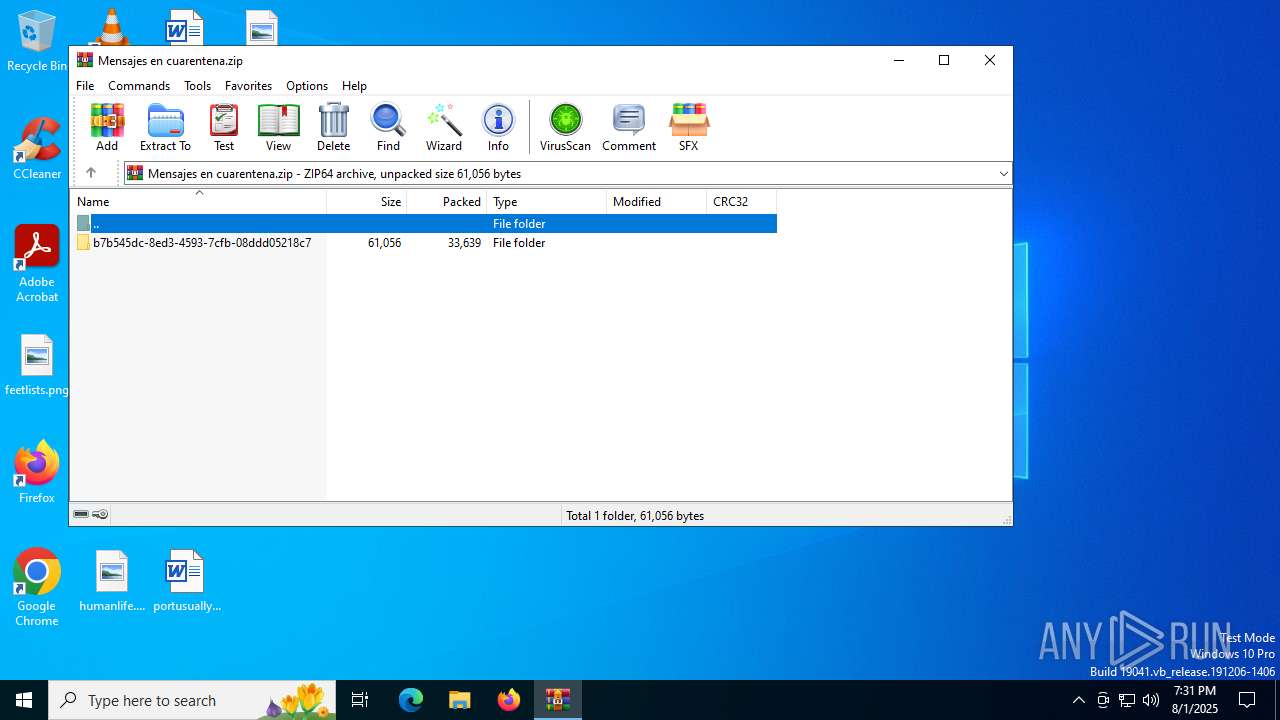
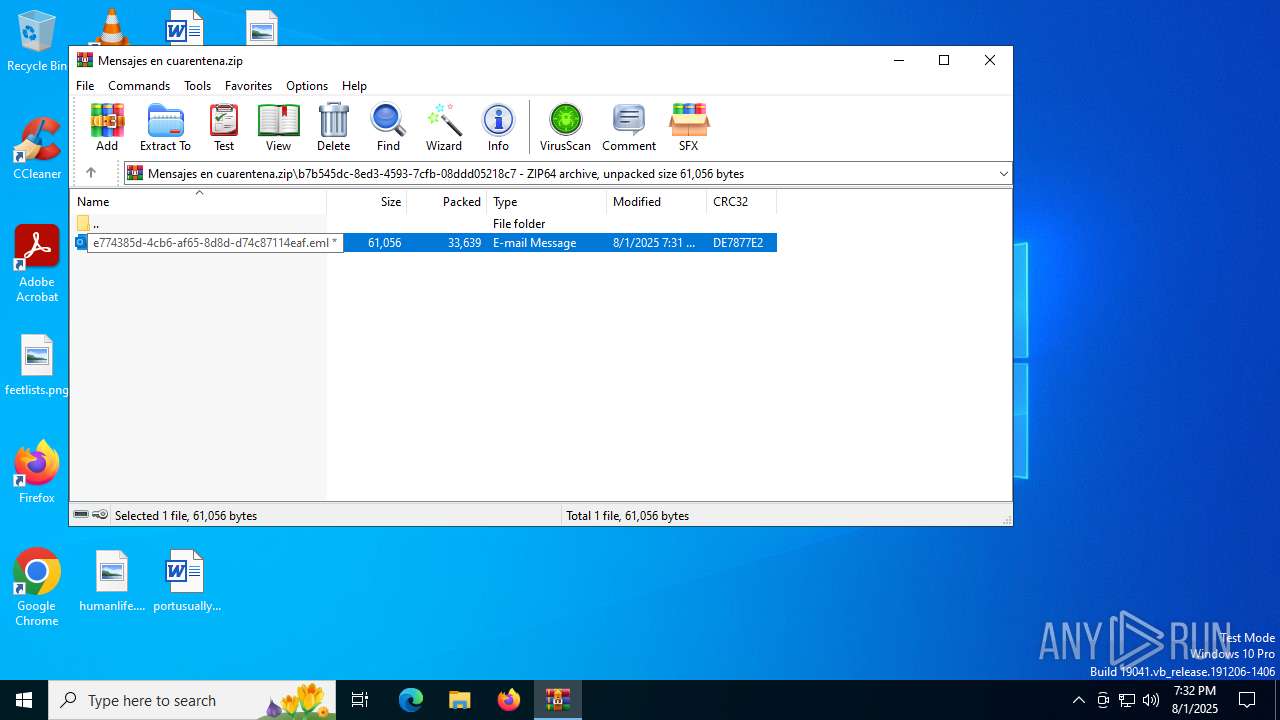
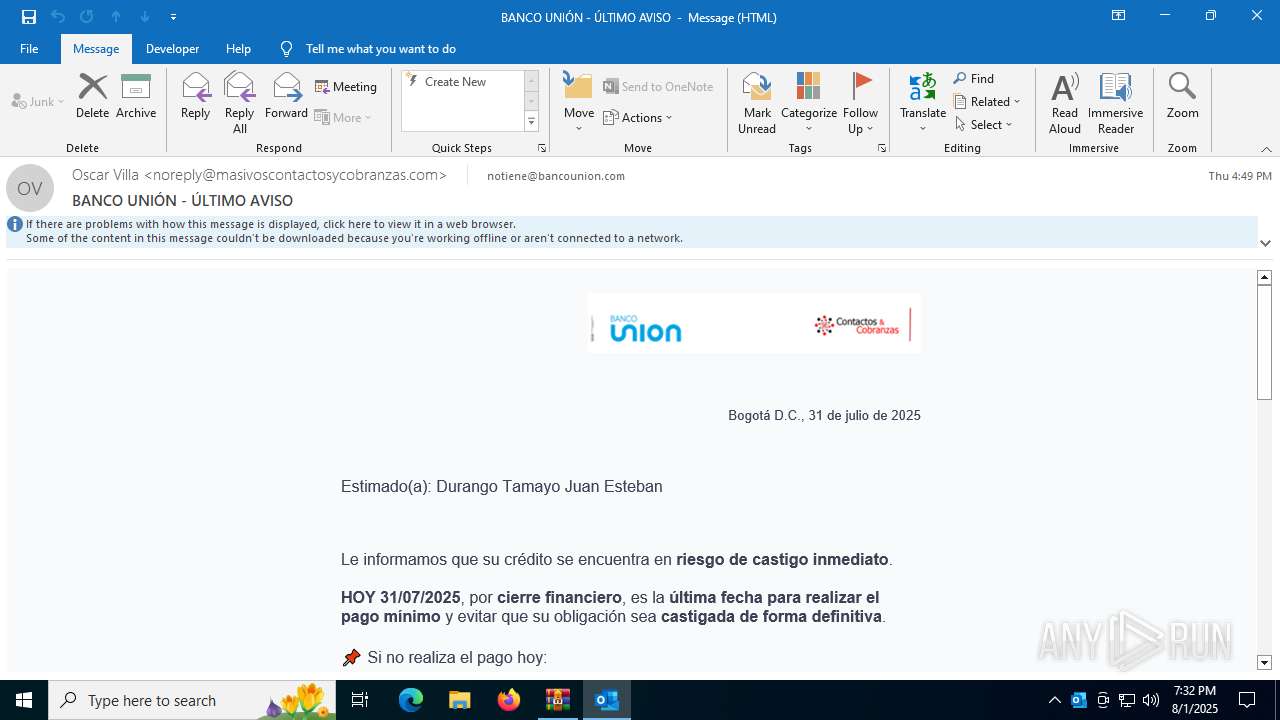
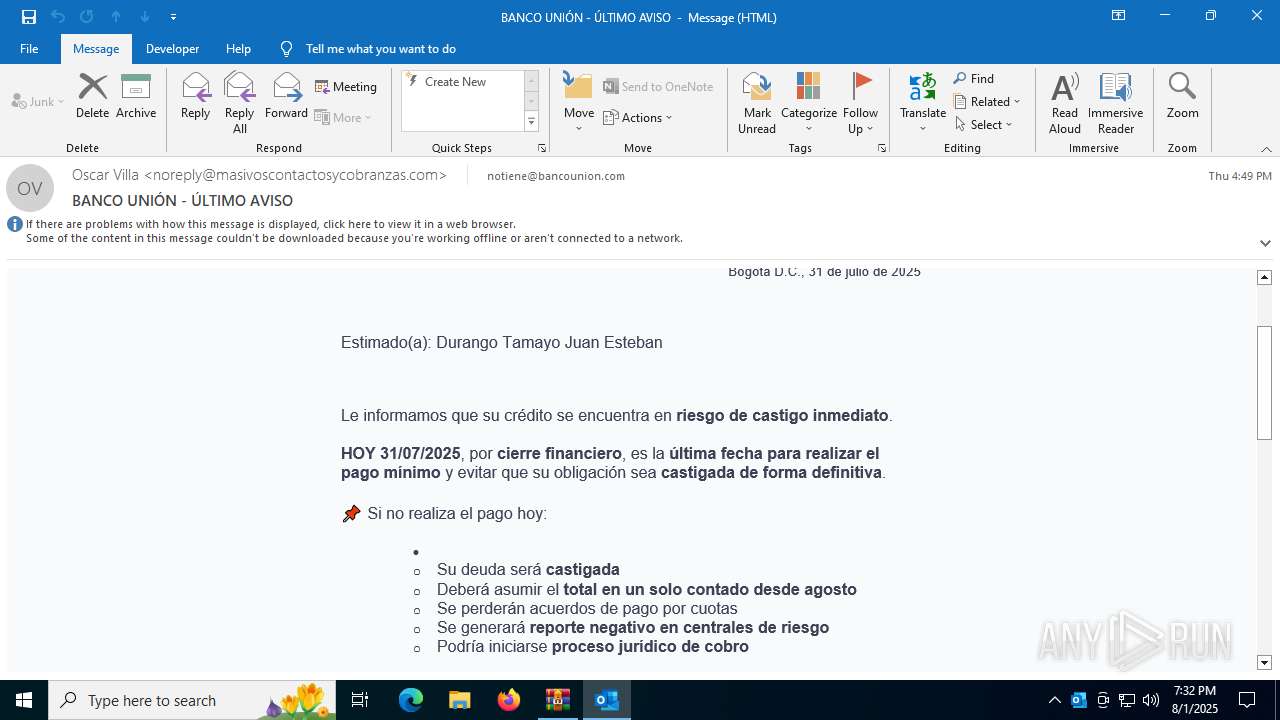
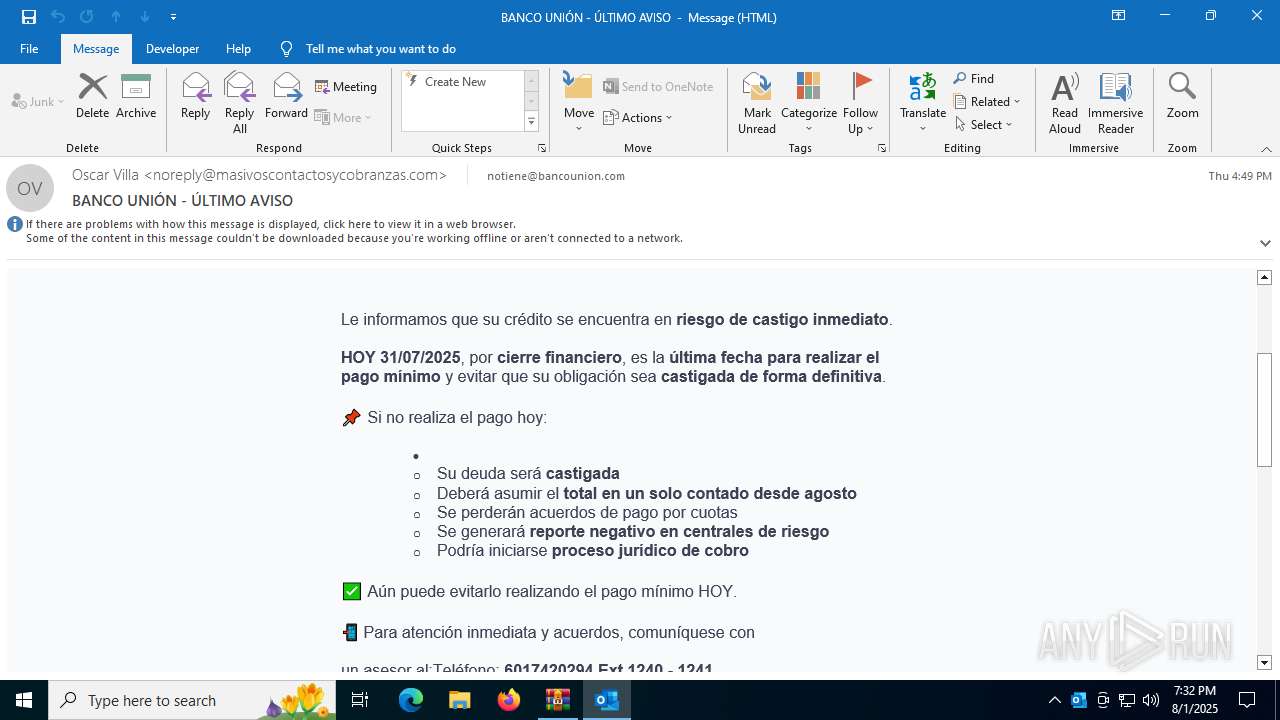
| File name: | Mensajes en cuarentena.zip |
| Full analysis: | https://app.any.run/tasks/d13c40a0-63a0-4ee4-9299-b74413babdca |
| Verdict: | Malicious activity |
| Analysis date: | August 01, 2025, 19:31:53 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v4.5 to extract, compression method=deflate |
| MD5: | 18BC2A92BCC4EBA2ED4BAAFCA04AE0AE |
| SHA1: | AD4DE88E1CC0A870B23265EECAB18974291FE725 |
| SHA256: | CF90FF723AAF722A8F4C706CE1EB0C684FE8C8BEFFFE71D8914118D706F8BA2D |
| SSDEEP: | 768:ElPBClA0bDII6eYsJTGlA83fS1CyfTxc9tg7kApKhpRGYBnkZdm:EzQ3vIIBDal5a1bfdsG7kZhpR3y0 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6420)
Reads Microsoft Outlook installation path
- WinRAR.exe (PID: 6420)
INFO
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 6420)
Application launched itself
- msedge.exe (PID: 2324)
- msedge.exe (PID: 7912)
Checks supported languages
- identity_helper.exe (PID: 7580)
- identity_helper.exe (PID: 7672)
Reads Environment values
- identity_helper.exe (PID: 7580)
- identity_helper.exe (PID: 7672)
Reads the computer name
- identity_helper.exe (PID: 7580)
- identity_helper.exe (PID: 7672)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 45 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:08:01 19:31:00 |
| ZipCRC: | 0xde7877e2 |
| ZipCompressedSize: | 4294967295 |
| ZipUncompressedSize: | 4294967295 |
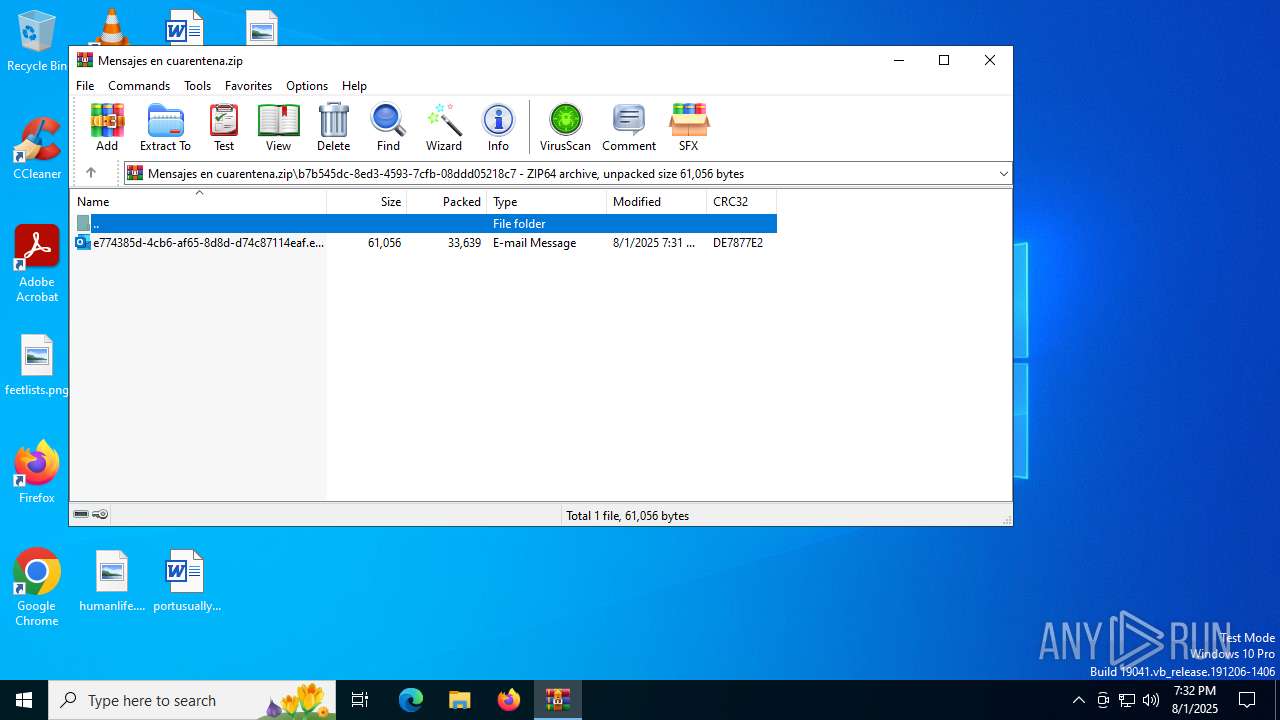
| ZipFileName: | b7b545dc-8ed3-4593-7cfb-08ddd05218c7/e774385d-4cb6-af65-8d8d-d74c87114eaf.eml |
Total processes
174
Monitored processes
36
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 640 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --extension-process --renderer-sub-type=extension --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --always-read-main-dll --field-trial-handle=4268,i,6529534140560174024,4193406554827351831,262144 --variations-seed-version --mojo-platform-channel-handle=4296 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1100 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=2084,i,6529534140560174024,4193406554827351831,262144 --variations-seed-version --mojo-platform-channel-handle=2672 /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1156 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --string-annotations --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --always-read-main-dll --field-trial-handle=2464,i,6529534140560174024,4193406554827351831,262144 --variations-seed-version --mojo-platform-channel-handle=2476 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1936 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=2424,i,6529534140560174024,4193406554827351831,262144 --variations-seed-version --mojo-platform-channel-handle=2808 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2216 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --extension-process --renderer-sub-type=extension --pdf-upsell-enabled --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --always-read-main-dll --field-trial-handle=3800,i,196952856171095682,6824069635458536546,262144 --variations-seed-version --mojo-platform-channel-handle=3840 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
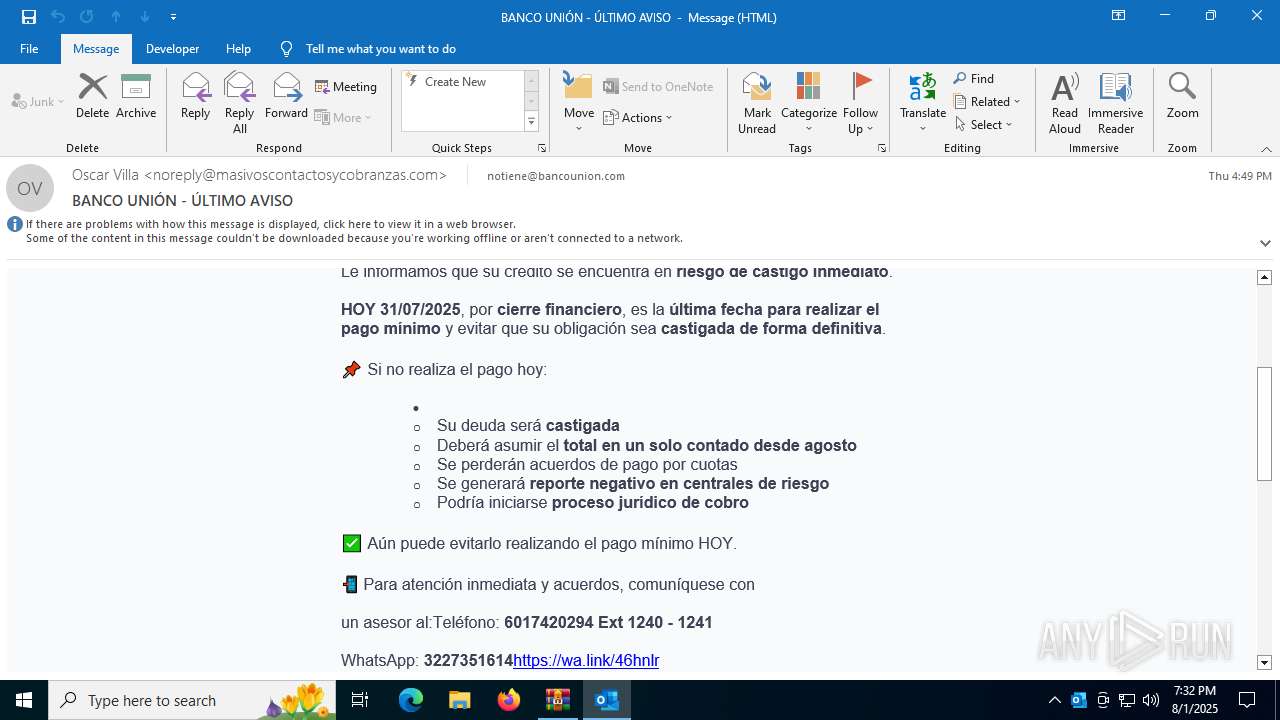
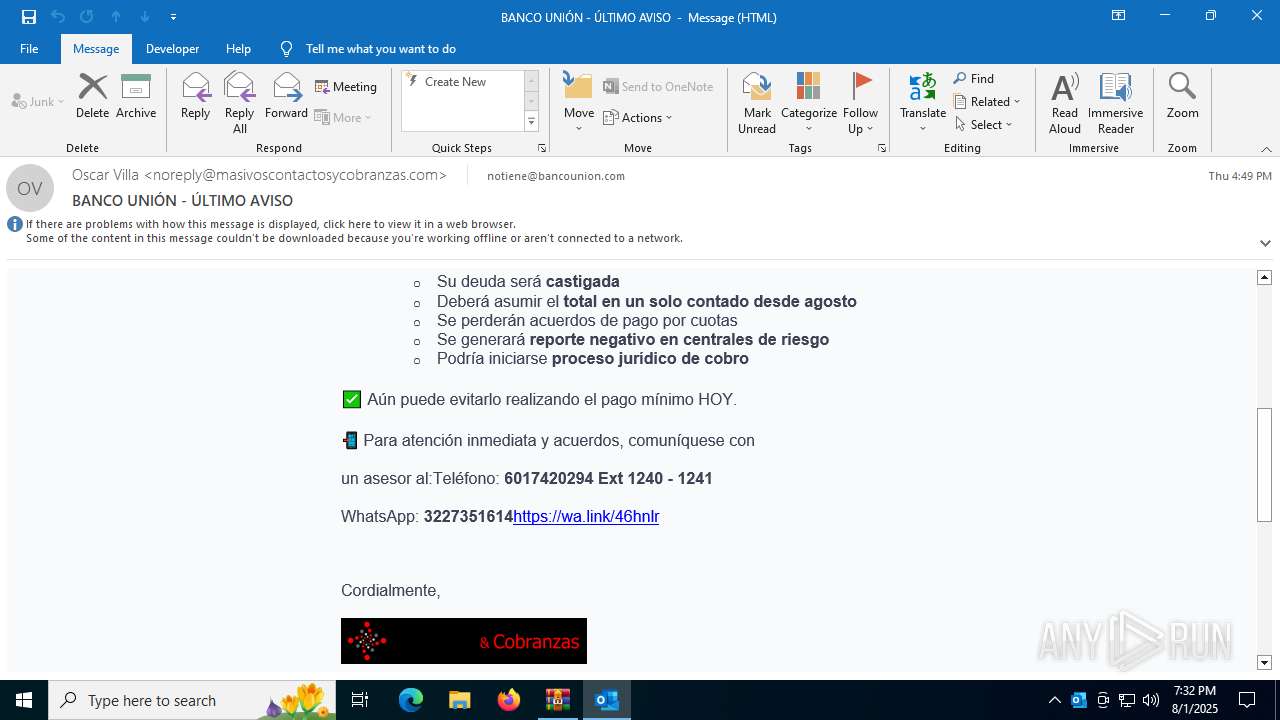
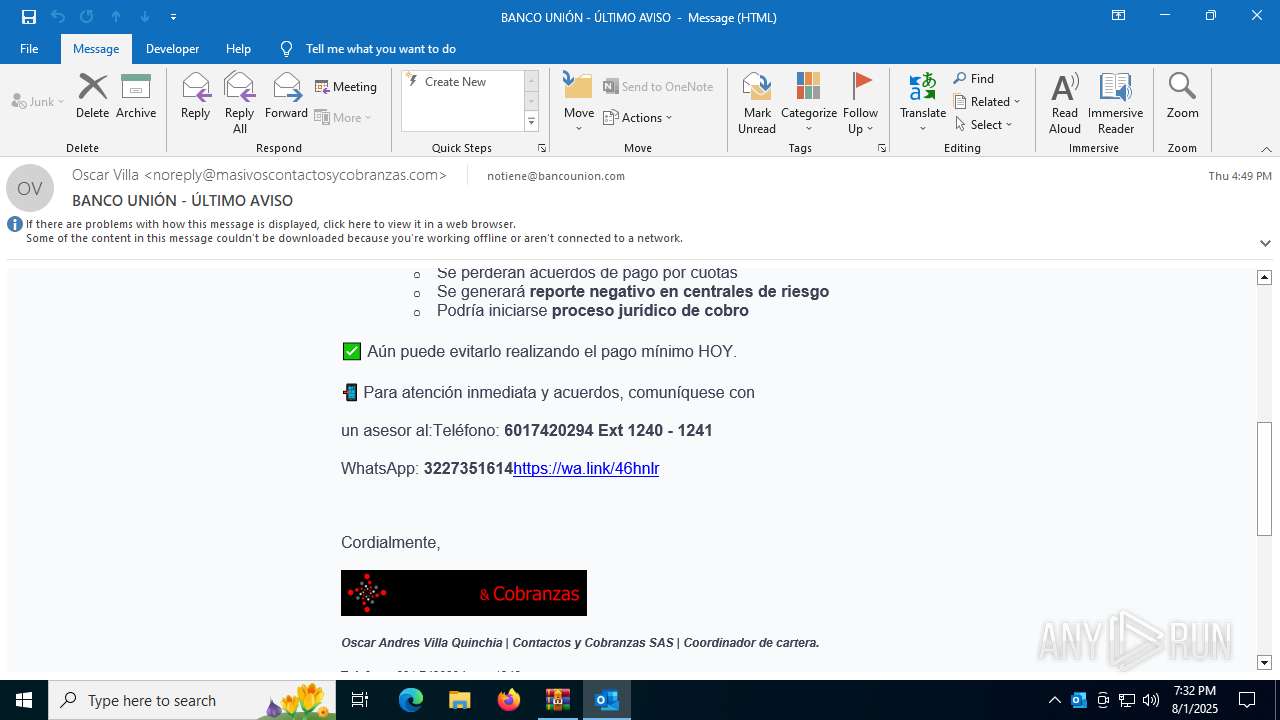
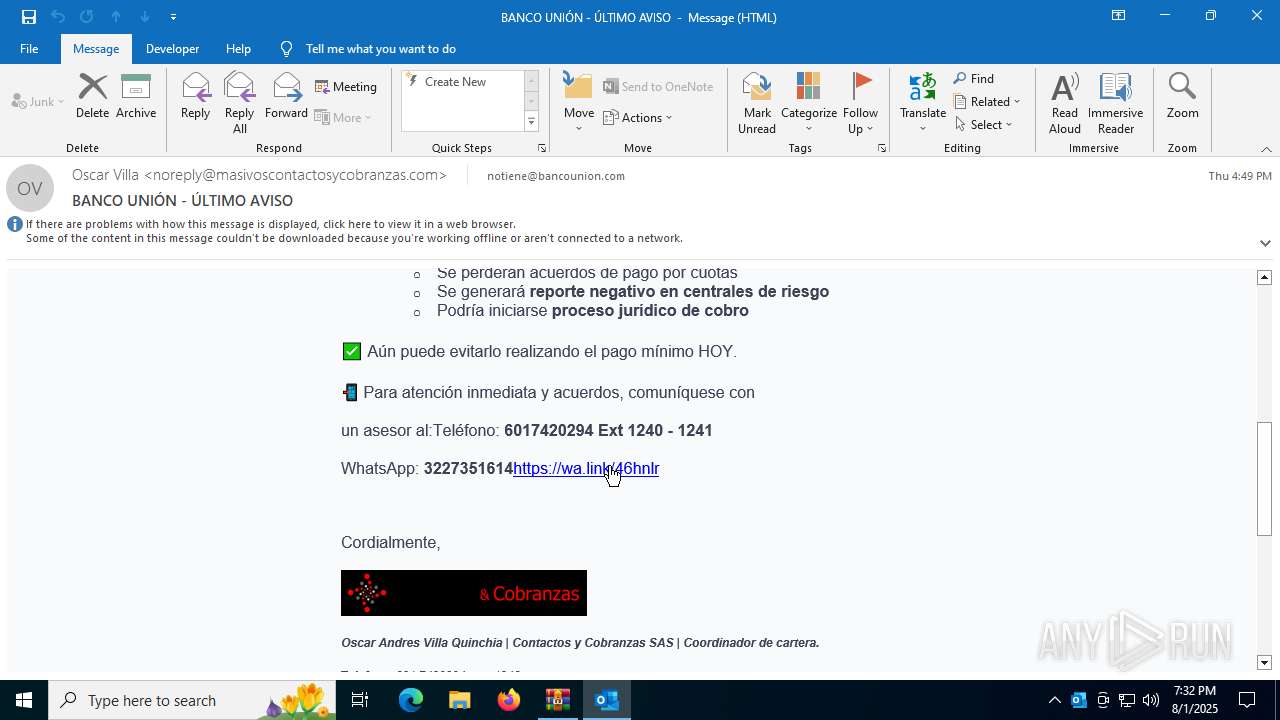
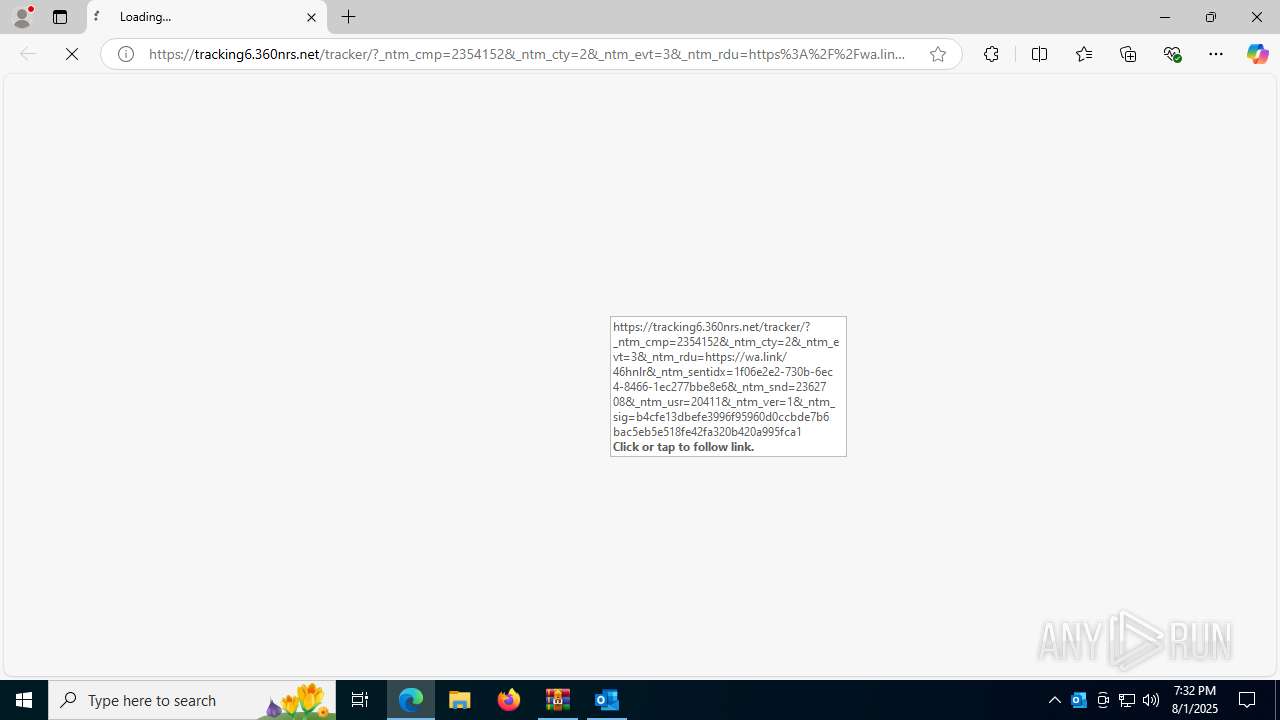
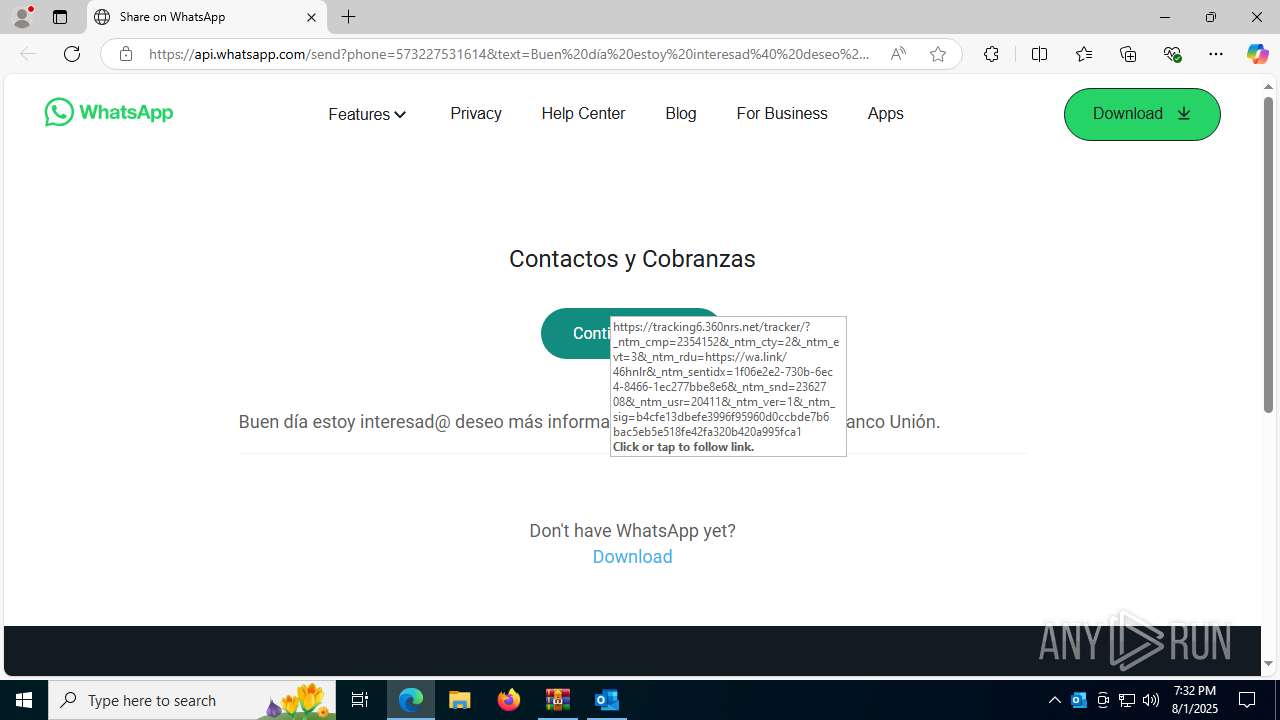
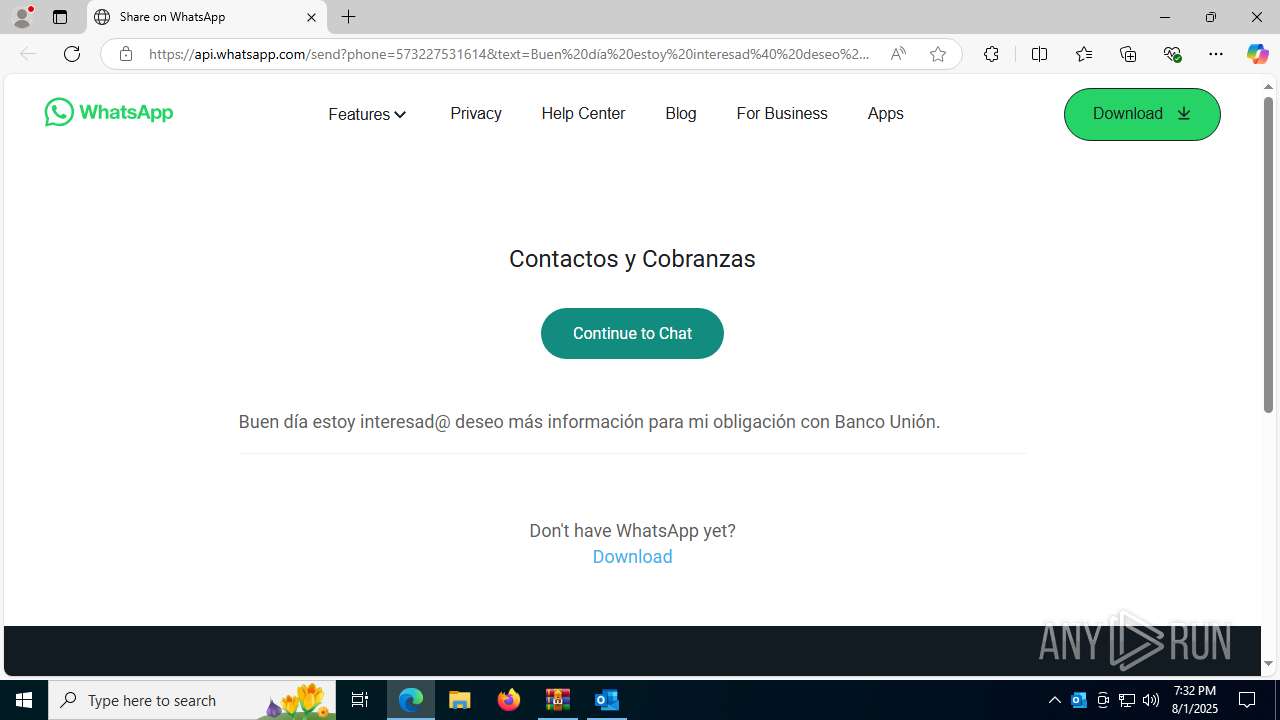
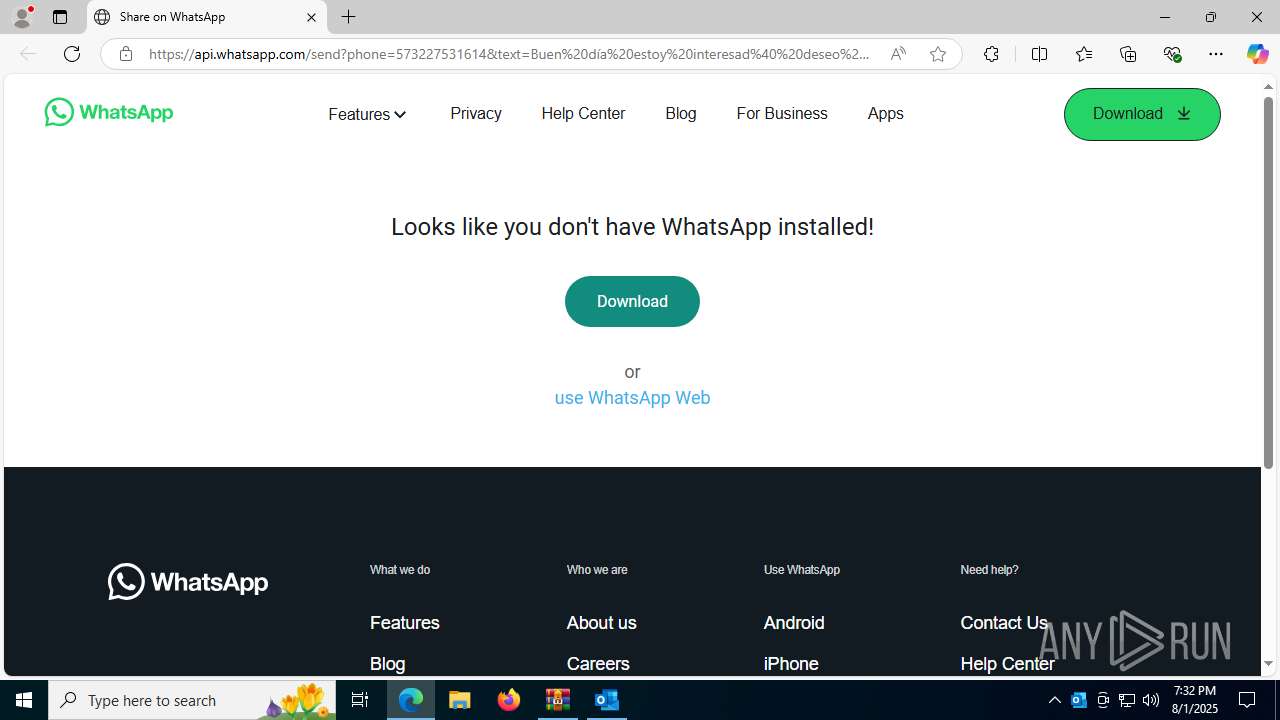
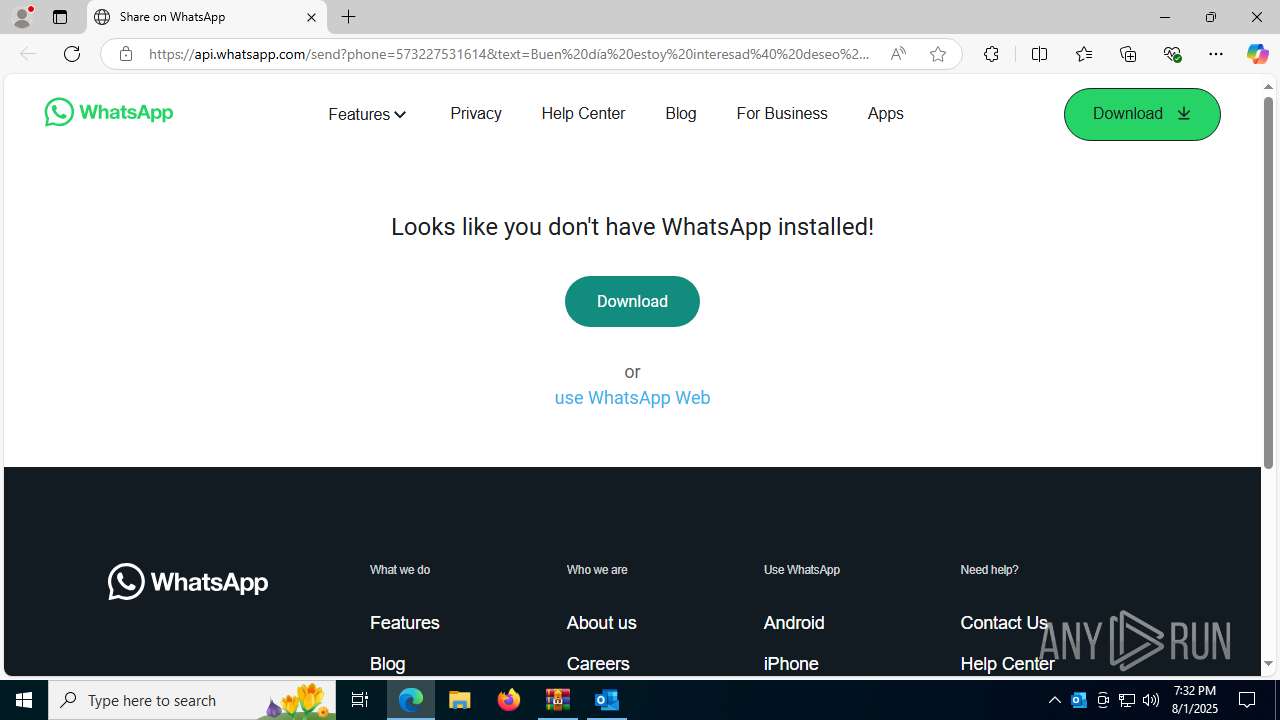
| 2324 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --single-argument https://tracking6.360nrs.net/tracker/?_ntm_cmp=2354152&_ntm_cty=2&_ntm_evt=3&_ntm_rdu=https%3A%2F%2Fwa.link%2F46hnlr&_ntm_sentIdx=1f06e2e2-730b-6ec4-8466-1ec277bbe8e6&_ntm_snd=2362708&_ntm_usr=20411&_ntm_ver=1&_ntm_sig=b4cfe13dbefe3996f95960d0ccbde7b6bac5eb5e518fe42fa320b420a995fca1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2356 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "79103C83-9C10-42F2-AC65-9E702F8C22F3" "54799C94-77DF-442C-ABCB-3A61D94143F6" "3504" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 2524 | "C:\Program Files (x86)\Microsoft\Edge\Application\133.0.3065.92\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=4740,i,196952856171095682,6824069635458536546,262144 --variations-seed-version --mojo-platform-channel-handle=4804 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\133.0.3065.92\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 3221226029 Version: 133.0.3065.92 Modules
| |||||||||||||||
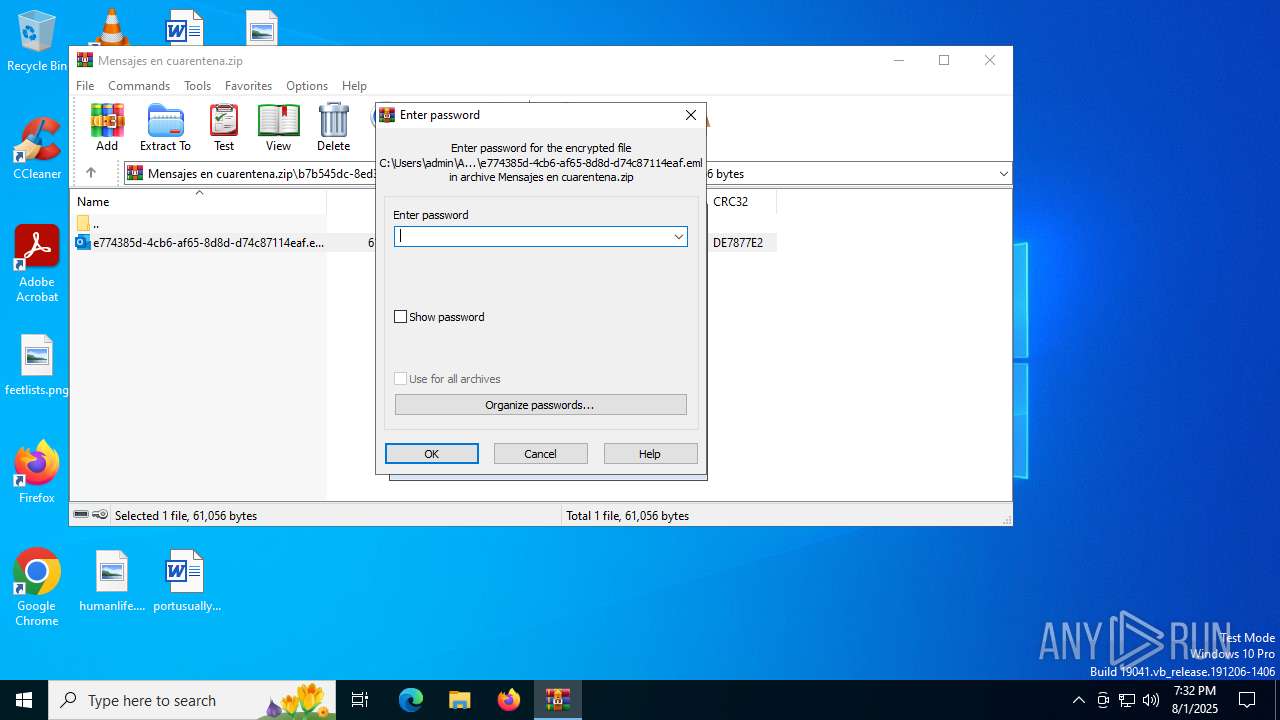
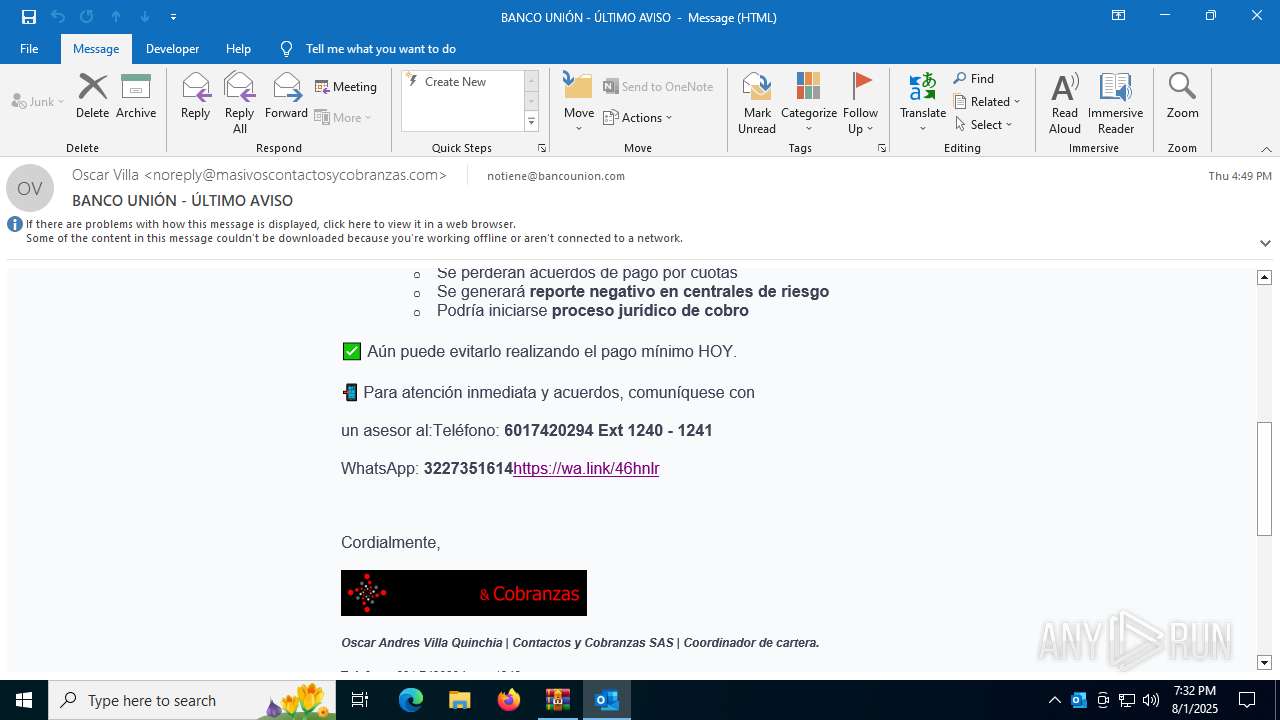
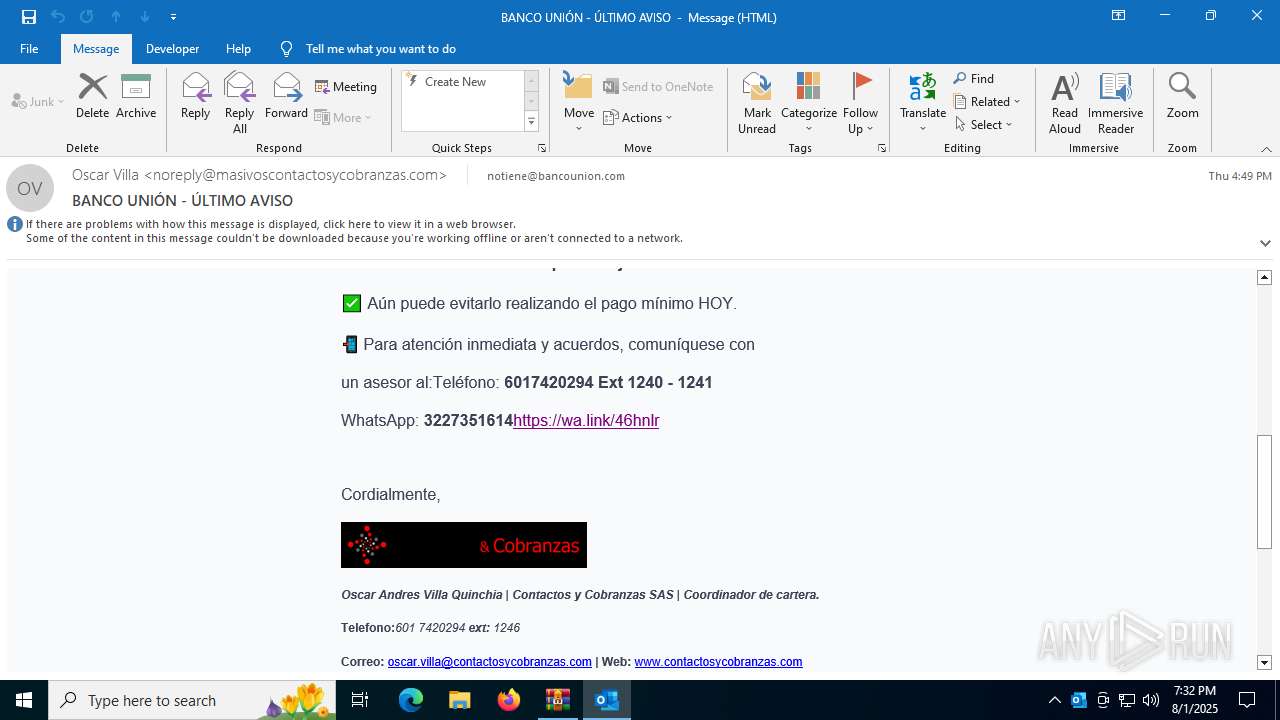
| 3504 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\Rar$DIb6420.3655\e774385d-4cb6-af65-8d8d-d74c87114eaf.eml" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 3788 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
17 835
Read events
17 434
Write events
351
Delete events
50
Modification events
| (PID) Process: | (6420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Mensajes en cuarentena.zip | |||
| (PID) Process: | (6420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.eml\OpenWithProgids |
| Operation: | write | Name: | Outlook.File.eml.15 |
Value: | |||
Executable files
0
Suspicious files
251
Text files
102
Unknown types
30
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3504 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 3504 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\333E951D.tmp | image | |
MD5:AD4BF1B58BC525C5AC0C6C78371482EB | SHA256:4D95AAF7B64C1EA050B0103B732D6245FDFBBACAB372B5EB2EA17A724F272B5A | |||
| 3504 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\5475cb191e478c39370a215b2da98a37e9dc813d.tbres | binary | |
MD5:B5941DFAB1432E6B9585B5379BF0D203 | SHA256:E6F1DF038A21191A08E79C7CD23886294715D325001FD40404207778C05D3CCC | |||
| 3504 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:9A39F69271D230F2008D11CFC4FA2D2C | SHA256:F5922D65A715F1407B40F44FE7B81FA169F927D1BAC9CA4BEF7BF82F7AAE95E1 | |||
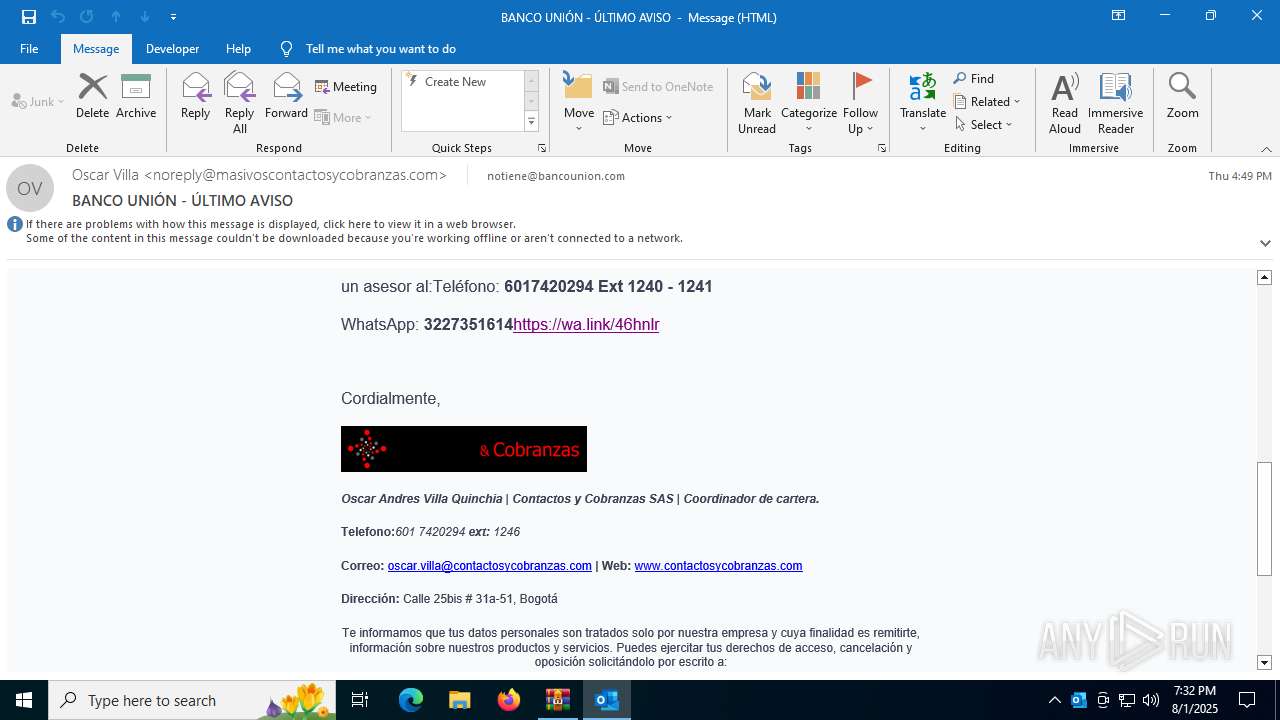
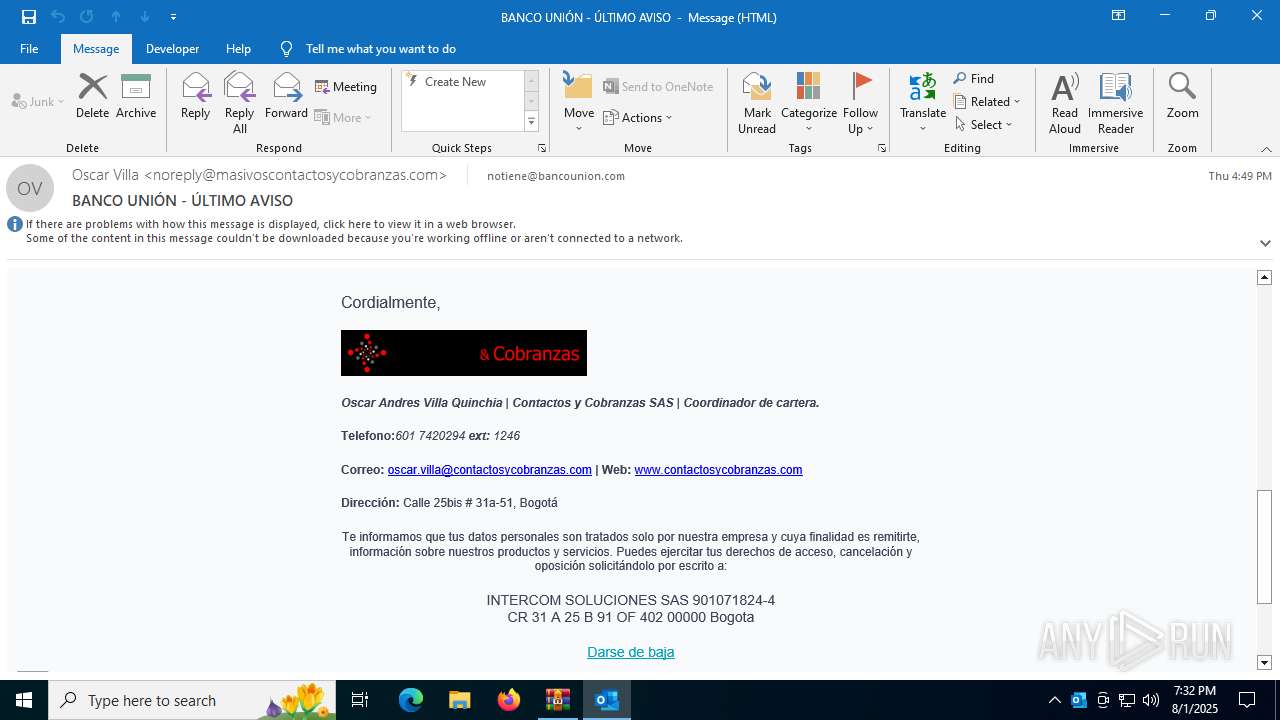
| 6420 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb6420.3655\e774385d-4cb6-af65-8d8d-d74c87114eaf.eml | eml | |
MD5:FF30094EB3C7EED6A11D85A45BE1656A | SHA256:D6742D583D359C37CA38E8ACEFE7A87A2C8C0588149CA817F74CECDA9760BEA3 | |||
| 2324 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old~RF193e86.TMP | — | |
MD5:— | SHA256:— | |||
| 3504 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:B5BE393A3A744C7D183447E8484AA2F7 | SHA256:3BAFACDB7C02ADE988E084BC600F56E2421ADF4F44D79CF20E61224737464081 | |||
| 2324 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2324 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF193ea5.TMP | — | |
MD5:— | SHA256:— | |||
| 2324 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
73
DNS requests
78
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.216.77.18:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.32.97.216:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3504 | OUTLOOK.EXE | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
1100 | msedge.exe | GET | 200 | 150.171.28.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:2VYchCj49364kcMBvU4qzDnAOoO0648gULOLdV6xw_E&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
4168 | SIHClient.exe | GET | 200 | 23.32.97.216:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4168 | SIHClient.exe | GET | 200 | 23.32.97.216:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1044 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5824 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 23.216.77.18:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.32.97.216:80 | www.microsoft.com | AKAMAI-AS | SE | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3504 | OUTLOOK.EXE | 52.123.128.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3504 | OUTLOOK.EXE | 2.16.168.101:443 | omex.cdn.office.net | Akamai International B.V. | RU | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
8148 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
8148 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
8148 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
8148 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
8148 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
8148 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
8148 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
8148 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |