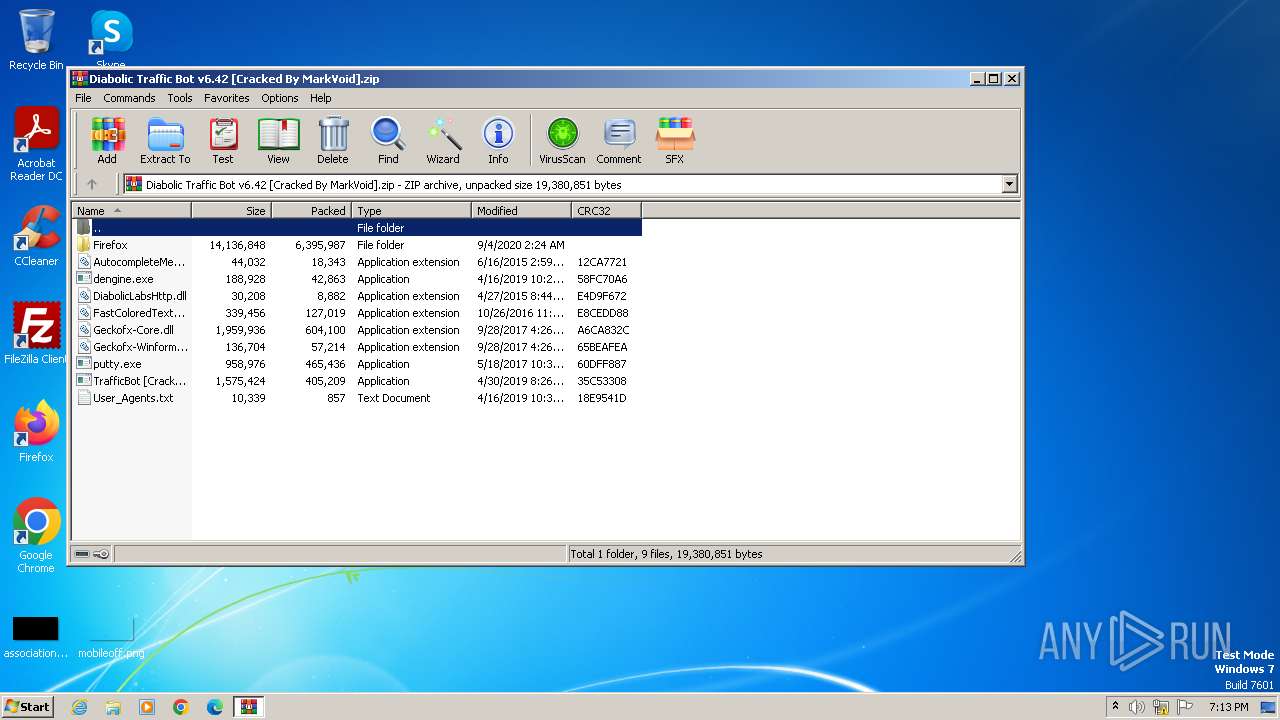
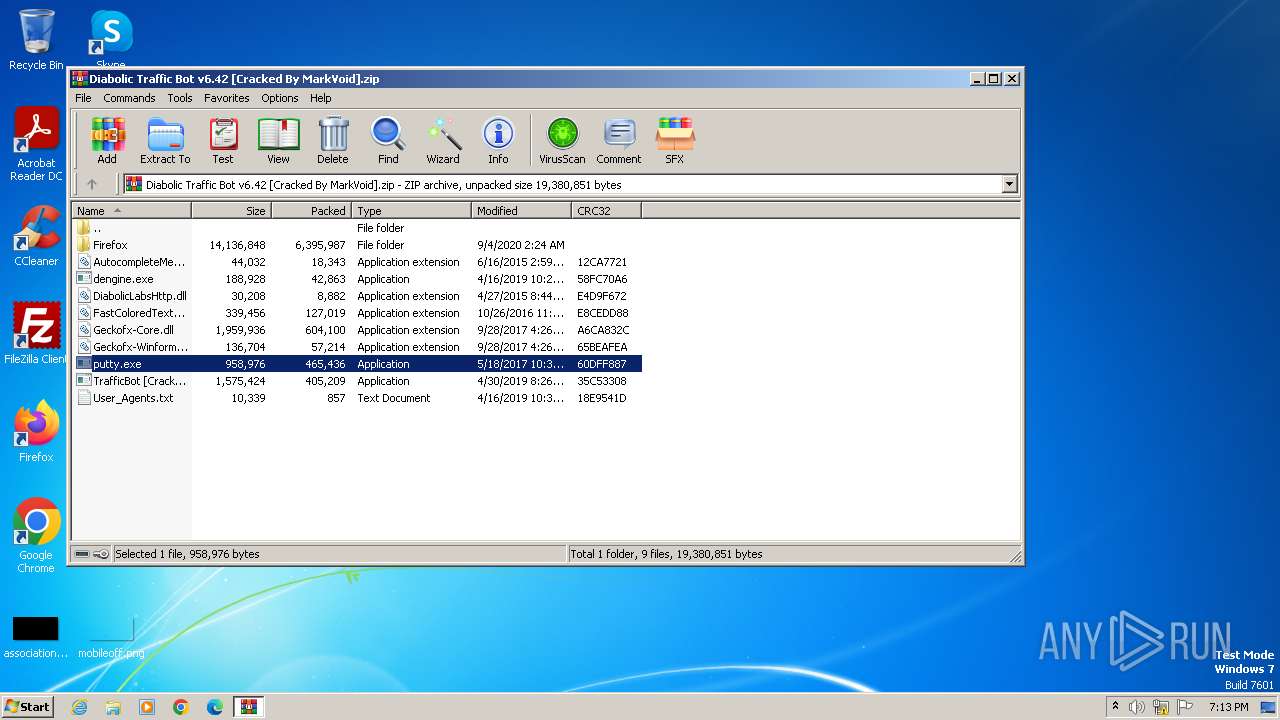
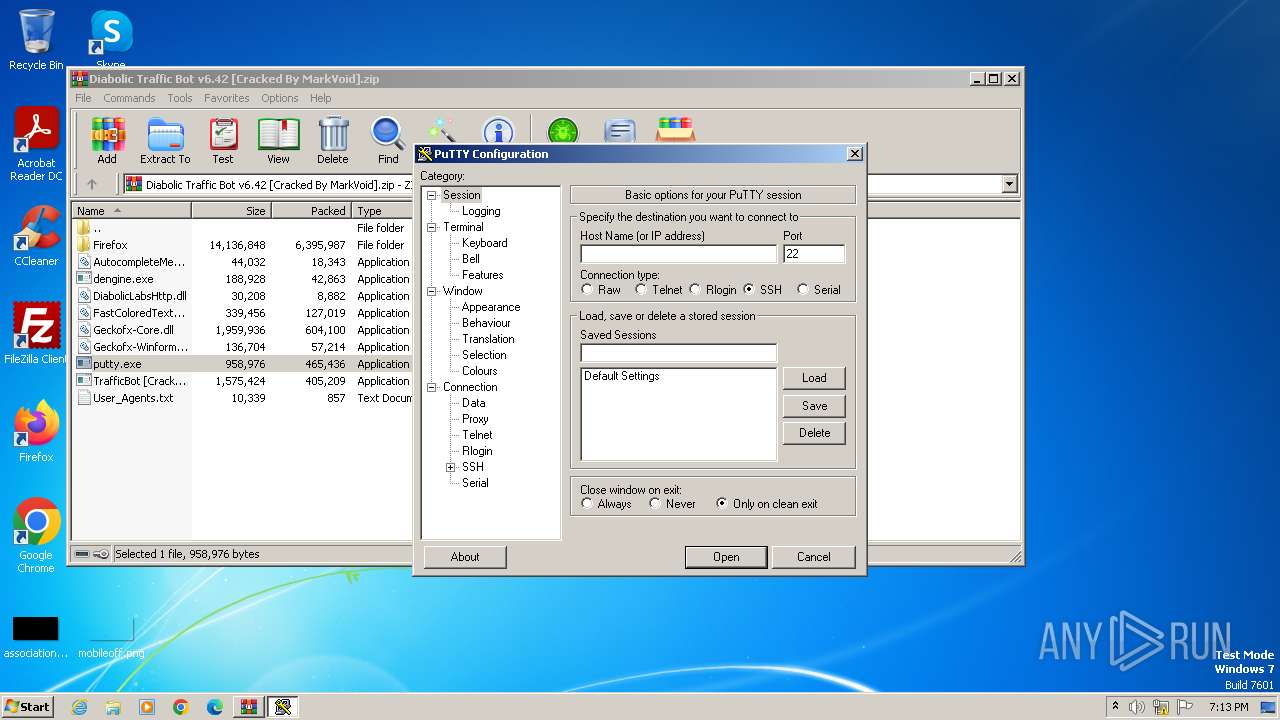
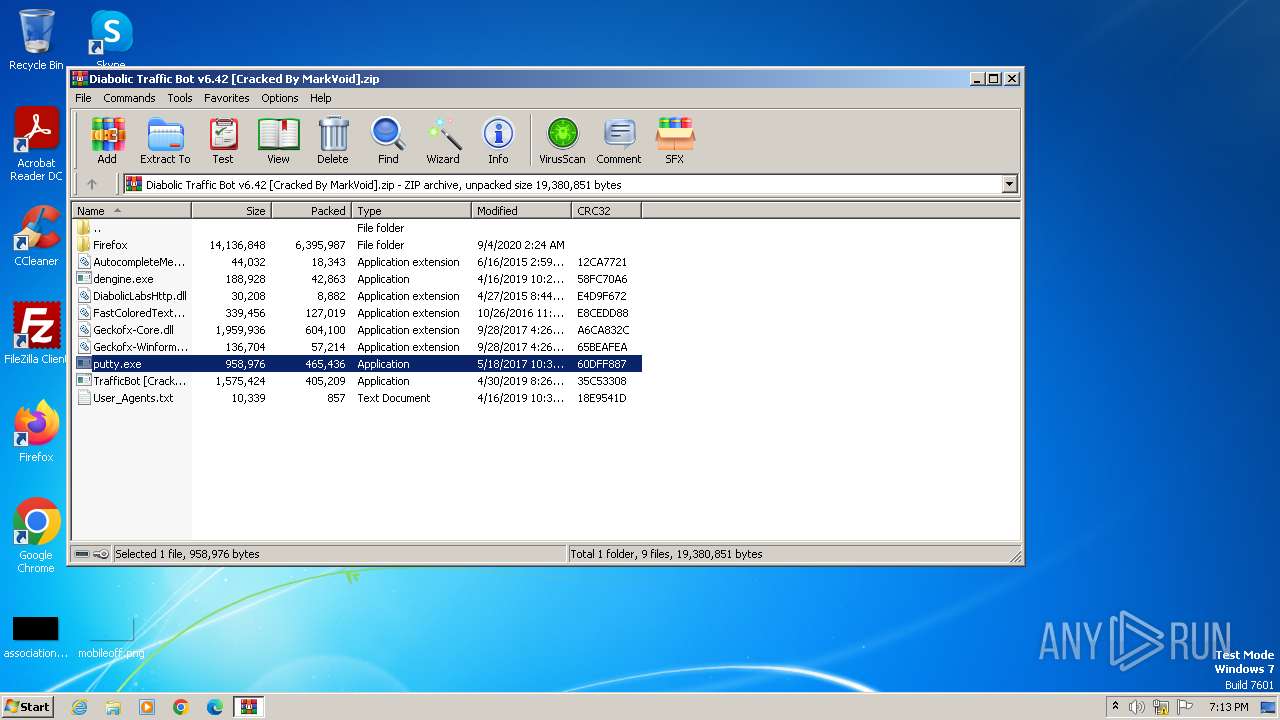
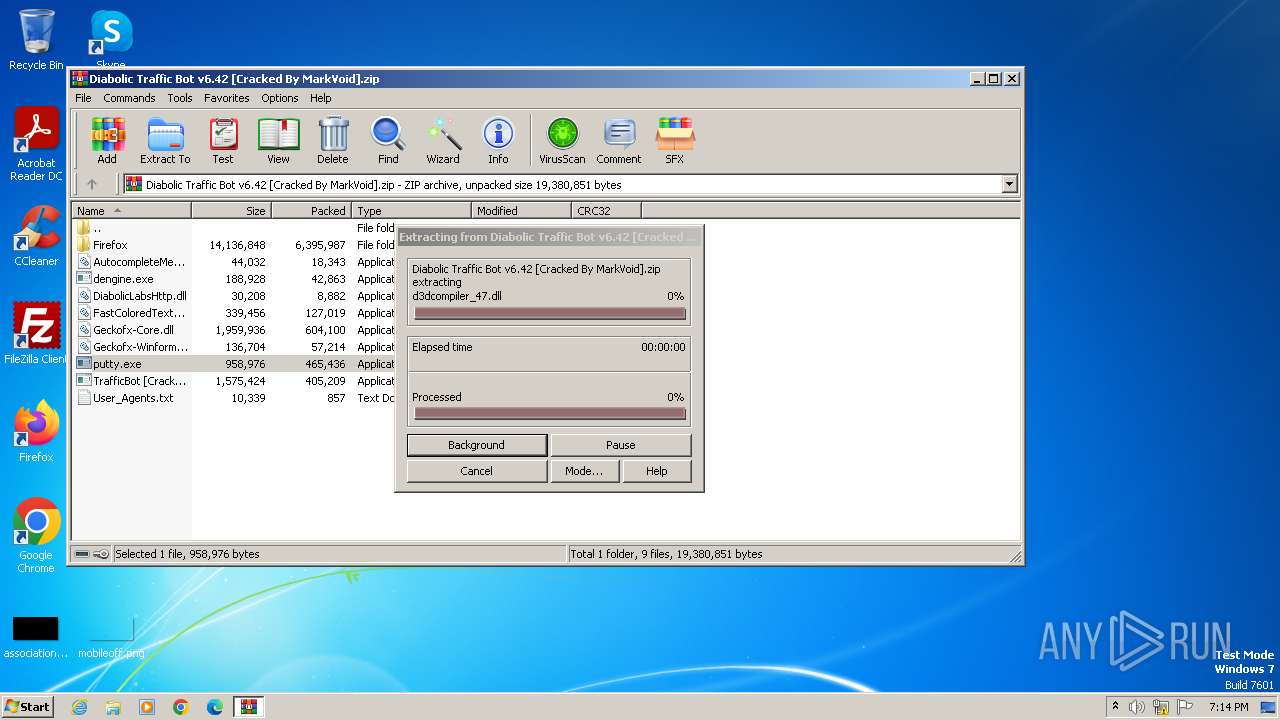
| File name: | Diabolic Traffic Bot v6.42 [Cracked By MarkVoid].zip |
| Full analysis: | https://app.any.run/tasks/1bcaa7c9-e08e-4cea-b265-49c56c1c4bd5 |
| Verdict: | Malicious activity |
| Analysis date: | May 03, 2024, 18:13:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 370E783A1F4A801C8CF14CA94AB995A0 |
| SHA1: | 9A9610BF81987F4741CEF2C02F232D322EEDA38D |
| SHA256: | D0250B1D2C287D9F2731C7240464D07E1EBE0560C13062D856124ED87FFA2F4A |
| SSDEEP: | 98304:iXAkGQ/WghqMKQ1UlDItuXocBNShI9IhMbVCkXPuZqwiICwM8C7A8+emiDuuTd7y:+UHMt+LXhAPN |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3968)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 3968)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3968)
Reads the Internet Settings
- TrafficBot [Cracked By MarkVoid].exe (PID: 4028)
- TrafficBot [Cracked By MarkVoid].exe (PID: 2072)
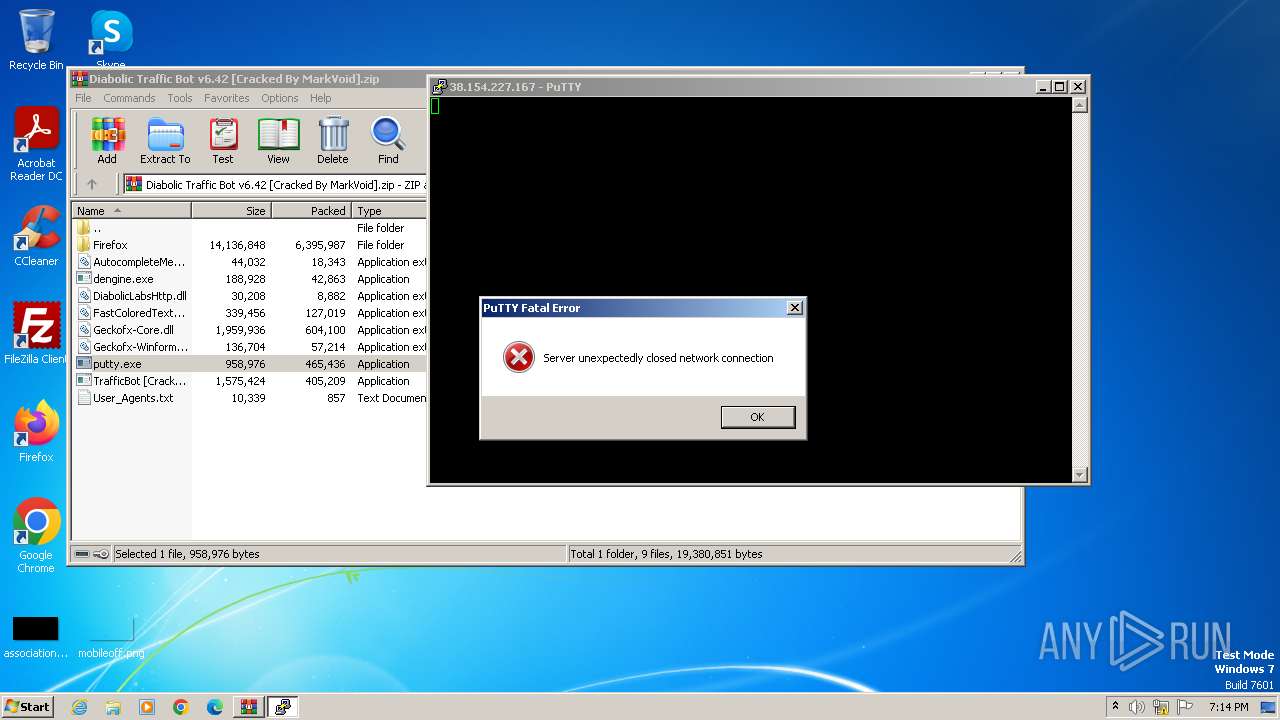
Connects to unusual port
- putty.exe (PID: 2032)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3968)
Checks supported languages
- putty.exe (PID: 4012)
- TrafficBot [Cracked By MarkVoid].exe (PID: 4028)
- TrafficBot [Cracked By MarkVoid].exe (PID: 2072)
- putty.exe (PID: 1064)
- putty.exe (PID: 2032)
Reads the computer name
- putty.exe (PID: 4012)
- TrafficBot [Cracked By MarkVoid].exe (PID: 4028)
- TrafficBot [Cracked By MarkVoid].exe (PID: 2072)
- putty.exe (PID: 2032)
- putty.exe (PID: 1064)
Reads the machine GUID from the registry
- TrafficBot [Cracked By MarkVoid].exe (PID: 4028)
- TrafficBot [Cracked By MarkVoid].exe (PID: 2072)
- putty.exe (PID: 1064)
- putty.exe (PID: 2032)
Reads Environment values
- TrafficBot [Cracked By MarkVoid].exe (PID: 4028)
- TrafficBot [Cracked By MarkVoid].exe (PID: 2072)
Creates files or folders in the user directory
- putty.exe (PID: 1064)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (33.3) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2020:09:04 03:24:48 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Firefox/ |
Total processes
37
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1064 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3968.35617\putty.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3968.35617\putty.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Simon Tatham Integrity Level: MEDIUM Description: SSH, Telnet and Rlogin client Exit code: 0 Version: Release 0.69 Modules
| |||||||||||||||
| 2032 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3968.36352\putty.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3968.36352\putty.exe | WinRAR.exe | ||||||||||||
User: admin Company: Simon Tatham Integrity Level: MEDIUM Description: SSH, Telnet and Rlogin client Version: Release 0.69 Modules
| |||||||||||||||
| 2072 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3968.35420\TrafficBot [Cracked By MarkVoid].exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3968.35420\TrafficBot [Cracked By MarkVoid].exe | WinRAR.exe | ||||||||||||
User: admin Company: Diabolic Labs Integrity Level: MEDIUM Description: Traffic Bot Version: 6.42 Modules
| |||||||||||||||
| 3968 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Diabolic Traffic Bot v6.42 [Cracked By MarkVoid].zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4012 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3968.34302\putty.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3968.34302\putty.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Simon Tatham Integrity Level: MEDIUM Description: SSH, Telnet and Rlogin client Exit code: 0 Version: Release 0.69 Modules
| |||||||||||||||
| 4028 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3968.34869\TrafficBot [Cracked By MarkVoid].exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3968.34869\TrafficBot [Cracked By MarkVoid].exe | WinRAR.exe | ||||||||||||
User: admin Company: Diabolic Labs Integrity Level: MEDIUM Description: Traffic Bot Version: 6.42 Modules
| |||||||||||||||
Total events
7 681
Read events
7 649
Write events
32
Delete events
0
Modification events
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Diabolic Traffic Bot v6.42 [Cracked By MarkVoid].zip | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
140
Suspicious files
0
Text files
5
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3968.34302\Firefox\freebl3.dll | executable | |
MD5:D17E43F3F93FE70CBD2B474CBB52749B | SHA256:7917402A4102E301B1C48E68D6C8F45DCD302D604BCCA9822AC707403DB35294 | |||
| 3968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3968.34302\Firefox\d3dcompiler_47.dll | executable | |
MD5:C5B362BCE86BB0AD3149C4540201331D | SHA256:EFBDBBCD0D954F8FDC53467DE5D89AD525E4E4A9CFFF8A15D07C6FDB350C407F | |||
| 3968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3968.34302\Firefox\AccessibleMarshal.dll | executable | |
MD5:59CC6AD62CDB45A281A602369DC69FDA | SHA256:F16C9311830CA1628448AE4ABA4B54DF33AC1CD1682BCBBB129E4B28D6536B6C | |||
| 3968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3968.34302\Firefox\libEGL.dll | executable | |
MD5:F761BE1F6E49B08A8724496D1FE16343 | SHA256:6806DEF406AE61AFEDBDF8C3D70E5FF8B85B21DDFEF910080AE263932A6E106E | |||
| 3968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3968.34302\Firefox\nssckbi.dll | executable | |
MD5:CB2C4AB44B14C9567015EC4352A4FBBC | SHA256:E807076EDEFA13AA292A6DB354F98A8243C868F71988C7D80954B14816107588 | |||
| 3968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3968.34302\Firefox\icuin56.dll | executable | |
MD5:109A802AAA0177266CF0D045B8C26C56 | SHA256:58356AF3F49E25ED2201D3367EB3CA49DEC8EC78D5711475719778EBA3CFD8AD | |||
| 3968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3968.34302\Firefox\D3DCompiler_43.dll | executable | |
MD5:1C9B45E87528B8BB8CFA884EA0099A85 | SHA256:2F23182EC6F4889397AC4BF03D62536136C5BDBA825C7D2C4EF08C827F3A8A1C | |||
| 3968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3968.34302\Firefox\lgpllibs.dll | executable | |
MD5:6E218202CF13E07DF71B28A5CB797387 | SHA256:8546698D1C5E38CD055E41ED9B5787BFD0299AAC0C2923C5759884B5A9B944B8 | |||
| 3968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3968.34302\Firefox\mozglue.dll | executable | |
MD5:67360640285661EB1004C704D760F7AD | SHA256:0EDCFA424F9DA0D1894D99B99DB4DE8EA1B31F7717E8E14DD643F87D4D1C8EB6 | |||
| 3968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3968.34302\Firefox\libGLESv2.dll | executable | |
MD5:9191452050C86F3B6CA9278A276E0F23 | SHA256:348703ADDA8FE086CC8DB304C8638D4A496A4A86F2AE3BE916CB52A9B787C28A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
11
DNS requests
2
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4028 | TrafficBot [Cracked By MarkVoid].exe | 49.13.77.253:80 | prx.biz | Hetzner Online GmbH | DE | unknown |
2072 | TrafficBot [Cracked By MarkVoid].exe | 49.13.77.253:80 | prx.biz | Hetzner Online GmbH | DE | unknown |
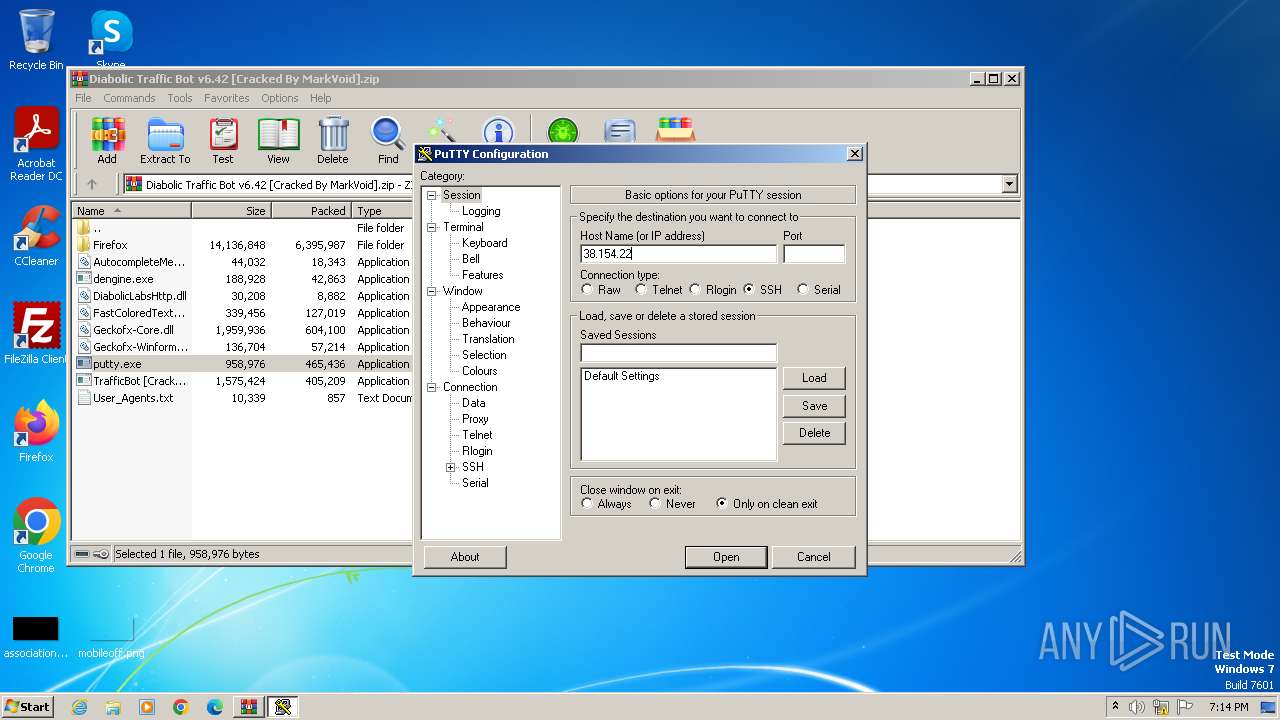
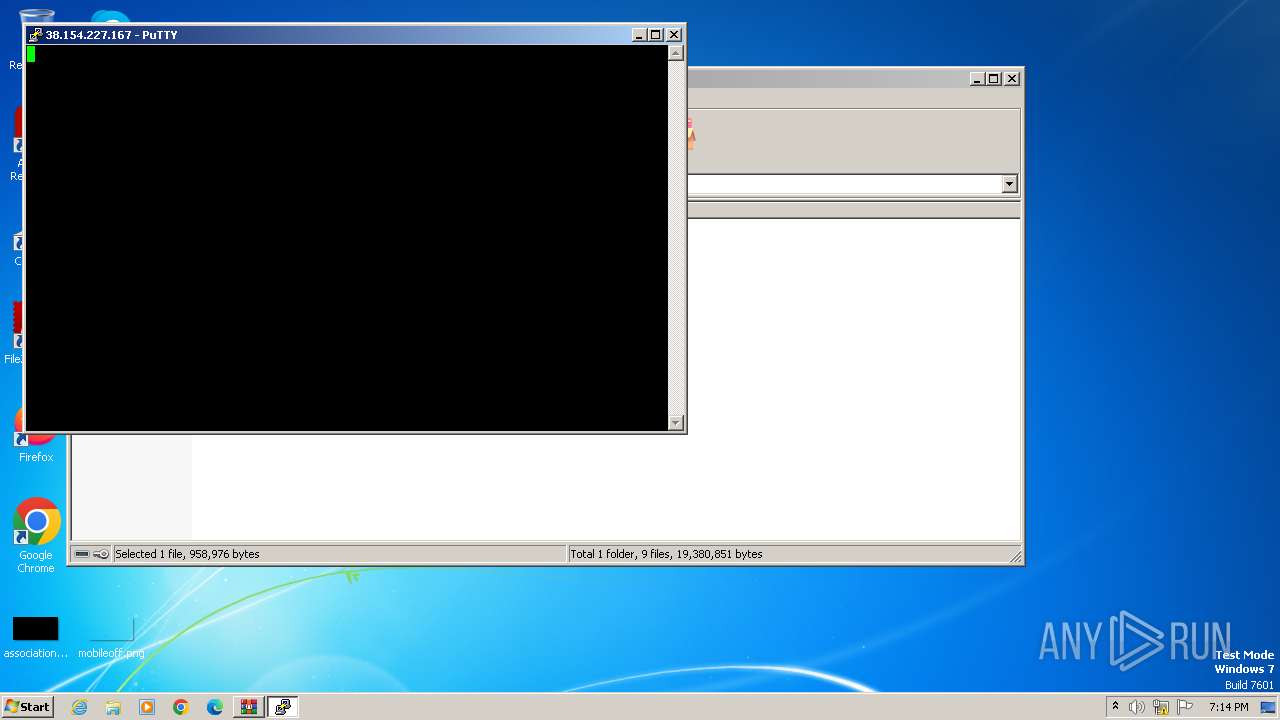
2032 | putty.exe | 38.154.227.167:5868 | — | COGENT-174 | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
prx.biz |
| unknown |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1088 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |