| File name: | rufus-3.21.exe |
| Full analysis: | https://app.any.run/tasks/85fbb6b4-6fe8-440a-b8ca-e099caabba38 |
| Verdict: | Malicious activity |
| Analysis date: | March 06, 2024, 21:53:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows, UPX compressed |
| MD5: | C2AB67A2561AC7F5ADD3256FE9BF85D4 |
| SHA1: | CC5742D1F128C439740A56734C0E105F11A62FE6 |
| SHA256: | D0554F1FC47407D678A4D8EACE607272013C475033B636BFB1824ED6B1A22E36 |
| SSDEEP: | 24576:3sqLY/SQe/JGy8U6epCdC4B4K8cvKBUlrVI3r+B4lz/i/ywNRhjSFOA:jYARGyLmCq4VciKlr2b+EjmzSN |
MALICIOUS
Drops the executable file immediately after the start
- rufus-3.21.exe (PID: 2848)
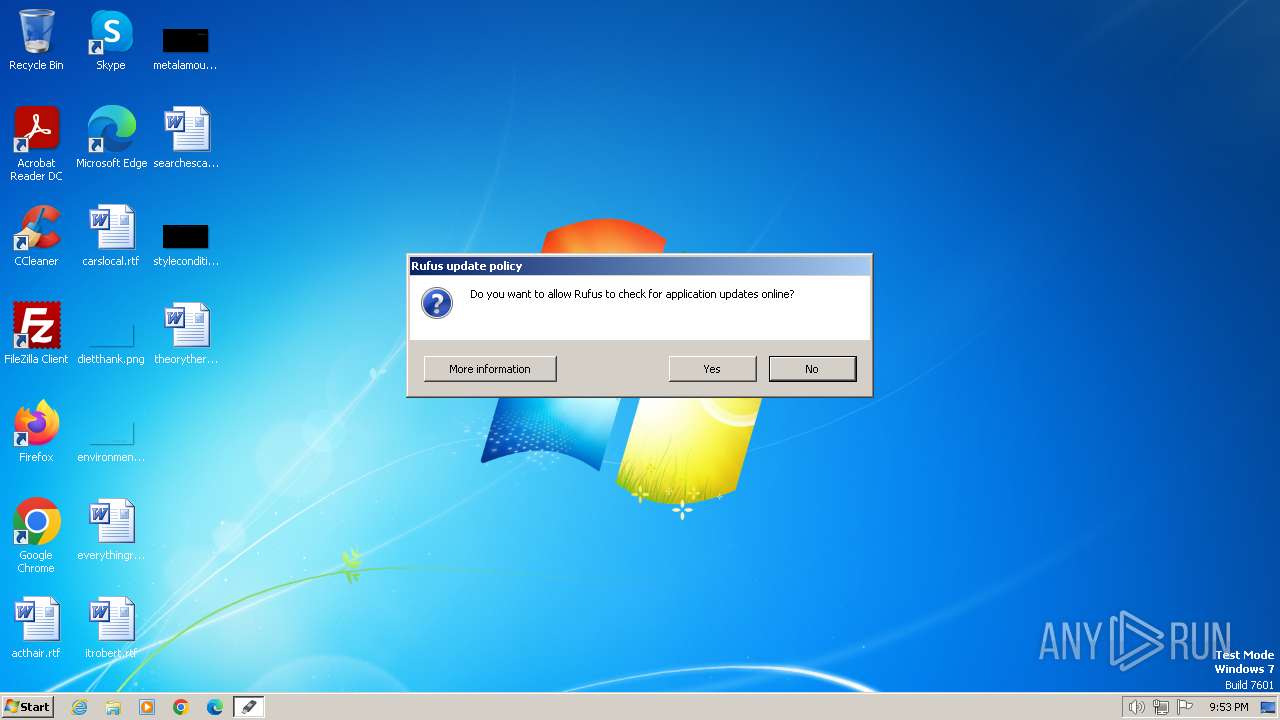
Changes the Windows auto-update feature
- rufus-3.21.exe (PID: 2848)
SUSPICIOUS
Executes as Windows Service
- vds.exe (PID: 2304)
INFO
Checks supported languages
- rufus-3.21.exe (PID: 2848)
Reads the computer name
- rufus-3.21.exe (PID: 2848)
Reads the machine GUID from the registry
- rufus-3.21.exe (PID: 2848)
Process checks whether UAC notifications are on
- rufus-3.21.exe (PID: 2848)
Create files in a temporary directory
- rufus-3.21.exe (PID: 2848)
Creates files or folders in the user directory
- rufus-3.21.exe (PID: 2848)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (64.2) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.6) |
| .exe | | | Win32 Executable (generic) (10.6) |
| .exe | | | Generic Win/DOS Executable (4.7) |
| .exe | | | DOS Executable Generic (4.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:11:28 16:47:53+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, 32-bit, No debug |
| PEType: | PE32 |
| LinkerVersion: | 2.39 |
| CodeSize: | 1347584 |
| InitializedDataSize: | 45056 |
| UninitializedDataSize: | 2691072 |
| EntryPoint: | 0x3d99a0 |
| OSVersion: | 4 |
| ImageVersion: | 1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.21.1949.0 |
| ProductVersionNumber: | 3.21.1949.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | https://rufus.ie |
| CompanyName: | Akeo Consulting |
| FileDescription: | Rufus |
| FileVersion: | 3.21.1949 |
| InternalName: | Rufus |
| LegalCopyright: | © 2011-2022 Pete Batard (GPL v3) |
| LegalTrademarks: | https://www.gnu.org/licenses/gpl-3.0.html |
| OriginalFileName: | rufus-3.21.exe |
| ProductName: | Rufus |
| ProductVersion: | 3.21.1949 |
Total processes
45
Monitored processes
4
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2160 | "C:\Users\admin\AppData\Local\Temp\rufus-3.21.exe" | C:\Users\admin\AppData\Local\Temp\rufus-3.21.exe | — | explorer.exe | |||||||||||
User: admin Company: Akeo Consulting Integrity Level: MEDIUM Description: Rufus Exit code: 3221226540 Version: 3.21.1949 Modules
| |||||||||||||||
| 2304 | C:\Windows\System32\vds.exe | C:\Windows\System32\vds.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Virtual Disk Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2848 | "C:\Users\admin\AppData\Local\Temp\rufus-3.21.exe" | C:\Users\admin\AppData\Local\Temp\rufus-3.21.exe | explorer.exe | ||||||||||||
User: admin Company: Akeo Consulting Integrity Level: HIGH Description: Rufus Exit code: 0 Version: 3.21.1949 Modules
| |||||||||||||||
| 3948 | C:\Windows\System32\vdsldr.exe -Embedding | C:\Windows\System32\vdsldr.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Virtual Disk Service Loader Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
553
Read events
469
Write events
27
Delete events
57
Modification events
| (PID) Process: | (2848) rufus-3.21.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2848) rufus-3.21.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Group Policy Objects\{4BA85850-5441-42B3-BF67-5C282B3E4E29}Machine\Software\Policies\Microsoft\Windows\WindowsUpdate\AU |
| Operation: | write | Name: | IncludeRecommendedUpdates |
Value: 0 | |||
| (PID) Process: | (2848) rufus-3.21.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Group Policy Objects\{4BA85850-5441-42B3-BF67-5C282B3E4E29}Machine\Software\Policies\Microsoft\Windows\WindowsUpdate\AU |
| Operation: | write | Name: | AutoInstallMinorUpdates |
Value: 0 | |||
| (PID) Process: | (2848) rufus-3.21.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Group Policy Objects\{4BA85850-5441-42B3-BF67-5C282B3E4E29}Machine\Software\Policies\Microsoft\Windows Defender |
| Operation: | write | Name: | DisableAntiSpyware |
Value: 1 | |||
| (PID) Process: | (2848) rufus-3.21.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Group Policy Objects\{4BA85850-5441-42B3-BF67-5C282B3E4E29}Machine\Software\Policies\Microsoft\Windows Defender\Real-time Protection |
| Operation: | write | Name: | DisableRealtimeMonitoring |
Value: 1 | |||
| (PID) Process: | (2848) rufus-3.21.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Group Policy Objects\{4BA85850-5441-42B3-BF67-5C282B3E4E29}Machine\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer |
| Operation: | write | Name: | NoDriveTypeAutorun |
Value: 158 | |||
| (PID) Process: | (2848) rufus-3.21.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Group Policy Objects\{4BA85850-5441-42B3-BF67-5C282B3E4E29}User |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2848) rufus-3.21.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Group Policy Objects |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2848) rufus-3.21.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Group Policy Objects\{4BA85850-5441-42B3-BF67-5C282B3E4E29}Machine |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2848) rufus-3.21.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Group Policy Objects\{4BA85850-5441-42B3-BF67-5C282B3E4E29}Machine\Software |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
0
Suspicious files
1
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2848 | rufus-3.21.exe | C:\Users\admin\AppData\Local\Rufus\rufus.log | text | |
MD5:12E91346EED1A36EFA984D616D01779C | SHA256:2E7C71EA55BFA4A7FD851F1776006F8C8C05D240B86C5A50EE7FA64C6F178FEA | |||
| 2848 | rufus-3.21.exe | C:\Windows\System32\GroupPolicy\gpt.ini | text | |
MD5:FED929AE34422010496B5B4A1827A501 | SHA256:2DDA40A266ECA9DDD736701EFA24C6FE186EDD6737DB7BF52BFFE32D614667ED | |||
| 2848 | rufus-3.21.exe | C:\Users\admin\AppData\Local\Temp\RufF5BA.tmp | text | |
MD5:3054AB699BF0FB9B972BAA36EB701B84 | SHA256:591489CB8F30BECB02CB178548B368D9384EFF124BEBCC2DE3E6B7646A3C0638 | |||
| 2848 | rufus-3.21.exe | C:\Windows\System32\GroupPolicy\Machine\Registry.pol | binary | |
MD5:377AC641CF4F9667421E54D62A25BD4C | SHA256:F25A5A5ABA722FC2F09A1086A132AEEBDBCC17ADCBBDBDE1A7AE960DB97DBD37 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
6
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
DNS requests
Threats
Process | Message |
|---|---|
rufus-3.21.exe | *** Rufus init ***
|
rufus-3.21.exe | Binary executable is signed by 'Akeo Consulting'
|
rufus-3.21.exe | Will use settings from registry
|
rufus-3.21.exe | loc file not found in current directory - embedded one will be used
|
rufus-3.21.exe | localization: extracted data to 'C:\Users\admin\AppData\Local\Temp\RufF5BA.tmp'
|
rufus-3.21.exe | localization: found locale 'en-US'
|
rufus-3.21.exe | localization: found locale 'ar-SA'
|
rufus-3.21.exe | embedded.loc(413): the version of this translation is older than the base one and may result in some messages not being properly translated.
If you are the translator, please update your translation with the changes that intervened between v3.5 and v3.14.
See https://github.com/pbatard/rufus/blob/master/res/loc/ChangeLog.txt
|
rufus-3.21.exe | localization: found locale 'bg-BG'
|
rufus-3.21.exe | embedded.loc(767): the version of this translation is older than the base one and may result in some messages not being properly translated.
If you are the translator, please update your translation with the changes that intervened between v3.5 and v3.14.
See https://github.com/pbatard/rufus/blob/master/res/loc/ChangeLog.txt
|