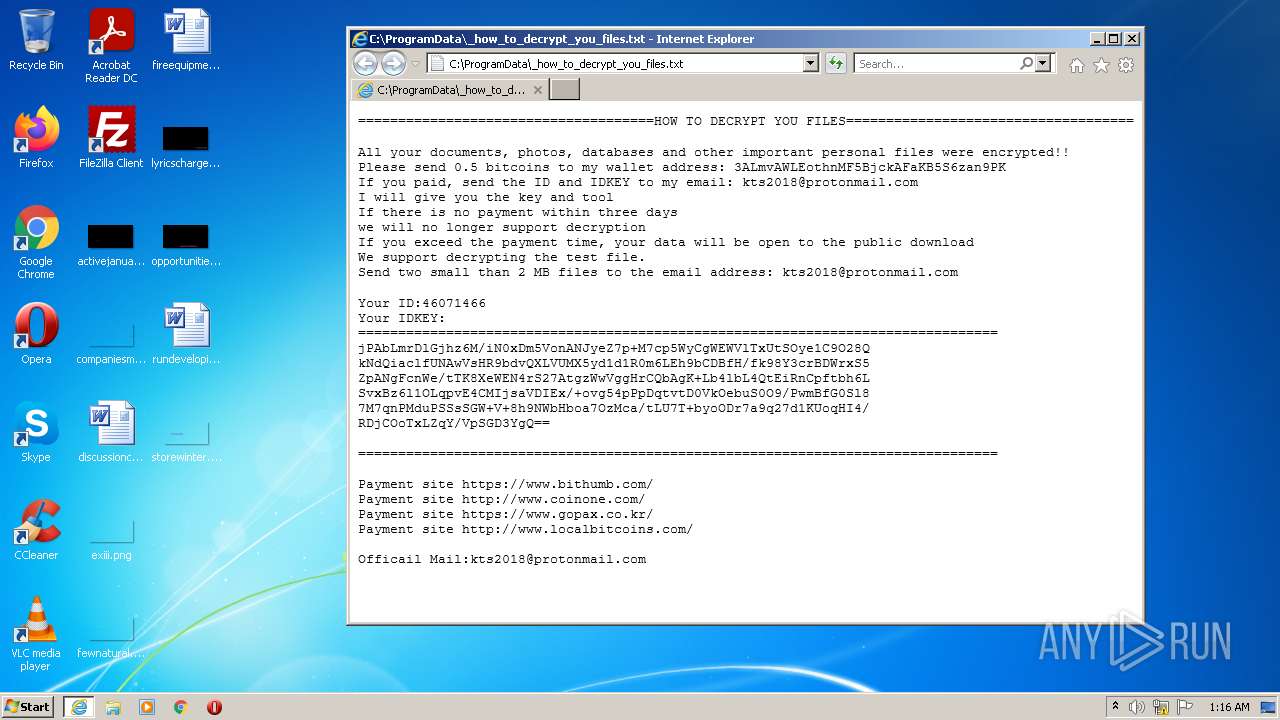
| File name: | KatyushaRansomware.exe |
| Full analysis: | https://app.any.run/tasks/cfc5d597-a6fb-4cd3-9b15-f4e6c960889d |
| Verdict: | Malicious activity |
| Analysis date: | January 15, 2022, 01:15:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | MS-DOS executable, MZ for MS-DOS |
| MD5: | 7F87DB33980C0099739DE40D1B725500 |
| SHA1: | F0626999B7F730F9003AC1389D3060C50068DA5A |
| SHA256: | D00EE0E6EAB686424F8D383E151D22005F19ADBDA5B380A75669629E32FE12A6 |
| SSDEEP: | 49152:tzlhgyBIjVpPZHZlPpLPk0vglJIAc/8KYBsxdO0G7x+dP1Y+U:zy9jRZlFknvzcEKY8dOD7x8NYl |
MALICIOUS
Drops executable file immediately after starts
- zkts.exe (PID: 2736)
- KatyushaRansomware.exe (PID: 3816)
Application was dropped or rewritten from another process
- zkts.exe (PID: 2736)
- ktsi.exe (PID: 2424)
- m32.exe (PID: 4048)
Deletes shadow copies
- cmd.exe (PID: 3956)
SUSPICIOUS
Checks supported languages
- zkts.exe (PID: 2736)
- cmd.exe (PID: 3684)
- KatyushaRansomware.exe (PID: 3816)
- cmd.exe (PID: 3280)
- m32.exe (PID: 4048)
- ktsi.exe (PID: 2424)
- cmd.exe (PID: 3056)
- cmd.exe (PID: 3988)
- cmd.exe (PID: 3544)
- cmd.exe (PID: 848)
- cmd.exe (PID: 3948)
- cmd.exe (PID: 2664)
- cmd.exe (PID: 2296)
- cmd.exe (PID: 1368)
- cmd.exe (PID: 2360)
- cmd.exe (PID: 1236)
- cmd.exe (PID: 2112)
- cmd.exe (PID: 3564)
- cmd.exe (PID: 3720)
- cmd.exe (PID: 3148)
- cmd.exe (PID: 3956)
Drops a file with too old compile date
- zkts.exe (PID: 2736)
Starts CMD.EXE for commands execution
- KatyushaRansomware.exe (PID: 3816)
- ktsi.exe (PID: 2424)
Creates files in the Windows directory
- KatyushaRansomware.exe (PID: 3816)
- zkts.exe (PID: 2736)
Executable content was dropped or overwritten
- KatyushaRansomware.exe (PID: 3816)
- zkts.exe (PID: 2736)
Removes files from Windows directory
- KatyushaRansomware.exe (PID: 3816)
Reads the computer name
- m32.exe (PID: 4048)
- KatyushaRansomware.exe (PID: 3816)
- ktsi.exe (PID: 2424)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 3056)
- cmd.exe (PID: 3988)
- cmd.exe (PID: 3544)
- cmd.exe (PID: 3948)
- cmd.exe (PID: 2664)
- cmd.exe (PID: 2296)
- cmd.exe (PID: 1368)
- cmd.exe (PID: 848)
- cmd.exe (PID: 2360)
- cmd.exe (PID: 1236)
- cmd.exe (PID: 2112)
- cmd.exe (PID: 3564)
- cmd.exe (PID: 3720)
- cmd.exe (PID: 3148)
Creates files in the program directory
- ktsi.exe (PID: 2424)
Starts Internet Explorer
- ktsi.exe (PID: 2424)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 1472)
INFO
Checks supported languages
- taskkill.exe (PID: 2508)
- taskkill.exe (PID: 3676)
- taskkill.exe (PID: 1596)
- taskkill.exe (PID: 4080)
- taskkill.exe (PID: 2768)
- taskkill.exe (PID: 2052)
- taskkill.exe (PID: 3264)
- taskkill.exe (PID: 1592)
- taskkill.exe (PID: 976)
- taskkill.exe (PID: 2584)
- taskkill.exe (PID: 3848)
- taskkill.exe (PID: 1128)
- taskkill.exe (PID: 3684)
- taskkill.exe (PID: 3596)
- vssadmin.exe (PID: 3228)
- vssadmin.exe (PID: 804)
- WINWORD.EXE (PID: 3840)
- iexplore.exe (PID: 1472)
- iexplore.exe (PID: 2836)
Reads the computer name
- taskkill.exe (PID: 2508)
- taskkill.exe (PID: 1596)
- taskkill.exe (PID: 4080)
- taskkill.exe (PID: 2768)
- taskkill.exe (PID: 2052)
- taskkill.exe (PID: 3264)
- taskkill.exe (PID: 3676)
- taskkill.exe (PID: 1592)
- taskkill.exe (PID: 976)
- taskkill.exe (PID: 2584)
- taskkill.exe (PID: 3848)
- taskkill.exe (PID: 1128)
- taskkill.exe (PID: 3684)
- taskkill.exe (PID: 3596)
- vssadmin.exe (PID: 3228)
- vssadmin.exe (PID: 804)
- WINWORD.EXE (PID: 3840)
- iexplore.exe (PID: 1472)
- iexplore.exe (PID: 2836)
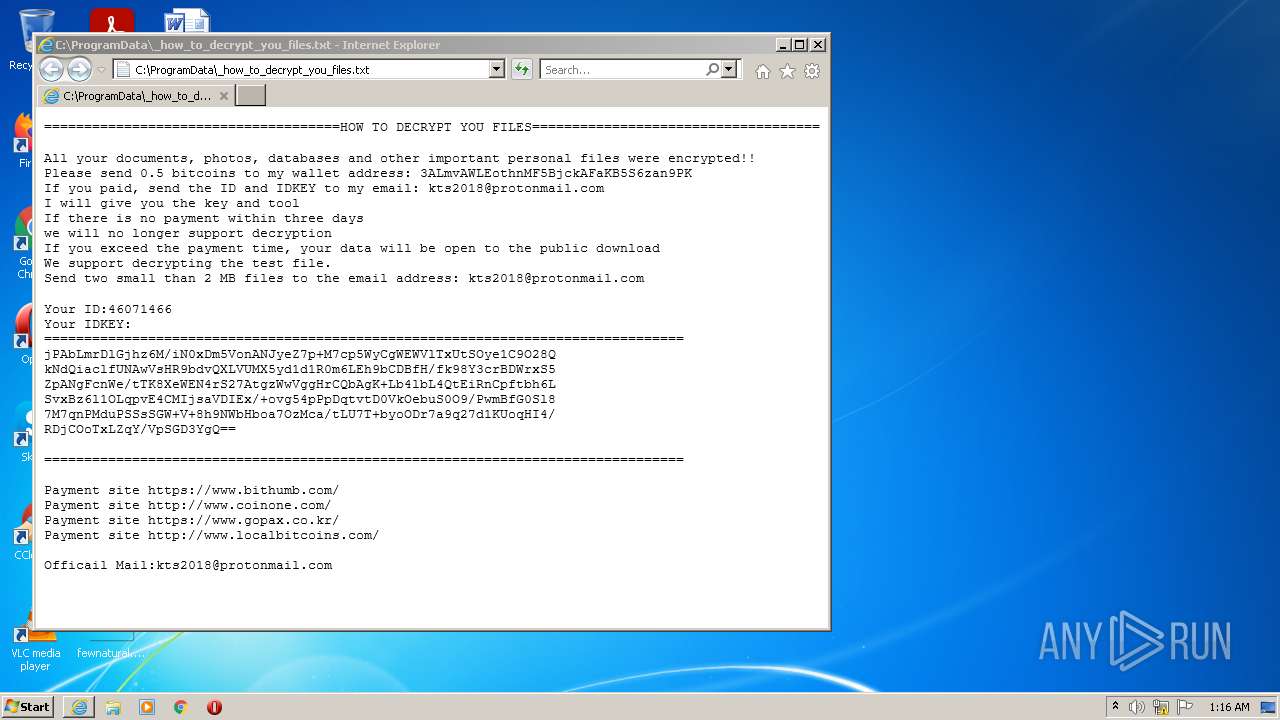
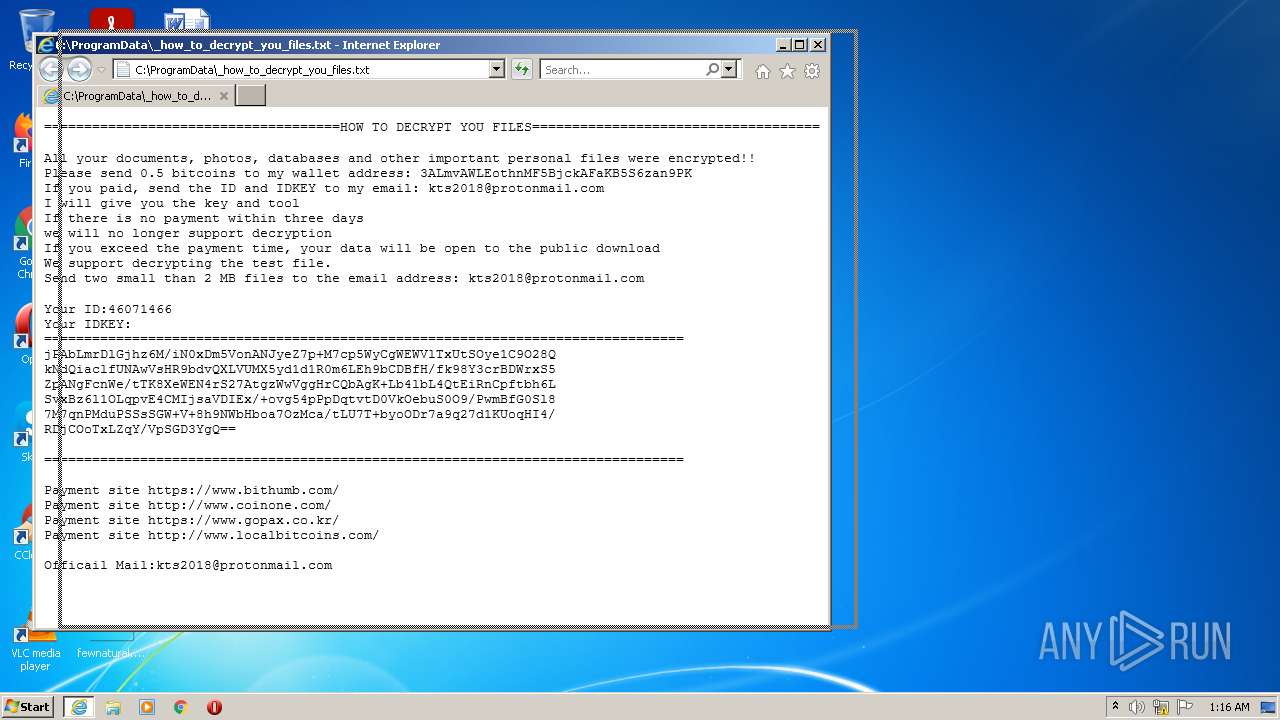
Dropped object may contain Bitcoin addresses
- ktsi.exe (PID: 2424)
Manual execution by user
- WINWORD.EXE (PID: 3840)
Creates files in the user directory
- WINWORD.EXE (PID: 3840)
Changes internet zones settings
- iexplore.exe (PID: 2836)
Application launched itself
- iexplore.exe (PID: 2836)
Checks Windows Trust Settings
- iexplore.exe (PID: 2836)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3840)
Reads internet explorer settings
- iexplore.exe (PID: 1472)
Reads the date of Windows installation
- iexplore.exe (PID: 2836)
Reads settings of System Certificates
- iexplore.exe (PID: 2836)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| Subsystem: | Windows command line |
|---|---|
| SubsystemVersion: | 5.1 |
| ImageVersion: | - |
| OSVersion: | 5.1 |
| EntryPoint: | 0x2f919d |
| UninitializedDataSize: | - |
| InitializedDataSize: | 2508800 |
| CodeSize: | 586752 |
| LinkerVersion: | 14 |
| PEType: | PE32 |
| TimeStamp: | 2018:10:14 17:23:06+02:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_CUI |
| Compilation Date: | 14-Oct-2018 15:23:06 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0040 |
| Pages in file: | 0x0001 |
| Relocations: | 0x0000 |
| Size of header: | 0x0002 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0xB400 |
| OEM information: | 0xCD09 |
| Address of NE header: | 0x00000040 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 14-Oct-2018 15:23:06 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.MPRESS1 | 0x00001000 | 0x002F8000 | 0x0025B800 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.99993 |
.MPRESS2(\x0d | 0x002F9000 | 0x00000D28 | 0x00000E00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.81229 |
.rsrc | 0x002FA000 | 0x00000258 | 0x00000400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.24563 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.91161 | 381 | UNKNOWN | English - United States | RT_MANIFEST |
101 | 7.99977 | 1934640 | UNKNOWN | Chinese - PRC | EXE |
102 | 0 | 336384 | UNKNOWN | Chinese - PRC | EXE |
Imports
ADVAPI32.dll |
IPHLPAPI.DLL |
KERNEL32.DLL |
SHELL32.dll |
USER32.dll |
WLDAP32.dll |
WS2_32.dll |
Total processes
80
Monitored processes
40
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 804 | vssadmin delete shadows /all /quiet | C:\Windows\system32\vssadmin.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Command Line Interface for Microsoft� Volume Shadow Copy Service Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 848 | C:\Windows\system32\cmd.exe /c taskkill /F /IM sqlwriter.exe | C:\Windows\system32\cmd.exe | — | ktsi.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 128 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 976 | taskkill /F /IM reportingservicesservice.exe | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1128 | taskkill /F /IM oracle.exe | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1236 | C:\Windows\system32\cmd.exe /c taskkill /F /IM omtsreco.exe | C:\Windows\system32\cmd.exe | — | ktsi.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 128 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1368 | C:\Windows\system32\cmd.exe /c taskkill /F /IM fdlauncher.exe | C:\Windows\system32\cmd.exe | — | ktsi.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 128 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1472 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2836 CREDAT:144385 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1592 | taskkill /F /IM fdlauncher.exe | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1596 | taskkill /F /IM httpd.exe | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2052 | taskkill /F /IM sqlagent.exe | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
13 403
Read events
12 946
Write events
316
Delete events
141
Modification events
| (PID) Process: | (3816) KatyushaRansomware.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3816) KatyushaRansomware.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3816) KatyushaRansomware.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3816) KatyushaRansomware.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3840) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | !1? |
Value: 21313F00000F0000010000000000000000000000 | |||
| (PID) Process: | (3840) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3840) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3840) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3840) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3840) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
Executable files
24
Suspicious files
599
Text files
9
Unknown types
11
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2736 | zkts.exe | C:\windows\temp\KillDuplicate.cmd | text | |
MD5:68CECDF24AA2FD011ECE466F00EF8450 | SHA256:64929489DC8A0D66EA95113D4E676368EDB576EA85D23564D53346B21C202770 | |||
| 2736 | zkts.exe | C:\windows\temp\exma-1.dll | executable | |
MD5:BA629216DB6CF7C0C720054B0C9A13F3 | SHA256:15292172A83F2E7F07114693AB92753ED32311DFBA7D54FE36CC7229136874D9 | |||
| 3816 | KatyushaRansomware.exe | C:\windows\temp\ktsi.exe | executable | |
MD5:DD2E5FD5109C54CC90B30B88EC0C585A | SHA256:A3DABB63F11E208A0D1D9B43B3D2575E2DC2A7D87C14EB654D3062F3BC0AD12D | |||
| 3816 | KatyushaRansomware.exe | C:\windows\temp\zkts.exe | executable | |
MD5:5D74E736C5C4224B813BEA351093C27F | SHA256:7F5F134FD3EC2C14956ACD7362C76E66759B8ECC51F986EF80BBF9F7F94B89FE | |||
| 2736 | zkts.exe | C:\windows\temp\coli-0.dll | executable | |
MD5:3C2FE2DBDF09CFA869344FDB53307CB2 | SHA256:0439628816CABE113315751E7113A9E9F720D7E499FFDD78ACBAC1ED8BA35887 | |||
| 2736 | zkts.exe | C:\windows\temp\svchostb.xml | xml | |
MD5:F56025565DE4F53F5771D4966C2B5555 | SHA256:EA7CAA08E115DBB438E29DA46B47F54C62C29697617BAE44464A9B63D9BDDF18 | |||
| 2736 | zkts.exe | C:\windows\temp\svchostp.exe | executable | |
MD5:0E2D6BE0556D0A1EC47A934DA3244FC0 | SHA256:FA2A5DB45A4808A3D087BB9CF807C5672BE9E856166A049D15997B56C4626AF4 | |||
| 2736 | zkts.exe | C:\windows\temp\katyusha.dll | executable | |
MD5:94BD92AD65EE59117DB13EAB0D40AE21 | SHA256:AD8008D02B66AD40ACB6389E51AEE351363968DA5A6B7DC4AC293AF354AF738F | |||
| 2736 | zkts.exe | C:\windows\temp\svchostbs.xml | xml | |
MD5:09D45AE26830115FD8D9CDC2AA640CA5 | SHA256:CF33A92A05BA3C807447A5F6B7E45577ED53174699241DA360876D4F4A2EB2DE | |||
| 2736 | zkts.exe | C:\windows\temp\posh-0.dll | executable | |
MD5:2F0A52CE4F445C6E656ECEBBCACEADE5 | SHA256:CDE45F7FF05F52B7215E4B0EA1F2F42AD9B42031E16A3BE9772AA09E014BACDB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
143
DNS requests
9
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2836 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
2836 | iexplore.exe | GET | 200 | 2.16.106.171:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?87fa8657099d92a8 | unknown | compressed | 4.70 Kb | whitelisted |
2836 | iexplore.exe | GET | 200 | 2.16.106.171:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?5aa5c0d7a2939da8 | unknown | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.1:90 | — | — | — | unknown |
— | — | 192.168.100.1:777 | — | — | — | unknown |
— | — | 192.168.100.1:8181 | — | — | — | unknown |
— | — | 192.168.100.1:445 | — | — | — | unknown |
— | — | 192.168.100.1:8020 | — | — | — | unknown |
— | — | 192.168.100.1:8008 | — | — | — | unknown |
— | — | 192.168.100.1:7080 | — | — | — | unknown |
— | — | 192.168.100.1:8060 | — | — | — | unknown |
— | — | 192.168.100.1:8010 | — | — | — | unknown |
— | — | 192.168.100.1:8082 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Generic Protocol Command Decode | SURICATA HTTP Unexpected Request body |
— | — | Generic Protocol Command Decode | SURICATA HTTP Unexpected Request body |
— | — | Generic Protocol Command Decode | SURICATA HTTP Unexpected Request body |