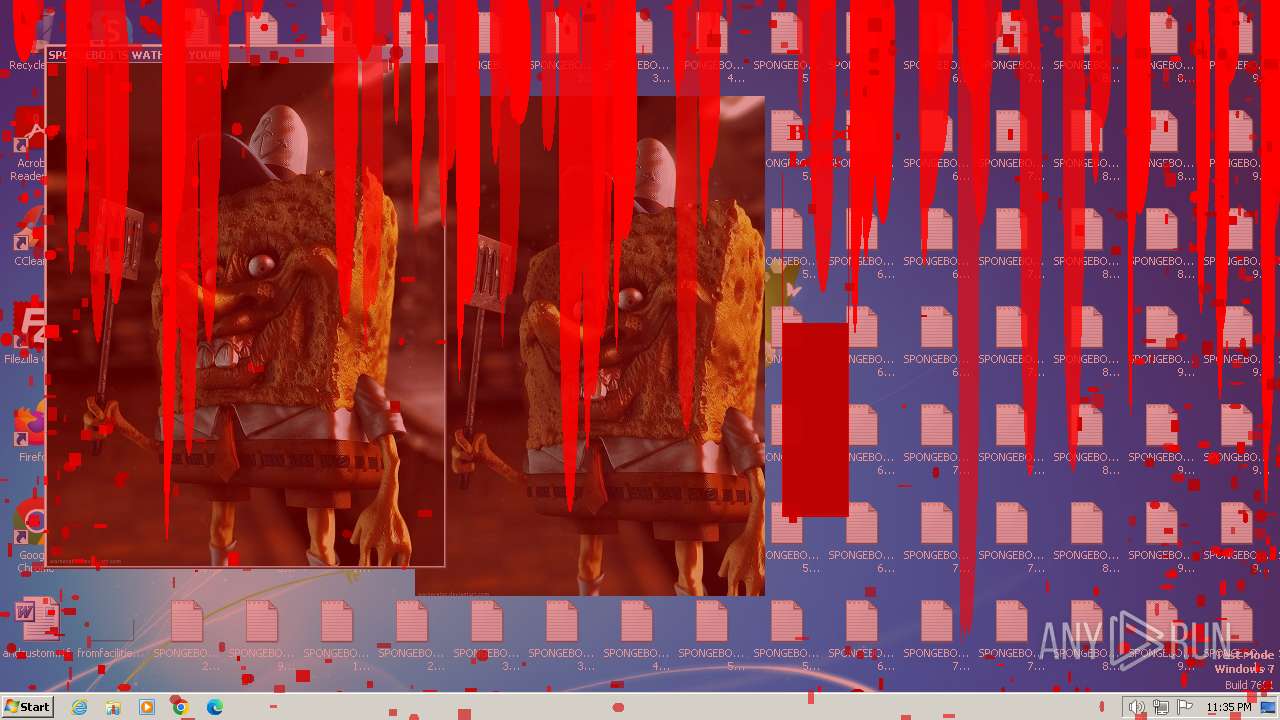
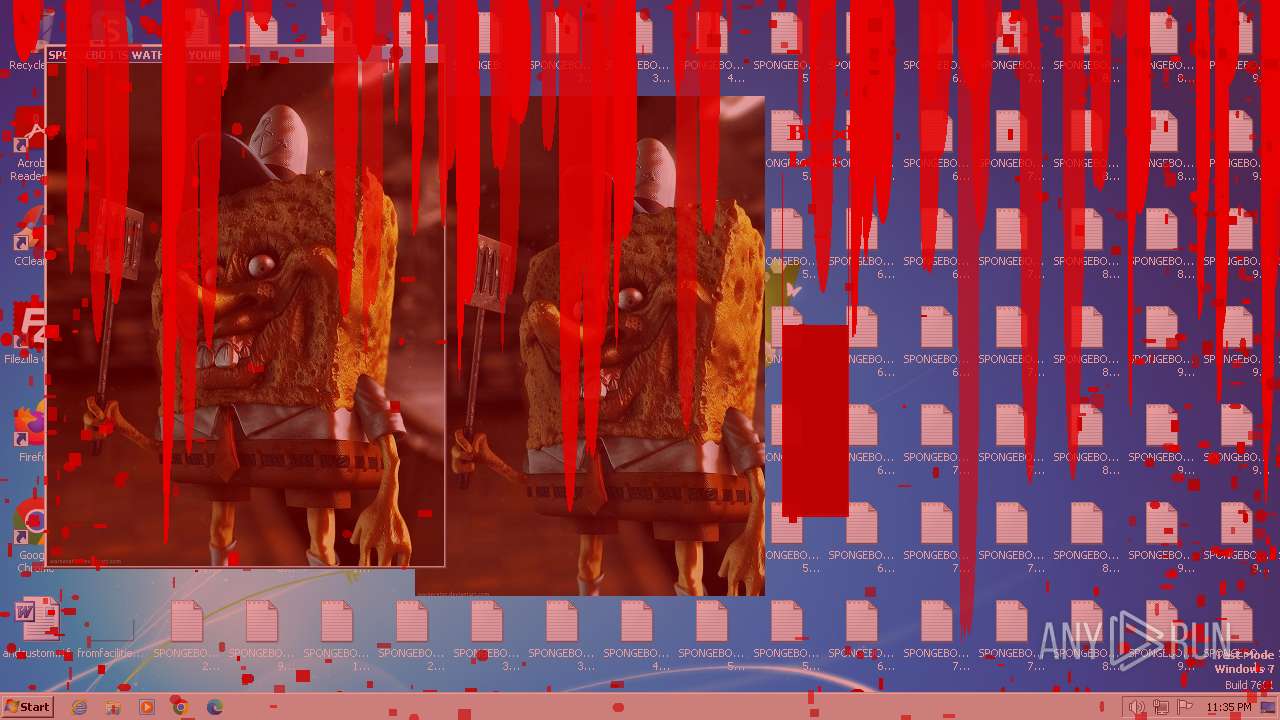
Changes the desktop background image
- reg.exe (PID: 3476)
Creates or modifies Windows services
- gdifuncs.exe (PID: 4032)
INFO
Checks supported languages
- SpongebobNoSleep2.exe (PID: 3128)
- mbr.exe (PID: 2432)
- gdifuncs.exe (PID: 4032)
- MainWindow.exe (PID: 4028)
Create files in a temporary directory
- SpongebobNoSleep2.exe (PID: 3128)
Reads the computer name
- SpongebobNoSleep2.exe (PID: 3128)
- gdifuncs.exe (PID: 4032)
Reads the machine GUID from the registry
- gdifuncs.exe (PID: 4032)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (41) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.6) |
| .exe | | | Win32 Executable (generic) (5.9) |
| .exe | | | Win16/32 Executable Delphi generic (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:02:01 20:46:09+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 66048 |
| InitializedDataSize: | 10260992 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.6.6.6 |
| ProductVersionNumber: | 5.6.6.6 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Debug, Pre-release, Private build |
| FileOS: | Windows 16-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| FileVersion: | 5.6.6.6 |
| ProductVersion: | 5.6.6.6 |
| ProductName: | SpongebobNoSleep2 |
| OriginalFileName: | HorrorBob5.exe |
| InternalName: | HorrorBob5 |
| FileDescription: | SPONGEBOB IS WATCHING YOU! |
| CompanyName: | HorrorTrojans |
| LegalCopyright: | 2022 |
Total processes
85
Monitored processes
43
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 268 | RUNDLL32.EXE user32.dll,UpdatePerUserSystemParameters | C:\Windows\System32\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 524 | RUNDLL32.EXE user32.dll,UpdatePerUserSystemParameters | C:\Windows\System32\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 568 | RUNDLL32.EXE user32.dll,UpdatePerUserSystemParameters | C:\Windows\System32\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 764 | RUNDLL32.EXE user32.dll,UpdatePerUserSystemParameters | C:\Windows\System32\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1172 | RUNDLL32.EXE user32.dll,UpdatePerUserSystemParameters | C:\Windows\System32\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1476 | RUNDLL32.EXE user32.dll,UpdatePerUserSystemParameters | C:\Windows\System32\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1596 | RUNDLL32.EXE user32.dll,UpdatePerUserSystemParameters | C:\Windows\System32\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1620 | RUNDLL32.EXE user32.dll,UpdatePerUserSystemParameters | C:\Windows\System32\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1828 | RUNDLL32.EXE user32.dll,UpdatePerUserSystemParameters | C:\Windows\System32\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2136 | RUNDLL32.EXE user32.dll,UpdatePerUserSystemParameters | C:\Windows\System32\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
13 108
Read events
11 542
Write events
1 566
Delete events
0
Modification events
| (PID) Process: | (3128) SpongebobNoSleep2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3128) SpongebobNoSleep2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3128) SpongebobNoSleep2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3128) SpongebobNoSleep2.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3164) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3164) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3164) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3164) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3476) reg.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | Wallpaper |
Value: c:\bg.bmp | |||
| (PID) Process: | (3164) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Speech\CurrentUserLexicon |
| Operation: | write | Name: | CLSID |
Value: {C9E37C15-DF92-4727-85D6-72E5EEB6995A} | |||
Executable files
4
Suspicious files
2
Text files
10
Unknown types
195
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3128 | SpongebobNoSleep2.exe | C:\Users\admin\AppData\Local\Temp\F559.tmp\mainbgtheme.wav | — | |
MD5:— | SHA256:— | |||
| 3128 | SpongebobNoSleep2.exe | C:\Users\admin\AppData\Local\Temp\F559.tmp\MainWindow.exe | executable | |
MD5:7C92316762D584133B9CABF31AB6709B | SHA256:01995C3715C30C0C292752448516B94485DB51035C3A4F86EB18C147F10B6298 | |||
| 3164 | wscript.exe | C:\Users\admin\Desktop\SPONGEBOB_IS_WATCHING_YOU 5.txt | sp | |
MD5:BB6D68D7181108015CD381C28360DFC4 | SHA256:AEA8FB9235900760AC374C6A4A10FBA62C2A0EF5BEA2DD7EF4DB70FE55E0B317 | |||
| 3164 | wscript.exe | C:\Users\admin\Desktop\SPONGEBOB_IS_WATCHING_YOU 4.txt | sp | |
MD5:BB6D68D7181108015CD381C28360DFC4 | SHA256:AEA8FB9235900760AC374C6A4A10FBA62C2A0EF5BEA2DD7EF4DB70FE55E0B317 | |||
| 3164 | wscript.exe | C:\Users\admin\Desktop\SPONGEBOB_IS_WATCHING_YOU 3.txt | sp | |
MD5:BB6D68D7181108015CD381C28360DFC4 | SHA256:AEA8FB9235900760AC374C6A4A10FBA62C2A0EF5BEA2DD7EF4DB70FE55E0B317 | |||
| 3164 | wscript.exe | C:\Users\admin\Desktop\SPONGEBOB_IS_WATCHING_YOU 2.txt | sp | |
MD5:BB6D68D7181108015CD381C28360DFC4 | SHA256:AEA8FB9235900760AC374C6A4A10FBA62C2A0EF5BEA2DD7EF4DB70FE55E0B317 | |||
| 3164 | wscript.exe | C:\Users\admin\Desktop\SPONGEBOB_IS_WATCHING_YOU 8.txt | sp | |
MD5:BB6D68D7181108015CD381C28360DFC4 | SHA256:AEA8FB9235900760AC374C6A4A10FBA62C2A0EF5BEA2DD7EF4DB70FE55E0B317 | |||
| 3164 | wscript.exe | C:\Users\admin\Desktop\SPONGEBOB_IS_WATCHING_YOU 12.txt | sp | |
MD5:BB6D68D7181108015CD381C28360DFC4 | SHA256:AEA8FB9235900760AC374C6A4A10FBA62C2A0EF5BEA2DD7EF4DB70FE55E0B317 | |||
| 3164 | wscript.exe | C:\Users\admin\Desktop\SPONGEBOB_IS_WATCHING_YOU 7.txt | sp | |
MD5:BB6D68D7181108015CD381C28360DFC4 | SHA256:AEA8FB9235900760AC374C6A4A10FBA62C2A0EF5BEA2DD7EF4DB70FE55E0B317 | |||
| 3128 | SpongebobNoSleep2.exe | C:\Users\admin\AppData\Local\Temp\F559.tmp\mbr.exe | executable | |
MD5:33BD7D68378C2E3AA4E06A6A85879F63 | SHA256:6E79302D7AE9CC69E4FD1BA77BD4315D5E09F7A173B55BA823D6069A587A2E05 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
12
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a9f83325acc8ca75 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1372 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
2564 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1372 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1372 | svchost.exe | 199.232.214.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
1372 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |