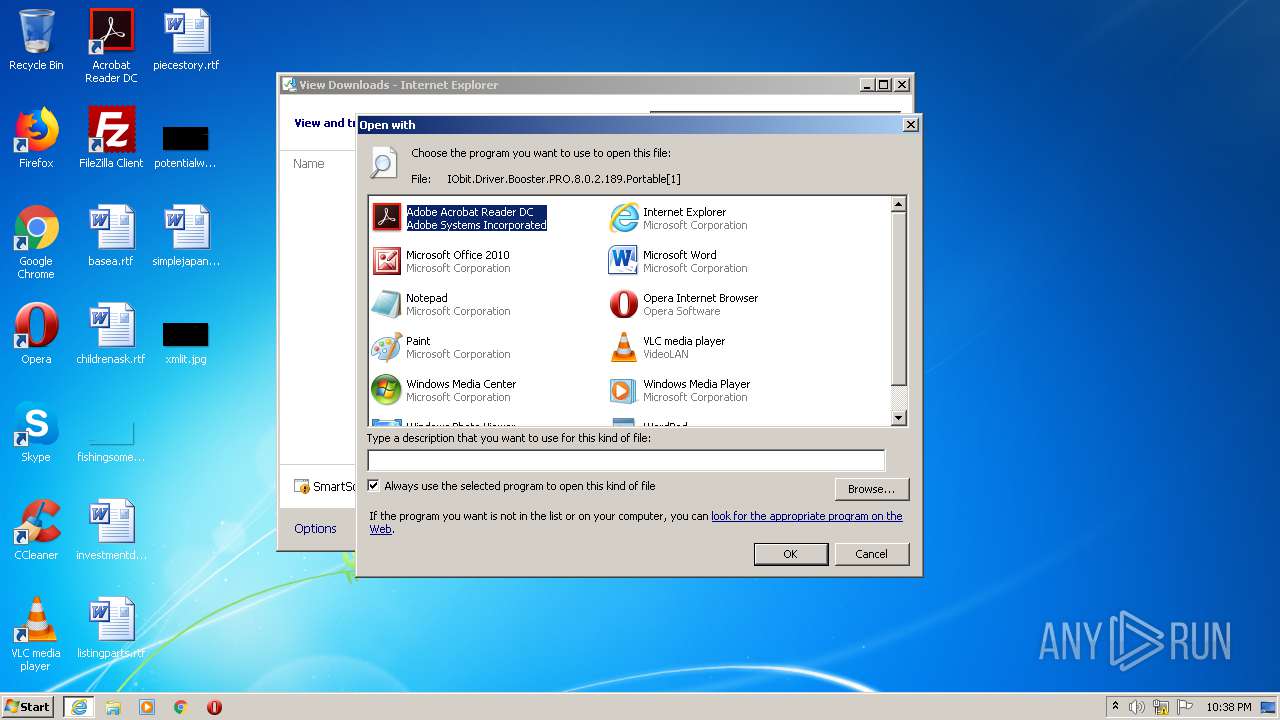
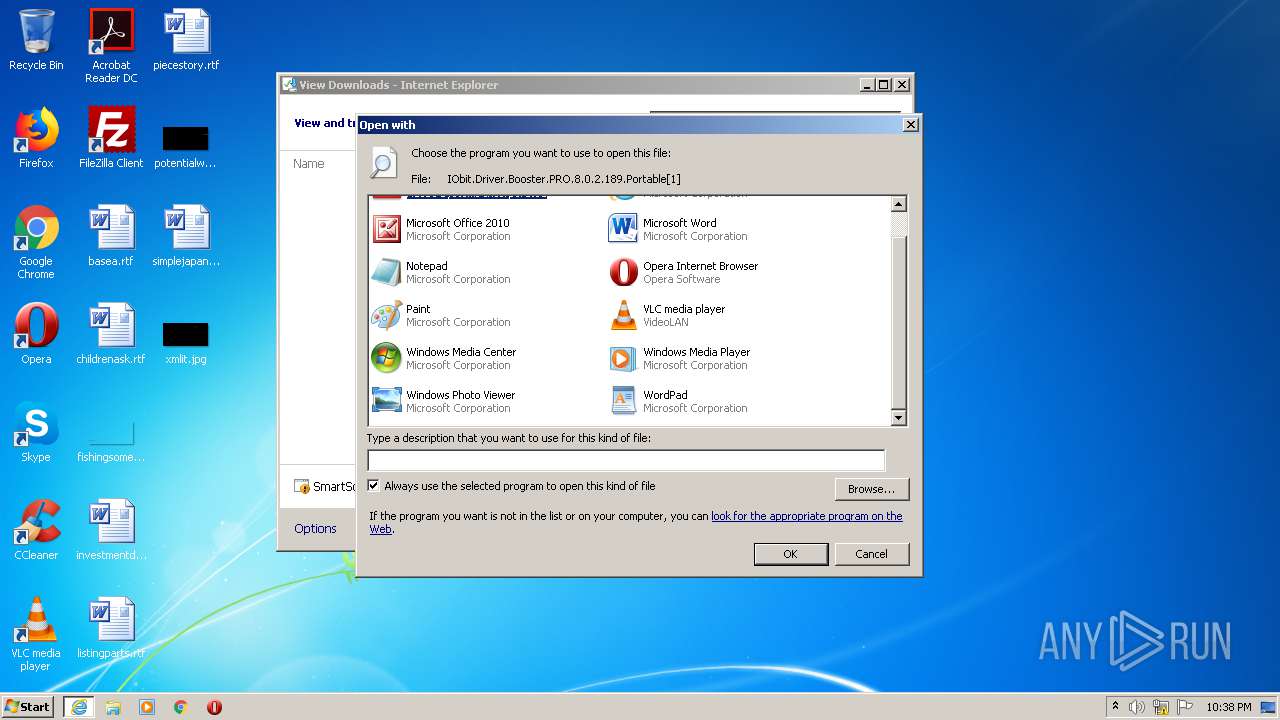
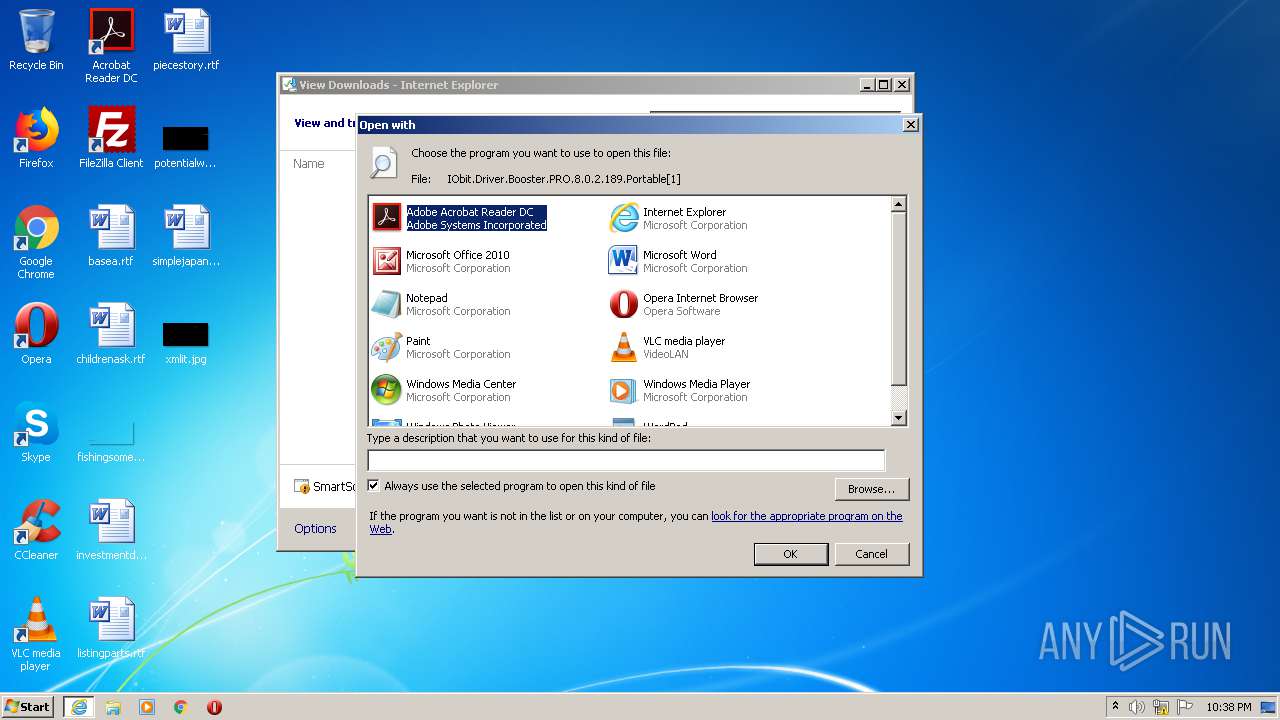
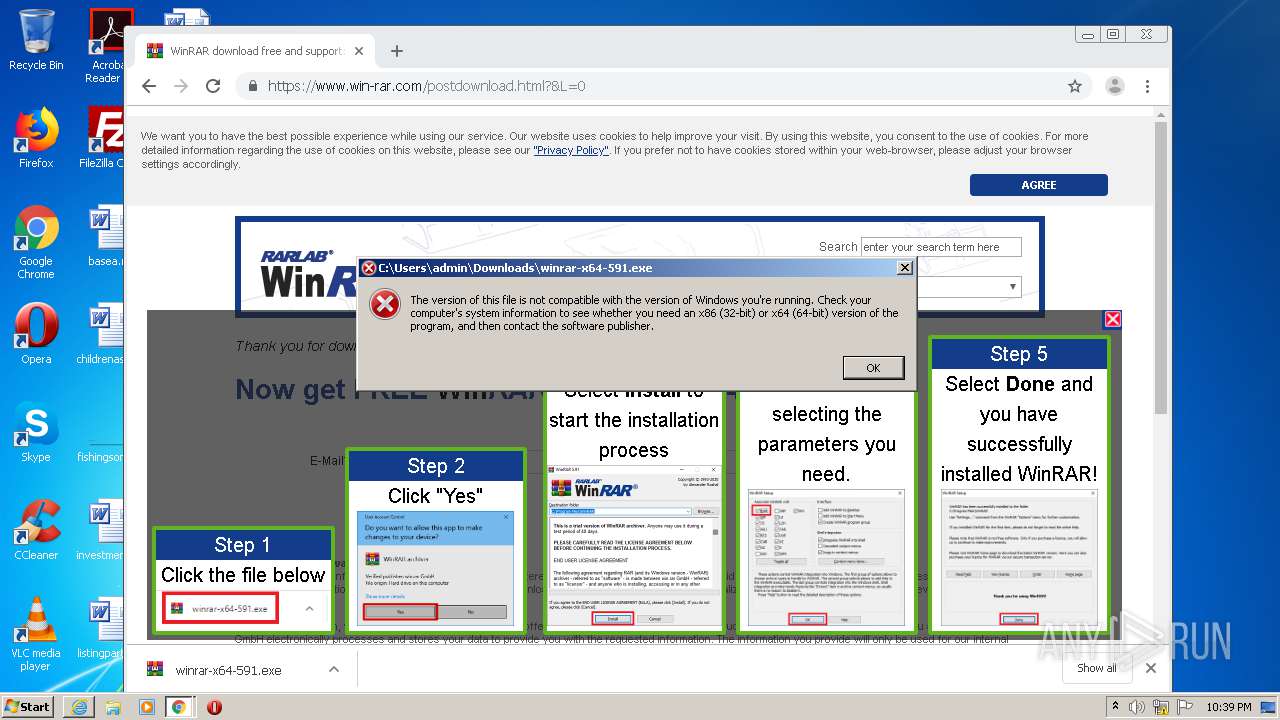
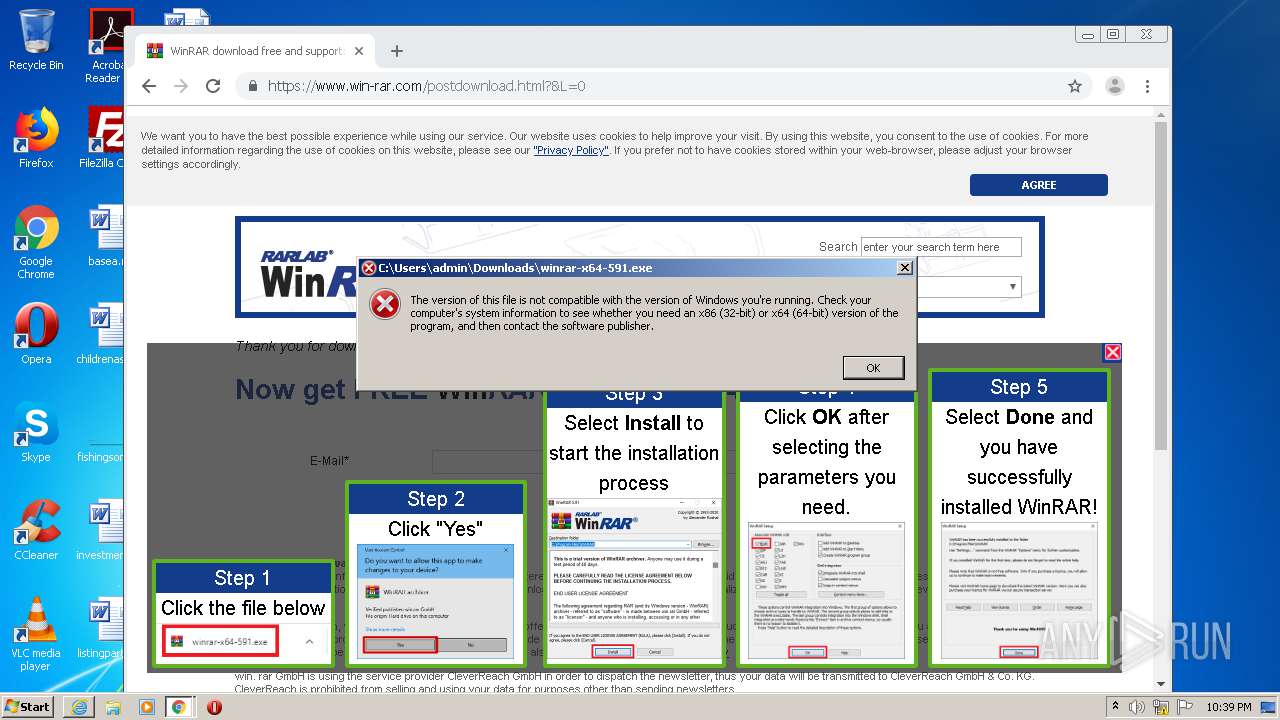
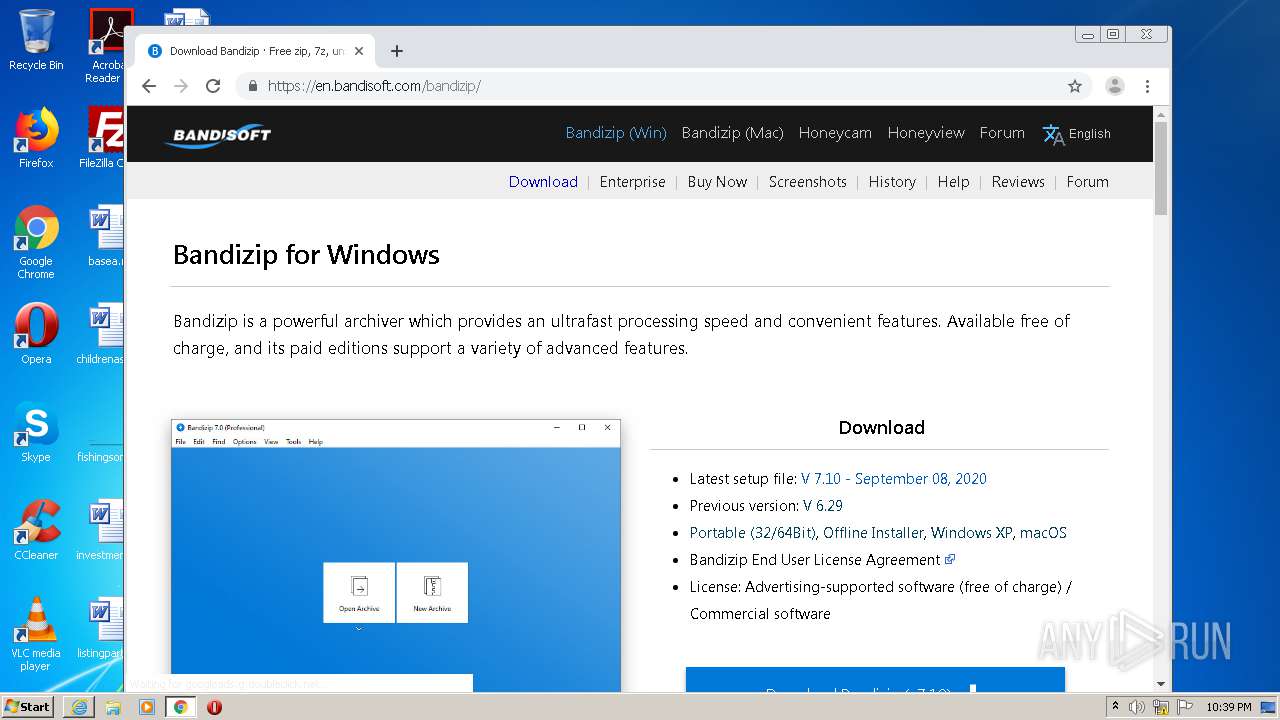
| URL: | https://dl2.soft98.ir/soft/i/IObit.Driver.Booster.PRO.8.0.2.189.Portable.exe?1601843672 |
| Full analysis: | https://app.any.run/tasks/0f802e2b-bb64-410f-bf27-06f0c36d8205 |
| Verdict: | Malicious activity |
| Analysis date: | October 04, 2020, 21:37:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 6C487810BA6D23519154424253BD1015 |
| SHA1: | 0E80D16DB32AC7BFD1441447135C70CDC48A97C0 |
| SHA256: | D07A9151E31BCB8C163D04C263C924B54936F116996557BC319DC2BC82B1C2E5 |
| SSDEEP: | 3:N8RyK4RHNbKNmR3wzE6AypBn:2cRHNWhQVQB |
MALICIOUS
Application was dropped or rewritten from another process
- BANDIZIP-SETUP-ONLINE.EXE (PID: 3512)
- BANDIZIP-SETUP-ONLINE.EXE (PID: 928)
- BANDIZIP-SETUP-STD-X86.EXE (PID: 4008)
- RegDll.x86.exe (PID: 2316)
- Bandizip.exe (PID: 4000)
- RegDll.x86.exe (PID: 3992)
- RegDll.x86.exe (PID: 3328)
- RegDll.x86.exe (PID: 3120)
- RegDll.x86.exe (PID: 1932)
- RegDll.x86.exe (PID: 2112)
- Bandizip.exe (PID: 1492)
- Bandizip.exe (PID: 2492)
- updater.exe (PID: 2808)
Changes settings of System certificates
- BANDIZIP-SETUP-ONLINE.EXE (PID: 928)
Loads dropped or rewritten executable
- RegDll.x86.exe (PID: 3328)
SUSPICIOUS
Executable content was dropped or overwritten
- chrome.exe (PID: 2656)
- chrome.exe (PID: 3448)
- iexplore.exe (PID: 2232)
- BANDIZIP-SETUP-ONLINE.EXE (PID: 928)
- BANDIZIP-SETUP-STD-X86.EXE (PID: 4008)
Uses RUNDLL32.EXE to load library
- iexplore.exe (PID: 2232)
Reads Internet Cache Settings
- BANDIZIP-SETUP-ONLINE.EXE (PID: 928)
- BANDIZIP-SETUP-STD-X86.EXE (PID: 4008)
- Bandizip.exe (PID: 2492)
- updater.exe (PID: 2808)
Adds / modifies Windows certificates
- BANDIZIP-SETUP-ONLINE.EXE (PID: 928)
Creates files in the program directory
- BANDIZIP-SETUP-STD-X86.EXE (PID: 4008)
Changes IE settings (feature browser emulation)
- RegDll.x86.exe (PID: 3992)
- RegDll.x86.exe (PID: 2316)
- RegDll.x86.exe (PID: 3120)
Creates COM task schedule object
- RegDll.x86.exe (PID: 3328)
Modifies the open verb of a shell class
- BANDIZIP-SETUP-STD-X86.EXE (PID: 4008)
- Bandizip.exe (PID: 1492)
- Bandizip.exe (PID: 4000)
Executed via COM
- explorer.exe (PID: 3736)
Creates a software uninstall entry
- BANDIZIP-SETUP-STD-X86.EXE (PID: 4008)
Reads internet explorer settings
- updater.exe (PID: 2808)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 2232)
- iexplore.exe (PID: 2964)
- chrome.exe (PID: 2656)
Application launched itself
- iexplore.exe (PID: 2232)
- chrome.exe (PID: 2656)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2232)
Reads settings of System Certificates
- iexplore.exe (PID: 2232)
- iexplore.exe (PID: 2964)
- updater.exe (PID: 2808)
Changes internet zones settings
- iexplore.exe (PID: 2232)
Manual execution by user
- chrome.exe (PID: 2656)
- explorer.exe (PID: 1452)
Reads the hosts file
- chrome.exe (PID: 2656)
- chrome.exe (PID: 3448)
Changes settings of System certificates
- iexplore.exe (PID: 2232)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2232)
Creates files in the user directory
- iexplore.exe (PID: 2232)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
90
Monitored processes
46
Malicious processes
7
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 928 | "C:\Users\admin\Downloads\BANDIZIP-SETUP-ONLINE.EXE" | C:\Users\admin\Downloads\BANDIZIP-SETUP-ONLINE.EXE | chrome.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 996 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1000,12060107765833255668,8554809789190633895,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=7607401971724618038 --mojo-platform-channel-handle=3716 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 996 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1000,12060107765833255668,8554809789190633895,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=7135484568598857949 --mojo-platform-channel-handle=3368 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1240 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1000,12060107765833255668,8554809789190633895,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=12828997935750209499 --mojo-platform-channel-handle=3200 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1260 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6cd9a9d0,0x6cd9a9e0,0x6cd9a9ec | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1452 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1492 | "C:\Program Files\Bandizip\Bandizip.exe" /setdefaultprogram | C:\Program Files\Bandizip\Bandizip.exe | — | BANDIZIP-SETUP-STD-X86.EXE | |||||||||||
User: admin Company: Bandisoft.com Integrity Level: HIGH Description: Bandizip Exit code: 0 Version: 7.10.0.1 Modules
| |||||||||||||||
| 1704 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1000,12060107765833255668,8554809789190633895,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=7512852539673031885 --mojo-platform-channel-handle=3432 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1724 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1000,12060107765833255668,8554809789190633895,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=18320486010110789257 --renderer-client-id=22 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3980 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1932 | "C:\Program Files\Bandizip\data/RegDll.x86.exe" /removepath "C:\Program Files\Bandizip\7z" | C:\Program Files\Bandizip\data\RegDll.x86.exe | — | BANDIZIP-SETUP-STD-X86.EXE | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
4 505
Read events
2 943
Write events
1 556
Delete events
6
Modification events
| (PID) Process: | (2232) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 2906443526 | |||
| (PID) Process: | (2232) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30841494 | |||
| (PID) Process: | (2232) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2232) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2232) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2232) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2232) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2232) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A5000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2232) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2232) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
20
Suspicious files
103
Text files
212
Unknown types
24
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2964 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab88D8.tmp | — | |
MD5:— | SHA256:— | |||
| 2964 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar88D9.tmp | — | |
MD5:— | SHA256:— | |||
| 2232 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2964 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\IObit.Driver.Booster.PRO.8.0.2.189.Portable[1] | — | |
MD5:— | SHA256:— | |||
| 2964 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\IObit.Driver.Booster.PRO.8.0.2.189.Portable[1].6s419ew.partial | — | |
MD5:— | SHA256:— | |||
| 2232 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF5B90BB7F898C59B9.TMP | — | |
MD5:— | SHA256:— | |||
| 2232 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\IObit.Driver.Booster.PRO.8.0.2.189.Portable[1].6s419ew.partial:Zone.Identifier | — | |
MD5:— | SHA256:— | |||
| 2656 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-5F7A40D7-A60.pma | — | |
MD5:— | SHA256:— | |||
| 2964 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\1B1F4BA66CDBFEC85A20E11BF729AF23_AA85F8F9DAFF33153B5AEC2E983B94B6 | binary | |
MD5:— | SHA256:— | |||
| 2964 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\68FAF71AF355126BCA00CE2E73CC7374_123B8BA19C64CE9A8B3EAC32000FAF3E | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
24
TCP/UDP connections
59
DNS requests
51
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1056 | svchost.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAx5qUSwjBGVIJJhX%2BJrHYM%3D | US | der | 471 b | whitelisted |
1056 | svchost.exe | GET | 200 | 104.18.24.243:80 | http://ocsp.msocsp.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIGkp0%2Fv9GUvNUu1EP06Tu7%2BChyAQUkZ47RGw9V5xCdyo010%2FRzEqXLNoCEyAAASWxwt68EQiA3cUAAAABJbE%3D | US | der | 1.75 Kb | whitelisted |
2964 | iexplore.exe | GET | 200 | 151.139.236.246:80 | http://dvcasha2.ocsp-certum.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNcCPjJ499lHmfPUvPsRjzr1YchwQU5TGtvzoRlvSDvFA81LeQm5Du3iUCEAWpWwrs2dJ%2BsmlJJ9u4oAc%3D | US | der | 1.56 Kb | whitelisted |
1056 | svchost.exe | GET | 200 | 216.58.210.3:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjqTAc%2FHIGOD%2BaUx0%3D | US | der | 492 b | whitelisted |
2964 | iexplore.exe | GET | 200 | 151.139.236.246:80 | http://dvcasha2.ocsp-certum.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNcCPjJ499lHmfPUvPsRjzr1YchwQU5TGtvzoRlvSDvFA81LeQm5Du3iUCEAWpWwrs2dJ%2BsmlJJ9u4oAc%3D | US | der | 1.56 Kb | whitelisted |
1056 | svchost.exe | GET | 200 | 2.17.123.90:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | der | 781 b | whitelisted |
1056 | svchost.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
1056 | svchost.exe | GET | 200 | 173.223.60.216:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | US | der | 813 b | whitelisted |
1056 | svchost.exe | GET | 200 | 2.17.123.90:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | der | 1.11 Kb | whitelisted |
1056 | svchost.exe | GET | 200 | 2.17.123.90:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | der | 550 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2964 | iexplore.exe | 212.33.193.76:443 | dl2.soft98.ir | Honar Rayaneh Pooya Andisheh PJSC | IR | unknown |
2964 | iexplore.exe | 151.139.236.246:80 | subca.ocsp-certum.com | netDNA | US | unknown |
2232 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
1056 | svchost.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1056 | svchost.exe | 2.17.123.90:80 | crl.microsoft.com | Akamai International B.V. | — | unknown |
1056 | svchost.exe | 205.185.216.42:80 | www.download.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
1056 | svchost.exe | 173.223.60.216:80 | www.microsoft.com | GTT Communications Inc. | US | unknown |
3448 | chrome.exe | 172.217.23.99:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
1056 | svchost.exe | 104.18.24.243:80 | ocsp.msocsp.com | Cloudflare Inc | US | shared |
3448 | chrome.exe | 172.217.18.163:443 | www.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dl2.soft98.ir |
| suspicious |
subca.ocsp-certum.com |
| whitelisted |
www.bing.com |
| whitelisted |
api.bing.com |
| whitelisted |
dvcasha2.ocsp-certum.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
ocsp.msocsp.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
www.microsoft.com |
| whitelisted |