| File name: | Browser.exe |
| Full analysis: | https://app.any.run/tasks/6acf91f0-51d4-4ed8-aa4d-465eacbecb81 |
| Verdict: | Malicious activity |
| Analysis date: | August 16, 2025, 06:39:47 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 6 sections |
| MD5: | DCF90D3A39BEE8F7F7DEBB1FD89130D2 |
| SHA1: | 04CBF8F9D57BDAB4CBE4C1F349E9EDF9DBF462FD |
| SHA256: | CF38C4839DB8EA8B7D78E786BFAA68F960E4B42C278E64A185257E54098B7807 |
| SSDEEP: | 3072:ZO4m1ob3l5NGjj/bqihawuqYzet0YX82ytbMqxO:Y1obzNGjj/bqihawuqYzet0YX82ytbV8 |
MALICIOUS
Changes the autorun value in the registry
- setup.exe (PID: 6664)
SUSPICIOUS
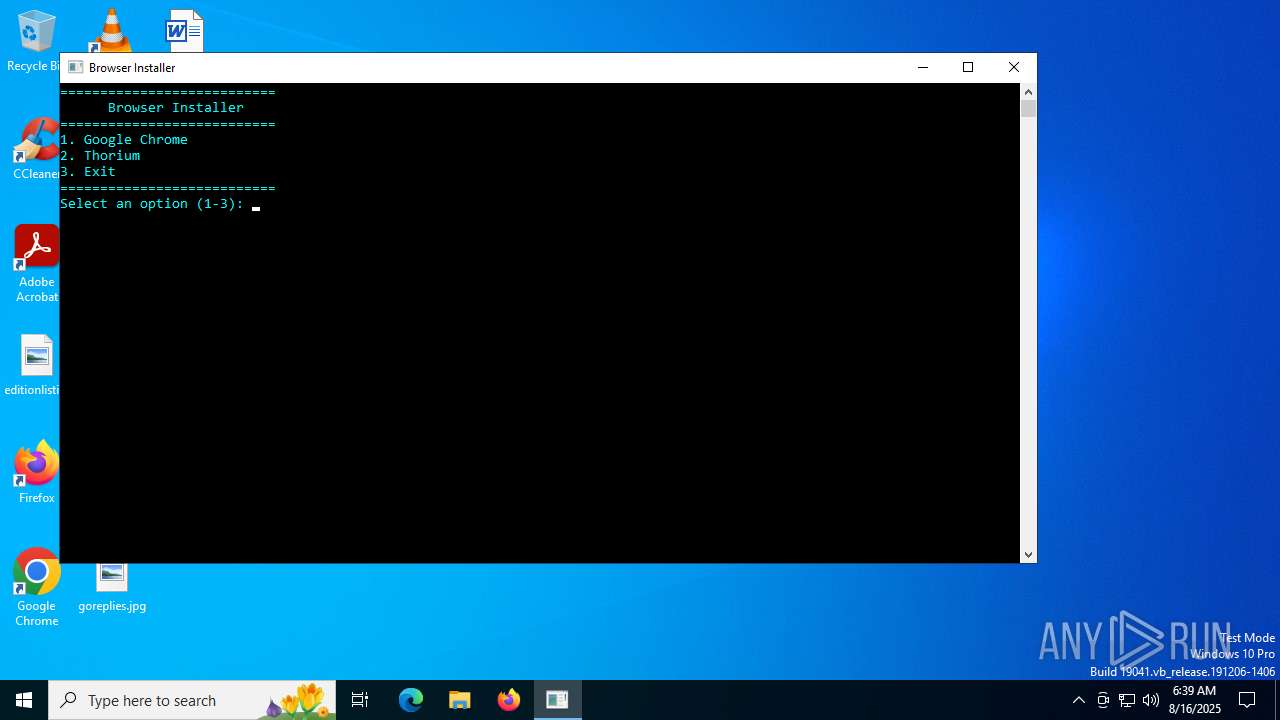
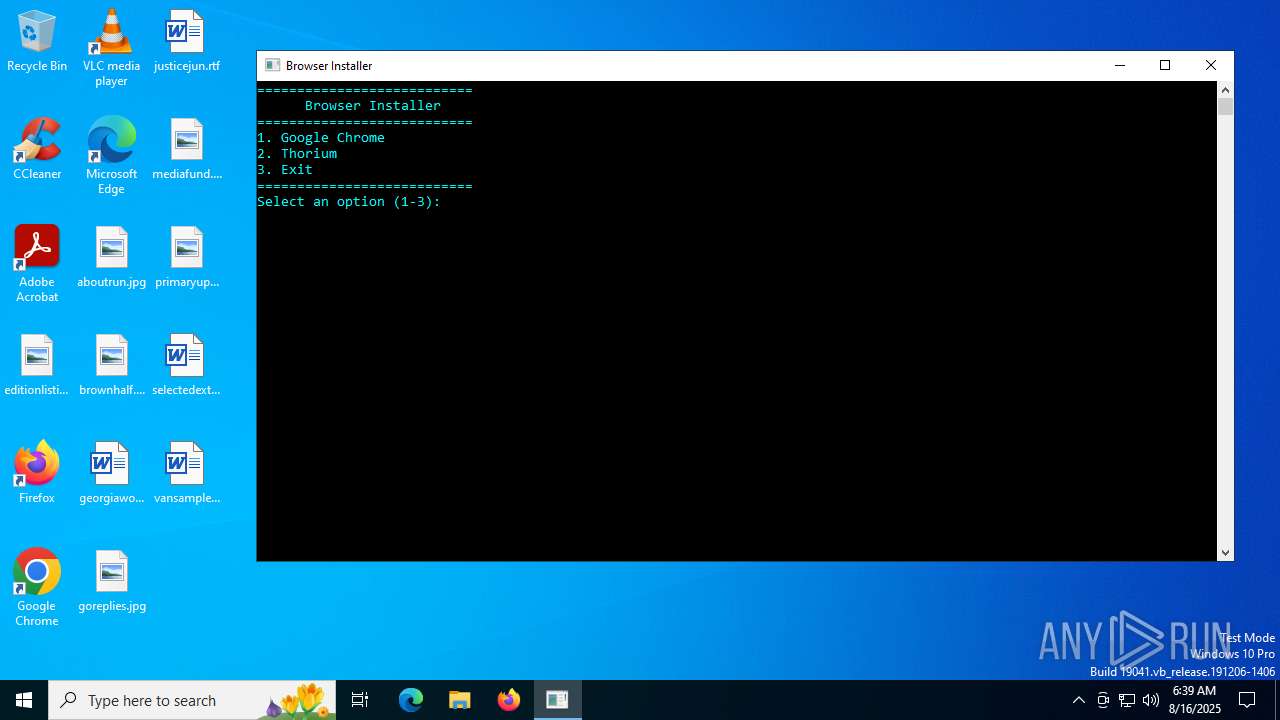
Starts CMD.EXE for commands execution
- Browser.exe (PID: 3788)
Executing commands from a ".bat" file
- Browser.exe (PID: 3788)
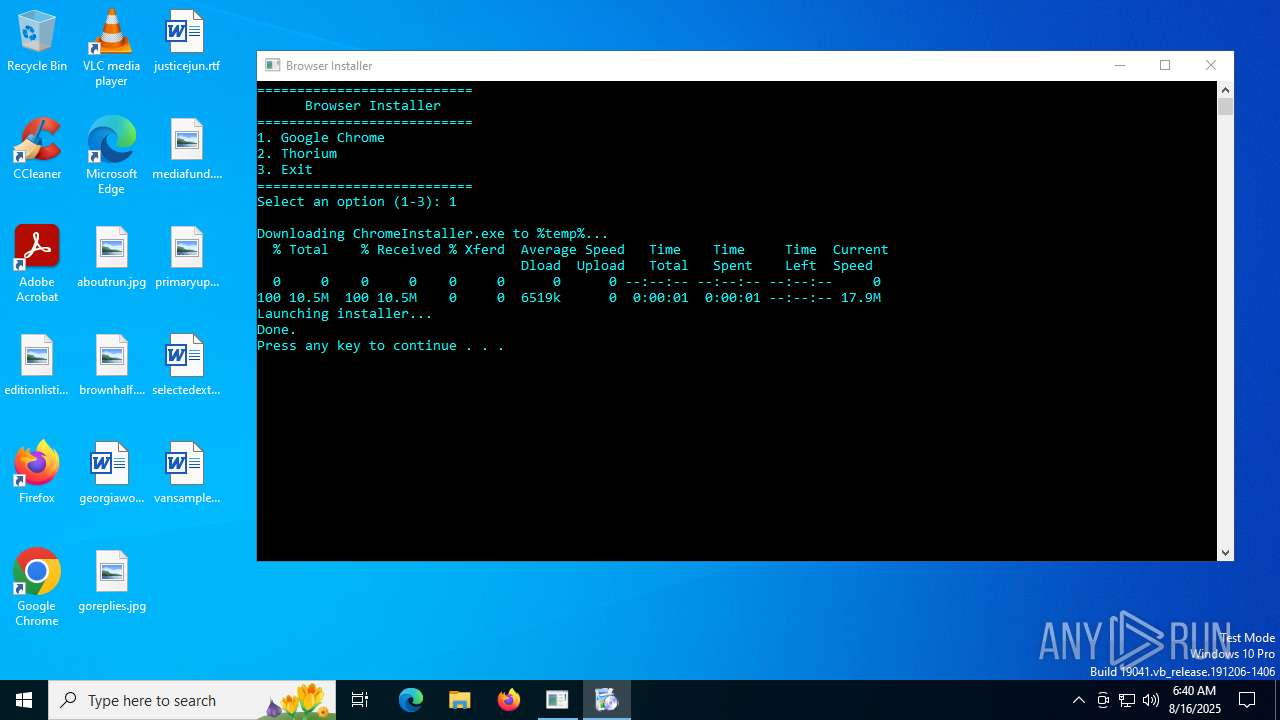
The executable file from the user directory is run by the CMD process
- ChromeInstaller.exe (PID: 6808)
Reads security settings of Internet Explorer
- ChromeInstaller.exe (PID: 6808)
- updater.exe (PID: 6636)
Executable content was dropped or overwritten
- curl.exe (PID: 2996)
- updater.exe (PID: 6636)
- updater.exe (PID: 4768)
- 139.0.7258.128_chrome_installer_uncompressed.exe (PID: 6676)
- setup.exe (PID: 6664)
Application launched itself
- ChromeInstaller.exe (PID: 6808)
- updater.exe (PID: 6636)
- updater.exe (PID: 4768)
- updater.exe (PID: 3672)
- setup.exe (PID: 6664)
- setup.exe (PID: 5368)
Executes as Windows Service
- updater.exe (PID: 4768)
- updater.exe (PID: 3672)
Creates a software uninstall entry
- setup.exe (PID: 6664)
Searches for installed software
- setup.exe (PID: 6664)
INFO
Checks supported languages
- Browser.exe (PID: 3788)
- curl.exe (PID: 2996)
- ChromeInstaller.exe (PID: 6808)
- ChromeInstaller.exe (PID: 1204)
- updater.exe (PID: 6636)
- updater.exe (PID: 2312)
- updater.exe (PID: 1520)
- updater.exe (PID: 4768)
- updater.exe (PID: 3672)
- updater.exe (PID: 7044)
- 139.0.7258.128_chrome_installer_uncompressed.exe (PID: 6676)
- setup.exe (PID: 3760)
- setup.exe (PID: 6664)
- setup.exe (PID: 5368)
- setup.exe (PID: 2168)
- elevation_service.exe (PID: 5708)
The sample compiled with english language support
- Browser.exe (PID: 3788)
- curl.exe (PID: 2996)
- updater.exe (PID: 6636)
- updater.exe (PID: 4768)
- 139.0.7258.128_chrome_installer_uncompressed.exe (PID: 6676)
- setup.exe (PID: 6664)
Create files in a temporary directory
- Browser.exe (PID: 3788)
- curl.exe (PID: 2996)
- ChromeInstaller.exe (PID: 1204)
- updater.exe (PID: 6636)
Execution of CURL command
- cmd.exe (PID: 6876)
Reads the computer name
- curl.exe (PID: 2996)
- ChromeInstaller.exe (PID: 6808)
- ChromeInstaller.exe (PID: 1204)
- updater.exe (PID: 6636)
- updater.exe (PID: 4768)
- 139.0.7258.128_chrome_installer_uncompressed.exe (PID: 6676)
- updater.exe (PID: 3672)
- setup.exe (PID: 6664)
- setup.exe (PID: 5368)
- elevation_service.exe (PID: 5708)
Process checks computer location settings
- ChromeInstaller.exe (PID: 6808)
Creates files in the program directory
- updater.exe (PID: 6636)
- updater.exe (PID: 2312)
- updater.exe (PID: 4768)
- updater.exe (PID: 3672)
- setup.exe (PID: 6664)
- setup.exe (PID: 5368)
Process checks whether UAC notifications are on
- updater.exe (PID: 6636)
- updater.exe (PID: 4768)
- updater.exe (PID: 3672)
Checks proxy server information
- updater.exe (PID: 6636)
Reads the software policy settings
- updater.exe (PID: 3672)
- updater.exe (PID: 6636)
Reads the machine GUID from the registry
- updater.exe (PID: 6636)
Creates files or folders in the user directory
- updater.exe (PID: 6636)
Launching a file from a Registry key
- setup.exe (PID: 6664)
Manual execution by a user
- chrome.exe (PID: 6656)
Application launched itself
- chrome.exe (PID: 6656)
Executes as Windows Service
- elevation_service.exe (PID: 5708)
Connects to unusual port
- chrome.exe (PID: 3940)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.2) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2019:07:30 08:52:08+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 2.5 |
| CodeSize: | 92672 |
| InitializedDataSize: | 32768 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Debug, Pre-release, Private build |
| FileOS: | Windows 16-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| FileVersion: | 1.0.0.0 |
| ProductName: | Browser |
| OriginalFileName: | Browser |
| InternalName: | Browser |
Total processes
170
Monitored processes
34
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1204 | "C:\Users\admin\AppData\Local\Temp\ChromeInstaller.exe" --install=appguid={8A69D345-D564-463C-AFF1-A69D9E530F96}&iid={A7B1197D-BA72-C242-69CE-517FD195398D}&lang=en&browser=4&usagestats=0&appname=Google%20Chrome&needsadmin=prefers&ap=x64-statsdef_1&installdataindex=empty --enable-logging --vmodule=*/components/winhttp/*=1,*/components/update_client/*=2,*/chrome/enterprise_companion/*=2,*/chrome/updater/*=2 --expect-elevated | C:\Users\admin\AppData\Local\Temp\ChromeInstaller.exe | ChromeInstaller.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: HIGH Description: Google Installer (x86) Exit code: 0 Version: 141.0.7340.0 Modules
| |||||||||||||||
| 1204 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --enable-dinosaur-easter-egg-alt-images --force-high-res-timeticks=disabled --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=12 --metrics-shmem-handle=5236,i,1269766641147909516,15872054277772268336,2097152 --field-trial-handle=1868,i,5885215776343114923,9230722159622840377,262144 --variations-seed-version --mojo-platform-channel-handle=5200 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 139.0.7258.128 Modules
| |||||||||||||||
| 1520 | "C:\Program Files (x86)\Google\GoogleUpdater\141.0.7340.0\updater.exe" --crash-handler --system "--database=C:\Program Files (x86)\Google\GoogleUpdater\141.0.7340.0\Crashpad" --url=https://clients2.google.com/cr/report --annotation=prod=Update4 --annotation=ver=141.0.7340.0 "--attachment=C:\Program Files (x86)\Google\GoogleUpdater\updater.log" --initial-client-data=0x29c,0x2a0,0x2a4,0x274,0x2a8,0xcd42e8,0xcd42f4,0xcd4300 | C:\Program Files (x86)\Google\GoogleUpdater\141.0.7340.0\updater.exe | — | updater.exe | |||||||||||
User: SYSTEM Company: Google LLC Integrity Level: SYSTEM Description: Google Updater (x86) Exit code: 0 Version: 141.0.7340.0 Modules
| |||||||||||||||
| 1644 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --enable-dinosaur-easter-egg-alt-images --force-high-res-timeticks=disabled --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=11 --metrics-shmem-handle=4900,i,6405896687167281562,14630880917818889943,2097152 --field-trial-handle=1868,i,5885215776343114923,9230722159622840377,262144 --variations-seed-version --mojo-platform-channel-handle=4904 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 139.0.7258.128 Modules
| |||||||||||||||
| 1712 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --enable-dinosaur-easter-egg-alt-images --force-high-res-timeticks=disabled --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --metrics-shmem-handle=3724,i,7774293228492057423,11882534165974282320,2097152 --field-trial-handle=1868,i,5885215776343114923,9230722159622840377,262144 --variations-seed-version --mojo-platform-channel-handle=3864 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 139.0.7258.128 Modules
| |||||||||||||||
| 2168 | C:\WINDOWS\SystemTemp\chrome_Unpacker_BeginUnzipping3672_2004738171\CR_27973.tmp\setup.exe --type=crashpad-handler /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler --database=C:\WINDOWS\SystemTemp\Crashpad --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=139.0.7258.128 --initial-client-data=0x2ac,0x2b0,0x2b4,0x288,0x2b8,0x7ff71e8d2520,0x7ff71e8d252c,0x7ff71e8d2538 | C:\Windows\SystemTemp\chrome_Unpacker_BeginUnzipping3672_2004738171\CR_27973.tmp\setup.exe | — | setup.exe | |||||||||||
User: SYSTEM Company: Google LLC Integrity Level: SYSTEM Description: Google Chrome Installer Exit code: 0 Version: 139.0.7258.128 Modules
| |||||||||||||||
| 2296 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --extension-process --enable-dinosaur-easter-egg-alt-images --force-high-res-timeticks=disabled --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --metrics-shmem-handle=3672,i,8645020727576926840,13200503592847553302,2097152 --field-trial-handle=1868,i,5885215776343114923,9230722159622840377,262144 --variations-seed-version --mojo-platform-channel-handle=3840 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 139.0.7258.128 Modules
| |||||||||||||||
| 2312 | C:\Users\admin\AppData\Local\Temp\Google1204_2077427050\bin\updater.exe --crash-handler --system "--database=C:\Program Files (x86)\Google\GoogleUpdater\141.0.7340.0\Crashpad" --url=https://clients2.google.com/cr/report --annotation=prod=Update4 --annotation=ver=141.0.7340.0 "--attachment=C:\Program Files (x86)\Google\GoogleUpdater\updater.log" --initial-client-data=0x2a8,0x2ac,0x2b0,0x284,0x2b4,0x5f42e8,0x5f42f4,0x5f4300 | C:\Users\admin\AppData\Local\Temp\Google1204_2077427050\bin\updater.exe | — | updater.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: HIGH Description: Google Updater (x86) Exit code: 0 Version: 141.0.7340.0 Modules
| |||||||||||||||
| 2312 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --enable-dinosaur-easter-egg-alt-images --force-high-res-timeticks=disabled --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=13 --metrics-shmem-handle=5412,i,6265720243676731802,293022690444545507,2097152 --field-trial-handle=1868,i,5885215776343114923,9230722159622840377,262144 --variations-seed-version --mojo-platform-channel-handle=5432 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 139.0.7258.128 Modules
| |||||||||||||||
| 2460 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --no-pre-read-main-dll --force-high-res-timeticks=disabled --gpu-preferences=SAAAAAAAAADgAAAIAAAAAAAAAAAAAGAAAQAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAQAAAAAAAAABAAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --metrics-shmem-handle=1740,i,1867020195409828186,17112490238632017694,262144 --field-trial-handle=1868,i,5885215776343114923,9230722159622840377,262144 --variations-seed-version --mojo-platform-channel-handle=1876 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 139.0.7258.128 Modules
| |||||||||||||||
Total events
6 403
Read events
6 247
Write events
142
Delete events
14
Modification events
| (PID) Process: | (4768) updater.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{8018F647-BF07-55BB-82BE-A2D7049F7CE4} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4768) updater.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{8A1D4361-2C08-4700-A351-3EAA9CBFF5E4} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4768) updater.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{534F5323-3569-4F42-919D-1E1CF93E5BF6} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4768) updater.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{521FDB42-7130-4806-822A-FC5163FAD983} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4768) updater.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{ABC01078-F197-4B0B-ADBC-CFE684B39C82} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4768) updater.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{8018F647-BF07-55BB-82BE-A2D7049F7CE4} |
| Operation: | write | Name: | AppID |
Value: {8018F647-BF07-55BB-82BE-A2D7049F7CE4} | |||
| (PID) Process: | (4768) updater.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\AppID\{8018F647-BF07-55BB-82BE-A2D7049F7CE4} |
| Operation: | write | Name: | LocalService |
Value: GoogleUpdaterService141.0.7340.0 | |||
| (PID) Process: | (4768) updater.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\AppID\{8018F647-BF07-55BB-82BE-A2D7049F7CE4} |
| Operation: | write | Name: | ServiceParameters |
Value: --com-service | |||
| (PID) Process: | (4768) updater.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{8A1D4361-2C08-4700-A351-3EAA9CBFF5E4} |
| Operation: | write | Name: | AppID |
Value: {8A1D4361-2C08-4700-A351-3EAA9CBFF5E4} | |||
| (PID) Process: | (4768) updater.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\AppID\{8A1D4361-2C08-4700-A351-3EAA9CBFF5E4} |
| Operation: | write | Name: | LocalService |
Value: GoogleUpdaterService141.0.7340.0 | |||
Executable files
9
Suspicious files
107
Text files
55
Unknown types
26
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1204 | ChromeInstaller.exe | C:\Users\admin\AppData\Local\Temp\Google1204_1149070650\UPDATER.PACKED.7Z | — | |
MD5:— | SHA256:— | |||
| 6636 | updater.exe | C:\Program Files (x86)\Google\GoogleUpdater\141.0.7340.0\uninstall.cmd | text | |
MD5:FBC297EE9060D4256192E4EDB98CAD1B | SHA256:099592FFA867124D16C0C6D868AF1214FD2B7180FA76E4EEE01ABF2A5CF8F044 | |||
| 3788 | Browser.exe | C:\Users\admin\AppData\Local\Temp\CA11.tmp\CA12.tmp\CA13.bat | text | |
MD5:D2985210BF3FE9BB5B889CFC75C61E13 | SHA256:491F4BB23D05F5499A2EE43169E6CDCC58AC5C097626CE95ED2CF2BF75CAADDC | |||
| 4768 | updater.exe | C:\Program Files (x86)\Google\Update\GoogleUpdate.exe | executable | |
MD5:4BBA7FFD6F76411F51011349BB584775 | SHA256:A635DC2808FB688B61E84E1D70F0253F189363D410CD3F32B5D42CB877F3026F | |||
| 6636 | updater.exe | C:\Program Files (x86)\Google\GoogleUpdater\141.0.7340.0\updater.exe | executable | |
MD5:4BBA7FFD6F76411F51011349BB584775 | SHA256:A635DC2808FB688B61E84E1D70F0253F189363D410CD3F32B5D42CB877F3026F | |||
| 3672 | updater.exe | C:\Windows\SystemTemp\chrome_url_fetcher_3672_1135400818\e10312e09643e2b370158d95005b7a8c3ca224ac6eace831abf97efa32ed675c | — | |
MD5:— | SHA256:— | |||
| 6636 | updater.exe | C:\Program Files (x86)\Google\GoogleUpdater\dab32b03-9005-4df1-9c60-e03db3e2acdb.tmp | binary | |
MD5:A46C18F0067E79C4896FF72440523DA1 | SHA256:792F97B75CE3A0BD9B6A314530F1B3615120EE03564FD0BA39BFA641B256F7C1 | |||
| 4768 | updater.exe | C:\Program Files (x86)\Google\GoogleUpdater\prefs.json~RF18f6ce.TMP | binary | |
MD5:A46C18F0067E79C4896FF72440523DA1 | SHA256:792F97B75CE3A0BD9B6A314530F1B3615120EE03564FD0BA39BFA641B256F7C1 | |||
| 6636 | updater.exe | C:\Program Files (x86)\Google\GoogleUpdater\prefs.json | binary | |
MD5:A46C18F0067E79C4896FF72440523DA1 | SHA256:792F97B75CE3A0BD9B6A314530F1B3615120EE03564FD0BA39BFA641B256F7C1 | |||
| 6636 | updater.exe | C:\Program Files (x86)\Google\GoogleUpdater\prefs.json~RF18f5c5.TMP | binary | |
MD5:6A7C22B00ADBF302C1F53F51AF1AB2F6 | SHA256:BFD4268EDA9AB3F0E8D8D2ED0884BD28C0B34546332B36E54EBD30ACF45053FF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
60
DNS requests
66
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
764 | lsass.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEFZnHQTqT5lMbxCBR1nSdZQ%3D | unknown | — | — | whitelisted |
764 | lsass.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBSr83eyJy3njhjVpn5bEpfc6MXawQQUOuEJhtTPGcKWdnRJdtzgNcZjY5oCEQDzZE5rbgBQI34JRr174fUd | unknown | — | — | whitelisted |
764 | lsass.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | — | — | whitelisted |
764 | lsass.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTPlNxcMEqnlIVyH5VuZ4lawhZX3QQU9oUKOxGG4QR9DqoLLNLuzGR7e64CEQCrZoa1YnvoBZaCEzAShkn1 | unknown | — | — | whitelisted |
764 | lsass.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | — | — | whitelisted |
5644 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.8:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6636 | updater.exe | GET | 200 | 142.250.185.131:80 | http://o.pki.goog/we2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTuMJxAT2trYla0jia%2F5EUSmLrk3QQUdb7Ed66J9kQ3fc%2BxaB8dGuvcNFkCEQDPZmByDOs98xJONhjjIZaE | unknown | — | — | whitelisted |
6636 | updater.exe | GET | 200 | 142.250.185.131:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3628 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2996 | curl.exe | 140.82.121.3:443 | github.com | GITHUB | US | whitelisted |
764 | lsass.exe | 172.64.149.23:80 | ocsp.comodoca.com | CLOUDFLARENET | US | whitelisted |
2996 | curl.exe | 185.199.108.133:443 | release-assets.githubusercontent.com | FASTLY | US | whitelisted |
5644 | svchost.exe | 40.126.31.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5644 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
github.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
release-assets.githubusercontent.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access release user assets on GitHub |
— | — | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
— | — | Misc activity | ET INFO EXE - Served Attached HTTP |
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
3940 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
3940 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
Process | Message |
|---|---|
chrome.exe | I0000 00:00:1755326444.587268 1328 voice_transcription.cc:58] Registering VoiceTranscriptionCapability
|