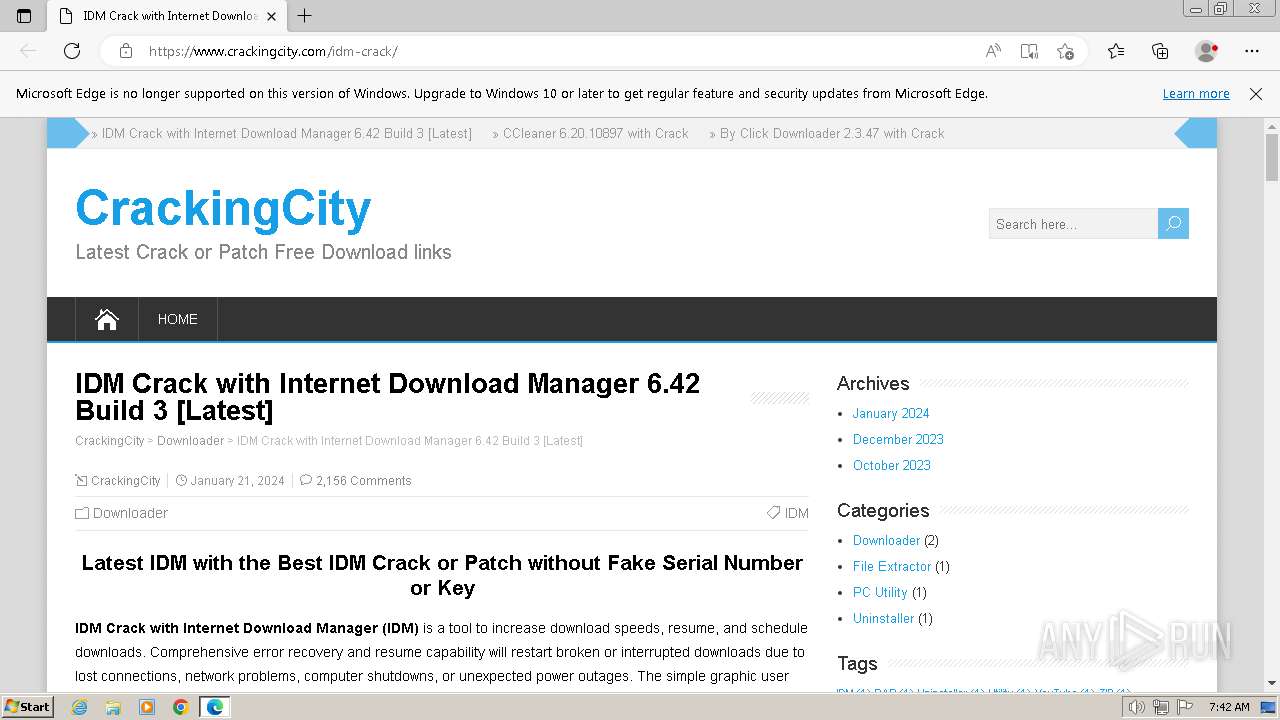
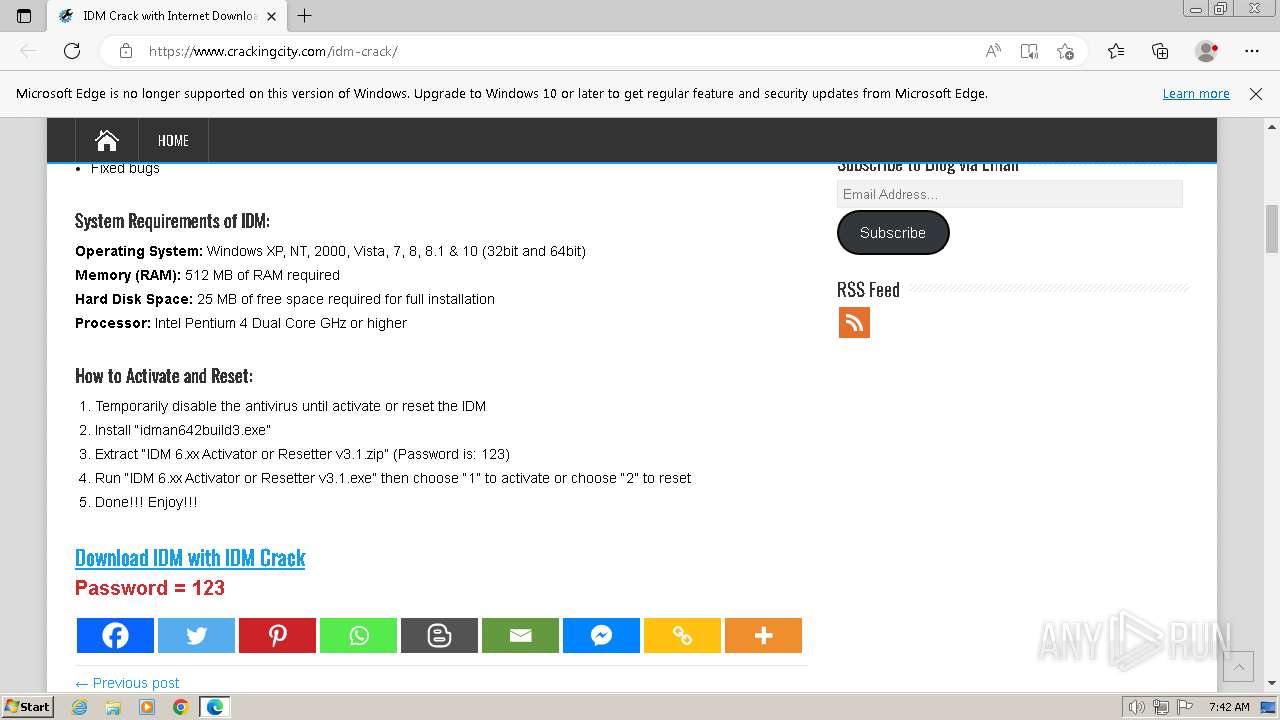
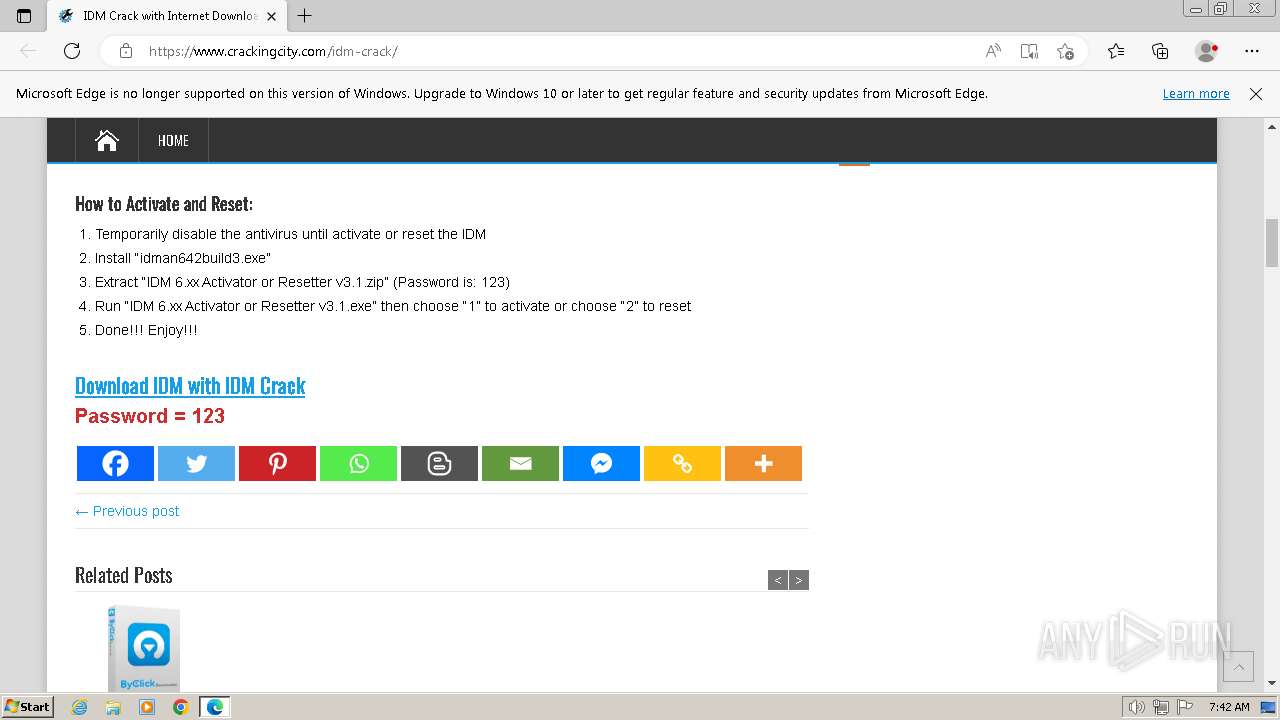
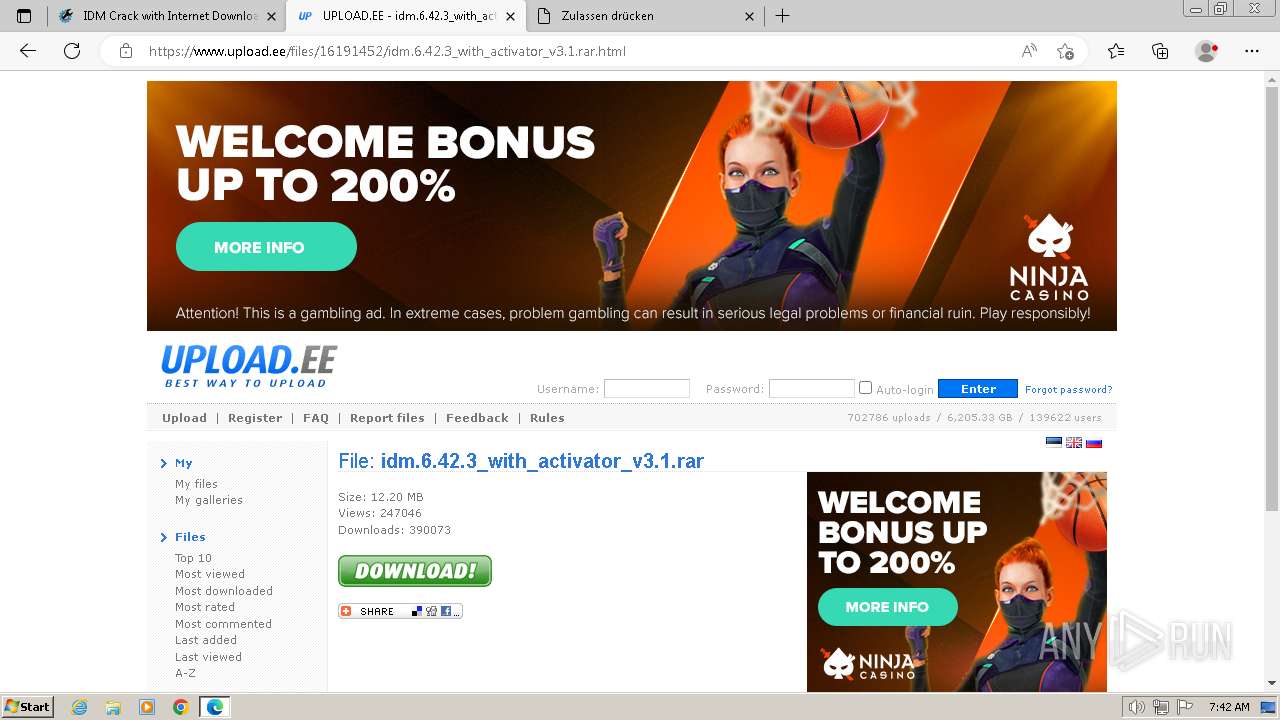
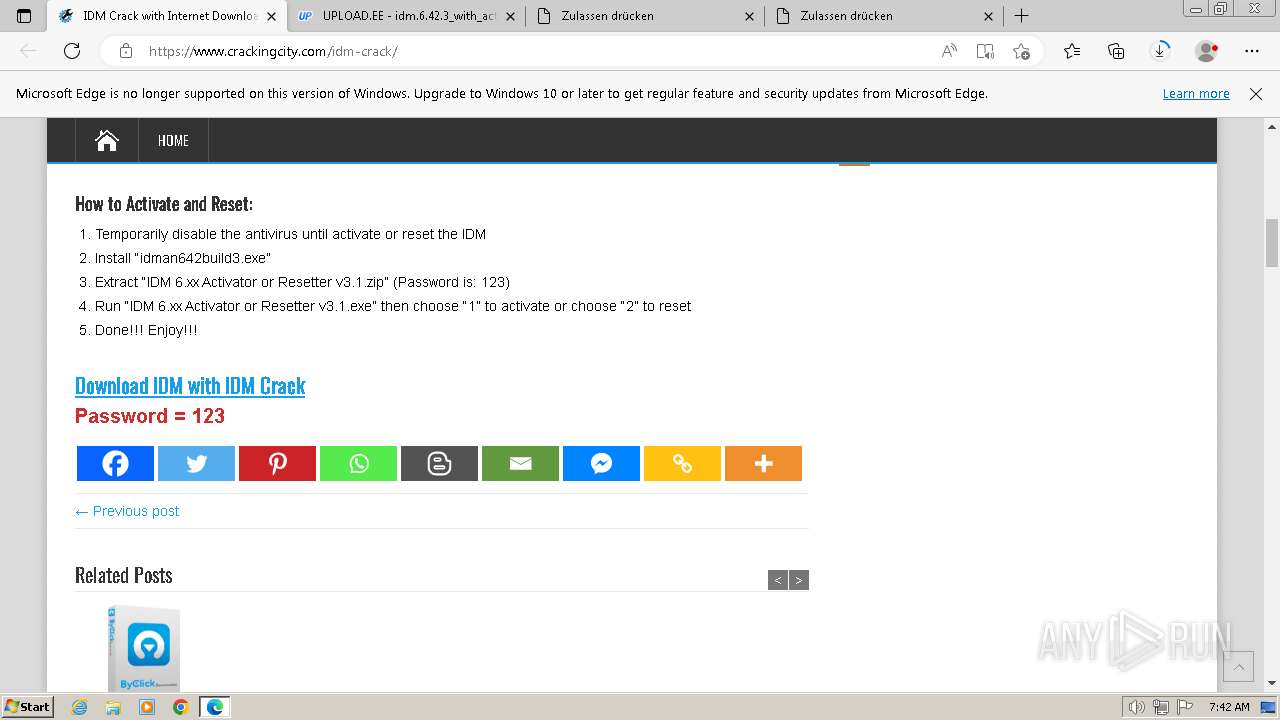
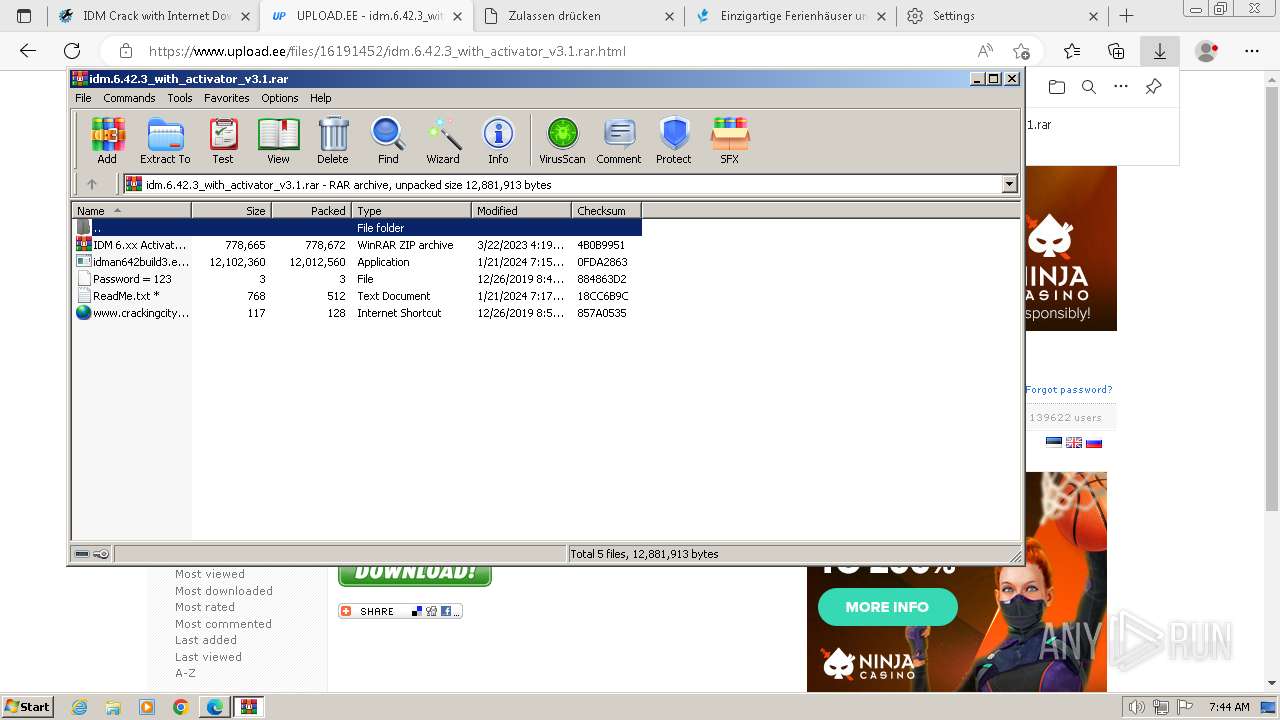
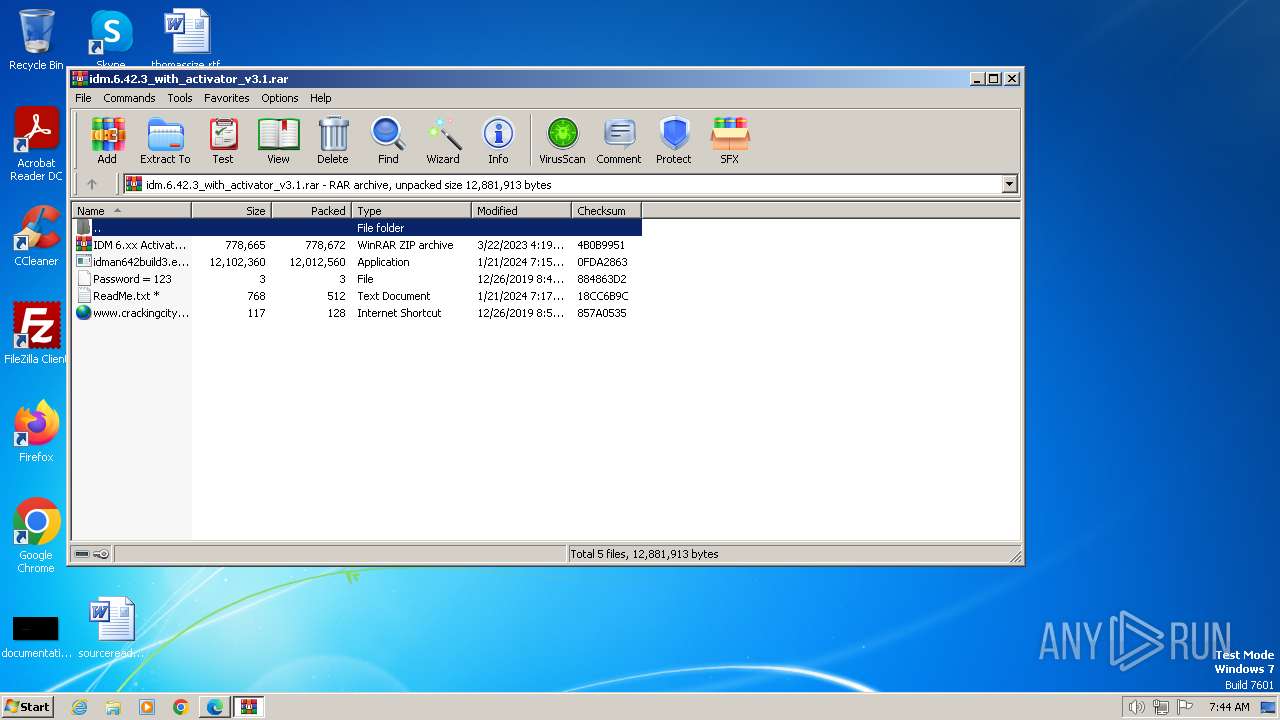
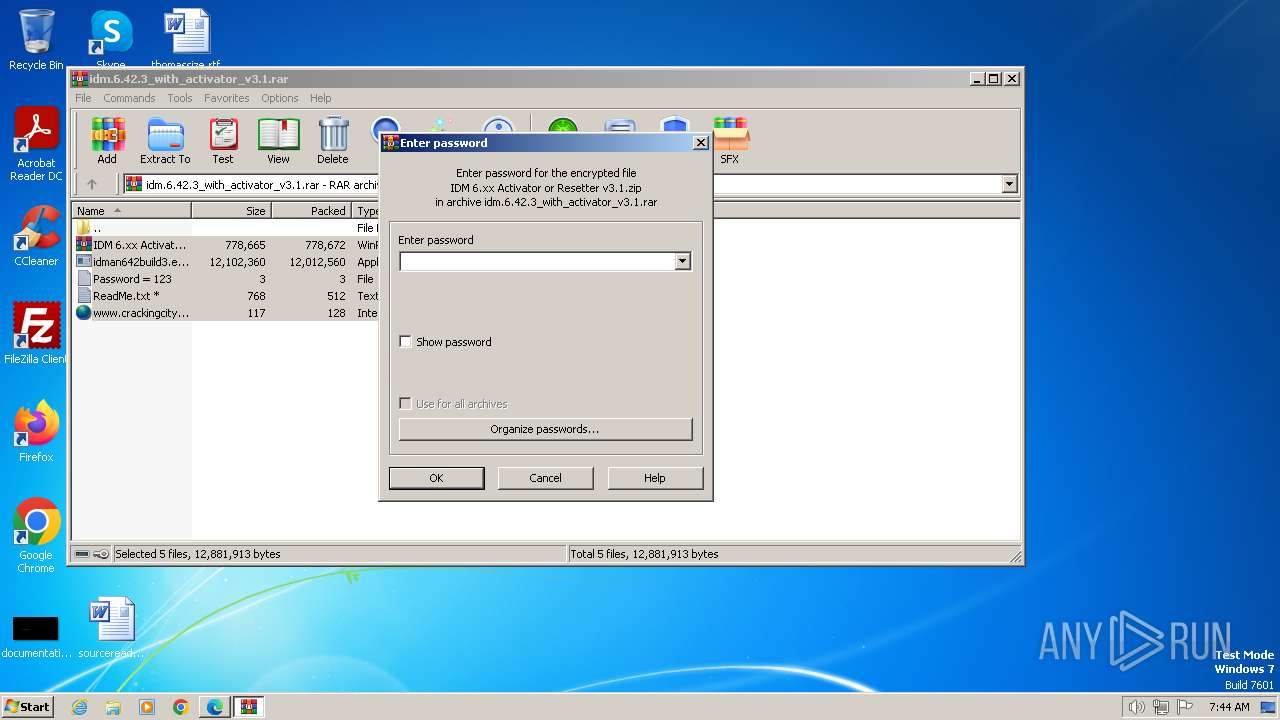
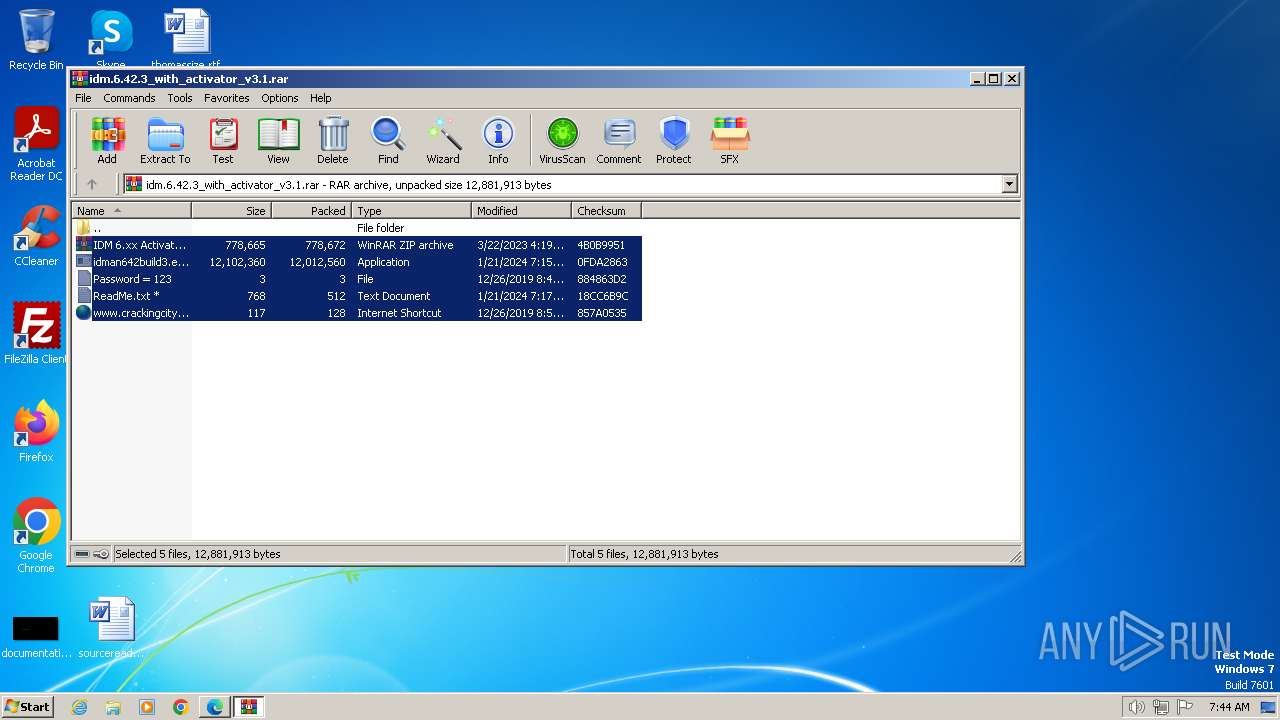
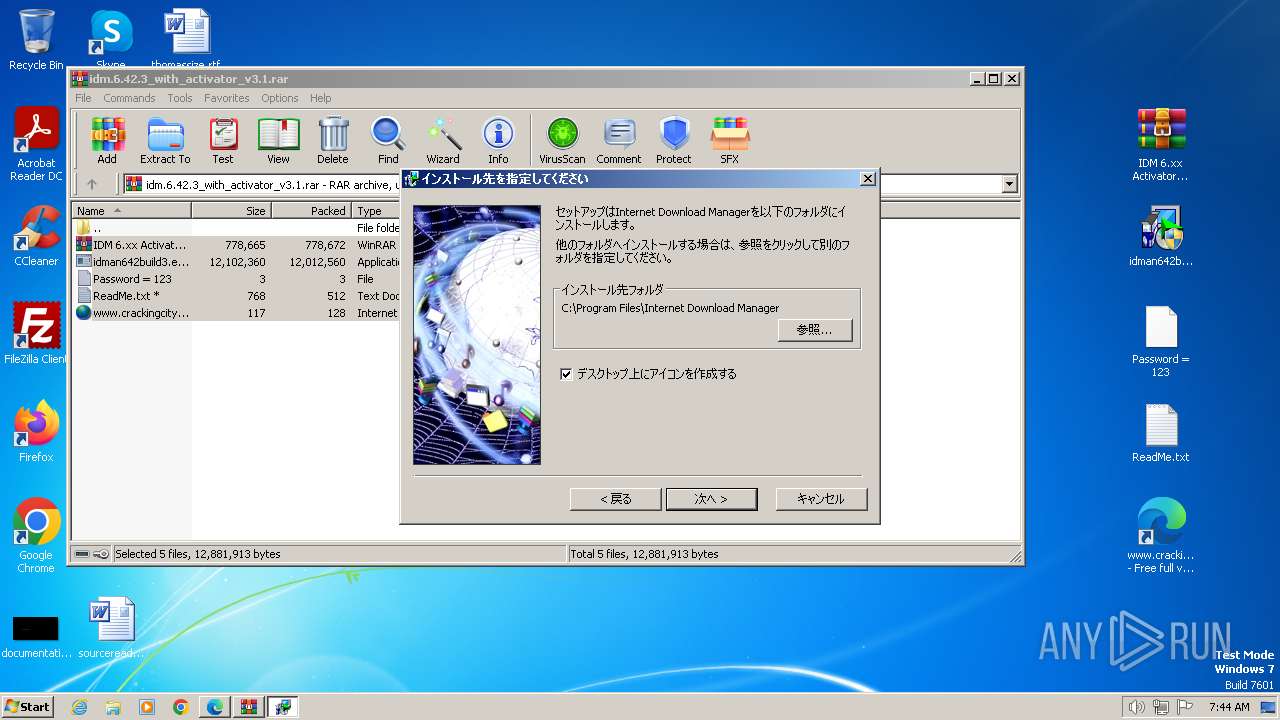
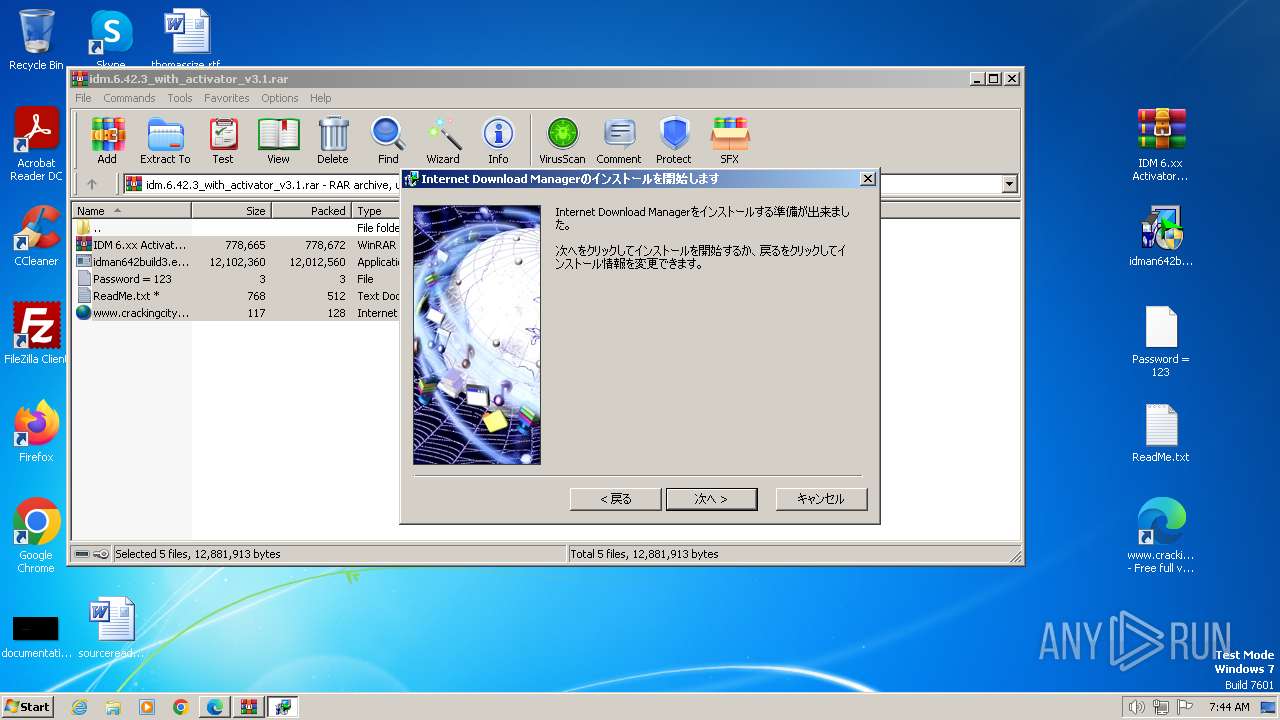
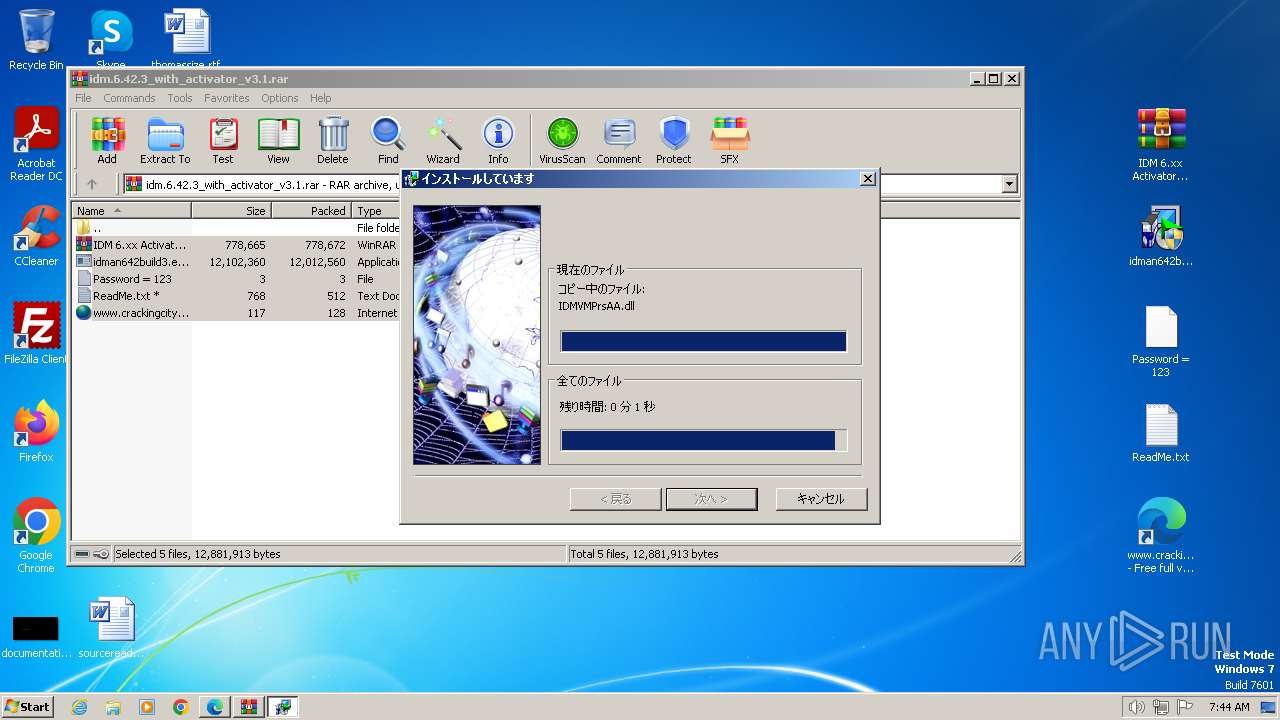
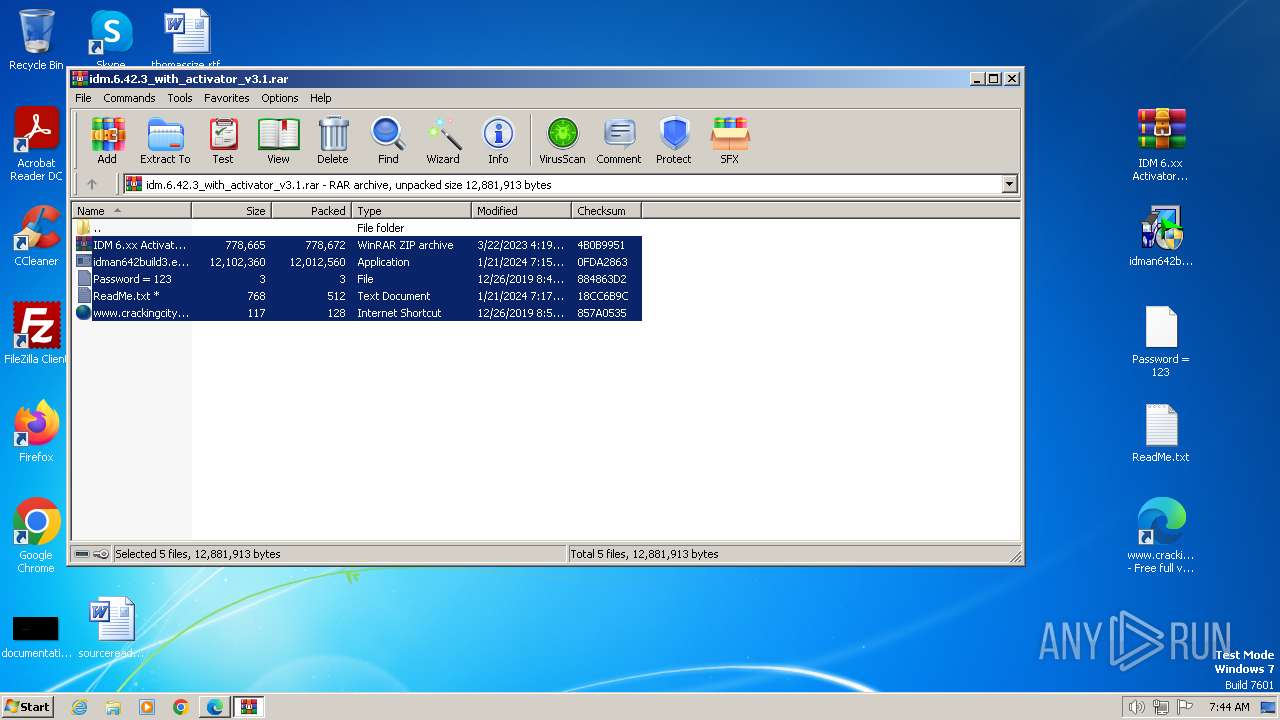
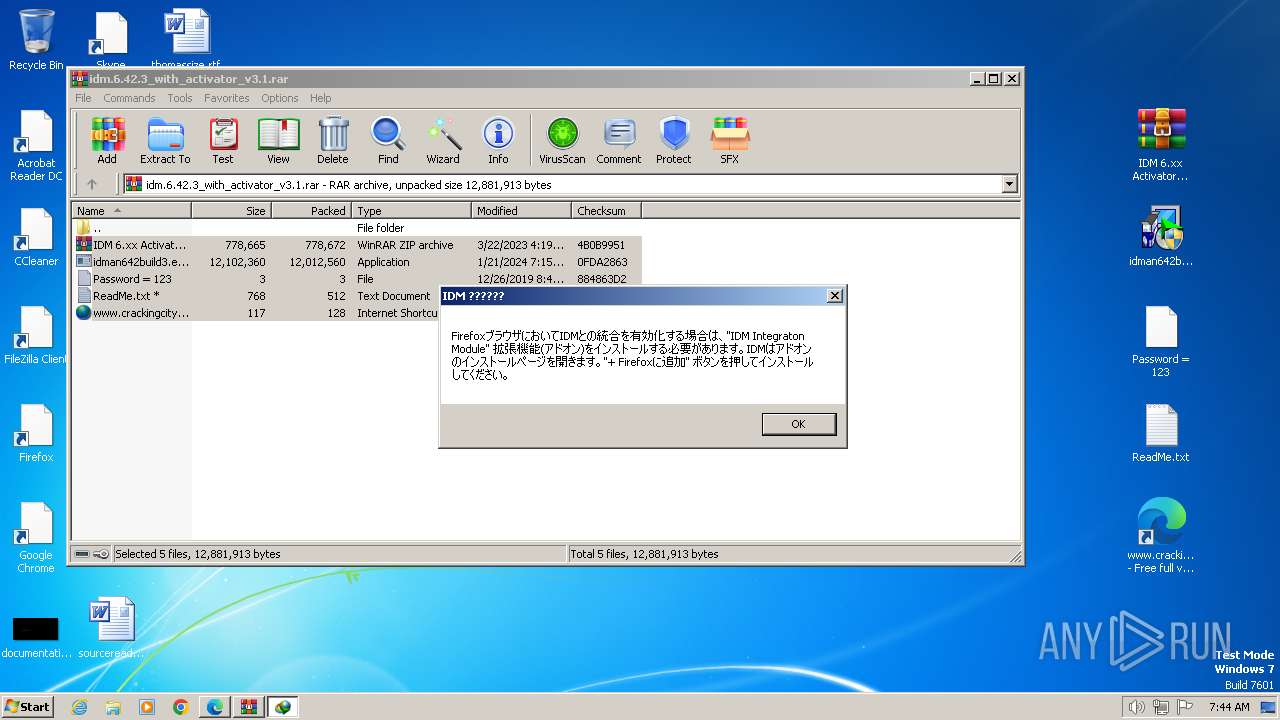
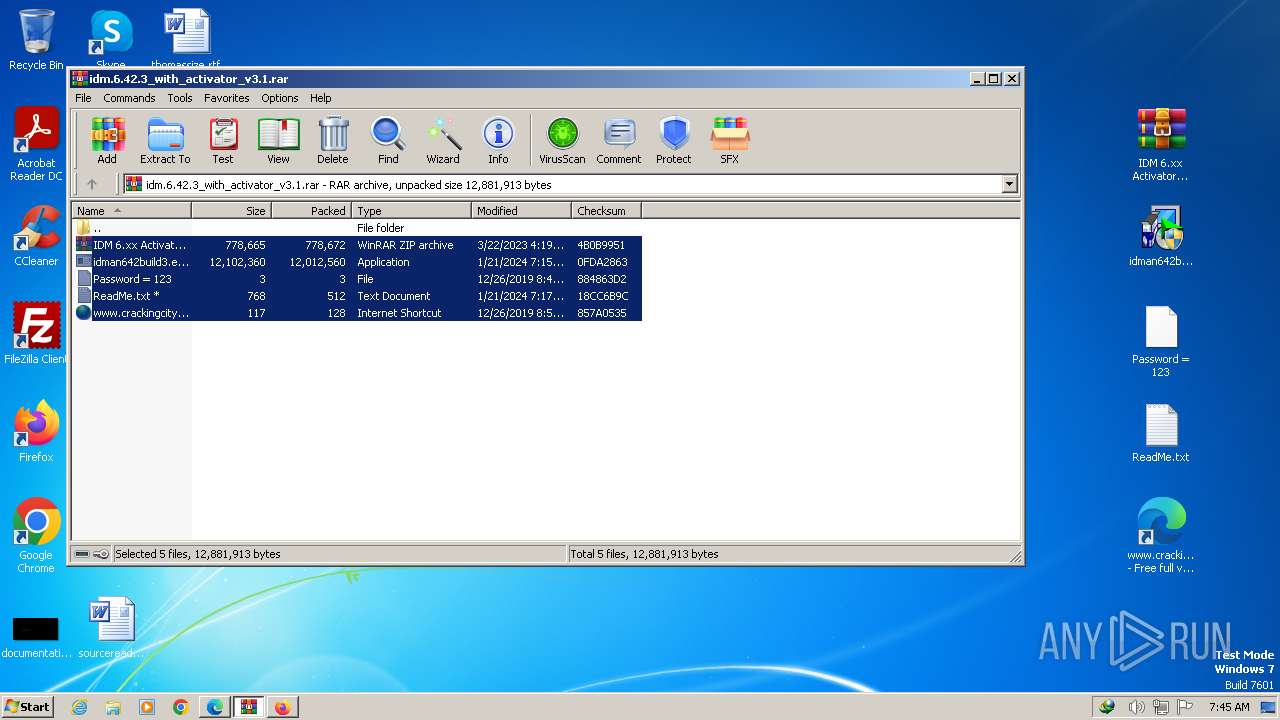
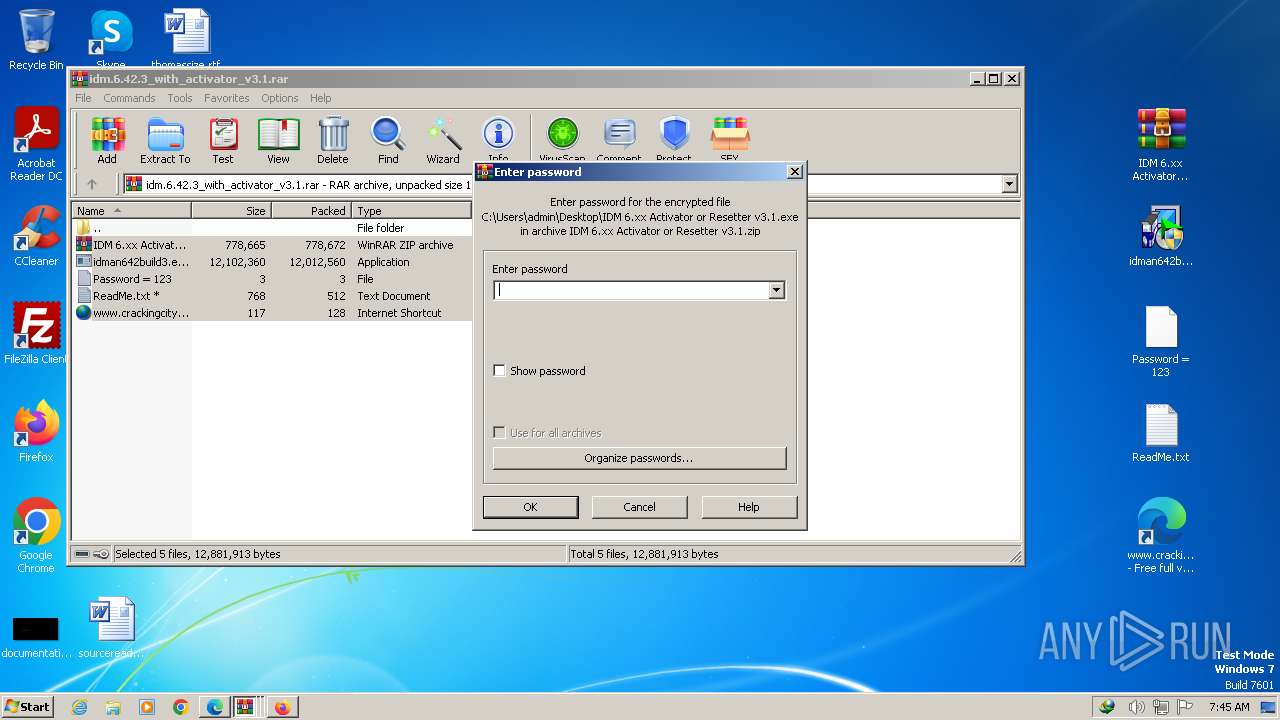
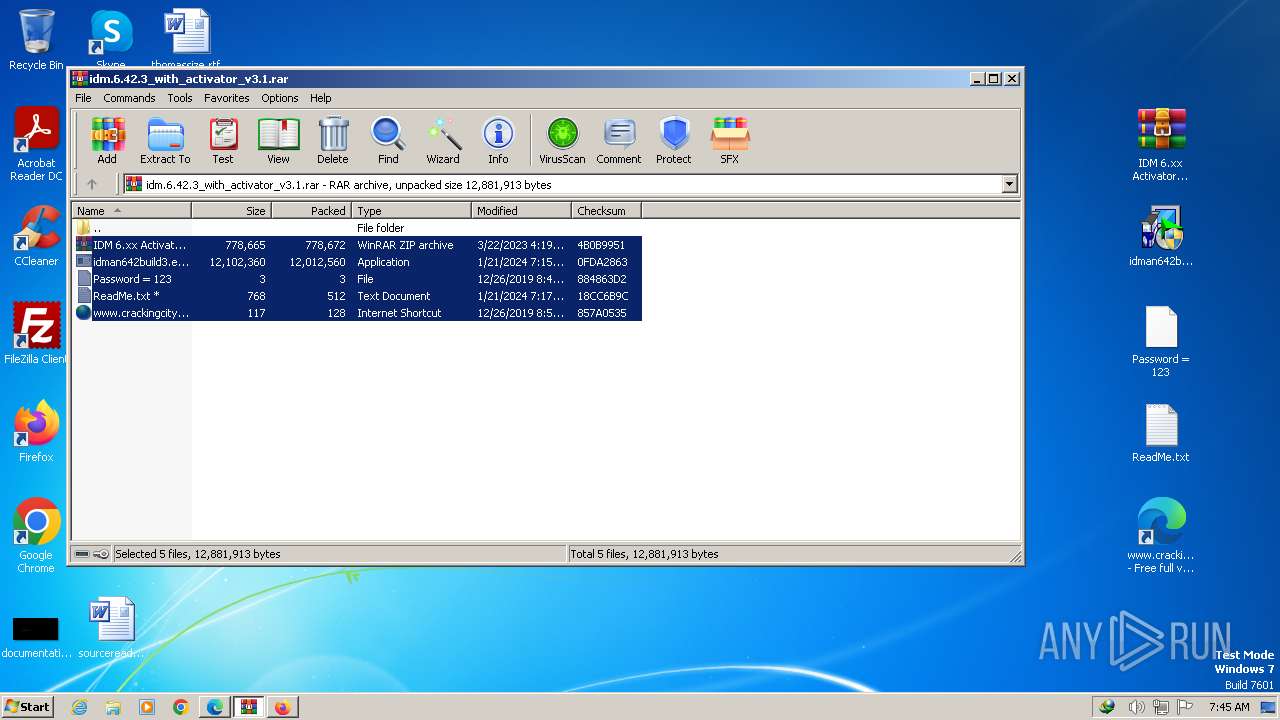
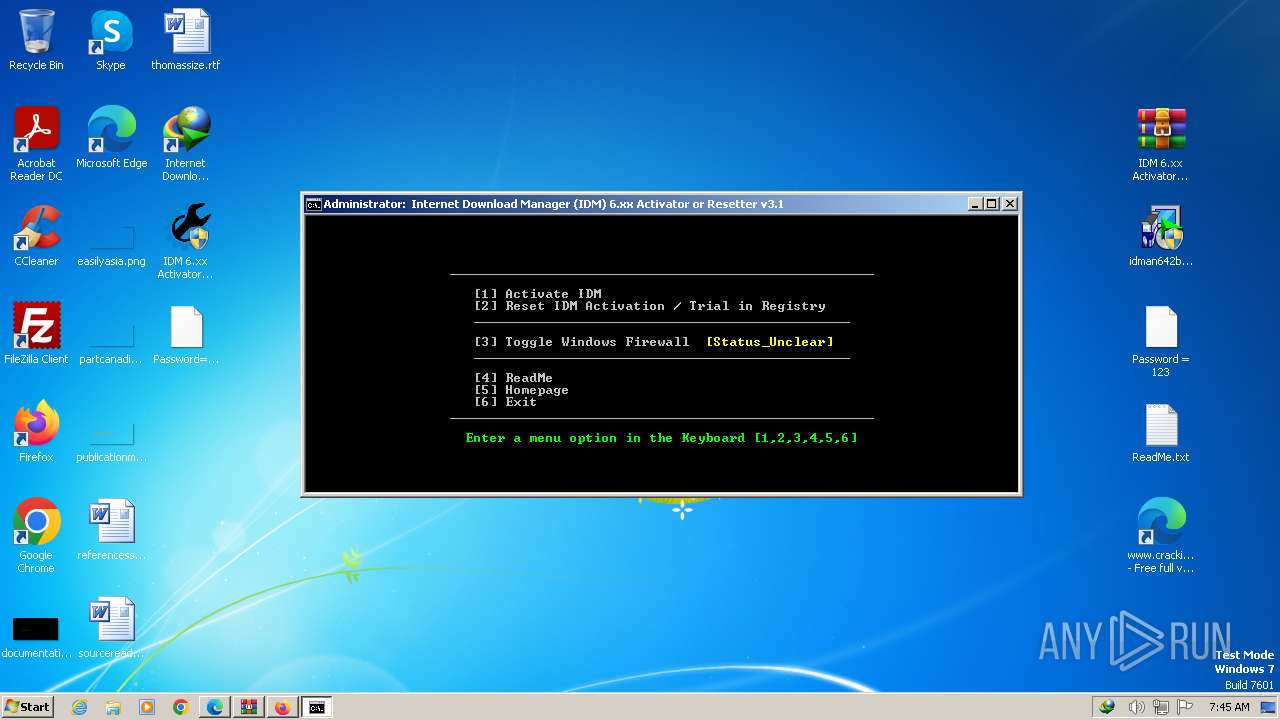
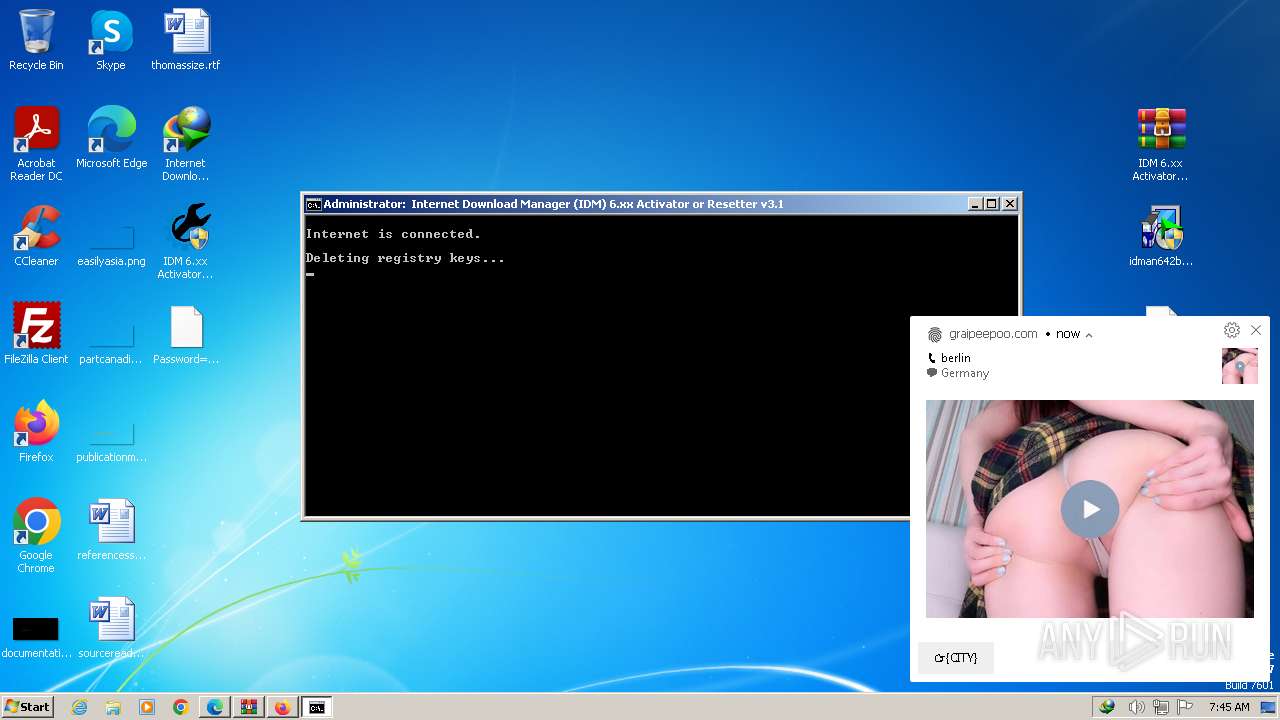
| URL: | https://www.crackingcity.com/idm-crack/ |
| Full analysis: | https://app.any.run/tasks/d9f880c8-8b29-457b-8fef-2d07190e916d |
| Verdict: | Malicious activity |
| Analysis date: | February 26, 2024, 07:42:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 5D91DA13F2DE9367F54F80D3D118E9AF |
| SHA1: | 4662EFF267E35446C40CD13D31ABBFA09801E272 |
| SHA256: | D00B8E831BD1D0303B23DA37F8CDB7BEA97B696F593F1DCEE29E152FD8CBBA48 |
| SSDEEP: | 3:N8DSLbMLF8TKtfl:2OLQ9 |
MALICIOUS
Starts NET.EXE for service management
- net.exe (PID: 3756)
- Uninstall.exe (PID: 908)
Creates a writable file in the system directory
- rundll32.exe (PID: 3168)
Changes the autorun value in the registry
- rundll32.exe (PID: 3168)
- IDMan.exe (PID: 2448)
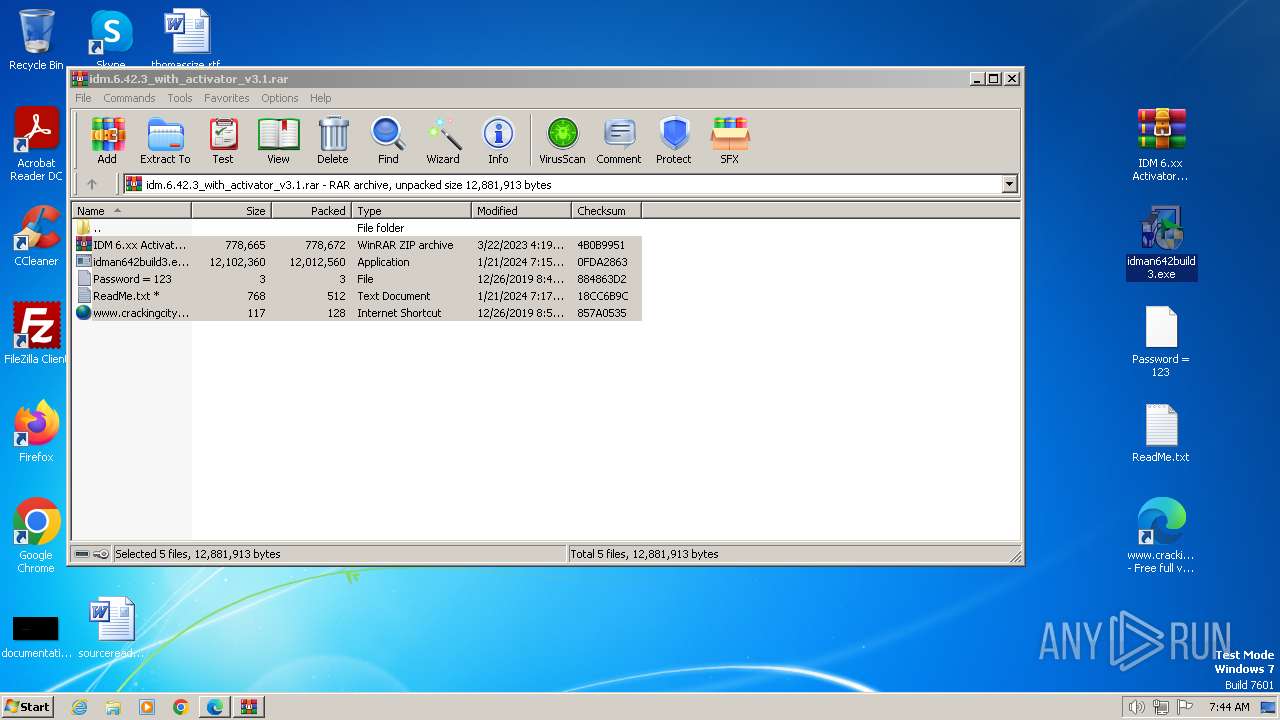
Drops the executable file immediately after the start
- IDMan.exe (PID: 2448)
- IDM 6.xx Activator or Resetter v3.1.exe (PID: 4580)
- 7za.exe (PID: 4696)
- 7za.exe (PID: 4728)
Starts CMD.EXE for commands execution
- msedge.exe (PID: 1384)
SUSPICIOUS
Creates a software uninstall entry
- IDM1.tmp (PID: 2548)
Starts application with an unusual extension
- idman642build3.exe (PID: 1056)
The process creates files with name similar to system file names
- IDM1.tmp (PID: 2548)
Creates/Modifies COM task schedule object
- IDM1.tmp (PID: 2548)
- IDMan.exe (PID: 2448)
- Uninstall.exe (PID: 908)
Reads the Internet Settings
- IDM1.tmp (PID: 2548)
- IDMan.exe (PID: 2448)
- Uninstall.exe (PID: 908)
- runonce.exe (PID: 2360)
- IDMan.exe (PID: 3748)
- IDM 6.xx Activator or Resetter v3.1.exe (PID: 4580)
Reads settings of System Certificates
- IDMan.exe (PID: 2448)
- IDMan.exe (PID: 3748)
Reads security settings of Internet Explorer
- IDM1.tmp (PID: 2548)
- IDMan.exe (PID: 2448)
- Uninstall.exe (PID: 908)
- IDMan.exe (PID: 3748)
- IDM 6.xx Activator or Resetter v3.1.exe (PID: 4580)
Checks Windows Trust Settings
- IDMan.exe (PID: 2448)
- IDMan.exe (PID: 3748)
Executable content was dropped or overwritten
- IDMan.exe (PID: 2448)
- rundll32.exe (PID: 3168)
- IDM 6.xx Activator or Resetter v3.1.exe (PID: 4580)
- 7za.exe (PID: 4696)
- 7za.exe (PID: 4728)
Uses RUNDLL32.EXE to load library
- Uninstall.exe (PID: 908)
Drops a system driver (possible attempt to evade defenses)
- rundll32.exe (PID: 3168)
Creates or modifies Windows services
- Uninstall.exe (PID: 908)
Drops 7-zip archiver for unpacking
- IDM 6.xx Activator or Resetter v3.1.exe (PID: 4580)
Executing commands from a ".bat" file
- IDM 6.xx Activator or Resetter v3.1.exe (PID: 4580)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 4612)
The executable file from the user directory is run by the CMD process
- 7za.exe (PID: 4648)
- 7za.exe (PID: 4672)
- 7za.exe (PID: 4696)
- 7za.exe (PID: 4728)
- AB2EF.exe (PID: 5048)
Starts CMD.EXE for commands execution
- IDM 6.xx Activator or Resetter v3.1.exe (PID: 4580)
- cmd.exe (PID: 4788)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 4908)
- cmd.exe (PID: 4788)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 4788)
Get information on the list of running processes
- cmd.exe (PID: 4788)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 4788)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4788)
Application launched itself
- cmd.exe (PID: 4788)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 4788)
INFO
Checks supported languages
- idman642build3.exe (PID: 1056)
- wmpnscfg.exe (PID: 2028)
- IDM1.tmp (PID: 2548)
- IDMan.exe (PID: 2448)
- idmBroker.exe (PID: 796)
- Uninstall.exe (PID: 908)
- MediumILStart.exe (PID: 3788)
- IDMan.exe (PID: 3748)
- IEMonitor.exe (PID: 2232)
- IDM 6.xx Activator or Resetter v3.1.exe (PID: 4580)
- 7za.exe (PID: 4648)
- 7za.exe (PID: 4672)
- 7za.exe (PID: 4696)
- AB2EF.exe (PID: 5048)
- 7za.exe (PID: 4728)
- mode.com (PID: 4964)
- IDMMsgHost.exe (PID: 1892)
- IDMMsgHost.exe (PID: 4508)
- IDMMsgHost.exe (PID: 5372)
- mode.com (PID: 5164)
Manual execution by a user
- idman642build3.exe (PID: 2424)
- idman642build3.exe (PID: 1056)
- wmpnscfg.exe (PID: 2028)
- firefox.exe (PID: 2492)
- WinRAR.exe (PID: 4388)
- IDM 6.xx Activator or Resetter v3.1.exe (PID: 4580)
- IDM 6.xx Activator or Resetter v3.1.exe (PID: 4480)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1336)
- WinRAR.exe (PID: 4388)
The process uses the downloaded file
- WinRAR.exe (PID: 1336)
- msedge.exe (PID: 3544)
Create files in a temporary directory
- idman642build3.exe (PID: 1056)
- IDM1.tmp (PID: 2548)
- IDMan.exe (PID: 2448)
- IDMan.exe (PID: 3748)
- IDM 6.xx Activator or Resetter v3.1.exe (PID: 4580)
- 7za.exe (PID: 4648)
- 7za.exe (PID: 4672)
- 7za.exe (PID: 4696)
- 7za.exe (PID: 4728)
Application launched itself
- msedge.exe (PID: 1384)
- firefox.exe (PID: 2492)
- firefox.exe (PID: 2296)
Reads the computer name
- wmpnscfg.exe (PID: 2028)
- IDM1.tmp (PID: 2548)
- IDMan.exe (PID: 2448)
- Uninstall.exe (PID: 908)
- MediumILStart.exe (PID: 3788)
- IEMonitor.exe (PID: 2232)
- IDMan.exe (PID: 3748)
- IDM 6.xx Activator or Resetter v3.1.exe (PID: 4580)
- 7za.exe (PID: 4648)
- 7za.exe (PID: 4672)
- 7za.exe (PID: 4696)
- 7za.exe (PID: 4728)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1336)
- rundll32.exe (PID: 3168)
- WinRAR.exe (PID: 4388)
Creates files in the program directory
- IDM1.tmp (PID: 2548)
- IDMan.exe (PID: 2448)
Reads the machine GUID from the registry
- IDM1.tmp (PID: 2548)
- IDMan.exe (PID: 2448)
- MediumILStart.exe (PID: 3788)
- IDMan.exe (PID: 3748)
Creates files or folders in the user directory
- IDM1.tmp (PID: 2548)
- IDMan.exe (PID: 2448)
Reads the software policy settings
- IDMan.exe (PID: 2448)
- IDMan.exe (PID: 3748)
Checks proxy server information
- IDMan.exe (PID: 2448)
Creates files in the driver directory
- rundll32.exe (PID: 3168)
Reads the time zone
- runonce.exe (PID: 2360)
Reads security settings of Internet Explorer
- runonce.exe (PID: 2360)
Checks operating system version
- cmd.exe (PID: 4788)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
10 097
Monitored processes
10 040
Malicious processes
9
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 268 | findstr /r "{.*-.*-.*-.*-.*}" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 268 | reg query HKCU\Software\Classes\CLSID\{CAFEEFAC-0016-0000-0124-ABCDEFFEDCBB} | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 268 | C:\Windows\system32\cmd.exe /S /D /c" echo {CAFEEFAC-0016-0000-0206-ABCDEFFEDCBC}" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) | |||||||||||||||
| 268 | findstr /i "LocalServer32 InProcServer32 InProcHandler32" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | |||||||||||||||
| 268 | findstr /r "{.*-.*-.*-.*-.*}" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | |||||||||||||||
| 268 | C:\Windows\system32\cmd.exe /S /D /c" echo {CAFEEFAC-0017-0000-0113-ABCDEFFEDCBA}" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) | |||||||||||||||
| 268 | findstr /r "{.*-.*-.*-.*-.*}" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | |||||||||||||||
| 268 | findstr /i "LocalServer32 InProcServer32 InProcHandler32" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | |||||||||||||||
| 268 | findstr /i "LocalServer32 InProcServer32 InProcHandler32" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | |||||||||||||||
| 268 | reg query HKCU\Software\Classes\CLSID\{CAFEEFAC-0017-0000-0260-ABCDEFFEDCBB} | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | |||||||||||||||
Total events
170 548
Read events
169 731
Write events
702
Delete events
115
Modification events
| (PID) Process: | (1384) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1384) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1384) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (1384) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (1384) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1384) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\EdgeUpdate\ClientState\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (1384) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (1384) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1302019708-1500728564-335382590-1000 |
Value: 7D6C9754DA702F00 | |||
| (PID) Process: | (1384) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\FirstNotDefault |
| Operation: | delete value | Name: | S-1-5-21-1302019708-1500728564-335382590-1000 |
Value: | |||
| (PID) Process: | (1384) msedge.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Edge |
| Operation: | write | Name: | UsageStatsInSample |
Value: 1 | |||
Executable files
27
Suspicious files
241
Text files
189
Unknown types
213
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1384 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF17f702.TMP | — | |
MD5:— | SHA256:— | |||
| 1384 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1384 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF17f721.TMP | — | |
MD5:— | SHA256:— | |||
| 1384 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1384 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF17f731.TMP | — | |
MD5:— | SHA256:— | |||
| 1384 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF17f78f.TMP | — | |
MD5:— | SHA256:— | |||
| 1384 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1384 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgeCoupons\coupons_data.db\LOG.old | text | |
MD5:B1E05B031BC39D74E7AC1CA69AC72F82 | SHA256:899DE7900989F710A925E38FA5AE4EA2C3B0EF47A1FEEFBF9EB57C21FA513A8E | |||
| 1384 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:72265FBF816F9AAE473C0CEB421DE724 | SHA256:C549BD4A176A3744A5D91391D311E28F0503BB69213E38835A1CB213038D938C | |||
| 1384 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Local Storage\leveldb\LOG.old~RF17f82b.TMP | text | |
MD5:0CA877707F6ED6C4B35B287D48118FFF | SHA256:11770765695DAB0F178A31040772C6298956C31417AE3E9BD4641162F79A9339 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
26
TCP/UDP connections
217
DNS requests
344
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2296 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | text | 8 b | unknown |
2448 | IDMan.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?3b0b32ea15497bc5 | unknown | compressed | 65.2 Kb | unknown |
2296 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | text | 90 b | unknown |
2296 | firefox.exe | POST | 200 | 142.250.185.131:80 | http://ocsp.pki.goog/gts1c3 | unknown | binary | 472 b | unknown |
2296 | firefox.exe | POST | 200 | 95.101.54.121:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
2296 | firefox.exe | POST | 200 | 95.101.54.121:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
2296 | firefox.exe | POST | 200 | 95.101.54.121:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
2296 | firefox.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | binary | 471 b | unknown |
2296 | firefox.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | binary | 471 b | unknown |
2296 | firefox.exe | POST | 200 | 95.101.54.121:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1492 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
1384 | msedge.exe | 239.255.255.250:1900 | — | — | — | unknown |
1492 | msedge.exe | 188.114.97.3:443 | www.crackingcity.com | CLOUDFLARENET | NL | unknown |
1492 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1492 | msedge.exe | 142.250.185.163:443 | fonts.gstatic.com | GOOGLE | US | whitelisted |
1492 | msedge.exe | 192.0.77.2:443 | i0.wp.com | — | — | unknown |
1492 | msedge.exe | 142.250.185.106:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.crackingcity.com |
| unknown |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
ajax.googleapis.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
c0.wp.com |
| whitelisted |
i0.wp.com |
| whitelisted |
stats.wp.com |
| whitelisted |
secure.gravatar.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1492 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Global content delivery network (unpkg .com) |