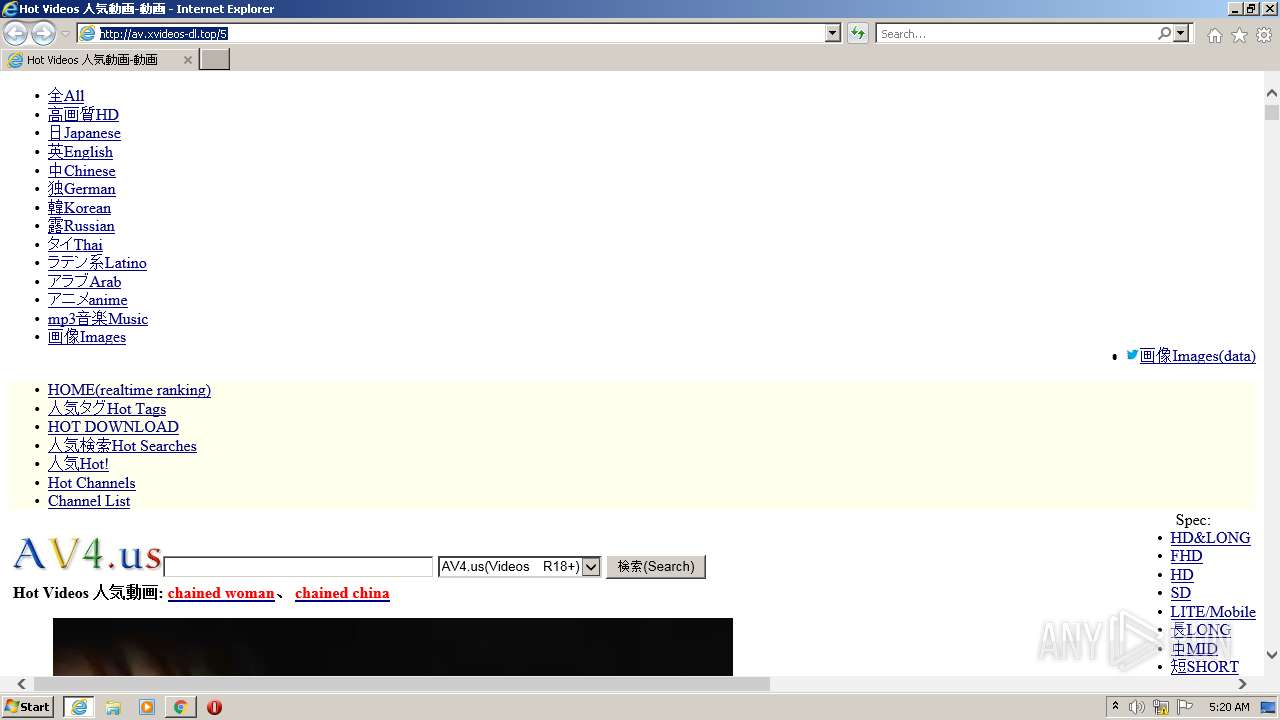
| URL: | http://av.xvideos-dl.top/5 |
| Full analysis: | https://app.any.run/tasks/539d7888-292a-4dd7-936d-63a533908d20 |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2022, 04:19:43 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 7AB35751EA61EA769C9D897EF068678F |
| SHA1: | 54D257FF125A7B2CBF5B36090FAA7B23F0FB116B |
| SHA256: | CED57CEC9906AAE293300E60DE43283686B2EAEFE96B43D007F9E08E7A8F7501 |
| SSDEEP: | 3:N1Kfp3KQ:CNKQ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 1428)
INFO
Checks supported languages
- iexplore.exe (PID: 1164)
- iexplore.exe (PID: 1428)
Reads the computer name
- iexplore.exe (PID: 1164)
- iexplore.exe (PID: 1428)
Application launched itself
- iexplore.exe (PID: 1164)
Reads internet explorer settings
- iexplore.exe (PID: 1428)
Changes internet zones settings
- iexplore.exe (PID: 1164)
Reads settings of System Certificates
- iexplore.exe (PID: 1428)
Checks Windows Trust Settings
- iexplore.exe (PID: 1428)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
36
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1164 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://av.xvideos-dl.top/5" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1428 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1164 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2180 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 86.0.4240.198 | |||||||||||||||
Total events
61 526
Read events
61 463
Write events
63
Delete events
0
Modification events
| (PID) Process: | (1164) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (1164) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 764796544 | |||
| (PID) Process: | (1164) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30959836 | |||
| (PID) Process: | (1164) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (1164) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30959836 | |||
| (PID) Process: | (1164) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1164) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1164) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1164) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1164) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
0
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1428 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\5[1].htm | html | |
MD5:D9BD8300161443AD0DF771087CA4D554 | SHA256:BC5AE03297B76F7A5272D0E89714BB26D38619F50B06E87BF81D910B15197674 | |||
| 1428 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\777-young-clipwatching-14b2t32cgq3t[1].jpg | image | |
MD5:07515B194176CF80121013B58A9AF389 | SHA256:053425D2EBD2836B49F22B292C5AA2AB7F9B80C3E11B552F334FC90157612267 | |||
| 1428 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\AV4.us[1].jpg | image | |
MD5:EDFE007A6E5B3D268B2528F564B60B43 | SHA256:BF5BB657F5E788AF0C02B9B437D3F15BEC91E27175E5A654E3D431FB6D063390 | |||
| 1428 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\361314-1[1].jpg | text | |
MD5:FDA44910DEB1A460BE4AC5D56D61D837 | SHA256:933B971C6388D594A23FA1559825DB5BEC8ADE2DB1240AA8FC9D0C684949E8C9 | |||
| 1428 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\525951-1[1].jpg | text | |
MD5:FDA44910DEB1A460BE4AC5D56D61D837 | SHA256:933B971C6388D594A23FA1559825DB5BEC8ADE2DB1240AA8FC9D0C684949E8C9 | |||
| 1428 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\467467-1[1].jpg | text | |
MD5:FDA44910DEB1A460BE4AC5D56D61D837 | SHA256:933B971C6388D594A23FA1559825DB5BEC8ADE2DB1240AA8FC9D0C684949E8C9 | |||
| 1428 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\392674-1[1].jpg | text | |
MD5:FDA44910DEB1A460BE4AC5D56D61D837 | SHA256:933B971C6388D594A23FA1559825DB5BEC8ADE2DB1240AA8FC9D0C684949E8C9 | |||
| 1428 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\559893-1[1].jpg | text | |
MD5:FDA44910DEB1A460BE4AC5D56D61D837 | SHA256:933B971C6388D594A23FA1559825DB5BEC8ADE2DB1240AA8FC9D0C684949E8C9 | |||
| 1428 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\156429-1[1].jpg | text | |
MD5:FDA44910DEB1A460BE4AC5D56D61D837 | SHA256:933B971C6388D594A23FA1559825DB5BEC8ADE2DB1240AA8FC9D0C684949E8C9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
159
TCP/UDP connections
261
DNS requests
98
Threats
19
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1428 | iexplore.exe | GET | 301 | 104.27.205.87:80 | http://static.thisav.com/images/videothumbs/467467-1.jpg | US | — | — | suspicious |
1428 | iexplore.exe | GET | 301 | 104.27.205.87:80 | http://static.thisav.com/images/videothumbs/156429-1.jpg | US | — | — | suspicious |
1428 | iexplore.exe | GET | 301 | 104.27.205.87:80 | http://static.thisav.com/images/videothumbs/361314-1.jpg | US | — | — | suspicious |
1428 | iexplore.exe | GET | 301 | 104.27.205.87:80 | http://static.thisav.com/images/videothumbs/559893-1.jpg | US | — | — | suspicious |
1428 | iexplore.exe | GET | — | 208.86.34.87:80 | http://siwazywcdn.com/upload/vod/20210724-1/e947adfb290116865fa06ed88a8ea1bd.jpg | US | — | — | unknown |
1428 | iexplore.exe | GET | 301 | 104.27.205.87:80 | http://static.thisav.com/images/videothumbs/392674-1.jpg | US | — | — | suspicious |
1428 | iexplore.exe | GET | 301 | 104.27.205.87:80 | http://static.thisav.com/images/videothumbs/525951-1.jpg | US | — | — | suspicious |
1428 | iexplore.exe | GET | — | 208.86.34.87:80 | http://siwazywcdn.com/upload/vod/20210724-1/e947adfb290116865fa06ed88a8ea1bd.jpg | US | — | — | unknown |
1428 | iexplore.exe | GET | 200 | 103.124.106.254:80 | http://av.xvideos-dl.top/5 | unknown | html | 10.8 Kb | suspicious |
1428 | iexplore.exe | GET | 200 | 66.254.122.16:80 | http://cdne-pics.youjizz.com/6/7/a/67a9c9c0f8d7895cb3ad288c20aac1b41483632321-480-320-466-h264.mp4-11.jpg?revnum=1 | US | image | 15.4 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1428 | iexplore.exe | 103.124.106.254:80 | av.xvideos-dl.top | — | — | suspicious |
1428 | iexplore.exe | 143.47.187.250:443 | yewtu.be | — | IE | suspicious |
1428 | iexplore.exe | 104.27.205.87:80 | static.thisav.com | Cloudflare Inc | US | unknown |
1428 | iexplore.exe | 199.232.136.159:443 | pbs.twimg.com | — | US | unknown |
1428 | iexplore.exe | 104.244.42.1:443 | twitter.com | Twitter Inc. | US | malicious |
1428 | iexplore.exe | 172.67.140.175:80 | cacrip.nakadashi.pw | — | US | suspicious |
1428 | iexplore.exe | 104.21.233.245:443 | js.gazo.space | Cloudflare Inc | US | unknown |
1428 | iexplore.exe | 45.89.209.131:443 | pic.kankandie.com | — | — | unknown |
1428 | iexplore.exe | 104.21.233.246:443 | js.gazo.space | Cloudflare Inc | US | suspicious |
1428 | iexplore.exe | 104.21.235.78:443 | mobifcuk.com | Cloudflare Inc | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
av.xvideos-dl.top |
| suspicious |
js.gazo.space |
| whitelisted |
jsjs.gazo.space |
| suspicious |
twitter.com |
| whitelisted |
cacrip.nakadashi.pw |
| suspicious |
pbs.twimg.com |
| whitelisted |
pic.kankandie.com |
| unknown |
ak21727.com |
| unknown |
static.thisav.com |
| suspicious |
yewtu.be |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
— | — | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
— | — | Potentially Bad Traffic | ET DNS Query to a *.pw domain - Likely Hostile |
— | — | Potentially Bad Traffic | ET INFO HTTP Request to a *.pw domain |
— | — | Not Suspicious Traffic | ET POLICY OpenSSL Demo CA - Internet Widgits Pty (O) |
— | — | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
— | — | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
— | — | Not Suspicious Traffic | ET POLICY OpenSSL Demo CA - Internet Widgits Pty (O) |
— | — | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
— | — | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |