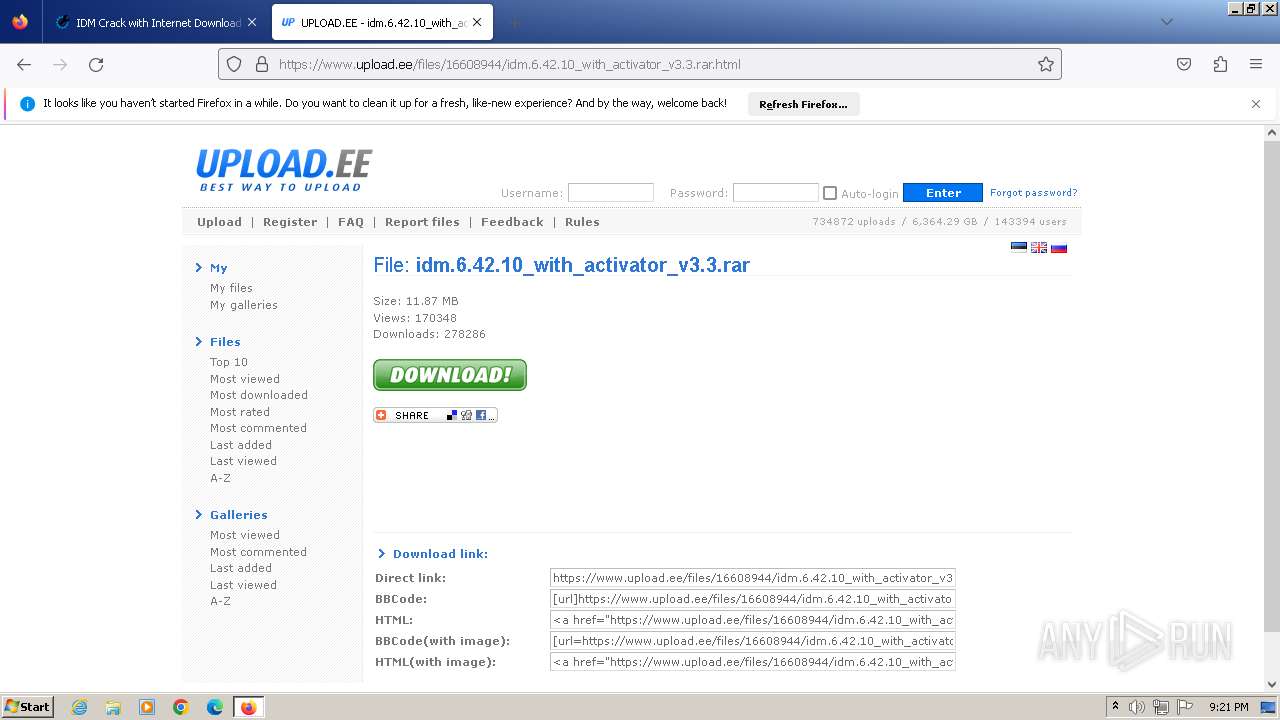
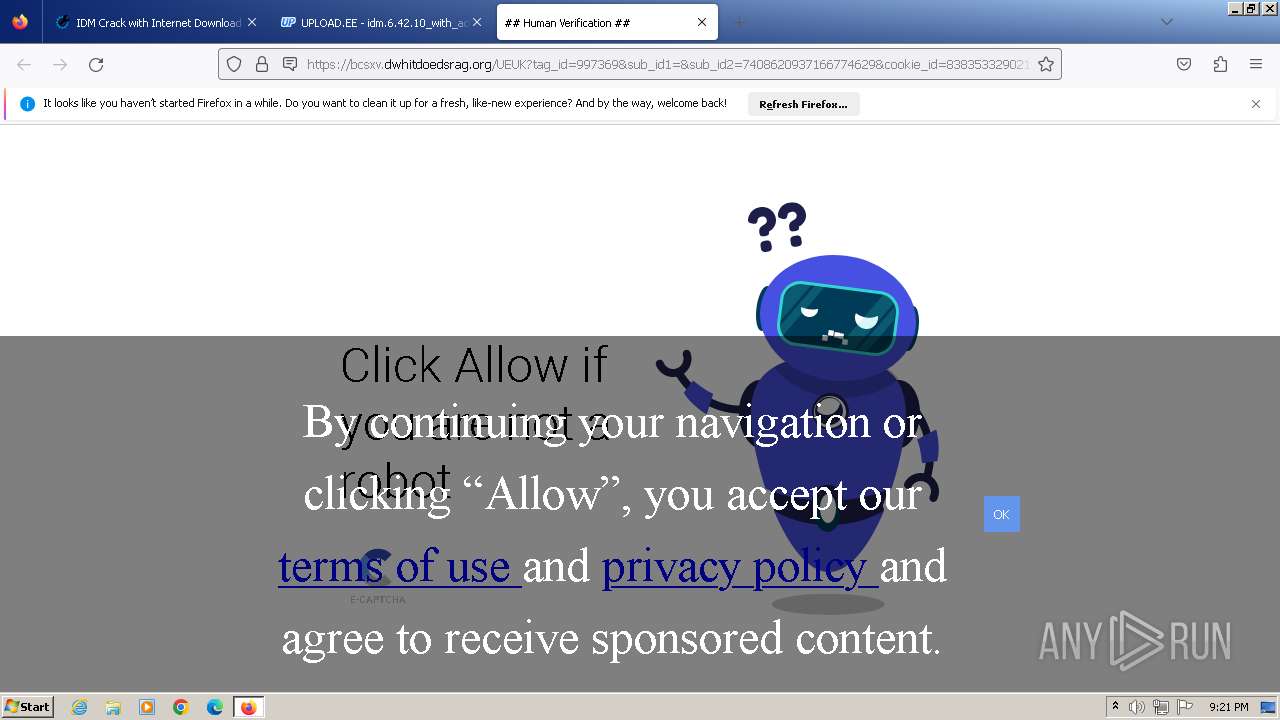
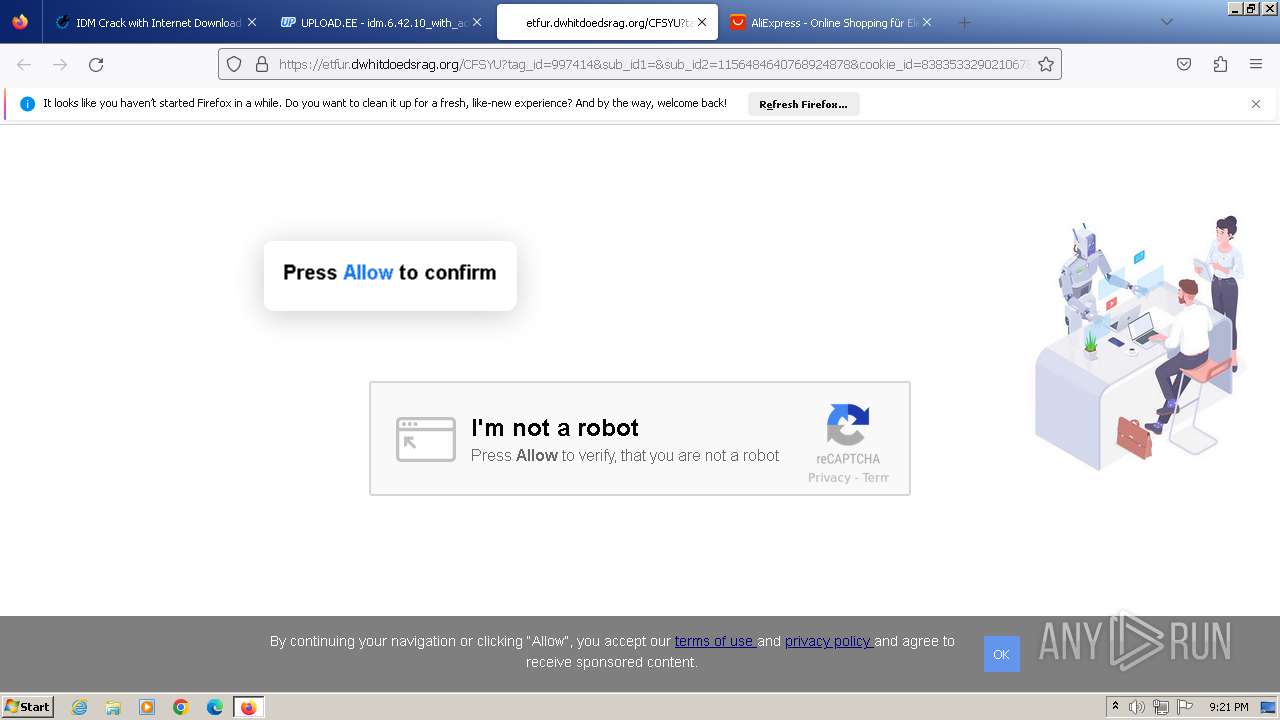
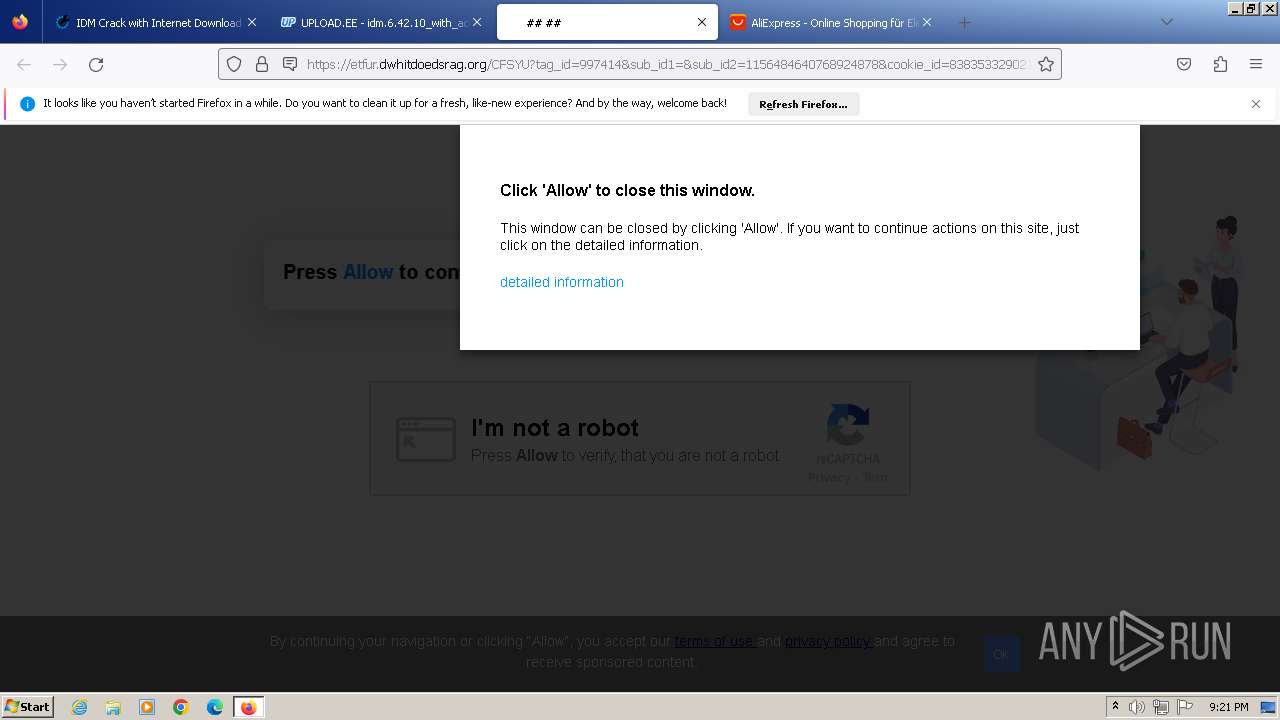
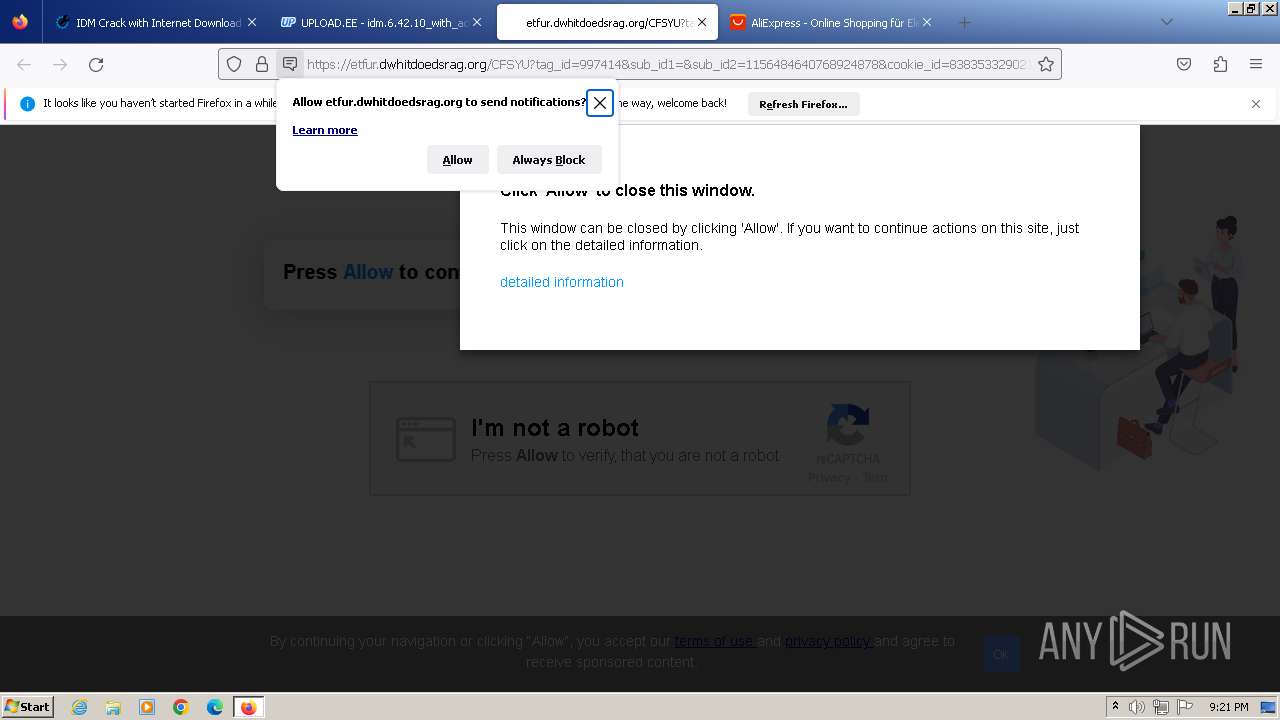
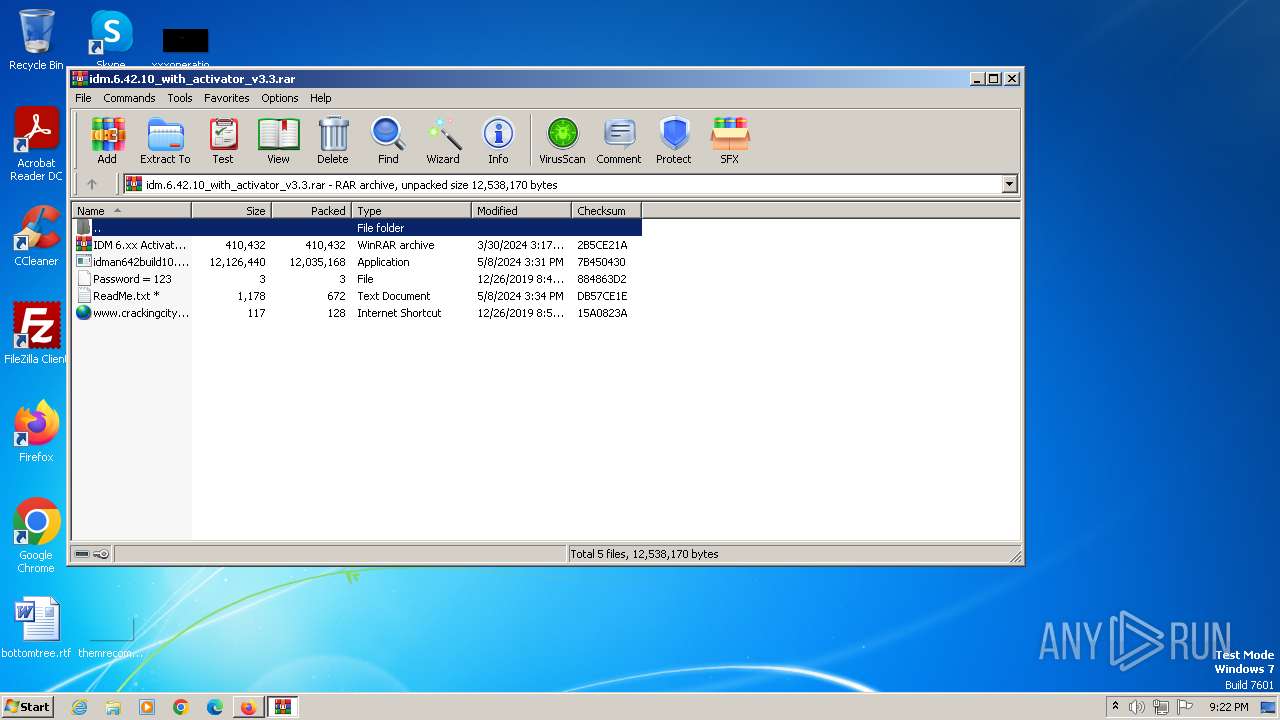
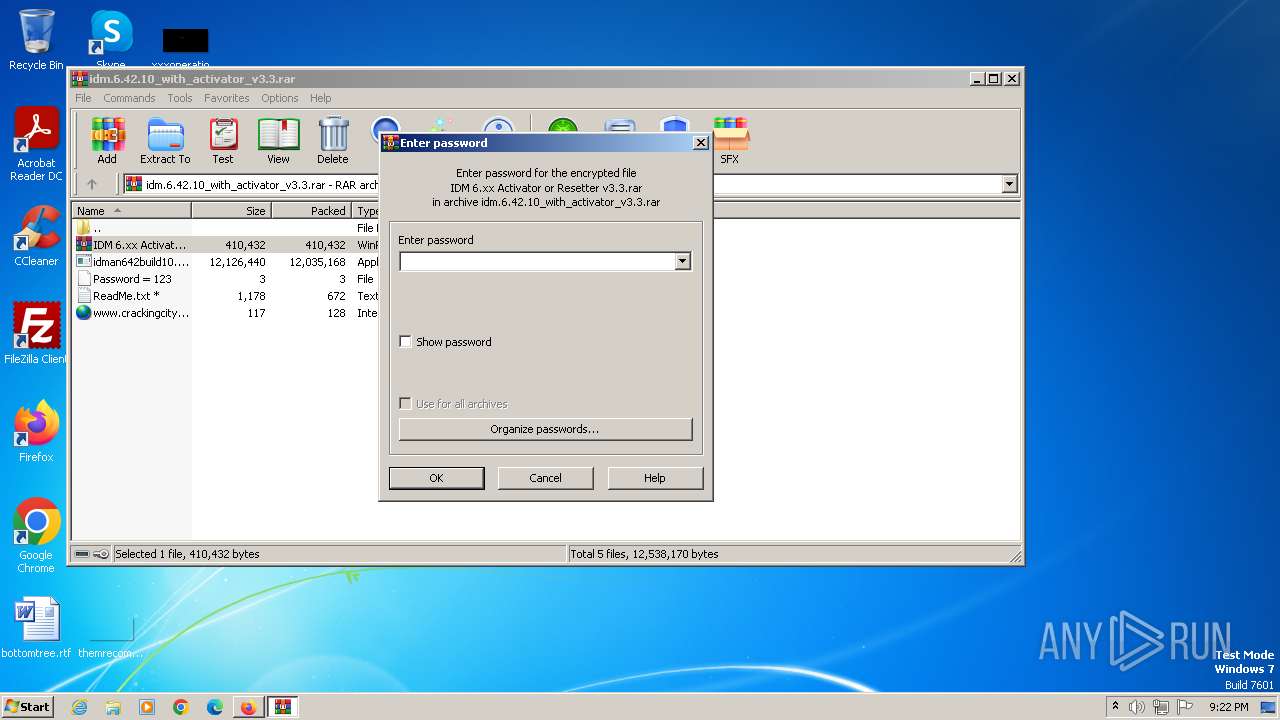
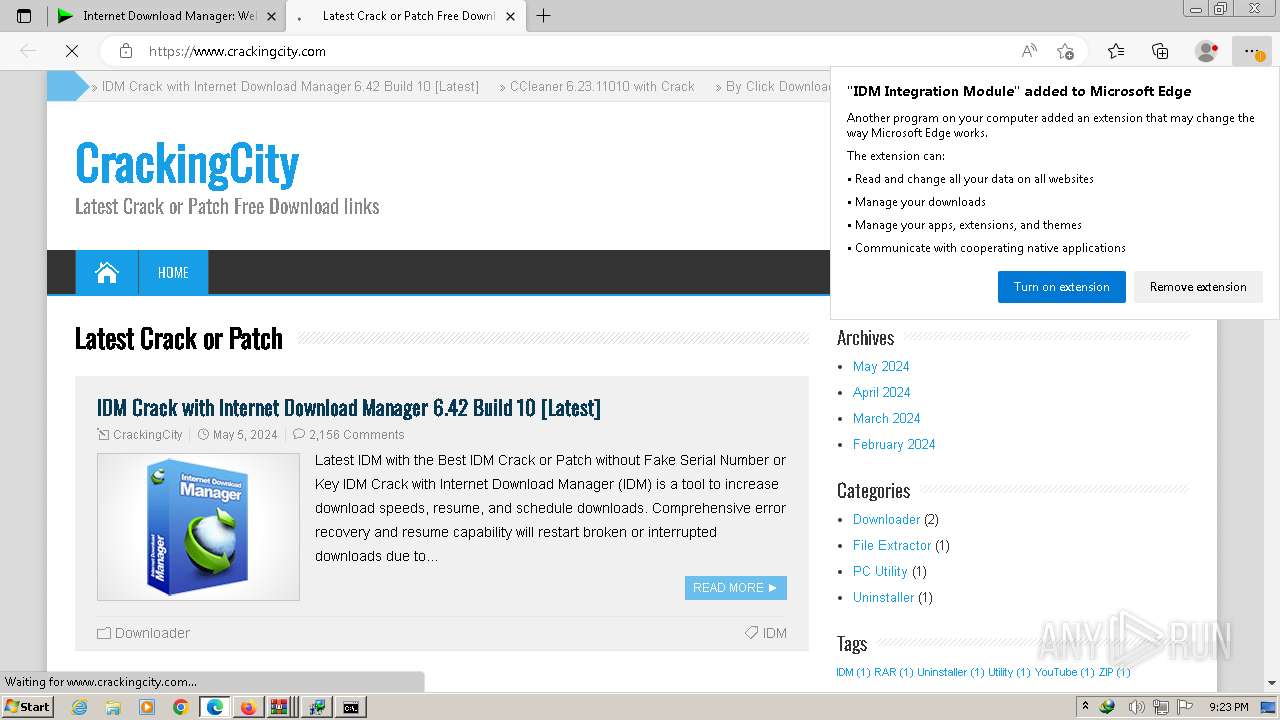
| URL: | https://www.crackingcity.com/idm-crack/ |
| Full analysis: | https://app.any.run/tasks/a8de5420-a28e-46eb-8f54-2b8360a27b24 |
| Verdict: | Malicious activity |
| Analysis date: | May 31, 2024, 20:20:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 5D91DA13F2DE9367F54F80D3D118E9AF |
| SHA1: | 4662EFF267E35446C40CD13D31ABBFA09801E272 |
| SHA256: | D00B8E831BD1D0303B23DA37F8CDB7BEA97B696F593F1DCEE29E152FD8CBBA48 |
| SSDEEP: | 3:N8DSLbMLF8TKtfl:2OLQ9 |
MALICIOUS
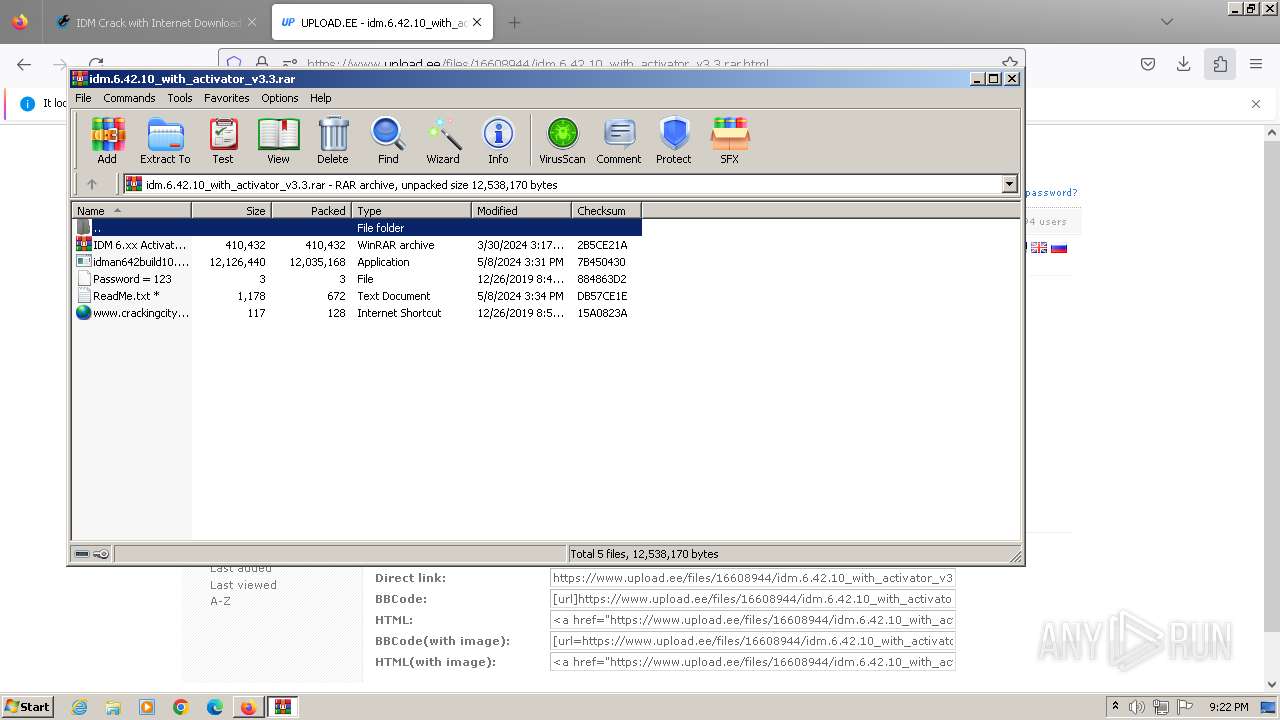
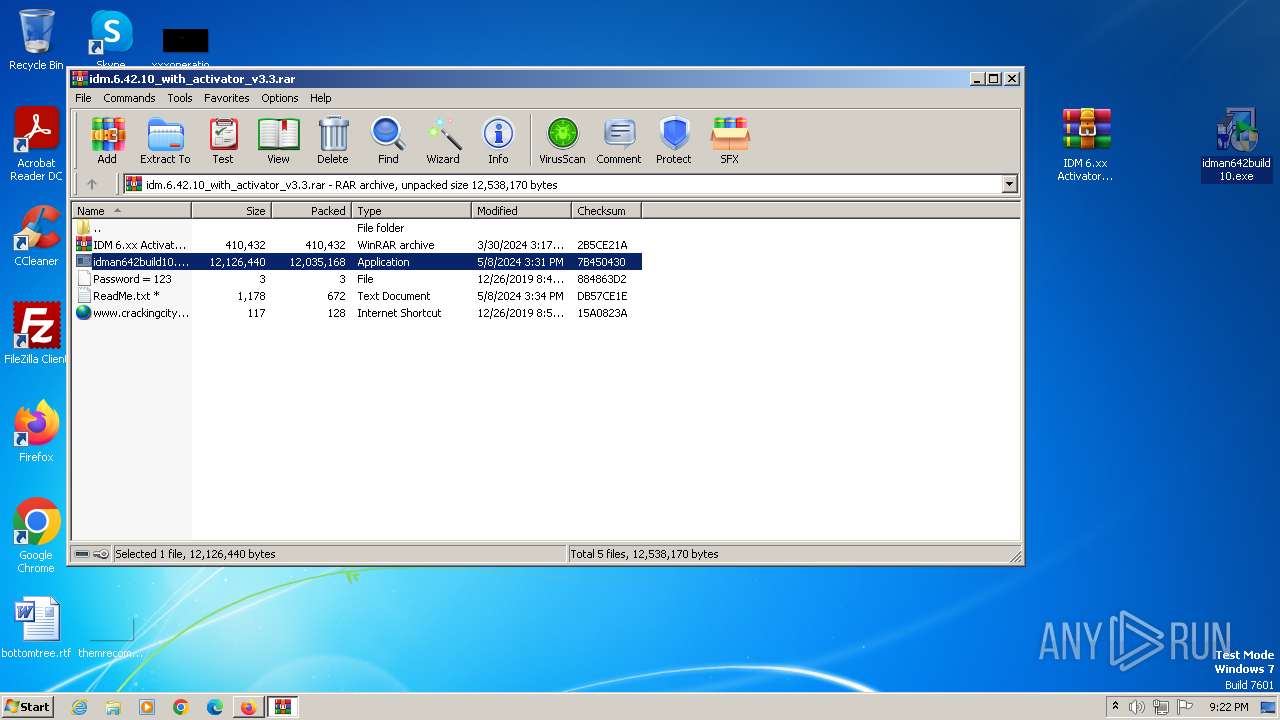
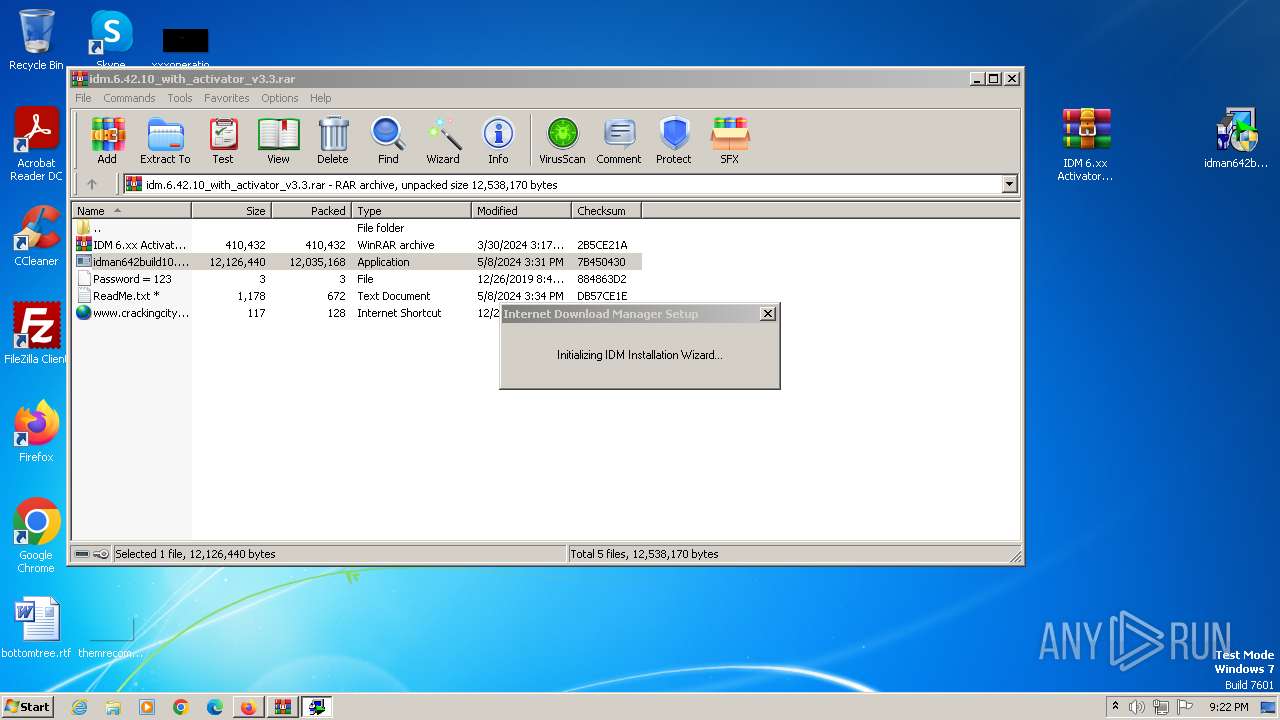
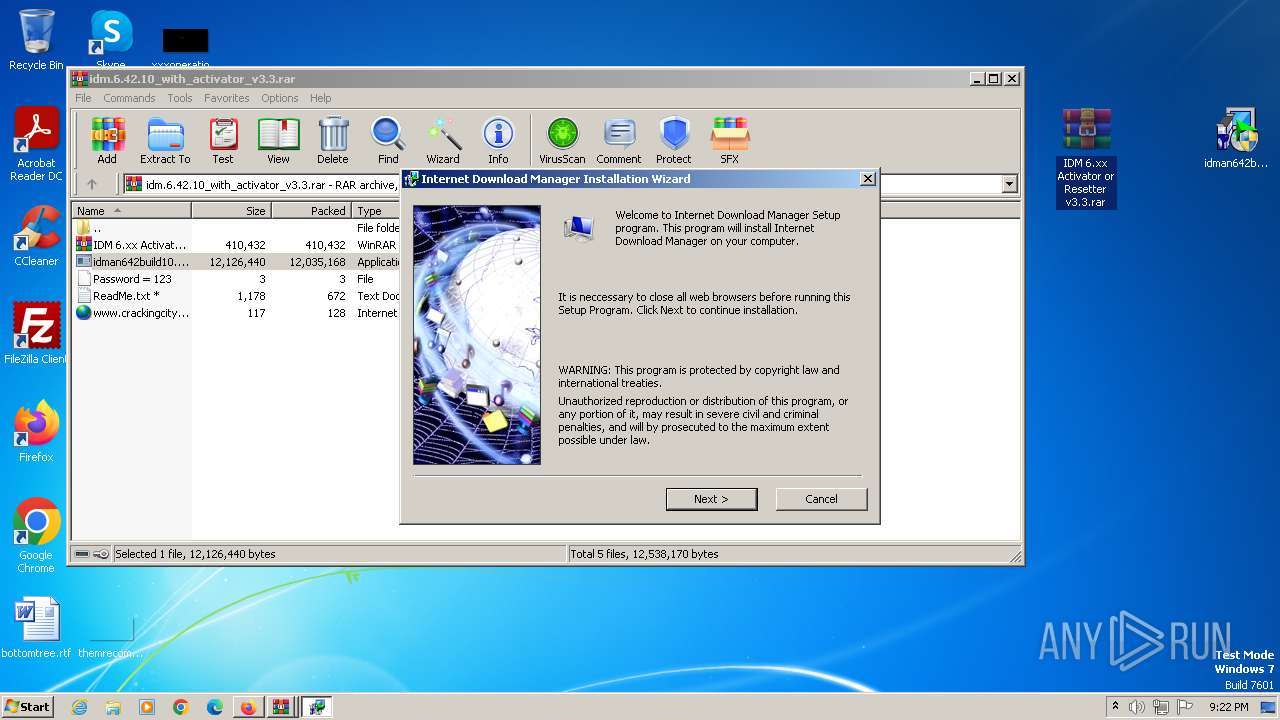
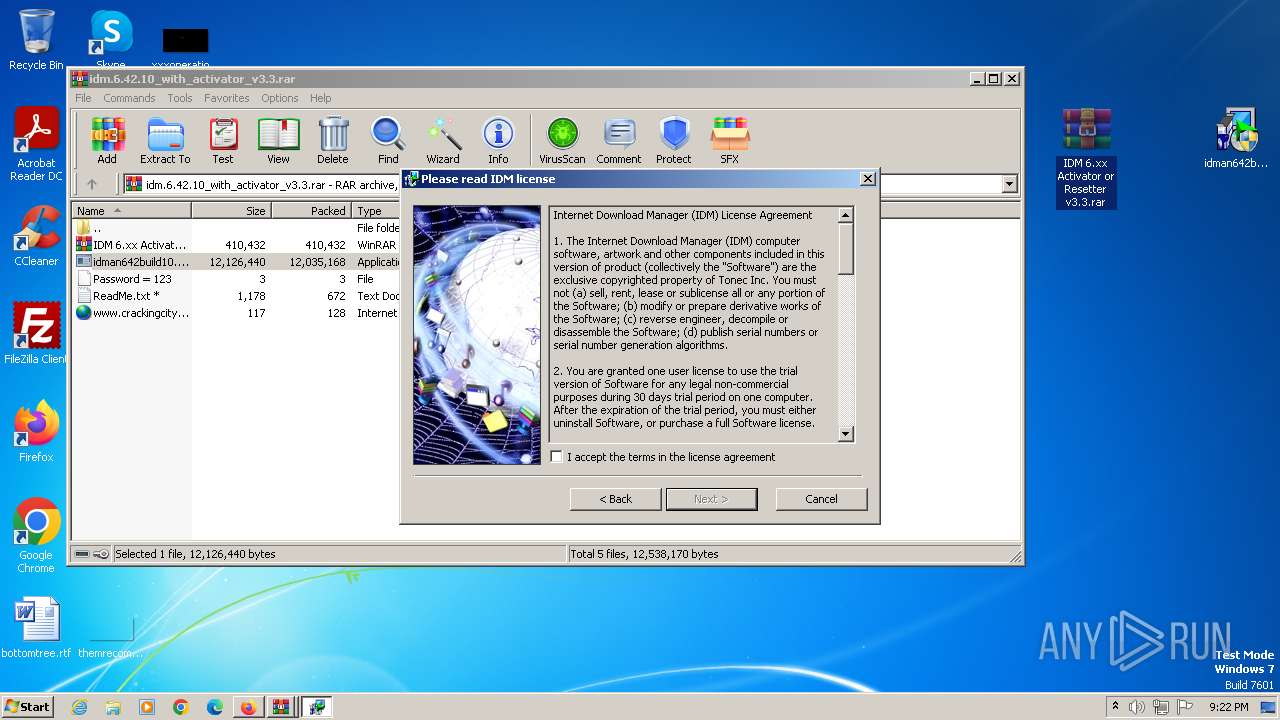
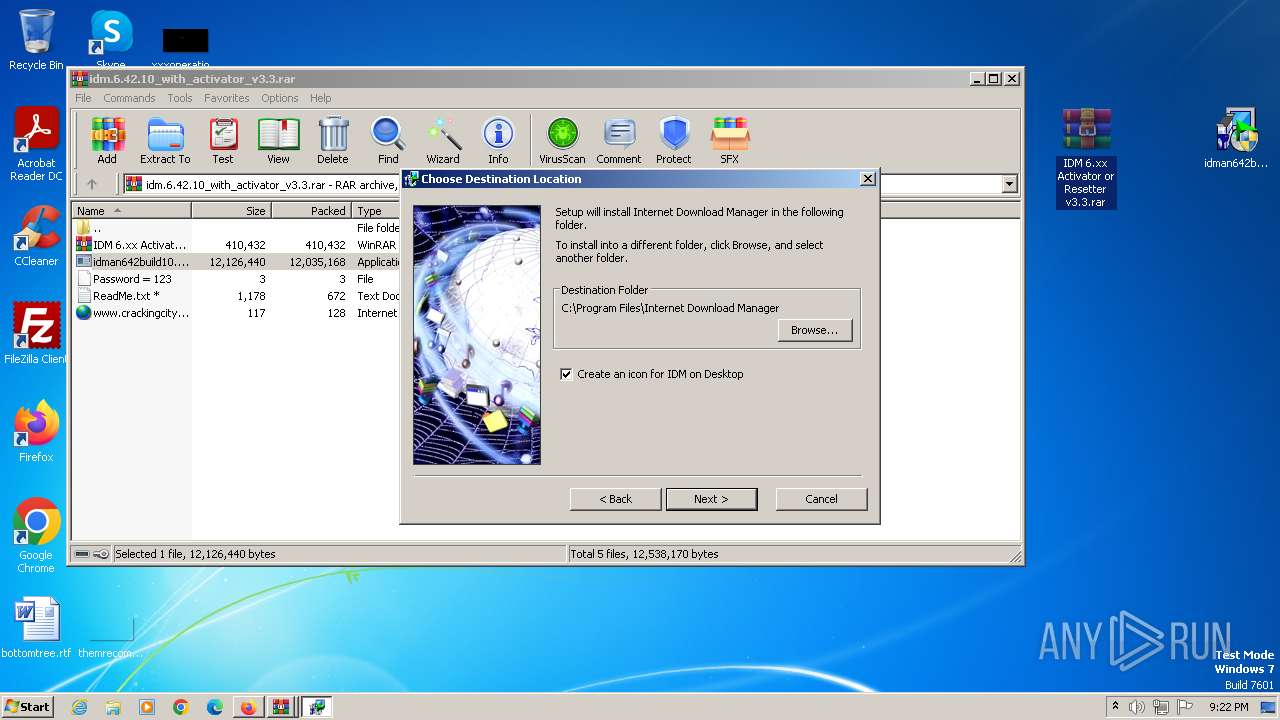
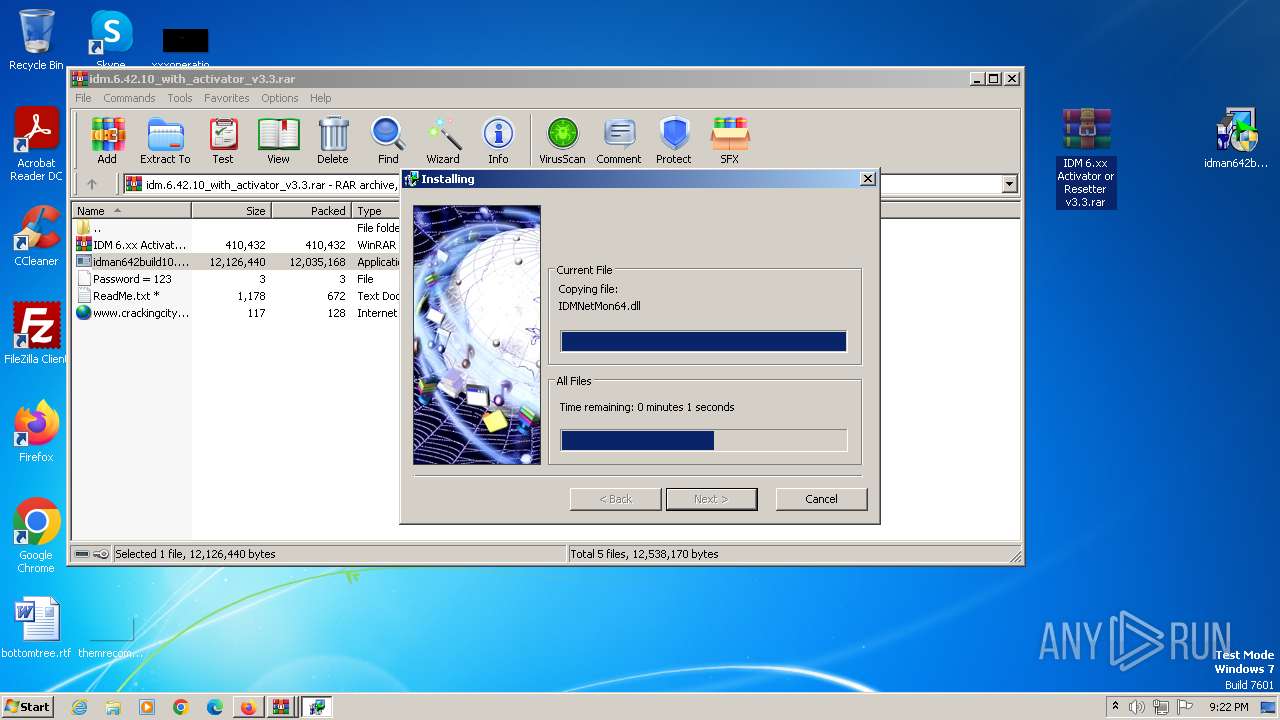
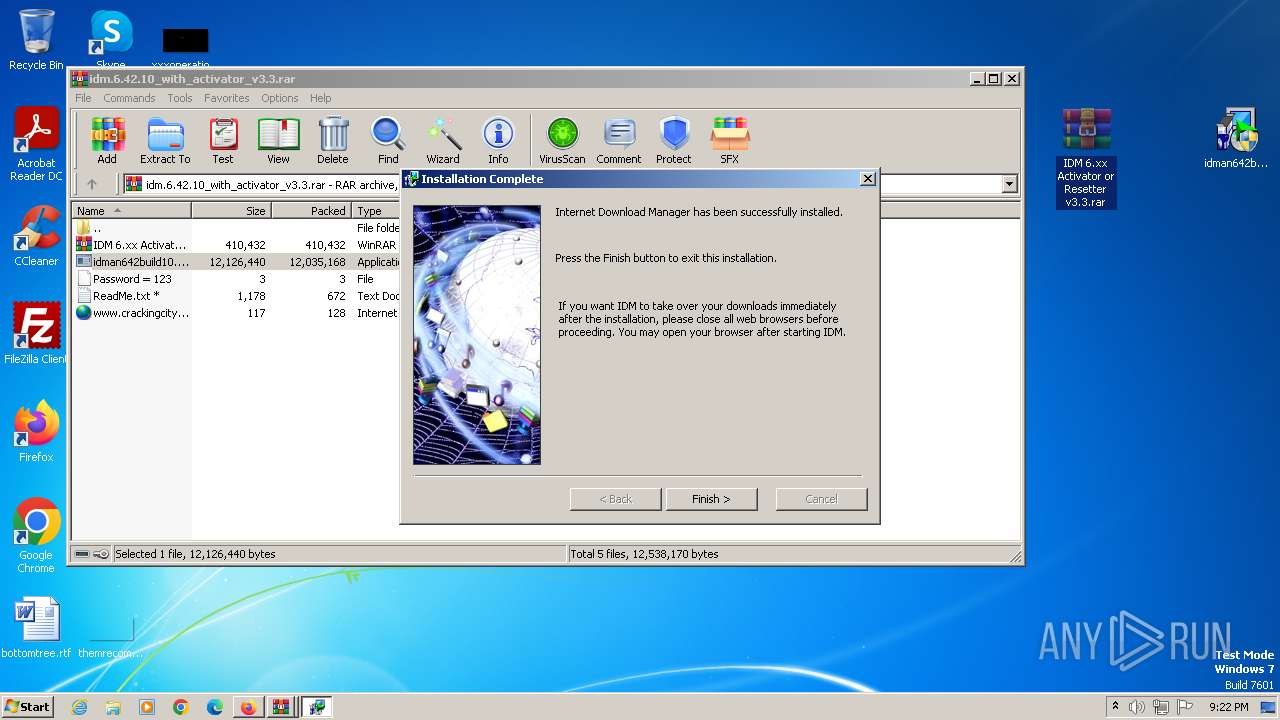
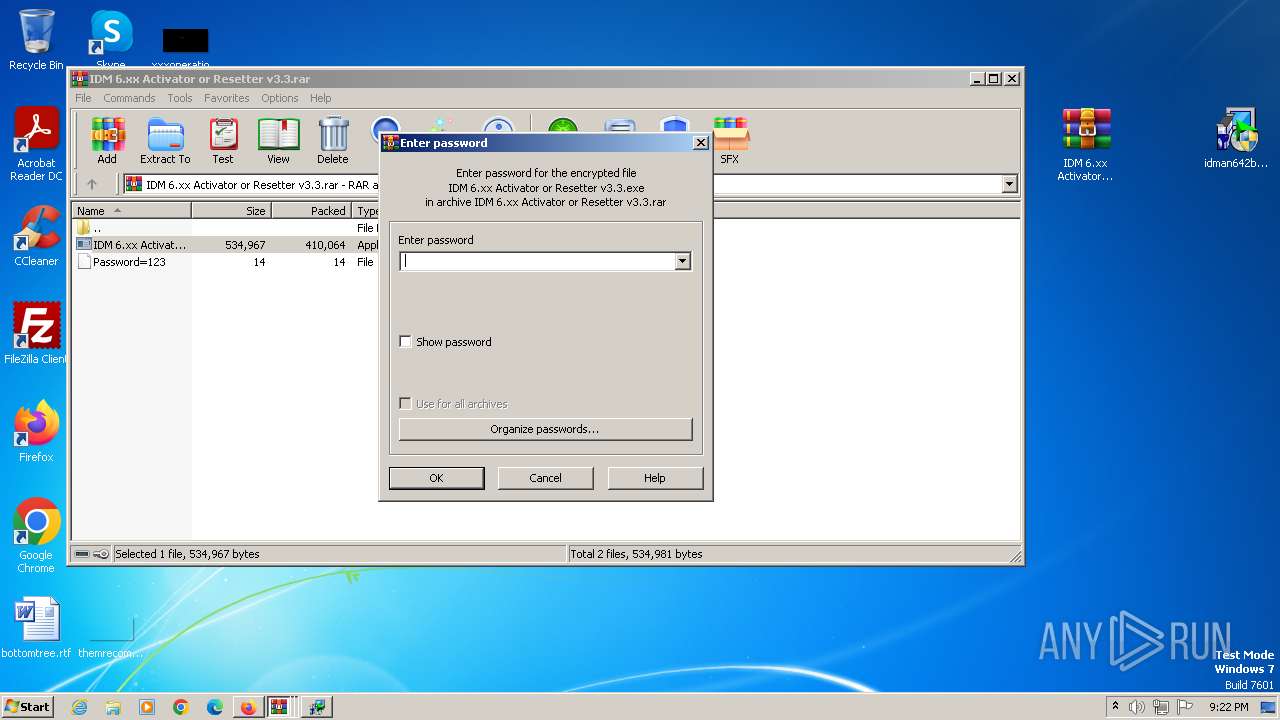
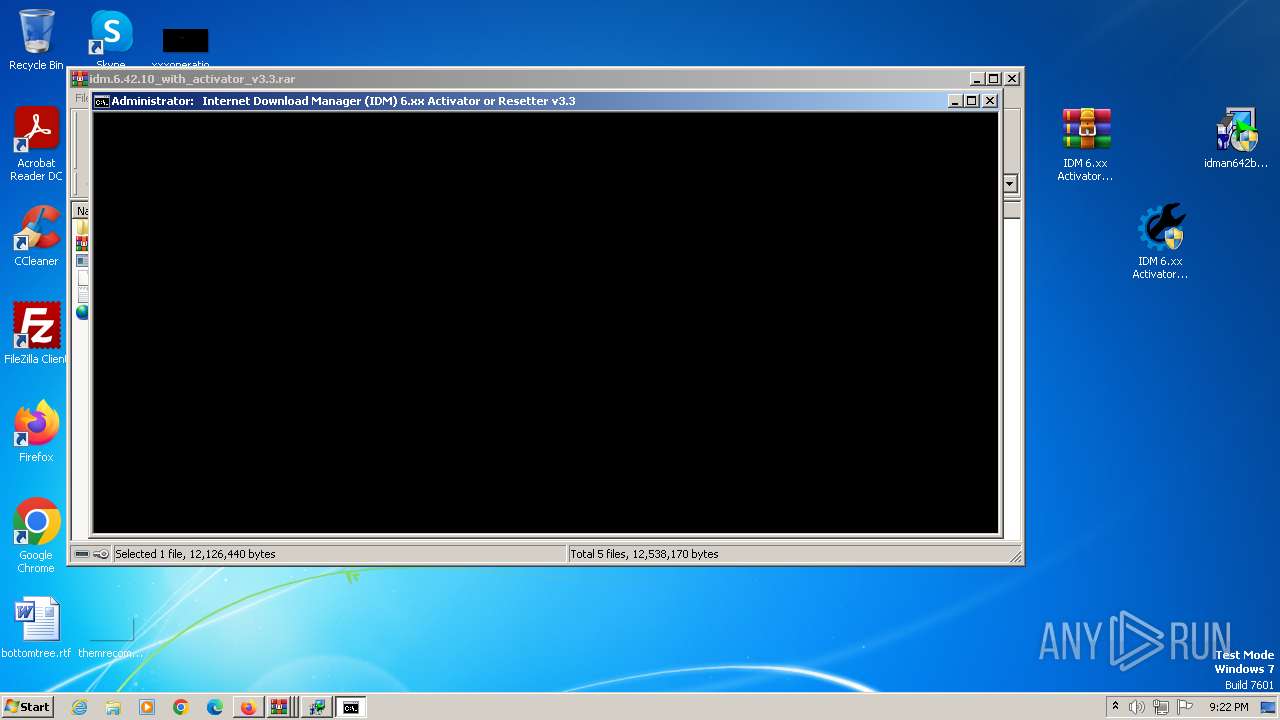
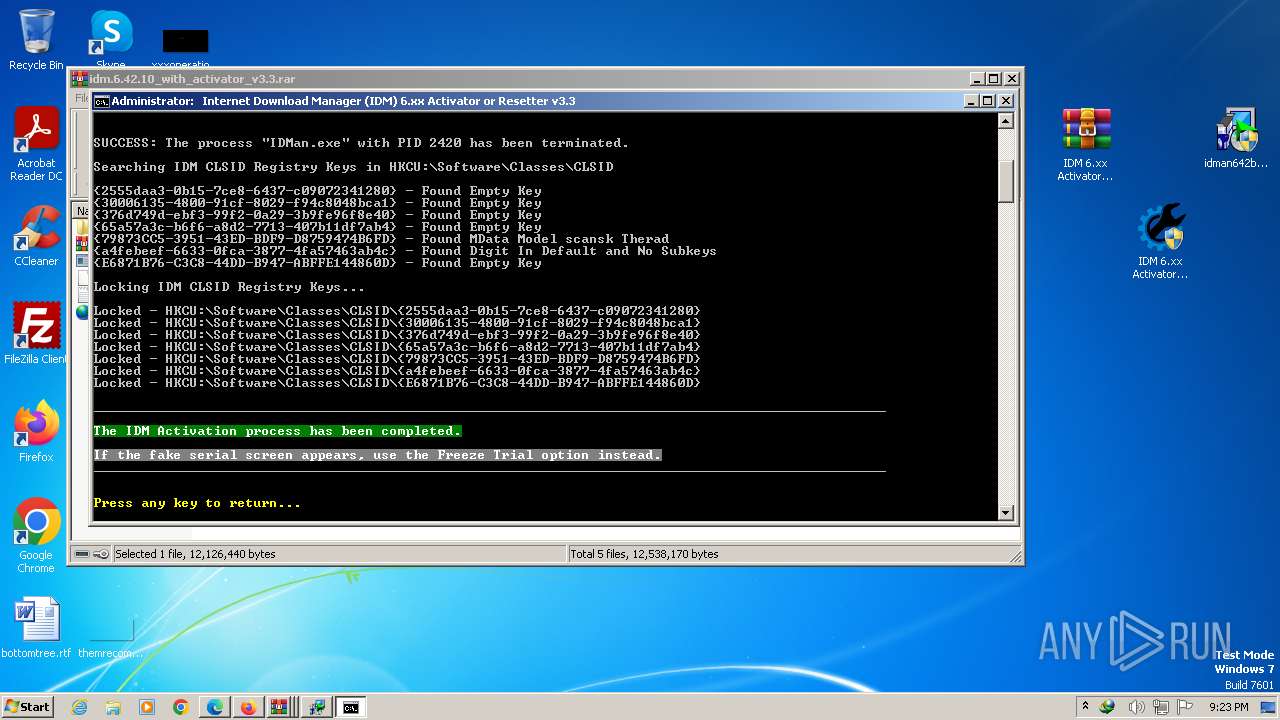
Drops the executable file immediately after the start
- IDM 6.xx Activator or Resetter v3.3.exe (PID: 3648)
- 7za.exe (PID: 2676)
- IDMan.exe (PID: 2420)
Creates a writable file in the system directory
- rundll32.exe (PID: 2864)
Starts NET.EXE for service management
- net.exe (PID: 3160)
- Uninstall.exe (PID: 3140)
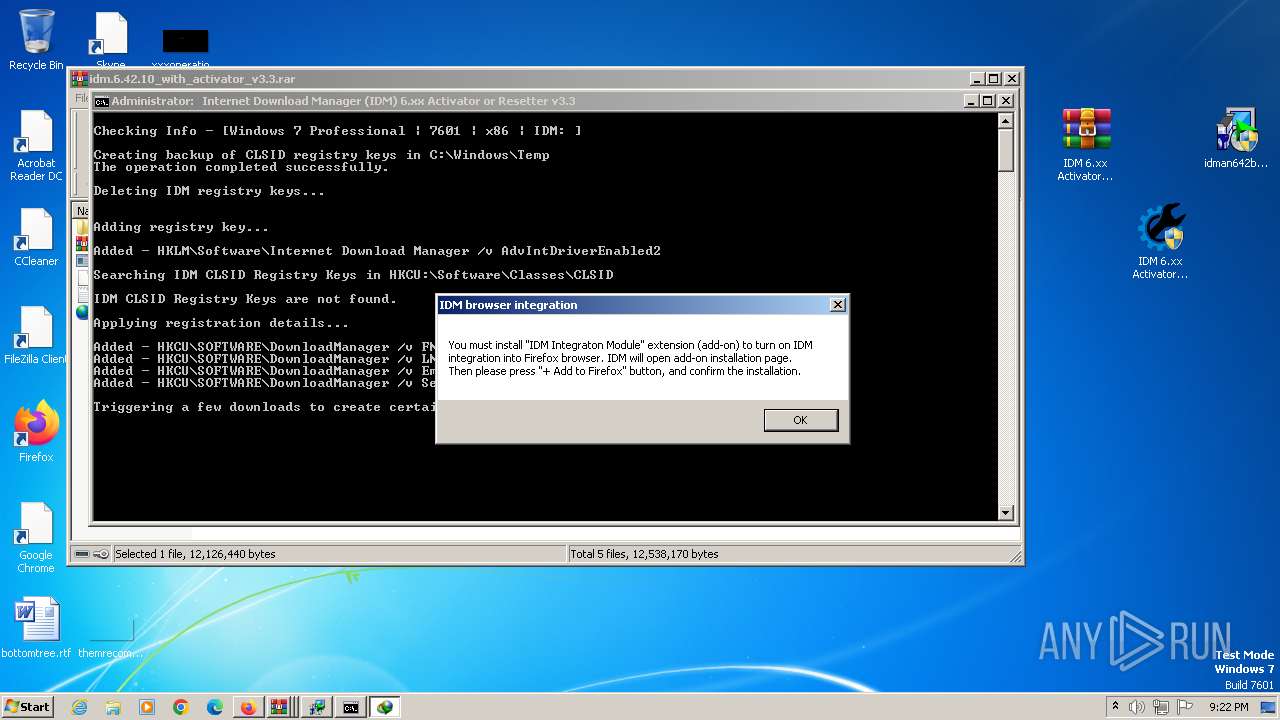
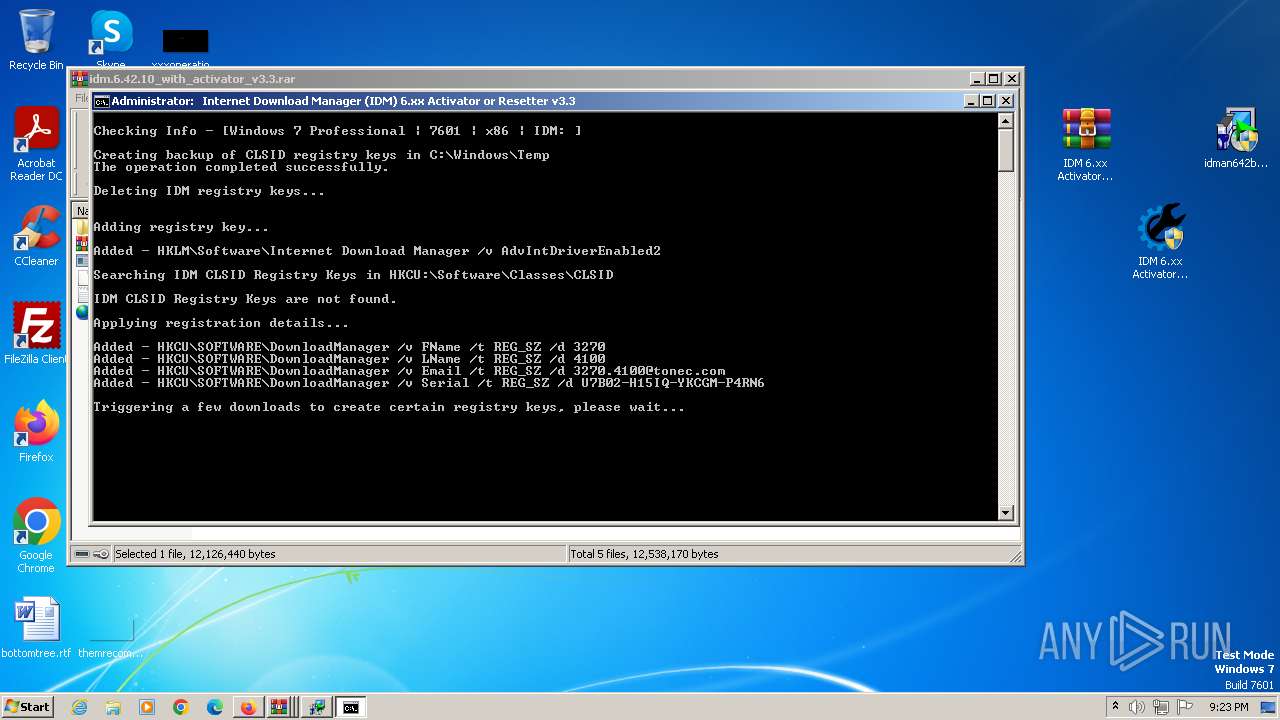
Changes the autorun value in the registry
- rundll32.exe (PID: 2864)
- IDMan.exe (PID: 2420)
Actions looks like stealing of personal data
- IDMan.exe (PID: 2420)
SUSPICIOUS
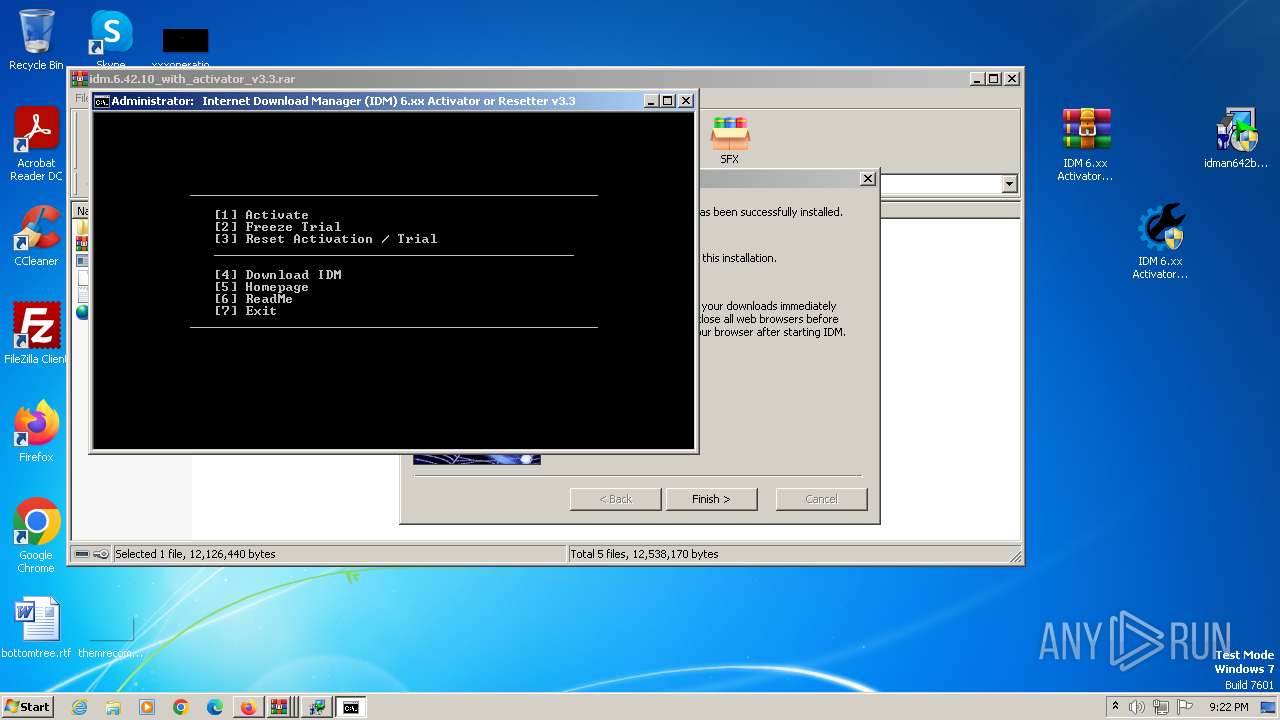
Starts application with an unusual extension
- idman642build10.exe (PID: 1900)
Creates a software uninstall entry
- IDM1.tmp (PID: 3056)
The process creates files with name similar to system file names
- IDM1.tmp (PID: 3056)
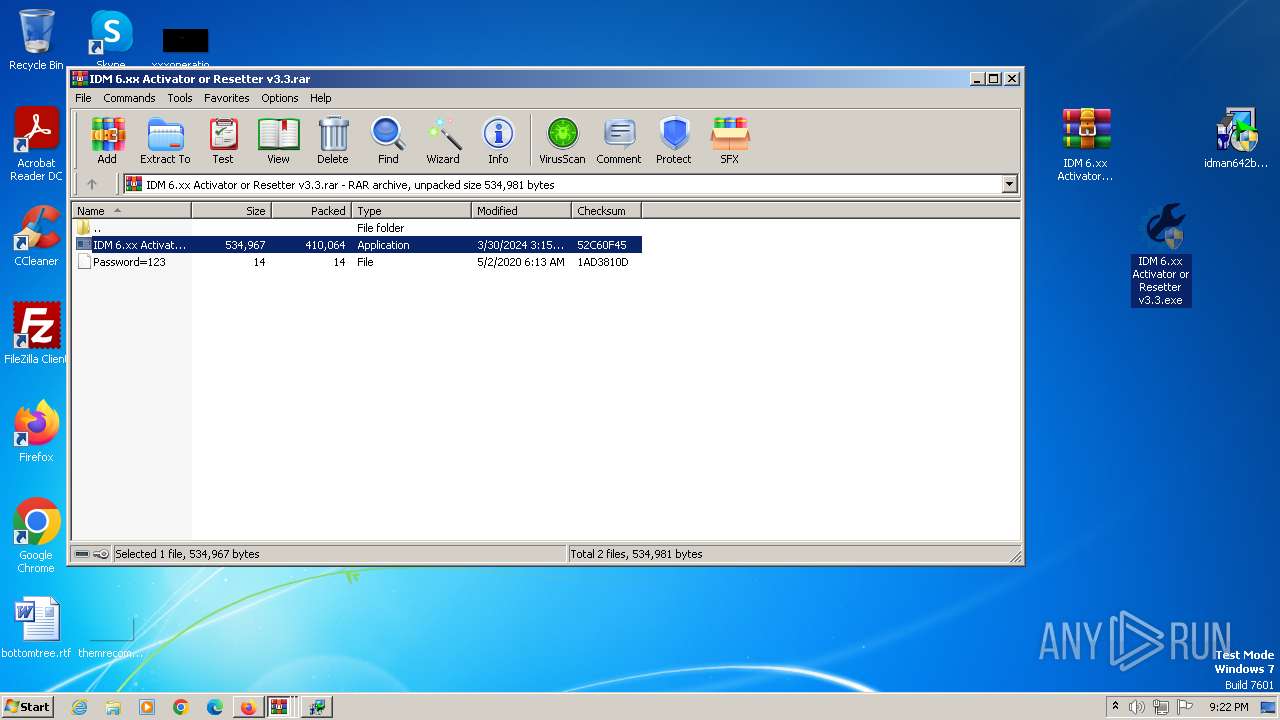
Drops 7-zip archiver for unpacking
- IDM 6.xx Activator or Resetter v3.3.exe (PID: 3648)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 3244)
The executable file from the user directory is run by the CMD process
- 7za.exe (PID: 2456)
- 7za.exe (PID: 3632)
- 7za.exe (PID: 2676)
- 7za.exe (PID: 3356)
- 7za.exe (PID: 3496)
- NSudo86x.exe (PID: 5284)
Reads security settings of Internet Explorer
- IDM 6.xx Activator or Resetter v3.3.exe (PID: 3648)
- IDMan.exe (PID: 2420)
- Uninstall.exe (PID: 3140)
- IDMan.exe (PID: 2388)
- IDMan.exe (PID: 2856)
Executable content was dropped or overwritten
- IDM 6.xx Activator or Resetter v3.3.exe (PID: 3648)
- 7za.exe (PID: 2676)
- rundll32.exe (PID: 2864)
- IDMan.exe (PID: 2420)
Starts CMD.EXE for commands execution
- IDM 6.xx Activator or Resetter v3.3.exe (PID: 3648)
- cmd.exe (PID: 2528)
Reads the Internet Settings
- IDM 6.xx Activator or Resetter v3.3.exe (PID: 3648)
- Uninstall.exe (PID: 3140)
- IDMan.exe (PID: 2420)
- runonce.exe (PID: 3320)
- cmd.exe (PID: 2528)
Executing commands from a ".bat" file
- IDM 6.xx Activator or Resetter v3.3.exe (PID: 3648)
Starts SC.EXE for service management
- cmd.exe (PID: 2528)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 2528)
Application launched itself
- cmd.exe (PID: 2528)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 2528)
- cmd.exe (PID: 2320)
- cmd.exe (PID: 3760)
- cmd.exe (PID: 3476)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 2528)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 2528)
- cmd.exe (PID: 3760)
Hides command output
- cmd.exe (PID: 3476)
- cmd.exe (PID: 1820)
- cmd.exe (PID: 2844)
- cmd.exe (PID: 3508)
- cmd.exe (PID: 3760)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2528)
- cmd.exe (PID: 1820)
- cmd.exe (PID: 3508)
Get information on the list of running processes
- cmd.exe (PID: 2528)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2528)
Reads settings of System Certificates
- IDMan.exe (PID: 2420)
- IDMan.exe (PID: 2388)
- IDMan.exe (PID: 2856)
Checks Windows Trust Settings
- IDMan.exe (PID: 2420)
- IDMan.exe (PID: 2388)
- IDMan.exe (PID: 2856)
- IDMan.exe (PID: 5296)
Drops a system driver (possible attempt to evade defenses)
- rundll32.exe (PID: 2864)
Uses RUNDLL32.EXE to load library
- Uninstall.exe (PID: 3140)
Creates/Modifies COM task schedule object
- IDMan.exe (PID: 2420)
- Uninstall.exe (PID: 3140)
Creates or modifies Windows services
- Uninstall.exe (PID: 3140)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2528)
INFO
Manual execution by a user
- wmpnscfg.exe (PID: 2908)
- WinRAR.exe (PID: 3784)
- idman642build10.exe (PID: 1900)
- idman642build10.exe (PID: 3092)
- WinRAR.exe (PID: 3000)
- WinRAR.exe (PID: 2712)
- IDM 6.xx Activator or Resetter v3.3.exe (PID: 3924)
- IDM 6.xx Activator or Resetter v3.3.exe (PID: 3648)
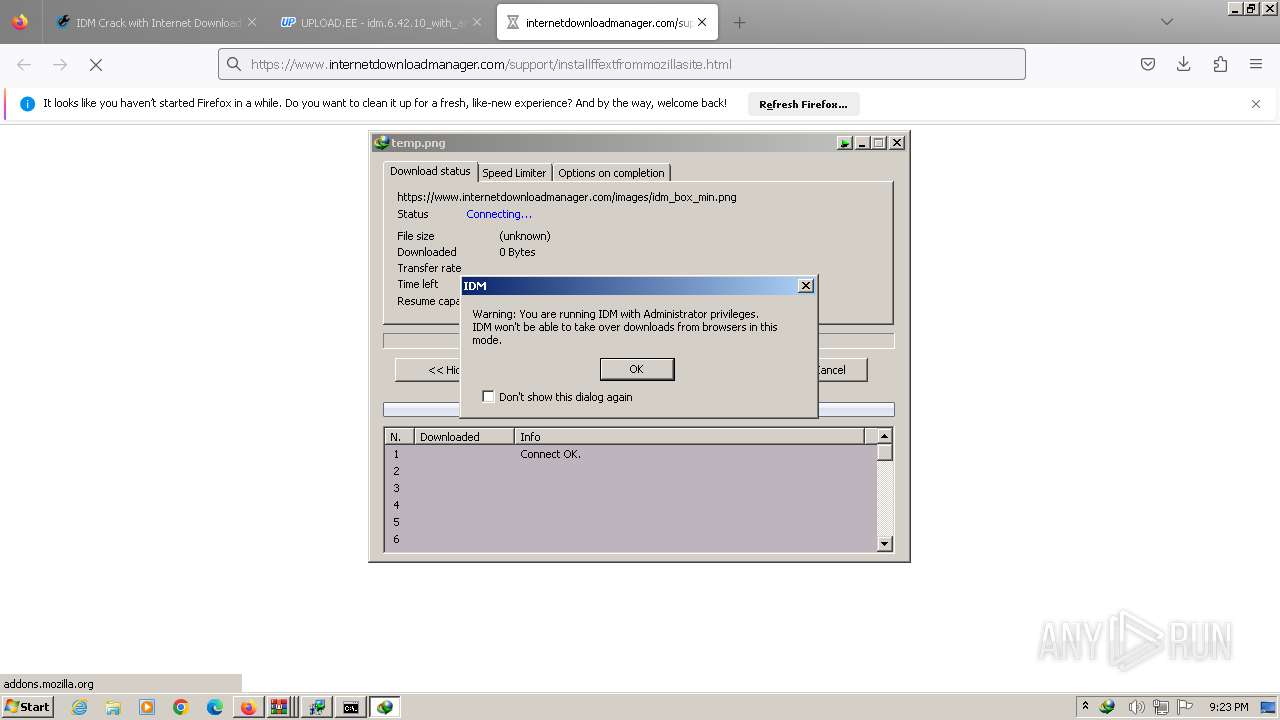
- firefox.exe (PID: 2324)
- msedge.exe (PID: 3124)
Drops the executable file immediately after the start
- firefox.exe (PID: 3992)
- WinRAR.exe (PID: 3784)
- WinRAR.exe (PID: 2712)
- rundll32.exe (PID: 2864)
Application launched itself
- firefox.exe (PID: 3976)
- firefox.exe (PID: 3992)
- firefox.exe (PID: 2324)
- msedge.exe (PID: 992)
- msedge.exe (PID: 3124)
- msedge.exe (PID: 5328)
Checks supported languages
- wmpnscfg.exe (PID: 2908)
- idman642build10.exe (PID: 1900)
- IDM1.tmp (PID: 3056)
- IDM 6.xx Activator or Resetter v3.3.exe (PID: 3648)
- 7za.exe (PID: 2456)
- 7za.exe (PID: 3632)
- 7za.exe (PID: 2676)
- 7za.exe (PID: 3356)
- 7za.exe (PID: 3496)
- mode.com (PID: 3256)
- mode.com (PID: 2412)
- IDMan.exe (PID: 2420)
- Uninstall.exe (PID: 3140)
- IDMan.exe (PID: 2388)
- IDMan.exe (PID: 2856)
- IDMan.exe (PID: 5296)
- NSudo86x.exe (PID: 5284)
- IEMonitor.exe (PID: 5532)
- mode.com (PID: 5936)
- mode.com (PID: 4128)
- mode.com (PID: 4480)
- mode.com (PID: 4596)
- mode.com (PID: 4516)
- mode.com (PID: 4528)
- mode.com (PID: 4556)
- mode.com (PID: 4668)
- mode.com (PID: 4416)
Reads the computer name
- wmpnscfg.exe (PID: 2908)
- IDM1.tmp (PID: 3056)
- IDM 6.xx Activator or Resetter v3.3.exe (PID: 3648)
- 7za.exe (PID: 3632)
- 7za.exe (PID: 2456)
- 7za.exe (PID: 2676)
- 7za.exe (PID: 3496)
- 7za.exe (PID: 3356)
- IDMan.exe (PID: 2420)
- Uninstall.exe (PID: 3140)
- IDMan.exe (PID: 2388)
- IDMan.exe (PID: 2856)
- NSudo86x.exe (PID: 5284)
- IDMan.exe (PID: 5296)
- IEMonitor.exe (PID: 5532)
Executable content was dropped or overwritten
- firefox.exe (PID: 3992)
- WinRAR.exe (PID: 3784)
- WinRAR.exe (PID: 2712)
The process uses the downloaded file
- WinRAR.exe (PID: 3784)
- firefox.exe (PID: 3992)
Create files in a temporary directory
- idman642build10.exe (PID: 1900)
- IDM1.tmp (PID: 3056)
- IDM 6.xx Activator or Resetter v3.3.exe (PID: 3648)
- 7za.exe (PID: 2676)
- 7za.exe (PID: 3632)
- 7za.exe (PID: 2456)
- reg.exe (PID: 2324)
- IDMan.exe (PID: 2420)
- IDMan.exe (PID: 5296)
Reads the machine GUID from the registry
- IDM1.tmp (PID: 3056)
- IDMan.exe (PID: 2420)
- IDMan.exe (PID: 2388)
- IDMan.exe (PID: 2856)
- IDMan.exe (PID: 5296)
Creates files in the program directory
- IDM1.tmp (PID: 3056)
- IDMan.exe (PID: 2420)
Creates files or folders in the user directory
- IDM1.tmp (PID: 3056)
- IDMan.exe (PID: 2420)
- IDMan.exe (PID: 5296)
Checks operating system version
- cmd.exe (PID: 2528)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 3912)
- powershell.exe (PID: 2392)
- powershell.exe (PID: 4844)
Gets a random number, or selects objects randomly from a collection (POWERSHELL)
- powershell.exe (PID: 3912)
- powershell.exe (PID: 2392)
- powershell.exe (PID: 4844)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 3912)
- powershell.exe (PID: 2392)
- powershell.exe (PID: 4844)
Reads the software policy settings
- IDMan.exe (PID: 2420)
- IDMan.exe (PID: 2388)
- IDMan.exe (PID: 2856)
- IDMan.exe (PID: 5296)
Disables trace logs
- IDMan.exe (PID: 2420)
- IDMan.exe (PID: 2388)
- IDMan.exe (PID: 2856)
- IDMan.exe (PID: 5296)
Creates files in the driver directory
- rundll32.exe (PID: 2864)
Checks proxy server information
- IDMan.exe (PID: 2420)
Reads the time zone
- runonce.exe (PID: 3320)
Reads security settings of Internet Explorer
- runonce.exe (PID: 3320)
Process checks whether UAC notifications are on
- IDMan.exe (PID: 2420)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
258
Monitored processes
203
Malicious processes
8
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3992.1.1088134197\516750012" -parentBuildID 20230710165010 -prefsHandle 1436 -prefMapHandle 1432 -prefsLen 28600 -prefMapSize 244195 -appDir "C:\Program Files\Mozilla Firefox\browser" - {591fa58d-073c-4ec5-9c4c-827c70c3ee61} 3992 "\\.\pipe\gecko-crash-server-pipe.3992" 1448 ef8d390 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 312 | reg query HKU\S-1-5-21-1302019708-1500728564-335382590-1000\Software | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 316 | powershell.exe "Get-WmiObject -Class Win32_ComputerSystem | Select-Object -Property CreationClassName" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 368 | REG QUERY "HKLM\Hardware\Description\System\CentralProcessor\0" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 560 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3992.6.443800782\166689045" -childID 5 -isForBrowser -prefsHandle 4192 -prefMapHandle 4200 -prefsLen 29209 -prefMapSize 244195 -jsInitHandle 900 -jsInitLen 240908 -parentBuildID 20230710165010 -appDir "C:\Program Files\Mozilla Firefox\browser" - {90bba365-4515-47ee-bde5-d2000ed841dd} 3992 "\\.\pipe\gecko-crash-server-pipe.3992" 4176 18ba9280 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 580 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3992.21.1693671243\808594994" -childID 20 -isForBrowser -prefsHandle 7612 -prefMapHandle 7420 -prefsLen 31981 -prefMapSize 244195 -jsInitHandle 900 -jsInitLen 240908 -parentBuildID 20230710165010 -appDir "C:\Program Files\Mozilla Firefox\browser" - {c5c85257-77c8-408f-94da-a6f880536e2b} 3992 "\\.\pipe\gecko-crash-server-pipe.3992" 7272 18b19e00 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 924 | powershell.exe "(Get-Date).ToString('yyyyMMdd-HHmmssfff')" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 936 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1184 --field-trial-handle=1352,i,16578303349411664436,13538207998792407227,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 956 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1220 --field-trial-handle=1284,i,8316670753150841619,10111295456082779758,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 960 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3992.4.941802623\851853167" -childID 3 -isForBrowser -prefsHandle 3852 -prefMapHandle 3888 -prefsLen 29209 -prefMapSize 244195 -jsInitHandle 900 -jsInitLen 240908 -parentBuildID 20230710165010 -appDir "C:\Program Files\Mozilla Firefox\browser" - {6e5087ac-e2f5-4d90-bd5a-0f0ef9d34305} 3992 "\\.\pipe\gecko-crash-server-pipe.3992" 3900 18ba9560 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
Total events
127 317
Read events
126 171
Write events
1 059
Delete events
87
Modification events
| (PID) Process: | (3976) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Launcher |
Value: FABEFBE200000000 | |||
| (PID) Process: | (3992) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: 1235FDE200000000 | |||
| (PID) Process: | (3992) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Installer\308046B0AF4A39CB |
| Operation: | delete value | Name: | installer.taskbarpin.win10.enabled |
Value: | |||
| (PID) Process: | (3992) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 0 | |||
| (PID) Process: | (3992) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (3992) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Theme |
Value: 1 | |||
| (PID) Process: | (3992) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Enabled |
Value: 1 | |||
| (PID) Process: | (3992) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableTelemetry |
Value: 1 | |||
| (PID) Process: | (3992) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableDefaultBrowserAgent |
Value: 0 | |||
| (PID) Process: | (3992) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|SetDefaultBrowserUserChoice |
Value: 1 | |||
Executable files
24
Suspicious files
502
Text files
153
Unknown types
35
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3992 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 3992 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 3992 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 3992 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\urlCache-current.bin | binary | |
MD5:04BADC0A17F546BBD91CC2404D2776D9 | SHA256:54CD83D3031D15EA1F5B1C5D73416C0B2F9151F93E130DD525DDA488A8EB9110 | |||
| 3992 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 3992 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 3992 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3561288849sdhlie.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 3992 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\datareporting\glean\db\data.safe.bin | dbf | |
MD5:63B1BB87284EFE954E1C3AE390E7EE44 | SHA256:B017EE25A7F5C09EB4BF359CA721D67E6E9D9F95F8CE6F741D47F33BDE6EF73A | |||
| 3992 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\activity-stream.discovery_stream.json.tmp | binary | |
MD5:F45B9A6E2AF1573F05DC479D390A4E05 | SHA256:4AEF80F1250A23C95AF41CEB78D4543A869CCCA21536BA9C25341ED4A4F0F7FC | |||
| 3992 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
57
TCP/UDP connections
247
DNS requests
414
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3992 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | unknown |
3992 | firefox.exe | POST | — | 23.211.60.70:80 | http://r3.o.lencr.org/ | unknown | — | — | unknown |
3992 | firefox.exe | POST | 200 | 142.250.186.35:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
3992 | firefox.exe | POST | 200 | 23.211.60.70:80 | http://r3.o.lencr.org/ | unknown | — | — | unknown |
3992 | firefox.exe | POST | 200 | 142.250.186.35:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
3992 | firefox.exe | POST | 200 | 23.211.60.70:80 | http://r3.o.lencr.org/ | unknown | — | — | unknown |
3992 | firefox.exe | POST | 200 | 23.211.60.70:80 | http://r3.o.lencr.org/ | unknown | — | — | unknown |
3992 | firefox.exe | POST | 200 | 23.211.60.70:80 | http://r3.o.lencr.org/ | unknown | — | — | unknown |
3992 | firefox.exe | POST | 200 | 23.211.60.70:80 | http://r3.o.lencr.org/ | unknown | — | — | unknown |
3992 | firefox.exe | POST | 200 | 23.211.60.70:80 | http://r3.o.lencr.org/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3992 | firefox.exe | 188.114.96.3:443 | www.crackingcity.com | CLOUDFLARENET | NL | unknown |
3992 | firefox.exe | 34.107.243.93:443 | push.services.mozilla.com | GOOGLE | US | unknown |
3992 | firefox.exe | 142.250.185.74:443 | safebrowsing.googleapis.com | — | — | whitelisted |
3992 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
3992 | firefox.exe | 142.250.186.35:80 | o.pki.goog | GOOGLE | US | whitelisted |
3992 | firefox.exe | 142.250.186.138:443 | ajax.googleapis.com | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.crackingcity.com |
| unknown |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
spocs.getpocket.com |
| shared |
prod.ads.prod.webservices.mozgcp.net |
| unknown |
r3.o.lencr.org |
| shared |
a1887.dscq.akamai.net |
| whitelisted |