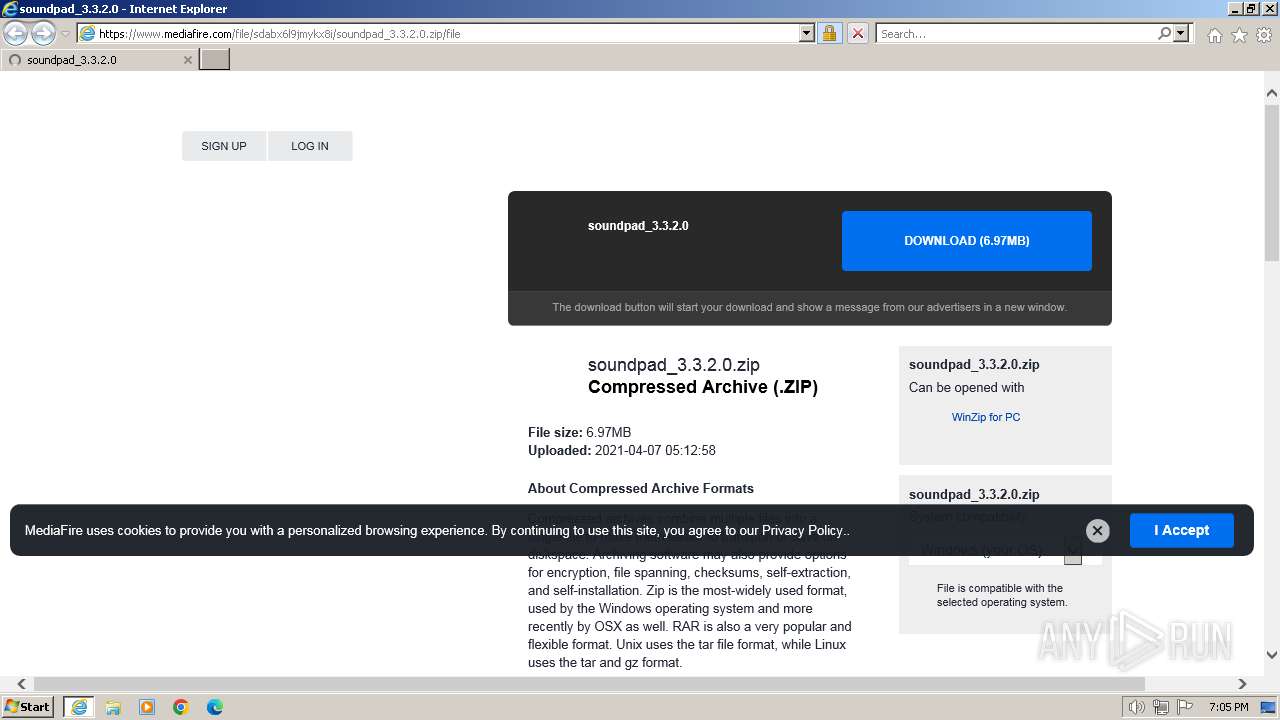
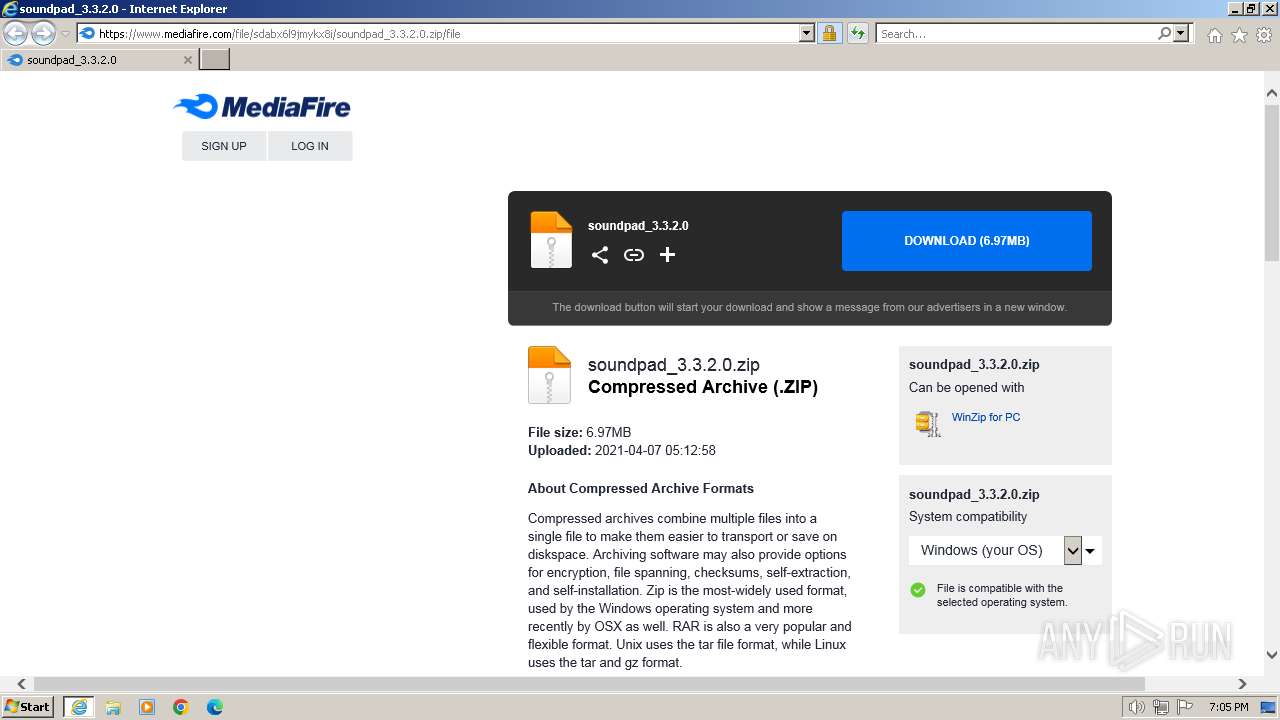
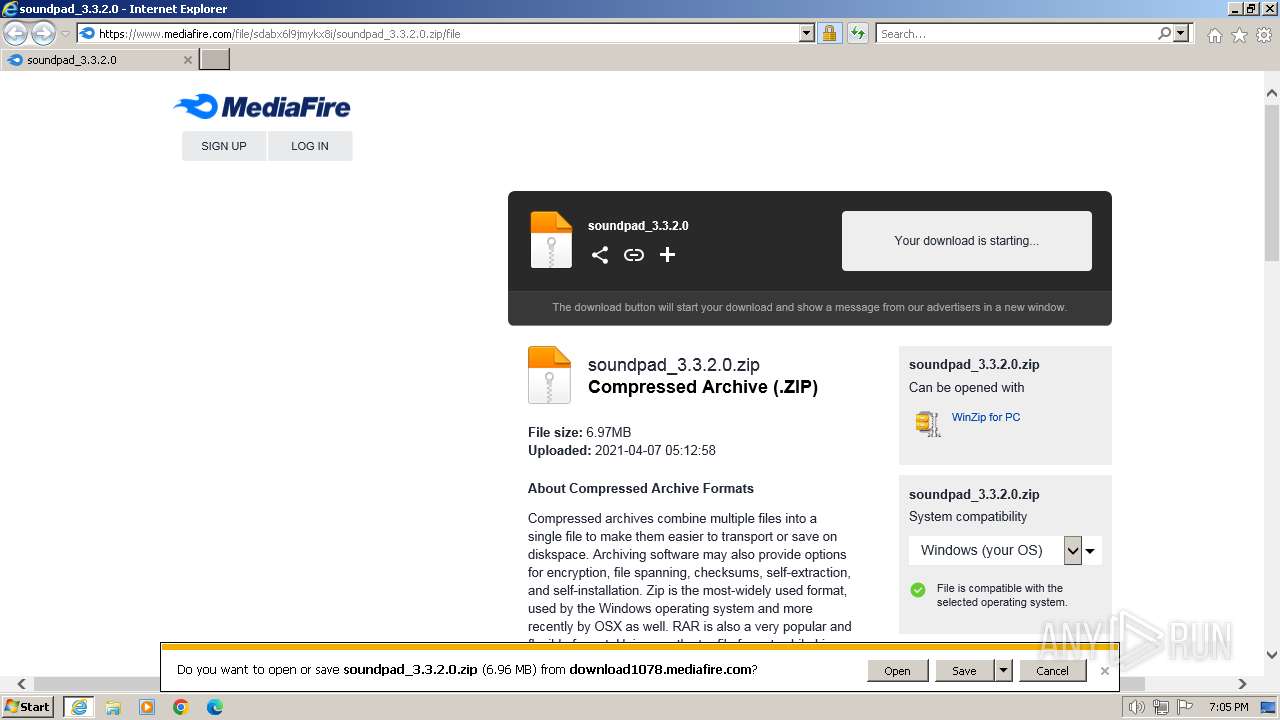
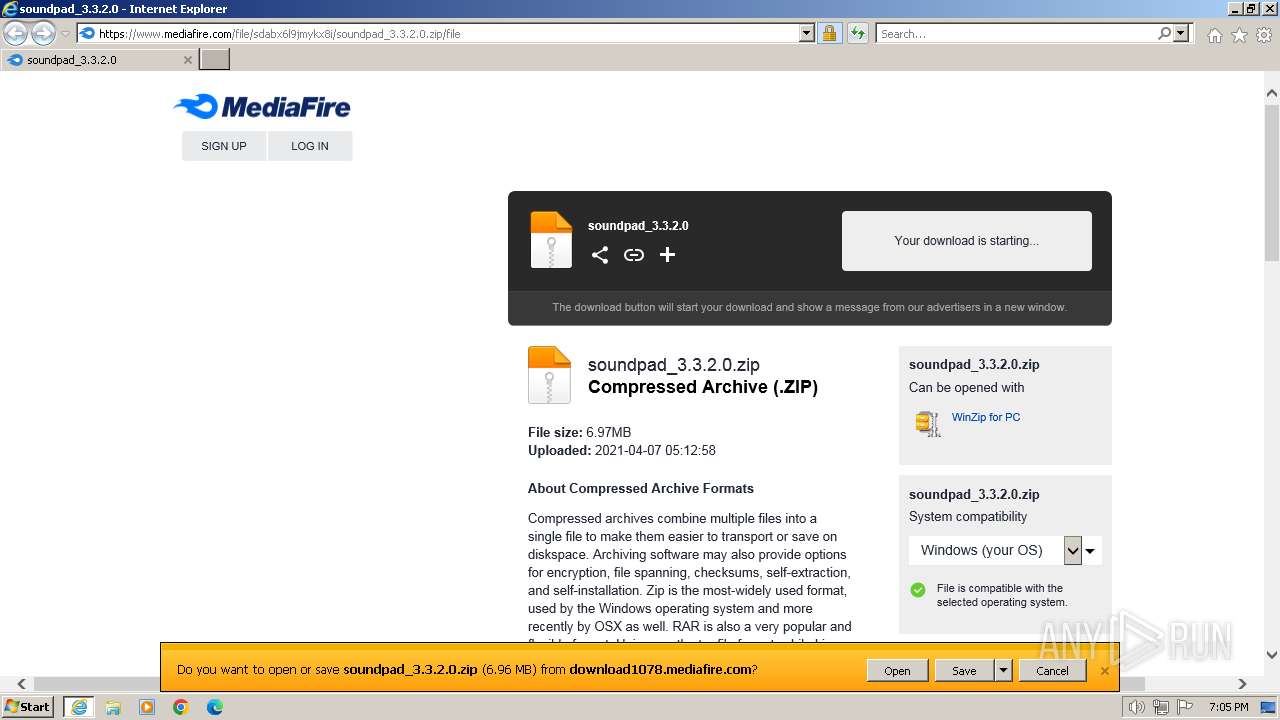
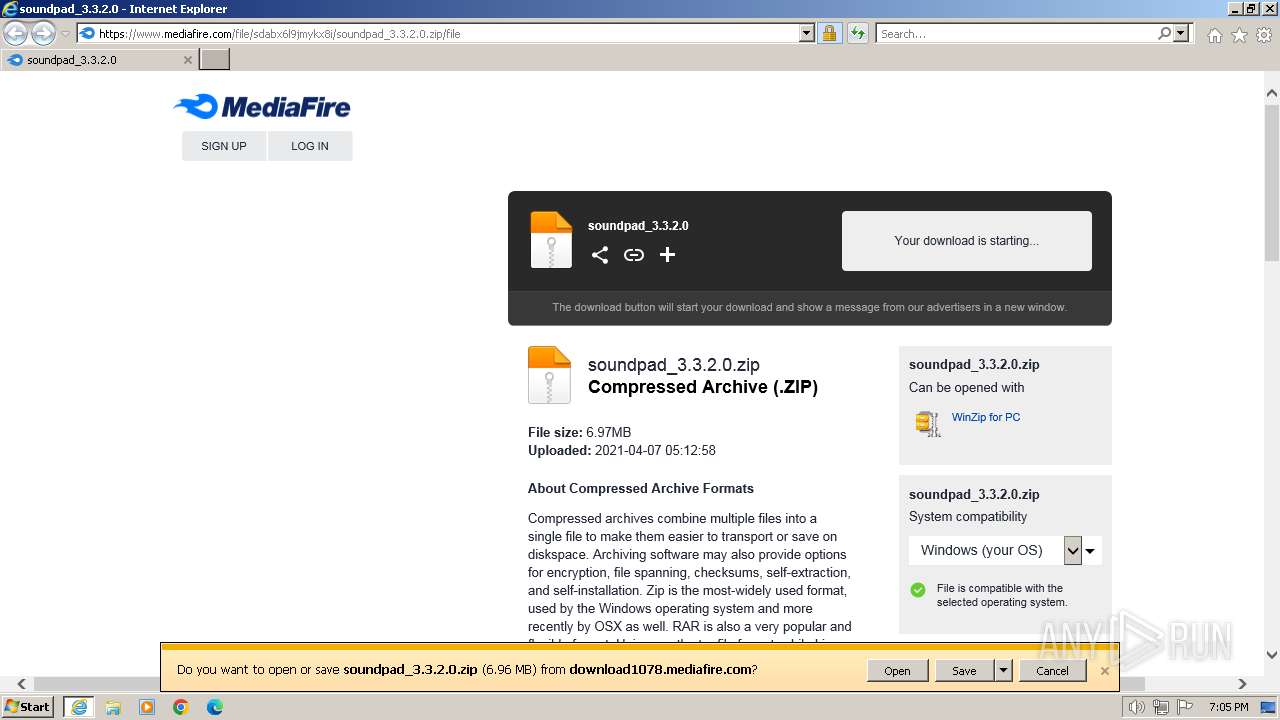
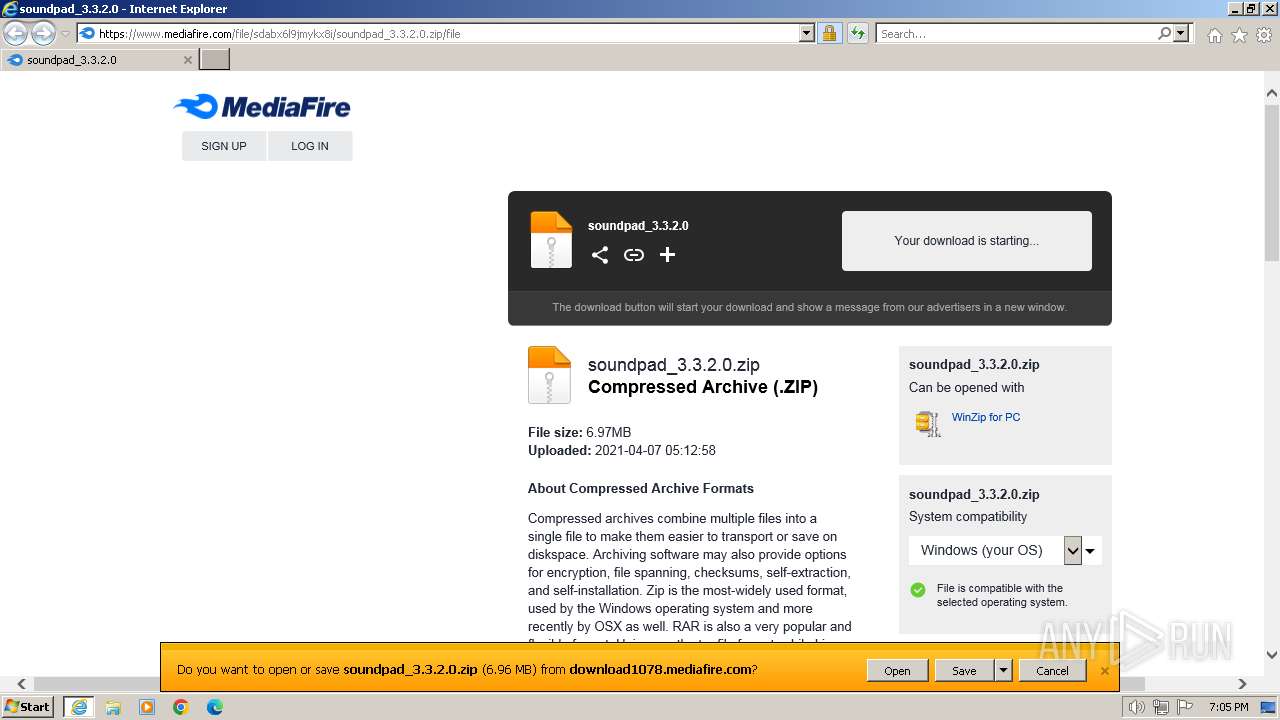
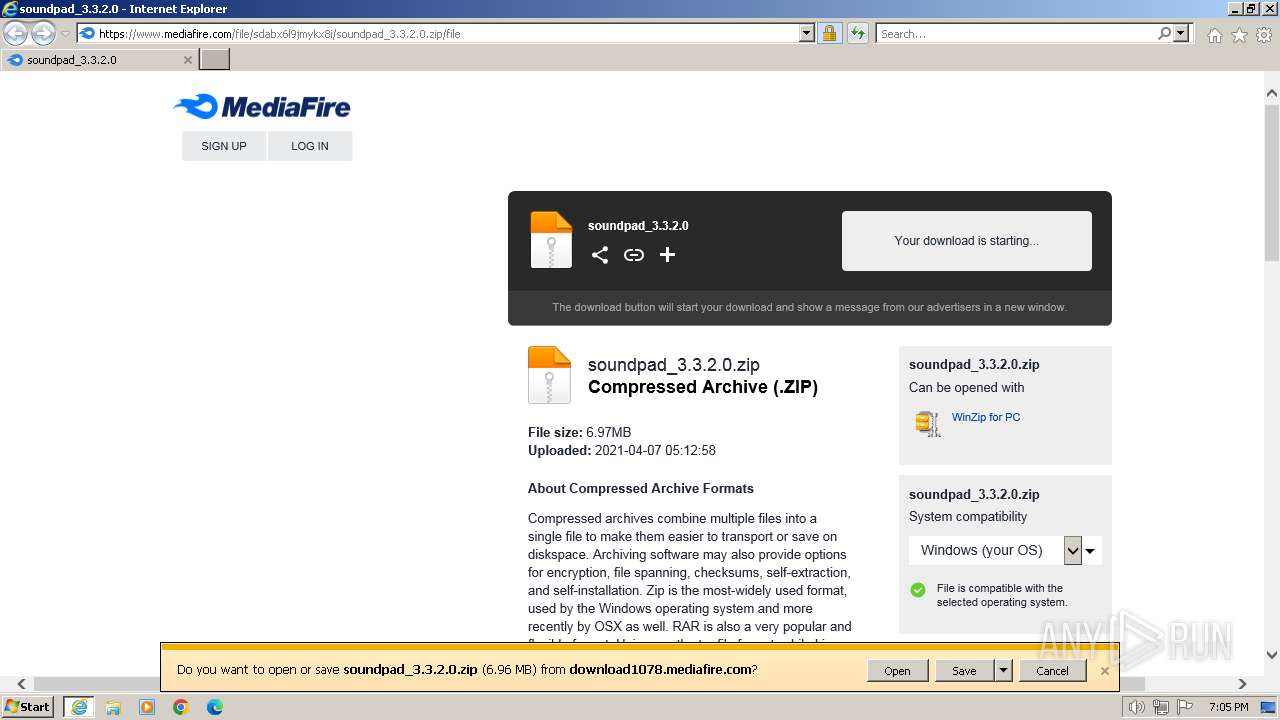
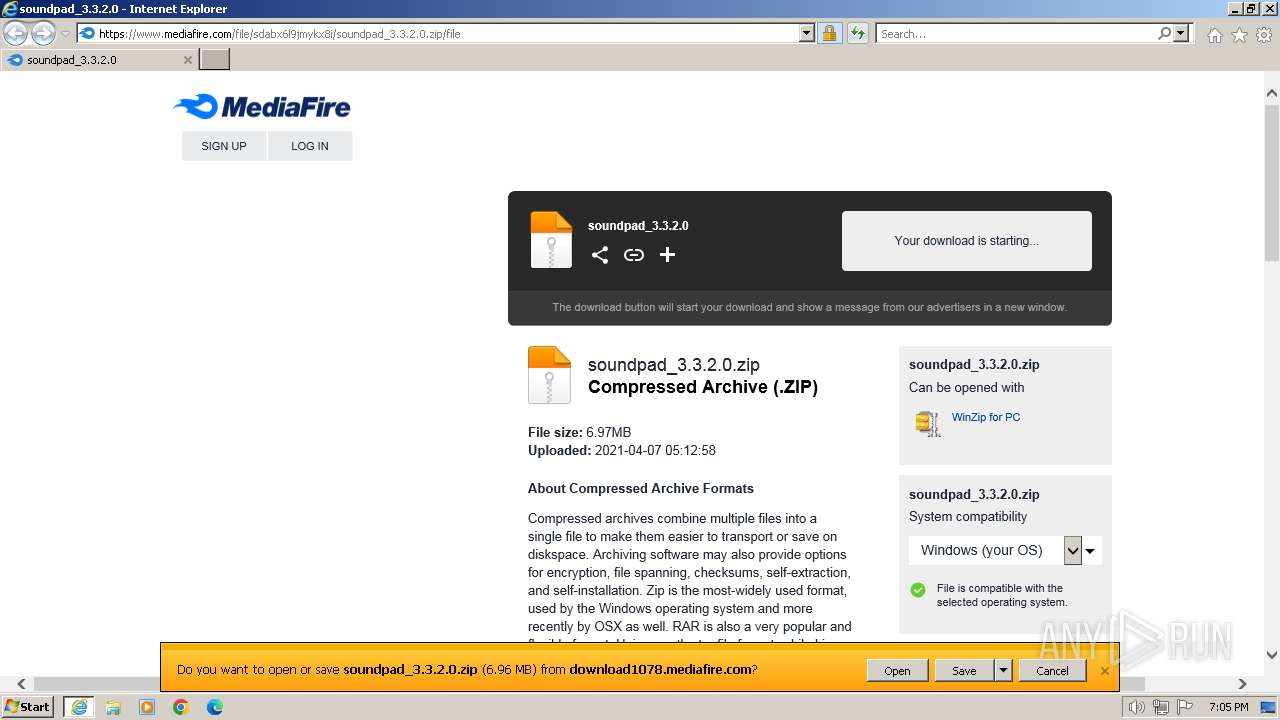
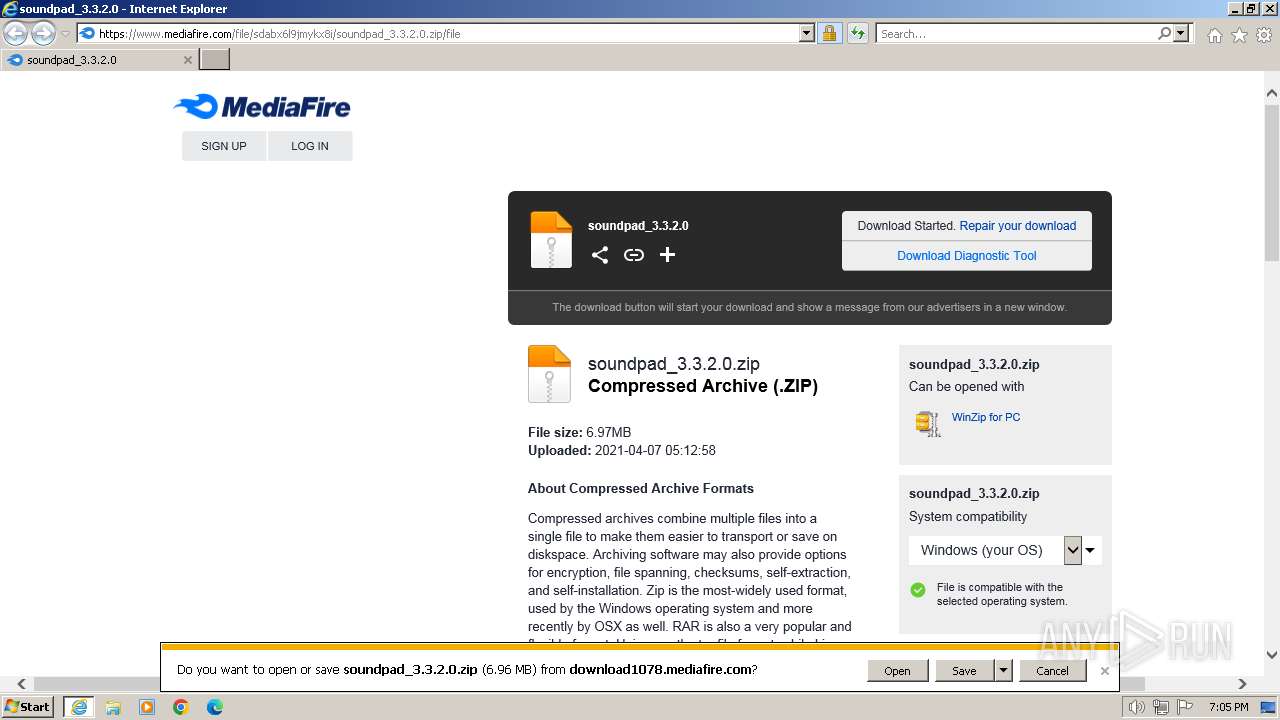
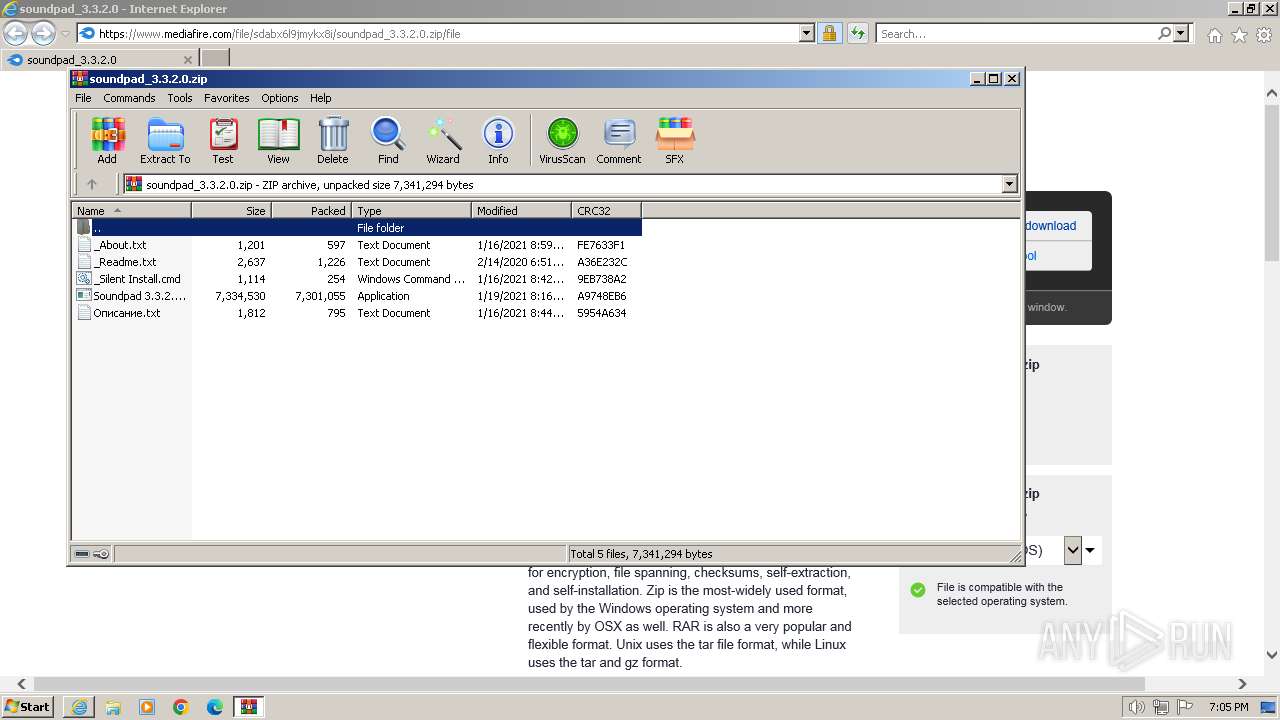
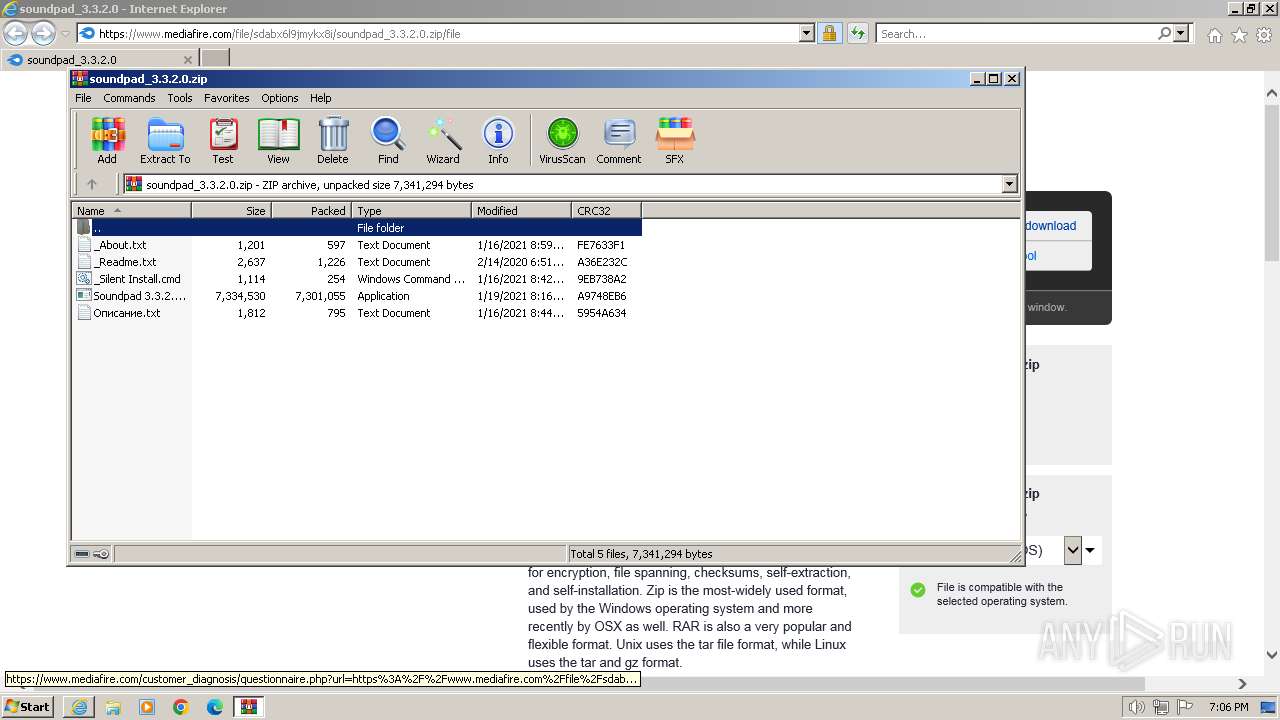
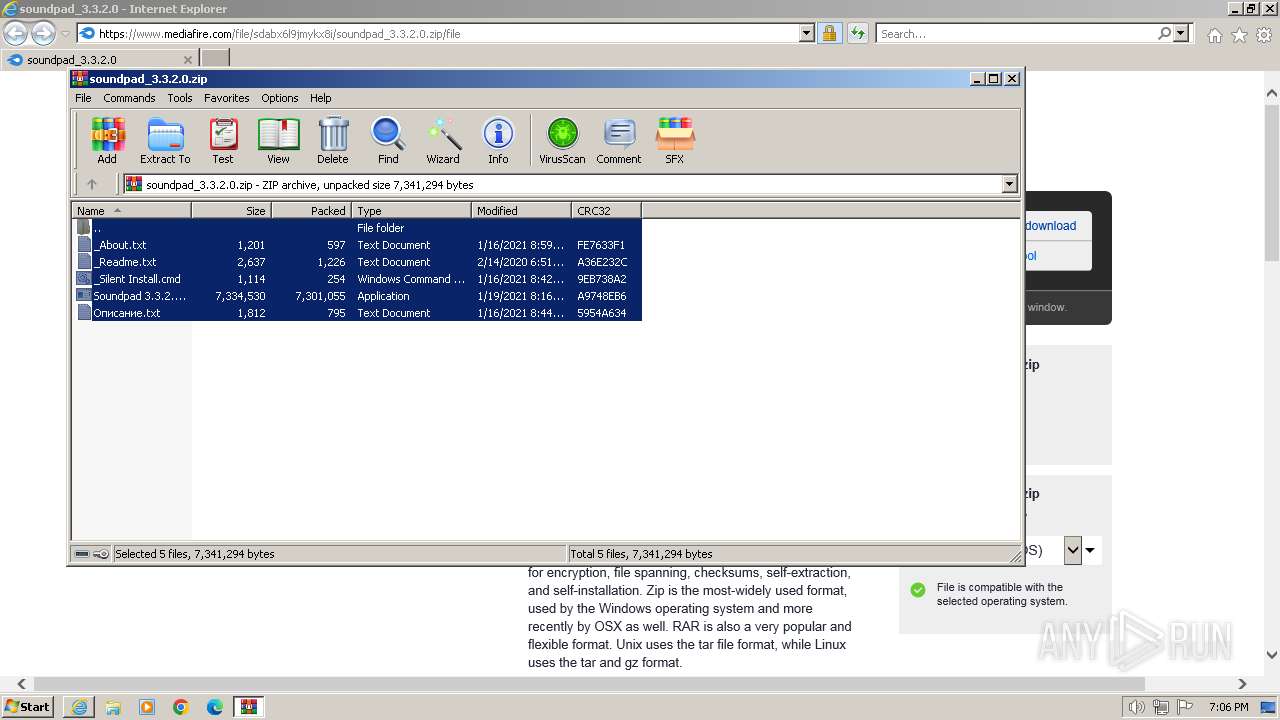
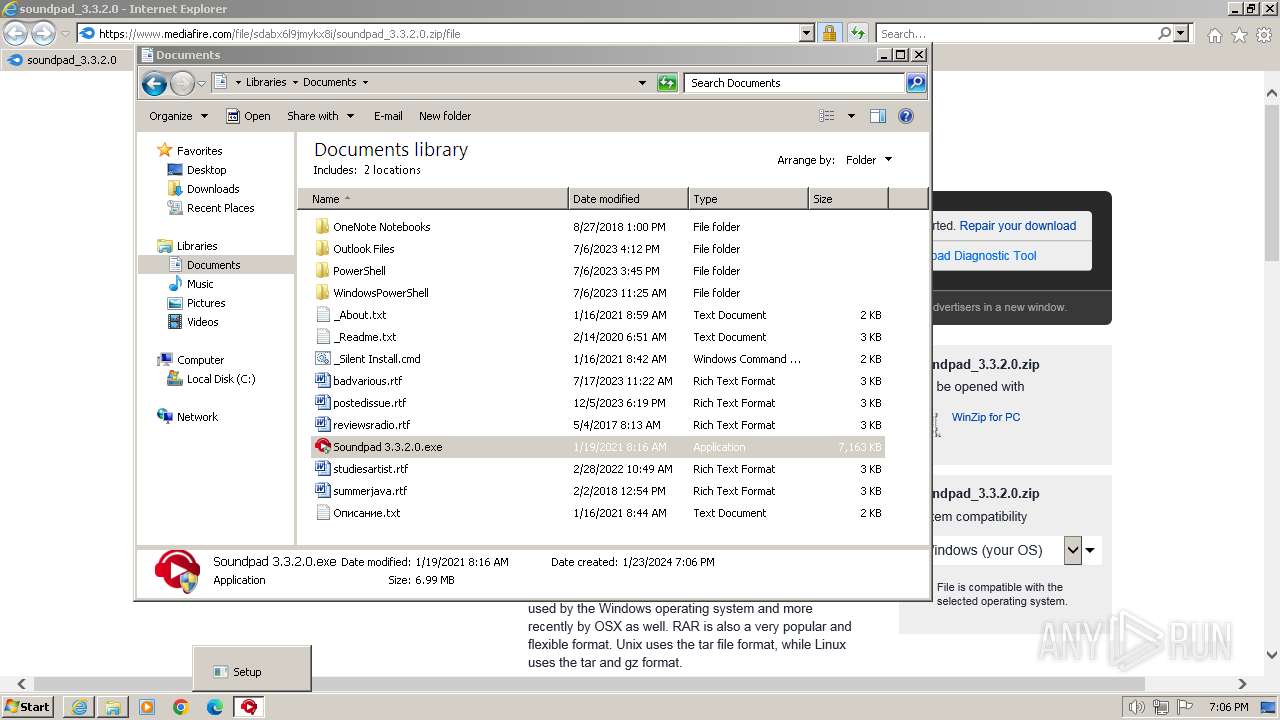
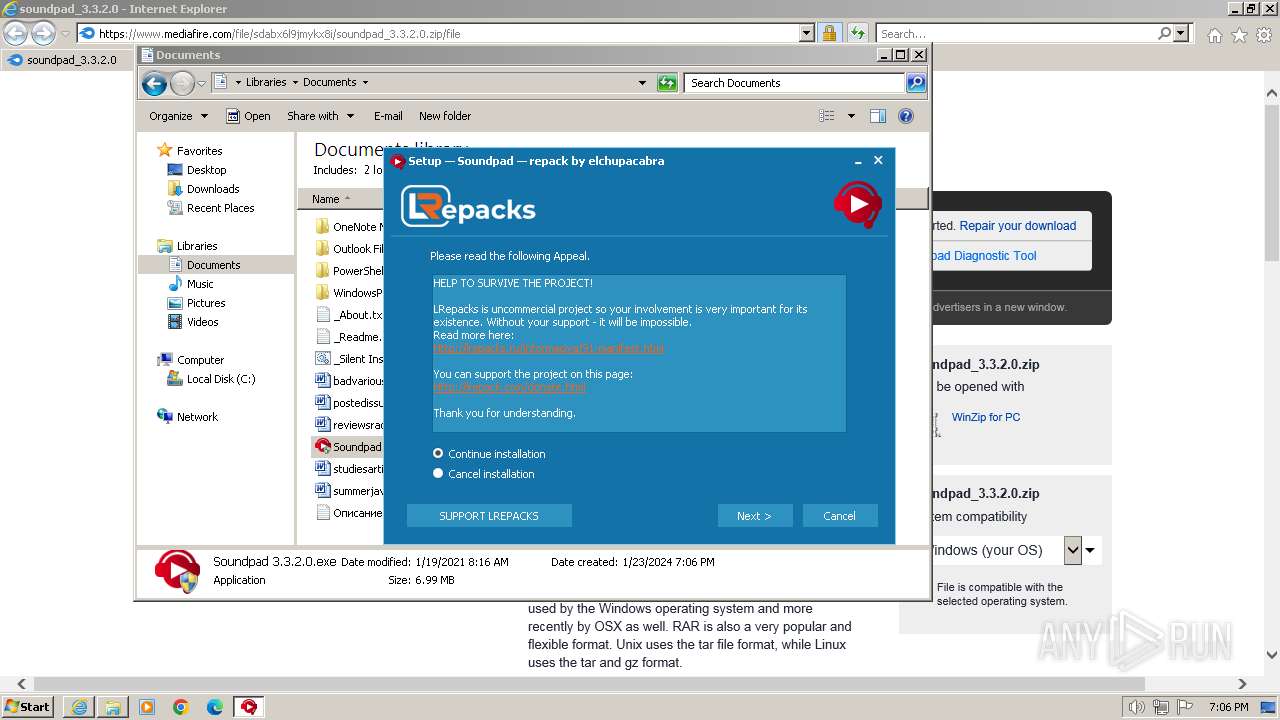
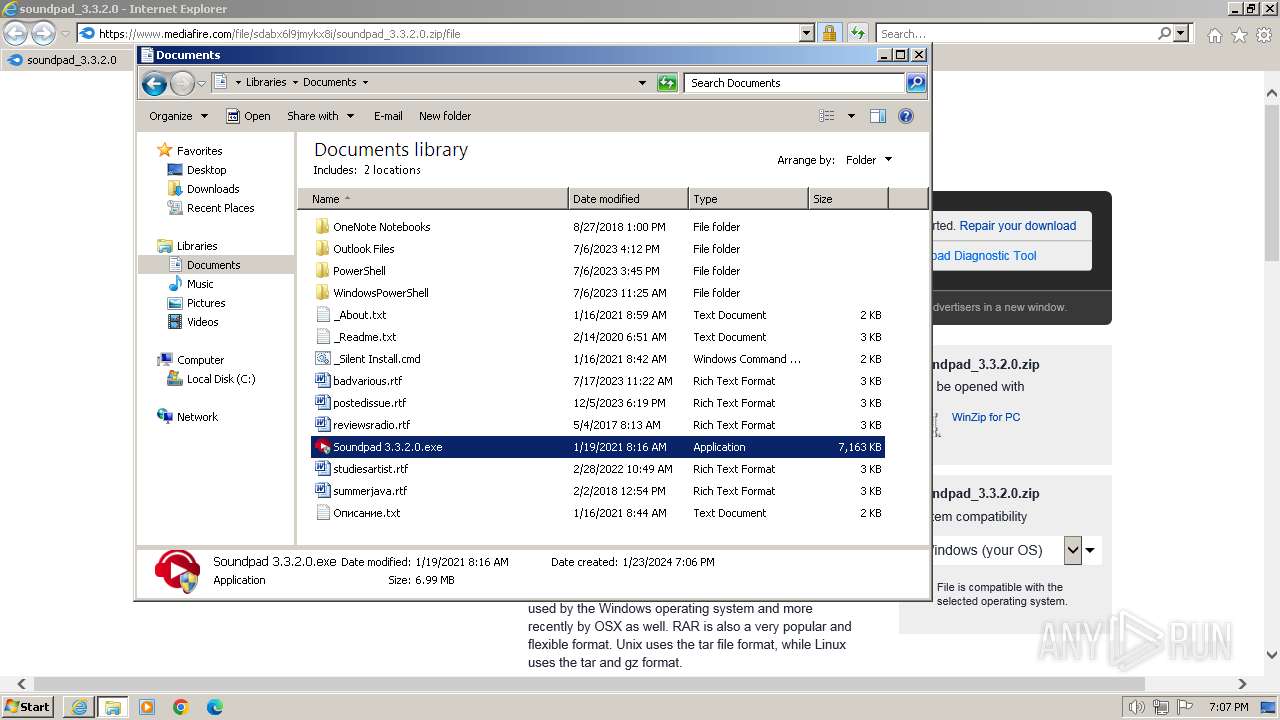
| URL: | https://www.mediafire.com/file/sdabx6l9jmykx8i/soundpad_3.3.2.0.zip/file |
| Full analysis: | https://app.any.run/tasks/86ce5869-c585-4ccf-a940-ff588cad0867 |
| Verdict: | Malicious activity |
| Analysis date: | January 23, 2024, 19:04:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | C6ED7F79441B24410062E34065085462 |
| SHA1: | EA5B0F70613DD2DC310CEAB0787AAAD63AEF4728 |
| SHA256: | CFB74ACDAED79AC5490F7B0605063111C7819C62D6A431378A1B1525308CE360 |
| SSDEEP: | 3:N8DSLw3eGUoLvcpOdML7dky:2OLw3eG3UyML7dky |
MALICIOUS
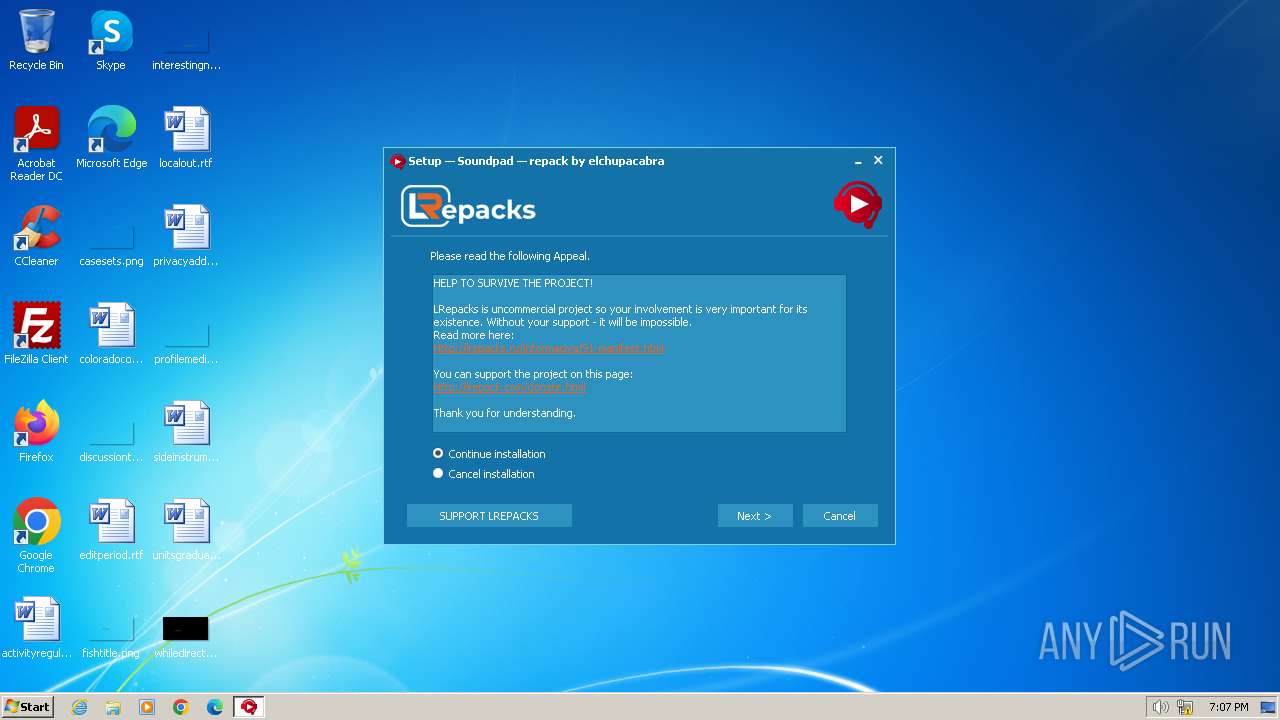
Drops the executable file immediately after the start
- Soundpad 3.3.2.0.tmp (PID: 2132)
- Soundpad 3.3.2.0.exe (PID: 2748)
- Soundpad 3.3.2.0.tmp (PID: 2768)
- Soundpad 3.3.2.0.exe (PID: 2812)
SUSPICIOUS
Process drops legitimate windows executable
- Soundpad 3.3.2.0.tmp (PID: 2132)
- Soundpad 3.3.2.0.tmp (PID: 2768)
Executable content was dropped or overwritten
- Soundpad 3.3.2.0.tmp (PID: 2132)
- Soundpad 3.3.2.0.exe (PID: 2748)
- Soundpad 3.3.2.0.tmp (PID: 2768)
- Soundpad 3.3.2.0.exe (PID: 2812)
Uses REG/REGEDIT.EXE to modify registry
- Soundpad 3.3.2.0.tmp (PID: 2132)
The process executes via Task Scheduler
- ctfmon.exe (PID: 1844)
- sipnotify.exe (PID: 1856)
Reads the Internet Settings
- sipnotify.exe (PID: 1856)
Reads settings of System Certificates
- sipnotify.exe (PID: 1856)
Reads the Windows owner or organization settings
- Soundpad 3.3.2.0.tmp (PID: 2768)
- Soundpad 3.3.2.0.tmp (PID: 2132)
INFO
The process uses the downloaded file
- iexplore.exe (PID: 2628)
- WinRAR.exe (PID: 2944)
Reads the computer name
- Soundpad 3.3.2.0.tmp (PID: 2132)
- Soundpad 3.3.2.0.exe (PID: 2812)
- IMEKLMG.EXE (PID: 2084)
- IMEKLMG.EXE (PID: 2096)
- wmpnscfg.exe (PID: 2348)
- wmpnscfg.exe (PID: 2372)
- Soundpad 3.3.2.0.tmp (PID: 2768)
Creates files in the program directory
- Soundpad 3.3.2.0.tmp (PID: 2132)
Checks supported languages
- Soundpad 3.3.2.0.exe (PID: 2812)
- IMEKLMG.EXE (PID: 2084)
- IMEKLMG.EXE (PID: 2096)
- wmpnscfg.exe (PID: 2348)
- wmpnscfg.exe (PID: 2372)
- Soundpad 3.3.2.0.exe (PID: 2748)
- Soundpad 3.3.2.0.tmp (PID: 2768)
- Soundpad 3.3.2.0.tmp (PID: 2132)
Application launched itself
- iexplore.exe (PID: 2628)
Manual execution by a user
- Soundpad 3.3.2.0.exe (PID: 3884)
- Soundpad 3.3.2.0.exe (PID: 2812)
- explorer.exe (PID: 3572)
- IMEKLMG.EXE (PID: 2084)
- IMEKLMG.EXE (PID: 2096)
- wmpnscfg.exe (PID: 2348)
- wmpnscfg.exe (PID: 2372)
- Soundpad 3.3.2.0.exe (PID: 2640)
- explorer.exe (PID: 2844)
- notepad.exe (PID: 3024)
- Soundpad 3.3.2.0.exe (PID: 2748)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2944)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2944)
Create files in a temporary directory
- msiexec.exe (PID: 3664)
- Soundpad 3.3.2.0.exe (PID: 2748)
- Soundpad 3.3.2.0.tmp (PID: 2768)
- Soundpad 3.3.2.0.tmp (PID: 2132)
- Soundpad 3.3.2.0.exe (PID: 2812)
Process checks whether UAC notifications are on
- IMEKLMG.EXE (PID: 2084)
- IMEKLMG.EXE (PID: 2096)
Reads security settings of Internet Explorer
- sipnotify.exe (PID: 1856)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
115
Monitored processes
20
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 664 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2628 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1844 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1856 | C:\Windows\system32\sipnotify.exe -LogonOrUnlock | C:\Windows\System32\sipnotify.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: sipnotify Exit code: 0 Version: 6.1.7602.20480 (win7sp1_ldr_escrow.191010-1716) Modules
| |||||||||||||||
| 2084 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /JPN /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 2096 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /KOR /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 2132 | "C:\Users\admin\AppData\Local\Temp\is-4SCJN.tmp\Soundpad 3.3.2.0.tmp" /SL5="$B01DA,6996435,67072,C:\Users\admin\Documents\Soundpad 3.3.2.0.exe" | C:\Users\admin\AppData\Local\Temp\is-4SCJN.tmp\Soundpad 3.3.2.0.tmp | Soundpad 3.3.2.0.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 2348 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2372 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2628 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://www.mediafire.com/file/sdabx6l9jmykx8i/soundpad_3.3.2.0.zip/file" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1073807364 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2640 | "C:\Users\admin\Documents\Soundpad 3.3.2.0.exe" | C:\Users\admin\Documents\Soundpad 3.3.2.0.exe | — | explorer.exe | |||||||||||
User: admin Company: lrepacks.ru Integrity Level: MEDIUM Description: Soundpad Setup Exit code: 3221226540 Version: 3.3.2.0.0 Modules
| |||||||||||||||
Total events
26 385
Read events
26 216
Write events
146
Delete events
23
Modification events
| (PID) Process: | (2628) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (2628) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (2628) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (2628) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2628) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2628) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2628) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2628) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2628) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2628) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
22
Suspicious files
176
Text files
101
Unknown types
11
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 664 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | binary | |
MD5:DEE1CB98104931DB27A73DCBA2CDF91C | SHA256:52F35D6BDD32064C55A7C1C7F3B9E349E30912B7F922569A5BBF45E150127AE8 | |||
| 664 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:7CBB7FC3B8714908E0DF78EEAD4DB236 | SHA256:7EF574BD3089C70E3396C34CFFA67BBB9BAB4FCAF23E2F272F24E27653E7814F | |||
| 664 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\07CEF2F654E3ED6050FFC9B6EB844250_BACC6CD2B29F18349081C9FD2343833B | binary | |
MD5:9F4F7A385D206559A54D29A6F7E10112 | SHA256:3339FE7938169F3139D125AB1879A36CF1AD2571FC5D13A09E9C455AE0D69412 | |||
| 664 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\ZJSYKSK2.txt | text | |
MD5:8CF745AAE77AE6BFDC2B0518270CB59D | SHA256:48505F1CB8367C385C9531C376BBDB2109D3CAF2AA78980717118F80C359F0E3 | |||
| 664 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | binary | |
MD5:8761661A074F898D61AE0DF7213D6CBE | SHA256:B87890CC9D309831D4C52CDAB889FAEBF1196FABF56CE90F599E917DEBAC514F | |||
| 664 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\35KR8A14.txt | text | |
MD5:7BDEE5F5594823891CA8DA6C0C743F73 | SHA256:D17EB36CB18E73CE8017049310FCE2D0524B91F777EEF3C50997C9309434216D | |||
| 664 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\07CEF2F654E3ED6050FFC9B6EB844250_BACC6CD2B29F18349081C9FD2343833B | binary | |
MD5:0A5175DA92CD1BE09B8BD4F06995762F | SHA256:37FA0B8FFE06559B5C73660AE25EBFA0FEA49AE84E37C8ADBD3CB9ECD01BE42A | |||
| 664 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:B03F28F41882A78D17DFA5525CDB915D | SHA256:F50EDFE73C5F0AFC029619FB5C1DC45B1CC364E6D9A5FE53AD5A2F3B61918FD4 | |||
| 664 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\file[1].htm | html | |
MD5:43B0F63BABF049F10270EE718536C1E6 | SHA256:2F950D47042B4FE73262E268CCC9BCFBCF529B3CEBD3AECC9BB18A1D9A1F9A80 | |||
| 664 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:EE31326360FF4D672C4CC5A1BCC1194D | SHA256:330B423C925889954DB2F9E70FA18137F7C4A715CD77A62CDC345D68DABAB395 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
40
TCP/UDP connections
94
DNS requests
43
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
664 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?96e261c22e45b24e | unknown | — | — | unknown |
664 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f27fe043238c6b38 | unknown | — | — | unknown |
664 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | binary | 1.42 Kb | unknown |
664 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEBN9U5yqfDGppDNwGWiEeo0%3D | unknown | binary | 2.18 Kb | unknown |
664 | iexplore.exe | GET | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
664 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | unknown | binary | 1.47 Kb | unknown |
664 | iexplore.exe | GET | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
664 | iexplore.exe | GET | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | binary | 724 b | unknown |
664 | iexplore.exe | GET | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | binary | 724 b | unknown |
664 | iexplore.exe | GET | 200 | 142.250.185.163:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | binary | 724 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
664 | iexplore.exe | 104.16.113.74:443 | www.mediafire.com | CLOUDFLARENET | — | unknown |
664 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
664 | iexplore.exe | 104.18.38.233:80 | ocsp.comodoca.com | CLOUDFLARENET | — | shared |
664 | iexplore.exe | 142.250.186.72:443 | www.googletagmanager.com | GOOGLE | US | unknown |
664 | iexplore.exe | 172.67.41.60:443 | btloader.com | CLOUDFLARENET | US | unknown |
664 | iexplore.exe | 104.21.42.32:443 | the.gatekeeperconsent.com | CLOUDFLARENET | — | unknown |
664 | iexplore.exe | 172.64.128.8:443 | www.ezojs.com | CLOUDFLARENET | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.mediafire.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
the.gatekeeperconsent.com |
| unknown |
www.googletagmanager.com |
| whitelisted |
btloader.com |
| whitelisted |
www.ezojs.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
1080 | svchost.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |
Process | Message |
|---|---|
regedit.exe | REGEDIT: CreateFile failed, GetLastError() = 2
|