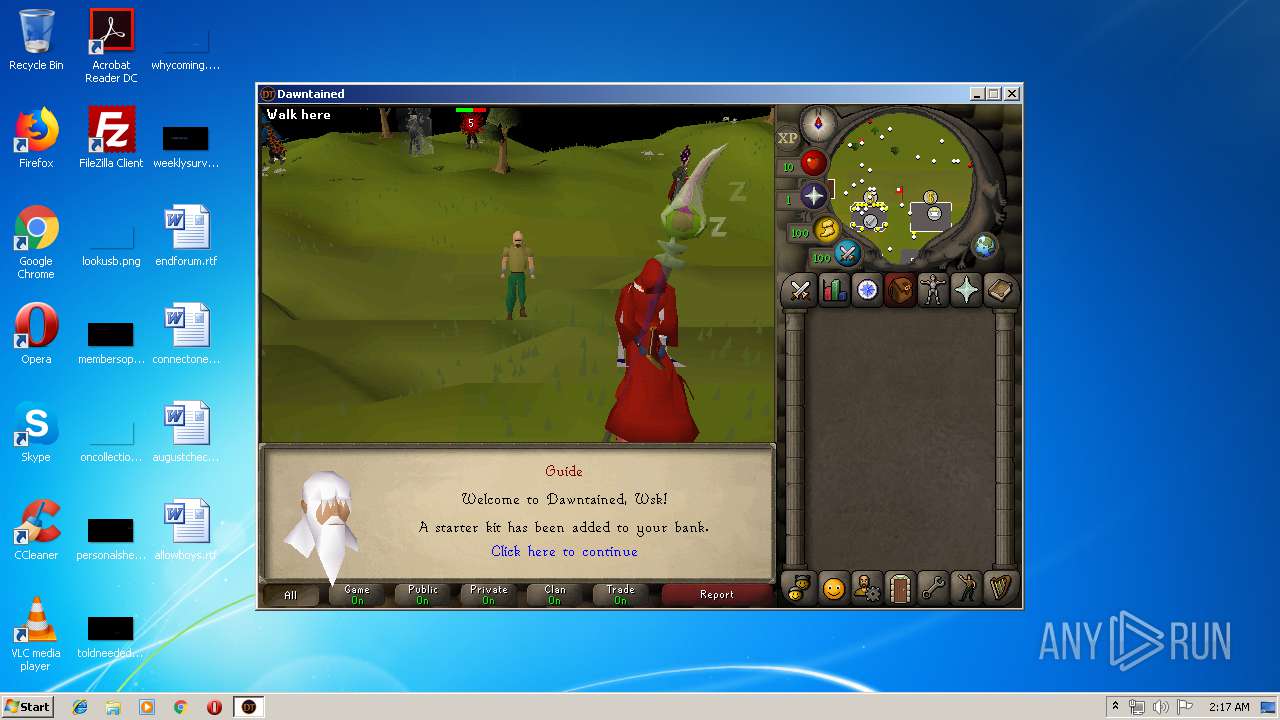
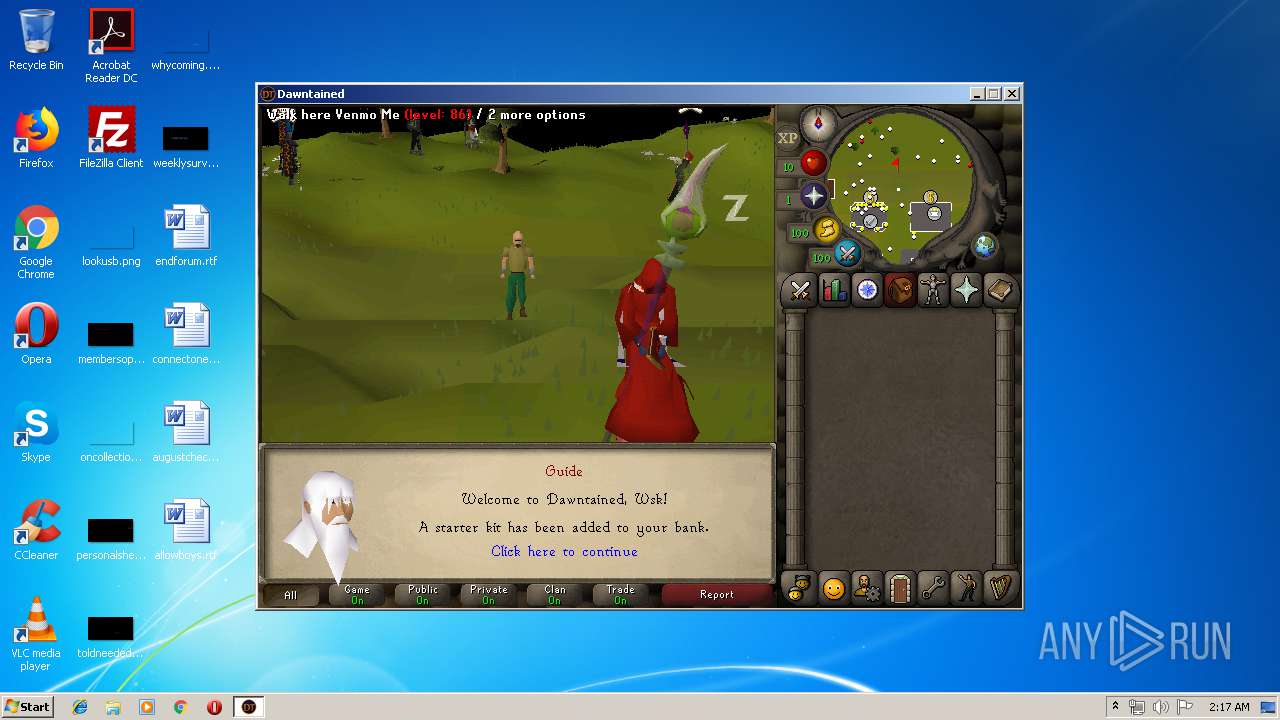
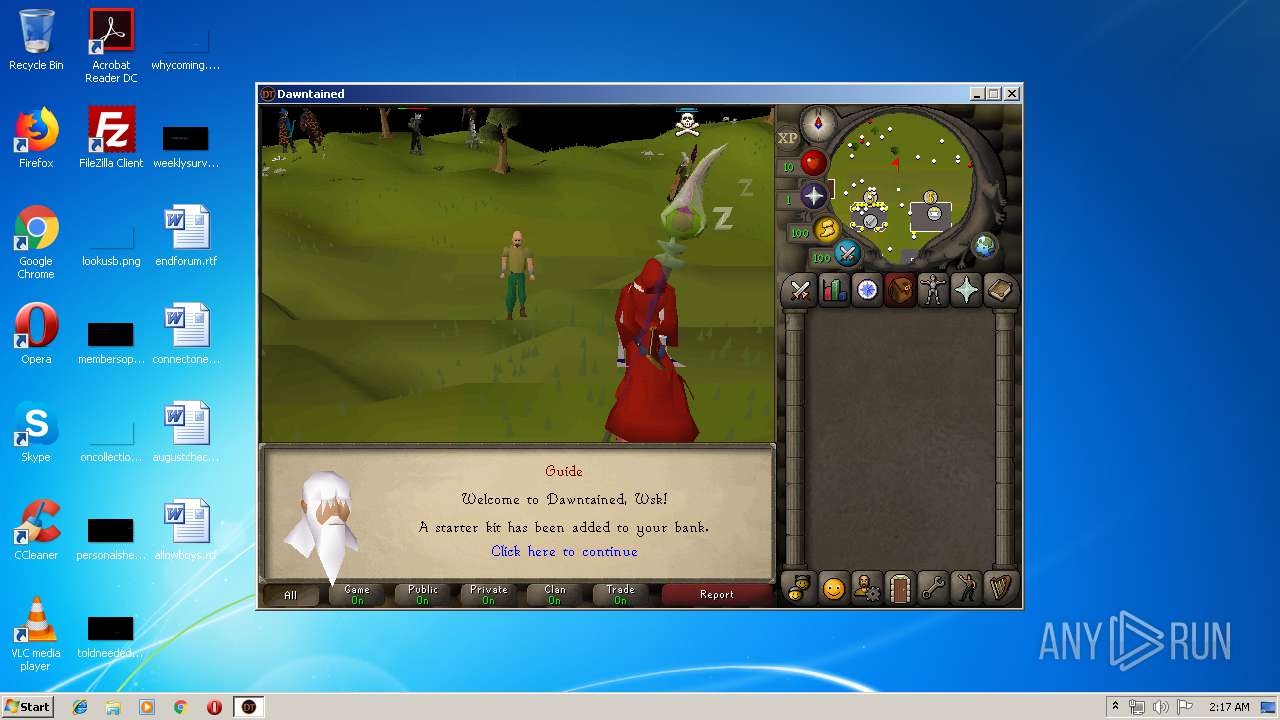
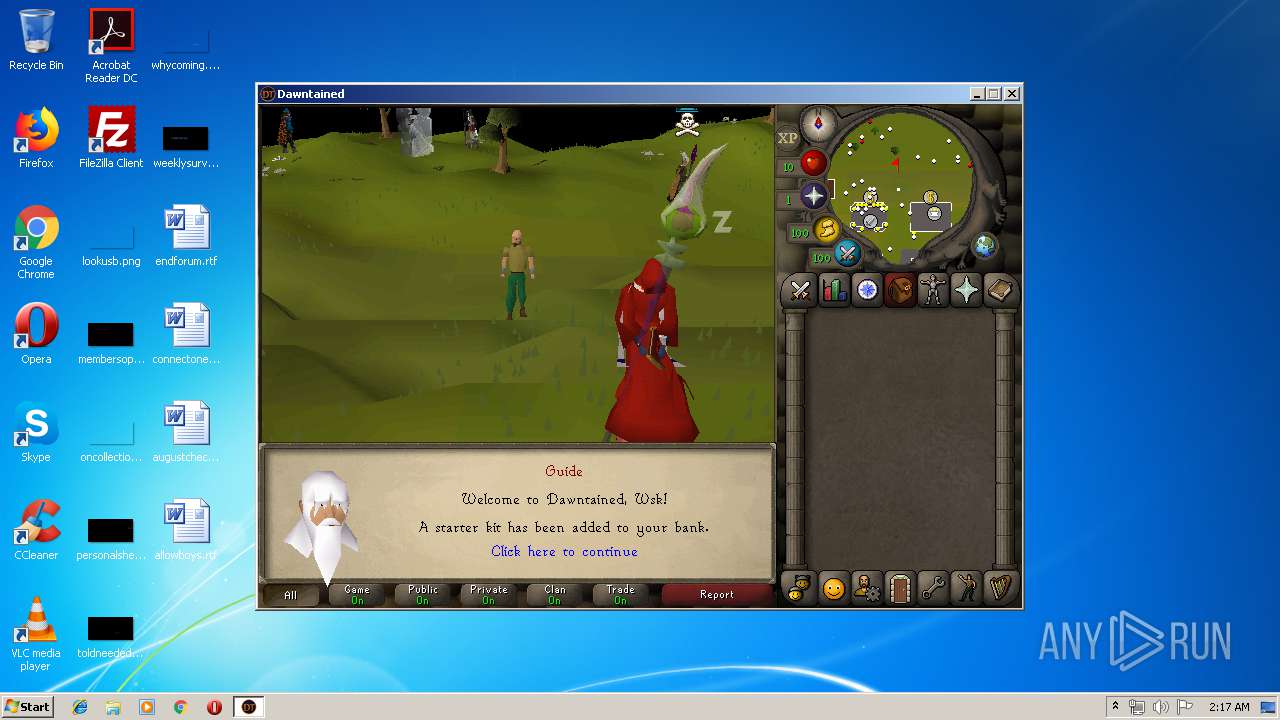
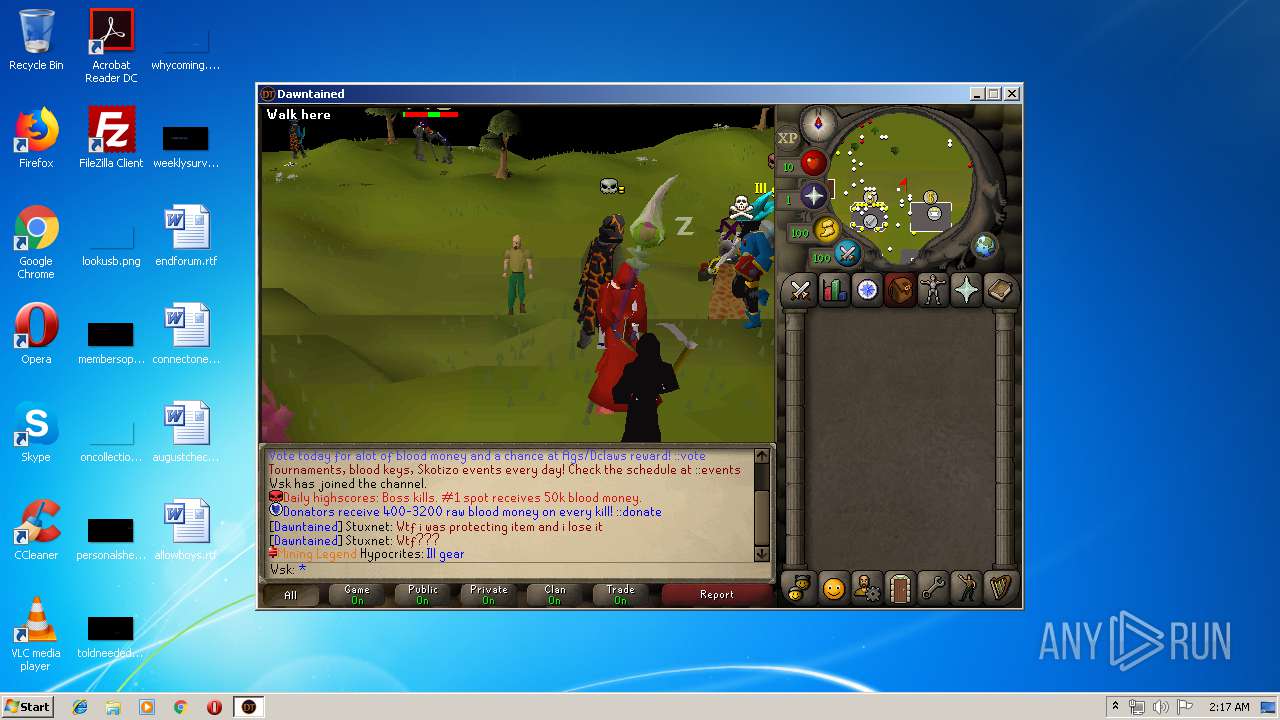
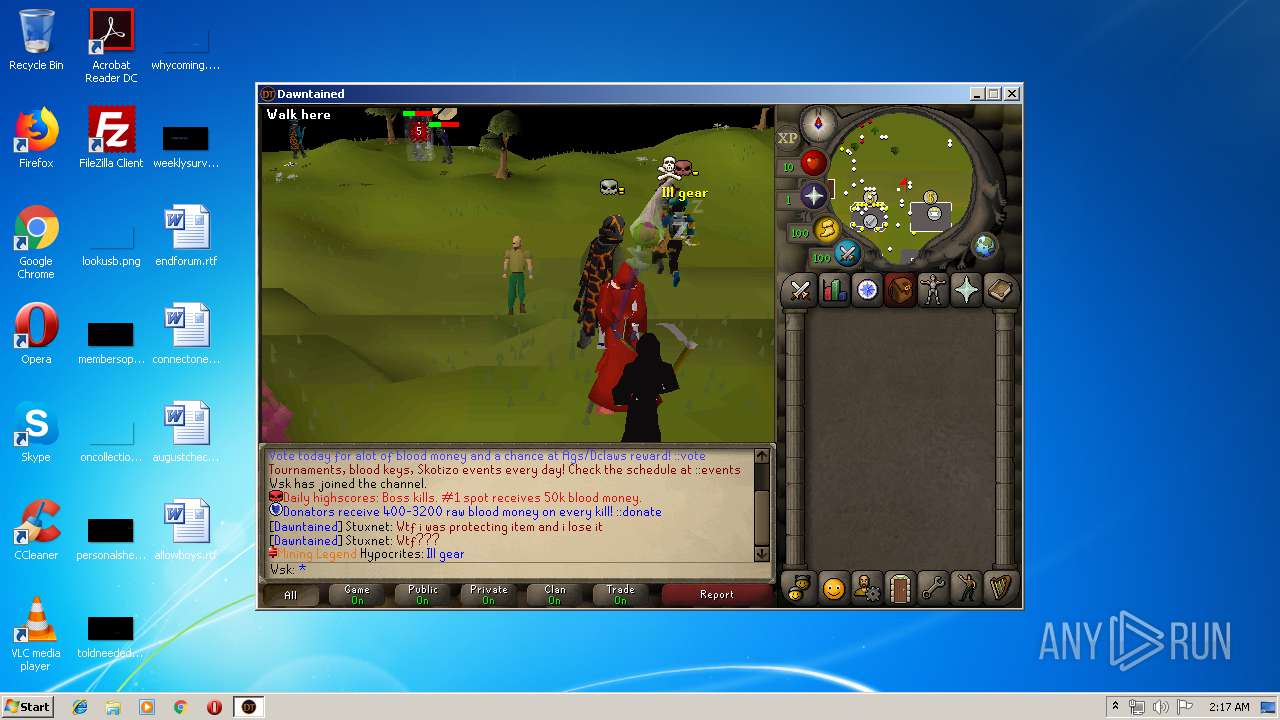
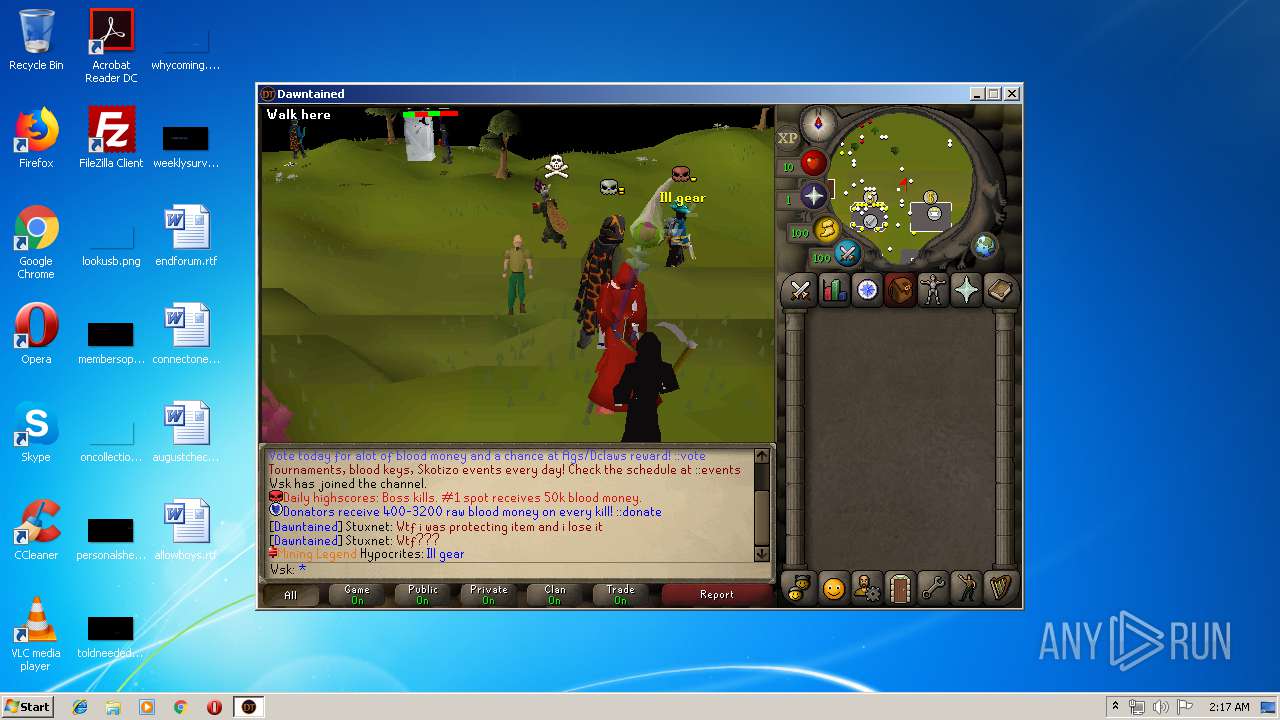
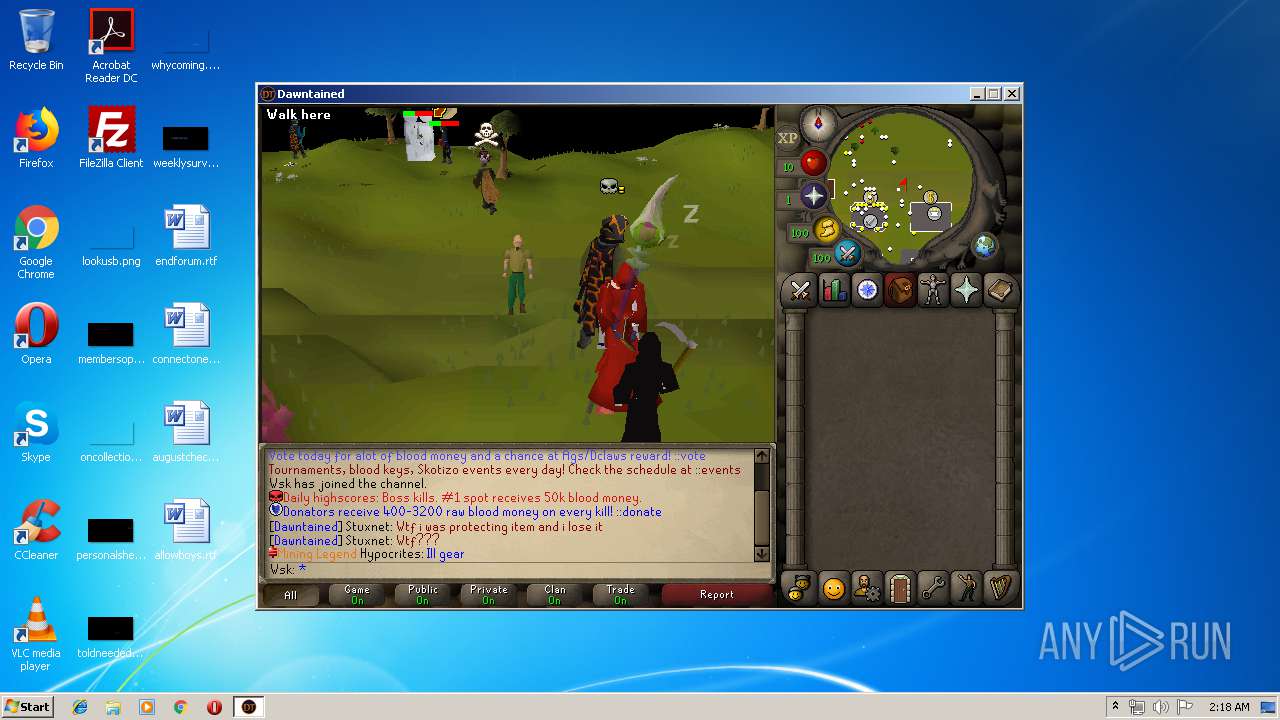
| File name: | dawntained_client.jar |
| Full analysis: | https://app.any.run/tasks/3d5d5c96-d1c6-4805-bdc2-68acaee32adf |
| Verdict: | Malicious activity |
| Analysis date: | April 07, 2019, 01:14:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 52EB03770E85D98487740A364B7E0BA3 |
| SHA1: | 83DBB0B5329C08C3DE17D6AF0F3194AAF9256446 |
| SHA256: | CFD403DB15547781CC3E6E3E8F6ED0E347ABDD11AAC55DD0A51C240FA837342D |
| SSDEEP: | 98304:/skjlI5gFMrM0X7VkryV8SZaGWK28YyZW5Rksi+0+WXM8Y1E:0h5n7myiCL2eZW5Rksi+N8Y1E |
MALICIOUS
Loads dropped or rewritten executable
- javaw.exe (PID: 3576)
SUSPICIOUS
Creates files in the user directory
- javaw.exe (PID: 3576)
Executable content was dropped or overwritten
- javaw.exe (PID: 3576)
Starts CMD.EXE for commands execution
- javaw.exe (PID: 3576)
Executes scripts
- cmd.exe (PID: 2516)
- cmd.exe (PID: 2088)
- cmd.exe (PID: 2876)
- cmd.exe (PID: 3984)
Checks for external IP
- javaw.exe (PID: 3576)
Connects to unusual port
- javaw.exe (PID: 3576)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .jar | | | Java Archive (78.3) |
|---|---|---|
| .zip | | | ZIP compressed archive (21.6) |
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:04:04 15:00:22 |
| ZipCRC: | 0x2db8e7ef |
| ZipCompressedSize: | 56 |
| ZipUncompressedSize: | 56 |
| ZipFileName: | META-INF/MANIFEST.MF |
Total processes
57
Monitored processes
14
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 928 | cscript.exe C:\Users\admin\AppData\Local\Temp\jwmi.vbs | C:\Windows\system32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1016 | cmd.exe /C "echo %TEMP%" | C:\Windows\system32\cmd.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1024 | cscript.exe C:\Users\admin\AppData\Local\Temp\jwmi.vbs | C:\Windows\system32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2088 | cmd.exe /C cscript.exe C:\Users\admin\AppData\Local\Temp\jwmi.vbs | C:\Windows\system32\cmd.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2516 | cmd.exe /C cscript.exe C:\Users\admin\AppData\Local\Temp\jwmi.vbs | C:\Windows\system32\cmd.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2616 | cscript.exe C:\Users\admin\AppData\Local\Temp\jwmi.vbs | C:\Windows\system32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2876 | cmd.exe /C cscript.exe C:\Users\admin\AppData\Local\Temp\jwmi.vbs | C:\Windows\system32\cmd.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3288 | cmd.exe /C "echo %TEMP%" | C:\Windows\system32\cmd.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3528 | wmic bios get serialnumber | C:\Windows\System32\Wbem\wmic.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3576 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -jar "C:\Users\admin\AppData\Local\Temp\dawntained_client.jar" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | explorer.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
Total events
183
Read events
182
Write events
1
Delete events
0
Modification events
| (PID) Process: | (3576) javaw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: javaw.exe | |||
Executable files
1
Suspicious files
14
Text files
100
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3576 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio878103759220430694.tmp | — | |
MD5:— | SHA256:— | |||
| 3576 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio5971693380413331528.tmp | — | |
MD5:— | SHA256:— | |||
| 3576 | javaw.exe | C:\Users\admin\AppData\Local\Temp\jwmi.vbs | — | |
MD5:— | SHA256:— | |||
| 3576 | javaw.exe | C:\Users\admin\dawntained\v34\474_cache\dt\474_cache.zip | — | |
MD5:— | SHA256:— | |||
| 3576 | javaw.exe | C:\Users\admin\dawntained\v34\474_cache\dt\main_file_cache.dat | — | |
MD5:— | SHA256:— | |||
| 3576 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio7702023675221319640.tmp | — | |
MD5:— | SHA256:— | |||
| 3576 | javaw.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 3576 | javaw.exe | C:\Users\admin\dawntained_local\arguments.properties | text | |
MD5:— | SHA256:— | |||
| 3576 | javaw.exe | C:\Users\admin\dawntained\v34\474_cache\dt\main_file_cache.idx5 | binary | |
MD5:— | SHA256:— | |||
| 3576 | javaw.exe | C:\Users\admin\dawntained\v34\474_cache\dt\main_file_cache.idx2 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
11
DNS requests
7
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3576 | javaw.exe | GET | 200 | 52.6.79.229:80 | http://checkip.amazonaws.com/ | US | text | 14 b | malicious |
3576 | javaw.exe | GET | 200 | 94.23.249.25:80 | http://www.dawntained.com/game/data.txt | FR | text | 494 b | suspicious |
3576 | javaw.exe | GET | 200 | 94.23.249.25:80 | http://www.dawntained.com/game/data.txt | FR | text | 494 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3576 | javaw.exe | 94.23.249.25:80 | www.dawntained.com | OVH SAS | FR | suspicious |
3576 | javaw.exe | 52.6.79.229:80 | checkip.amazonaws.com | Amazon.com, Inc. | US | shared |
3576 | javaw.exe | 162.125.66.6:443 | ucf8d95794b5aae85bad150364d5.dl.dropboxusercontent.com | Dropbox, Inc. | DE | shared |
3576 | javaw.exe | 54.36.126.177:43595 | — | OVH SAS | FR | unknown |
3576 | javaw.exe | 94.23.218.44:443 | webservice.dawntained.com | OVH SAS | FR | unknown |
3576 | javaw.exe | 162.125.66.1:443 | www.dropbox.com | Dropbox, Inc. | DE | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.dawntained.com |
| suspicious |
checkip.amazonaws.com |
| malicious |
www.dropbox.com |
| shared |
ucf8d95794b5aae85bad150364d5.dl.dropboxusercontent.com |
| malicious |
uc69e33c235a876b28d863ab2b7c.dl.dropboxusercontent.com |
| malicious |
webservice.dawntained.com |
| unknown |
Threats
1 ETPRO signatures available at the full report