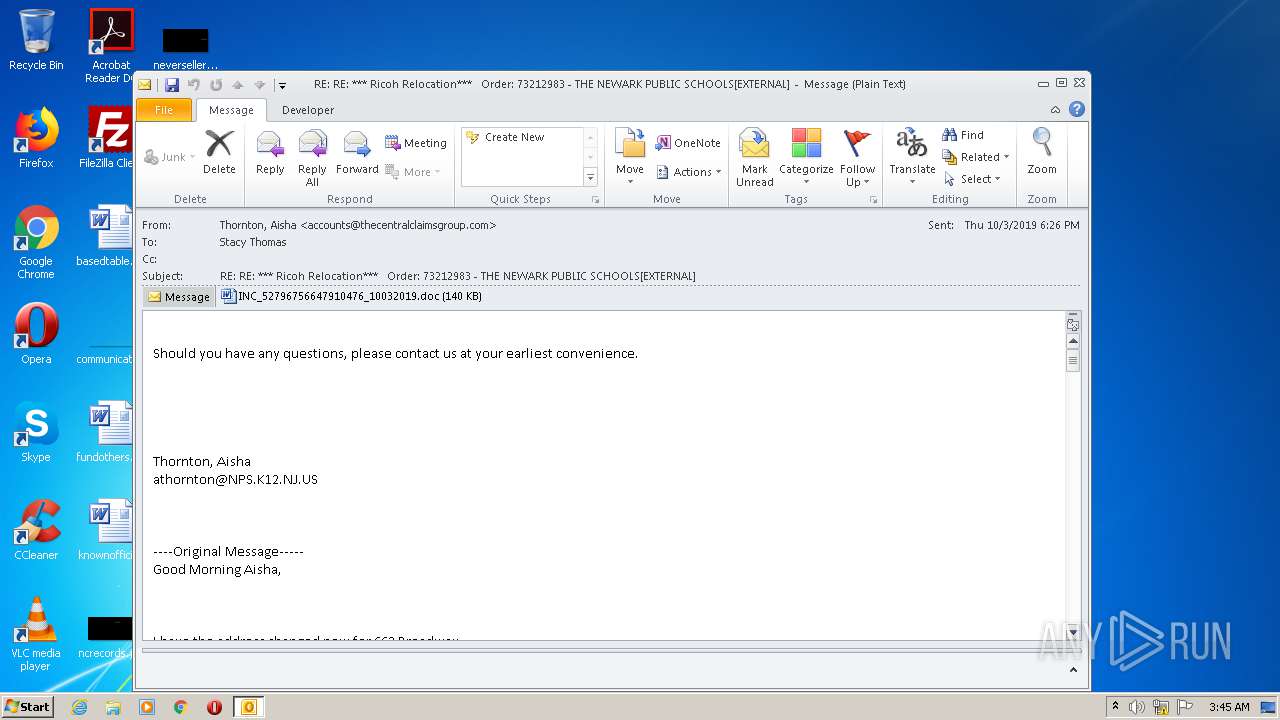
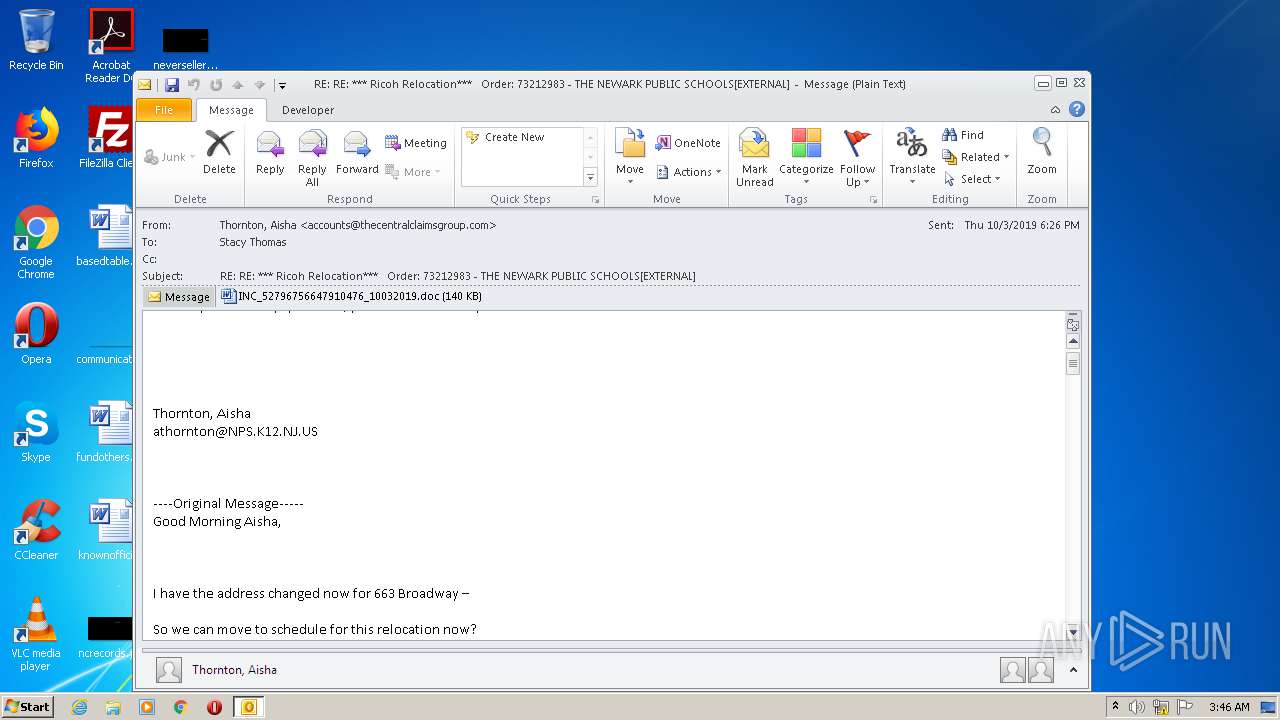
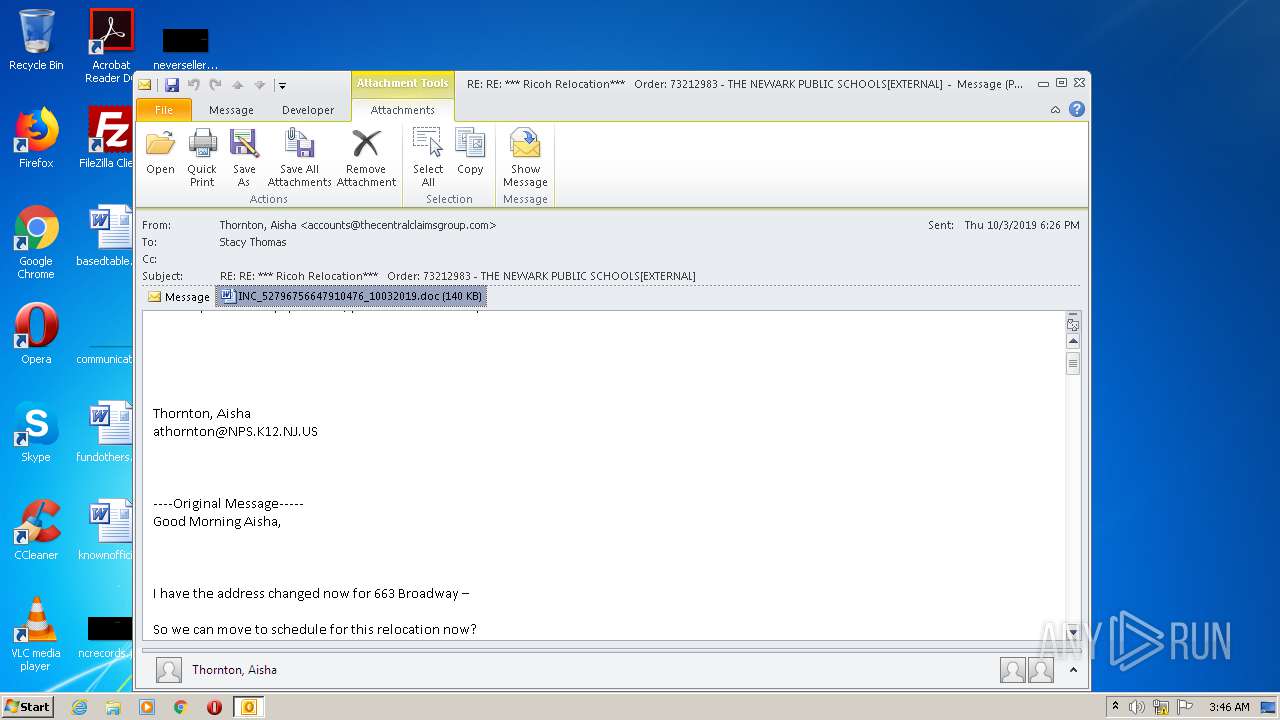
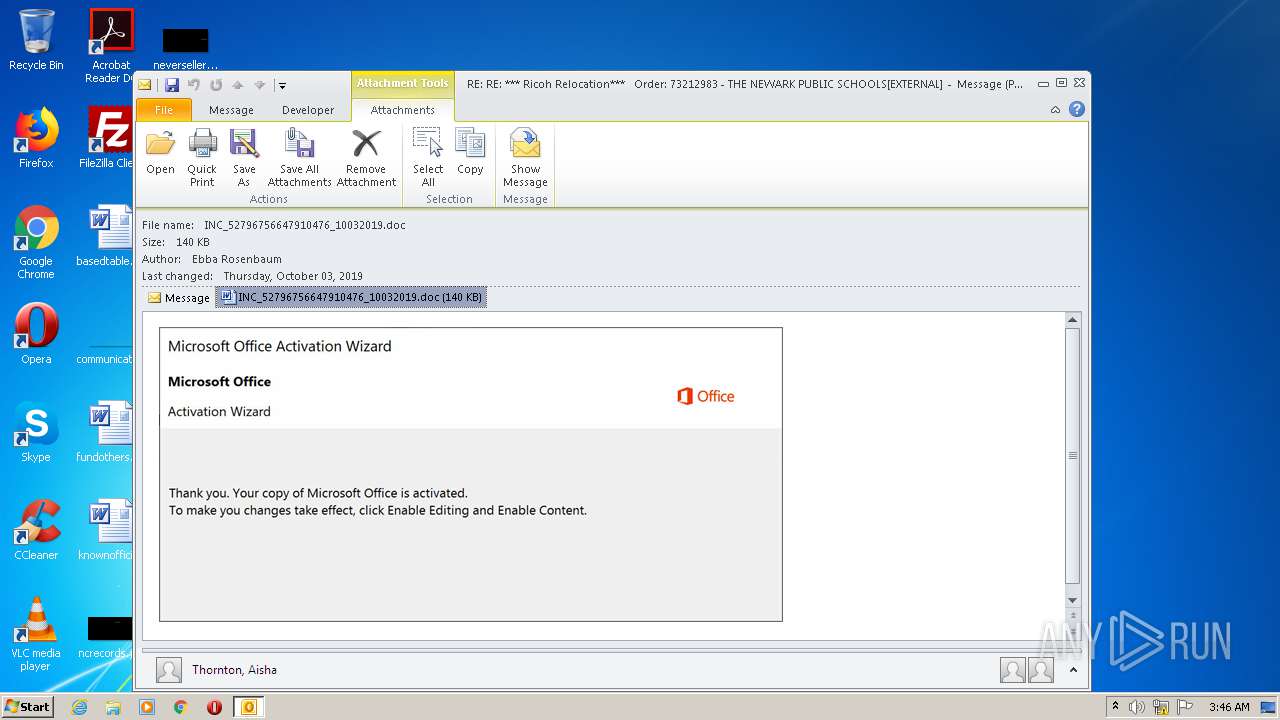
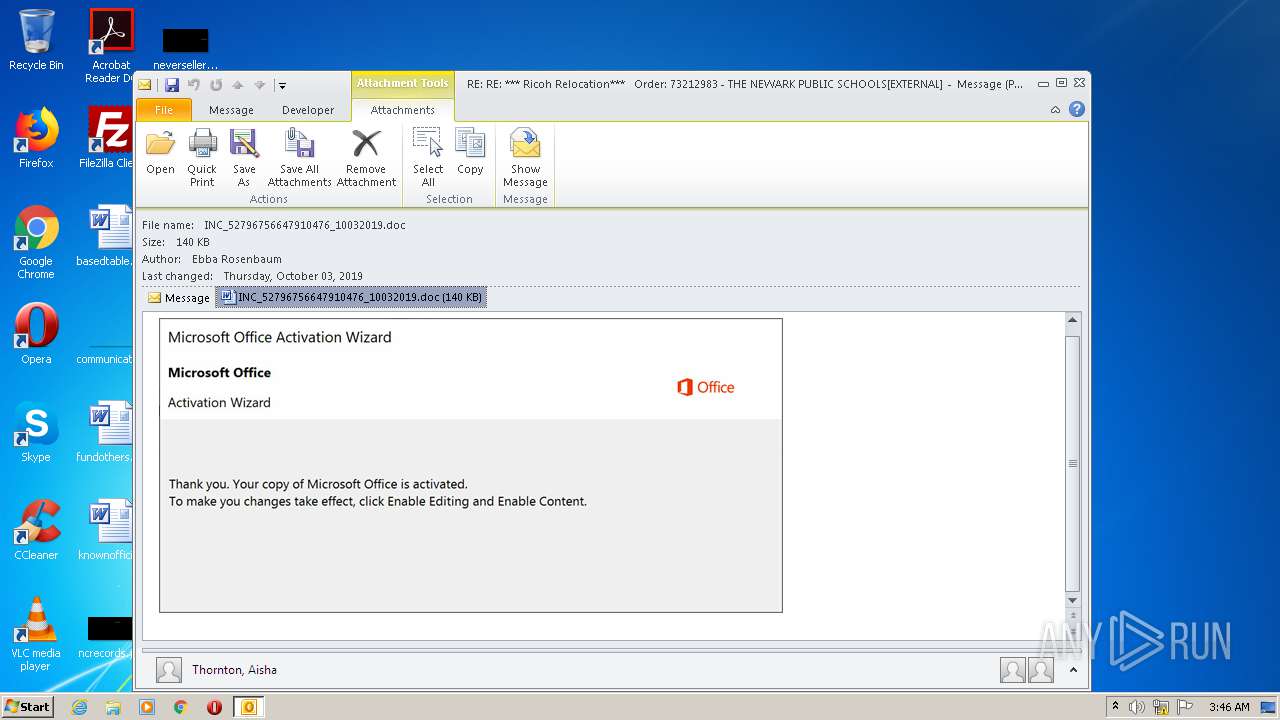
| File name: | RE%3a RE%3a %2a%2a%2a Ricoh Relocation%2a%2a%2a Order%3a 73212983 - THE NEWARK PUBLIC SCHOOLS[EXTERNAL].eml |
| Full analysis: | https://app.any.run/tasks/e3c77f36-dc44-4347-a018-6d8b786aafd2 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | September 30, 2020, 02:45:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF line terminators |
| MD5: | 271D0DDA77F8628178A228D12F52E396 |
| SHA1: | AB8A9438654C56D8B21E694F2FED3BE786AC4781 |
| SHA256: | CEDF990B964A2A1F819F864102F973DC3E71075C2A154F1FD95122F51FE869EE |
| SSDEEP: | 3072:+34RKVz7MtaaQZGCKAGCIH2OKsp+7VDgPa+LQT0tfKwho8PU8n:+QKVz7MQZZKOjM+7iaPT0tfJW8cu |
MALICIOUS
Drops known malicious document
- OUTLOOK.EXE (PID: 2536)
SUSPICIOUS
Creates files in the user directory
- OUTLOOK.EXE (PID: 2536)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 2536)
Starts Microsoft Office Application
- OUTLOOK.EXE (PID: 2536)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2828)
- OUTLOOK.EXE (PID: 2536)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 11) (100) |
|---|
Total processes
37
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2536 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\e5d63173-1f7c-4ea4-9a9f-d938f4e1402b.eml" | C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 2828 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
1 725
Read events
1 164
Write events
542
Delete events
19
Modification events
| (PID) Process: | (2536) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2536) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2536) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2536) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2536) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2536) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2536) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2536) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2536) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (2536) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
3
Text files
27
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2536 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRB01C.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2536 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\tmpB24F.tmp | — | |
MD5:— | SHA256:— | |||
| 2536 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DF3220AB3B6F047D48.TMP | — | |
MD5:— | SHA256:— | |||
| 2536 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\G8B9GGPU\INC_52796756647910476_10032019 (2).doc\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 2536 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DF55F6ECFE9AAA9692.TMP | — | |
MD5:— | SHA256:— | |||
| 2536 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DF598EF82846C424E6.TMP | — | |
MD5:— | SHA256:— | |||
| 2536 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\OICE_262E4A09-4AE9-44E2-84B4-5FD102B737B0.0\1C953936.doc\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 2536 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 2536 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2536 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\{EDCAB9D6-03A1-4DE5-803D-A08C605C09EA}\{1C306CB1-771E-4B4B-A902-86E897877F5B}.png | image | |
MD5:4C61C12EDBC453D7AE184976E95258E1 | SHA256:296526F9A716C1AA91BA5D6F69F0EB92FDF79C2CB2CFCF0CEB22B7CCBC27035F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2536 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2536 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |