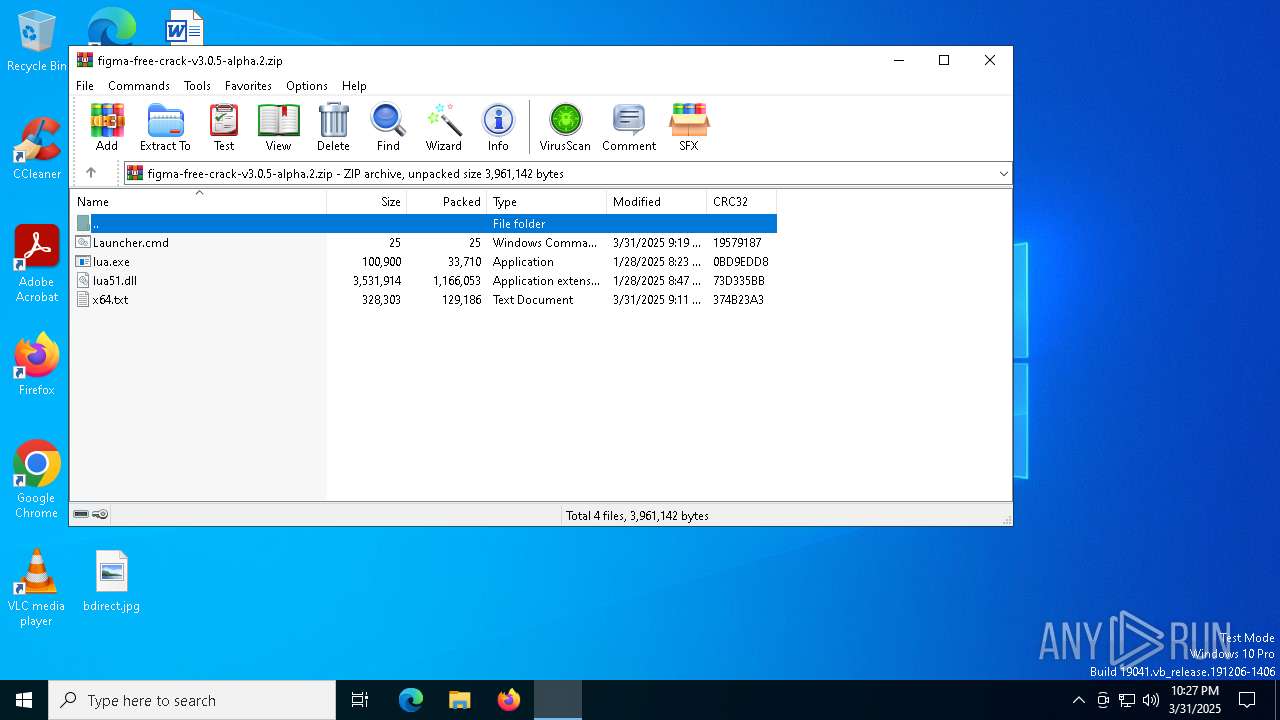
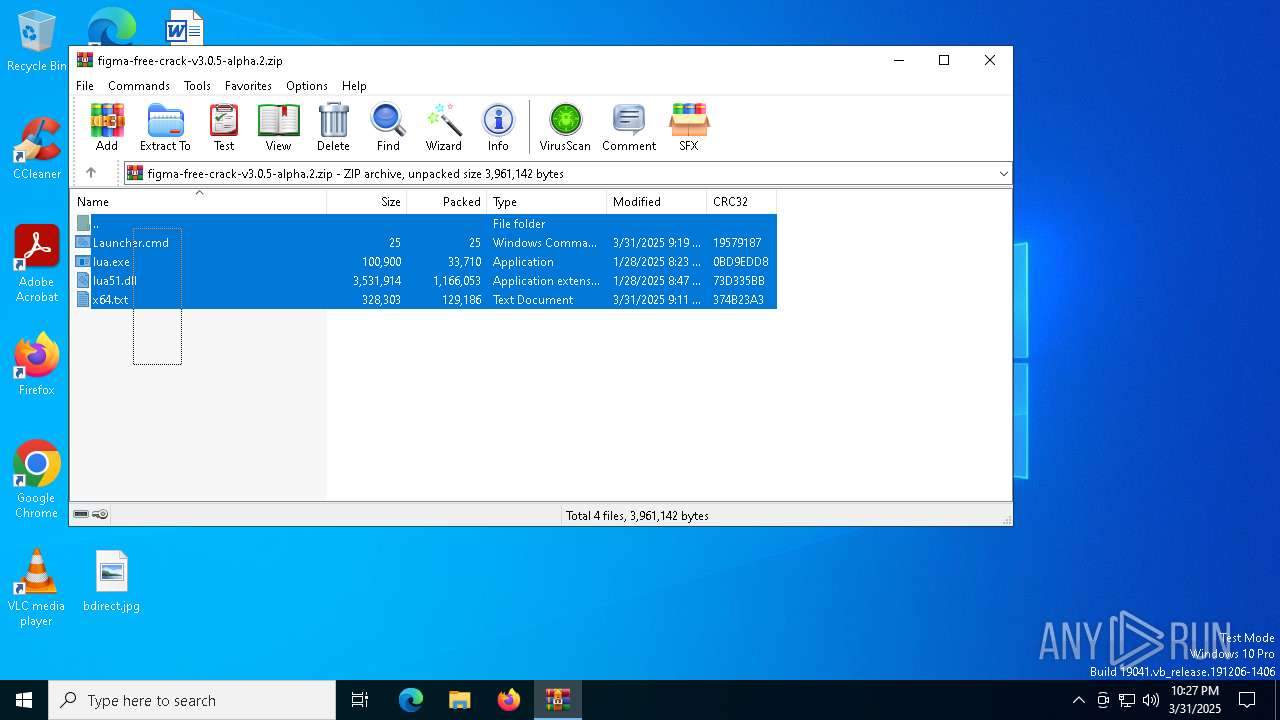
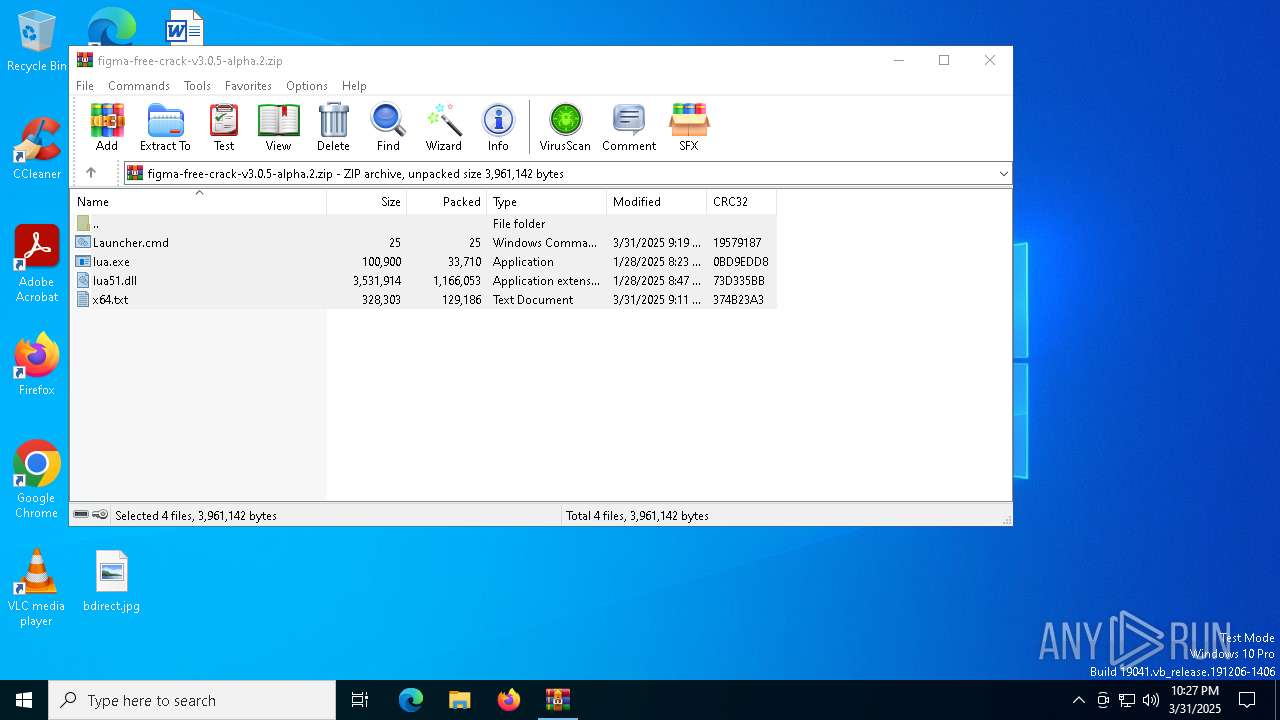
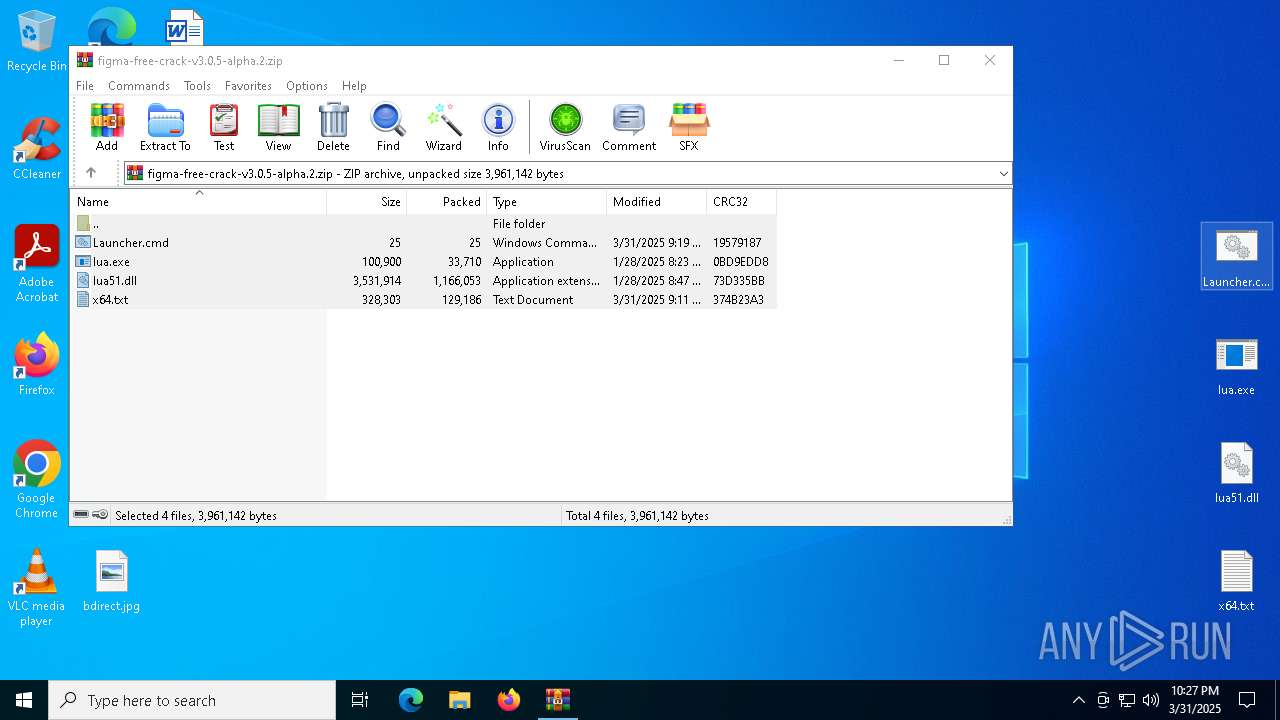
| File name: | figma-free-crack-v3.0.5-alpha.2.zip |
| Full analysis: | https://app.any.run/tasks/d1da900f-7ece-4f0b-b798-36a5d7f27abe |
| Verdict: | Malicious activity |
| Analysis date: | March 31, 2025, 22:27:08 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 7294082DB2E8BE3E8E97A5D0F9B0A656 |
| SHA1: | B26A5ADC36EB5921D2B7DF0F755AEB59E5EFF56E |
| SHA256: | D028D532DE065335D870F5ABED0333629C33C592668F11A8A1A26CCD7E5C4148 |
| SSDEEP: | 49152:oA52VHYlg+p0YepFOB+3KR5X+GafFArkvuNeNCe6Vgp7lwJrAwjvkgUJ9Lw0xfaE:o42VHWg+pdoABrOvArENCe6kwJswA/3V |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6032)
SUSPICIOUS
Checks for external IP
- svchost.exe (PID: 2196)
- lua.exe (PID: 6736)
Reads security settings of Internet Explorer
- lua.exe (PID: 6736)
Connects to the server without a host name
- lua.exe (PID: 6736)
INFO
Checks supported languages
- lua.exe (PID: 6736)
Checks proxy server information
- lua.exe (PID: 6736)
Reads the software policy settings
- lua.exe (PID: 6736)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6032)
Manual execution by a user
- cmd.exe (PID: 1276)
Reads the computer name
- lua.exe (PID: 6736)
Reads the machine GUID from the registry
- lua.exe (PID: 6736)
Creates files or folders in the user directory
- lua.exe (PID: 6736)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:03:31 02:19:42 |
| ZipCRC: | 0x19579187 |
| ZipCompressedSize: | 25 |
| ZipUncompressedSize: | 25 |
| ZipFileName: | Launcher.cmd |
Total processes
133
Monitored processes
8
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1276 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\Launcher.cmd" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3884 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3896 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4692 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5072 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | lua.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6032 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\figma-free-crack-v3.0.5-alpha.2.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6736 | lua.exe x64.txt | C:\Users\admin\Desktop\lua.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
2 722
Read events
2 711
Write events
11
Delete events
0
Modification events
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\figma-free-crack-v3.0.5-alpha.2.zip | |||
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6736) lua.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6736) lua.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
Executable files
2
Suspicious files
9
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6032 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6032.35194\x64.txt | text | |
MD5:79E2DC17AD1C47883AD536688ADEFE93 | SHA256:2393226B03F4E1282D4A8E98BC272C1CB33B68D94E5B9175A3ED40691D10105B | |||
| 6736 | lua.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:EF04987F9EF0C0F32227D7815BD79F0E | SHA256:965E79D24427D54F8454D2307D0BE1872963476759E3963F617888EDFA89328D | |||
| 6736 | lua.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_0FB9553B978E7F00C6B2309507DEB64A | binary | |
MD5:44E1B88324A9858988B03D9F9DDD4C4B | SHA256:4D3613A3CDCF82BC47D2B59CD85DAF4BB4DF5C3371B0D815614D3E60138DBD81 | |||
| 6736 | lua.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_0FB9553B978E7F00C6B2309507DEB64A | binary | |
MD5:CBF00F37CD06719383C19AAFEA8D5774 | SHA256:88BB0C0588AF5B01B7F18A90A856E79AE2D17EB07AC5C29C1B91F11D4F7F3CD0 | |||
| 6032 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6032.35194\Launcher.cmd | text | |
MD5:9497DB1D4B16BC7DFEFD83EEDD064081 | SHA256:4EEAD87255101E4E8DF1407020D4F06477A842CA67965287B3BF62E33DC17EC2 | |||
| 6032 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6032.35194\lua51.dll | executable | |
MD5:4EBD617A3AD9A9619172BD14A902A400 | SHA256:C7A657AF5455812FB215A8888B7E3FD8FA1BA27672A3ED9021EB6004EFF271AC | |||
| 6032 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6032.35194\lua.exe | executable | |
MD5:00F60EE3FF2DEE681B5D7D442009B2C2 | SHA256:5343326FB0B4F79C32276F08FFCC36BD88CDE23AA19962BD1E8D8B80F5D33953 | |||
| 6736 | lua.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\156E5E5C9602A29AA6BBF45E82B7BA19_DA6A6500179D0936895AC8C0E13B3101 | binary | |
MD5:58E2202C0A561244EC03F123DCB40459 | SHA256:33A0D7822CE50A5BB88624EA85E9041D8DC7DCB8DFB489FA7BAFCBD81CD69FC6 | |||
| 6736 | lua.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\05DDC6AA91765AACACDB0A5F96DF8199 | binary | |
MD5:0500885D4896F9F99B5C972DDF6B93CA | SHA256:221F9E9E6CA4CEAA531D288E56B4A07ACAE993A9416924F92610EFD6549ADD34 | |||
| 6736 | lua.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\156E5E5C9602A29AA6BBF45E82B7BA19_DA6A6500179D0936895AC8C0E13B3101 | binary | |
MD5:74540857318F982DD0FA4FD38E100B1A | SHA256:DB2214301FE130456ACC149BB072AA09D1CCBB089D514AE205E934FE316007F3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
25
DNS requests
18
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6736 | lua.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/ | unknown | — | — | whitelisted |
6736 | lua.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6736 | lua.exe | GET | 200 | 172.217.16.131:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | whitelisted |
6736 | lua.exe | GET | 200 | 172.217.16.131:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | whitelisted |
6736 | lua.exe | GET | 200 | 216.58.212.131:80 | http://o.pki.goog/s/wr1/8sg/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBQwHTUyHgfAxFi3r4z8dPC7p%2BvIYAQUZmlJ1N4qnJEDz4kOJLgOMANuiC4CEQDyyPT0ORb9KRHPGROU8Hqa | unknown | — | — | whitelisted |
6736 | lua.exe | POST | 200 | 185.184.123.138:80 | http://185.184.123.138/api/YTAsODYsODIsOWQsYTEsODgsOTAsOTUsNjUsN2Qs | unknown | — | — | unknown |
4724 | SIHClient.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4724 | SIHClient.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3216 | svchost.exe | 20.7.2.167:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6544 | svchost.exe | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
6736 | lua.exe | 208.95.112.1:80 | ip-api.com | TUT-AS | US | whitelisted |
6736 | lua.exe | 23.219.150.101:443 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
6736 | lua.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ip-api.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
polygon-rpc.com |
| unknown |
ocsp.pki.goog |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
6736 | lua.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |