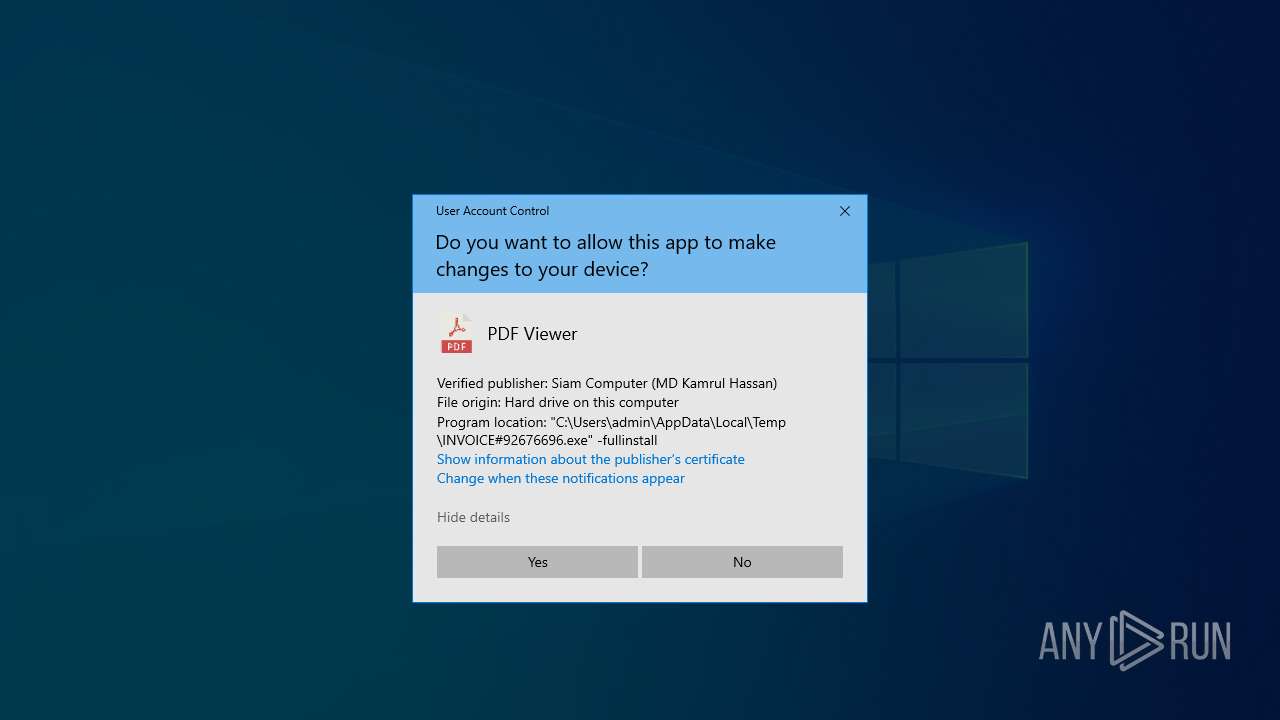
| File name: | INVOICE#92676696.exe |
| Full analysis: | https://app.any.run/tasks/44587e7f-6f3b-4a4d-8187-179587bc4d90 |
| Verdict: | Malicious activity |
| Analysis date: | July 24, 2024, 18:05:14 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (console) x86-64, for MS Windows |
| MD5: | 474975EF4357ACCB444831BD44A1BE7E |
| SHA1: | 2D6B68A58B33D516EB54D7BE4E037F055E55C904 |
| SHA256: | CF3FC4B5949539064CAA06600FAF7FFAADFD5CA52DE79C7DDB1A990B3255217A |
| SSDEEP: | 98304:VhNJBgktHnIIfTduqLSqwT2A5DpOftCLmMJmyUc7dQdG40qXQCmX1XjkZxVrfSkO:2d |
MALICIOUS
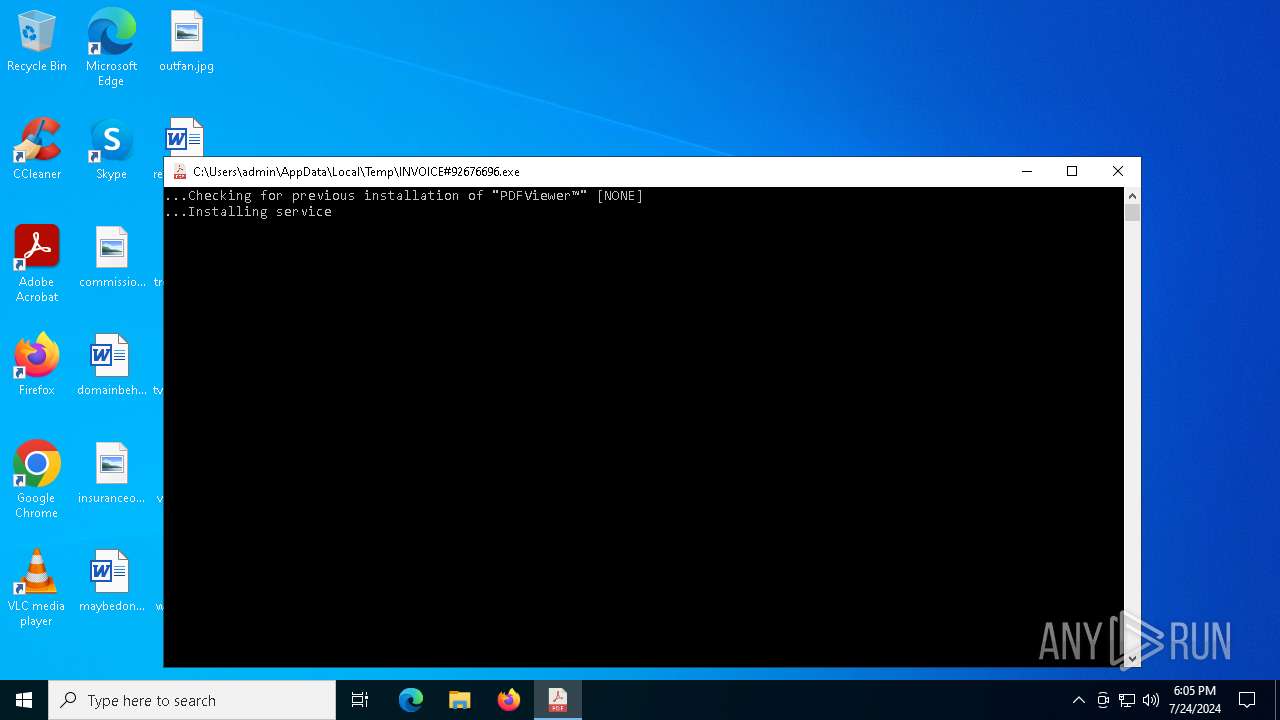
Drops the executable file immediately after the start
- INVOICE#92676696.exe (PID: 3360)
- INVOICE#92676696.exe (PID: 6604)
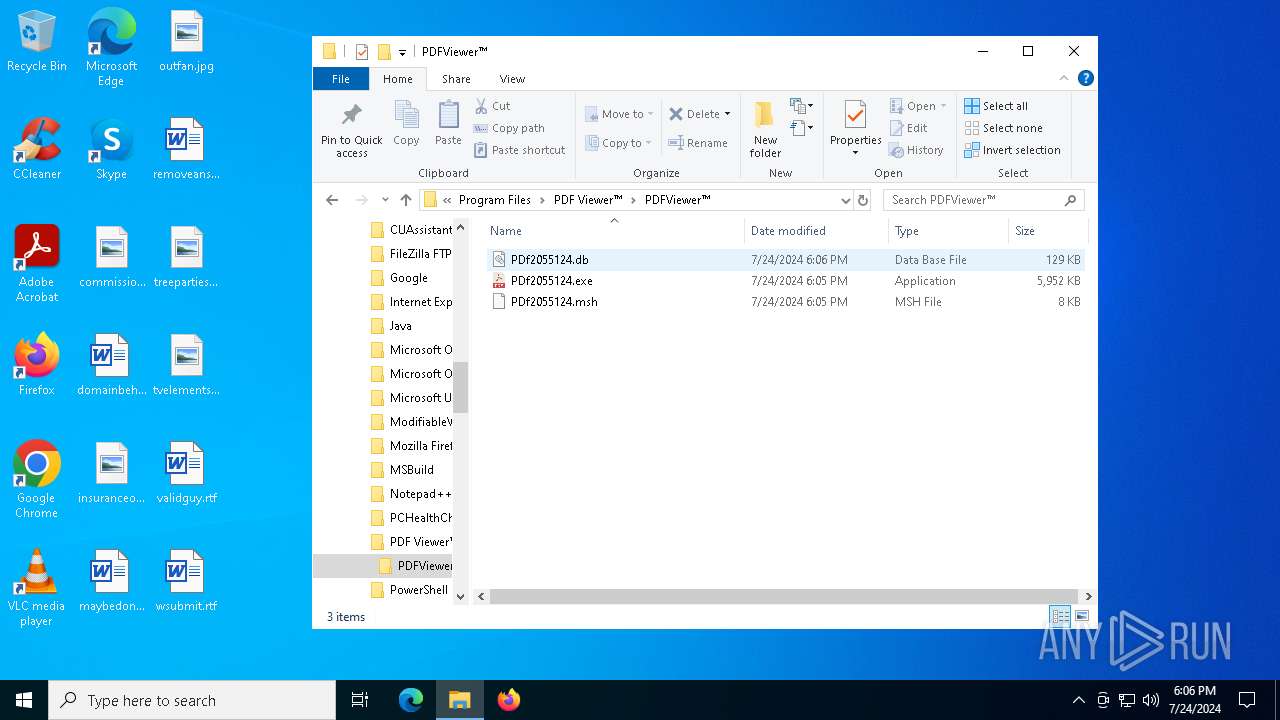
- PDf2055124.exe (PID: 6040)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 6624)
SUSPICIOUS
Executable content was dropped or overwritten
- INVOICE#92676696.exe (PID: 3360)
- PDf2055124.exe (PID: 6040)
Uses WMIC.EXE to obtain operating system information
- INVOICE#92676696.exe (PID: 6604)
- PDf2055124.exe (PID: 6040)
- PDf2055124.exe (PID: 5532)
Creates or modifies Windows services
- INVOICE#92676696.exe (PID: 3360)
Executes as Windows Service
- PDf2055124.exe (PID: 6040)
Reads security settings of Internet Explorer
- INVOICE#92676696.exe (PID: 6604)
- PDf2055124.exe (PID: 6040)
Reads the date of Windows installation
- INVOICE#92676696.exe (PID: 6604)
Creates a software uninstall entry
- INVOICE#92676696.exe (PID: 3360)
- PDf2055124.exe (PID: 6040)
Uses WMIC.EXE to obtain system information
- PDf2055124.exe (PID: 6040)
Uses WMIC.EXE to obtain computer system information
- PDf2055124.exe (PID: 6040)
Starts POWERSHELL.EXE for commands execution
- PDf2055124.exe (PID: 6040)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 6624)
The process bypasses the loading of PowerShell profile settings
- PDf2055124.exe (PID: 6040)
The process hides Powershell's copyright startup banner
- PDf2055124.exe (PID: 6040)
Starts CMD.EXE for commands execution
- PDf2055124.exe (PID: 6040)
There is functionality for taking screenshot (YARA)
- PDf2055124.exe (PID: 5532)
Application launched itself
- INVOICE#92676696.exe (PID: 6604)
- PDf2055124.exe (PID: 6040)
Process drops legitimate windows executable
- PDf2055124.exe (PID: 6040)
Creates file in the systems drive root
- PDf2055124.exe (PID: 6040)
INFO
Process checks computer location settings
- INVOICE#92676696.exe (PID: 6604)
Reads the computer name
- INVOICE#92676696.exe (PID: 3360)
- PDf2055124.exe (PID: 6040)
- INVOICE#92676696.exe (PID: 6604)
- PDf2055124.exe (PID: 5532)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 6700)
- WMIC.exe (PID: 6592)
- WMIC.exe (PID: 1552)
- WMIC.exe (PID: 6640)
- WMIC.exe (PID: 4992)
- WMIC.exe (PID: 7040)
- WMIC.exe (PID: 5692)
- WMIC.exe (PID: 6640)
Creates files in the program directory
- PDf2055124.exe (PID: 6040)
- INVOICE#92676696.exe (PID: 3360)
Reads the machine GUID from the registry
- PDf2055124.exe (PID: 6040)
- INVOICE#92676696.exe (PID: 6604)
- PDf2055124.exe (PID: 5532)
Checks supported languages
- PDf2055124.exe (PID: 6040)
- INVOICE#92676696.exe (PID: 3360)
- INVOICE#92676696.exe (PID: 6604)
- PDf2055124.exe (PID: 5532)
- PDf2055124.exe (PID: 6940)
- PDf2055124.exe (PID: 2816)
Manual execution by a user
- WINWORD.EXE (PID: 6920)
- PDf2055124.exe (PID: 5532)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 2128)
Gets data length (POWERSHELL)
- powershell.exe (PID: 2128)
Checks proxy server information
- slui.exe (PID: 2464)
Reads the software policy settings
- slui.exe (PID: 2464)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:07:08 17:00:34+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.4 |
| CodeSize: | 4264960 |
| InitializedDataSize: | 1979392 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x37d230 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x0017 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
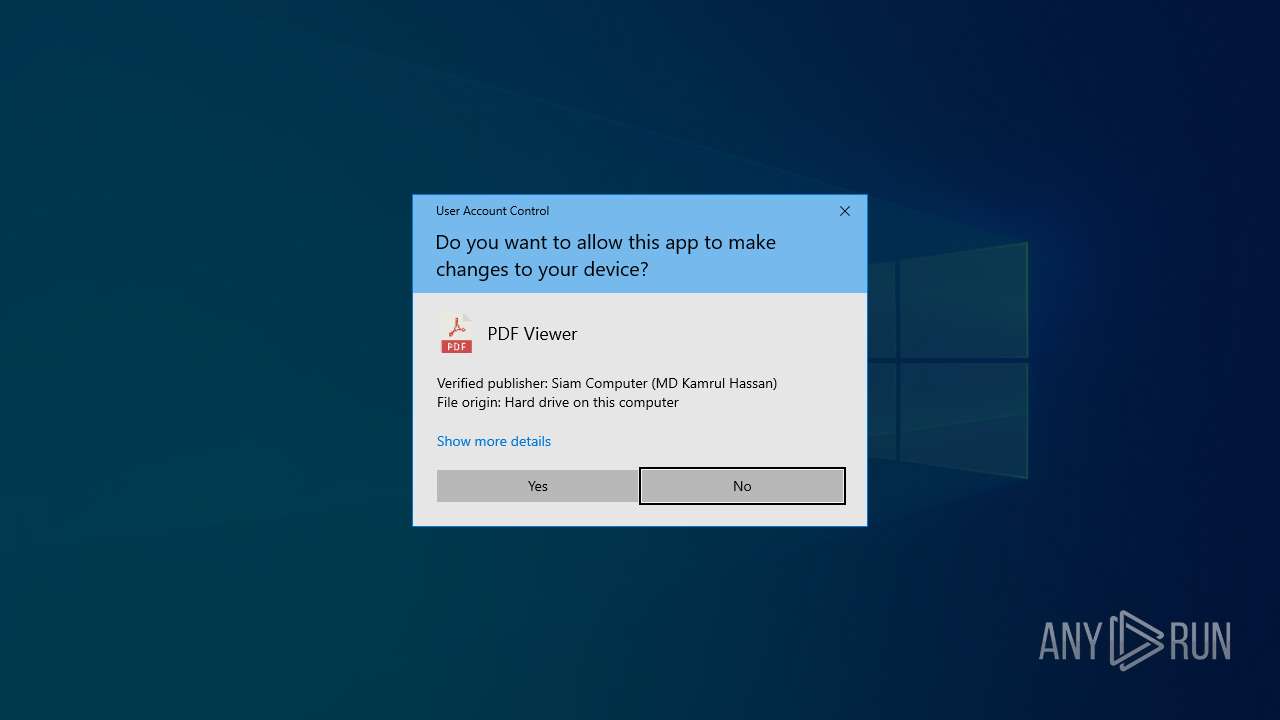
| FileDescription: | PDF Viewer |
| FileVersion: | 2022-Oct-21 22:58:31-0700 |
| LegalCopyright: | Apache 2.0 License |
| ProductName: | PDF Viewer |
| ProductVersion: | Commit: 2022-Oct-21 22:58:31-0700 |
Total processes
185
Monitored processes
42
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1028 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | PDf2055124.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1048 | /c manage-bde -protectors -get C: -Type recoverypassword | C:\Windows\System32\cmd.exe | — | PDf2055124.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 4294967295 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1096 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1128 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1160 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1392 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1504 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | PDf2055124.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1548 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | PDf2055124.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1552 | wmic os get oslanguage /FORMAT:LIST | C:\Windows\System32\wbem\WMIC.exe | — | PDf2055124.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2128 | powershell -noprofile -nologo -command - | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | PDf2055124.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
44 819
Read events
44 427
Write events
362
Delete events
30
Modification events
| (PID) Process: | (6604) INVOICE#92676696.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6604) INVOICE#92676696.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6604) INVOICE#92676696.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6604) INVOICE#92676696.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3360) INVOICE#92676696.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\PDFViewer™ |
| Operation: | write | Name: | ImagePath |
Value: "C:\Program Files\PDF Viewer™\PDFViewer™\PDf2055124.exe" --meshServiceName="PDFViewer™" --installedByUser="S-1-5-21-1693682860-607145093-2874071422-1001" | |||
| (PID) Process: | (3360) INVOICE#92676696.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\PDFViewer™ |
| Operation: | write | Name: | _InstalledBy |
Value: S-1-5-21-1693682860-607145093-2874071422-1001 | |||
| (PID) Process: | (3360) INVOICE#92676696.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\PDFViewer™ |
| Operation: | write | Name: | DisplayName |
Value: PDF Viewer™ | |||
| (PID) Process: | (3360) INVOICE#92676696.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\PDFViewer™ |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files\PDF Viewer™\PDFViewer™\PDf2055124.exe | |||
| (PID) Process: | (3360) INVOICE#92676696.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\PDFViewer™ |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\PDF Viewer™\PDFViewer™\ | |||
| (PID) Process: | (3360) INVOICE#92676696.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\PDFViewer™ |
| Operation: | write | Name: | EstimatedSize |
Value: 5951 | |||
Executable files
2
Suspicious files
24
Text files
20
Unknown types
15
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6040 | PDf2055124.exe | C:\Windows\System32\config\systemprofile\AppData\Roaming\Microsoft\SystemCertificates\My\Certificates\BF411215A28225EC7531C309D61C909149B5BBD1 | dbf | |
MD5:25C0D4274CE9A6AD3F69A1A2B2E5FF71 | SHA256:EC1D149DA6589E6B127A9A327F893B4E2D11709FC5371FAE8BACFCD04A70A838 | |||
| 3360 | INVOICE#92676696.exe | C:\Program Files\PDF Viewer™\PDFViewer™\PDf2055124.exe | executable | |
MD5:474975EF4357ACCB444831BD44A1BE7E | SHA256:CF3FC4B5949539064CAA06600FAF7FFAADFD5CA52DE79C7DDB1A990B3255217A | |||
| 6920 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | der | |
MD5:94351CB105884B824E9778D0DDED1C64 | SHA256:B67FD799051EC989F549F50EBE37D5EB7A81AD311E0017806D93A138EB4525EF | |||
| 6040 | PDf2055124.exe | C:\Windows\System32\config\systemprofile\AppData\Roaming\Microsoft\SystemCertificates\My\Keys\D0CDD2AA816D0F84DCC90C2409D8033355EC91CD | binary | |
MD5:CCF9C6CEC175CA93723C9FFA5A580C43 | SHA256:7210E86536C3170A1C69C9BD8BC7BDE00C62983EE0133A2230579E88B4FDBCB5 | |||
| 6920 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\5475cb191e478c39370a215b2da98a37e9dc813d.tbres | binary | |
MD5:6794C8FB077D9EE2458DE9C5A185166C | SHA256:625632C95673E2C517694816D3B671C0B0433046F35E87B6727916294F393C30 | |||
| 6920 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | abr | |
MD5:02194BC9FAD77096472E45167C972361 | SHA256:0442F45EF58CF11B33D83D23DDF9D6FF2206BA46CAC4B21722A4829F835BE0CA | |||
| 6920 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 6920 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:60048EB988A65A92326CF9584838C828 | SHA256:E8127E75B958D78B41B654CE5B98DE0A9AEDE3608267CB2F49D8355596CC483D | |||
| 6920 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:DE77084626C9B28D2CC56B8E179BF197 | SHA256:8DF4650ABE902E03816AF0A5DA3BCAA919D572AC6F72272CF869A421C9E8CD67 | |||
| 6040 | PDf2055124.exe | C:\Windows\System32\config\systemprofile\AppData\Roaming\Microsoft\SystemCertificates\My\Keys\C7E122F545E1964EA814CBA18054A225D44F422F | binary | |
MD5:EEFC8EA7C3D0DD86801D3D4D2E9D9614 | SHA256:87EB260281A2D09683806B488D9CBB96EBDBD6126381C98A1D5FC912F68C6675 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
70
DNS requests
30
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5272 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6228 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
504 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3148 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6920 | WINWORD.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
5272 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6920 | WINWORD.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 104.126.37.160:443 | — | Akamai International B.V. | DE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6012 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3108 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3392 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 4.208.221.206:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
3992 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5368 | SearchApp.exe | 2.23.209.133:443 | www.bing.com | Akamai International B.V. | GB | unknown |
5272 | svchost.exe | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
syn.hiddenvnc.com |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
INVOICE#92676696.exe | Detected memory leaks!
|
INVOICE#92676696.exe | Dumping objects ->
|
INVOICE#92676696.exe | C:\Users\yfjvy\Downloads\MeshAgent-master\microscript\ILibDuktape_ScriptContainer.c(1611) : |
INVOICE#92676696.exe | {75763} |
INVOICE#92676696.exe | normal block at 0x000001F97BFFE850, 6001 bytes long.
|
INVOICE#92676696.exe | Data: <9 > 39 17 00 00 00 00 00 00 08 00 00 00 00 00 00 00
|
INVOICE#92676696.exe | C:\Users\yfjvy\Downloads\MeshAgent-master\microscript\ILibDuktape_ScriptContainer.c(1611) : |
INVOICE#92676696.exe | {75625} |
INVOICE#92676696.exe | normal block at 0x000001F97BEAD410, 536 bytes long.
|
INVOICE#92676696.exe | Data: < > E0 01 00 00 00 00 00 00 08 00 00 00 00 00 00 00
|