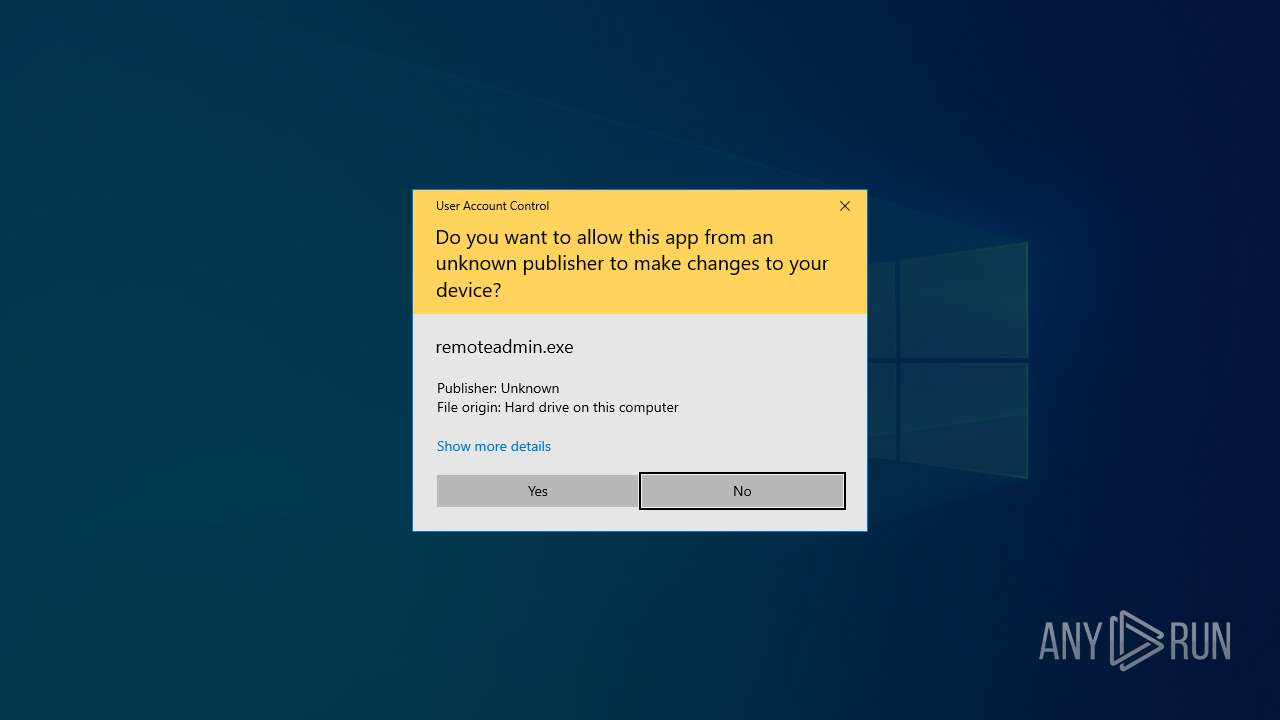
| File name: | remoteadmin.exe |
| Full analysis: | https://app.any.run/tasks/53c63014-e943-4a48-9e06-9b86359a0d76 |
| Verdict: | Malicious activity |
| Analysis date: | June 14, 2025, 19:33:41 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64 Mono/.Net assembly, for MS Windows, 2 sections |
| MD5: | C5D7D8CA672F1E3698BD3C786514E4A8 |
| SHA1: | E67D49D6C0DEBF580E884CD2931C27F973F4C9B2 |
| SHA256: | CF75A4BB6793649841A5C9C4A7DCD93E3BEA2924333D13BB855B8996B2CB8955 |
| SSDEEP: | 12288:ToeGfyaV2yYSgfbElgwer/i28AxgE+dj9+xhblvj3PpcxlPsxaAfIjDoUJ70QpCw:seGYyYnfbEljer/i28AxgE+dj9+xhbly |
MALICIOUS
Executing a file with an untrusted certificate
- remoteadmin.exe (PID: 188)
- remoteadmin.exe (PID: 5928)
- remoteadmin.exe (PID: 1132)
- remoteadmin.exe (PID: 5240)
- remoteadmin.exe (PID: 4444)
- remoteadmin.exe (PID: 4752)
- remoteadmin.exe (PID: 1728)
Changes the login/logoff helper path in the registry
- remoteadmin.exe (PID: 5928)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 7000)
- cmd.exe (PID: 760)
Changes the AppInit_DLLs value (autorun option)
- remoteadmin.exe (PID: 5928)
SUSPICIOUS
Reads the date of Windows installation
- remoteadmin.exe (PID: 188)
- remoteadmin.exe (PID: 5928)
Reads security settings of Internet Explorer
- remoteadmin.exe (PID: 188)
- remoteadmin.exe (PID: 5928)
Application launched itself
- remoteadmin.exe (PID: 188)
- updater.exe (PID: 812)
Connects to unusual port
- remoteadmin.exe (PID: 1132)
- remoteadmin.exe (PID: 4752)
Starts itself from another location
- remoteadmin.exe (PID: 5928)
The process executes via Task Scheduler
- remoteadmin.exe (PID: 5240)
- PLUGScheduler.exe (PID: 2996)
- updater.exe (PID: 812)
- remoteadmin.exe (PID: 4752)
- remoteadmin.exe (PID: 1728)
Starts CMD.EXE for commands execution
- remoteadmin.exe (PID: 5928)
- remoteadmin.exe (PID: 4444)
Executable content was dropped or overwritten
- remoteadmin.exe (PID: 5928)
INFO
Checks supported languages
- remoteadmin.exe (PID: 188)
- remoteadmin.exe (PID: 5928)
- remoteadmin.exe (PID: 1132)
- remoteadmin.exe (PID: 5240)
- remoteadmin.exe (PID: 1728)
Reads the computer name
- remoteadmin.exe (PID: 188)
- remoteadmin.exe (PID: 5928)
- remoteadmin.exe (PID: 1132)
- remoteadmin.exe (PID: 5240)
- remoteadmin.exe (PID: 1728)
Reads the machine GUID from the registry
- remoteadmin.exe (PID: 188)
- remoteadmin.exe (PID: 5928)
- remoteadmin.exe (PID: 1132)
- remoteadmin.exe (PID: 5240)
- remoteadmin.exe (PID: 1728)
Process checks computer location settings
- remoteadmin.exe (PID: 188)
- remoteadmin.exe (PID: 5928)
Creates files or folders in the user directory
- remoteadmin.exe (PID: 5928)
Launching a file from Task Scheduler
- cmd.exe (PID: 760)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:08:26 21:19:29+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 48 |
| CodeSize: | 472064 |
| InitializedDataSize: | 4096 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x0000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.1.2 |
| ProductVersionNumber: | 1.0.1.2 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | MS |
| FileDescription: | Graphical front end to Invoke-PS2EXE |
| FileVersion: | 1.0.1.2 |
| InternalName: | Win-PS2EXE.exe |
| LegalCopyright: | © Markus Scholtes 2023 |
| LegalTrademarks: | - |
| OriginalFileName: | Win-PS2EXE.exe |
| ProductName: | Win-PS2EXE |
| ProductVersion: | 1.0.1.2 |
| AssemblyVersion: | 1.0.1.2 |
Total processes
313
Monitored processes
25
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Users\admin\Desktop\remoteadmin.exe" | C:\Users\admin\Desktop\remoteadmin.exe | — | explorer.exe | |||||||||||
User: admin Company: MS Integrity Level: MEDIUM Description: Graphical front end to Invoke-PS2EXE Exit code: 0 Version: 1.0.1.2 Modules
| |||||||||||||||
| 760 | "cmd" /c schtasks /create /f /sc minute /mo 30 /tn "antiremove" /tr "C:\Users\admin\AppData\Roaming\Discord\Files\remoteadmin\antifucked.exe" /RL HIGHEST & exit | C:\Windows\System32\cmd.exe | — | remoteadmin.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 812 | "C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe" --wake --system | C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Google LLC Integrity Level: SYSTEM Description: Google Updater Exit code: 0 Version: 134.0.6985.0 Modules
| |||||||||||||||
| 1132 | "C:\Users\admin\AppData\Roaming\Discord\Files\remoteadmin\remoteadmin.exe" | C:\Users\admin\AppData\Roaming\Discord\Files\remoteadmin\remoteadmin.exe | remoteadmin.exe | ||||||||||||
User: admin Company: MS Integrity Level: HIGH Description: Graphical front end to Invoke-PS2EXE Exit code: 0 Version: 1.0.1.2 Modules
| |||||||||||||||
| 1728 | "C:\Users\admin\AppData\Roaming\Discord\Files\remoteadmin\remoteadmin.exe" | C:\Users\admin\AppData\Roaming\Discord\Files\remoteadmin\remoteadmin.exe | — | svchost.exe | |||||||||||
User: admin Company: MS Integrity Level: HIGH Description: Graphical front end to Invoke-PS2EXE Exit code: 0 Version: 1.0.1.2 Modules
| |||||||||||||||
| 2152 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2996 | "C:\Program Files\RUXIM\PLUGscheduler.exe" | C:\Program Files\RUXIM\PLUGScheduler.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Update LifeCycle Component Scheduler Exit code: 0 Version: 10.0.19041.3623 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3740 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3744 | "CMD" /c schtasks /run /i /tn "remoteadmin" | C:\Windows\System32\cmd.exe | — | remoteadmin.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 080
Read events
7 076
Write events
4
Delete events
0
Modification events
| (PID) Process: | (5928) remoteadmin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon |
| Operation: | write | Name: | Userinit |
Value: C:\Windows\System32\userinit.exe,C:\Users\admin\AppData\Roaming\Discord\Files\remoteadmin\remoteadmin.exe | |||
| (PID) Process: | (5928) remoteadmin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows |
| Operation: | write | Name: | AppInit_DLLs |
Value: C:\WINDOWS\xdwd.dll | |||
| (PID) Process: | (5928) remoteadmin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows |
| Operation: | write | Name: | LoadAppInit_DLLs |
Value: 1 | |||
| (PID) Process: | (5928) remoteadmin.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows |
| Operation: | write | Name: | RequireSignedAppInit_DLLs |
Value: 0 | |||
Executable files
3
Suspicious files
42
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5928 | remoteadmin.exe | C:\Users\admin\AppData\Roaming\Discord\Files\remoteadmin\remoteadmin.exe | executable | |
MD5:C5D7D8CA672F1E3698BD3C786514E4A8 | SHA256:CF75A4BB6793649841A5C9C4A7DCD93E3BEA2924333D13BB855B8996B2CB8955 | |||
| 2996 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.042.etl | binary | |
MD5:AB9303129E2242D02DC2069E5A4F3896 | SHA256:9031A5BD681D52A903A2BCA625F6D9D8B1456B26D2335CA8170BB39A2FE8F2A0 | |||
| 2996 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.045.etl | binary | |
MD5:A477FE56C25FCDB850EA1AAB8D01B5C2 | SHA256:5C85DC2B41C2D076D6B2653C0BA5F5681ADABFEBDA8883C704E625EB9338F505 | |||
| 2996 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.043.etl | binary | |
MD5:DCB94F822B793FF178C7332174A89DFB | SHA256:4AB418FA76DFA333D37F7401B40B0B0F0E806876C79AB2F36CD3FD7CCAD8665B | |||
| 5928 | remoteadmin.exe | C:\Users\admin\AppData\Roaming\Discord\Files\remoteadmin\antifucked.exe | executable | |
MD5:C5D7D8CA672F1E3698BD3C786514E4A8 | SHA256:CF75A4BB6793649841A5C9C4A7DCD93E3BEA2924333D13BB855B8996B2CB8955 | |||
| 2996 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.050.etl | binary | |
MD5:09359EE89B0634478ADFF73CDA7BFB12 | SHA256:4D800AC7C55960B107C9D3E40F63130407835E69DF4F5C558C500FC0BD20D8ED | |||
| 5928 | remoteadmin.exe | C:\Windows\xdwd.dll | executable | |
MD5:16E5A492C9C6AE34C59683BE9C51FA31 | SHA256:35C8D022E1D917F1AABDCEAE98097CCC072161B302F84C768CA63E4B32AC2B66 | |||
| 2996 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.048.etl | binary | |
MD5:0DE8B8CBE71A7CD60D67AFE279E1ACB9 | SHA256:D17A442ABEB021BFA77E5EDAB3D7F3C6FFEA9C33B8D04409D149B518C5FDB57C | |||
| 2996 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.046.etl | binary | |
MD5:B787593A02A4E0A601164A65952D0CB9 | SHA256:3594AD496D8E1771BCC3E8B6F68B4C2B4190A9A331FB43F068A7DF4E1894E2CF | |||
| 2996 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.047.etl | binary | |
MD5:F9485F2BA891697F8B6CF8FB1E7F42C0 | SHA256:69146D4AAEFB8609745B6CA780B48ABC66054AA3CDB8061248CF7B32F3B32617 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
82
DNS requests
45
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2292 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3504 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3504 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5888 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5412 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5412 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
2108 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2468 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2336 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2292 | svchost.exe | 20.190.159.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2292 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
1268 | svchost.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
must-directed.gl.at.ply.gg |
| unknown |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | A Network Trojan was detected | MALWARE [ANY.RUN] Suspected domain Associated with Malware Distribution (.ply .gg) |
2200 | svchost.exe | Misc activity | ET TA_ABUSED_SERVICES Tunneling Service in DNS Lookup (* .ply .gg) |
2200 | svchost.exe | Potentially Bad Traffic | ET INFO playit .gg Tunneling Domain in DNS Lookup |
2152 | svchost.exe | A Network Trojan was detected | MALWARE [ANY.RUN] Suspected domain Associated with Malware Distribution (.ply .gg) |
2152 | svchost.exe | Misc activity | ET TA_ABUSED_SERVICES Tunneling Service in DNS Lookup (* .ply .gg) |
2152 | svchost.exe | Potentially Bad Traffic | ET INFO playit .gg Tunneling Domain in DNS Lookup |