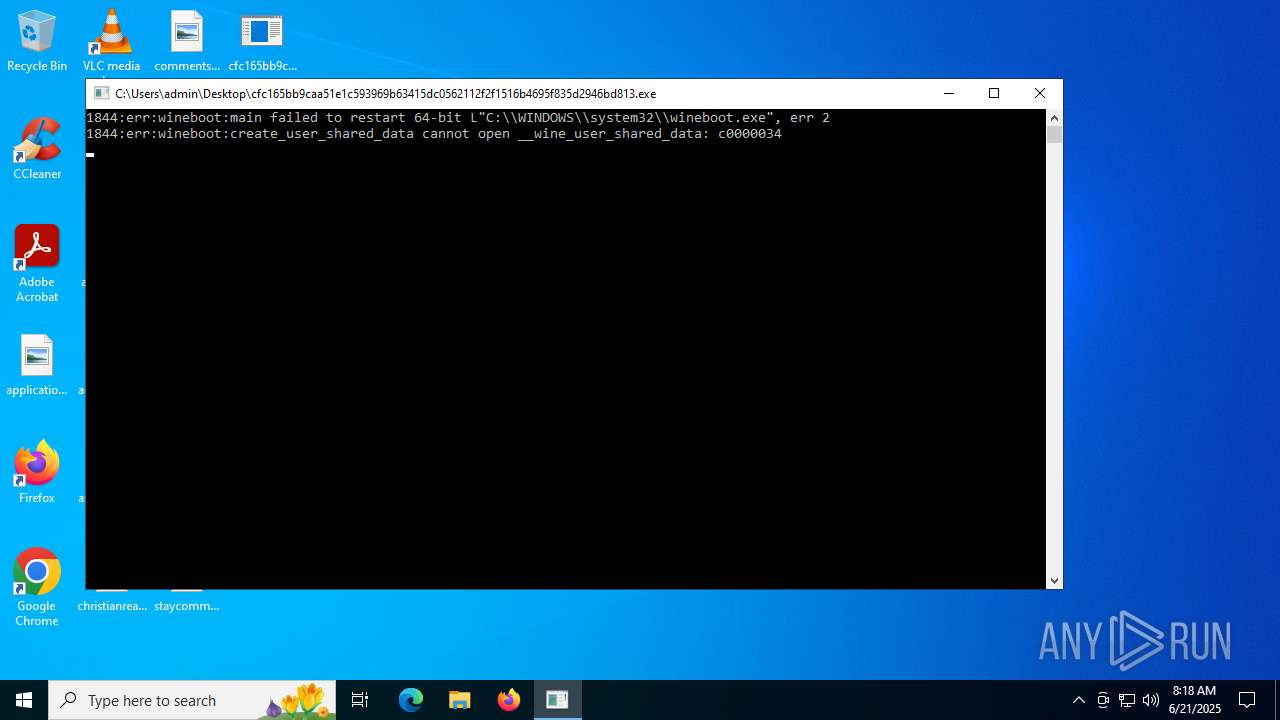
| File name: | cfc165bb9caa51e1c593969b63415dc0562112f2f1516b4695f835d2946bd813 |
| Full analysis: | https://app.any.run/tasks/c414dc5a-153e-4313-977a-5e08d97bbc21 |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 08:17:57 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386, for MS Windows, 6 sections |
| MD5: | 693E491EACFE20666F2A14983381EFCC |
| SHA1: | 9AC1FEF94C3365DB499666381450A76F2167B1AD |
| SHA256: | CFC165BB9CAA51E1C593969B63415DC0562112F2F1516B4695F835D2946BD813 |
| SSDEEP: | 3072:i+PFdbgKvKFHUGZ2lla0+gWtxRyyyP7NGjdX6wjWLgZj16:i+ddbgKvNGZ2LgPyyyPeswjWLgq |
MALICIOUS
Changes the autorun value in the registry
- CCleaner64.exe (PID: 4800)
SUSPICIOUS
Checks for Java to be installed
- jusched.exe (PID: 3872)
Reads security settings of Internet Explorer
- CCleaner64.exe (PID: 3504)
- cfc165bb9caa51e1c593969b63415dc0562112f2f1516b4695f835d2946bd813.exe (PID: 2952)
- CCleaner64.exe (PID: 4800)
Reads the date of Windows installation
- CCleaner64.exe (PID: 3504)
Reads Internet Explorer settings
- CCleaner64.exe (PID: 4800)
Application launched itself
- CCleaner64.exe (PID: 3504)
Executable content was dropped or overwritten
- CCleaner64.exe (PID: 4800)
Searches for installed software
- CCleaner64.exe (PID: 4800)
- CCleaner64.exe (PID: 5908)
The process verifies whether the antivirus software is installed
- CCleaner64.exe (PID: 4800)
Checks for external IP
- CCleaner64.exe (PID: 4800)
The process executes via Task Scheduler
- CCleaner.exe (PID: 3944)
INFO
Reads the computer name
- cfc165bb9caa51e1c593969b63415dc0562112f2f1516b4695f835d2946bd813.exe (PID: 2952)
- CCleaner64.exe (PID: 3504)
- OneDrive.exe (PID: 4512)
- CCleaner64.exe (PID: 4800)
- CCleaner64.exe (PID: 2512)
- CCleaner.exe (PID: 3944)
- CCleaner64.exe (PID: 5908)
Checks supported languages
- jusched.exe (PID: 3872)
- OneDrive.exe (PID: 4512)
- CCleaner64.exe (PID: 3504)
- CCleaner64.exe (PID: 4800)
- cfc165bb9caa51e1c593969b63415dc0562112f2f1516b4695f835d2946bd813.exe (PID: 2952)
- CCleaner64.exe (PID: 2512)
- CCleaner.exe (PID: 3944)
- CCleaner64.exe (PID: 5908)
Reads the machine GUID from the registry
- OneDrive.exe (PID: 4512)
- cfc165bb9caa51e1c593969b63415dc0562112f2f1516b4695f835d2946bd813.exe (PID: 2952)
- CCleaner64.exe (PID: 4800)
- CCleaner64.exe (PID: 5908)
Create files in a temporary directory
- OneDrive.exe (PID: 4512)
Application launched itself
- msedge.exe (PID: 4380)
- msedge.exe (PID: 3788)
Reads Environment values
- CCleaner64.exe (PID: 3504)
- CCleaner64.exe (PID: 4800)
- CCleaner64.exe (PID: 2512)
- CCleaner.exe (PID: 3944)
- CCleaner64.exe (PID: 5908)
Creates files or folders in the user directory
- OneDrive.exe (PID: 4512)
- CCleaner64.exe (PID: 4800)
Process checks computer location settings
- CCleaner64.exe (PID: 3504)
- cfc165bb9caa51e1c593969b63415dc0562112f2f1516b4695f835d2946bd813.exe (PID: 2952)
Reads CPU info
- OneDrive.exe (PID: 4512)
- CCleaner64.exe (PID: 4800)
- CCleaner64.exe (PID: 5908)
Creates files in the program directory
- CCleaner64.exe (PID: 4800)
Launching a file from a Registry key
- CCleaner64.exe (PID: 4800)
Reads product name
- CCleaner64.exe (PID: 4800)
Reads the time zone
- OneDrive.exe (PID: 4512)
Checks proxy server information
- CCleaner64.exe (PID: 4800)
- slui.exe (PID: 5928)
Manual execution by a user
- CCleaner64.exe (PID: 2512)
The sample compiled with english language support
- CCleaner64.exe (PID: 4800)
Reads the software policy settings
- CCleaner64.exe (PID: 4800)
- CCleaner64.exe (PID: 5908)
- slui.exe (PID: 5928)
Detects AutoHotkey samples (YARA)
- CCleaner64.exe (PID: 4800)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:02:28 21:52:37+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 28672 |
| InitializedDataSize: | 106496 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x6fd0 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
152
Monitored processes
16
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 504 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cfc165bb9caa51e1c593969b63415dc0562112f2f1516b4695f835d2946bd813.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1700 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --subproc-heap-profiling --always-read-main-dll --field-trial-handle=2812,i,10513694644189521590,286151666373898799,262144 --variations-seed-version --mojo-platform-channel-handle=2776 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2512 | "C:\Program Files\CCleaner\CCleaner64.exe" /MONITOR | C:\Program Files\CCleaner\CCleaner64.exe | — | explorer.exe | |||||||||||
User: admin Company: Piriform Software Ltd Integrity Level: MEDIUM Description: CCleaner Exit code: 0 Version: 6.20.0.10897 Modules
| |||||||||||||||
| 2952 | "C:\Users\admin\Desktop\cfc165bb9caa51e1c593969b63415dc0562112f2f1516b4695f835d2946bd813.exe" | C:\Users\admin\Desktop\cfc165bb9caa51e1c593969b63415dc0562112f2f1516b4695f835d2946bd813.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3504 | "C:\Program Files\CCleaner\CCleaner64.exe" /MONITOR | C:\Program Files\CCleaner\CCleaner64.exe | — | cfc165bb9caa51e1c593969b63415dc0562112f2f1516b4695f835d2946bd813.exe | |||||||||||
User: admin Company: Piriform Software Ltd Integrity Level: MEDIUM Description: CCleaner Exit code: 0 Version: 6.20.0.10897 Modules
| |||||||||||||||
| 3788 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --no-startup-window --win-session-start --edge-skip-compat-layer-relaunch | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 3872 | "C:\Program Files (x86)\Common Files\Java\Java Update\jusched.exe" | C:\Program Files (x86)\Common Files\Java\Java Update\jusched.exe | — | cfc165bb9caa51e1c593969b63415dc0562112f2f1516b4695f835d2946bd813.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java Update Scheduler Exit code: 4294967292 Version: 2.8.271.9 Modules
| |||||||||||||||
| 3872 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=133.0.6943.142 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 --annotation=prod=Edge --annotation=ver=133.0.3065.92 --initial-client-data=0x29c,0x2a0,0x2a4,0x290,0x298,0x7ffc43a1f208,0x7ffc43a1f214,0x7ffc43a1f220 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 3944 | "C:\Program Files\CCleaner\CCleaner.exe" /MONITOR /uac | C:\Program Files\CCleaner\CCleaner.exe | — | svchost.exe | |||||||||||
User: admin Company: Piriform Software Ltd Integrity Level: HIGH Description: CCleaner Exit code: 0 Version: 6.20.0.10897 Modules
| |||||||||||||||
| 3964 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --subproc-heap-profiling --always-read-main-dll --field-trial-handle=2216,i,10513694644189521590,286151666373898799,262144 --variations-seed-version --mojo-platform-channel-handle=856 /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
Total events
20 205
Read events
20 166
Write events
31
Delete events
8
Modification events
| (PID) Process: | (2952) cfc165bb9caa51e1c593969b63415dc0562112f2f1516b4695f835d2946bd813.exe | Key: | HKEY_CURRENT_USER\Volatile Environment |
| Operation: | write | Name: | APPDATA |
Value: C:\Users\admin\AppData\Roaming | |||
| (PID) Process: | (2952) cfc165bb9caa51e1c593969b63415dc0562112f2f1516b4695f835d2946bd813.exe | Key: | HKEY_CURRENT_USER\Volatile Environment |
| Operation: | write | Name: | CLIENTNAME |
Value: Console | |||
| (PID) Process: | (2952) cfc165bb9caa51e1c593969b63415dc0562112f2f1516b4695f835d2946bd813.exe | Key: | HKEY_CURRENT_USER\Volatile Environment |
| Operation: | write | Name: | USERPROFILE |
Value: C:\Users\admin | |||
| (PID) Process: | (2952) cfc165bb9caa51e1c593969b63415dc0562112f2f1516b4695f835d2946bd813.exe | Key: | HKEY_CURRENT_USER\Volatile Environment |
| Operation: | write | Name: | HOMEPATH |
Value: \Users\admin | |||
| (PID) Process: | (2952) cfc165bb9caa51e1c593969b63415dc0562112f2f1516b4695f835d2946bd813.exe | Key: | HKEY_CURRENT_USER\Volatile Environment |
| Operation: | write | Name: | HOMEDRIVE |
Value: C: | |||
| (PID) Process: | (2952) cfc165bb9caa51e1c593969b63415dc0562112f2f1516b4695f835d2946bd813.exe | Key: | HKEY_CURRENT_USER\Volatile Environment |
| Operation: | write | Name: | USERNAME |
Value: admin | |||
| (PID) Process: | (2952) cfc165bb9caa51e1c593969b63415dc0562112f2f1516b4695f835d2946bd813.exe | Key: | HKEY_CURRENT_USER\Volatile Environment |
| Operation: | write | Name: | HOMESHARE |
Value: | |||
| (PID) Process: | (2952) cfc165bb9caa51e1c593969b63415dc0562112f2f1516b4695f835d2946bd813.exe | Key: | HKEY_CURRENT_USER\Volatile Environment |
| Operation: | write | Name: | LOCALAPPDATA |
Value: C:\Users\admin\AppData\Local | |||
| (PID) Process: | (2952) cfc165bb9caa51e1c593969b63415dc0562112f2f1516b4695f835d2946bd813.exe | Key: | HKEY_CURRENT_USER\Volatile Environment |
| Operation: | write | Name: | USERDOMAIN |
Value: DESKTOP-JGLLJLD | |||
| (PID) Process: | (2952) cfc165bb9caa51e1c593969b63415dc0562112f2f1516b4695f835d2946bd813.exe | Key: | HKEY_CURRENT_USER\Volatile Environment |
| Operation: | write | Name: | LOGONSERVER |
Value: \\DESKTOP-JGLLJLD | |||
Executable files
2
Suspicious files
28
Text files
27
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3788 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF177e77.TMP | — | |
MD5:— | SHA256:— | |||
| 3788 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3788 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF177e77.TMP | — | |
MD5:— | SHA256:— | |||
| 4512 | OneDrive.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\logs\Personal\TraceCurrent.0304.0013.etl | binary | |
MD5:8BBB0EB3E0FDB2C6C607BB0552EAD49F | SHA256:0C99E3486108CD83E1AACABAB8CC584497EB403C87F29BAC3FD8E0E5509D628E | |||
| 3788 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4512 | OneDrive.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\logs\Personal\SyncEngine-2025-06-21.0818.4512.1.aodl | binary | |
MD5:28DCA2FF4B34B5A52A2E59DF202A6ED3 | SHA256:33BACCB7296F1ED1F995FC77A23049F261CF391AC0388F9E8DD161F8C17B7F94 | |||
| 3788 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\352d0c01-c9d9-4f0a-90e1-2cd5700f3777.tmp | binary | |
MD5:FA70DD4B3BE6509D2597510FB8F2BAA5 | SHA256:2376BAF4F0CB8C26A5587D36E34ACBC8267AF6CF191D445FFEC4105B08938947 | |||
| 3788 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Variations | binary | |
MD5:CDDDC745A8C954DC438C931889999BDB | SHA256:3DC9043838386F5363AC96A01477CF3163B5118B80191576A11B32CE9894314C | |||
| 3788 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old~RF177e96.TMP | — | |
MD5:— | SHA256:— | |||
| 3788 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
53
TCP/UDP connections
53
DNS requests
27
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.55.104.172:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4708 | RUXIMICS.exe | GET | 200 | 23.55.104.172:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.55.104.172:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4708 | RUXIMICS.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4800 | CCleaner64.exe | GET | 200 | 23.200.87.13:80 | http://ncc.avast.com/ncc.txt | unknown | — | — | whitelisted |
— | — | POST | 200 | 34.117.223.223:443 | https://analytics.avcdn.net/receive3 | unknown | text | 24 b | whitelisted |
— | — | GET | 200 | 34.111.175.102:443 | https://ip-info.ff.avast.com/v1/info | unknown | binary | 322 b | whitelisted |
— | — | POST | 200 | 40.126.31.131:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4708 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.55.104.172:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
4708 | RUXIMICS.exe | 23.55.104.172:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
1268 | svchost.exe | 23.55.104.172:80 | crl.microsoft.com | Akamai International B.V. | US | whitelisted |
5944 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ncc.avast.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
analytics.avcdn.net |
| whitelisted |
ip-info.ff.avast.com |
| whitelisted |
login.live.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Misc activity | ET INFO External IP Lookup Service in DNS Query (ip-info .ff .avast .com) |
4800 | CCleaner64.exe | Misc activity | ET INFO Observed External IP Lookup Domain (ip-info .ff .avast .com) in TLS SNI |
— | — | Potential Corporate Privacy Violation | ET INFO External IP Lookup (avast .com) |
Process | Message |
|---|---|
CCleaner64.exe | [2025-06-21 08:18:09.691] [error ] [settings ] [ 4800: 2976] [000000: 0] Failed to get program directory
Exception: Unable to determine program folder of product 'piriform-cc'!
Code: 0x000000c0 (192)
|
CCleaner64.exe | [2025-06-21 08:18:09.691] [error ] [ini_access ] [ 4800: 2976] [000000: 0] Incorrect ini_accessor configuration! Fixing relative input path to avoid recursion. Input was: Setup
|
CCleaner64.exe | Failed to open log file 'C:\Program Files\CCleaner' |
CCleaner64.exe | OnLanguage - en
|
CCleaner64.exe | [2025-06-21 08:18:18.832] [error ] [settings ] [ 5908: 4196] [000000: 0] Failed to get program directory
Exception: Unable to determine program folder of product 'piriform-cc'!
Code: 0x000000c0 (192)
|
CCleaner64.exe | [2025-06-21 08:18:20.003] [error ] [ini_access ] [ 5908: 4196] [000000: 0] Incorrect ini_accessor configuration! Fixing relative input path to avoid recursion. Input was: Setup
|
CCleaner64.exe | Failed to open log file 'C:\Program Files\CCleaner' |