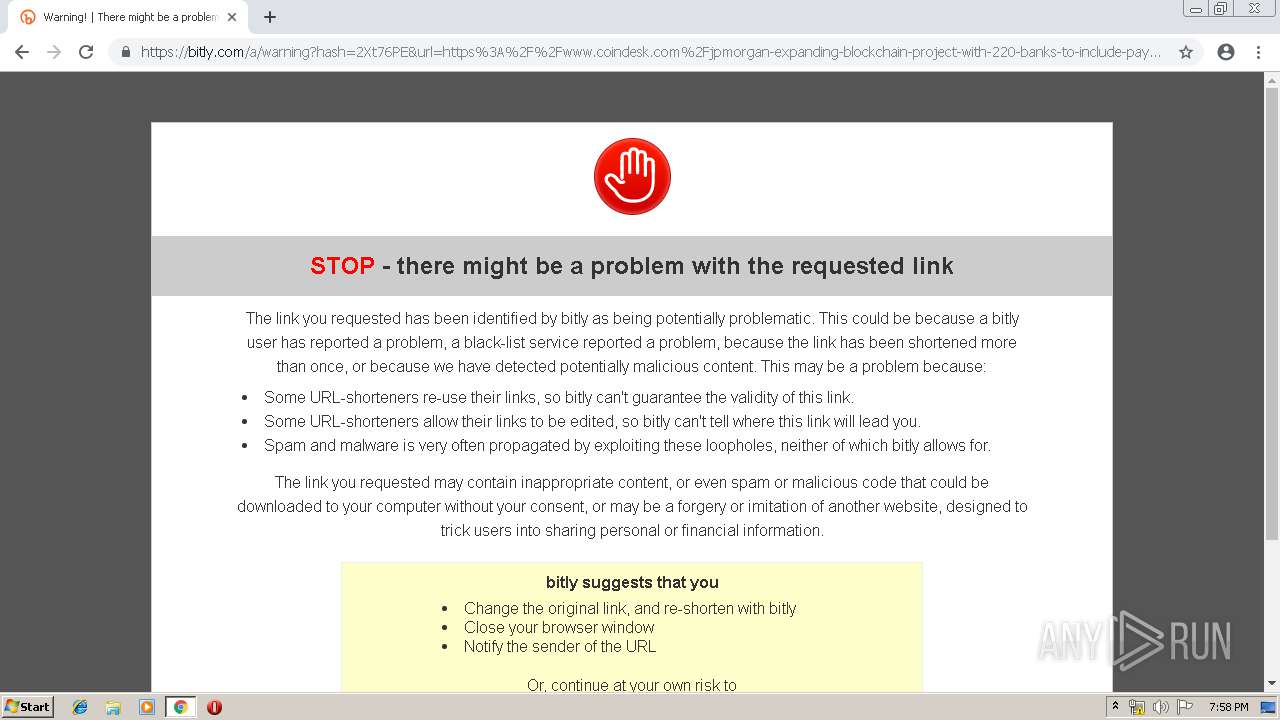
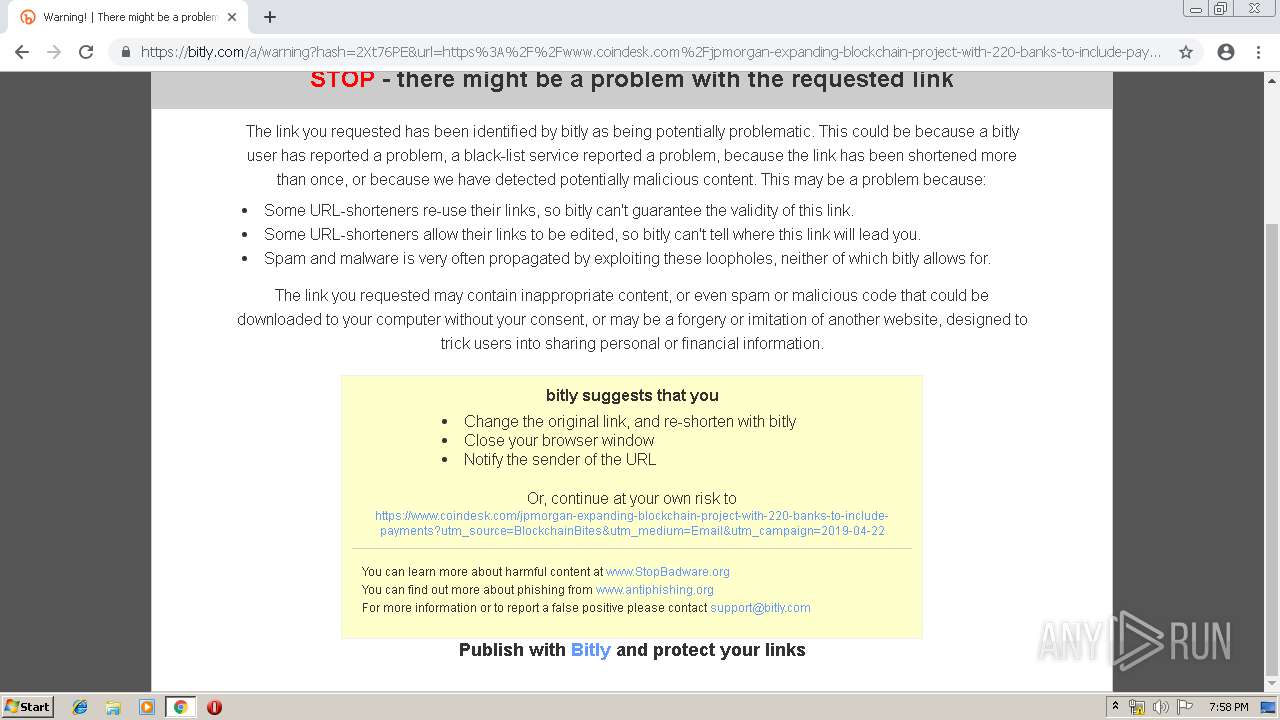
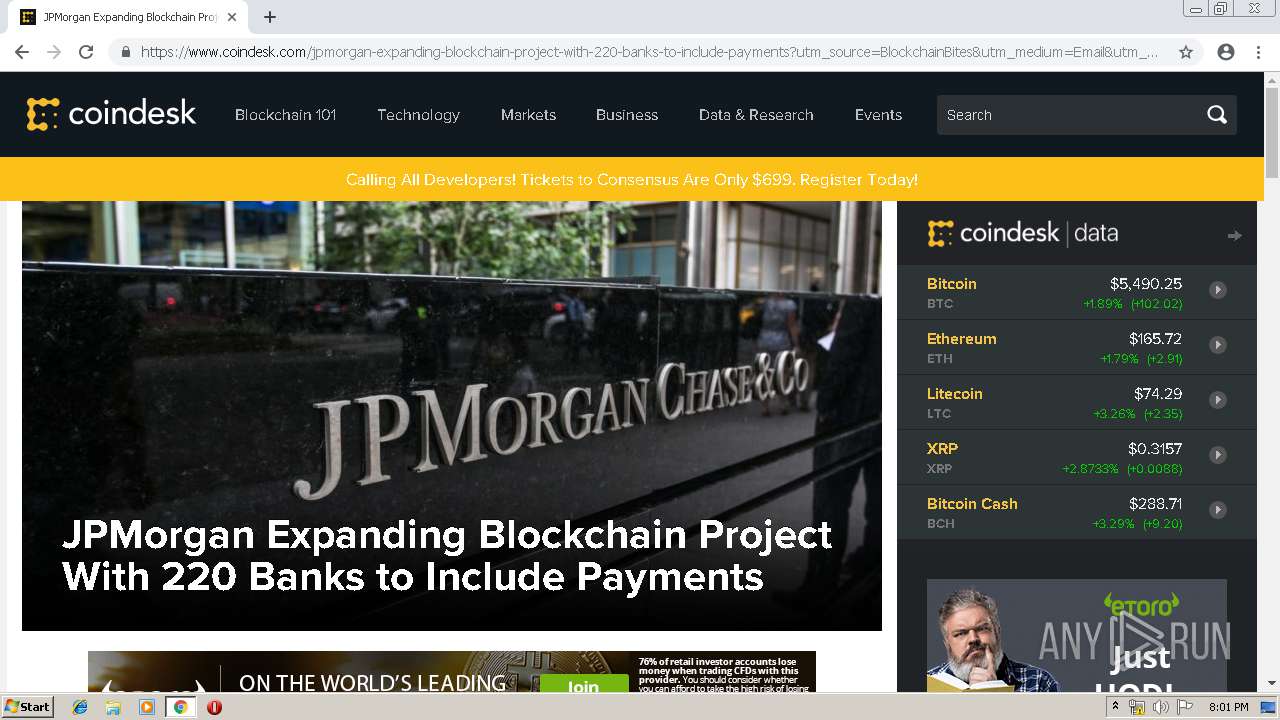
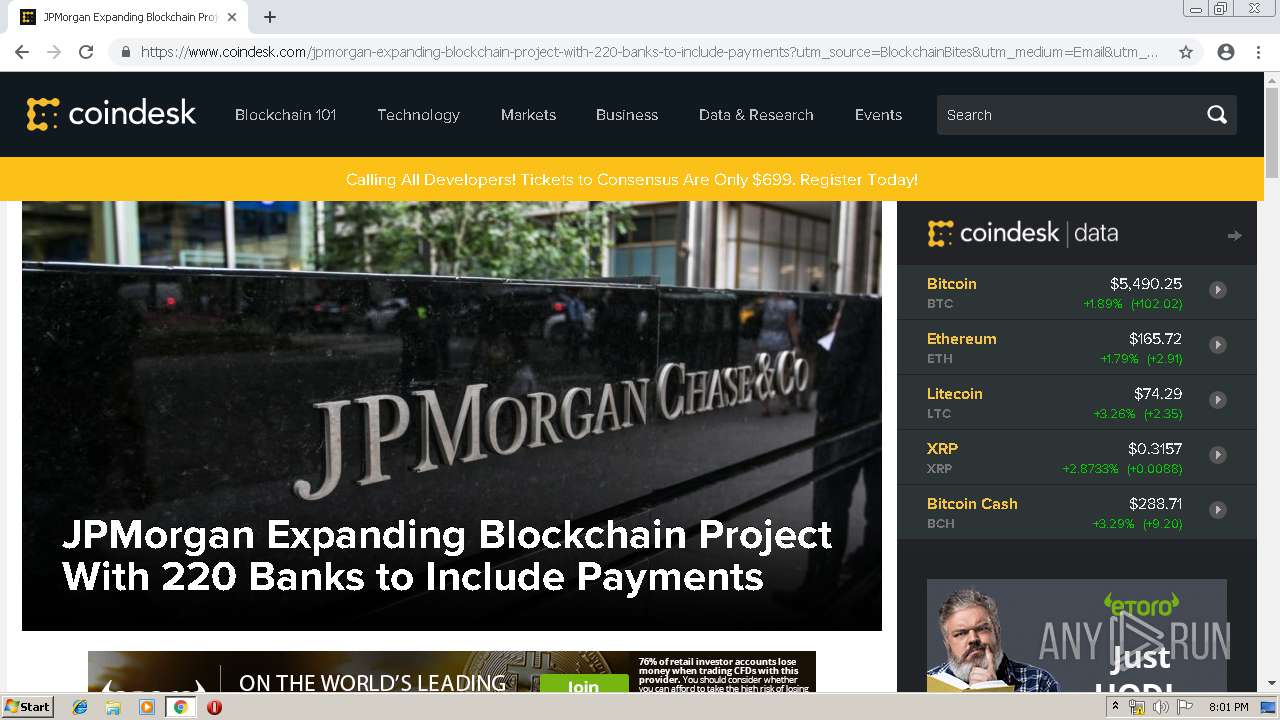
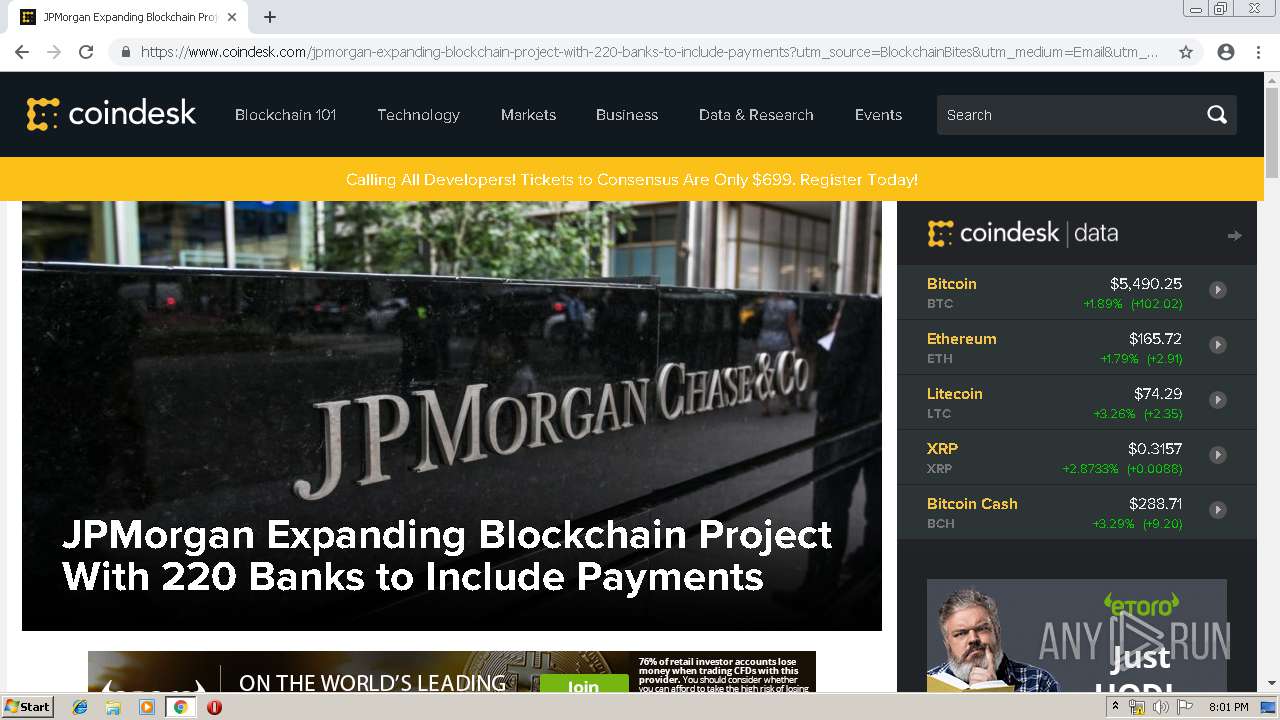
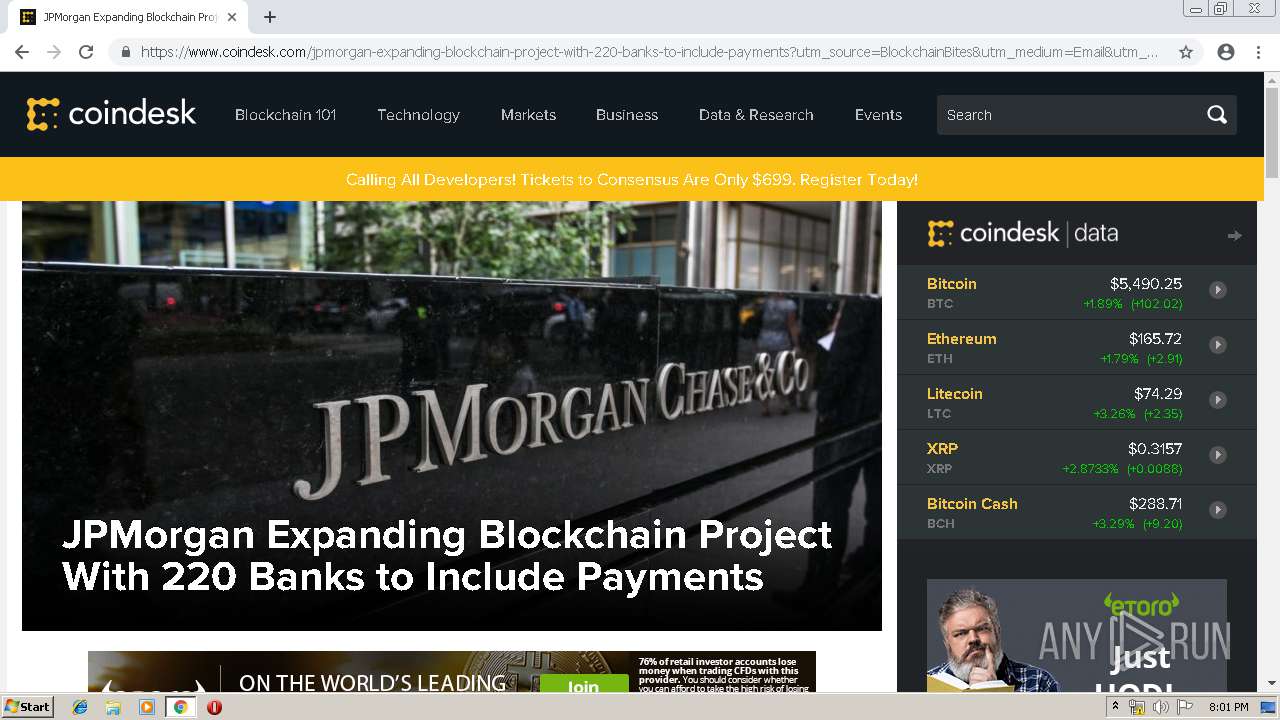
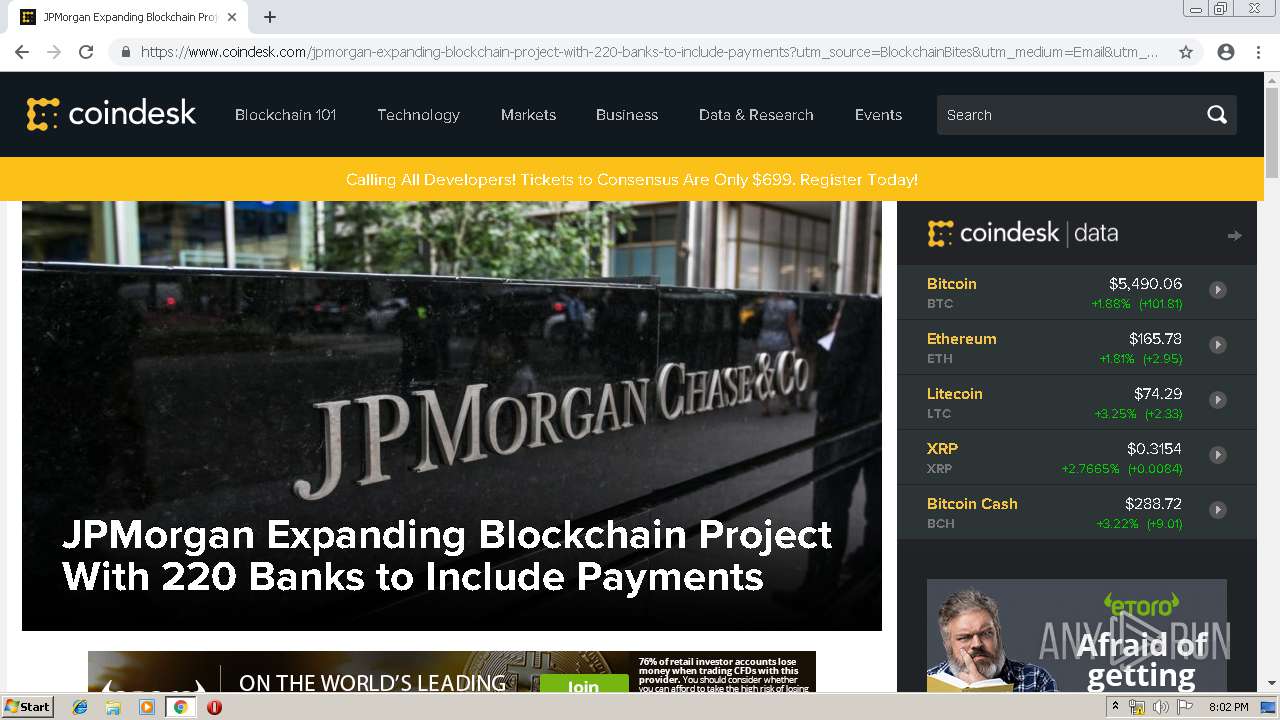
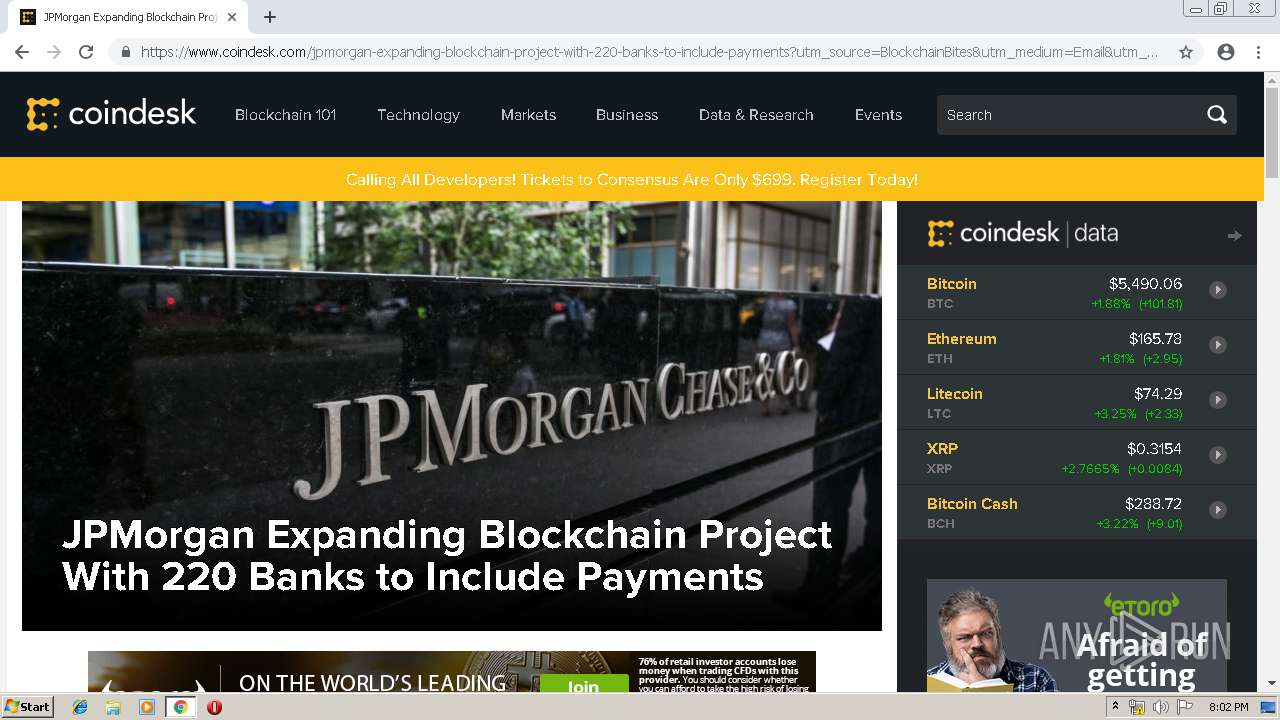
| download: | jpmorgan-expanding-blockchain-project-with-220-banks-to-include-payments |
| Full analysis: | https://app.any.run/tasks/012347fd-9d76-4958-ad1b-aa9e7080fb36 |
| Verdict: | Malicious activity |
| Analysis date: | April 25, 2019, 18:57:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, UTF-8 Unicode text, with very long lines, with CRLF, LF line terminators |
| MD5: | 26F01A0D276AA6A50465DEF9471ECAE7 |
| SHA1: | F50A06132B1B7798E4F41FCB55F93A6AA0B7C4D9 |
| SHA256: | CF28B8B33793C23ACE65C1E645BBF4A3CFF239CEA73821085D0D3B882B0A22A4 |
| SSDEEP: | 1536:9C304WhFnro/HgCNy3+XXRCM0yzTcQxOyB4prbJyy/Vf/XybAxZRyQ6ElyAYYYTb:ufWTrRJeOTcERvBsO/C |
MALICIOUS
No malicious indicators.SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 3908)
INFO
Application launched itself
- iexplore.exe (PID: 2288)
- chrome.exe (PID: 3908)
Reads internet explorer settings
- iexplore.exe (PID: 2112)
Changes settings of System certificates
- iexplore.exe (PID: 2112)
Reads settings of System Certificates
- chrome.exe (PID: 3908)
- iexplore.exe (PID: 2112)
Changes internet zones settings
- iexplore.exe (PID: 2288)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2112)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .htm/html | | | HyperText Markup Language with DOCTYPE (80.6) |
|---|---|---|
| .html | | | HyperText Markup Language (19.3) |
EXIF
HTML
| pDomain_verify: | 266ef71c542343fed103b1f5f9ebba6e |
|---|---|
| alexaVerifyID: | CGq9LThNt02vzHpLoscJj-arUCM |
| msapplicationConfig: | none |
| viewport: | width=device-width,initial-scale=1 |
| formatDetection: | telephone=no |
| microtip: | 1G1pCNLKZCZde4dgznZDE5wiikQeyDGeuh |
| bravePublisherVerification: | 02c1e8b9dd0ce28e441b68ee57756dba7b00b65efb6649d6a751411c5140a1c7 |
| pocketSiteVerification: | b34cfc52d091d98bf731da4fe501d6 |
| parselyMetadata: | {"id":393955,"excerpt":"Investment bank JPMorgan is reportedly expanding an existing blockchain platform with hundreds of banking members to include settlement.","path":"\/jpmorgan-expanding-blockchain-project-with-220-banks-to-include-payments"} |
| msvalidate01: | 67079DDEA8D1943F49A6A5260E166131 |
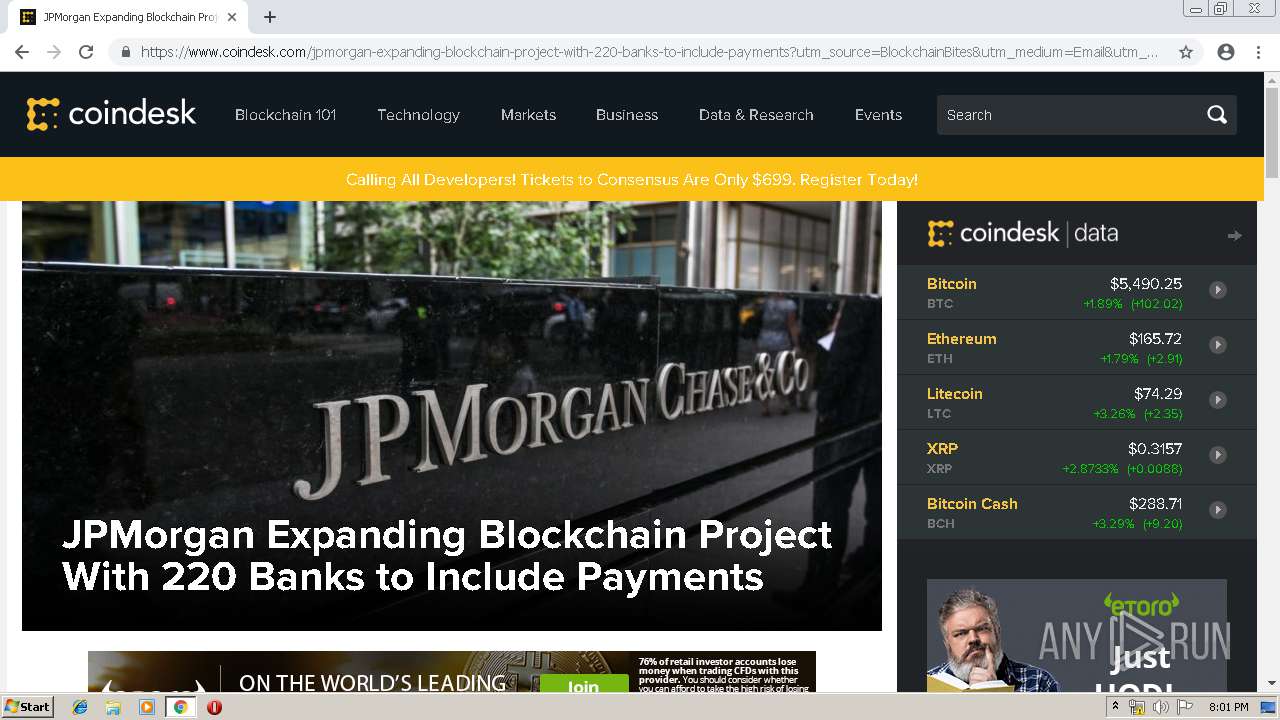
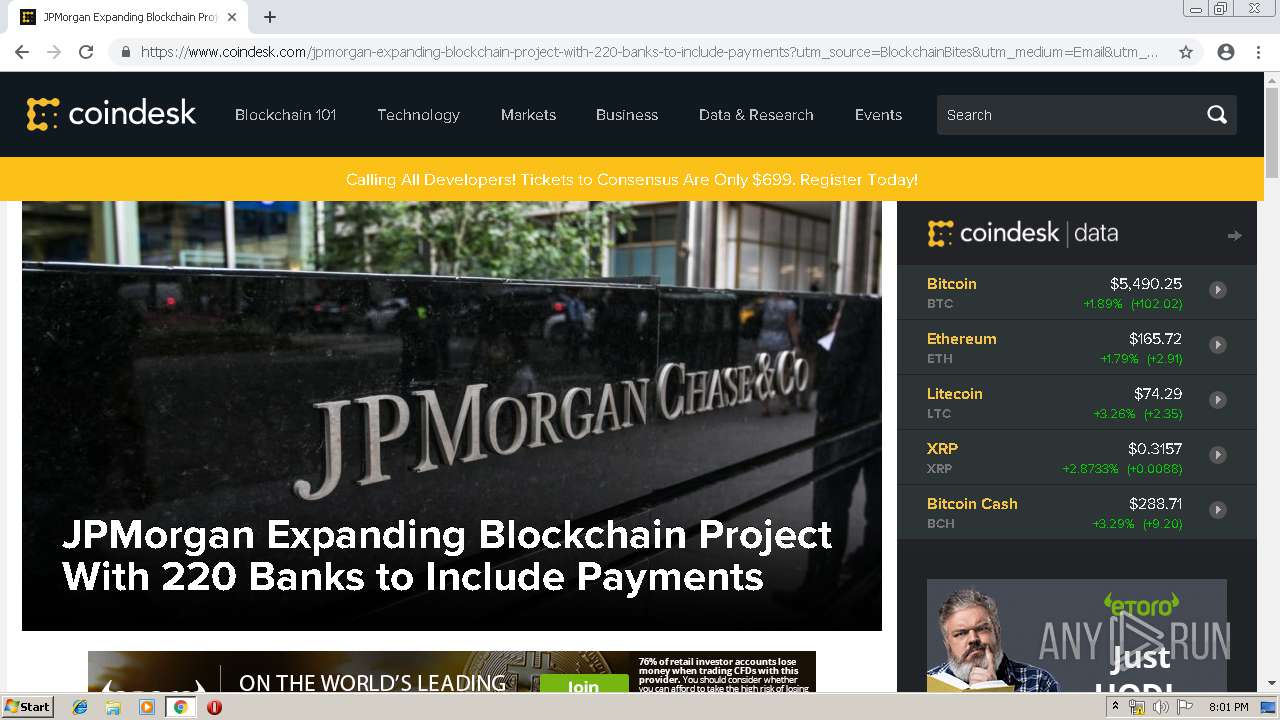
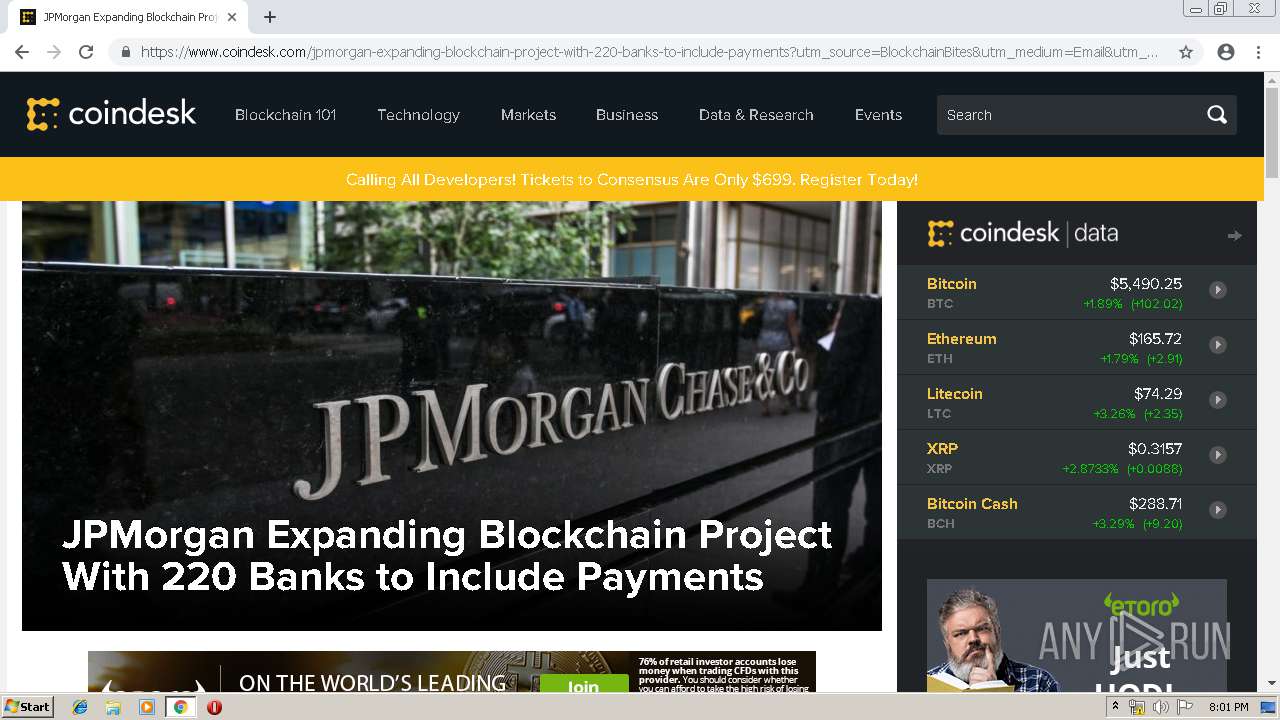
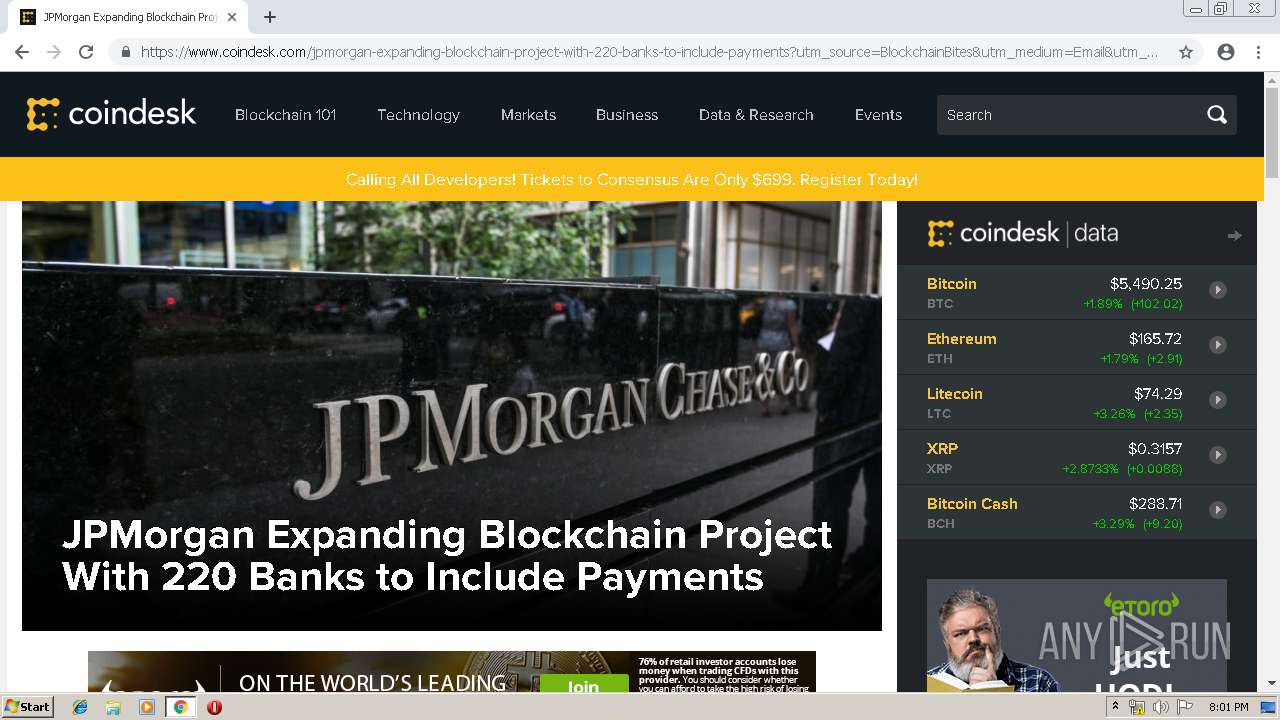
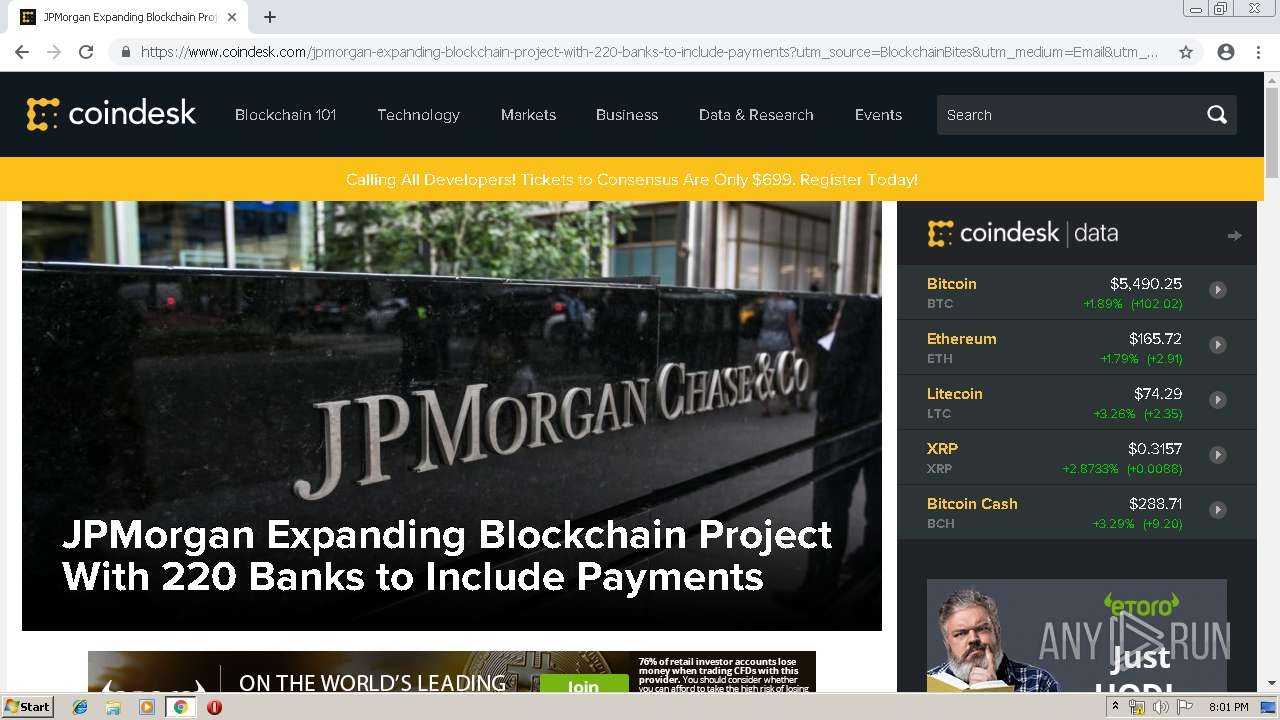
| Title: | JPMorgan Expanding Blockchain Project With 220 Banks to Include Payments - CoinDesk |
| twitterCard: | summary_large_image |
| twitterDescription: | Investment bank JPMorgan is reportedly expanding an existing blockchain platform with hundreds of banking members to include settlement. |
| twitterTitle: | JPMorgan Expanding Blockchain Project With 220 Banks to Include Payments - CoinDesk |
| twitterSite: | @coindesk |
| twitterImage: | https://static.coindesk.com/wp-content/uploads/2016/07/jpmorgan-e1468882068523.jpg |
| twitterCreator: | @Dan_Z_Palmer |
| Generator: | WordPress 4.9.10 |
| msapplicationTileImage: | https://static.coindesk.com/wp-content/uploads/2017/05/cropped-coindesk-new-favicon.png |
Total processes
92
Monitored processes
60
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=920,10171220364030200673,1817994004370053506,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=8358737221329042580 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=8358737221329042580 --renderer-client-id=57 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=7808 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 276 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=920,10171220364030200673,1817994004370053506,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=4476478126734904189 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=4476478126734904189 --renderer-client-id=30 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3148 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 544 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=920,10171220364030200673,1817994004370053506,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=10876936312275081983 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=10876936312275081983 --renderer-client-id=19 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2176 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 572 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=920,10171220364030200673,1817994004370053506,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=4825442902671891480 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=4825442902671891480 --renderer-client-id=34 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=7900 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 788 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=920,10171220364030200673,1817994004370053506,131072 --enable-features=PasswordImport --service-pipe-token=716241570461649857 --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=716241570461649857 --renderer-client-id=3 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2176 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 832 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=920,10171220364030200673,1817994004370053506,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=5044748485965764976 --mojo-platform-channel-handle=3356 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 856 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=920,10171220364030200673,1817994004370053506,131072 --enable-features=PasswordImport --service-pipe-token=12636734850318720936 --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=12636734850318720936 --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1944 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 916 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=920,10171220364030200673,1817994004370053506,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=16955130143887084445 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=16955130143887084445 --renderer-client-id=21 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4060 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 928 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=920,10171220364030200673,1817994004370053506,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=13977639327921260296 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=13977639327921260296 --renderer-client-id=51 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=8384 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1160 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=920,10171220364030200673,1817994004370053506,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=17662209608247798352 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=17662209608247798352 --renderer-client-id=24 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=5380 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
Total events
1 122
Read events
886
Write events
217
Delete events
19
Modification events
| (PID) Process: | (2288) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2288) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2288) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2288) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2112) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\iexplore |
| Operation: | write | Name: | Type |
Value: 3 | |||
| (PID) Process: | (2112) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\iexplore |
| Operation: | write | Name: | Count |
Value: 1 | |||
| (PID) Process: | (2112) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{761497BB-D6F0-462C-B6EB-D4DAF1D92D43}\iexplore |
| Operation: | write | Name: | Time |
Value: E307040004001900120039003200B702 | |||
| (PID) Process: | (2288) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2288) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000071000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2288) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {051ACF5D-678C-11E9-A09E-5254004A04AF} |
Value: 0 | |||
Executable files
0
Suspicious files
199
Text files
181
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2288 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2288 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2112 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Cab6DD9.tmp | — | |
MD5:— | SHA256:— | |||
| 2112 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Tar6DDA.tmp | — | |
MD5:— | SHA256:— | |||
| 2112 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Cab6DFA.tmp | — | |
MD5:— | SHA256:— | |||
| 2112 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Tar6DFB.tmp | — | |
MD5:— | SHA256:— | |||
| 2112 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Cab6E3A.tmp | — | |
MD5:— | SHA256:— | |||
| 2112 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Tar6E3B.tmp | — | |
MD5:— | SHA256:— | |||
| 2112 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Cab6E4C.tmp | — | |
MD5:— | SHA256:— | |||
| 2112 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Cab6E4D.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
239
DNS requests
181
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3908 | chrome.exe | GET | 302 | 172.217.22.14:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjJlQUFXRC12Ny1ldUFnMXF3SDlXZDlFZw/7319.128.0.1_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 504 b | whitelisted |
2112 | iexplore.exe | GET | 200 | 2.16.186.81:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | unknown | compressed | 55.6 Kb | whitelisted |
3908 | chrome.exe | GET | 200 | 173.194.164.140:80 | http://r6---sn-4g5e6nle.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjJlQUFXRC12Ny1ldUFnMXF3SDlXZDlFZw/7319.128.0.1_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mip=185.217.119.8&mm=28&mn=sn-4g5e6nle&ms=nvh&mt=1556218544&mv=m&pl=24&shardbypass=yes | US | crx | 842 Kb | whitelisted |
2112 | iexplore.exe | GET | 200 | 2.16.186.81:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | unknown | compressed | 55.6 Kb | whitelisted |
2112 | iexplore.exe | GET | 200 | 52.85.188.163:80 | http://x.ss2.us/x.cer | US | der | 1.27 Kb | whitelisted |
2112 | iexplore.exe | GET | 200 | 52.85.188.159:80 | http://x.ss2.us/x.cer | US | der | 1.27 Kb | whitelisted |
2112 | iexplore.exe | GET | 200 | 52.85.188.163:80 | http://x.ss2.us/x.cer | US | der | 1.27 Kb | whitelisted |
2288 | iexplore.exe | GET | 200 | 13.107.21.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
3908 | chrome.exe | GET | 200 | 204.13.202.71:80 | http://ssl.trustwave.com/issuers/STCA.crt | US | der | 956 b | whitelisted |
3908 | chrome.exe | GET | 200 | 205.185.216.42:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/47BEABC922EAE80E78783462A79F45C254FDE68B.crt | US | der | 969 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2112 | iexplore.exe | 52.164.210.24:443 | consent.cookiebot.com | Microsoft Corporation | IE | whitelisted |
2288 | iexplore.exe | 13.107.21.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2112 | iexplore.exe | 104.16.125.175:443 | unpkg.com | Cloudflare Inc | US | shared |
2112 | iexplore.exe | 54.230.93.247:443 | static.coindesk.com | Amazon.com, Inc. | US | unknown |
2112 | iexplore.exe | 192.0.73.2:443 | secure.gravatar.com | Automattic, Inc | US | whitelisted |
2112 | iexplore.exe | 52.85.188.202:80 | x.ss2.us | Amazon.com, Inc. | US | unknown |
2112 | iexplore.exe | 52.85.188.163:80 | x.ss2.us | Amazon.com, Inc. | US | unknown |
2112 | iexplore.exe | 52.85.188.159:80 | x.ss2.us | Amazon.com, Inc. | US | whitelisted |
2112 | iexplore.exe | 2.16.186.81:80 | www.download.windowsupdate.com | Akamai International B.V. | — | whitelisted |
3908 | chrome.exe | 172.217.23.141:443 | accounts.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
consent.cookiebot.com |
| whitelisted |
www.bing.com |
| whitelisted |
unpkg.com |
| whitelisted |
static.coindesk.com |
| whitelisted |
secure.gravatar.com |
| whitelisted |
x.ss2.us |
| whitelisted |
www.download.windowsupdate.com |
| whitelisted |
www.google.com.ua |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |