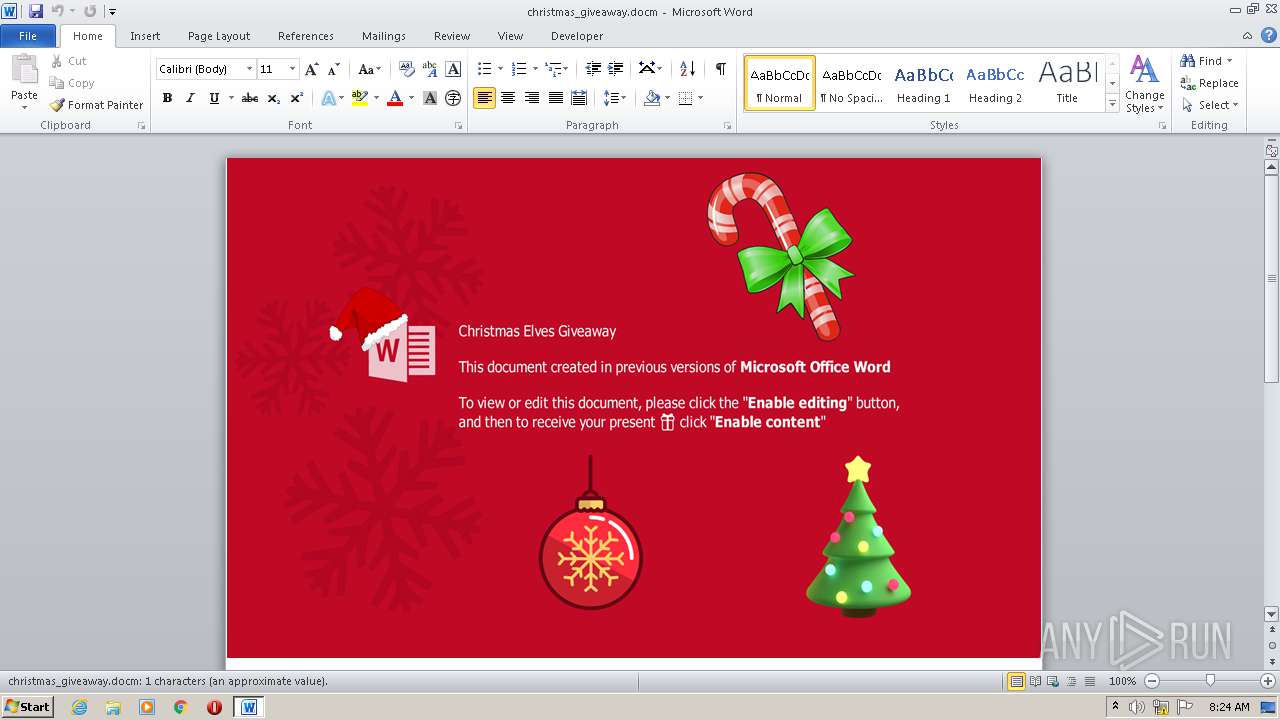
| File name: | christmas_giveaway.docm |
| Full analysis: | https://app.any.run/tasks/2d00c601-cb6b-4a3a-93e8-965a013c70c2 |
| Verdict: | Malicious activity |
| Analysis date: | December 06, 2021, 08:24:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | 00CBA6C1746444C8B796049ED7638A88 |
| SHA1: | 4F42E754053A6D11EA2ADAEECEFC6BE8346D493B |
| SHA256: | CED24054149DF964B66BA695842E3055E2200232C6F1676CE820F81FD26FB9D6 |
| SSDEEP: | 12288:Oype66D9Bgz6g1nVbXcB3q/emfz1bjk+A9CLVYWQ+DJH7WUeWtvNF:O4n6Dfgv19cq/emfljkDCyj+9heWzF |
MALICIOUS
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 3636)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 3636)
SUSPICIOUS
Checks supported languages
- cmd.exe (PID: 2920)
- cmd.exe (PID: 3344)
- chcp.com (PID: 3804)
- cscript.exe (PID: 3992)
- powershell.exe (PID: 468)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 468)
Reads the computer name
- cscript.exe (PID: 3992)
- powershell.exe (PID: 468)
Starts application with an unusual extension
- cmd.exe (PID: 2920)
Executes PowerShell scripts
- cscript.exe (PID: 3992)
Executes scripts
- cmd.exe (PID: 2920)
Reads Environment values
- powershell.exe (PID: 468)
INFO
Checks supported languages
- WINWORD.EXE (PID: 3636)
- PING.EXE (PID: 2376)
Reads the computer name
- WINWORD.EXE (PID: 3636)
- PING.EXE (PID: 2376)
Creates files in the user directory
- WINWORD.EXE (PID: 3636)
Checks Windows Trust Settings
- cscript.exe (PID: 3992)
- powershell.exe (PID: 468)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3636)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docm | | | Word Microsoft Office Open XML Format document (with Macro) (53.6) |
|---|---|---|
| .docx | | | Word Microsoft Office Open XML Format document (24.2) |
| .zip | | | Open Packaging Conventions container (18) |
| .zip | | | ZIP compressed archive (4.1) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0x3f450766 |
| ZipCompressedSize: | 399 |
| ZipUncompressedSize: | 1503 |
| ZipFileName: | [Content_Types].xml |
XMP
| Title: | - |
|---|---|
| Subject: | - |
| Creator: | - |
| Description: | - |
XML
| Keywords: | - |
|---|---|
| LastModifiedBy: | - |
| RevisionNumber: | 1 |
| CreateDate: | 2021:11:30 23:18:00Z |
| ModifyDate: | 2021:11:30 23:19:00Z |
| Template: | Normal.dotm |
| TotalEditTime: | - |
| Pages: | 1 |
| Words: | - |
| Characters: | 1 |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 1 |
| Paragraphs: | 1 |
| ScaleCrop: | No |
| Company: | - |
| LinksUpToDate: | No |
| CharactersWithSpaces: | 1 |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 16 |
Total processes
44
Monitored processes
7
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 468 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -noexit -ExecutionPolicy bypass -noprofile -file C:\Users\admin\AppData\Local\Temp\adobeacd-update.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2376 | ping 1.1.2.2 -n 2 | C:\Windows\system32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2920 | C:\Windows\system32\cmd.exe /c c:\Users\admin\AppData\Local\Temp\adobeacd-update.bat | C:\Windows\system32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3344 | "C:\Windows\system32\cmd.exe" /c c:\Users\admin\AppData\Local\Temp\444.exe | C:\Windows\system32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3636 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\christmas_giveaway.docm" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3804 | chcp 1251 | C:\Windows\system32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3992 | cscript.exe "c:\Users\admin\AppData\Local\Temp\adobeacd-update.vbs" | C:\Windows\system32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft � Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
Total events
4 441
Read events
3 839
Write events
528
Delete events
74
Modification events
| (PID) Process: | (3636) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 1d? |
Value: 31643F00340E0000010000000000000000000000 | |||
| (PID) Process: | (3636) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3636) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3636) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3636) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3636) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3636) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3636) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3636) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3636) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
3
Text files
3
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3636 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR5011.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3636 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3636 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$ristmas_giveaway.docm | pgc | |
MD5:— | SHA256:— | |||
| 468 | powershell.exe | C:\Users\admin\AppData\Local\Temp\arnzwa1y.r5q.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 468 | powershell.exe | C:\Users\admin\AppData\Local\Temp\czwavngg.03f.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3636 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\adobeacd-update.bat | text | |
MD5:6CCDA348CEDD7C1A015B050CC5293EC7 | SHA256:6577D4EC489FBB21ED1F8D6957FF3279D3BF8587C9F348734DA1BB55E761744F | |||
| 468 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:1068BF0B9B98C206F587A7DB05F6DD06 | SHA256:534478EDAFC5087DAA3749624454988B1F7DF923BF1A0A9E28C5F97C3308CFDB | |||
| 3636 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\adobeacd-update.vbs | text | |
MD5:8CD65CBF2BA5358AF189AEE6B9181531 | SHA256:320FCAA30E58756A5ADA91463E2A5D695A312FDB0692592F8C48F9AD9512CDAE | |||
| 3636 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\adobeacd-update.ps1 | text | |
MD5:BEF90BAFC4182662A6062D5359E117F2 | SHA256:859BDAA155A5812C719F7624882F797898A346F0AA0BDFEA7D97A958C8DA0A37 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
3
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
468 | powershell.exe | 211.125.116.200:80 | hiro-wish.com | Kurashiki Cable TV | JP | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
hiro-wish.com |
| malicious |
dns.msftncsi.com |
| shared |