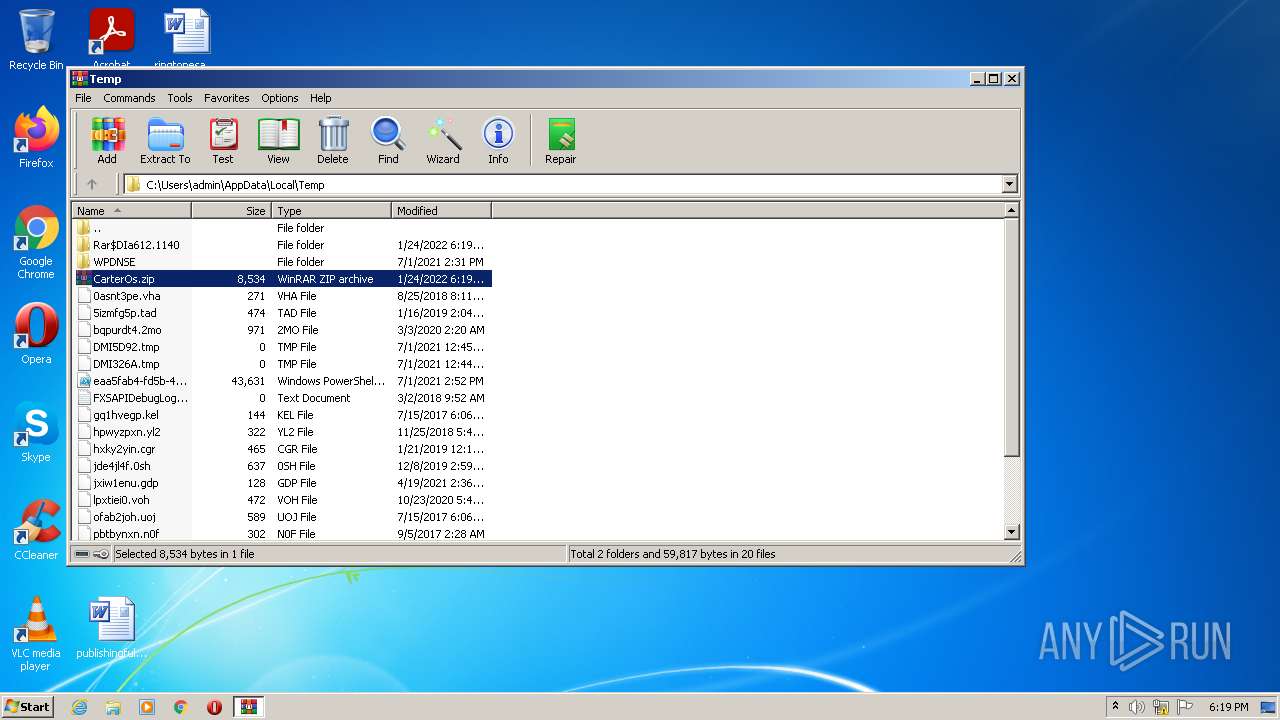
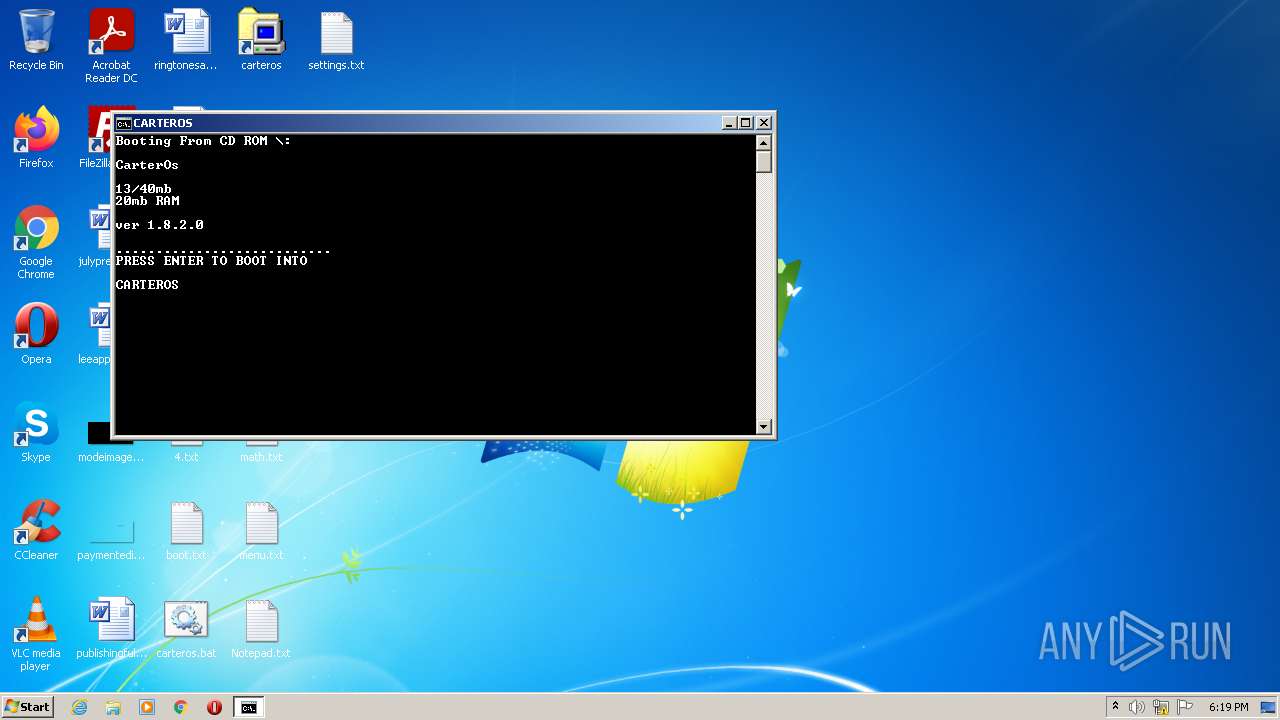
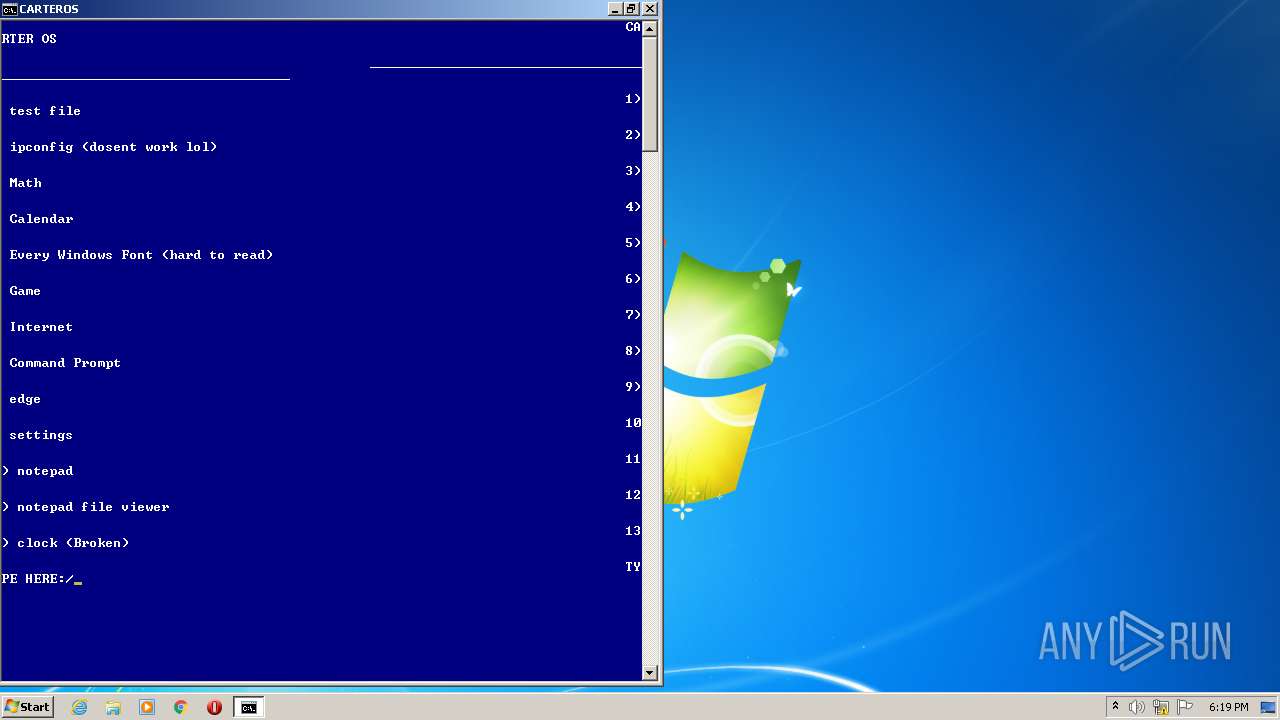
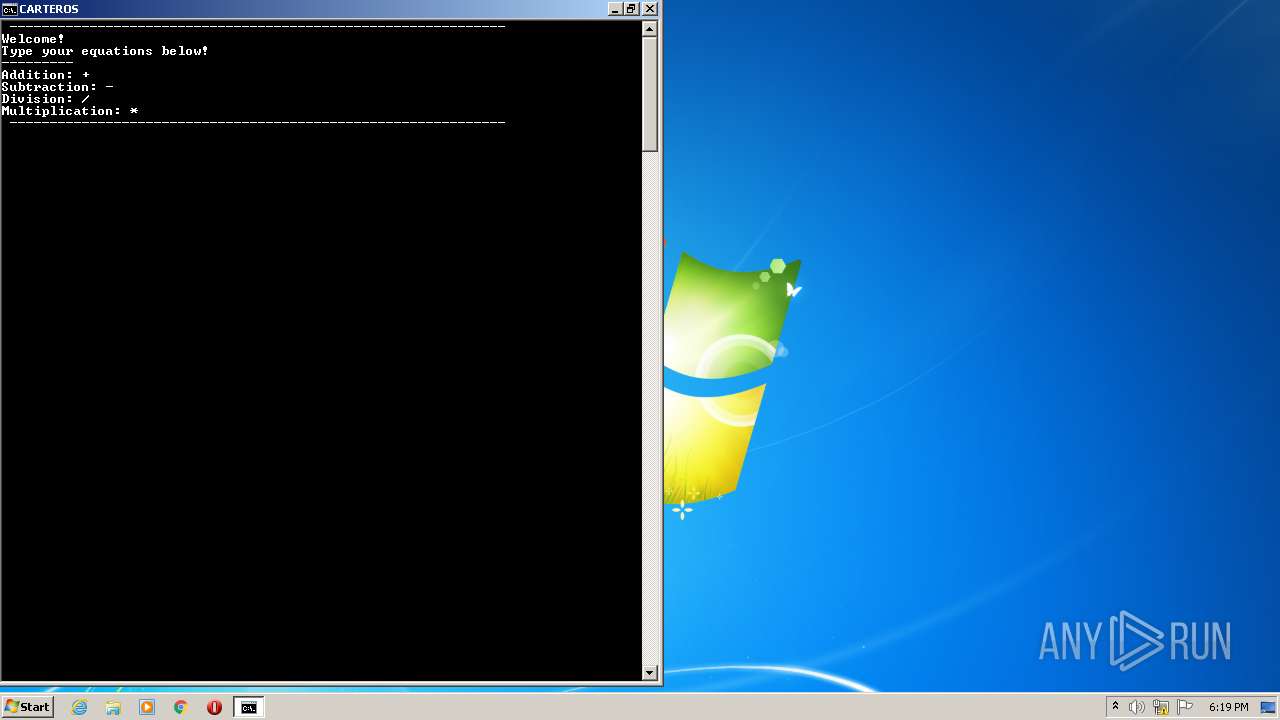
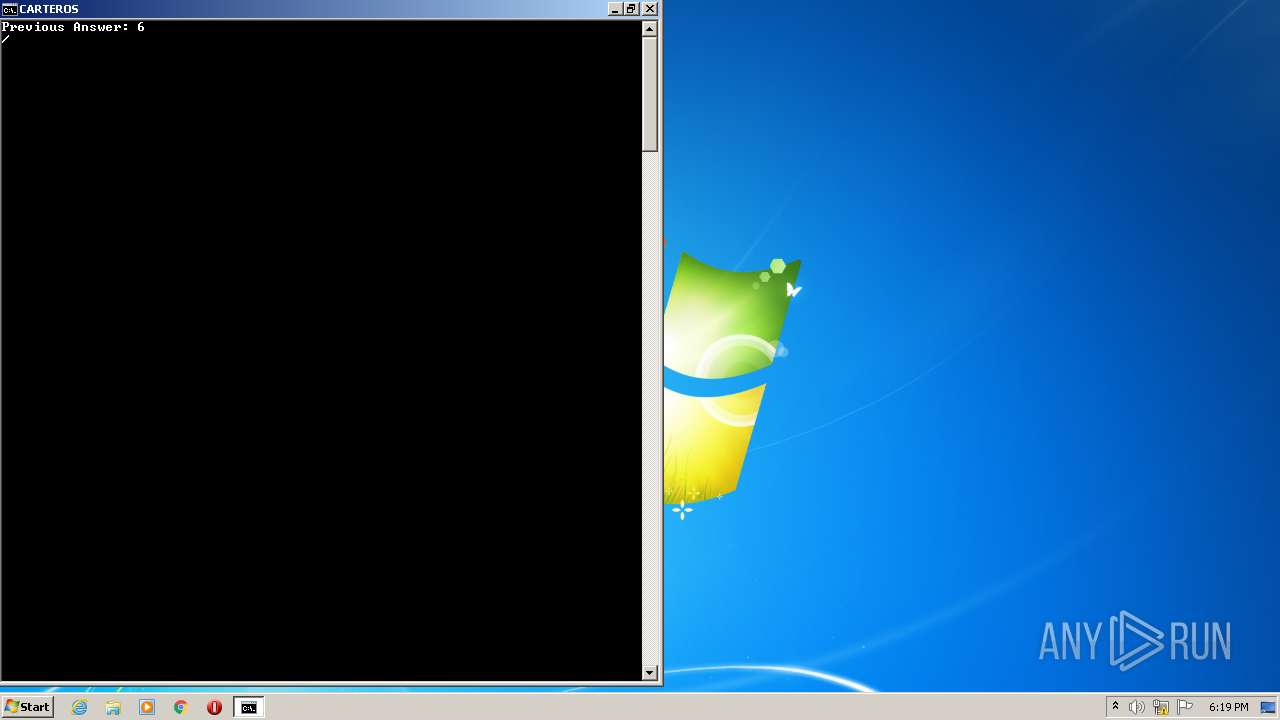
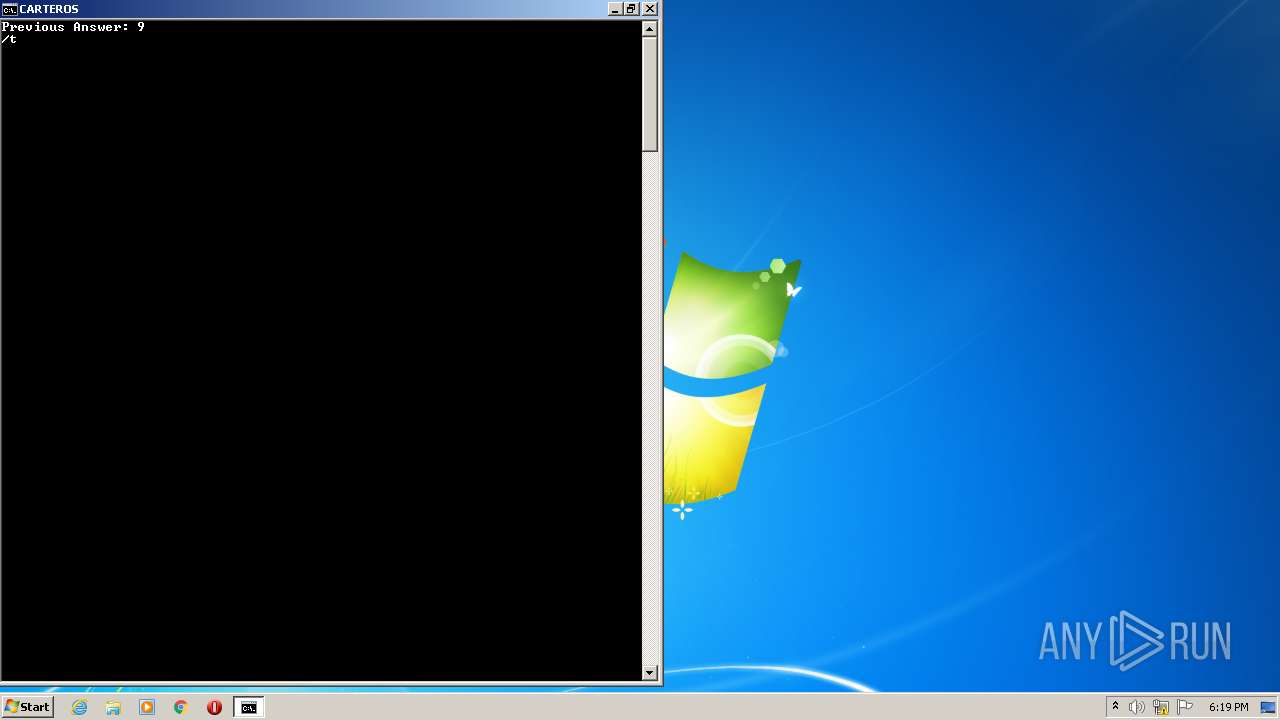
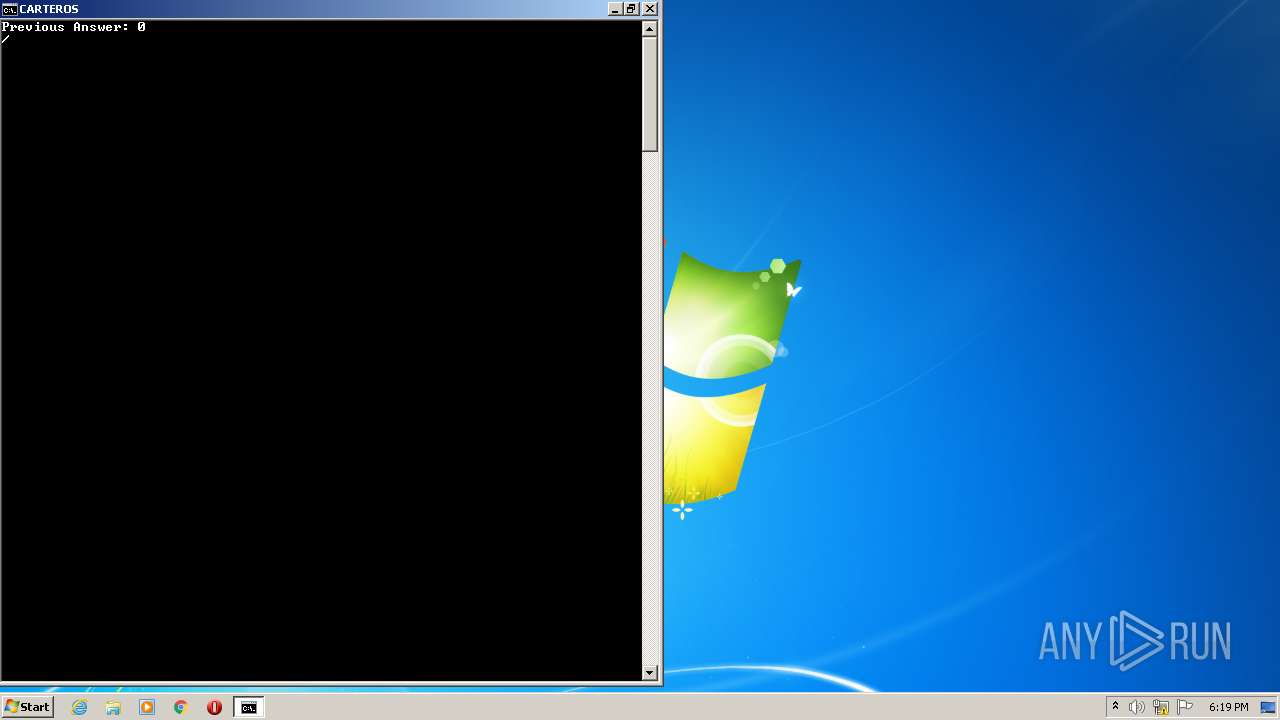
| File name: | CarterOs.zip |
| Full analysis: | https://app.any.run/tasks/032d9681-4776-4d9b-9363-b256ecb3d189 |
| Verdict: | Malicious activity |
| Analysis date: | January 24, 2022, 18:19:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 24EF4394FC1A6F227D82D8EC4536550B |
| SHA1: | F370D79DCF0FADC349D44EEC398321E8C6A5B4AD |
| SHA256: | D0487C7F2A690CD415D38BA75A4DA5253BA54E40CBDE2F117FFAAC1AD7C358AE |
| SSDEEP: | 192:dzJ/3hfnmaof77GHtX+RfSu7EwyglXflV3hrN91l32Rs4CP:bxfn1I2Ht0SusgFlV3lwXCP |
MALICIOUS
No malicious indicators.SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 612)
- cmd.exe (PID: 2440)
- cmd.exe (PID: 2292)
- cmd.exe (PID: 1508)
- cmd.exe (PID: 2244)
- cmd.exe (PID: 1116)
- cmd.exe (PID: 3708)
- cmd.exe (PID: 2800)
- cmd.exe (PID: 3044)
- cmd.exe (PID: 1112)
- cmd.exe (PID: 3208)
- cmd.exe (PID: 2640)
- cmd.exe (PID: 1220)
- cmd.exe (PID: 3428)
- cmd.exe (PID: 2408)
- cmd.exe (PID: 4028)
- cmd.exe (PID: 2940)
- cmd.exe (PID: 3272)
- cmd.exe (PID: 1228)
- cmd.exe (PID: 2580)
- cmd.exe (PID: 2476)
- cmd.exe (PID: 3468)
- cmd.exe (PID: 2104)
- cmd.exe (PID: 3552)
- cmd.exe (PID: 2252)
- cmd.exe (PID: 2328)
- cmd.exe (PID: 2332)
- cmd.exe (PID: 2420)
- cmd.exe (PID: 3300)
- cmd.exe (PID: 2984)
- cmd.exe (PID: 2992)
- cmd.exe (PID: 3992)
- cmd.exe (PID: 3044)
- cmd.exe (PID: 532)
- cmd.exe (PID: 2692)
- cmd.exe (PID: 576)
- cmd.exe (PID: 3608)
- cmd.exe (PID: 3056)
- cmd.exe (PID: 2224)
- cmd.exe (PID: 4028)
- cmd.exe (PID: 684)
- cmd.exe (PID: 3272)
- cmd.exe (PID: 2140)
- cmd.exe (PID: 2688)
- cmd.exe (PID: 3804)
- cmd.exe (PID: 2104)
- cmd.exe (PID: 356)
- cmd.exe (PID: 1096)
- cmd.exe (PID: 3988)
- cmd.exe (PID: 2640)
- cmd.exe (PID: 3552)
- cmd.exe (PID: 3720)
- cmd.exe (PID: 2692)
- cmd.exe (PID: 2708)
- cmd.exe (PID: 3180)
- cmd.exe (PID: 3012)
- cmd.exe (PID: 572)
- cmd.exe (PID: 4052)
- cmd.exe (PID: 2252)
- cmd.exe (PID: 3300)
- cmd.exe (PID: 3952)
- cmd.exe (PID: 4024)
- cmd.exe (PID: 688)
- cmd.exe (PID: 2992)
- cmd.exe (PID: 1164)
- cmd.exe (PID: 2132)
- cmd.exe (PID: 3976)
- cmd.exe (PID: 2744)
- cmd.exe (PID: 1248)
- cmd.exe (PID: 2960)
- cmd.exe (PID: 1296)
- cmd.exe (PID: 2696)
- cmd.exe (PID: 1596)
- cmd.exe (PID: 2504)
- cmd.exe (PID: 2080)
- cmd.exe (PID: 2464)
- cmd.exe (PID: 3412)
- cmd.exe (PID: 576)
- cmd.exe (PID: 2884)
- cmd.exe (PID: 1708)
- cmd.exe (PID: 3472)
- cmd.exe (PID: 2392)
- cmd.exe (PID: 1284)
- cmd.exe (PID: 3740)
- cmd.exe (PID: 2096)
- cmd.exe (PID: 4076)
- cmd.exe (PID: 2932)
- cmd.exe (PID: 3640)
- cmd.exe (PID: 2688)
- cmd.exe (PID: 3804)
- cmd.exe (PID: 1472)
- cmd.exe (PID: 3904)
- cmd.exe (PID: 3300)
- cmd.exe (PID: 2372)
- cmd.exe (PID: 2964)
- cmd.exe (PID: 2128)
- cmd.exe (PID: 552)
- cmd.exe (PID: 3164)
- cmd.exe (PID: 3712)
- cmd.exe (PID: 3736)
- cmd.exe (PID: 3352)
- cmd.exe (PID: 3068)
- cmd.exe (PID: 2500)
- cmd.exe (PID: 3688)
- cmd.exe (PID: 3148)
- cmd.exe (PID: 3976)
- cmd.exe (PID: 3100)
- cmd.exe (PID: 3864)
- cmd.exe (PID: 3180)
- cmd.exe (PID: 2572)
- cmd.exe (PID: 2704)
- cmd.exe (PID: 2244)
- cmd.exe (PID: 2368)
- cmd.exe (PID: 2828)
- cmd.exe (PID: 4072)
- cmd.exe (PID: 3280)
- cmd.exe (PID: 2684)
- cmd.exe (PID: 3436)
- cmd.exe (PID: 2736)
- cmd.exe (PID: 2884)
- cmd.exe (PID: 564)
- cmd.exe (PID: 1000)
- cmd.exe (PID: 1588)
- cmd.exe (PID: 1228)
- cmd.exe (PID: 3156)
- cmd.exe (PID: 3760)
- cmd.exe (PID: 3688)
- cmd.exe (PID: 2960)
- cmd.exe (PID: 1984)
- cmd.exe (PID: 2792)
- cmd.exe (PID: 2688)
- cmd.exe (PID: 1368)
- cmd.exe (PID: 3804)
- cmd.exe (PID: 3460)
- cmd.exe (PID: 3956)
- cmd.exe (PID: 2332)
- cmd.exe (PID: 1024)
- cmd.exe (PID: 636)
- cmd.exe (PID: 2328)
- cmd.exe (PID: 3484)
- cmd.exe (PID: 4064)
- cmd.exe (PID: 4092)
- cmd.exe (PID: 3196)
- cmd.exe (PID: 1556)
- cmd.exe (PID: 2148)
- cmd.exe (PID: 1688)
- cmd.exe (PID: 876)
- cmd.exe (PID: 3164)
- cmd.exe (PID: 356)
- cmd.exe (PID: 1096)
- cmd.exe (PID: 3904)
- cmd.exe (PID: 2948)
- cmd.exe (PID: 1332)
- cmd.exe (PID: 676)
- cmd.exe (PID: 2836)
- cmd.exe (PID: 1228)
- cmd.exe (PID: 3220)
- cmd.exe (PID: 3768)
- cmd.exe (PID: 1408)
- cmd.exe (PID: 2932)
- cmd.exe (PID: 3640)
- cmd.exe (PID: 2828)
- cmd.exe (PID: 4072)
- cmd.exe (PID: 356)
- cmd.exe (PID: 3456)
- cmd.exe (PID: 3052)
- cmd.exe (PID: 1696)
- cmd.exe (PID: 1524)
- cmd.exe (PID: 3272)
- cmd.exe (PID: 3444)
- cmd.exe (PID: 2824)
- cmd.exe (PID: 652)
- cmd.exe (PID: 3832)
- cmd.exe (PID: 2148)
- cmd.exe (PID: 1876)
- cmd.exe (PID: 2424)
- cmd.exe (PID: 3844)
- cmd.exe (PID: 3848)
- cmd.exe (PID: 3716)
- cmd.exe (PID: 1124)
- cmd.exe (PID: 2868)
- cmd.exe (PID: 4080)
- cmd.exe (PID: 3364)
- cmd.exe (PID: 3132)
- cmd.exe (PID: 3420)
- cmd.exe (PID: 3224)
- cmd.exe (PID: 3144)
- cmd.exe (PID: 1408)
- cmd.exe (PID: 356)
- cmd.exe (PID: 1592)
- cmd.exe (PID: 3032)
- cmd.exe (PID: 3644)
- cmd.exe (PID: 3336)
- cmd.exe (PID: 2024)
- cmd.exe (PID: 3272)
- cmd.exe (PID: 1228)
- cmd.exe (PID: 2256)
- cmd.exe (PID: 3068)
- cmd.exe (PID: 3380)
- cmd.exe (PID: 472)
- cmd.exe (PID: 3748)
- cmd.exe (PID: 3532)
- cmd.exe (PID: 2948)
Reads the computer name
- WinRAR.exe (PID: 612)
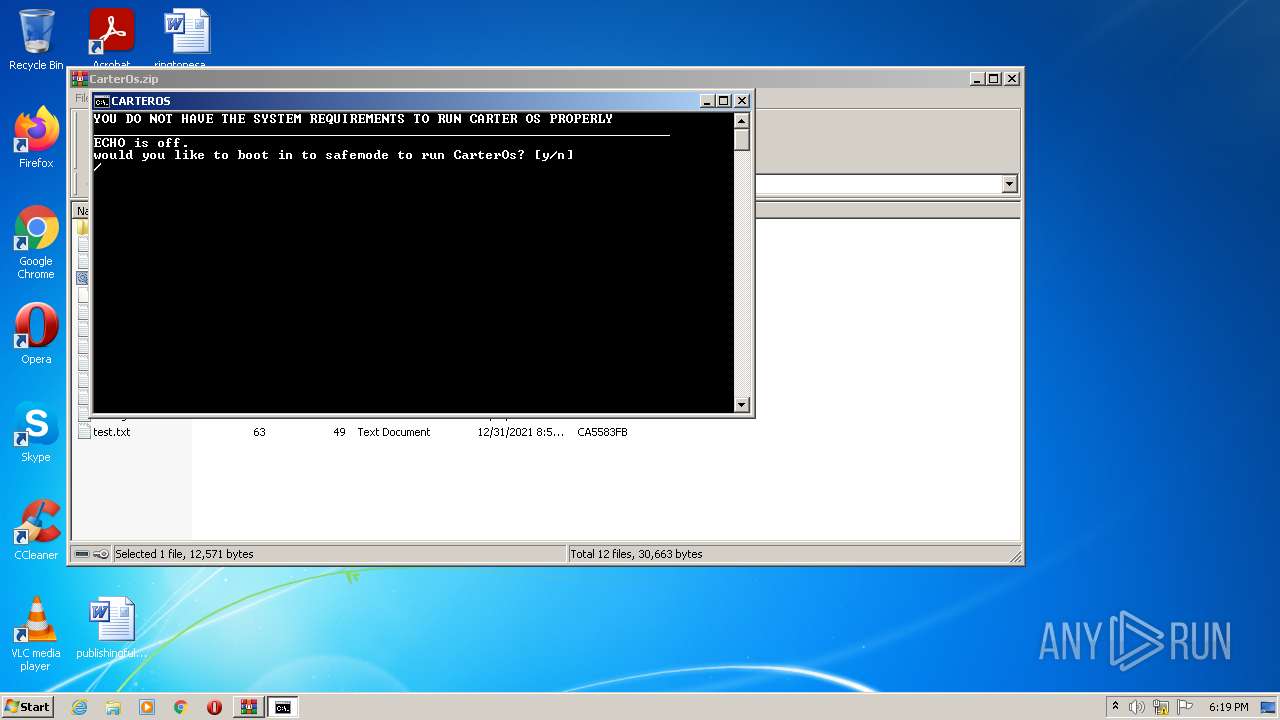
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 612)
- cmd.exe (PID: 2292)
Application launched itself
- cmd.exe (PID: 2292)
INFO
Checks supported languages
- findstr.exe (PID: 3248)
- findstr.exe (PID: 3044)
Manual execution by user
- cmd.exe (PID: 2292)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | 4.txt |
|---|---|
| ZipUncompressedSize: | 2056 |
| ZipCompressedSize: | 619 |
| ZipCRC: | 0x3177d1a5 |
| ZipModifyDate: | 2021:12:31 07:17:29 |
| ZipCompression: | Deflated |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
244
Monitored processes
205
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 356 | C:\Windows\system32\cmd.exe /S /D /c" echo" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 356 | C:\Windows\system32\cmd.exe /S /D /c" set /p="#"" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 356 | C:\Windows\system32\cmd.exe /S /D /c" set /p="#"" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 356 | C:\Windows\system32\cmd.exe /S /D /c" echo" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 472 | C:\Windows\system32\cmd.exe /S /D /c" set /p="#"" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 532 | C:\Windows\system32\cmd.exe /S /D /c" echo" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 552 | C:\Windows\system32\cmd.exe /S /D /c" echo" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 564 | C:\Windows\system32\cmd.exe /S /D /c" echo" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 572 | C:\Windows\system32\cmd.exe /S /D /c" set /p="#"" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 576 | C:\Windows\system32\cmd.exe /S /D /c" set /p="#"" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
4 437
Read events
4 397
Write events
40
Delete events
0
Modification events
| (PID) Process: | (612) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (612) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (612) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (612) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (612) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (612) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\CarterOs.zip | |||
| (PID) Process: | (612) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (612) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (612) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (612) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
0
Suspicious files
0
Text files
12
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
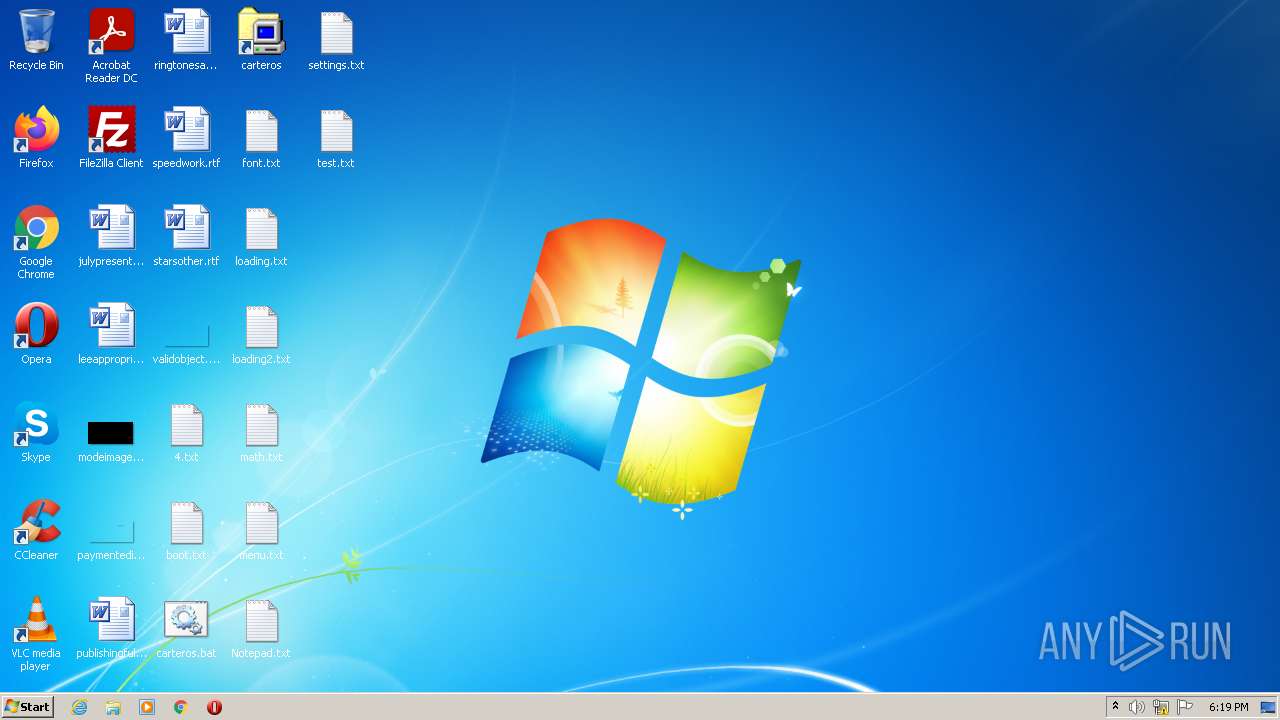
| 612 | WinRAR.exe | C:\Users\admin\Desktop\loading2.txt | text | |
MD5:— | SHA256:— | |||
| 612 | WinRAR.exe | C:\Users\admin\Desktop\loading.txt | text | |
MD5:— | SHA256:— | |||
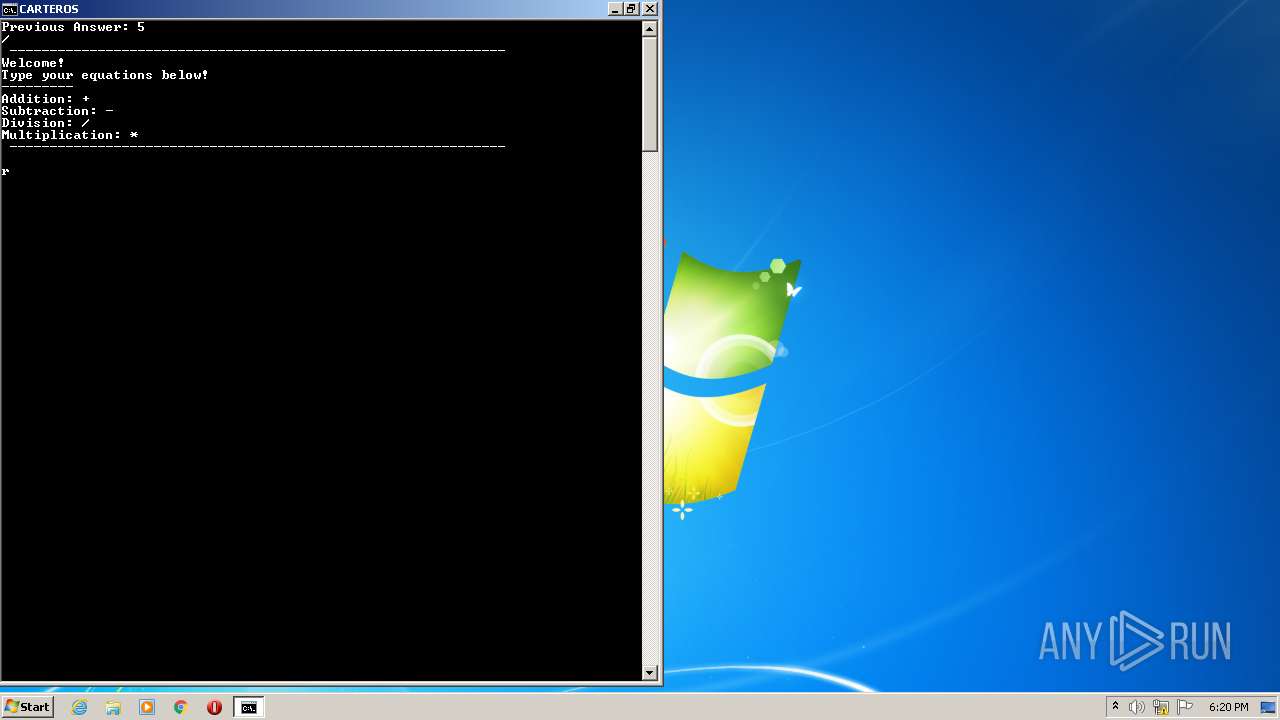
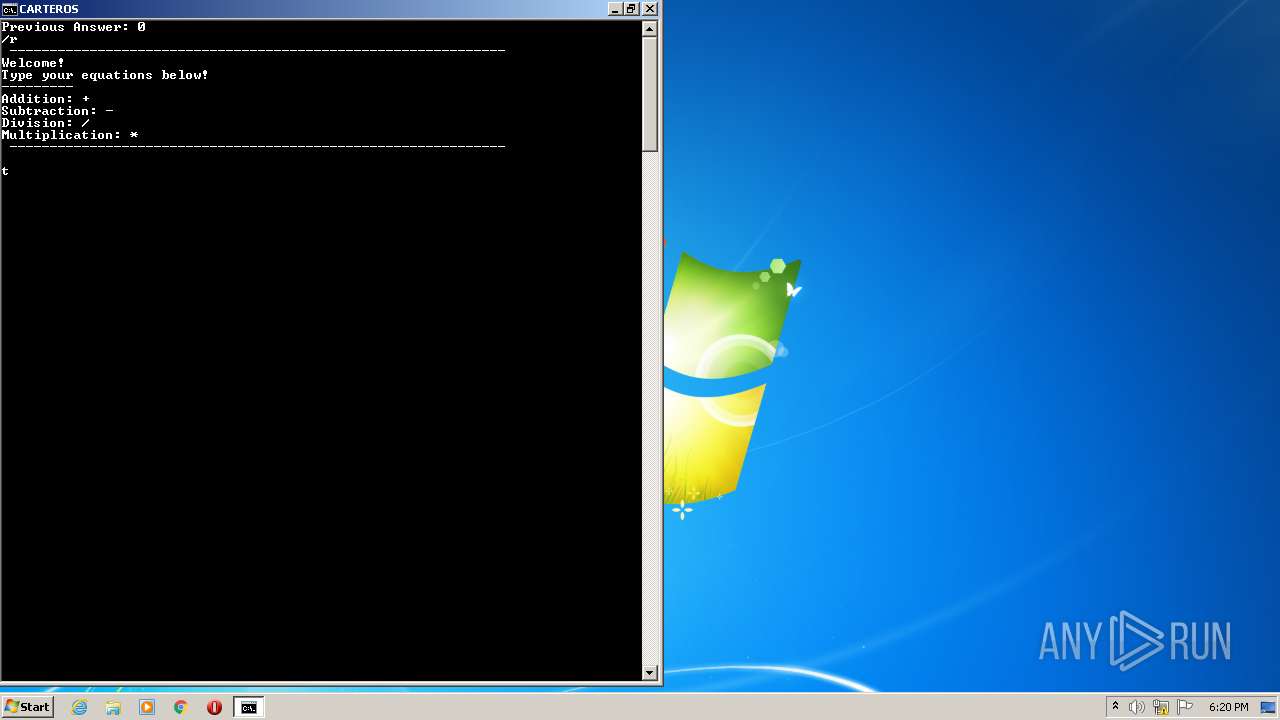
| 612 | WinRAR.exe | C:\Users\admin\Desktop\carteros.lnk | lnk | |
MD5:— | SHA256:— | |||
| 612 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa612.1140\carteros.bat | text | |
MD5:— | SHA256:— | |||
| 612 | WinRAR.exe | C:\Users\admin\Desktop\math.txt | text | |
MD5:— | SHA256:— | |||
| 612 | WinRAR.exe | C:\Users\admin\Desktop\test.txt | text | |
MD5:— | SHA256:— | |||
| 612 | WinRAR.exe | C:\Users\admin\Desktop\4.txt | text | |
MD5:— | SHA256:— | |||
| 612 | WinRAR.exe | C:\Users\admin\Desktop\carteros.bat | text | |
MD5:— | SHA256:— | |||
| 612 | WinRAR.exe | C:\Users\admin\Desktop\boot.txt | text | |
MD5:— | SHA256:— | |||
| 612 | WinRAR.exe | C:\Users\admin\Desktop\font.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.2:53 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.microsoft.com |
| whitelisted |