| File name: | CleanThis.exe |
| Full analysis: | https://app.any.run/tasks/1bf6a351-08a0-4c13-9b56-ae3df8b3d075 |
| Verdict: | Malicious activity |
| Analysis date: | December 09, 2023, 01:32:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | A50FC0DA1D2B3C4AA8A6ADACCF69A5DE |
| SHA1: | E001F4043AB4BE644EA10E0D65303D6E57B31FFE |
| SHA256: | CF6EB8377789E316629C0396A2DBB53C69B5FD67BBD0E7163B8D305AAA756E90 |
| SSDEEP: | 12288:EQIfqOiX9P/aazd1ctyDXHrJW2dGMToCRn5VxWRaqsrOkqgyQDd:EQIydX/d1rTLRd/TvVUsrOkqFQDd |
MALICIOUS
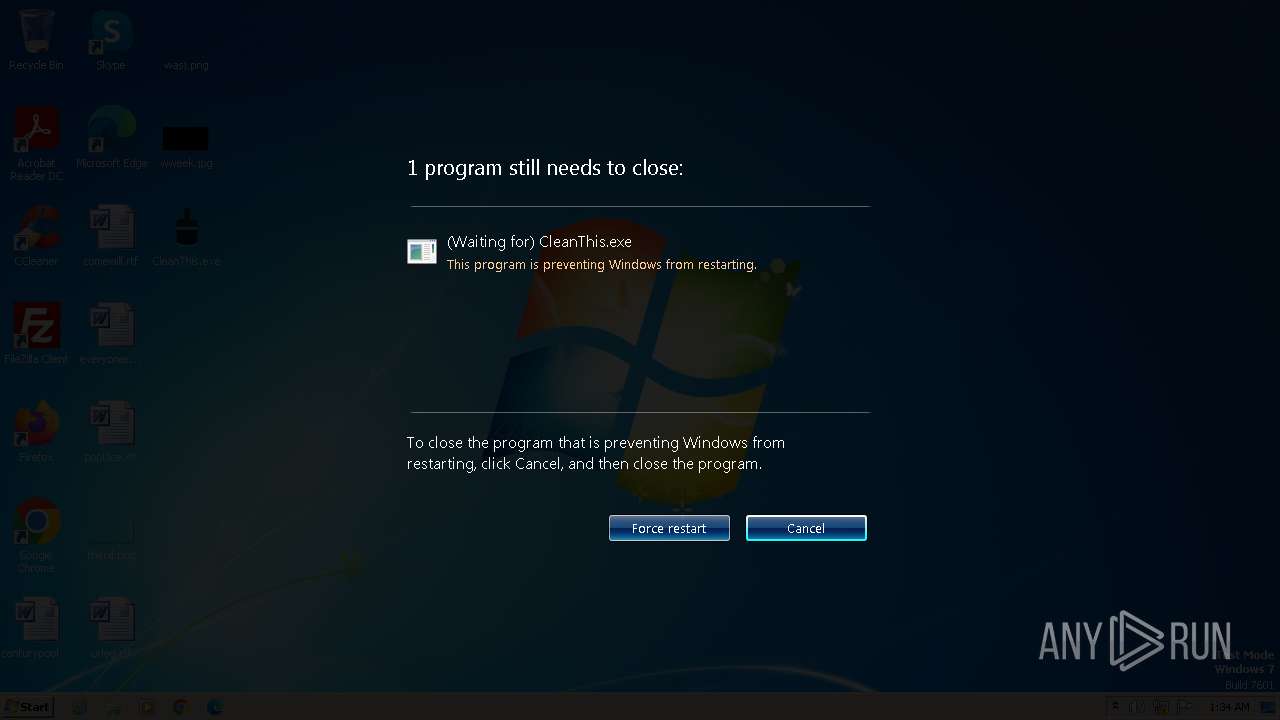
Drops the executable file immediately after the start
- CleanThis.exe (PID: 280)
Change Internet Settings
- CleanThis.exe (PID: 280)
- gog.exe (PID: 1028)
Creates a writable file in the system directory
- svchost.exe (PID: 904)
- svchost.exe (PID: 1284)
Steals credentials from Web Browsers
- taskhost.exe (PID: 332)
Changes the login/logoff helper path in the registry
- gog.exe (PID: 1028)
Changes Security Center notification settings
- svchost.exe (PID: 780)
SUSPICIOUS
Reads the Internet Settings
- CleanThis.exe (PID: 280)
- gog.exe (PID: 1028)
- sipnotify.exe (PID: 1804)
Reads Microsoft Outlook installation path
- CleanThis.exe (PID: 280)
Reads Internet Explorer settings
- CleanThis.exe (PID: 280)
Detected use of alternative data streams (AltDS)
- svchost.exe (PID: 820)
Reads settings of System Certificates
- sipnotify.exe (PID: 1804)
INFO
Reads the computer name
- CleanThis.exe (PID: 280)
- CleanThis.exe (PID: 3112)
- IMEKLMG.EXE (PID: 2124)
- IMEKLMG.EXE (PID: 2108)
- wmpnscfg.exe (PID: 2388)
- gog.exe (PID: 1028)
- wmpnscfg.exe (PID: 2432)
- mscorsvw.exe (PID: 2796)
Reads the machine GUID from the registry
- CleanThis.exe (PID: 280)
Checks supported languages
- CleanThis.exe (PID: 280)
- CleanThis.exe (PID: 3112)
- IMEKLMG.EXE (PID: 2108)
- IMEKLMG.EXE (PID: 2124)
- wmpnscfg.exe (PID: 2388)
- gog.exe (PID: 1028)
- mscorsvw.exe (PID: 2796)
- wmpnscfg.exe (PID: 2432)
Checks proxy server information
- CleanThis.exe (PID: 280)
Creates files or folders in the user directory
- CleanThis.exe (PID: 280)
Manual execution by a user
- CleanThis.exe (PID: 3112)
- smss.exe (PID: 392)
- smss.exe (PID: 332)
Reads the time zone
- services.exe (PID: 504)
- svchost.exe (PID: 780)
- svchost.exe (PID: 1404)
Process checks are UAC notifies on
- IMEKLMG.EXE (PID: 2124)
- IMEKLMG.EXE (PID: 2108)
Reads the Internet Settings
- explorer.exe (PID: 1808)
Reads security settings of Internet Explorer
- sipnotify.exe (PID: 1804)
Creates files in the program directory
- SearchIndexer.exe (PID: 2328)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (38.2) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (37.5) |
| .dll | | | Win32 Dynamic Link Library (generic) (9.2) |
| .exe | | | Win32 Executable (generic) (6.3) |
| .exe | | | Win16/32 Executable Delphi generic (2.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2011:05:02 23:13:07+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 598016 |
| InitializedDataSize: | 40960 |
| UninitializedDataSize: | 925696 |
| EntryPoint: | 0x173f80 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
Total processes
96
Monitored processes
49
Malicious processes
4
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 280 | "C:\Users\admin\Desktop\CleanThis.exe" | C:\Users\admin\Desktop\CleanThis.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1073807364 Modules
| |||||||||||||||
| 280 | \??\C:\Windows\system32\autochk.exe * | C:\Windows\System32\autochk.exe | — | smss.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Auto Check Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 284 | C:\Windows\system32\DllHost.exe /Processid:{E10F6C3A-F1AE-4ADC-AA9D-2FE65525666E} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 332 | \SystemRoot\System32\smss.exe 00000000 00000048 | C:\Windows\System32\smss.exe | — | smss.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Session Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 332 | "taskhost.exe" | C:\Windows\System32\taskhost.exe | services.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 356 | %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,12288,512 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=winsrv:ConServerDllInitialization,2 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16 | C:\Windows\System32\csrss.exe | — | smss.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Client Server Runtime Process Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 392 | \SystemRoot\System32\smss.exe 00000001 00000048 | C:\Windows\System32\smss.exe | — | smss.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Session Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 400 | wininit.exe | C:\Windows\System32\wininit.exe | — | smss.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Start-Up Application Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 408 | %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,12288,512 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=winsrv:ConServerDllInitialization,2 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16 | C:\Windows\System32\csrss.exe | — | smss.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Client Server Runtime Process Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 452 | winlogon.exe | C:\Windows\System32\winlogon.exe | — | smss.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Logon Application Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
44 158
Read events
43 523
Write events
582
Delete events
53
Modification events
| (PID) Process: | (280) CleanThis.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | WarnOnZoneCrossing |
Value: 0 | |||
| (PID) Process: | (280) CleanThis.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (280) CleanThis.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (280) CleanThis.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (280) CleanThis.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (280) CleanThis.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (280) CleanThis.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005A010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (280) CleanThis.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (280) CleanThis.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (280) CleanThis.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | WarnonBadCertRecving |
Value: 1 | |||
Executable files
1
Suspicious files
17
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 860 | svchost.exe | C:\Windows\ServiceProfiles\LocalService\AppData\Local\~FontCache-FontFace.dat | — | |
MD5:— | SHA256:— | |||
| 1404 | svchost.exe | C:\ProgramData\Microsoft\Diagnosis\events00.rbs | — | |
MD5:— | SHA256:— | |||
| 1404 | svchost.exe | C:\ProgramData\Microsoft\Diagnosis\events01.rbs | — | |
MD5:— | SHA256:— | |||
| 780 | svchost.exe | C:\Windows\System32\Winevt\Logs\System.evtx | — | |
MD5:— | SHA256:— | |||
| 780 | svchost.exe | C:\Windows\System32\Winevt\Logs\Security.evtx | — | |
MD5:— | SHA256:— | |||
| 2328 | SearchIndexer.exe | C:\ProgramData\Microsoft\Search\Data\Applications\Windows\Windows.edb | — | |
MD5:— | SHA256:— | |||
| 280 | CleanThis.exe | C:\Users\admin\AppData\Roaming\gog.exe | executable | |
MD5:A50FC0DA1D2B3C4AA8A6ADACCF69A5DE | SHA256:CF6EB8377789E316629C0396A2DBB53C69B5FD67BBD0E7163B8D305AAA756E90 | |||
| 1804 | sipnotify.exe | C:\Users\admin\AppData\Local\microsoft\windows\SipNotify\eoscontent\en-us.html | html | |
MD5:9752942B57692148B9F614CF4C119A36 | SHA256:E31B834DD53FA6815F396FC09C726636ABF98F3367F0CF1590EF5EB3801C75D1 | |||
| 904 | svchost.exe | C:\Windows\Tasks\SA.DAT | binary | |
MD5:F1A6CD5ADAAB953A6764EA364E17BFB8 | SHA256:12DC5CCD7FECAFE070976A1916E9672E3D53085633C86957AEE305CCC584184C | |||
| 860 | svchost.exe | C:\Windows\ServiceProfiles\LocalService\AppData\Local\~FontCache-System.dat | binary | |
MD5:007372EB8689ABB12F9C3272E643C0A6 | SHA256:91AFBEC1BA1869A3889960F9F2660EB5C24B3D8C14273337A4586DBEA074FF42 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
12
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1804 | sipnotify.exe | HEAD | 200 | 23.197.138.118:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133465592804210000 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
280 | CleanThis.exe | 94.244.80.60:80 | — | UAB Kauno interneto sistemos | LT | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1104 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1804 | sipnotify.exe | 23.197.138.118:80 | query.prod.cms.rt.microsoft.com | Akamai International B.V. | US | unknown |
2764 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dns.msftncsi.com |
| shared |
query.prod.cms.rt.microsoft.com |
| whitelisted |