| File name: | aaafeddedccbbaafeeedcddcccbbaafe |
| Full analysis: | https://app.any.run/tasks/d43b7917-38fb-43e4-8292-c1717325807c |
| Verdict: | Malicious activity |
| Analysis date: | January 22, 2019, 16:42:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (DLL) (GUI) Intel 80386, for MS Windows |
| MD5: | 7407545561EB01088043D5B400F50377 |
| SHA1: | 48987C8EE580AF3BA9A074B629C5DD44D3E55B3C |
| SHA256: | D00290AFE51D7177968915C3778E18659168EDC2356A32E41CCCBA23D390DAF6 |
| SSDEEP: | 98304:dV4XNpILQNegCEOllcc1J7W/72YUek6vT6v7pS0MMKkB6:viCLUClllcJ/71vTO7pSDk |
MALICIOUS
Loads dropped or rewritten executable
- explorer.exe (PID: 284)
- svchost.exe (PID: 844)
- consent.exe (PID: 3552)
- WerFault.exe (PID: 3100)
SUSPICIOUS
Uses RUNDLL32.EXE to load library
- explorer.exe (PID: 284)
Creates files in the user directory
- notepad++.exe (PID: 3092)
INFO
Loads main object executable
- rundll32.exe (PID: 3796)
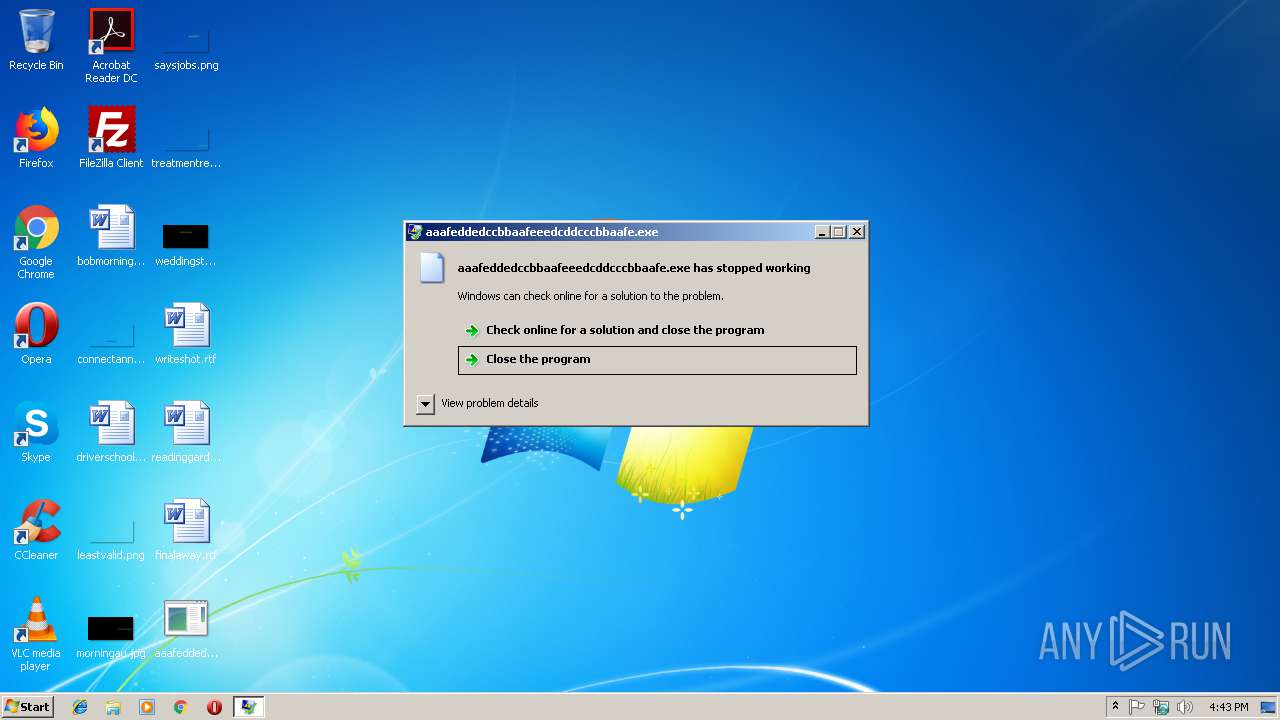
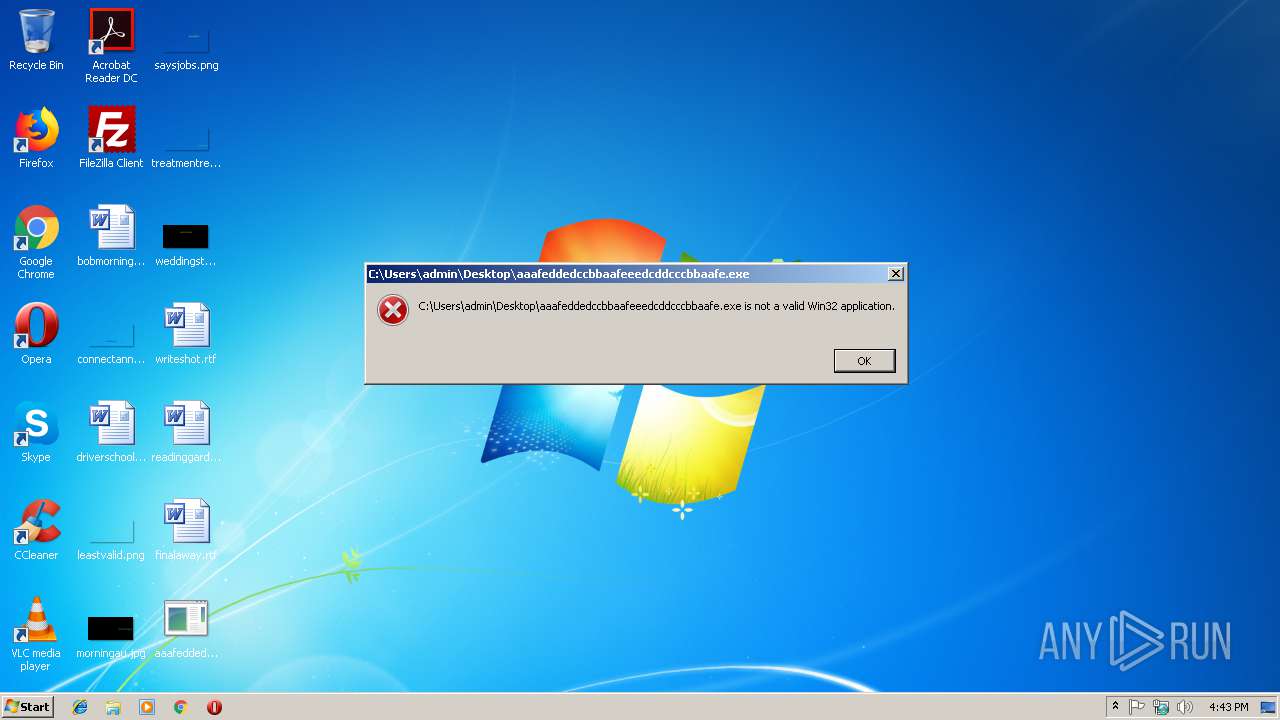
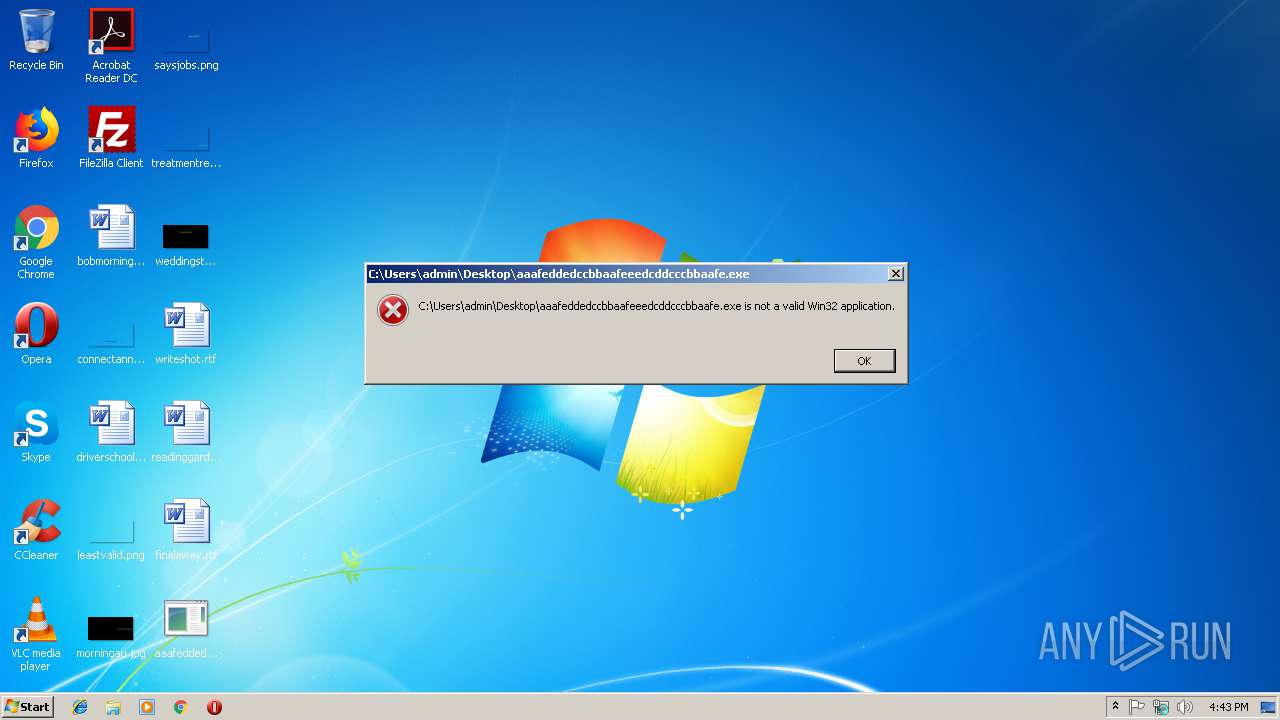
Application was crashed
- rundll32.exe (PID: 3796)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2017:06:28 23:22:43+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 74752 |
| InitializedDataSize: | 37888 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3ccf |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 28-Jun-2017 21:22:43 |
| Debug artifacts: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000E8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 28-Jun-2017 21:22:43 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00012294 | 0x00012400 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.69006 |
.rdata | 0x00014000 | 0x00004130 | 0x00004200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.34469 |
.data | 0x00019000 | 0x000036DC | 0x00001600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.42063 |
.reloc | 0x0001D000 | 0x00001954 | 0x00001A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 4.49894 |
.rsrc | 0x0001F000 | 0x0055C4C0 | 0x0055C600 | IMAGE_SCN_MEM_READ | 6.78423 |
Imports
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHLWAPI.dll |
USER32.dll |
Exports
Title | Ordinal | Address |
|---|---|---|
FEfAWapcxqRsTcVN | 1 | 0x00001BBB |
ilsvztovgctursuw | 2 | 0x00001292 |
kvforvjvgwuq | 3 | 0x00001017 |
obgyutgxz | 4 | 0x00001662 |
ooocdsvzfxl | 5 | 0x000011A2 |
yfslbsffcfpb | 6 | 0x0000194D |
ypagnacmlidrorpk | 7 | 0x00001270 |
Total processes
38
Monitored processes
7
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 284 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 844 | C:\Windows\system32\svchost.exe -k netsvcs | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2356 | "C:\Program Files\Notepad++\updater\gup.exe" -v7.51 | C:\Program Files\Notepad++\updater\gup.exe | notepad++.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: GUP : a free (LGPL) Generic Updater Exit code: 0 Version: 4.1 Modules
| |||||||||||||||
| 3092 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\aaafeddedccbbaafeeedcddcccbbaafe.exe" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.51 Modules
| |||||||||||||||
| 3100 | C:\Windows\system32\WerFault.exe -u -p 3796 -s 188 | C:\Windows\system32\WerFault.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3552 | consent.exe 844 432 029D5990 | C:\Windows\system32\consent.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Consent UI for administrative applications Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3796 | "C:\Windows\System32\rundll32.exe" "C:\Users\admin\Desktop\aaafeddedccbbaafeeedcddcccbbaafe.exe", FEfAWapcxqRsTcVN | C:\Windows\System32\rundll32.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 3221225477 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 917
Read events
1 859
Write events
58
Delete events
0
Modification events
| (PID) Process: | (284) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3552) consent.exe | Key: | HKEY_USERS\S-1-5-21-1302019708-1500728564-335382590-1000_CLASSES\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (844) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList\S-1-5-21-1302019708-1500728564-335382590-1000 |
| Operation: | write | Name: | RefCount |
Value: 2 | |||
| (PID) Process: | (844) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList\S-1-5-21-1302019708-1500728564-335382590-1000 |
| Operation: | write | Name: | RefCount |
Value: 1 | |||
| (PID) Process: | (3092) notepad++.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3092) notepad++.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3092) notepad++.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (284) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | {7P5N40RS-N0SO-4OSP-874N-P0S2R0O9SN8R}\Abgrcnq++\abgrcnq++.rkr |
Value: 000000000000000000000000D5010000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF000000000000000000000000 | |||
| (PID) Process: | (284) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 000000002E0000003D0000005A451500090000000B000000DCC402007B00370043003500410034003000450046002D0041003000460042002D0034004200460043002D0038003700340041002D004300300046003200450030004200390046004100380045007D005C00410064006F00620065005C004100630072006F0062006100740020005200650061006400650072002000440043005C005200650061006400650072005C004100630072006F0052006400330032002E0065007800650000000000D09866060000000034E82802C05D5A740200000002000000000C00940F000000E8E82802010000000400000001000000010000006B001001D098660605000000D098660602020000E20101AE2B51EA0088E7280239B58D76E20101AE24E82802130000000400000030000000120000001D000000130000001D0000000E00000012000000020000003200000014000000E387EE7A38E82802F3AE5B7400574100E20101AE010000000000000011000000F0443500E8443500A14A52740000000020E800001F51EA7AD0E728028291917520E828028CD800006B51EA7AE4E72802B69C917590D8D4035C0000000401000084F2280244F228026B4E317411000000F0443500E8443500A8EAD403FA4F31740000000074E80000AB5EEA7A24E828028291917574E8280228E8280227959175000000008CD8D40350E82802CD9491758CD8D403FCE8280200D4D403E19491750000000000D4D403FCE8280258E82802000000000E0000005DEC04007B00440036003500320033003100420030002D0042003200460031002D0034003800350037002D0041003400430045002D004100380045003700430036004500410037004400320037007D005C007400610073006B006D00670072002E0065007800650000003702000008023CE23702350100C082BAD075B048D4750200000001000000A048D4750100000068E23702C5B8D075A848D47501000000C81008000000000090E237026BB9D07500000000350100C001000000B0E23702973CB8779C3CB877F58CF77501000000350100C00000000088E23702FFFFFFFFF8E23702EDE0B47745727800FEFFFFFFC0E237020D6BD075A0E737028CE8370200000000F8E23702973CB8779C3CB877BD8CF775000000008CE83702A0E73702D0E237020100000070E73702EDE0B47745727800FEFFFFFF08E337020D6BD0757E0000008CE8370280E73702F36BD075E186D0752794C6128CE8370210000000570104003E0040008CE83702A0E73702000000000000000000000000000008025CE537020000080254E33702350100C000000000D8E637023200000018000000000000000000000088E3370211000000B8450B00B0450B0032000000D8E63702F0E300009B1EC112A0E3370282919576F0E33702A4E3370227959576000000006C155002CCE33702CD9495766C15500278E43702E0105002E194957600000000E010500278E43702D4E33702090000000B000000DCC402007B00370043003500410034003000450046002D0041003000460042002D0034004200460043002D0038003700340041002D004300300046003200450030004200390046004100380045007D005C00410064006F00620065005C004100630072006F0062006100740020005200650061006400650072002000440043005C005200650061006400650072005C004100630072006F0052006400330032002E0065007800650000000000D09866060000000034E82802C05D5A740200000002000000000C00940F000000E8E82802010000000400000001000000010000006B001001D098660605000000D098660602020000E20101AE2B51EA0088E7280239B58D76E20101AE24E82802130000000400000030000000120000001D000000130000001D0000000E00000012000000020000003200000014000000E387EE7A38E82802F3AE5B7400574100E20101AE010000000000000011000000F0443500E8443500A14A52740000000020E800001F51EA7AD0E728028291917520E828028CD800006B51EA7AE4E72802B69C917590D8D4035C0000000401000084F2280244F228026B4E317411000000F0443500E8443500A8EAD403FA4F31740000000074E80000AB5EEA7A24E828028291917574E8280228E8280227959175000000008CD8D40350E82802CD9491758CD8D403FCE8280200D4D403E19491750000000000D4D403FCE8280258E82802 | |||
| (PID) Process: | (284) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | {7P5N40RS-N0SO-4OSP-874N-P0S2R0O9SN8R}\Abgrcnq++\hcqngre\THC.rkr |
Value: 000000000000000000000000CD0A0000000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BF000080BFFFFFFFFF000000000000000000000000 | |||
Executable files
0
Suspicious files
1
Text files
4
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3092 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\stylers.xml | xml | |
MD5:44982E1D48434C0AB3E8277E322DD1E4 | SHA256:3E661D3F1FF3977B022A0ACC26B840B5E57D600BC03DCFC6BEFDB408C665904C | |||
| 3100 | WerFault.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\WER\ReportArchive\AppCrash_rundll32.exe_aaa_fe5af628cc8e5d7b24afbc2d58ea29ab421b8_0c3cfe98\Report.wer | binary | |
MD5:— | SHA256:— | |||
| 844 | svchost.exe | C:\Windows\appcompat\programs\RecentFileCache.bcf | txt | |
MD5:— | SHA256:— | |||
| 3100 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\rundll32.exe.3796.dmp | dmp | |
MD5:— | SHA256:— | |||
| 3092 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\shortcuts.xml | text | |
MD5:AD21A64014891793DD9B21D835278F36 | SHA256:C24699C9D00ABDD510140FE1B2ACE97BFC70D8B21BF3462DED85AFC4F73FE52F | |||
| 3092 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\langs.xml | xml | |
MD5:E792264BEC29005B9044A435FBA185AB | SHA256:5298FD2F119C43D04F6CF831F379EC25B4156192278E40E458EC356F9B49D624 | |||
| 3092 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\plugins\Config\converter.ini | text | |
MD5:F70F579156C93B097E656CABA577A5C9 | SHA256:B926498A19CA95DC28964B7336E5847107DD3C0F52C85195C135D9DD6CA402D4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
2
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 72.247.178.8:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEAXk3DuUOKs7hZfLpqGYUOM%3D | NL | der | 727 b | whitelisted |
— | — | GET | 200 | 72.247.178.8:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCEBPqKHBb9OztDDZjCYBhQzY%3D | NL | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 72.247.178.8:80 | ocsp.usertrust.com | Akamai International B.V. | NL | whitelisted |
2356 | gup.exe | 37.59.28.236:443 | notepad-plus-plus.org | OVH SAS | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
notepad-plus-plus.org |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | 42C4C5846BB675C74E2B2C90C69AB44366401093
|