| File name: | usbredirector-customer-module.exe |
| Full analysis: | https://app.any.run/tasks/17422e8e-6bf8-4ec2-8bad-50fc4b23c9cd |
| Verdict: | Malicious activity |
| Analysis date: | August 28, 2024, 08:16:08 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 68561300A678B4C7E022E988E46789A7 |
| SHA1: | 985F2F6283CD48246DD0FEC4FA51E20898F33F24 |
| SHA256: | CEDCF4410C554BD02151D9049638D7D02F50B597F743B3D4737115B1AD5C532E |
| SSDEEP: | 98304:4RSSVydgpXBA5x+ozs7TbighABgE5GIR6RZdIVEwDidHtB0XUle3yF45vfc0oGNn:9nBs7Ws0/COL |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- usbredirector-customer-module.exe (PID: 4680)
- usb-redirector-customer-module-gui.exe (PID: 5724)
Drops the executable file immediately after the start
- usbredirector-customer-module.exe (PID: 4680)
- usb-redirector-customer-module-gui.exe (PID: 5724)
Application launched itself
- usbredirectortechcsrv.exe (PID: 2252)
Drops a system driver (possible attempt to evade defenses)
- usbredirector-customer-module.exe (PID: 4680)
- usb-redirector-customer-module-gui.exe (PID: 5724)
Executes as Windows Service
- usbredirectortechcsrv.exe (PID: 2252)
Connects to unusual port
- usbredirectortechcsrv.exe (PID: 2252)
INFO
Checks supported languages
- usbredirector-customer-module.exe (PID: 4680)
- usbredirectortechcsrv.exe (PID: 5880)
Reads Microsoft Office registry keys
- CastSrv.exe (PID: 5880)
Reads the computer name
- usbredirectortechcsrv.exe (PID: 5880)
- usbredirector-customer-module.exe (PID: 4680)
Create files in a temporary directory
- usbredirector-customer-module.exe (PID: 4680)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:07:06 14:10:30+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 98816 |
| InitializedDataSize: | 192512 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xf97b |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.3.0.3330 |
| ProductVersionNumber: | 2.3.0.3330 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Private build, Special build |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
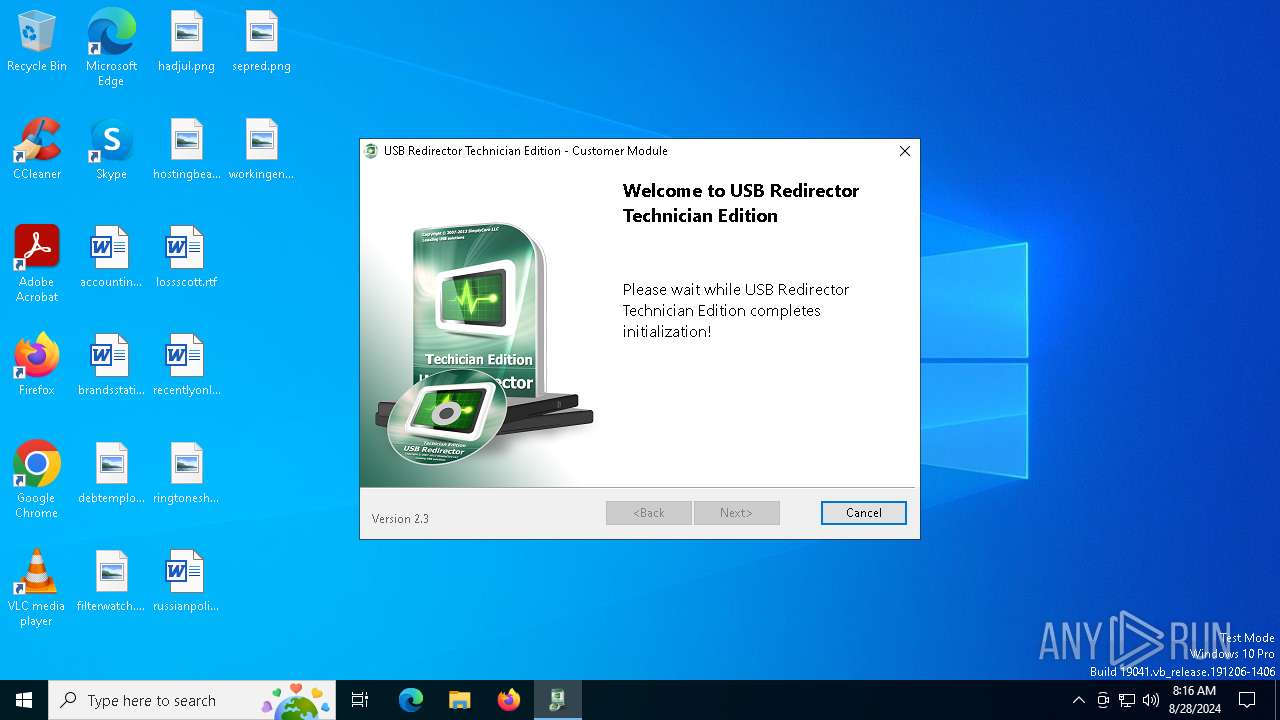
| Comments: | USB Redirector Technician Edition Customer Module |
| CompanyName: | SimplyCore LLC |
| FileDescription: | USB Redirector Technician Edition Customer Module |
| FileVersion: | 2,3,0,3330 |
| InternalName: | usbredirector-customer-module.exe |
| LegalCopyright: | Copyright (c) 2007 - 2022 SimplyCore LLC. All rights reserved. |
| LegalTrademarks: | Copyright (c) 2007 - 2022 SimplyCore LLC. All rights reserved. |
| OriginalFileName: | usbredirector-customer-module.exe |
| PrivateBuild: | 2,3,0,3330 |
| ProductName: | USB Redirector Technician Edition Customer Module |
| ProductVersion: | 2,3,0,3330 |
| SpecialBuild: | 2,3,0,3330 |
Total processes
154
Monitored processes
7
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2252 | C:\Users\admin\AppData\Local\Temp\69d6ef1af3f4cc2d81a8c8d573955def\usbredirectortechcsrv.exe | C:\Users\admin\AppData\Local\Temp\69d6ef1af3f4cc2d81a8c8d573955def\usbredirectortechcsrv.exe | services.exe | ||||||||||||
User: SYSTEM Company: SimplyCore LLC Integrity Level: SYSTEM Description: USB Redirector Technician Edition Customer Module service Exit code: 0 Version: 2,3,0,3330 Modules
| |||||||||||||||
| 4680 | "C:\Users\admin\AppData\Local\Temp\usbredirector-customer-module.exe" | C:\Users\admin\AppData\Local\Temp\usbredirector-customer-module.exe | explorer.exe | ||||||||||||
User: admin Company: SimplyCore LLC Integrity Level: HIGH Description: USB Redirector Technician Edition Customer Module Exit code: 0 Version: 2,3,0,3330 Modules
| |||||||||||||||
| 5724 | "C:\Users\admin\AppData\Local\Temp\69d6ef1af3f4cc2d81a8c8d573955def\usb-redirector-customer-module-gui.exe" | C:\Users\admin\AppData\Local\Temp\69d6ef1af3f4cc2d81a8c8d573955def\usb-redirector-customer-module-gui.exe | usbredirector-customer-module.exe | ||||||||||||
User: admin Company: SimplyCore LLC Integrity Level: HIGH Description: USB Redirector Technician Edition Customer Module Setup Wizard Exit code: 0 Version: 2,3,0,3330 Modules
| |||||||||||||||
| 5880 | -upnp-std-pipe | C:\Users\admin\AppData\Local\Temp\69d6ef1af3f4cc2d81a8c8d573955def\usbredirectortechcsrv.exe | — | usbredirectortechcsrv.exe | |||||||||||
User: SYSTEM Company: SimplyCore LLC Integrity Level: SYSTEM Description: USB Redirector Technician Edition Customer Module service Exit code: 0 Version: 2,3,0,3330 Modules
| |||||||||||||||
| 5880 | C:\Windows\System32\CastSrv.exe CCastServerControlInteractiveUser -Embedding | C:\Windows\System32\CastSrv.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Casting protocol connection listener Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6188 | "C:\Users\admin\AppData\Local\Temp\usbredirector-customer-module.exe" | C:\Users\admin\AppData\Local\Temp\usbredirector-customer-module.exe | — | explorer.exe | |||||||||||
User: admin Company: SimplyCore LLC Integrity Level: MEDIUM Description: USB Redirector Technician Edition Customer Module Exit code: 3221226540 Version: 2,3,0,3330 Modules
| |||||||||||||||
| 6192 | C:\WINDOWS\winsxs\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe -Embedding | C:\Windows\WinSxS\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Modules Installer Worker Version: 10.0.19041.3989 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 098
Read events
1 092
Write events
6
Delete events
0
Modification events
| (PID) Process: | (5880) CastSrv.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\PlayToReceiver |
| Operation: | write | Name: | MiracastContainerID |
Value: {2B178017-A56C-47A4-9C90-755C77BAA2C0} | |||
| (PID) Process: | (6192) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SideBySide |
| Operation: | write | Name: | LastScavengingStarvationReport |
Value: 0A497BA122F9DA01 | |||
| (PID) Process: | (6192) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdHigh |
Value: 31127842 | |||
| (PID) Process: | (6192) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdLow |
Value: | |||
Executable files
9
Suspicious files
6
Text files
3
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4680 | usbredirector-customer-module.exe | C:\Users\admin\AppData\Local\Temp\69d6ef1af3f4cc2d81a8c8d573955def\usbredirectortechcsrv.exe | executable | |
MD5:0B38C2B7C79B4A002E70C56CBF573F0E | SHA256:3F9C4FB1498280C430652CDCB3EA2E56CB1A08D9744820BF0C6060A772F98D82 | |||
| 4680 | usbredirector-customer-module.exe | C:\Users\admin\AppData\Local\Temp\69d6ef1af3f4cc2d81a8c8d573955def\usb-redirector-customer-module-gui.exe | executable | |
MD5:31901C8409E9F2271D278EE04465E5BF | SHA256:55D9A1E4003A7BDAC5A879375EECEA470D26C0454CE08AAE3065AED4B73B1C80 | |||
| 4680 | usbredirector-customer-module.exe | C:\Users\admin\AppData\Local\Temp\__try__temporary__file__1220218 | binary | |
MD5:7E528A20B382515EAA9E4FB2B44481E9 | SHA256:9172D8C5D0487A8E2B8AA0DC7933F14D03F36188EA3B535A6366A60ED39240A5 | |||
| 5724 | usb-redirector-customer-module-gui.exe | C:\Users\admin\AppData\Local\Temp\{9ac61ebc-5ff6-4a42-90a4-9cc27d1a2375}\ttechusbd.cat | cat | |
MD5:E6756A675A4D1367EF9463736E948FEF | SHA256:586C551BBF12221C693DB578F959BF6C3A4816B645C86EDF089CCB83EC15E2B0 | |||
| 5724 | usb-redirector-customer-module-gui.exe | C:\Users\admin\AppData\Local\Temp\{9ac61ebc-5ff6-4a42-90a4-9cc27d1a2375}\SETA9D5.tmp | cat | |
MD5:E6756A675A4D1367EF9463736E948FEF | SHA256:586C551BBF12221C693DB578F959BF6C3A4816B645C86EDF089CCB83EC15E2B0 | |||
| 5724 | usb-redirector-customer-module-gui.exe | C:\Users\admin\AppData\Local\Temp\{9ac61ebc-5ff6-4a42-90a4-9cc27d1a2375}\ttechusbd.inf | binary | |
MD5:3E0BF576033C3D90CE0EE543940DEA64 | SHA256:852BCA64B94A158D23FFCFA1CD5EA2FE87F5ED51FD3EBC39021430A0058DEDFA | |||
| 4680 | usbredirector-customer-module.exe | C:\Users\admin\AppData\Local\Temp\69d6ef1af3f4cc2d81a8c8d573955def\amd64\ttechusbd.sys | executable | |
MD5:3CF990F46D8772F4E731CEB526AADC48 | SHA256:ED34E9AD250A49E1B93164784EAD56A284A89ABAF1CDDF3213D61C02A73A3469 | |||
| 5724 | usb-redirector-customer-module-gui.exe | C:\Users\admin\AppData\Local\Temp\{9ac61ebc-5ff6-4a42-90a4-9cc27d1a2375}\SETA9D6.tmp | binary | |
MD5:3E0BF576033C3D90CE0EE543940DEA64 | SHA256:852BCA64B94A158D23FFCFA1CD5EA2FE87F5ED51FD3EBC39021430A0058DEDFA | |||
| 5724 | usb-redirector-customer-module-gui.exe | C:\Users\admin\AppData\Local\Temp\{9ac61ebc-5ff6-4a42-90a4-9cc27d1a2375}\amd64\ttechusbd.sys | executable | |
MD5:3CF990F46D8772F4E731CEB526AADC48 | SHA256:ED34E9AD250A49E1B93164784EAD56A284A89ABAF1CDDF3213D61C02A73A3469 | |||
| 5724 | usb-redirector-customer-module-gui.exe | C:\Users\admin\AppData\Local\Temp\{9ac61ebc-5ff6-4a42-90a4-9cc27d1a2375}\amd64\SETA9E6.tmp | executable | |
MD5:3CF990F46D8772F4E731CEB526AADC48 | SHA256:ED34E9AD250A49E1B93164784EAD56A284A89ABAF1CDDF3213D61C02A73A3469 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
40
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5088 | SIHClient.exe | GET | 200 | 104.79.89.142:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5088 | SIHClient.exe | GET | 200 | 104.79.89.142:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6908 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQQX6Z6gAidtSefNc6DC0OInqPHDQQUD4BhHIIxYdUvKOeNRji0LOHG2eICEASGp3XRNgzfylEWBFW6KKc%3D | unknown | — | — | whitelisted |
1028 | SystemSettings.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
1028 | SystemSettings.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6320 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
6160 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2252 | usbredirectortechcsrv.exe | 185.161.211.222:47912 | cloud.incentivespro.com | Zemlyaniy Dmitro Leonidovich | NL | unknown |
2252 | usbredirectortechcsrv.exe | 185.161.211.222:32192 | cloud.incentivespro.com | — | — | unknown |
6160 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2252 | usbredirectortechcsrv.exe | 193.111.152.11:32128 | — | — | — | unknown |
5336 | SearchApp.exe | 204.79.197.222:443 | fp.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
cloud.incentivespro.com |
| unknown |
settings-win.data.microsoft.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
www.bing.com |
| whitelisted |
rum8.perf.linkedin.com |
| whitelisted |
bx-ring.msedge.net |
| unknown |