| URL: | https://java-for-minecraft.com/en/ |
| Full analysis: | https://app.any.run/tasks/d2d0cc63-1e08-4a1a-a82c-bf183cfda316 |
| Verdict: | Malicious activity |
| Analysis date: | January 04, 2024, 09:33:57 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MD5: | 3E4A97208BA3FCF0C382AF4E250385EA |
| SHA1: | 93D7A7BFF7AE94D3BCDB82A778935191D3C4FCCB |
| SHA256: | CF4A46AC0D49800B4B0051E3D828345523ABC4D5D24F7C85BDE5AC661D171036 |
| SSDEEP: | 3:N8gSX4TKFn:2T4GFn |
MALICIOUS
Creates a writable file in the system directory
- installer.exe (PID: 5428)
SUSPICIOUS
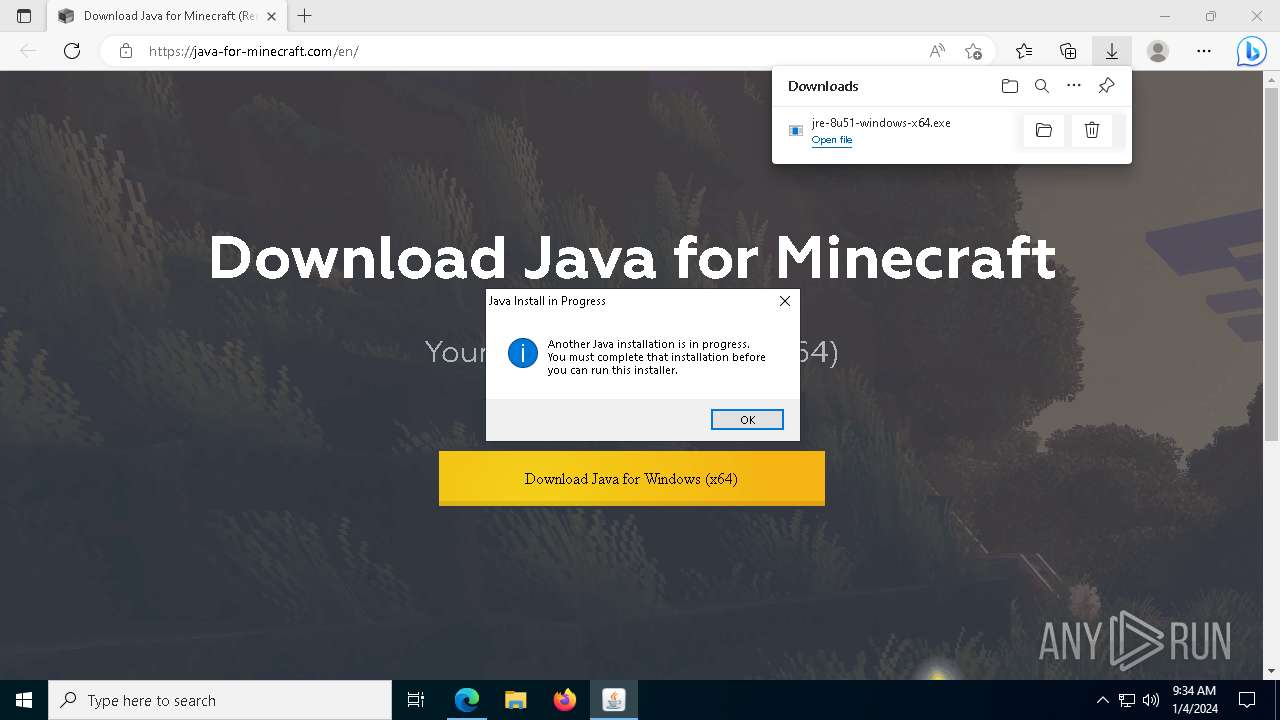
Checks for Java to be installed
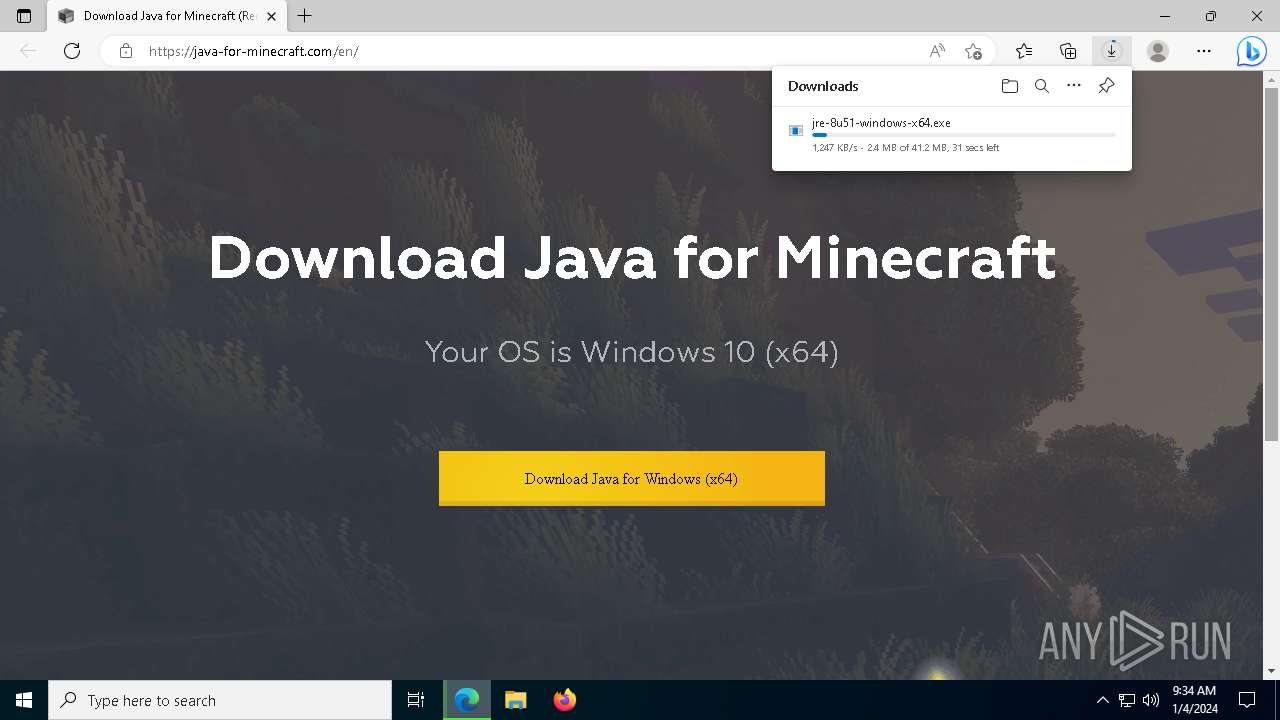
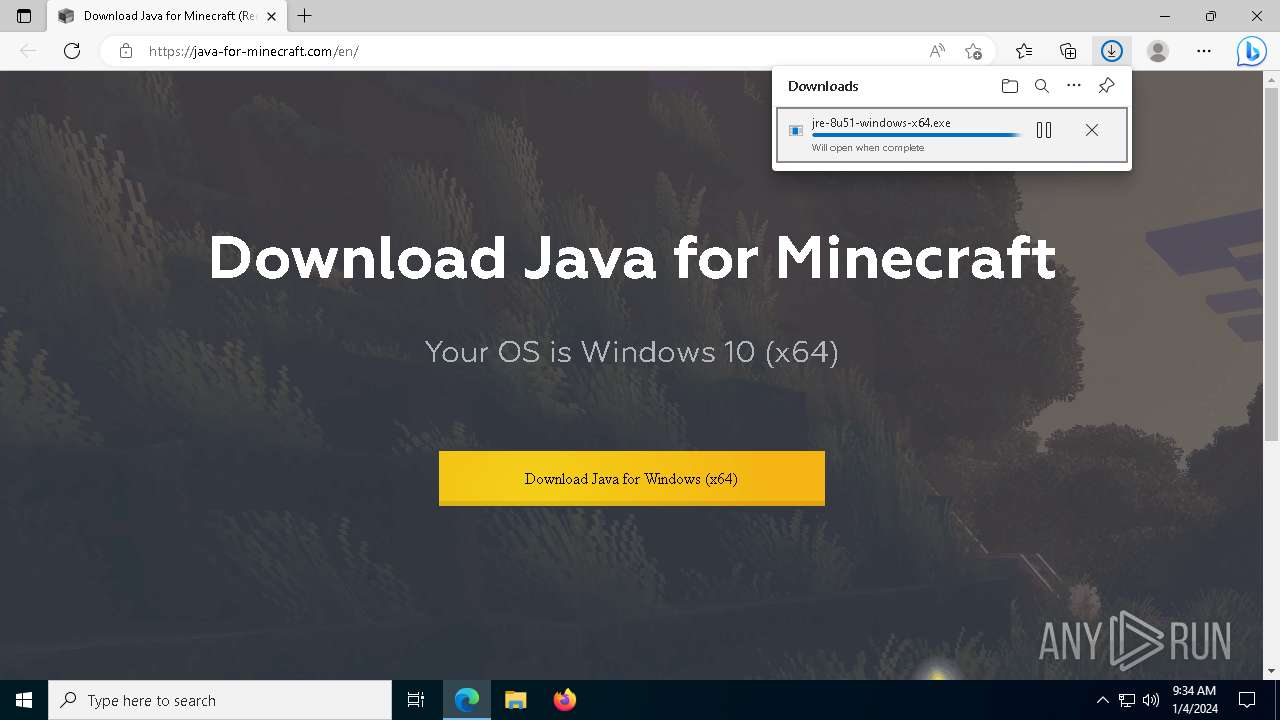
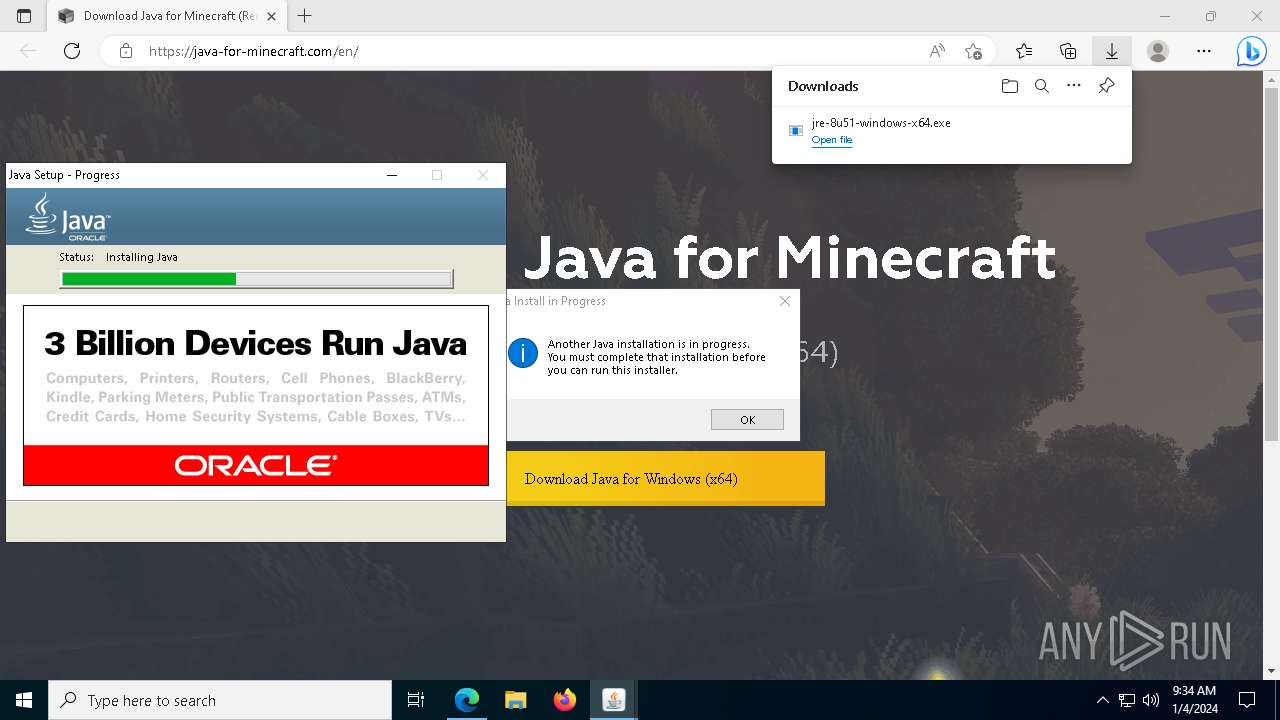
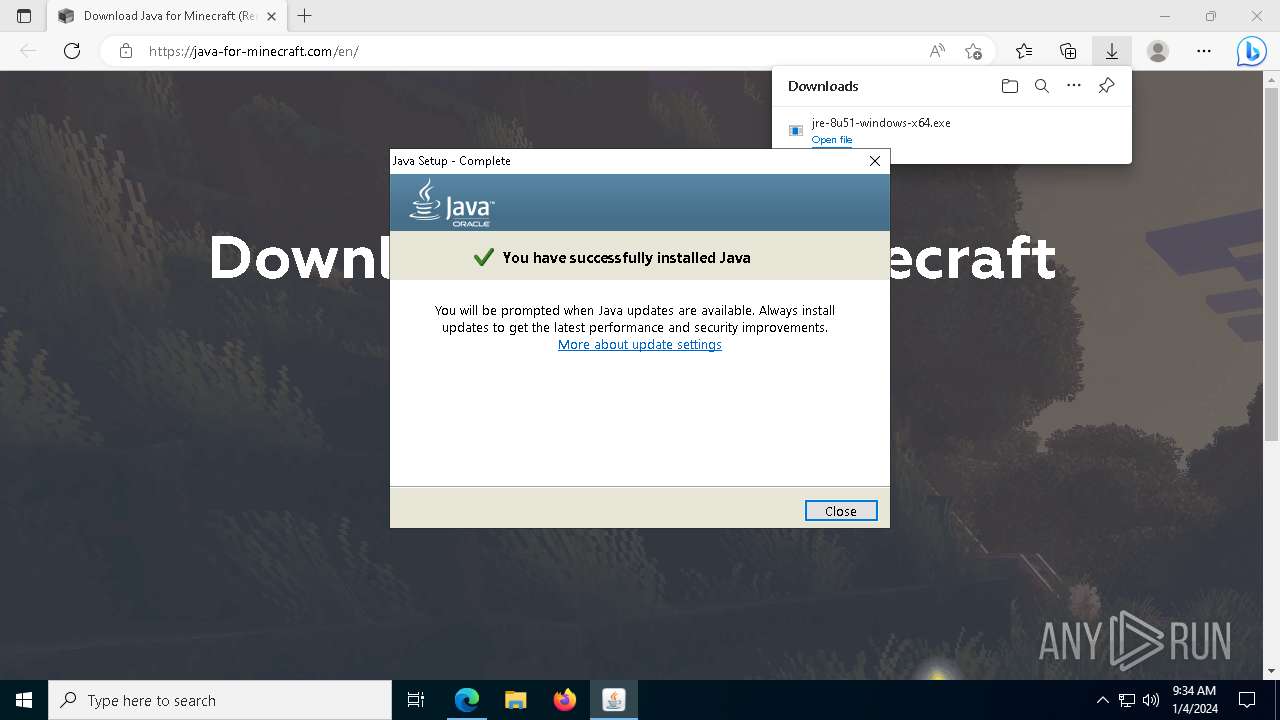
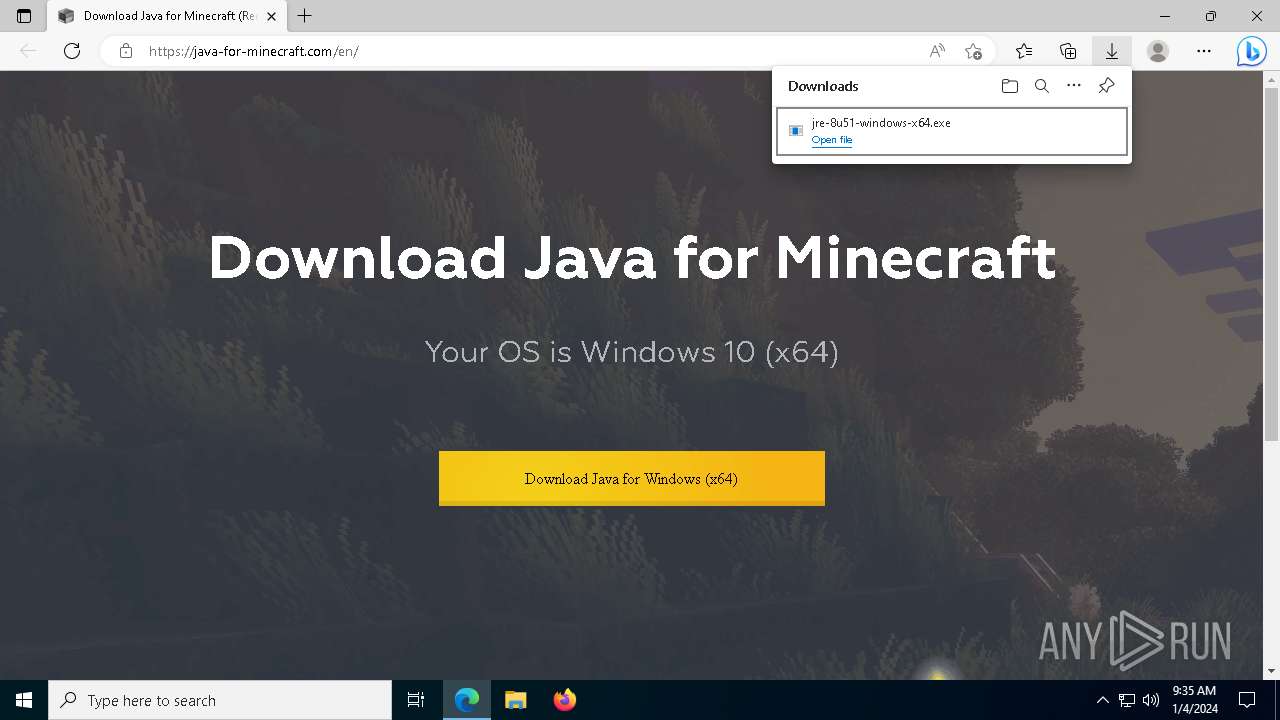
- jre-8u51-windows-x64.exe (PID: 908)
- jre-8u51-windows-x64.exe (PID: 1260)
- installer.exe (PID: 5428)
- javaws.exe (PID: 6696)
- jp2launcher.exe (PID: 2652)
- javaws.exe (PID: 6668)
- jp2launcher.exe (PID: 1124)
- javaw.exe (PID: 480)
Checks Windows Trust Settings
- jre-8u51-windows-x64.exe (PID: 908)
- msiexec.exe (PID: 6836)
Reads security settings of Internet Explorer
- jre-8u51-windows-x64.exe (PID: 908)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6836)
Reads Mozilla Firefox installation path
- installer.exe (PID: 5428)
Starts CMD.EXE for commands execution
- msiexec.exe (PID: 6908)
INFO
Checks supported languages
- identity_helper.exe (PID: 6780)
- jre-8u51-windows-x64.exe (PID: 908)
- jre-8u51-windows-x64.exe (PID: 1260)
- msiexec.exe (PID: 6836)
- installer.exe (PID: 5428)
- bspatch.exe (PID: 6944)
- unpack200.exe (PID: 3920)
- unpack200.exe (PID: 6980)
- unpack200.exe (PID: 6824)
- unpack200.exe (PID: 6488)
- unpack200.exe (PID: 6944)
- unpack200.exe (PID: 756)
- unpack200.exe (PID: 784)
- javaw.exe (PID: 6812)
- javaw.exe (PID: 6588)
- javaws.exe (PID: 6696)
- unpack200.exe (PID: 6696)
- jp2launcher.exe (PID: 2652)
- javaws.exe (PID: 6668)
- jp2launcher.exe (PID: 1124)
- msiexec.exe (PID: 6908)
- javaw.exe (PID: 6776)
- javaw.exe (PID: 480)
Application launched itself
- msedge.exe (PID: 4036)
Drops the executable file immediately after the start
- msedge.exe (PID: 4036)
- installer.exe (PID: 5428)
- msiexec.exe (PID: 6836)
- msedge.exe (PID: 1540)
- msedge.exe (PID: 480)
Reads the computer name
- identity_helper.exe (PID: 6780)
- jre-8u51-windows-x64.exe (PID: 908)
- jre-8u51-windows-x64.exe (PID: 1260)
- msiexec.exe (PID: 6836)
- installer.exe (PID: 5428)
- jp2launcher.exe (PID: 2652)
- jp2launcher.exe (PID: 1124)
- msiexec.exe (PID: 6908)
- javaw.exe (PID: 480)
- javaw.exe (PID: 6776)
Create files in a temporary directory
- jre-8u51-windows-x64.exe (PID: 908)
- javaw.exe (PID: 6812)
- installer.exe (PID: 5428)
- jp2launcher.exe (PID: 2652)
- jp2launcher.exe (PID: 1124)
- javaw.exe (PID: 6588)
- javaw.exe (PID: 480)
- javaw.exe (PID: 6776)
The process uses the downloaded file
- msedge.exe (PID: 4036)
- msedge.exe (PID: 6892)
Checks proxy server information
- jre-8u51-windows-x64.exe (PID: 908)
- jp2launcher.exe (PID: 2652)
- jp2launcher.exe (PID: 1124)
Reads the machine GUID from the registry
- jre-8u51-windows-x64.exe (PID: 908)
- msiexec.exe (PID: 6836)
Creates files or folders in the user directory
- jre-8u51-windows-x64.exe (PID: 908)
Reads the software policy settings
- jre-8u51-windows-x64.exe (PID: 908)
- msiexec.exe (PID: 6836)
Reads CPU info
- msiexec.exe (PID: 6836)
The process drops C-runtime libraries
- installer.exe (PID: 5428)
Creates files in the program directory
- installer.exe (PID: 5428)
- bspatch.exe (PID: 6944)
- unpack200.exe (PID: 6696)
- unpack200.exe (PID: 3920)
- unpack200.exe (PID: 6980)
- unpack200.exe (PID: 6824)
- javaw.exe (PID: 6812)
- unpack200.exe (PID: 6944)
- unpack200.exe (PID: 6488)
- unpack200.exe (PID: 784)
- unpack200.exe (PID: 756)
Process drops legitimate windows executable
- installer.exe (PID: 5428)
- msiexec.exe (PID: 6836)
Reads the time zone
- javaw.exe (PID: 6588)
- jp2launcher.exe (PID: 2652)
- jp2launcher.exe (PID: 1124)
- javaw.exe (PID: 480)
- javaw.exe (PID: 6776)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
200
Monitored processes
76
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 432 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.546 --gpu-preferences=UAAAAAAAAADoAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAACQAAAAAAAAAAAAAAAAAAAAAAAAABgAAAAAAAAAGAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=7308 --field-trial-handle=2064,i,16693501488532564157,11981906526147537830,131072 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 111.0.1661.62 Modules
| |||||||||||||||
| 480 | -cp "C:\Program Files\Java\jre1.8.0_51\bin\..\lib\deploy.jar" com.sun.deploy.panel.ControlPanel -getUserWebJavaStatus | C:\Program Files\Java\jre1.8.0_51\bin\javaw.exe | — | jre-8u51-windows-x64.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 1 Version: 8.0.51.16 Modules
| |||||||||||||||
| 480 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=6136 --field-trial-handle=2064,i,16693501488532564157,11981906526147537830,131072 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 111.0.1661.62 Modules
| |||||||||||||||
| 756 | "C:\Program Files\Java\jre1.8.0_51\bin\unpack200.exe" -r "C:\Program Files\Java\jre1.8.0_51\lib\ext\localedata.pack" "C:\Program Files\Java\jre1.8.0_51\lib\ext\localedata.jar" | C:\Program Files\Java\jre1.8.0_51\bin\unpack200.exe | — | installer.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.51.16 Modules
| |||||||||||||||
| 784 | "C:\Program Files\Java\jre1.8.0_51\bin\unpack200.exe" -r "C:\Program Files\Java\jre1.8.0_51\lib\ext\jfxrt.pack" "C:\Program Files\Java\jre1.8.0_51\lib\ext\jfxrt.jar" | C:\Program Files\Java\jre1.8.0_51\bin\unpack200.exe | — | installer.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.51.16 Modules
| |||||||||||||||
| 908 | "C:\Users\admin\Downloads\jre-8u51-windows-x64.exe" | C:\Users\admin\Downloads\jre-8u51-windows-x64.exe | msedge.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java Platform SE binary Exit code: 0 Version: 8.0.510.16 Modules
| |||||||||||||||
| 1068 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=111.0.5563.149 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=111.0.1661.62 --initial-client-data=0x100,0x104,0x108,0xdc,0x114,0x7ffbbc59b5f8,0x7ffbbc59b608,0x7ffbbc59b618 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 111.0.1661.62 Modules
| |||||||||||||||
| 1100 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --first-renderer-process --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=3396 --field-trial-handle=2064,i,16693501488532564157,11981906526147537830,131072 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 111.0.1661.62 Modules
| |||||||||||||||
| 1124 | "C:\Program Files\Java\jre1.8.0_51\bin\jp2launcher.exe" -secure -javaws -jre "C:\Program Files\Java\jre1.8.0_51" -vma LWNsYXNzcGF0aABDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfNTFcbGliXGRlcGxveS5qYXIALURqYXZhLnNlY3VyaXR5LnBvbGljeT1maWxlOkM6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUxLjguMF81MVxsaWJcc2VjdXJpdHlcamF2YXdzLnBvbGljeQAtRHRydXN0UHJveHk9dHJ1ZQAtWHZlcmlmeTpyZW1vdGUALURqbmxweC5ob21lPUM6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUxLjguMF81MVxiaW4ALURqYXZhLnNlY3VyaXR5Lm1hbmFnZXIALURzdW4uYXd0Lndhcm11cD10cnVlAC1YYm9vdGNsYXNzcGF0aC9hOkM6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUxLjguMF81MVxsaWJcamF2YXdzLmphcjtDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfNTFcbGliXGRlcGxveS5qYXI7QzpcUHJvZ3JhbSBGaWxlc1xKYXZhXGpyZTEuOC4wXzUxXGxpYlxwbHVnaW4uamFyAC1EamF2YS5hd3QuaGVhZGxlc3M9dHJ1ZQAtRGpubHB4Lmp2bT1DOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfNTFcYmluXGphdmF3LmV4ZQ== -ma LXdhaXQALWZpeAAtc2hvcnRjdXQALXNpbGVudAAtbm90V2ViSmF2YQ== | C:\Program Files\Java\jre1.8.0_51\bin\jp2launcher.exe | — | javaws.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java(TM) Platform SE binary Exit code: 0 Version: 11.51.2.16 Modules
| |||||||||||||||
| 1260 | "C:\Users\admin\Downloads\jre-8u51-windows-x64.exe" | C:\Users\admin\Downloads\jre-8u51-windows-x64.exe | msedge.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java Platform SE binary Exit code: 4294967295 Version: 8.0.510.16 Modules
| |||||||||||||||
Total events
23 363
Read events
17 039
Write events
82
Delete events
6 242
Modification events
| (PID) Process: | (4036) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (4036) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (4036) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (4036) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (4036) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\ClientState\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (4036) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (4036) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge |
| Operation: | write | Name: | UsageStatsInSample |
Value: 1 | |||
| (PID) Process: | (4036) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 74A98451B7602F00 | |||
| (PID) Process: | (4036) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (4036) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | urlstats |
Value: 0 | |||
Executable files
123
Suspicious files
337
Text files
182
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4036 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RFf2c85.TMP | — | |
MD5:— | SHA256:— | |||
| 4036 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4036 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RFf2c75.TMP | — | |
MD5:— | SHA256:— | |||
| 4036 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4036 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RFf2ce3.TMP | — | |
MD5:— | SHA256:— | |||
| 4036 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4036 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\10f04a66-d23c-429c-9632-bef0eebddff6.tmp | binary | |
MD5:12F08BB15BAB4A6B387388EBDEB34050 | SHA256:5001699D3D72648972C8B699B79DCA84D8F46B6C463B9D0A987381ACCD4EFA12 | |||
| 4036 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Sync Data\LevelDB\LOG.old~RFf2c75.TMP | text | |
MD5:7F54C8C86DAFAE68888F6F799ACFBBD8 | SHA256:F75E0D81BB38778FCFBCD031115B171E052E59E674F75FC41C0B353136ED976E | |||
| 4036 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgeCoupons\coupons_data.db\LOG.old | text | |
MD5:63D47248EB1C3F5B97CAAE6599A6FCD0 | SHA256:4124BD344E193D3DDBE94EF996C5AFBEA6C00C939F405B3CCBEE9058BA5AE257 | |||
| 4036 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Site Characteristics Database\LOG.old~RFf2c75.TMP | text | |
MD5:5DB127C66F688E2B285A0816EC4BDE1C | SHA256:1A490965A2E4688809FF31A5DB1971688F92700DEFA536BEF28D91512B9AA966 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
74
TCP/UDP connections
90
DNS requests
86
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5976 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
1092 | svchost.exe | POST | 302 | 184.30.17.189:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
6924 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | binary | 418 b | unknown |
6924 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | binary | 409 b | unknown |
1092 | svchost.exe | POST | 302 | 184.30.17.189:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
4036 | msedge.exe | GET | 200 | 152.199.19.74:80 | http://s2.symcb.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS56bKHAoUD%2BOyl%2B0LhPg9JxyQm4gQUf9Nlp8Ld7LvwMAnzQzn6Aq8zMTMCED141%2Fl2SWCyYX308B7Khio%3D | unknown | binary | 5 b | unknown |
4036 | msedge.exe | GET | 200 | 152.199.19.74:80 | http://s2.symcb.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS56bKHAoUD%2BOyl%2B0LhPg9JxyQm4gQUf9Nlp8Ld7LvwMAnzQzn6Aq8zMTMCED141%2Fl2SWCyYX308B7Khio%3D | unknown | binary | 5 b | unknown |
4036 | msedge.exe | GET | 200 | 192.229.221.95:80 | http://s1.symcb.com/pca3-g5.crl | unknown | binary | 834 b | unknown |
4036 | msedge.exe | GET | 200 | 152.199.19.74:80 | http://sv.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQe6LNDJdqx%2BJOp7hVgTeaGFJ%2FCQgQUljtT8Hkzl699g%2B8uK8zKt4YecmYCEBLwJ34PIzs5%2BUGbBujN41I%3D | unknown | binary | 1.47 Kb | unknown |
908 | jre-8u51-windows-x64.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4036 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3720 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4012 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4012 | msedge.exe | 104.21.71.37:443 | java-for-minecraft.com | CLOUDFLARENET | — | unknown |
4012 | msedge.exe | 20.103.180.120:443 | nav-edge.smartscreen.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
4012 | msedge.exe | 20.105.95.163:443 | data-edge.smartscreen.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4012 | msedge.exe | 142.250.186.136:443 | www.googletagmanager.com | GOOGLE | US | unknown |
4012 | msedge.exe | 216.239.32.36:443 | region1.google-analytics.com | GOOGLE | US | unknown |
4012 | msedge.exe | 104.126.37.137:443 | www.bing.com | Akamai International B.V. | DE | unknown |
5976 | svchost.exe | 40.126.32.138:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
java-for-minecraft.com |
| unknown |
config.edge.skype.com |
| whitelisted |
nav-edge.smartscreen.microsoft.com |
| whitelisted |
data-edge.smartscreen.microsoft.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
region1.google-analytics.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
javadl.sun.com |
| unknown |