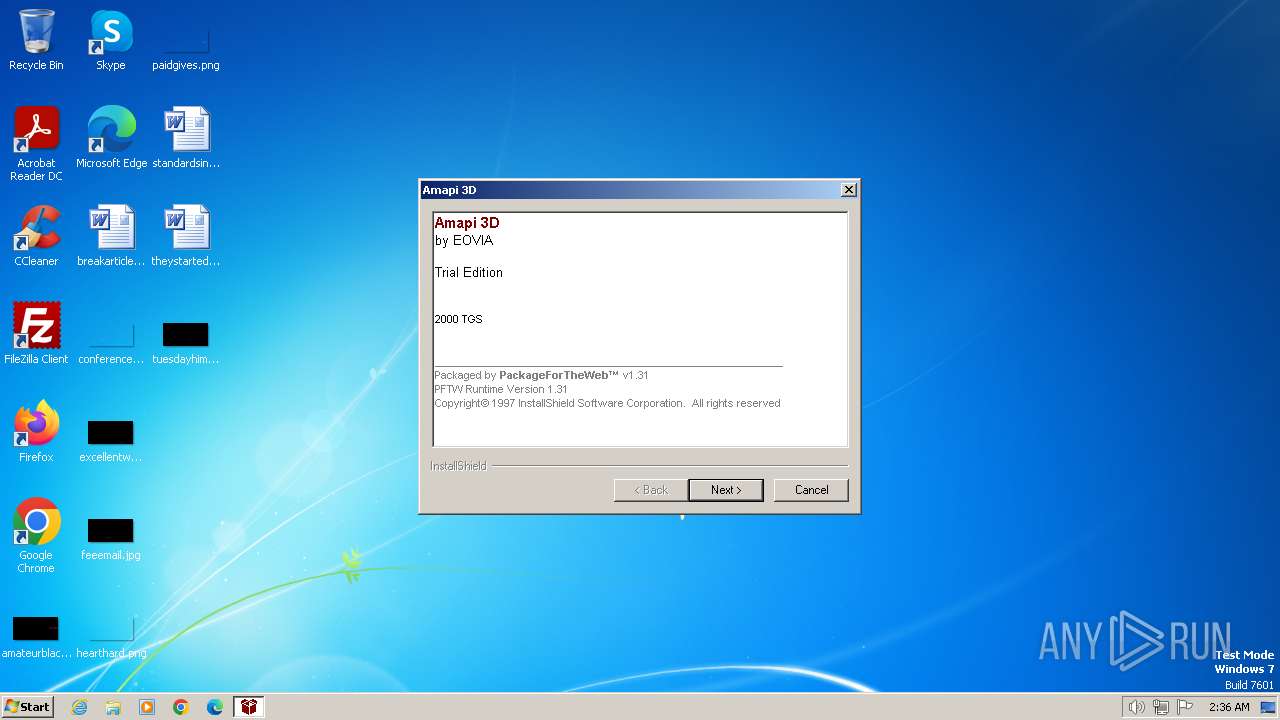
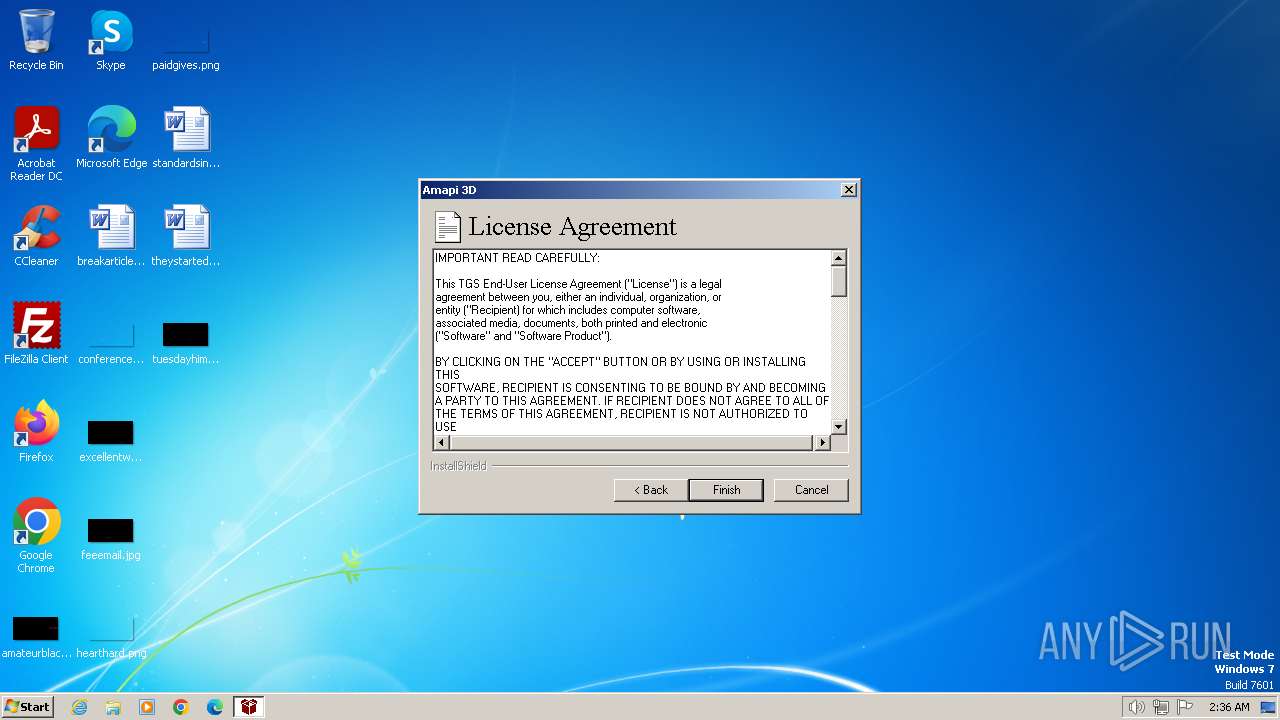
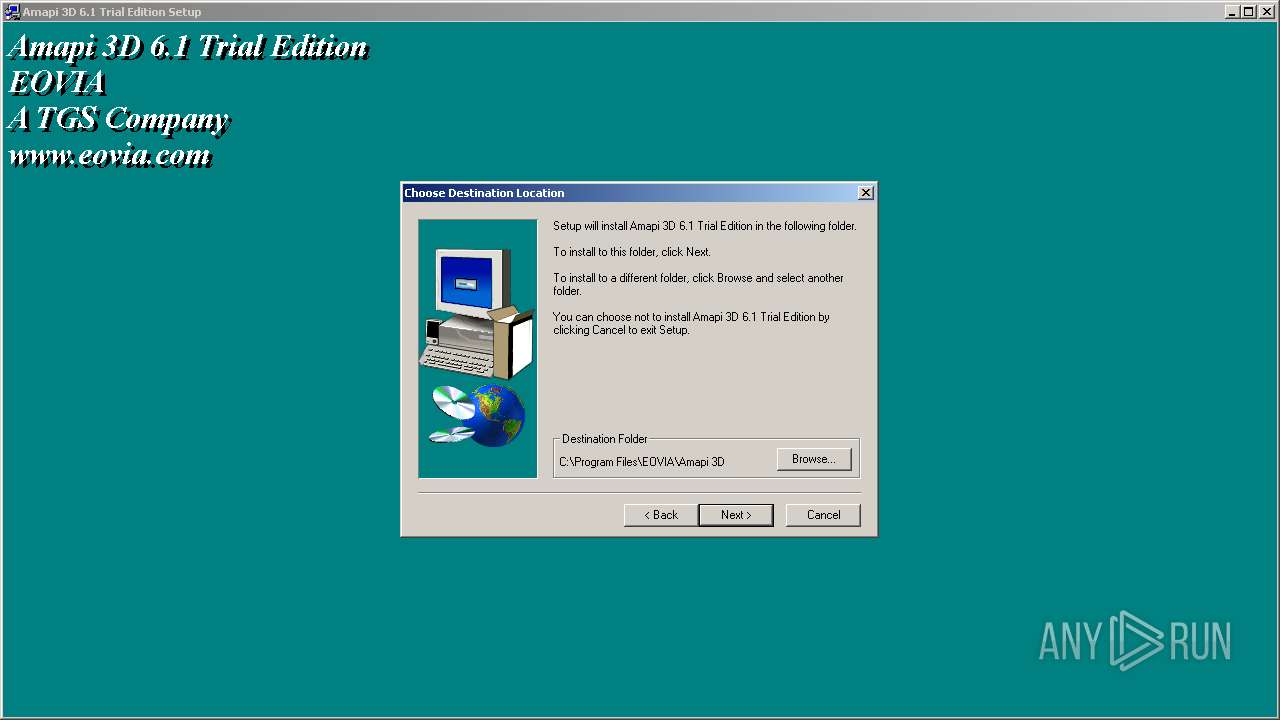
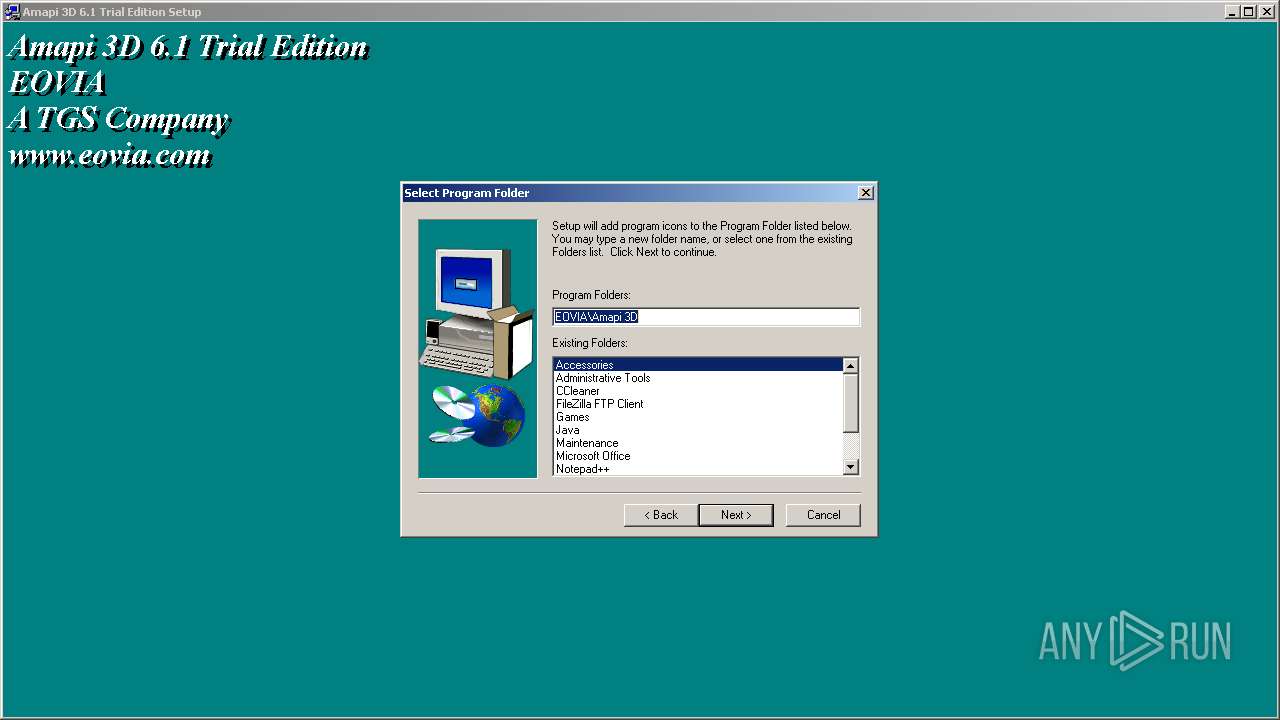
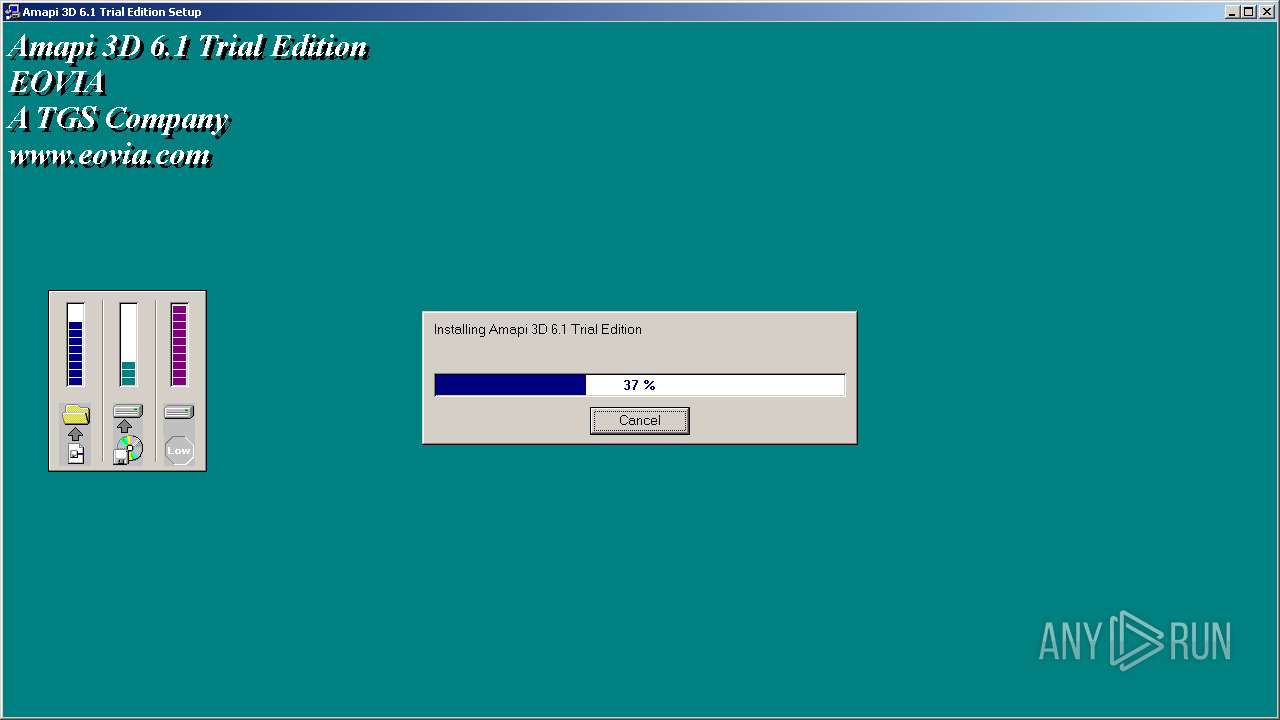
| File name: | Amapi3D61TEEnglish.exe |
| Full analysis: | https://app.any.run/tasks/beb337d6-3e98-4e1f-96e0-721b4a048e0c |
| Verdict: | Malicious activity |
| Analysis date: | April 07, 2024, 01:36:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, InstallShield self-extracting archive |
| MD5: | A8130BB17C361274314964529D47BC94 |
| SHA1: | EC33D3549D9E11487FD5986CFF97B48FC82A8514 |
| SHA256: | CF9F2A8E032E2F99F251FA9C844313E953FDD9E319A52DCBDAD2F9FA5C0CCCCE |
| SSDEEP: | 98304:QPAI6mOfeUNIcxYK8JLS7fT3fBg3KJNrCwRQau+bnDoK6jb5mGSYk+9Lpu6W+0wc:AI8pzJX1YDLhP9kIrND9 |
MALICIOUS
Drops the executable file immediately after the start
- Amapi3D61TEEnglish.exe (PID: 3996)
- _INS576._MP (PID: 1496)
SUSPICIOUS
Creates file in the systems drive root
- ntvdm.exe (PID: 2756)
Starts application with an unusual extension
- ntvdm.exe (PID: 2756)
Process drops legitimate windows executable
- _INS576._MP (PID: 1496)
Creates a software uninstall entry
- _INS576._MP (PID: 1496)
INFO
Checks supported languages
- Amapi3D61TEEnglish.exe (PID: 3996)
- _INS576._MP (PID: 1496)
- amapi.exe (PID: 3400)
Create files in a temporary directory
- ntvdm.exe (PID: 2756)
- Amapi3D61TEEnglish.exe (PID: 3996)
- _INS576._MP (PID: 1496)
Drops the executable file immediately after the start
- ntvdm.exe (PID: 2756)
Reads the computer name
- _INS576._MP (PID: 1496)
- amapi.exe (PID: 3400)
Creates files in the program directory
- _INS576._MP (PID: 1496)
Reads security settings of Internet Explorer
- explorer.exe (PID: 2168)
Creates files or folders in the user directory
- amapi.exe (PID: 3400)
Reads the machine GUID from the registry
- amapi.exe (PID: 3400)
Reads the Internet Settings
- explorer.exe (PID: 2168)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (36.1) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (26.2) |
| .exe | | | Win64 Executable (generic) (23.1) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.5) |
| .exe | | | Win32 Executable (generic) (3.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1997:08:26 14:07:18+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 5 |
| CodeSize: | 57856 |
| InitializedDataSize: | 57344 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5a0 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.3.197.10822 |
| ProductVersionNumber: | 1.3.197.10822 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | InstallShield Software Corporation |
| FileDescription: | PackageForTheWeb Stub |
| FileVersion: | 1.31 |
| InternalName: | STUB.EXE |
| LegalCopyright: | Copyright © 1996 InstallShield Software Corporation |
| OriginalFileName: | STUB32.EXE |
| ProductName: | PackageForTheWeb Stub |
| ProductVersion: | 1.31 |
Total processes
47
Monitored processes
7
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1496 | C:\Users\admin\AppData\Local\Temp\_INS576._MP | C:\Users\admin\AppData\Local\Temp\_INS576._MP | — | ntvdm.exe | |||||||||||
User: admin Company: InstallShield Software Corporation Integrity Level: HIGH Description: InstallShield Engine Version: 5.00.221.0 Modules
| |||||||||||||||
| 1928 | explorer.exe "C:\ProgramData\Microsoft\Windows\Start Menu\Programs\EOVIA\Amapi 3D" | C:\Windows\explorer.exe | — | _INS576._MP | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2124 | "C:\Users\admin\AppData\Local\Temp\Amapi3D61TEEnglish.exe" | C:\Users\admin\AppData\Local\Temp\Amapi3D61TEEnglish.exe | — | explorer.exe | |||||||||||
User: admin Company: InstallShield Software Corporation Integrity Level: MEDIUM Description: PackageForTheWeb Stub Exit code: 3221226540 Version: 1.31 Modules
| |||||||||||||||
| 2168 | C:\Windows\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2756 | "C:\Windows\system32\ntvdm.exe" -i1 -ws | C:\Windows\System32\ntvdm.exe | — | Amapi3D61TEEnglish.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: NTVDM.EXE Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3400 | "C:\Program Files\EOVIA\Amapi 3D\amapi.exe" | C:\Program Files\EOVIA\Amapi 3D\amapi.exe | — | explorer.exe | |||||||||||
User: admin Company: TGS Integrity Level: MEDIUM Description: AMAPI3D 6.1 Version: 6.1 Modules
| |||||||||||||||
| 3996 | "C:\Users\admin\AppData\Local\Temp\Amapi3D61TEEnglish.exe" | C:\Users\admin\AppData\Local\Temp\Amapi3D61TEEnglish.exe | explorer.exe | ||||||||||||
User: admin Company: InstallShield Software Corporation Integrity Level: HIGH Description: PackageForTheWeb Stub Version: 1.31 Modules
| |||||||||||||||
Total events
12 633
Read events
12 500
Write events
128
Delete events
5
Modification events
| (PID) Process: | (1496) _INS576._MP | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\UnTgsA3D60TEus |
| Operation: | write | Name: | UninstallString |
Value: C:\Windows\IsUninst.exe -f"C:\Program Files\EOVIA\Amapi 3D\Uninst.isu" | |||
| (PID) Process: | (1496) _INS576._MP | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\TgsA3D60TEus |
| Operation: | write | Name: | Path |
Value: C:\Program Files\EOVIA\Amapi 3D | |||
| (PID) Process: | (1496) _INS576._MP | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\UnTgsA3D60TEus |
| Operation: | write | Name: | DisplayName |
Value: Amapi 3D 6.1 Trial Edition | |||
| (PID) Process: | (2168) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 0202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (2168) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 01000000070000000200000006000000000000000B0000000C0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (2168) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\1\0 |
| Operation: | write | Name: | MRUListEx |
Value: 040000000100000000000000020000000500000003000000FFFFFFFF | |||
| (PID) Process: | (2168) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\1\0\4 |
| Operation: | write | Name: | MRUListEx |
Value: 000000000500000004000000030000000200000001000000FFFFFFFF | |||
| (PID) Process: | (2168) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\1\0\4\0\0\0\0 |
| Operation: | write | Name: | 1 |
Value: 4C003100000000008758960C1000454F56494100380008000400EFBE8758960C8758960C2A000000A6E2000000000600000000000000000000000000000045004F00560049004100000014000000 | |||
| (PID) Process: | (2168) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\1\0\4\0\0\0\0\1 |
| Operation: | delete value | Name: | MRUList |
Value: | |||
| (PID) Process: | (2168) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\1\0\4\0\0\0\0 |
| Operation: | write | Name: | MRUListEx |
Value: 0100000000000000FFFFFFFF | |||
Executable files
54
Suspicious files
58
Text files
109
Unknown types
48
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3996 | Amapi3D61TEEnglish.exe | C:\USERS\ADMIN\APPDATA\LOCAL\TEMP\~PFTW000\pftw1.pkg | — | |
MD5:— | SHA256:— | |||
| 3996 | Amapi3D61TEEnglish.exe | C:\USERS\ADMIN\APPDATA\LOCAL\TEMP\~PFTW000\DATA.TAG | text | |
MD5:— | SHA256:— | |||
| 3996 | Amapi3D61TEEnglish.exe | C:\USERS\ADMIN\APPDATA\LOCAL\TEMP\~PFTW000\data1.cab | — | |
MD5:— | SHA256:— | |||
| 3996 | Amapi3D61TEEnglish.exe | C:\USERS\ADMIN\APPDATA\LOCAL\TEMP\~PFTW000\lang.dat | text | |
MD5:— | SHA256:— | |||
| 3996 | Amapi3D61TEEnglish.exe | C:\USERS\ADMIN\APPDATA\LOCAL\TEMP\~PFTW000\layout.bin | binary | |
MD5:— | SHA256:— | |||
| 3996 | Amapi3D61TEEnglish.exe | C:\USERS\ADMIN\APPDATA\LOCAL\TEMP\~PFTW000\os.dat | text | |
MD5:— | SHA256:— | |||
| 3996 | Amapi3D61TEEnglish.exe | C:\USERS\ADMIN\APPDATA\LOCAL\TEMP\~PFTW000\setup.bmp | image | |
MD5:— | SHA256:— | |||
| 3996 | Amapi3D61TEEnglish.exe | C:\USERS\ADMIN\APPDATA\LOCAL\TEMP\~PFTW000\SETUP.EXE | executable | |
MD5:— | SHA256:— | |||
| 3996 | Amapi3D61TEEnglish.exe | C:\USERS\ADMIN\APPDATA\LOCAL\TEMP\~PFTW000\SETUP.INI | text | |
MD5:— | SHA256:— | |||
| 3996 | Amapi3D61TEEnglish.exe | C:\USERS\ADMIN\APPDATA\LOCAL\TEMP\~PFTW000\setup.ins | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |