| File name: | brainrot.bat |
| Full analysis: | https://app.any.run/tasks/b3d1d652-cfe5-4198-b14d-5edc40efa175 |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | July 23, 2025, 14:04:32 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text |
| MD5: | 552F258D079637F467F1ACE689BBBFB9 |
| SHA1: | 5D88CB5111A76F82520964AB7CB79A8766F8F244 |
| SHA256: | CFBACD9DB5432307629B7C45475D6AEB664EC460E4E12B2A2DFB4B568B903AF0 |
| SSDEEP: | 24:gjMGYpTTQOhlo5/JtDSMCIWxJzlb4ajOcOQvH/cHIa7MGQPv:zx9TQclo97PWjRJtgtlo |
MALICIOUS
Changes the autorun value in the registry
- CCleaner64.exe (PID: 8732)
- CCUpdate.exe (PID: 7776)
Scans artifacts that could help determine the target
- OfficeC2RClient.exe (PID: 8608)
- IntegratedOffice.exe (PID: 8972)
- OfficeC2RClient.exe (PID: 9116)
- IntegratedOffice.exe (PID: 8520)
- Integrator.exe (PID: 12240)
SUSPICIOUS
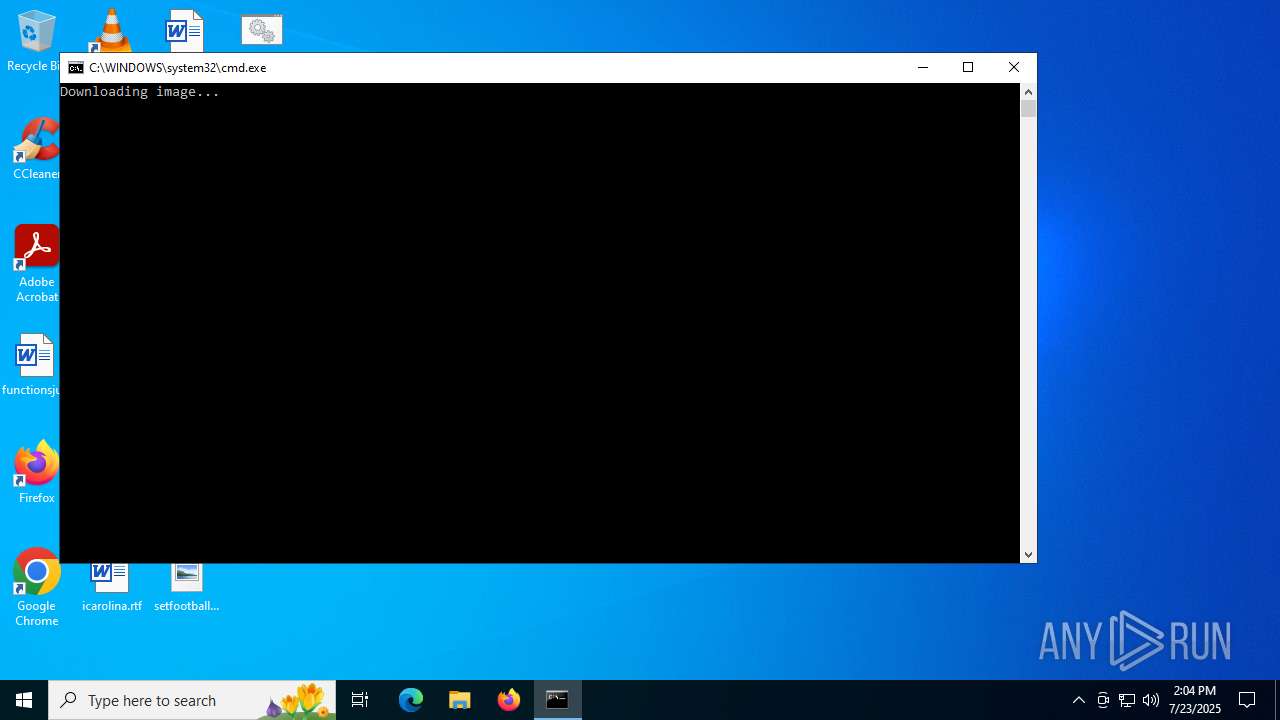
Downloads file from URI via Powershell
- powershell.exe (PID: 6876)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6948)
Imports DLL using pinvoke
- powershell.exe (PID: 5284)
CSC.EXE is used to compile C# code
- csc.exe (PID: 4884)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6948)
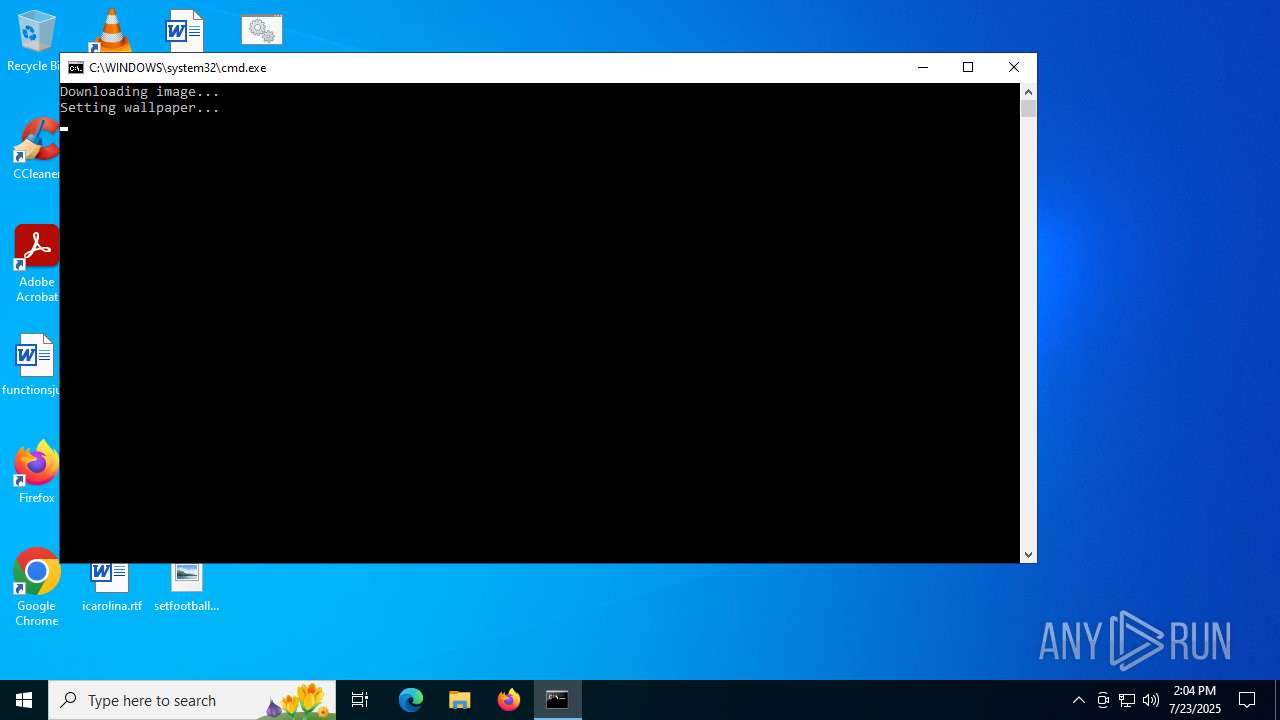
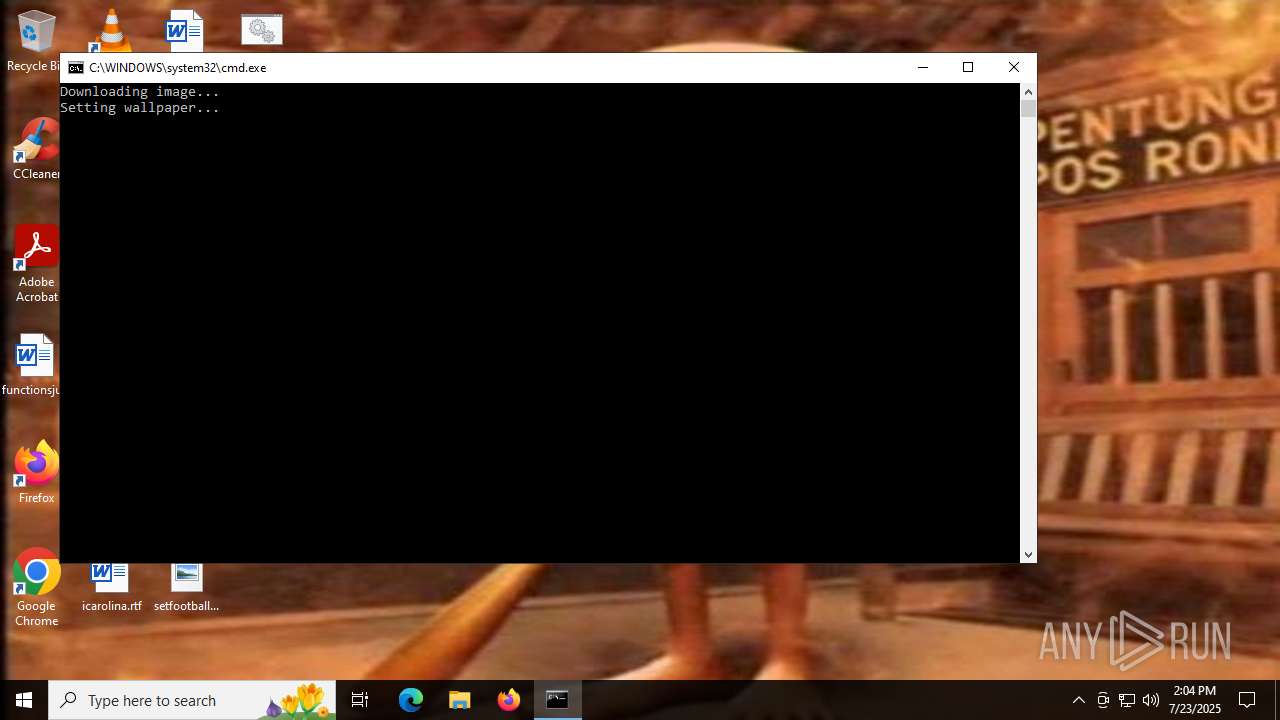
Changes the desktop background image
- reg.exe (PID: 3100)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 6948)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 6948)
Executable content was dropped or overwritten
- csc.exe (PID: 4884)
- uninst.exe (PID: 7656)
- CCleaner64.exe (PID: 7892)
- CCleaner64.exe (PID: 7792)
- Un_A.exe (PID: 8008)
- WindowsInstaller-KB893803-v2-x86.exe (PID: 8168)
- WindowsInstaller-KB893803-v2-x86.exe (PID: 8452)
- CCleaner64.exe (PID: 8732)
- uninstall.exe (PID: 9856)
- Un_A.exe (PID: 10068)
Application launched itself
- AdobeCollabSync.exe (PID: 5600)
- Acrobat.exe (PID: 7792)
- CCleaner64.exe (PID: 8072)
- CCleaner64.exe (PID: 8052)
- CCleaner64.exe (PID: 7792)
- CCleaner64.exe (PID: 7892)
- setup.exe (PID: 10092)
- msiexec.exe (PID: 8444)
Reads security settings of Internet Explorer
- Eula.exe (PID: 6236)
- AdobeCollabSync.exe (PID: 436)
- AdobeCollabSync.exe (PID: 5600)
- CCleaner64.exe (PID: 8072)
- CCleaner64.exe (PID: 8052)
- CCleaner64.exe (PID: 7792)
- CCleaner64.exe (PID: 7892)
- IntegratedOffice.exe (PID: 8520)
- OfficeC2RClient.exe (PID: 8680)
- OfficeC2RClient.exe (PID: 9036)
- OfficeClickToRun.exe (PID: 9044)
- OfficeC2RClient.exe (PID: 8608)
- IntegratedOffice.exe (PID: 8972)
- OfficeC2RClient.exe (PID: 9116)
- officesvcmgr.exe (PID: 8844)
- culauncher.exe (PID: 9784)
- CCleaner64.exe (PID: 8732)
- filezilla.exe (PID: 9796)
- iediagcmd.exe (PID: 9536)
- Integrator.exe (PID: 12240)
- msiexec.exe (PID: 10652)
Reads Microsoft Outlook installation path
- Eula.exe (PID: 6236)
Reads Internet Explorer settings
- Eula.exe (PID: 6236)
- CCleaner64.exe (PID: 7892)
- CCleaner64.exe (PID: 7792)
- CCleaner64.exe (PID: 8732)
- iediagcmd.exe (PID: 9536)
Executes application which crashes
- adobe_licensing_wf_helper_acro.exe (PID: 1160)
- chrome_pwa_launcher.exe (PID: 10048)
Reads the date of Windows installation
- CCleaner64.exe (PID: 8072)
- CCleaner64.exe (PID: 8052)
- CCleaner64.exe (PID: 7792)
- CCleaner64.exe (PID: 7892)
Starts itself from another location
- uninst.exe (PID: 7656)
- uninstall.exe (PID: 9856)
Checks for external IP
- CCUpdate.exe (PID: 7776)
- CCleaner64.exe (PID: 7892)
- CCleaner64.exe (PID: 7792)
Malware-specific behavior (creating "System.dll" in Temp)
- Un_A.exe (PID: 8008)
The process creates files with name similar to system file names
- Un_A.exe (PID: 8008)
- WindowsInstaller-KB893803-v2-x86.exe (PID: 8168)
- WindowsInstaller-KB893803-v2-x86.exe (PID: 8452)
Searches for installed software
- CCleaner64.exe (PID: 7792)
- CCleaner64.exe (PID: 7892)
- OfficeC2RClient.exe (PID: 8608)
- OfficeC2RClient.exe (PID: 9116)
- CCleaner64.exe (PID: 8752)
- CCleaner64.exe (PID: 8732)
- CCleaner64.exe (PID: 5928)
- CCleaner64.exe (PID: 10324)
Process drops legitimate windows executable
- WindowsInstaller-KB893803-v2-x86.exe (PID: 8168)
- WindowsInstaller-KB893803-v2-x86.exe (PID: 8452)
Checks for Java to be installed
- ssvagent.exe (PID: 10300)
- jucheck.exe (PID: 10948)
- javaw.exe (PID: 10204)
Reads Mozilla Firefox installation path
- ssvagent.exe (PID: 10300)
- javaw.exe (PID: 10204)
Creates/Modifies COM task schedule object
- ssvagent.exe (PID: 10300)
- msiexec.exe (PID: 8444)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 8444)
The process executes via Task Scheduler
- CCleaner.exe (PID: 11132)
The process verifies whether the antivirus software is installed
- CCleaner64.exe (PID: 8732)
Uses ROUTE.EXE to obtain the routing table information
- iediagcmd.exe (PID: 9536)
Suspicious use of NETSH.EXE
- iediagcmd.exe (PID: 9536)
Process uses IPCONFIG to discover network configuration
- iediagcmd.exe (PID: 9536)
Changes default file association
- msiexec.exe (PID: 8444)
Disables SEHOP
- msiexec.exe (PID: 8444)
Changes Internet Explorer settings (feature browser emulation)
- msiexec.exe (PID: 8444)
Executes as Windows Service
- armsvc.exe (PID: 3836)
INFO
Disables trace logs
- powershell.exe (PID: 6876)
- netsh.exe (PID: 13260)
Checks proxy server information
- powershell.exe (PID: 6876)
- AdobeCollabSync.exe (PID: 436)
- AdobeCollabSync.exe (PID: 5600)
- Eula.exe (PID: 6236)
- msiexec.exe (PID: 7876)
- IntegratedOffice.exe (PID: 8520)
- CCleaner64.exe (PID: 7892)
- OfficeC2RClient.exe (PID: 8680)
- CCleaner64.exe (PID: 7792)
- OfficeC2RClient.exe (PID: 8608)
- OfficeClickToRun.exe (PID: 8744)
- OfficeC2RClient.exe (PID: 9036)
- OfficeC2RClient.exe (PID: 9116)
- OfficeClickToRun.exe (PID: 9044)
- IntegratedOffice.exe (PID: 8972)
- officesvcmgr.exe (PID: 8844)
- iediagcmd.exe (PID: 9536)
- WerFault.exe (PID: 7688)
- WerFault.exe (PID: 8772)
- Integrator.exe (PID: 12240)
- dxdiag.exe (PID: 10508)
- slui.exe (PID: 7384)
Checks supported languages
- csc.exe (PID: 4884)
- ADNotificationManager.exe (PID: 5628)
- ADelRCP.exe (PID: 2400)
- AdobeCollabSync.exe (PID: 5600)
- cvtres.exe (PID: 3556)
- AcroTextExtractor.exe (PID: 3460)
- AcrobatInfo.exe (PID: 6648)
- AcroBroker.exe (PID: 3740)
- acrobat_sl.exe (PID: 5188)
- Eula.exe (PID: 6236)
- AdobeCollabSync.exe (PID: 436)
- SingleClientServicesUpdater.exe (PID: 4724)
- CRLogTransport.exe (PID: 2976)
- adobe_licensing_wf_acro.exe (PID: 1180)
- adobe_licensing_wf_helper_acro.exe (PID: 1160)
- CRWindowsClientService.exe (PID: 4400)
- AcroCEF.exe (PID: 3488)
- SingleClientServicesUpdater.exe (PID: 856)
- 32BitMAPIBroker.exe (PID: 3112)
- WCChromeNativeMessagingHost.exe (PID: 1212)
- MSRMSPIBroker.exe (PID: 7540)
- FullTrustNotifier.exe (PID: 7596)
- Acrobat.exe (PID: 7792)
- Acrobat.exe (PID: 7916)
- 64BitMAPIBroker.exe (PID: 7460)
- CCleanerPerformanceOptimizerService.exe (PID: 8144)
- CCleanerBugReport.exe (PID: 8116)
- CCleaner.exe (PID: 7816)
- CCleaner64.exe (PID: 8052)
- CCleaner64.exe (PID: 8072)
- CCleanerReactivator.exe (PID: 8164)
- CCUpdate.exe (PID: 7776)
- CCleaner64.exe (PID: 7892)
- CCleaner64.exe (PID: 7792)
- uninst.exe (PID: 7656)
- wa_3rd_party_host_64.exe (PID: 7640)
- Un_A.exe (PID: 8008)
- setup.exe (PID: 8076)
- WindowsInstaller-KB893803-v2-x86.exe (PID: 8168)
- Setup.exe (PID: 8240)
- update.exe (PID: 8256)
- WindowsInstaller-KB893803-v2-x86.exe (PID: 8452)
- appvcleaner.exe (PID: 8484)
- AppVShNotify.exe (PID: 8496)
- IntegratedOffice.exe (PID: 8520)
- CCleaner64.exe (PID: 8752)
- OfficeC2RClient.exe (PID: 8608)
- OfficeC2RClient.exe (PID: 8680)
- msiexec.exe (PID: 8444)
- MavInject32.exe (PID: 8628)
- CCleaner64.exe (PID: 8732)
- OfficeClickToRun.exe (PID: 8744)
- MavInject32.exe (PID: 9008)
- AppVShNotify.exe (PID: 8940)
- InspectorOfficeGadget.exe (PID: 8504)
- appvcleaner.exe (PID: 8884)
- update.exe (PID: 9000)
- InputPersonalization.exe (PID: 7724)
- IMESharePointDictionary.exe (PID: 9100)
- OfficeC2RClient.exe (PID: 9036)
- IntegratedOffice.exe (PID: 8972)
- ShapeCollector.exe (PID: 8296)
- OfficeClickToRun.exe (PID: 9044)
- officesvcmgr.exe (PID: 8844)
- InspectorOfficeGadget.exe (PID: 8948)
- OfficeC2RClient.exe (PID: 9116)
- ShapeCollector.exe (PID: 9268)
- officesvcmgr.exe (PID: 9052)
- mip.exe (PID: 7704)
- LICLUA.EXE (PID: 9760)
- TabTip.exe (PID: 9688)
- culauncher.exe (PID: 9784)
- msinfo32.exe (PID: 9728)
- uninstall.exe (PID: 9856)
- VSTOInstaller.exe (PID: 9772)
- filezilla.exe (PID: 9796)
- chrome_pwa_launcher.exe (PID: 10048)
- Un_A.exe (PID: 10068)
- fzsftp.exe (PID: 9820)
- elevated_tracing_service.exe (PID: 10120)
- InputPersonalization.exe (PID: 10140)
- fzputtygen.exe (PID: 9804)
- elevation_service.exe (PID: 9204)
- notification_helper.exe (PID: 9660)
- os_update_handler.exe (PID: 9712)
- chrome_proxy.exe (PID: 10036)
- fzstorj.exe (PID: 9832)
- setup.exe (PID: 10092)
- ExtExport.exe (PID: 10232)
- setup.exe (PID: 10016)
- ieinstal.exe (PID: 10144)
- ielowutil.exe (PID: 3932)
- javacpl.exe (PID: 9040)
- javaws.exe (PID: 9440)
- jabswitch.exe (PID: 1356)
- jp2launcher.exe (PID: 10460)
- iediagcmd.exe (PID: 9536)
- java-rmi.exe (PID: 3820)
- java.exe (PID: 6420)
- jjs.exe (PID: 8788)
- javaw.exe (PID: 10200)
- policytool.exe (PID: 10860)
- pack200.exe (PID: 10852)
- ktab.exe (PID: 10836)
- kinit.exe (PID: 10812)
- orbd.exe (PID: 10844)
- ssvagent.exe (PID: 10300)
- keytool.exe (PID: 10656)
- rmiregistry.exe (PID: 10880)
- klist.exe (PID: 10828)
- servertool.exe (PID: 11240)
- unpack200.exe (PID: 10224)
- rmid.exe (PID: 10872)
- tnameserv.exe (PID: 8984)
- AppVDllSurrogate32.exe (PID: 11612)
- AppVLP.exe (PID: 12100)
- AppVDllSurrogate.exe (PID: 11272)
- OSPPREARM.EXE (PID: 8584)
- AppVDllSurrogate64.exe (PID: 11784)
- javaw.exe (PID: 10204)
- msiexec.exe (PID: 11468)
- jucheck.exe (PID: 10948)
- Integrator.exe (PID: 12240)
- msiexec.exe (PID: 11612)
- CCleaner64.exe (PID: 5400)
- msiexec.exe (PID: 10280)
- CCleaner.exe (PID: 11132)
- CCleaner64.exe (PID: 5928)
- identity_helper.exe (PID: 12576)
- msiexec.exe (PID: 10652)
- MSIB4EA.tmp (PID: 10536)
- SingleClientServicesUpdater.exe (PID: 12508)
- msiexec.exe (PID: 12948)
- armsvc.exe (PID: 3836)
- makecab.exe (PID: 12852)
- CCleaner64.exe (PID: 10324)
Reads the machine GUID from the registry
- csc.exe (PID: 4884)
- AdobeCollabSync.exe (PID: 436)
- CCUpdate.exe (PID: 7776)
- CCleanerBugReport.exe (PID: 8116)
- CCleaner64.exe (PID: 7792)
- CCleaner64.exe (PID: 7892)
- WindowsInstaller-KB893803-v2-x86.exe (PID: 8168)
- appvcleaner.exe (PID: 8484)
- WindowsInstaller-KB893803-v2-x86.exe (PID: 8452)
- InspectorOfficeGadget.exe (PID: 8504)
- appvcleaner.exe (PID: 8884)
- CCleaner64.exe (PID: 8752)
- CCleaner64.exe (PID: 8732)
- IntegratedOffice.exe (PID: 8520)
- InspectorOfficeGadget.exe (PID: 8948)
- IntegratedOffice.exe (PID: 8972)
- OfficeC2RClient.exe (PID: 9036)
- culauncher.exe (PID: 9784)
- officesvcmgr.exe (PID: 8844)
- OfficeClickToRun.exe (PID: 9044)
- VSTOInstaller.exe (PID: 9772)
- javaw.exe (PID: 10204)
- rmiregistry.exe (PID: 10880)
- orbd.exe (PID: 10844)
- tnameserv.exe (PID: 8984)
- rmid.exe (PID: 10872)
- Integrator.exe (PID: 12240)
- CCleaner64.exe (PID: 5928)
- iediagcmd.exe (PID: 9536)
- CCleaner64.exe (PID: 10324)
Reads the computer name
- AcroBroker.exe (PID: 3740)
- AdobeCollabSync.exe (PID: 436)
- Eula.exe (PID: 6236)
- AdobeCollabSync.exe (PID: 5600)
- Acrobat.exe (PID: 7916)
- FullTrustNotifier.exe (PID: 7596)
- Acrobat.exe (PID: 7792)
- CCleaner64.exe (PID: 8072)
- CCleaner64.exe (PID: 8052)
- CCleanerPerformanceOptimizerService.exe (PID: 8144)
- CCleaner.exe (PID: 7816)
- CCUpdate.exe (PID: 7776)
- CCleaner64.exe (PID: 7892)
- CCleanerBugReport.exe (PID: 8116)
- CCleaner64.exe (PID: 7792)
- setup.exe (PID: 8076)
- Un_A.exe (PID: 8008)
- WindowsInstaller-KB893803-v2-x86.exe (PID: 8168)
- Setup.exe (PID: 8240)
- update.exe (PID: 8256)
- msiexec.exe (PID: 8444)
- AppVShNotify.exe (PID: 8496)
- IntegratedOffice.exe (PID: 8520)
- WindowsInstaller-KB893803-v2-x86.exe (PID: 8452)
- OfficeC2RClient.exe (PID: 8608)
- OfficeC2RClient.exe (PID: 8680)
- CCleaner64.exe (PID: 8732)
- CCleaner64.exe (PID: 8752)
- OfficeClickToRun.exe (PID: 8744)
- InspectorOfficeGadget.exe (PID: 8504)
- AppVShNotify.exe (PID: 8940)
- InputPersonalization.exe (PID: 7724)
- update.exe (PID: 9000)
- ShapeCollector.exe (PID: 8296)
- OfficeClickToRun.exe (PID: 9044)
- IntegratedOffice.exe (PID: 8972)
- officesvcmgr.exe (PID: 8844)
- mip.exe (PID: 7704)
- OfficeC2RClient.exe (PID: 9036)
- officesvcmgr.exe (PID: 9052)
- ShapeCollector.exe (PID: 9268)
- InspectorOfficeGadget.exe (PID: 8948)
- OfficeC2RClient.exe (PID: 9116)
- LICLUA.EXE (PID: 9760)
- msinfo32.exe (PID: 9728)
- culauncher.exe (PID: 9784)
- VSTOInstaller.exe (PID: 9772)
- elevated_tracing_service.exe (PID: 10120)
- InputPersonalization.exe (PID: 10140)
- Un_A.exe (PID: 10068)
- elevation_service.exe (PID: 9204)
- filezilla.exe (PID: 9796)
- setup.exe (PID: 10092)
- iediagcmd.exe (PID: 9536)
- javaw.exe (PID: 10204)
- orbd.exe (PID: 10844)
- rmiregistry.exe (PID: 10880)
- rmid.exe (PID: 10872)
- tnameserv.exe (PID: 8984)
- servertool.exe (PID: 11240)
- AppVLP.exe (PID: 12100)
- OSPPREARM.EXE (PID: 8584)
- policytool.exe (PID: 10860)
- jucheck.exe (PID: 10948)
- Integrator.exe (PID: 12240)
- msiexec.exe (PID: 11468)
- msiexec.exe (PID: 10280)
- msiexec.exe (PID: 11612)
- CCleaner64.exe (PID: 5400)
- CCleaner.exe (PID: 11132)
- CCleaner64.exe (PID: 5928)
- msiexec.exe (PID: 10652)
- MSIB4EA.tmp (PID: 10536)
- identity_helper.exe (PID: 12576)
- armsvc.exe (PID: 3836)
- msiexec.exe (PID: 12948)
- CCleaner64.exe (PID: 10324)
Application launched itself
- Acrobat.exe (PID: 3112)
- Acrobat.exe (PID: 4476)
- AcroCEF.exe (PID: 3572)
- chrome.exe (PID: 10128)
- chrome.exe (PID: 10024)
- chrmstp.exe (PID: 9892)
- chrome.exe (PID: 10160)
- chrome.exe (PID: 10120)
- msedge.exe (PID: 10664)
Create files in a temporary directory
- cvtres.exe (PID: 3556)
- csc.exe (PID: 4884)
- uninst.exe (PID: 7656)
- Un_A.exe (PID: 8008)
- OfficeC2RClient.exe (PID: 8608)
- OfficeC2RClient.exe (PID: 9036)
- OfficeC2RClient.exe (PID: 9116)
- OfficeC2RClient.exe (PID: 8680)
- OfficeClickToRun.exe (PID: 8744)
- uninstall.exe (PID: 9856)
- Un_A.exe (PID: 10068)
- IntegratedOffice.exe (PID: 8520)
- IntegratedOffice.exe (PID: 8972)
- javaw.exe (PID: 10200)
- OfficeClickToRun.exe (PID: 9044)
- jjs.exe (PID: 8788)
- java-rmi.exe (PID: 3820)
- java.exe (PID: 6420)
- javaw.exe (PID: 10204)
- ktab.exe (PID: 10836)
- pack200.exe (PID: 10852)
- rmid.exe (PID: 10872)
- orbd.exe (PID: 10844)
- rmiregistry.exe (PID: 10880)
- keytool.exe (PID: 10656)
- policytool.exe (PID: 10860)
- klist.exe (PID: 10828)
- tnameserv.exe (PID: 8984)
- kinit.exe (PID: 10812)
- servertool.exe (PID: 11240)
- jucheck.exe (PID: 10948)
- Integrator.exe (PID: 12240)
- dxdiag.exe (PID: 10508)
- iediagcmd.exe (PID: 9536)
- makecab.exe (PID: 12852)
Creates files or folders in the user directory
- AdobeCollabSync.exe (PID: 436)
- msiexec.exe (PID: 7876)
- filezilla.exe (PID: 9796)
- CCleaner64.exe (PID: 7892)
- CCleaner64.exe (PID: 7792)
- OfficeC2RClient.exe (PID: 9036)
- OfficeClickToRun.exe (PID: 9044)
- officesvcmgr.exe (PID: 8844)
- javaw.exe (PID: 10204)
- OfficeC2RClient.exe (PID: 8608)
- WerFault.exe (PID: 7688)
- IntegratedOffice.exe (PID: 8520)
- InputPersonalization.exe (PID: 7724)
- WerFault.exe (PID: 8772)
- Integrator.exe (PID: 12240)
- dxdiag.exe (PID: 10508)
- iediagcmd.exe (PID: 9536)
- OfficeC2RClient.exe (PID: 9116)
Reads Environment values
- CCleaner64.exe (PID: 8072)
- CCleaner64.exe (PID: 8052)
- CCleaner.exe (PID: 7816)
- CCleaner64.exe (PID: 7892)
- CCleaner64.exe (PID: 7792)
- CCleaner64.exe (PID: 8752)
- culauncher.exe (PID: 9784)
- CCleaner64.exe (PID: 8732)
- IntegratedOffice.exe (PID: 8520)
- OfficeC2RClient.exe (PID: 8608)
- IntegratedOffice.exe (PID: 8972)
- OfficeC2RClient.exe (PID: 9116)
- OSPPREARM.EXE (PID: 8584)
- CCleaner64.exe (PID: 5400)
- msiexec.exe (PID: 11612)
- CCleaner.exe (PID: 11132)
- CCleaner64.exe (PID: 5928)
- identity_helper.exe (PID: 12576)
- Integrator.exe (PID: 12240)
- CCleaner64.exe (PID: 10324)
Process checks computer location settings
- CCleaner64.exe (PID: 8072)
- CCleaner64.exe (PID: 8052)
- CCleaner64.exe (PID: 7892)
- IntegratedOffice.exe (PID: 8520)
- CCleaner64.exe (PID: 7792)
- OfficeC2RClient.exe (PID: 8608)
- OfficeC2RClient.exe (PID: 8680)
- IntegratedOffice.exe (PID: 8972)
- OfficeClickToRun.exe (PID: 9044)
- OfficeC2RClient.exe (PID: 9036)
- OfficeC2RClient.exe (PID: 9116)
- Integrator.exe (PID: 12240)
Reads the software policy settings
- CCUpdate.exe (PID: 7776)
- CCleaner64.exe (PID: 7792)
- CCleaner64.exe (PID: 7892)
- msiexec.exe (PID: 7876)
- IntegratedOffice.exe (PID: 8520)
- IntegratedOffice.exe (PID: 8972)
- OfficeC2RClient.exe (PID: 9036)
- CCleaner64.exe (PID: 8752)
- officesvcmgr.exe (PID: 8844)
- OfficeClickToRun.exe (PID: 9044)
- culauncher.exe (PID: 9784)
- CCleaner64.exe (PID: 8732)
- WerFault.exe (PID: 7688)
- dxdiag.exe (PID: 10508)
- WerFault.exe (PID: 8772)
- Integrator.exe (PID: 12240)
- CCleaner64.exe (PID: 5928)
- iediagcmd.exe (PID: 9536)
- CCleaner64.exe (PID: 10324)
- slui.exe (PID: 7384)
Reads CPU info
- CCleanerBugReport.exe (PID: 8116)
- CCleaner64.exe (PID: 7792)
- CCleaner64.exe (PID: 7892)
- CCleaner64.exe (PID: 8752)
- CCleaner64.exe (PID: 8732)
- Integrator.exe (PID: 12240)
- CCleaner64.exe (PID: 5928)
- CCleaner64.exe (PID: 10324)
The sample compiled with english language support
- uninst.exe (PID: 7656)
- CCleaner64.exe (PID: 7892)
- CCleaner64.exe (PID: 7792)
- WindowsInstaller-KB893803-v2-x86.exe (PID: 8168)
- WindowsInstaller-KB893803-v2-x86.exe (PID: 8452)
- CCleaner64.exe (PID: 8732)
- uninstall.exe (PID: 9856)
- msiexec.exe (PID: 7876)
- msiexec.exe (PID: 8444)
- msiexec.exe (PID: 10652)
Reads product name
- CCleaner64.exe (PID: 7792)
- CCleaner64.exe (PID: 7892)
- CCleaner64.exe (PID: 8732)
Creates files in the program directory
- CCleaner64.exe (PID: 7892)
- CCleaner64.exe (PID: 7792)
- CCUpdate.exe (PID: 7776)
- CCleaner64.exe (PID: 8732)
- javaw.exe (PID: 10200)
- SingleClientServicesUpdater.exe (PID: 12508)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 7876)
- dxdiag.exe (PID: 10508)
- netsh.exe (PID: 6420)
Reads Microsoft Office registry keys
- IntegratedOffice.exe (PID: 8520)
- OfficeClickToRun.exe (PID: 8744)
- OfficeC2RClient.exe (PID: 8608)
- OfficeC2RClient.exe (PID: 8680)
- OfficeClickToRun.exe (PID: 9044)
- OfficeC2RClient.exe (PID: 9036)
- OfficeC2RClient.exe (PID: 9116)
- IntegratedOffice.exe (PID: 8972)
- officesvcmgr.exe (PID: 8844)
- officesvcmgr.exe (PID: 9052)
- AppVLP.exe (PID: 12100)
- Integrator.exe (PID: 12240)
Launching a file from a Registry key
- CCleaner64.exe (PID: 8732)
- CCUpdate.exe (PID: 7776)
FileZilla executable
- cmd.exe (PID: 6948)
- uninstall.exe (PID: 9856)
Executable content was dropped or overwritten
- msiexec.exe (PID: 7876)
- msiexec.exe (PID: 8444)
- msiexec.exe (PID: 10652)
Manual execution by a user
- CCleaner64.exe (PID: 5400)
- ccupdate637_free.exe (PID: 11988)
Prints a route via ROUTE.EXE
- ROUTE.EXE (PID: 13196)
Starts application with an unusual extension
- msiexec.exe (PID: 8444)
Creates a software uninstall entry
- msiexec.exe (PID: 8444)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
441
Monitored processes
289
Malicious processes
17
Suspicious processes
10
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe" --type=renderer /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe | — | Acrobat.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Version: 23.1.20093.0 Modules
| |||||||||||||||
| 436 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\AdobeCollabSync.exe" --type=collab-renderer --proc=5600 | C:\Program Files\Adobe\Acrobat DC\Acrobat\AdobeCollabSync.exe | — | AdobeCollabSync.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Acrobat Collaboration Synchronizer 23.1 Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 856 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\AcroCEF\SingleClientServicesUpdater.exe" | C:\Program Files\Adobe\Acrobat DC\Acrobat\AcroCEF\SingleClientServicesUpdater.exe | — | cmd.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe WebInstaller 23.1 Exit code: 21 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1036 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --user-data-dir="C:\Users\admin\AppData\Local\CEF\User Data" --first-renderer-process --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --touch-events=enabled --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2280 --field-trial-handle=1636,i,9616329388690712125,8650463191164118700,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1100 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=entity_extraction_service.mojom.Extractor --lang=en-US --service-sandbox-type=entity_extraction --disable-quic --onnx-enabled-for-ee --string-annotations --always-read-main-dll --field-trial-handle=4344,i,10028209989747064442,17165656487277096358,262144 --variations-seed-version --mojo-platform-channel-handle=5272 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1160 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\NGL\cefWorkflow\adobe_licensing_wf_helper_acro.exe" | C:\Program Files\Adobe\Acrobat DC\Acrobat\NGL\cefWorkflow\adobe_licensing_wf_helper_acro.exe | cmd.exe | ||||||||||||
User: admin Company: Adobe Inc. Integrity Level: MEDIUM Description: Adobe Licensing WF Helper Exit code: 3228369022 Version: 1.6.0.4 Modules
| |||||||||||||||
| 1180 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\NGL\cefWorkflow\adobe_licensing_wf_acro.exe" | C:\Program Files\Adobe\Acrobat DC\Acrobat\NGL\cefWorkflow\adobe_licensing_wf_acro.exe | — | cmd.exe | |||||||||||
User: admin Company: Adobe Inc. Integrity Level: MEDIUM Description: Adobe Licensing WF Version: 1.6.0.4 Modules
| |||||||||||||||
| 1204 | reg add "HKEY_CURRENT_USER\Control Panel\Desktop" /v TileWallpaper /t REG_SZ /d 0 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1212 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\Browser\WCChromeExtn\WCChromeNativeMessagingHost.exe" | C:\Program Files\Adobe\Acrobat DC\Acrobat\Browser\WCChromeExtn\WCChromeNativeMessagingHost.exe | — | cmd.exe | |||||||||||
User: admin Company: Adobe Systems Inc. Integrity Level: MEDIUM Description: Adobe Create PDF plug-in listener for Chrome Exit code: 0 Version: 23.1.20064.0 Modules
| |||||||||||||||
| 1356 | "C:\Program Files\Java\jre1.8.0_271\bin\jabswitch.exe" | C:\Program Files\Java\jre1.8.0_271\bin\jabswitch.exe | — | cmd.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
Total events
235 442
Read events
229 530
Write events
5 646
Delete events
266
Modification events
| (PID) Process: | (3100) reg.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | WallpaperStyle |
Value: 2 | |||
| (PID) Process: | (1204) reg.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | TileWallpaper |
Value: 0 | |||
| (PID) Process: | (4476) Acrobat.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Mappings\S-1-15-2-2034283098-2252572593-1072577386-2659511007-3245387615-27016815-3920691934 |
| Operation: | write | Name: | DisplayName |
Value: Adobe Acrobat Reader Protected Mode | |||
| (PID) Process: | (3112) Acrobat.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Mappings\S-1-15-2-2034283098-2252572593-1072577386-2659511007-3245387615-27016815-3920691934 |
| Operation: | write | Name: | DisplayName |
Value: Adobe Acrobat Reader Protected Mode | |||
| (PID) Process: | (304) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
| (PID) Process: | (3540) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVGeneral |
| Operation: | write | Name: | iSLExitTimeHighPart |
Value: 31194074 | |||
| (PID) Process: | (3540) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\AVGeneral |
| Operation: | write | Name: | iSLExitTimeLowPart |
Value: | |||
| (PID) Process: | (3112) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\Privileged |
| Operation: | write | Name: | bProtectedMode |
Value: 1 | |||
| (PID) Process: | (2400) ADelRCP.exe | Key: | HKEY_CLASSES_ROOT\MIME\Database\Content Type\application/pdf |
| Operation: | write | Name: | CLSID |
Value: {CA8A9780-280D-11CF-A24D-444553540000} | |||
| (PID) Process: | (2400) ADelRCP.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 19 | |||
Executable files
133
Suspicious files
770
Text files
1 582
Unknown types
166
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3572 | AcroCEF.exe | C:\Users\admin\AppData\Local\Adobe\AcroCef\DC\Acrobat\Cache\000001.dbtmp | text | |
MD5:46295CAC801E5D4857D09837238A6394 | SHA256:0F1BAD70C7BD1E0A69562853EC529355462FCD0423263A3D39D6D0D70B780443 | |||
| 436 | AdobeCollabSync.exe | C:\Users\admin\AppData\LocalLow\Adobe\Acrobat\DC\Reader\Synchronizer\metadata\Synchronizer-journal | binary | |
MD5:BB7EA941A373A155923F7D2E65EFB48E | SHA256:6BE42761EC7AA2AC5A8EF6A61A4D373B31A47536A58761F2314D2A388FF0446C | |||
| 5284 | powershell.exe | C:\Users\admin\AppData\Local\Temp\q2qenyan.0.cs | text | |
MD5:148F3B294F8A93F5D18343D0A7BC7C82 | SHA256:78CBB3C37401A39E1D1F5EBEFF7744361A59ADAF970C9E0D0F840CA5A26A0985 | |||
| 5284 | powershell.exe | C:\Users\admin\AppData\Local\Temp\q2qenyan.cmdline | text | |
MD5:39C0D52AF8342F0095B5ABE7AEE87647 | SHA256:A3C2C4FD4E80F5A1582CCD53B6D85532A7A903A817E7733589FDCCB1D09F0F36 | |||
| 4884 | csc.exe | C:\Users\admin\AppData\Local\Temp\q2qenyan.dll | executable | |
MD5:E1DEFF202A9816D93448E1B404AB4591 | SHA256:C8ADE50C12AEC0A9FE26267039F94438F32A8C6F8B484301946CE8A5DC1BD777 | |||
| 4884 | csc.exe | C:\Users\admin\AppData\Local\Temp\q2qenyan.out | text | |
MD5:AA93C0307502B56973FE921CB3C3A406 | SHA256:92BD7616917DC9EB2EB4D6703CE3DD43697D1785488B208239FC161F3F02E62F | |||
| 3572 | AcroCEF.exe | C:\Users\admin\AppData\Local\Adobe\AcroCef\DC\Acrobat\Cache\CURRENT | text | |
MD5:46295CAC801E5D4857D09837238A6394 | SHA256:0F1BAD70C7BD1E0A69562853EC529355462FCD0423263A3D39D6D0D70B780443 | |||
| 4884 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSC608CAB8415624D38A5467E1140626021.TMP | res | |
MD5:2897B34A6CB3A19F214C150074420EE5 | SHA256:2B2ADD33F803BAB4D8211D10F3758408AA9D8F1220F5DF2907F485E5E15AEFFD | |||
| 6876 | powershell.exe | C:\Users\admin\Desktop\tung.jpg | image | |
MD5:BBF32199CAE75977052F6615F1B9520E | SHA256:86EB811C045DE2A464F8B6855600D096119B65878B6795FA664D5C489CBA31DB | |||
| 6876 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_anyl2fxu.ueb.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
228
TCP/UDP connections
167
DNS requests
110
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3572 | RUXIMICS.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3572 | RUXIMICS.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.190.159.131:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
— | — | GET | 200 | 140.82.121.4:443 | https://raw.githubusercontent.com/Suppy-spec/Image-hosting-/main/tung.jpeg | unknown | image | 56.3 Kb | whitelisted |
— | — | POST | 200 | 40.126.32.138:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 16.7 Kb | whitelisted |
— | — | POST | 400 | 40.126.32.138:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3572 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1268 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3572 | RUXIMICS.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
ip-info.ff.avast.com |
| whitelisted |
ncc.avast.com |
| whitelisted |
emupdate.avcdn.net |
| whitelisted |
ccleaner.tools.avcdn.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
2200 | svchost.exe | Misc activity | ET INFO External IP Lookup Service in DNS Query (ip-info .ff .avast .com) |
2200 | svchost.exe | Misc activity | ET INFO External IP Lookup Service in DNS Query (ip-info .ff .avast .com) |
7776 | CCUpdate.exe | Misc activity | ET INFO Observed External IP Lookup Domain (ip-info .ff .avast .com) in TLS SNI |
— | — | Potential Corporate Privacy Violation | ET INFO External IP Lookup (avast .com) |
7792 | CCleaner64.exe | Misc activity | ET INFO Observed External IP Lookup Domain (ip-info .ff .avast .com) in TLS SNI |
7892 | CCleaner64.exe | Misc activity | ET INFO Observed External IP Lookup Domain (ip-info .ff .avast .com) in TLS SNI |
— | — | Potential Corporate Privacy Violation | ET INFO External IP Lookup (avast .com) |
— | — | Potential Corporate Privacy Violation | ET INFO External IP Lookup (avast .com) |
Process | Message |
|---|---|
FullTrustNotifier.exe | |
FullTrustNotifier.exe | FullTrustNotifier |
FullTrustNotifier.exe | |
FullTrustNotifier.exe | FN NewNotifcationHasArrived from UWP |
FullTrustNotifier.exe | |
FullTrustNotifier.exe | FN ConnectToAppService create the async task |
FullTrustNotifier.exe | |
FullTrustNotifier.exe | |
FullTrustNotifier.exe | FullTrustNotifier Exit |
FullTrustNotifier.exe | FN ConnectToAppServiceAsync |