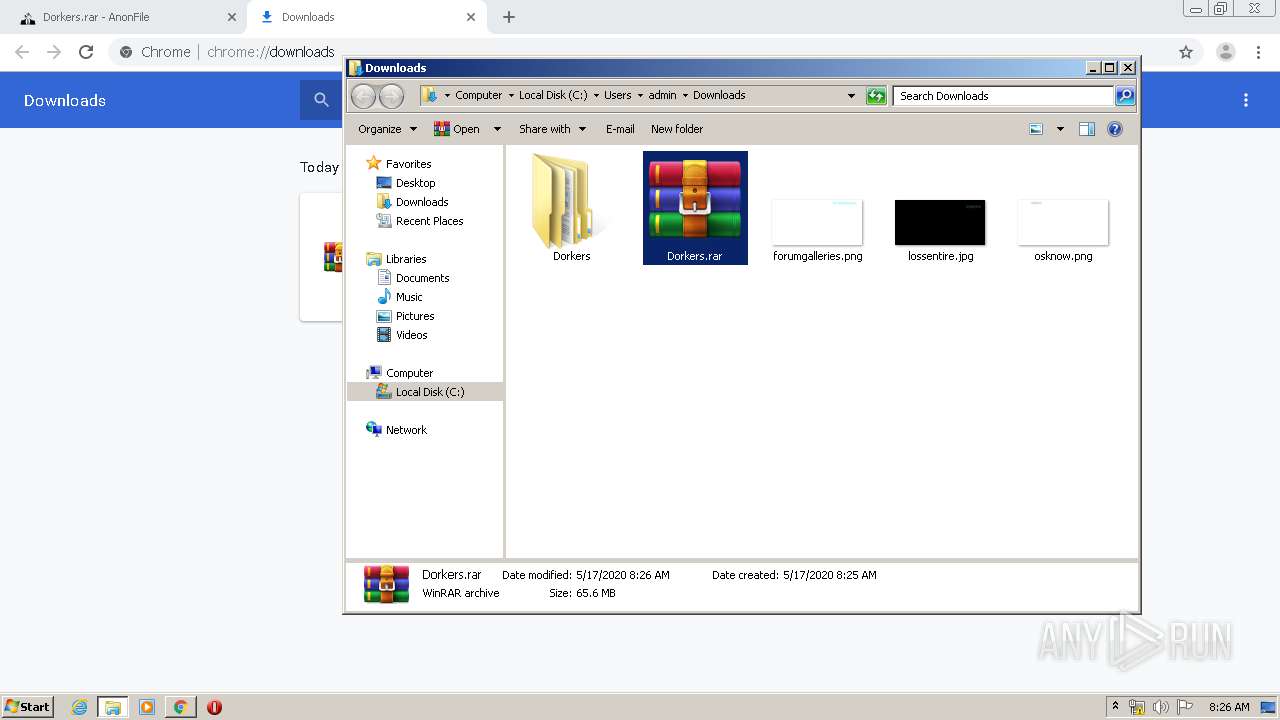
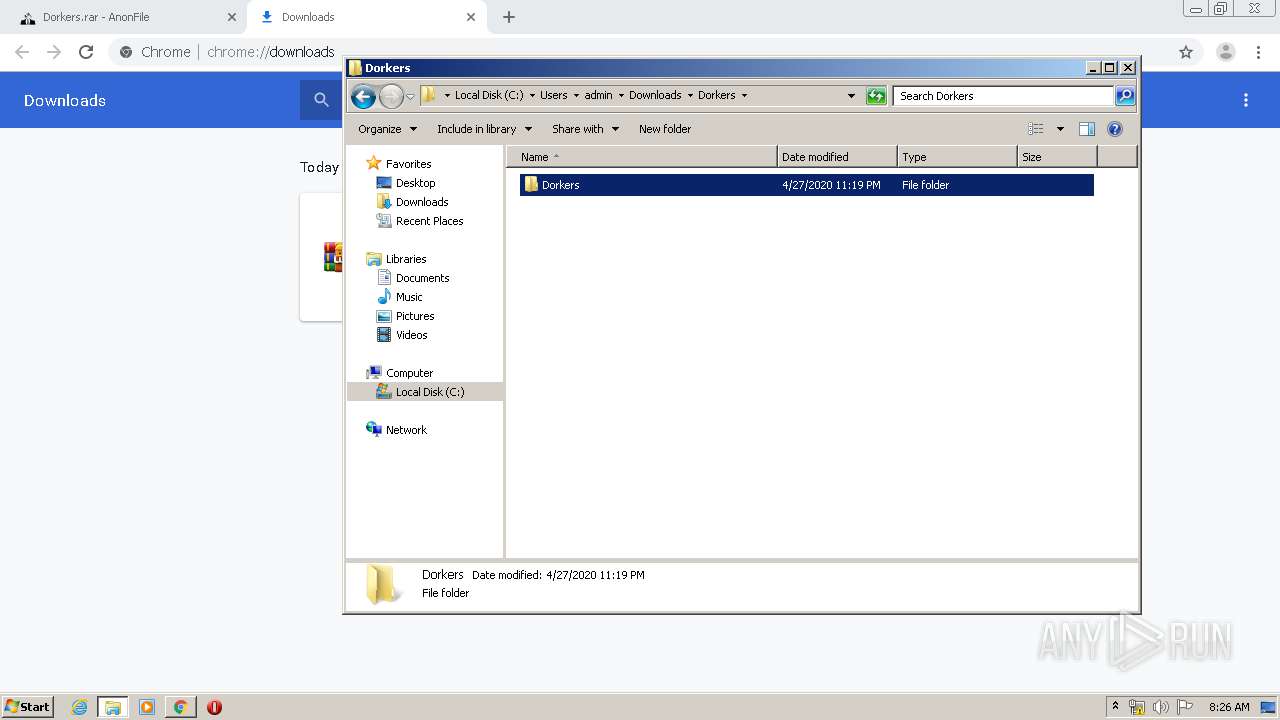
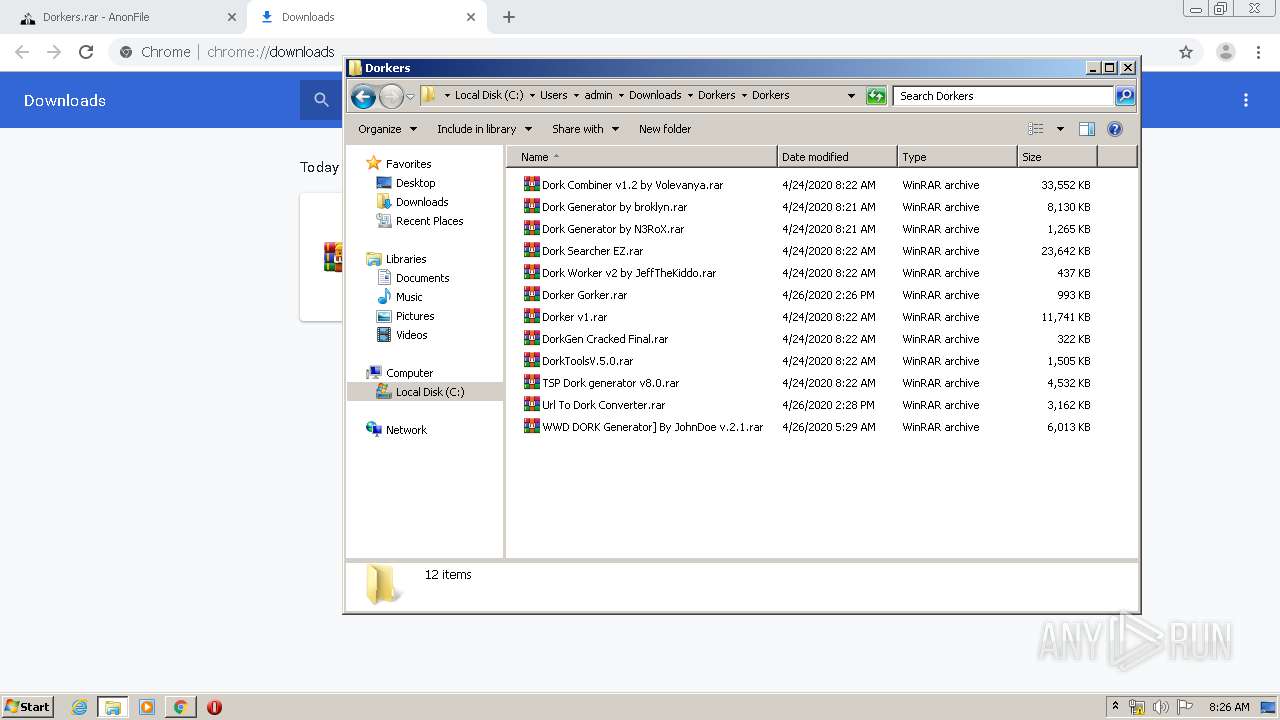
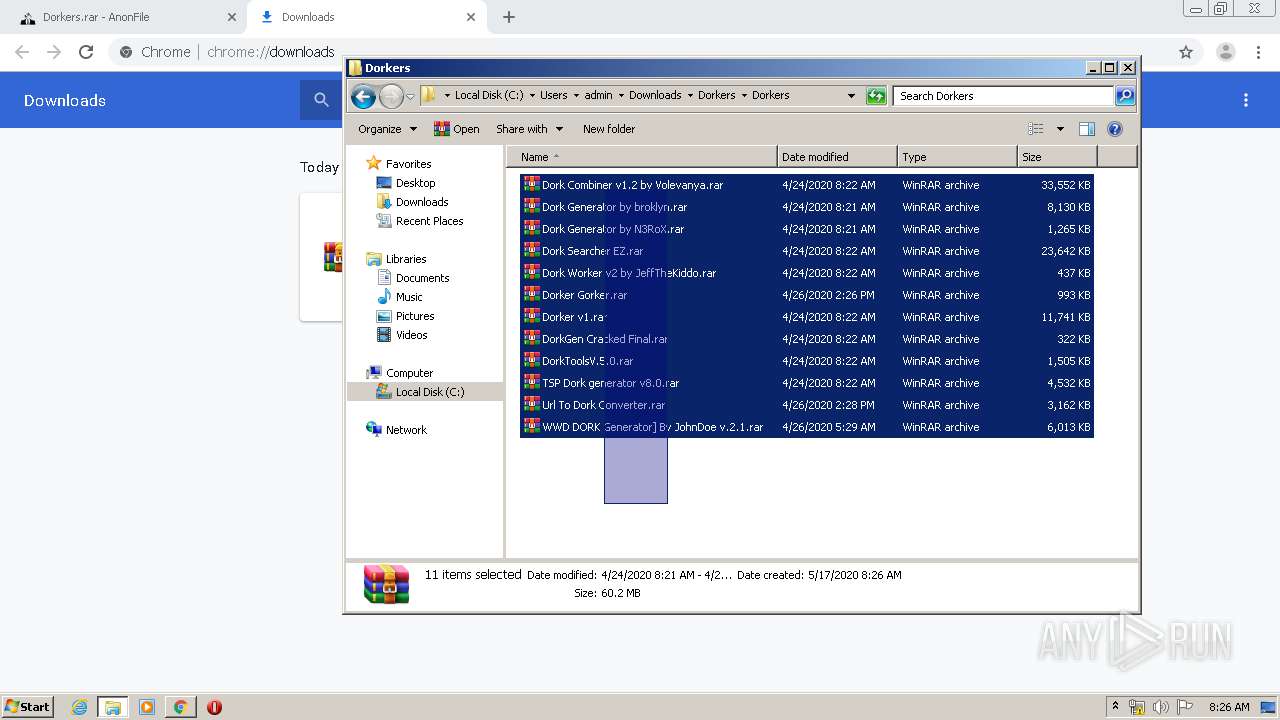
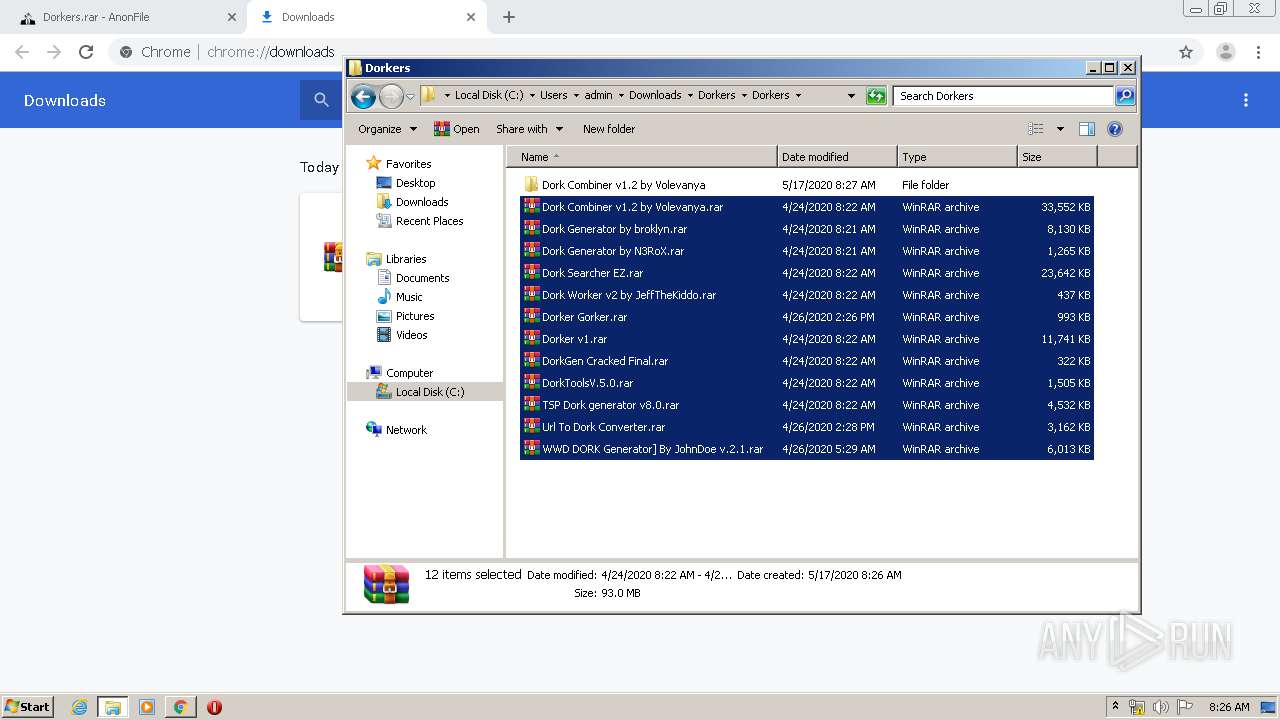
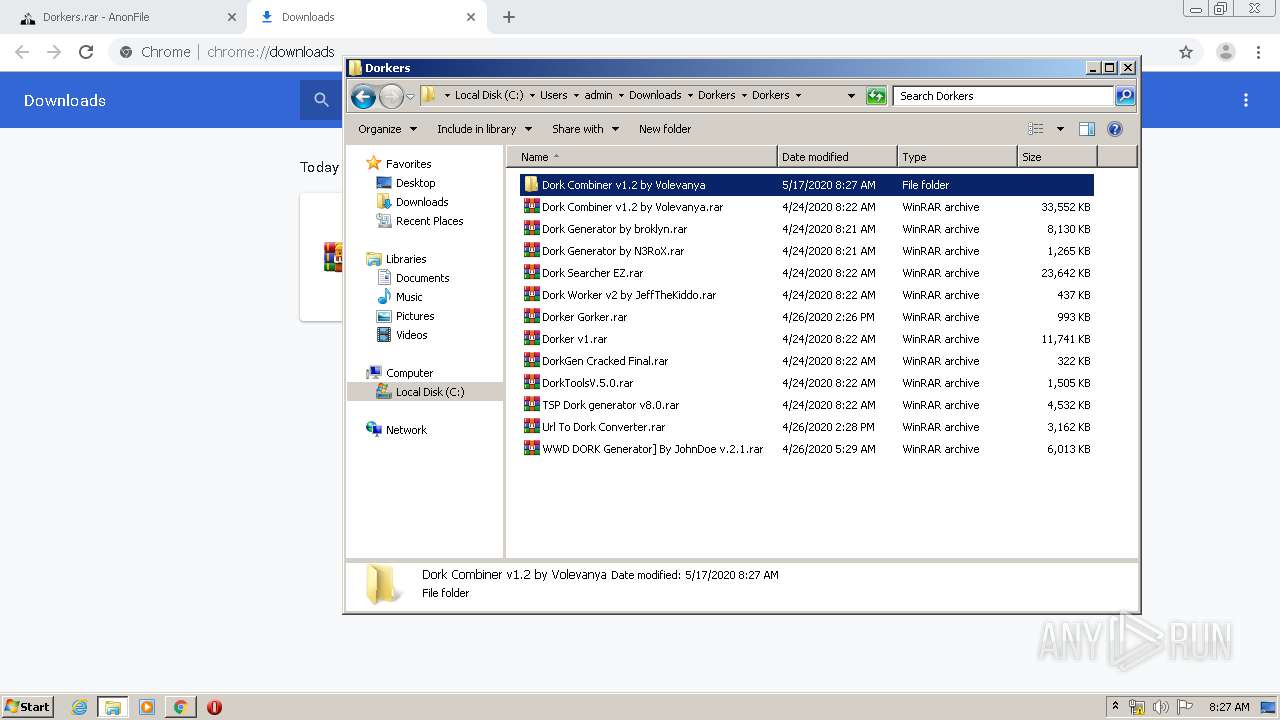
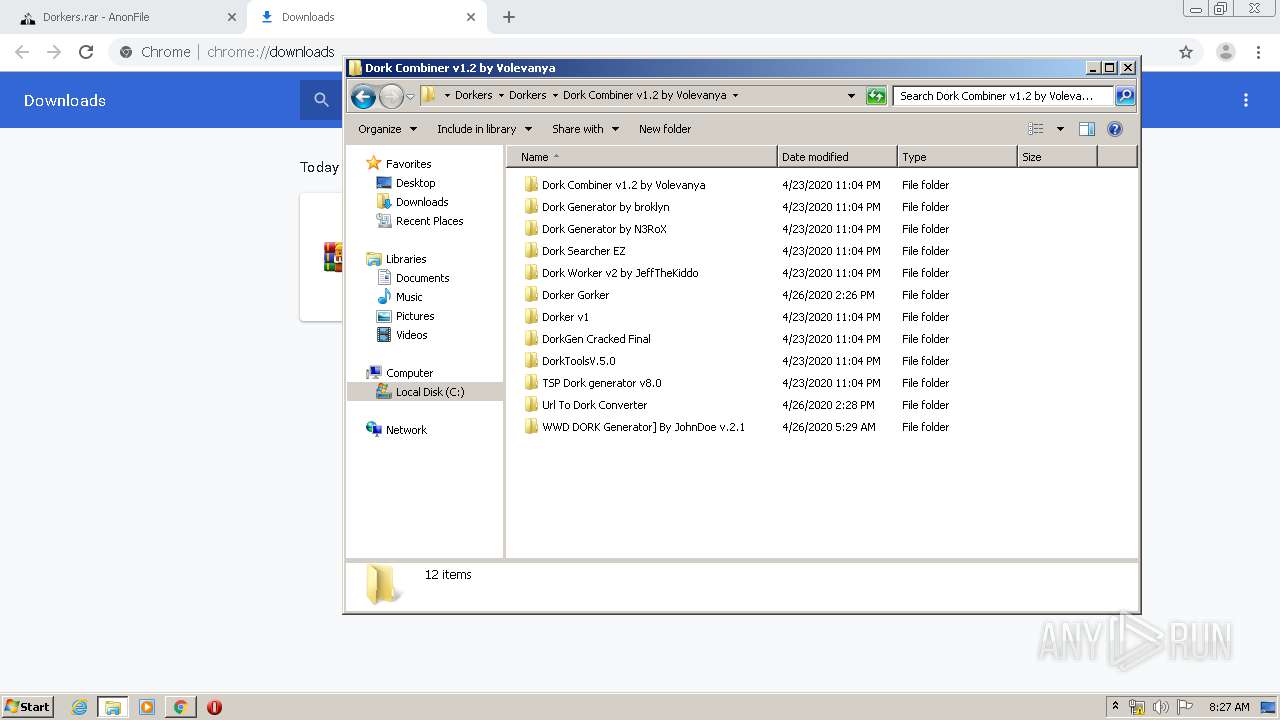
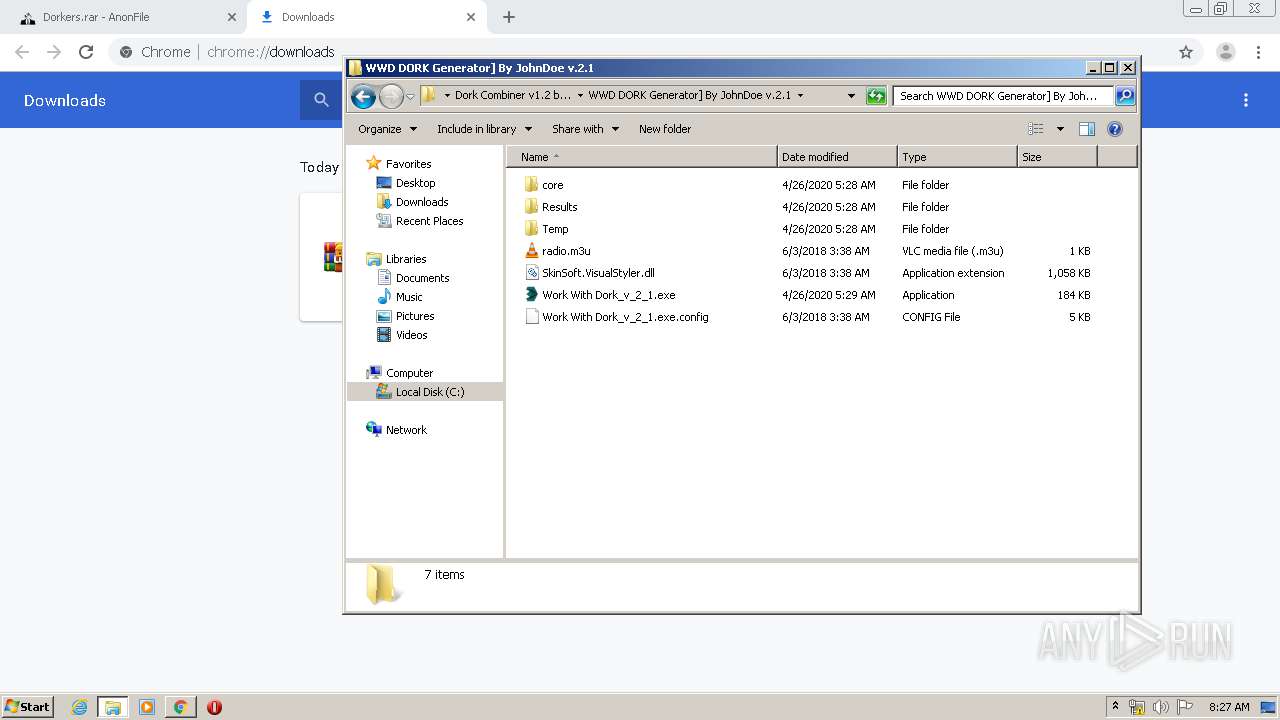
| URL: | https://anonfile.com/h2V0b0u5o9/Dorkers_rar |
| Full analysis: | https://app.any.run/tasks/072e474e-508f-40c5-bfab-278d00d5ba0c |
| Verdict: | Malicious activity |
| Analysis date: | May 17, 2020, 07:24:16 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | AB88C5E7F81C540DC5E35B4D241429A9 |
| SHA1: | E779F0BB1889BDDEB72512921F4DC49763A96475 |
| SHA256: | D072C1FF63DD8880EF474FA0F2F7CFFC72A2DF4808FC0FA3FC99081BEC213174 |
| SSDEEP: | 3:N8RGaXzVHzKhMdEXn:2gWHzKhMGX |
MALICIOUS
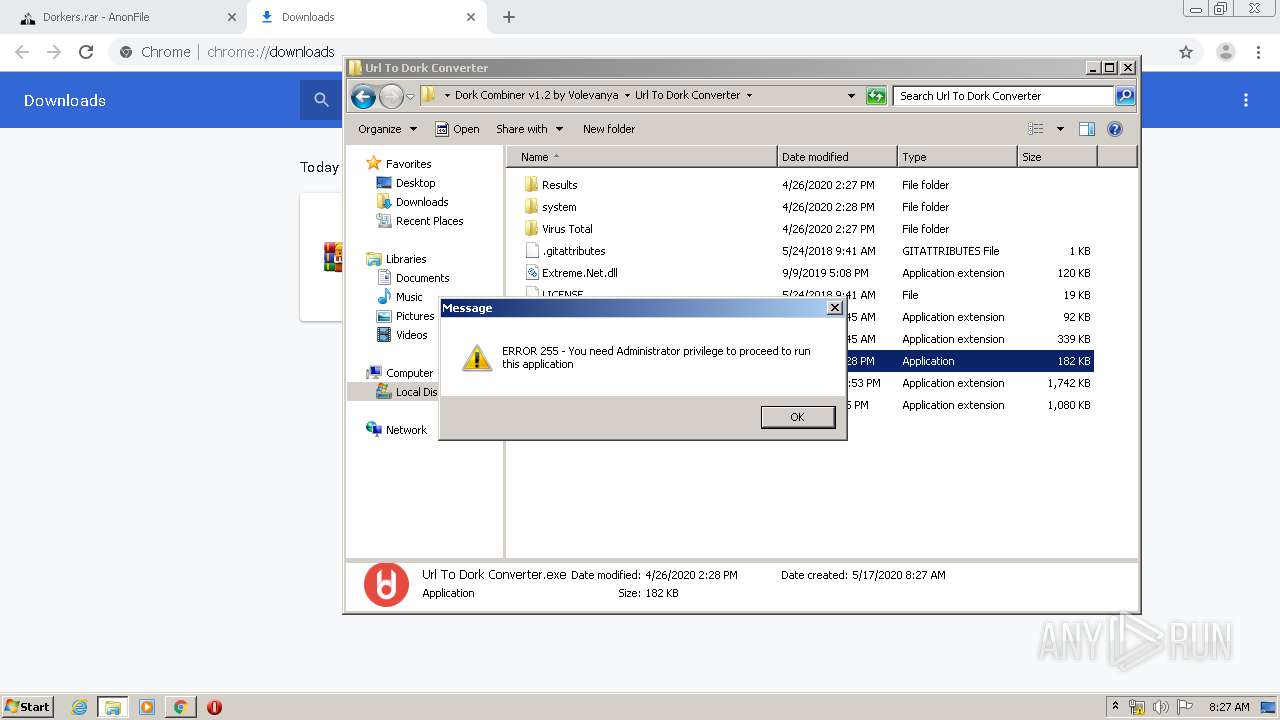
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 2648)
Writes to a start menu file
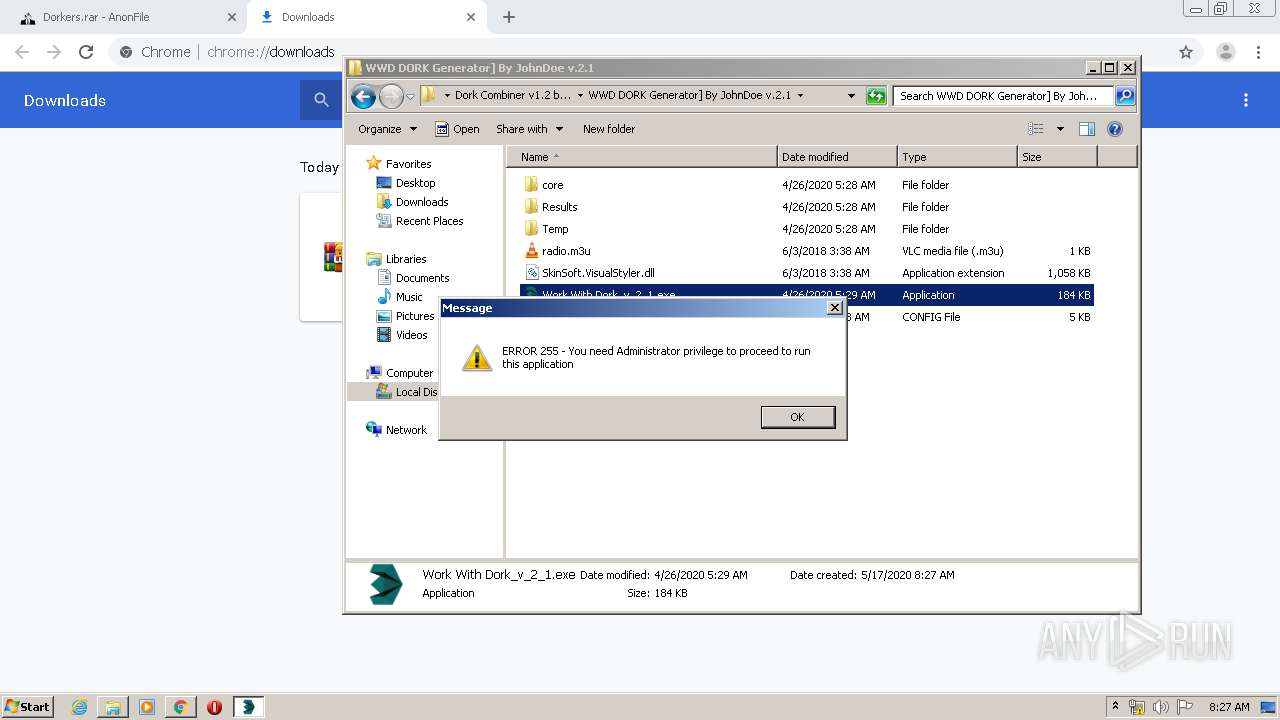
- Work With Dork_v_2_1.exe (PID: 3692)
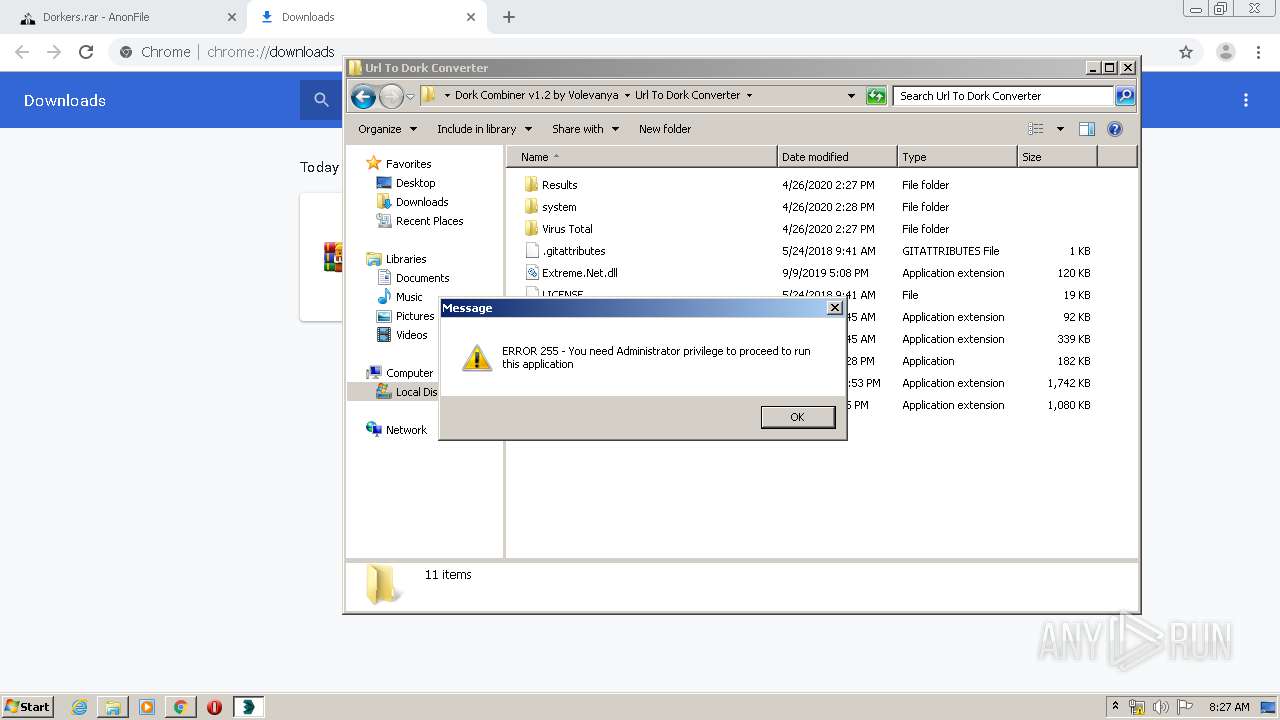
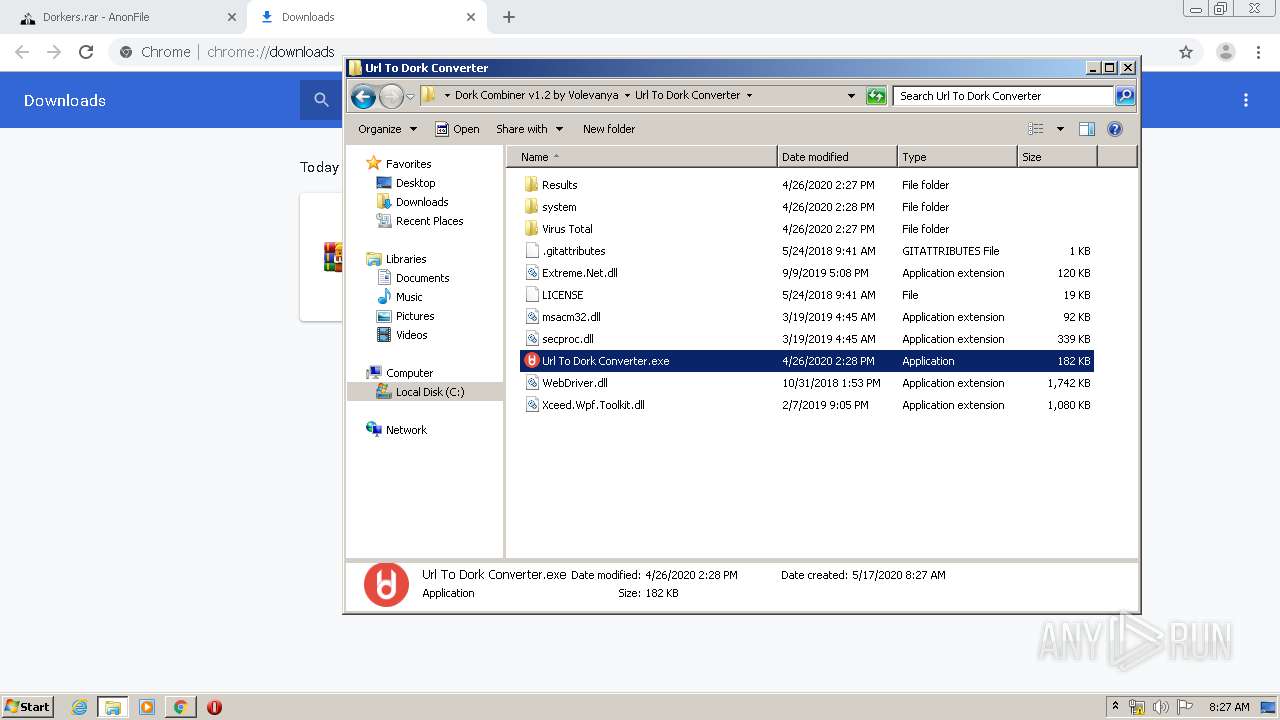
- Url To Dork Converter.exe (PID: 2884)
SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 3036)
Creates files in the user directory
- Work With Dork_v_2_1.exe (PID: 3692)
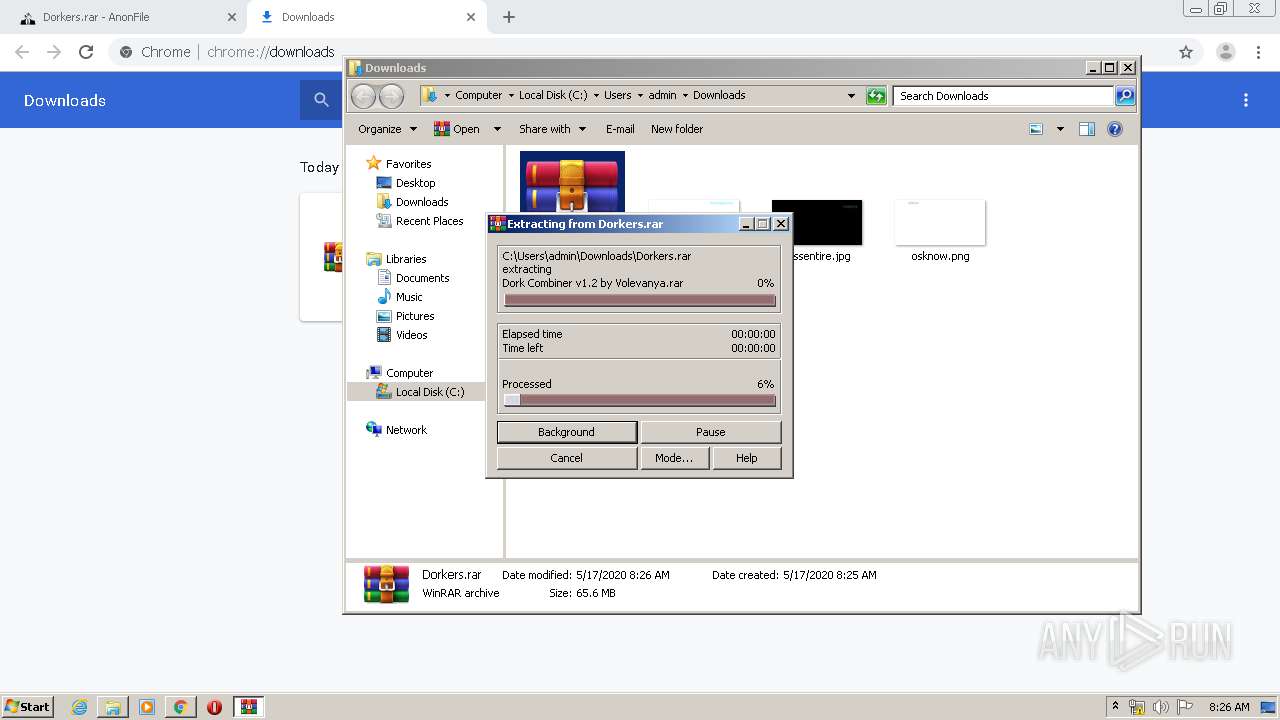
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2964)
Creates files in the program directory
- WinRAR.exe (PID: 2964)
Writes to a desktop.ini file (may be used to cloak folders)
- WinRAR.exe (PID: 2964)
INFO
Application launched itself
- chrome.exe (PID: 3036)
Dropped object may contain TOR URL's
- WinRAR.exe (PID: 2964)
Reads Internet Cache Settings
- chrome.exe (PID: 3036)
Manual execution by user
- Work With Dork_v_2_1.exe (PID: 3692)
- Url To Dork Converter.exe (PID: 2884)
- WinRAR.exe (PID: 1024)
- WinRAR.exe (PID: 2964)
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 2964)
Reads settings of System Certificates
- chrome.exe (PID: 2412)
Reads the hosts file
- chrome.exe (PID: 3036)
- chrome.exe (PID: 2412)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
79
Monitored processes
37
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 608 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1016,4757535733728955934,10651760874508958927,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=1448311328739859100 --renderer-client-id=26 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3420 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 676 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1016,4757535733728955934,10651760874508958927,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=12327140284240182818 --mojo-platform-channel-handle=1384 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 940 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1016,4757535733728955934,10651760874508958927,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=17772178996258719965 --renderer-client-id=7 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3412 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
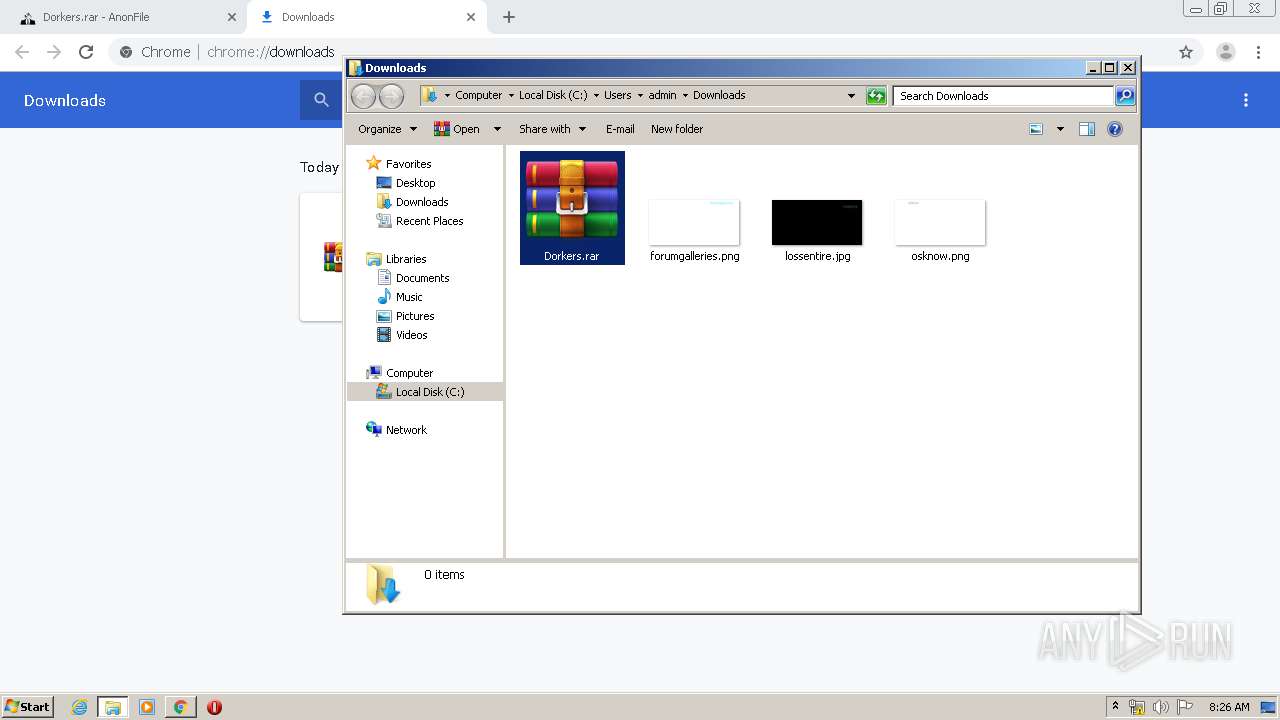
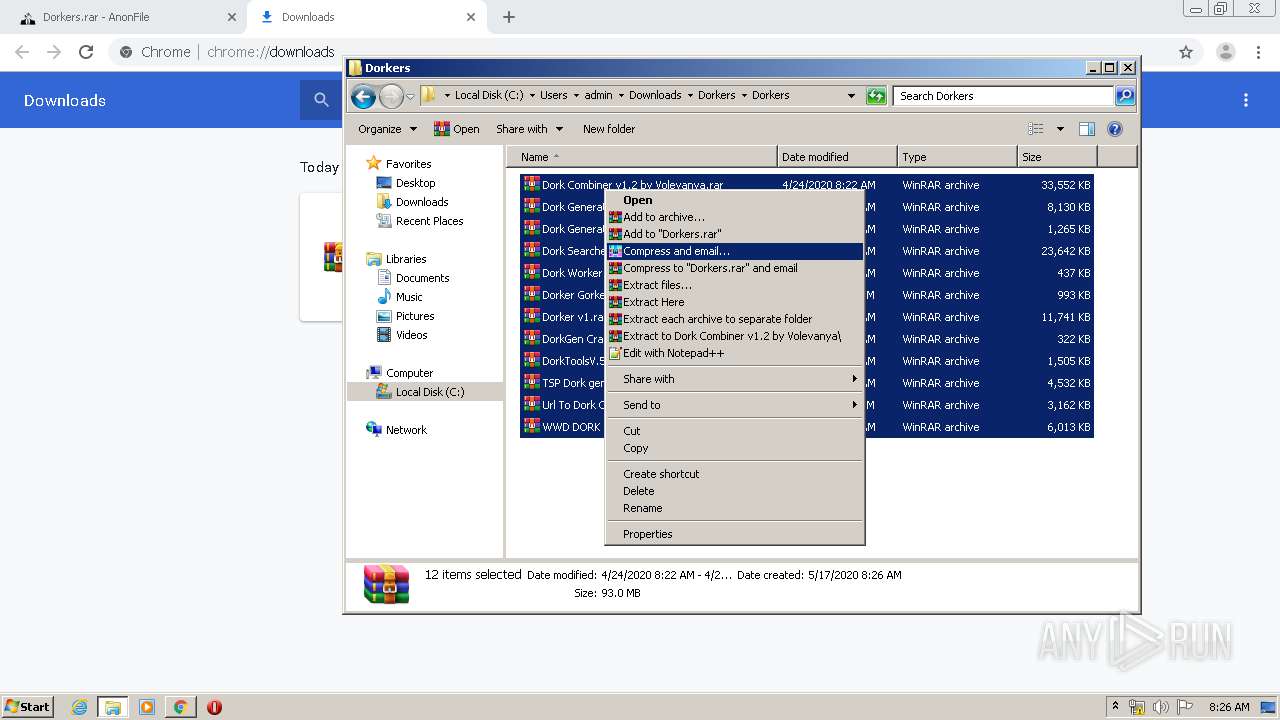
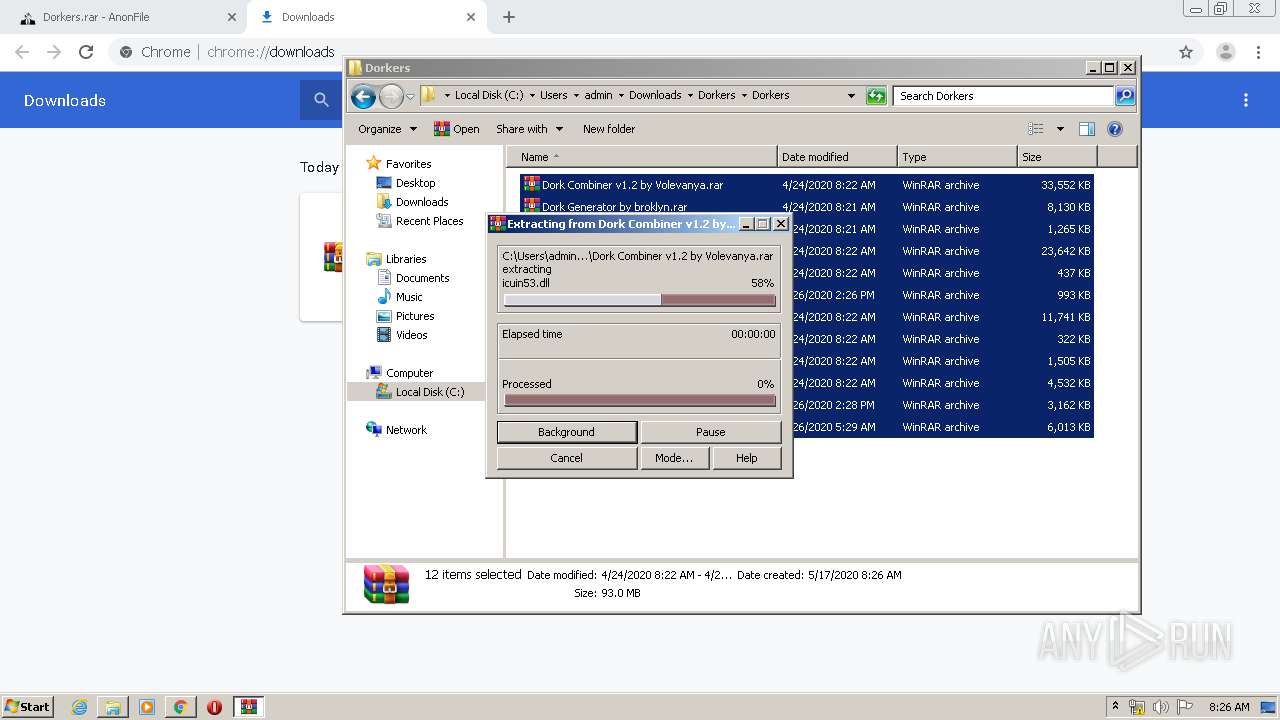
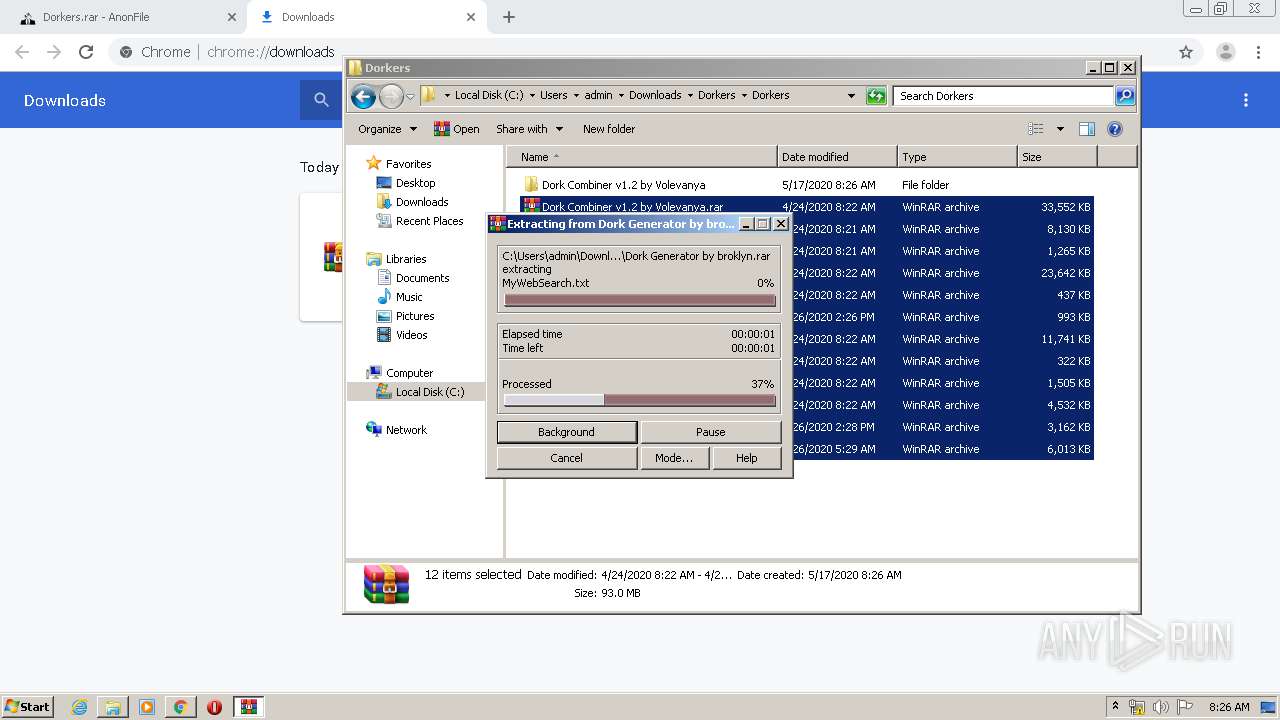
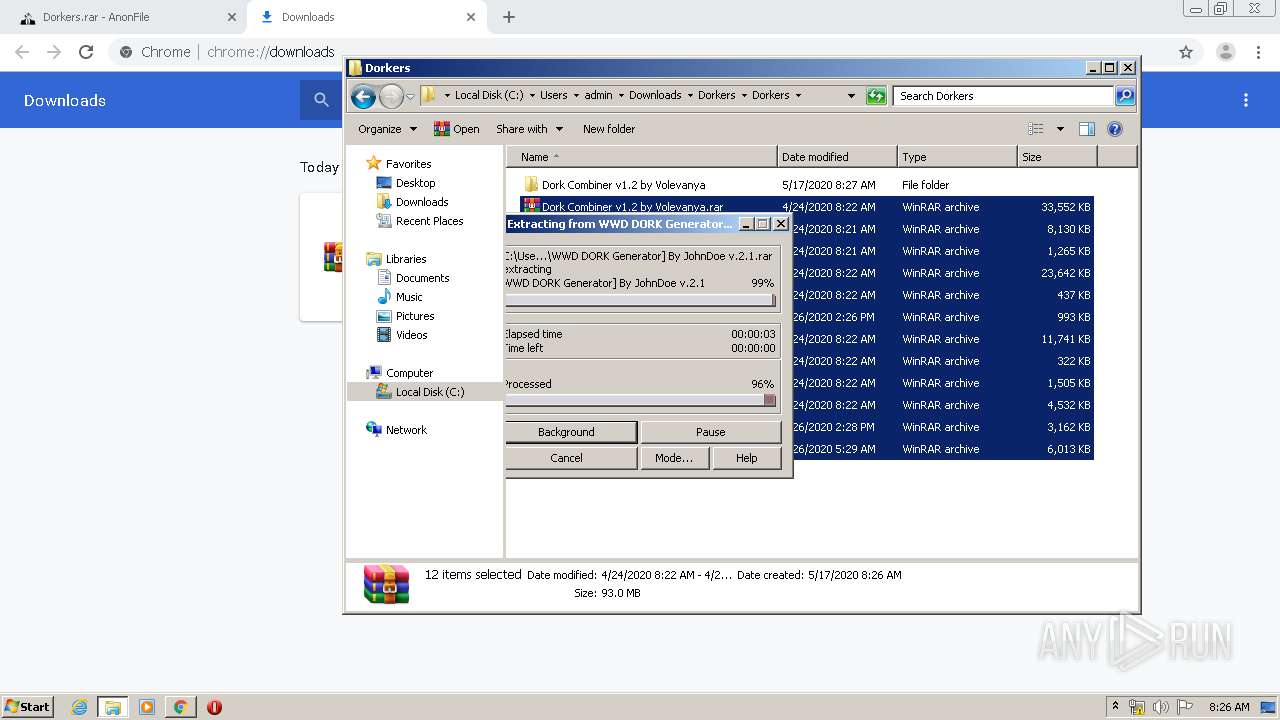
| 1024 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Downloads\Dorkers.rar" C:\Users\admin\Downloads\Dorkers\ | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1228 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1016,4757535733728955934,10651760874508958927,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=6867263303125565201 --mojo-platform-channel-handle=4056 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1256 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1016,4757535733728955934,10651760874508958927,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=6772315687965855040 --mojo-platform-channel-handle=2100 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1296 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1016,4757535733728955934,10651760874508958927,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=10027401452103994367 --mojo-platform-channel-handle=3752 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1356 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1016,4757535733728955934,10651760874508958927,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=10724521442444703604 --mojo-platform-channel-handle=736 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1792 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1016,4757535733728955934,10651760874508958927,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=8297606227713009224 --renderer-client-id=25 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4064 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1832 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1016,4757535733728955934,10651760874508958927,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=899194852456221741 --mojo-platform-channel-handle=4208 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
1 940
Read events
1 831
Write events
104
Delete events
5
Modification events
| (PID) Process: | (3036) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3036) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3036) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3036) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3036) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3376) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 3036-13234173872575875 |
Value: 259 | |||
| (PID) Process: | (3036) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3036) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3036) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3120-13213713943555664 |
Value: 0 | |||
| (PID) Process: | (3036) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
84
Suspicious files
66
Text files
445
Unknown types
17
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3036 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-5EC0E6B1-BDC.pma | — | |
MD5:— | SHA256:— | |||
| 3036 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\f18a4ab3-2e2c-49af-9e26-5f98fa83b558.tmp | — | |
MD5:— | SHA256:— | |||
| 3036 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000028.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3036 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\AvailabilityDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3036 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Session Storage\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3036 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3036 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RFabcc97.TMP | text | |
MD5:— | SHA256:— | |||
| 3036 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3036 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3036 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RFabce3d.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
29
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2412 | chrome.exe | GET | 302 | 216.58.205.238:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOTRmQUFXVHlhaGJaUTdMLWtCSkNJUl9ZQQ/1.0.0.5_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | html | 520 b | whitelisted |
2412 | chrome.exe | GET | 302 | 216.58.205.238:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjY5QUFXTEQwc2RPVXhRY3picjhxblh1dw/7619.603.0.2_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 525 b | whitelisted |
2412 | chrome.exe | GET | 200 | 173.194.183.134:80 | http://r1---sn-aigl6ner.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjY5QUFXTEQwc2RPVXhRY3picjhxblh1dw/7619.603.0.2_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mh=Qx&mip=185.192.69.140&mm=28&mn=sn-aigl6ner&ms=nvh&mt=1589700192&mv=m&mvi=0&pl=25&shardbypass=yes | US | crx | 816 Kb | whitelisted |
2412 | chrome.exe | GET | 200 | 173.194.183.73:80 | http://r4---sn-aigl6ned.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOTRmQUFXVHlhaGJaUTdMLWtCSkNJUl9ZQQ/1.0.0.5_nmmhkkegccagdldgiimedpiccmgmieda.crx?cms_redirect=yes&mh=QJ&mip=185.192.69.140&mm=28&mn=sn-aigl6ned&ms=nvh&mt=1589700192&mv=m&mvi=3&pl=25&shardbypass=yes | US | crx | 293 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2412 | chrome.exe | 172.217.23.173:443 | accounts.google.com | Google Inc. | US | whitelisted |
2412 | chrome.exe | 216.58.208.36:443 | www.google.com | Google Inc. | US | whitelisted |
2412 | chrome.exe | 104.16.107.170:443 | cambrianter.club | Cloudflare Inc | US | unknown |
2412 | chrome.exe | 104.31.85.66:443 | — | Cloudflare Inc | US | suspicious |
2412 | chrome.exe | 104.16.108.139:443 | anglishreasts.site | Cloudflare Inc | US | suspicious |
2412 | chrome.exe | 104.16.108.36:443 | providentsopport.site | Cloudflare Inc | US | unknown |
2412 | chrome.exe | 151.101.2.217:443 | vjs.zencdn.net | Fastly | US | suspicious |
2412 | chrome.exe | 104.16.107.40:443 | withinknuko.club | Cloudflare Inc | US | suspicious |
2412 | chrome.exe | 216.58.205.238:80 | redirector.gvt1.com | Google Inc. | US | whitelisted |
— | — | 172.217.21.238:443 | clients2.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
anonfile.com |
| whitelisted |
accounts.google.com |
| shared |
vjs.zencdn.net |
| whitelisted |
shermore.info |
| whitelisted |
d3ud741uvs727m.cloudfront.net |
| whitelisted |
cambrianter.club |
| shared |
www.google.com |
| malicious |
withinknuko.club |
| suspicious |
anglishreasts.site |
| suspicious |