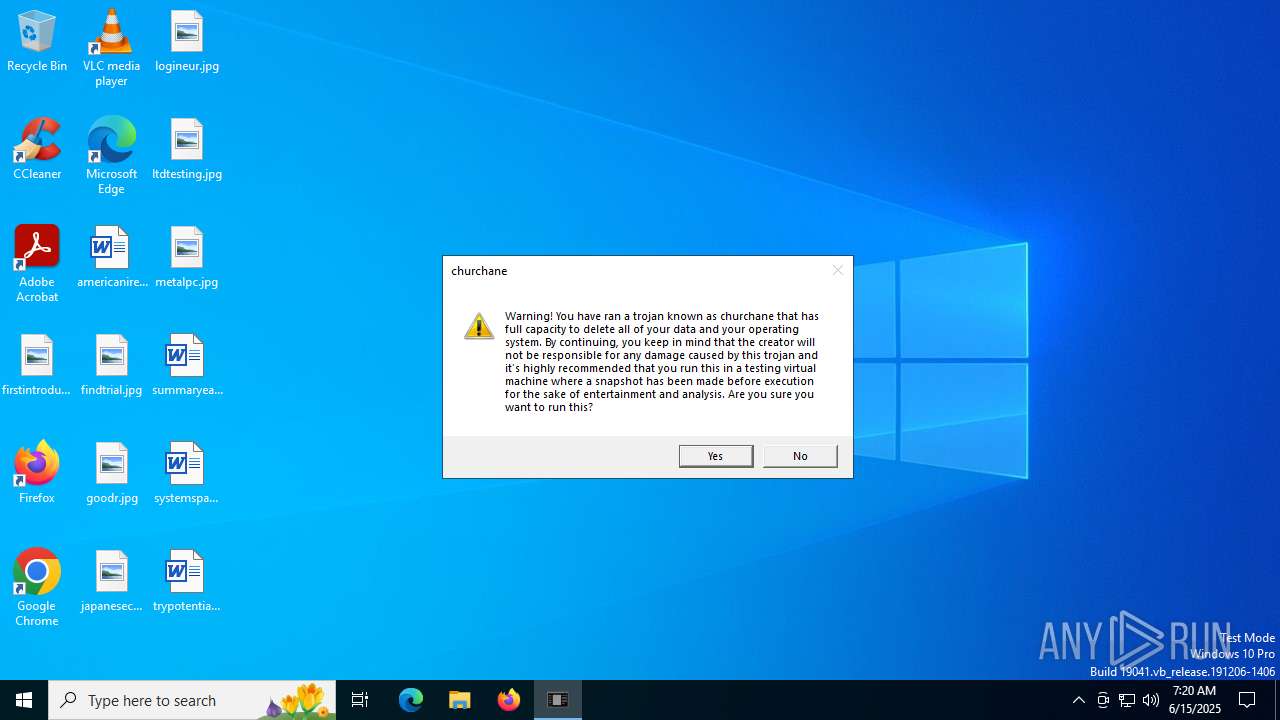
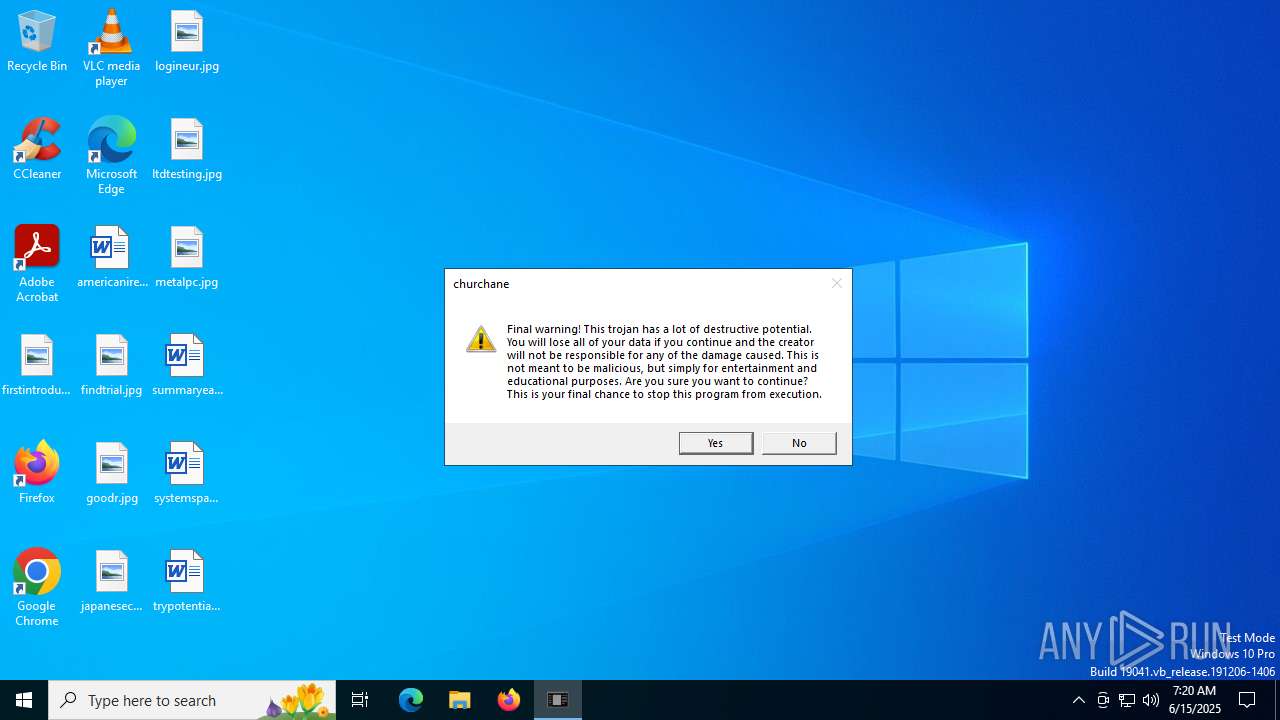
| File name: | churchane.exe |
| Full analysis: | https://app.any.run/tasks/d0239bcb-f451-48e8-aed6-a358b59d0f1d |
| Verdict: | Malicious activity |
| Analysis date: | June 15, 2025, 07:20:40 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 9AB83628D51A49D37990CEE00B13875A |
| SHA1: | 5B4C4E5A2DBF3BA35AF31A9EE5AEA7728AF02A3C |
| SHA256: | D0174E6589527C9D7A9CE8DAD63E9F3BC79E44722010DFDB83BA254FF4F35C20 |
| SSDEEP: | 384:aZdyDPsd4m6jDXiO3zoSTocAfZ/VaJ1NbOIOsqa:azoe4BiOjoRR/M19Oy |
MALICIOUS
Disables task manager
- churchane.exe (PID: 3388)
SUSPICIOUS
There is functionality for taking screenshot (YARA)
- churchane.exe (PID: 3388)
Reads security settings of Internet Explorer
- churchane.exe (PID: 3388)
Uses ATTRIB.EXE to modify file attributes
- churchane.exe (PID: 3388)
Creates file in the systems drive root
- bootcfg.exe (PID: 6016)
Uses ICACLS.EXE to modify access control lists
- churchane.exe (PID: 3388)
Executes as Windows Service
- msdtc.exe (PID: 7796)
- vds.exe (PID: 8376)
- VSSVC.exe (PID: 5644)
- dllhost.exe (PID: 7404)
Starts CMD.EXE for commands execution
- churchane.exe (PID: 3388)
INFO
Checks supported languages
- churchane.exe (PID: 3388)
- agentactivationruntimestarter.exe (PID: 4552)
- appidtel.exe (PID: 4460)
Reads the computer name
- churchane.exe (PID: 3388)
- agentactivationruntimestarter.exe (PID: 4552)
Process checks computer location settings
- churchane.exe (PID: 3388)
Uses BITSADMIN.EXE
- churchane.exe (PID: 3388)
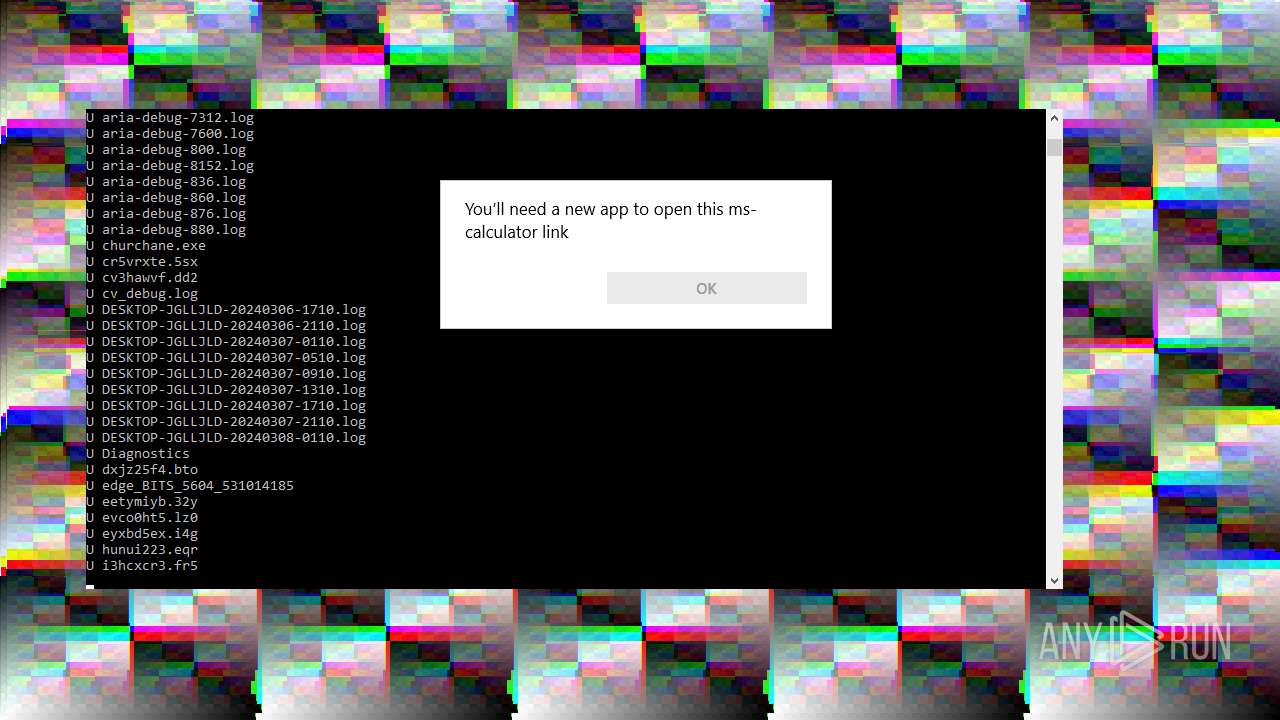
Reads security settings of Internet Explorer
- calc.exe (PID: 6492)
- OpenWith.exe (PID: 2140)
- certreq.exe (PID: 4236)
Execution of CURL command
- churchane.exe (PID: 3388)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:06:14 19:55:20+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.44 |
| CodeSize: | 9216 |
| InitializedDataSize: | 13824 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2685 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
255
Monitored processes
102
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 420 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | bitsadmin.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 436 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | certutil.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 640 | "C:\Windows\System32\bitsadmin.exe" | C:\Windows\SysWOW64\bitsadmin.exe | — | churchane.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: BITS administration utility Exit code: 0 Version: 7.8.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 728 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | at.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 760 | "C:\Windows\System32\cacls.exe" | C:\Windows\SysWOW64\cacls.exe | — | churchane.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Control ACLs Program Exit code: 160 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1128 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | ByteCodeGenerator.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1324 | "C:\Windows\System32\dcomcnfg.exe" | C:\Windows\SysWOW64\dcomcnfg.exe | — | churchane.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM+ Exit code: 0 Version: 2001.12.10941.16384 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1568 | "C:\Windows\System32\cmdl32.exe" | C:\Windows\SysWOW64\cmdl32.exe | — | churchane.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Connection Manager Auto-Download Exit code: 1 Version: 7.2.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1568 | "C:\Windows\System32\control.exe" | C:\Windows\SysWOW64\control.exe | — | churchane.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Control Panel Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1660 | "C:\Windows\System32\cmdkey.exe" | C:\Windows\SysWOW64\cmdkey.exe | — | churchane.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Credential Manager Command Line Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
15 737
Read events
15 637
Write events
100
Delete events
0
Modification events
| (PID) Process: | (3388) churchane.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableTaskMgr |
Value: 1 | |||
| (PID) Process: | (3388) churchane.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableRegistryTools |
Value: 1 | |||
| (PID) Process: | (3388) churchane.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Policies\Microsoft\Windows\System |
| Operation: | write | Name: | DisableCMD |
Value: 2 | |||
| (PID) Process: | (3980) AtBroker.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Accessibility |
| Operation: | write | Name: | Configuration |
Value: | |||
| (PID) Process: | (3980) AtBroker.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Accessibility |
| Operation: | write | Name: | NarratorAfterSigninResetCompleted |
Value: 1 | |||
| (PID) Process: | (6492) calc.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (2140) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2140) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2140) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6492) calc.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
Executable files
0
Suspicious files
6
Text files
11
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3388 | churchane.exe | \Device\Harddisk0\DR0 | — | |
MD5:— | SHA256:— | |||
| 3740 | cleanmgr.exe | C:\Windows\System32\LogFiles\setupcln\setupact.log | — | |
MD5:— | SHA256:— | |||
| 3740 | cleanmgr.exe | C:\Users\admin\AppData\Local\Packages\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\AC\F4EB2D6C-ED2B-4BDD-AD9D-F913287E6768.lock | text | |
MD5:F49655F856ACB8884CC0ACE29216F511 | SHA256:7852FCE59C67DDF1D6B8B997EAA1ADFAC004A9F3A91C37295DE9223674011FBA | |||
| 3740 | cleanmgr.exe | C:\Windows\System32\LogFiles\setupcln\diagerr.xml | text | |
MD5:A0C22C9F1D7FADAAADABF0C83A1F4145 | SHA256:B39BD2E8B9D0CAE257127FE86F4CDAD8A730B923E11CF7C480C441D51E49D3B8 | |||
| 3740 | cleanmgr.exe | C:\Windows\System32\LogFiles\setupcln\diagwrn.xml | text | |
MD5:37A45C2C17E98ED82C9C8AE183D3E438 | SHA256:102F0354290625AC4C1CD771BCA4C0B85ABD1AD7FE493CB7775D0DCB2A9F8C3E | |||
| 3740 | cleanmgr.exe | C:\Users\admin\AppData\Local\D3DSCache\3534848bb9f4cb71\F4EB2D6C-ED2B-4BDD-AD9D-F913287E6768.lock | text | |
MD5:F49655F856ACB8884CC0ACE29216F511 | SHA256:7852FCE59C67DDF1D6B8B997EAA1ADFAC004A9F3A91C37295DE9223674011FBA | |||
| 3740 | cleanmgr.exe | C:\Users\admin\AppData\Local\D3DSCache\f4d41c5d09ae781\F4EB2D6C-ED2B-4BDD-AD9D-F913287E6768.lock | text | |
MD5:F49655F856ACB8884CC0ACE29216F511 | SHA256:7852FCE59C67DDF1D6B8B997EAA1ADFAC004A9F3A91C37295DE9223674011FBA | |||
| 3740 | cleanmgr.exe | C:\Windows\System32\LogFiles\setupcln\setuperr.log | text | |
MD5:B3EC14354434E9F753284E2955E24F83 | SHA256:12CE9AF9824D7012D95C7DAA7BC8C61DF591E56E49E85561647E478487E6B022 | |||
| 3740 | cleanmgr.exe | C:\Users\admin\AppData\Local\D3DSCache\cb00da9ba77862e\F4EB2D6C-ED2B-4BDD-AD9D-F913287E6768.lock | text | |
MD5:F49655F856ACB8884CC0ACE29216F511 | SHA256:7852FCE59C67DDF1D6B8B997EAA1ADFAC004A9F3A91C37295DE9223674011FBA | |||
| 3740 | cleanmgr.exe | C:\Users\admin\AppData\Local\D3DSCache\d3fe7cdcb51a5ef5\F4EB2D6C-ED2B-4BDD-AD9D-F913287E6768.lock | text | |
MD5:F49655F856ACB8884CC0ACE29216F511 | SHA256:7852FCE59C67DDF1D6B8B997EAA1ADFAC004A9F3A91C37295DE9223674011FBA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
37
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3944 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4764 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5040 | SystemSettings.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5040 | SystemSettings.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4764 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
8056 | msedge.exe | GET | 200 | 150.171.27.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:miaw1DnTjosj26hwMuI_SbNdM7bU5M4g-p8ZdjUpbMI&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4960 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2336 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
3944 | svchost.exe | 20.190.160.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3944 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
mmc.exe | ViewerExternalLogsPath = 'C:\ProgramData\Microsoft\Event Viewer\ExternalLogs': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerViewsFolderPath = 'C:\ProgramData\Microsoft\Event Viewer\Views': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerConfigPath = 'C:\ProgramData\Microsoft\Event Viewer': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerAdminViewsPath = 'C:\ProgramData\Microsoft\Event Viewer\Views\ApplicationViewsRootNode': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
Dism.exe | PID=8532 TID=8536 Instantiating the Provider Store. - CDISMImageSession::get_ProviderStore |
Dism.exe | PID=8532 TID=8536 Initializing a provider store for the LOCAL session type. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=8532 TID=8536 Attempting to initialize the logger from the Image Session. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=8532 TID=8536 Provider has not previously been encountered. Attempting to initialize the provider. - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=8532 TID=8536 Loading Provider from location C:\Windows\System32\Dism\LogProvider.dll - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=8532 TID=8536 Connecting to the provider located at C:\Windows\System32\Dism\LogProvider.dll. - CDISMProviderStore::Internal_LoadProvider |