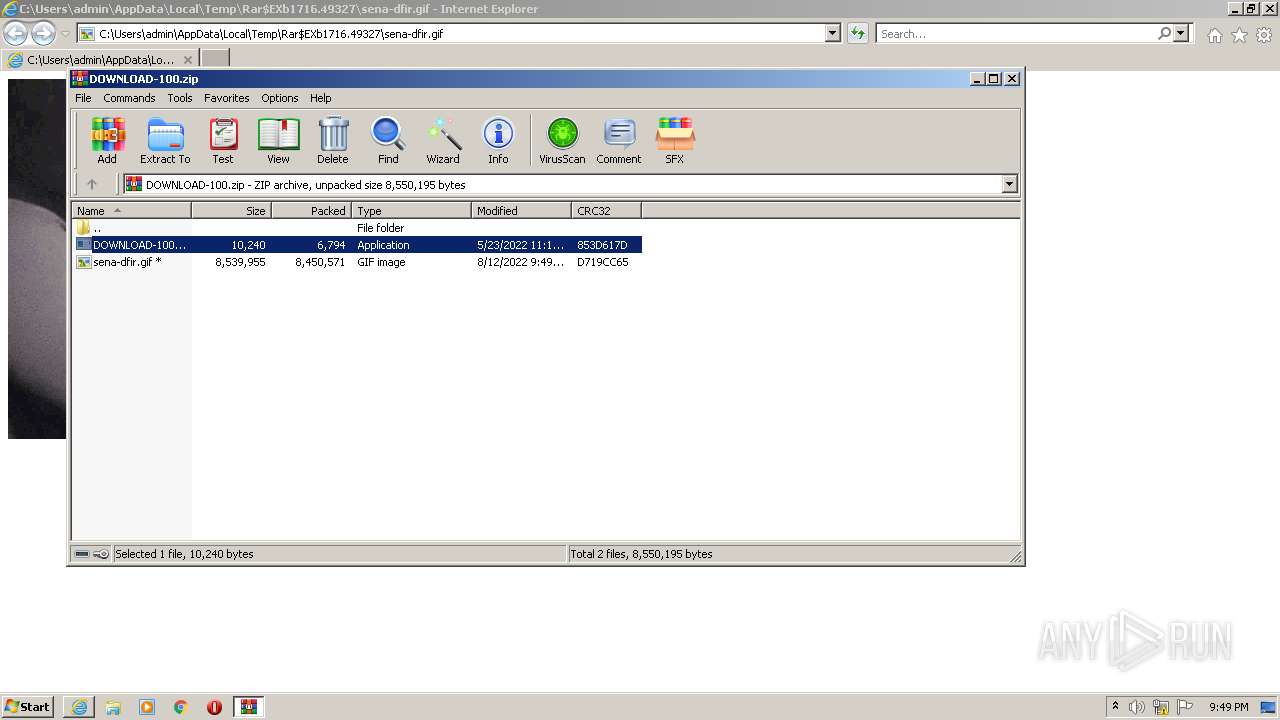
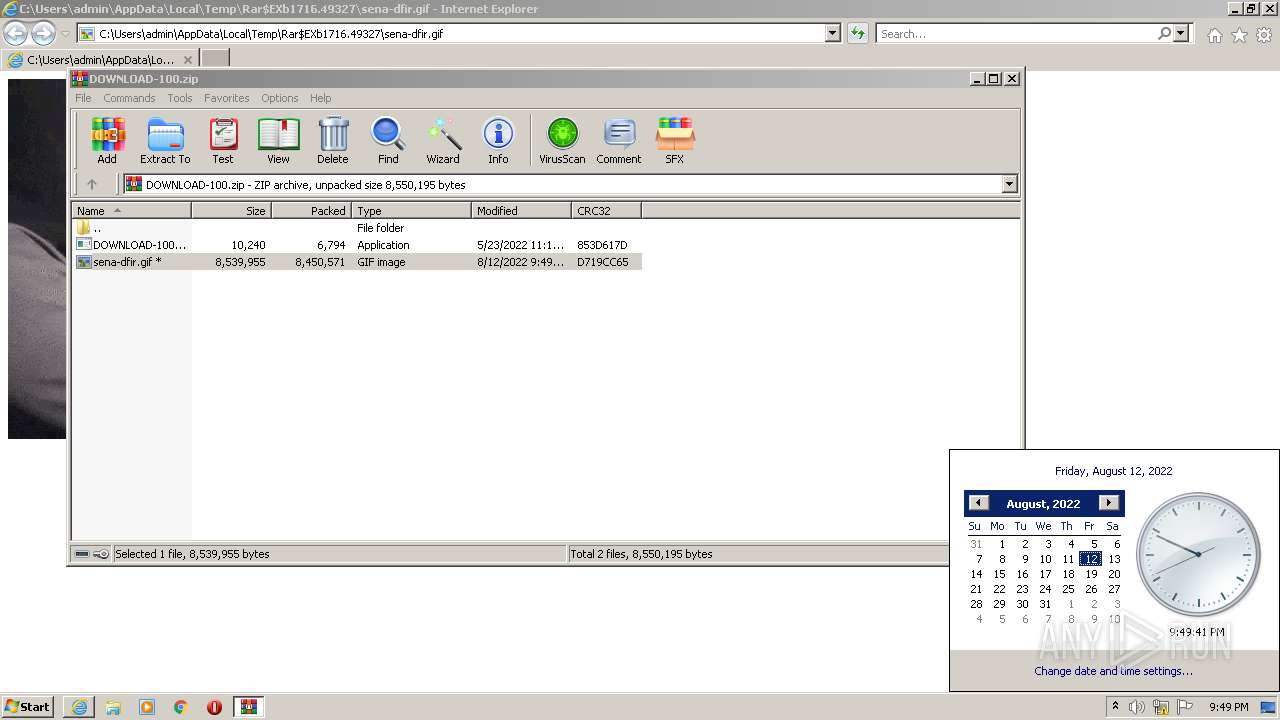
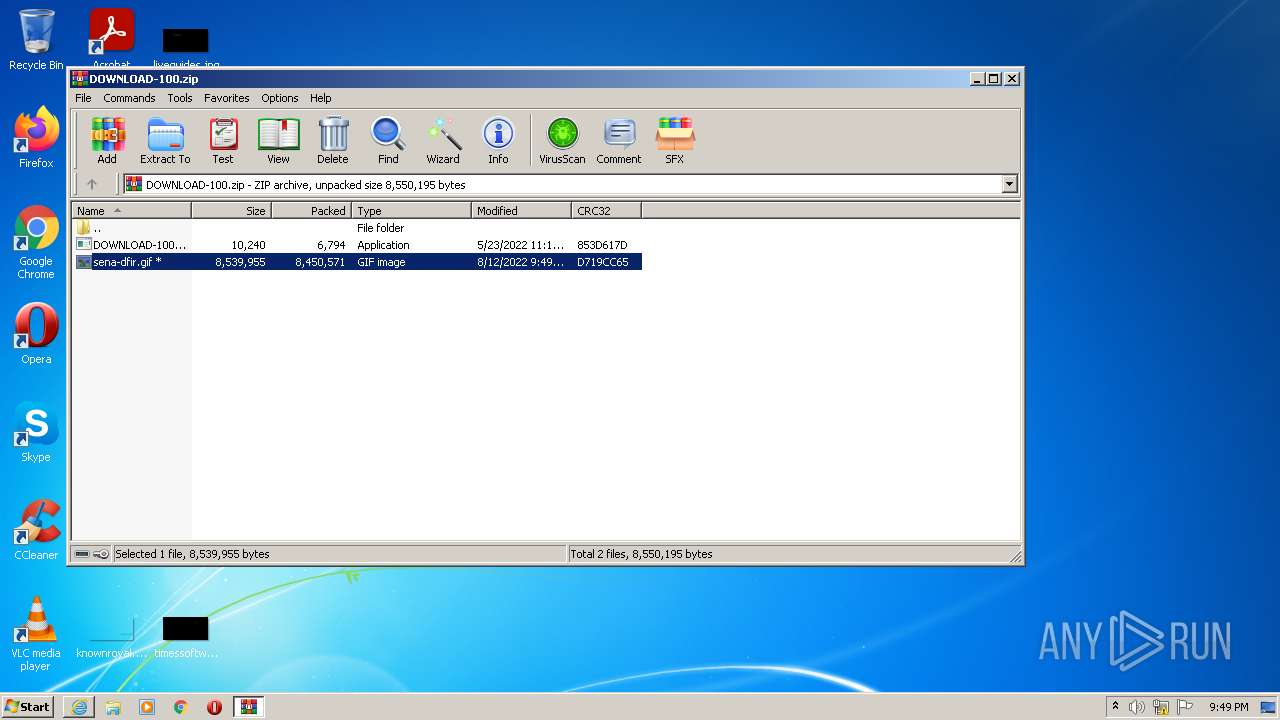
| File name: | DOWNLOAD-100.zip |
| Full analysis: | https://app.any.run/tasks/d8732162-332a-4f30-bab4-1e865dd7c592 |
| Verdict: | Malicious activity |
| Analysis date: | August 12, 2022, 20:48:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 3A857A5178641E533F2381540E366B2B |
| SHA1: | 68DC53253FD79331C9D9920B6EBD160077C71F6F |
| SHA256: | CF8A0892A10B319CC7F82232FB4C2DFCF42FE27CEC9D15F7BD9DB576D83202BF |
| SSDEEP: | 96:lgZr0lBsI+KelaCgZGacCGDUd9w6FRuhpXeAc0ATa2Sh7ae1vtJJunW26BhaGGeD:+LJx+ZXcCGUw6yddvn2c1lzF26BFG4zr |
MALICIOUS
Application was dropped or rewritten from another process
- DOWNLOAD-100.exe (PID: 3360)
Drops executable file immediately after starts
- WinRAR.exe (PID: 1716)
Changes settings of System certificates
- DOWNLOAD-100.exe (PID: 3360)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 328)
Checks supported languages
- WinRAR.exe (PID: 1716)
- DOWNLOAD-100.exe (PID: 3360)
Reads the computer name
- WinRAR.exe (PID: 1716)
- DOWNLOAD-100.exe (PID: 3360)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1716)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 1716)
Adds / modifies Windows certificates
- DOWNLOAD-100.exe (PID: 3360)
INFO
Checks supported languages
- iexplore.exe (PID: 3800)
- iexplore.exe (PID: 328)
- iexplore.exe (PID: 2692)
Reads the computer name
- iexplore.exe (PID: 328)
- iexplore.exe (PID: 3800)
- iexplore.exe (PID: 2692)
Changes internet zones settings
- iexplore.exe (PID: 3800)
Application launched itself
- iexplore.exe (PID: 3800)
- iexplore.exe (PID: 328)
Reads internet explorer settings
- iexplore.exe (PID: 328)
Checks Windows Trust Settings
- DOWNLOAD-100.exe (PID: 3360)
- iexplore.exe (PID: 3800)
Reads settings of System Certificates
- DOWNLOAD-100.exe (PID: 3360)
- iexplore.exe (PID: 3800)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | DOWNLOAD-100.exe |
|---|---|
| ZipUncompressedSize: | 10240 |
| ZipCompressedSize: | 6740 |
| ZipCRC: | 0x853d617d |
| ZipModifyDate: | 2022:05:23 17:16:04 |
| ZipCompression: | Deflated |
| ZipBitFlag: | 0x0001 |
| ZipRequiredVersion: | 20 |
Total processes
41
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 328 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3800 CREDAT:144385 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1716 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\DOWNLOAD-100.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2692 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3800 CREDAT:333057 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3360 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb1716.49327\DOWNLOAD-100.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb1716.49327\DOWNLOAD-100.exe | WinRAR.exe | ||||||||||||
User: admin Company: PoC-BootCamp Integrity Level: MEDIUM Exit code: 0 Version: 1 Modules
| |||||||||||||||
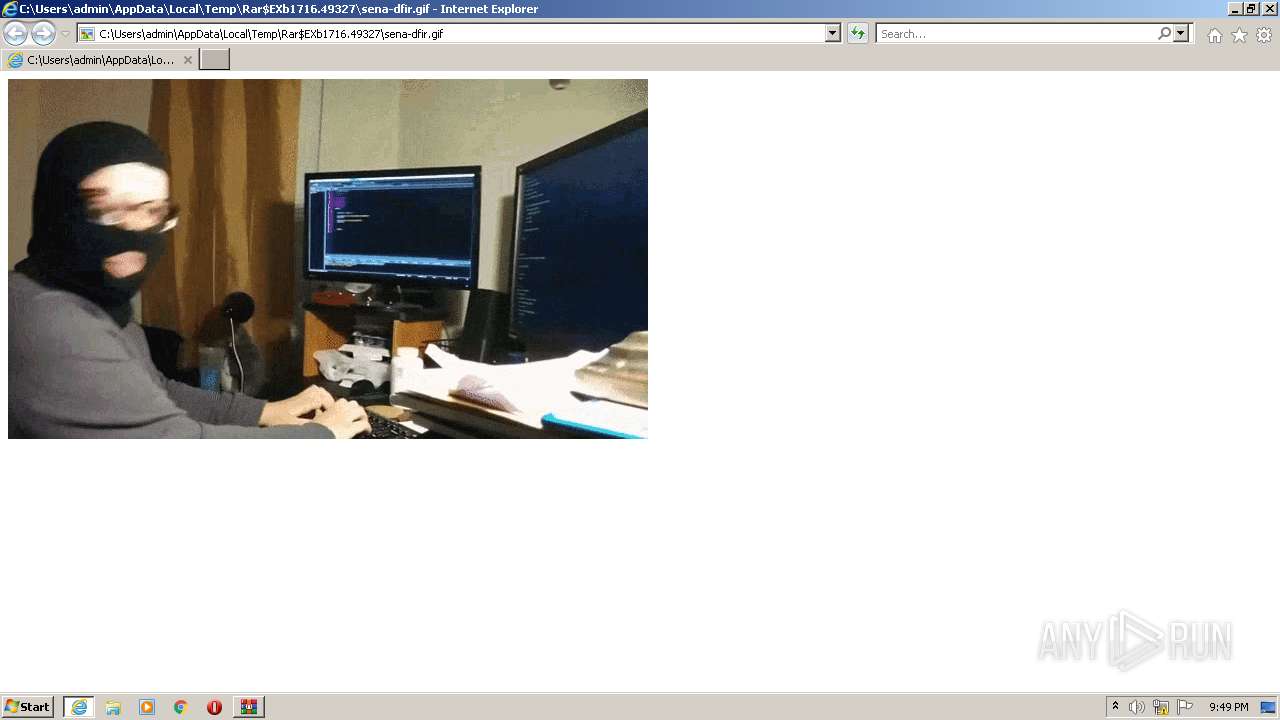
| 3800 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\AppData\Local\Temp\Rar$EXb1716.49327\sena-dfir.gif | C:\Program Files\Internet Explorer\iexplore.exe | DOWNLOAD-100.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
11 758
Read events
11 556
Write events
199
Delete events
3
Modification events
| (PID) Process: | (1716) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1716) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1716) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1716) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1716) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1716) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\DOWNLOAD-100.zip | |||
| (PID) Process: | (1716) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1716) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1716) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1716) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
1
Suspicious files
8
Text files
4
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3360 | DOWNLOAD-100.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\hacker-meme[1].gif | — | |
MD5:— | SHA256:— | |||
| 3360 | DOWNLOAD-100.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1716.49327\sena-dfir.gif | — | |
MD5:— | SHA256:— | |||
| 3360 | DOWNLOAD-100.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | der | |
MD5:— | SHA256:— | |||
| 3360 | DOWNLOAD-100.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\dfirsena[1].htm | html | |
MD5:— | SHA256:— | |||
| 3360 | DOWNLOAD-100.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:— | SHA256:— | |||
| 3360 | DOWNLOAD-100.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:— | SHA256:— | |||
| 3360 | DOWNLOAD-100.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\265C0DEB29181DD1891051371C5F863A_16BC07929C59A36AC8D9861B1F0E63C2 | der | |
MD5:— | SHA256:— | |||
| 3360 | DOWNLOAD-100.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3360 | DOWNLOAD-100.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:— | SHA256:— | |||
| 3360 | DOWNLOAD-100.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | der | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
16
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3800 | iexplore.exe | GET | — | 93.184.220.29:80 | http://crl3.digicert.com/Omniroot2025.crl | US | — | — | whitelisted |
3800 | iexplore.exe | GET | — | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | — | — | whitelisted |
3360 | DOWNLOAD-100.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
3360 | DOWNLOAD-100.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | der | 724 b | whitelisted |
3360 | DOWNLOAD-100.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
3360 | DOWNLOAD-100.exe | GET | 200 | 8.249.63.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b869a4ecb04a0f66 | US | compressed | 4.70 Kb | whitelisted |
3360 | DOWNLOAD-100.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCJ0LMUWb9%2FFgo%2FwIbO2Mkq | US | der | 472 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3360 | DOWNLOAD-100.exe | 172.67.1.225:443 | tinyurl.com | — | US | malicious |
3360 | DOWNLOAD-100.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3360 | DOWNLOAD-100.exe | 172.217.16.193:443 | c.tenor.com | Google Inc. | US | whitelisted |
3360 | DOWNLOAD-100.exe | 8.249.63.254:80 | ctldl.windowsupdate.com | Level 3 Communications, Inc. | US | suspicious |
3800 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
3360 | DOWNLOAD-100.exe | 142.250.181.227:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
— | — | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
3800 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3800 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3800 | iexplore.exe | 13.107.21.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
tinyurl.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
c.tenor.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl3.digicert.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |