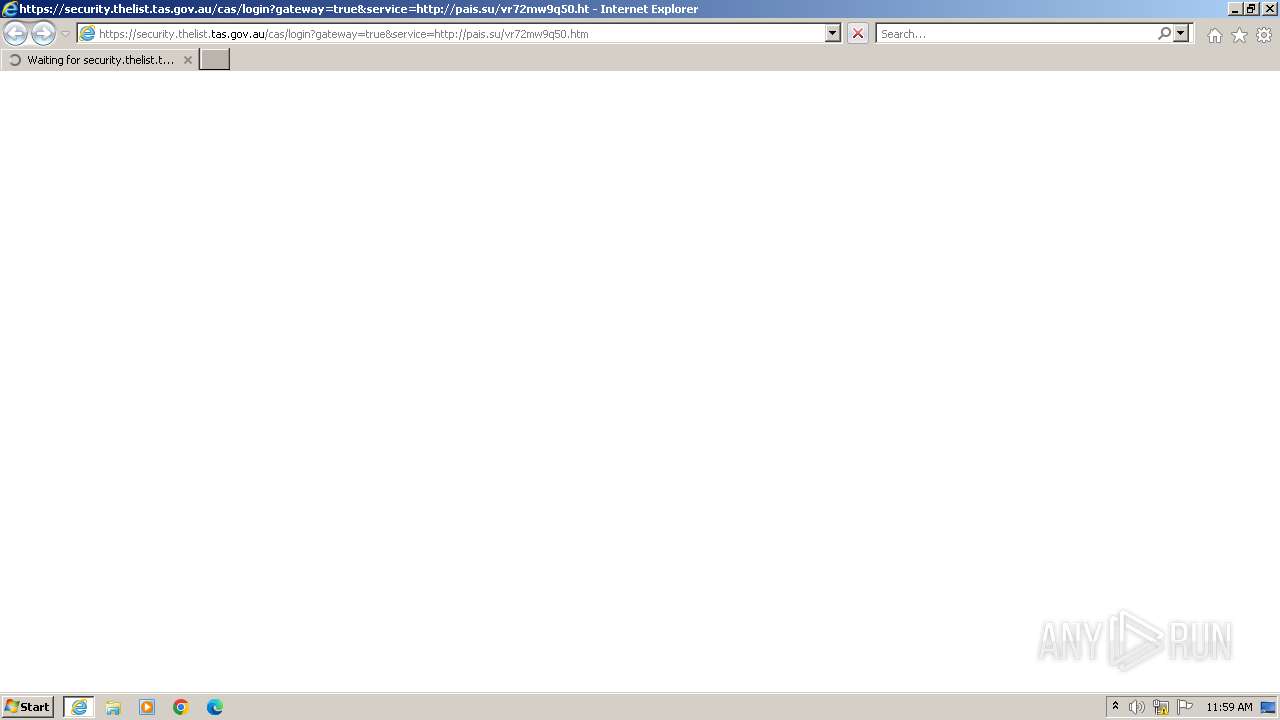
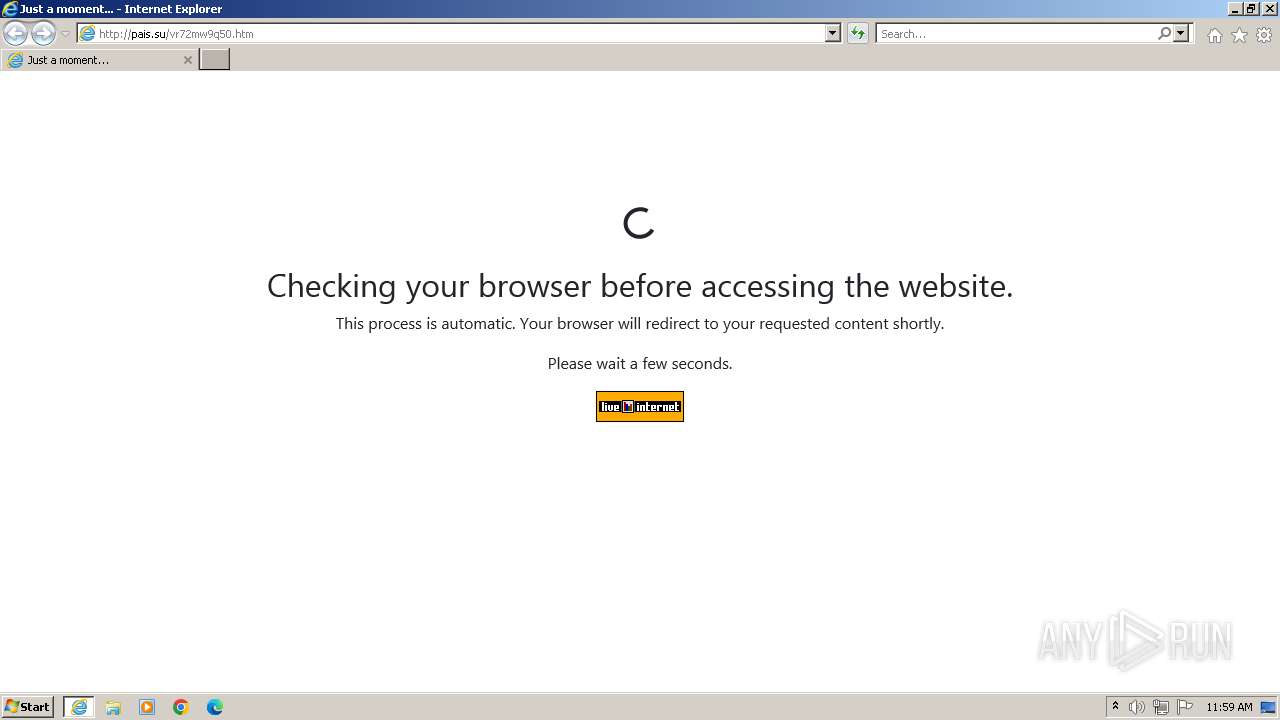
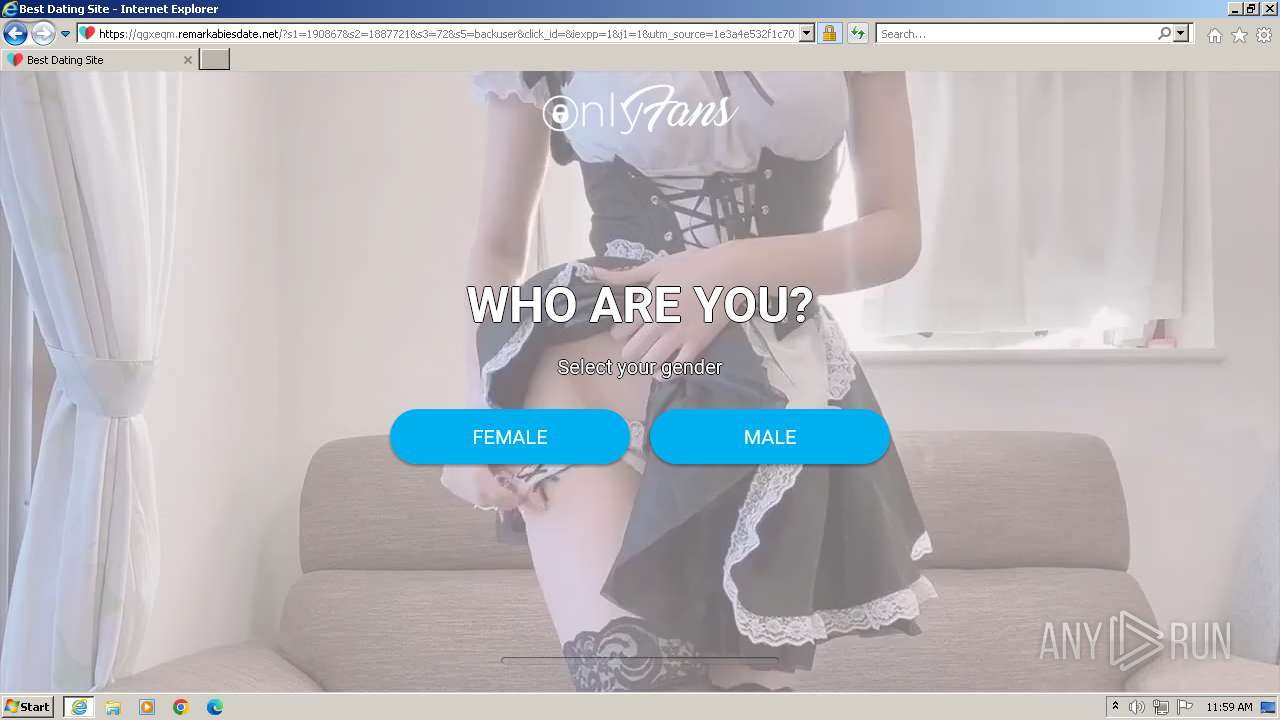
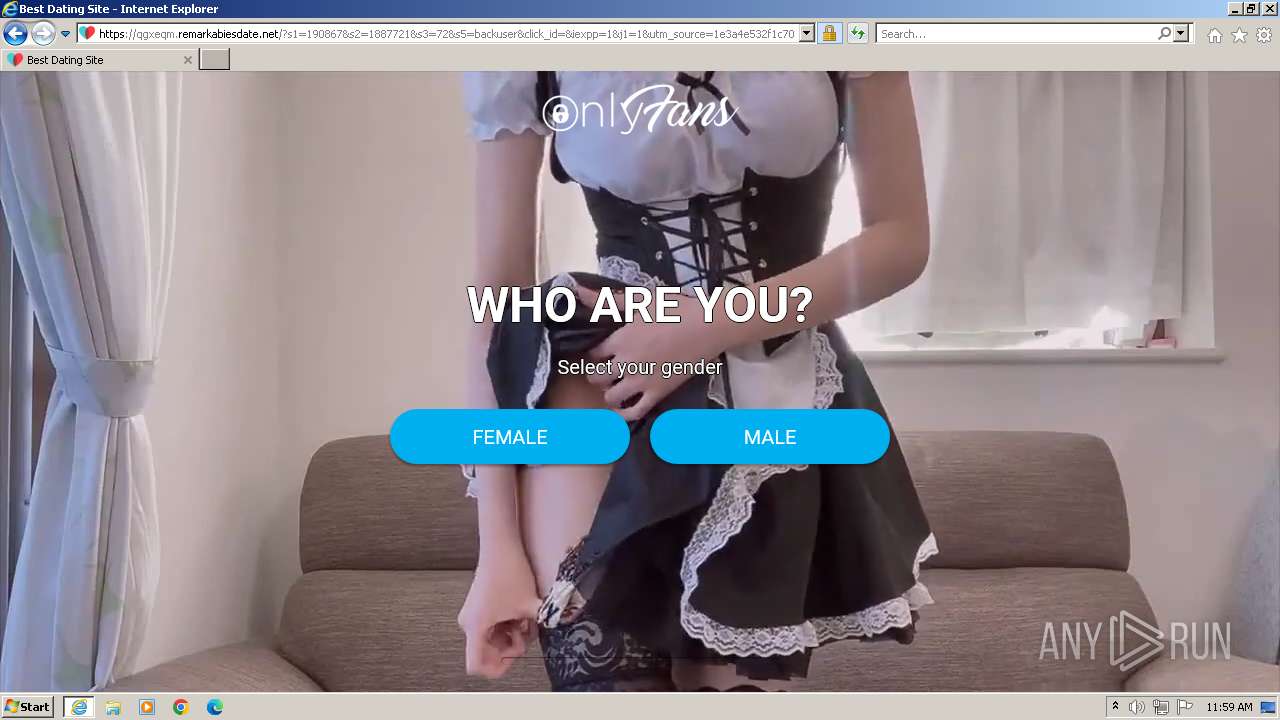
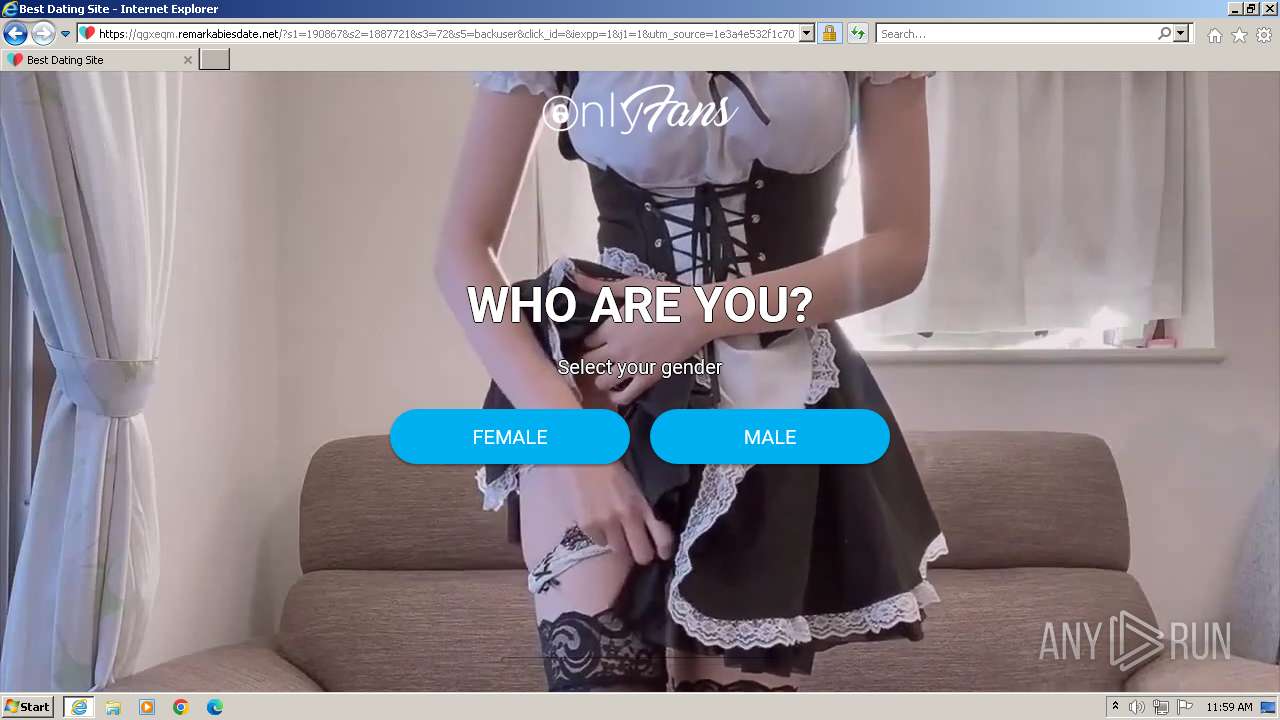
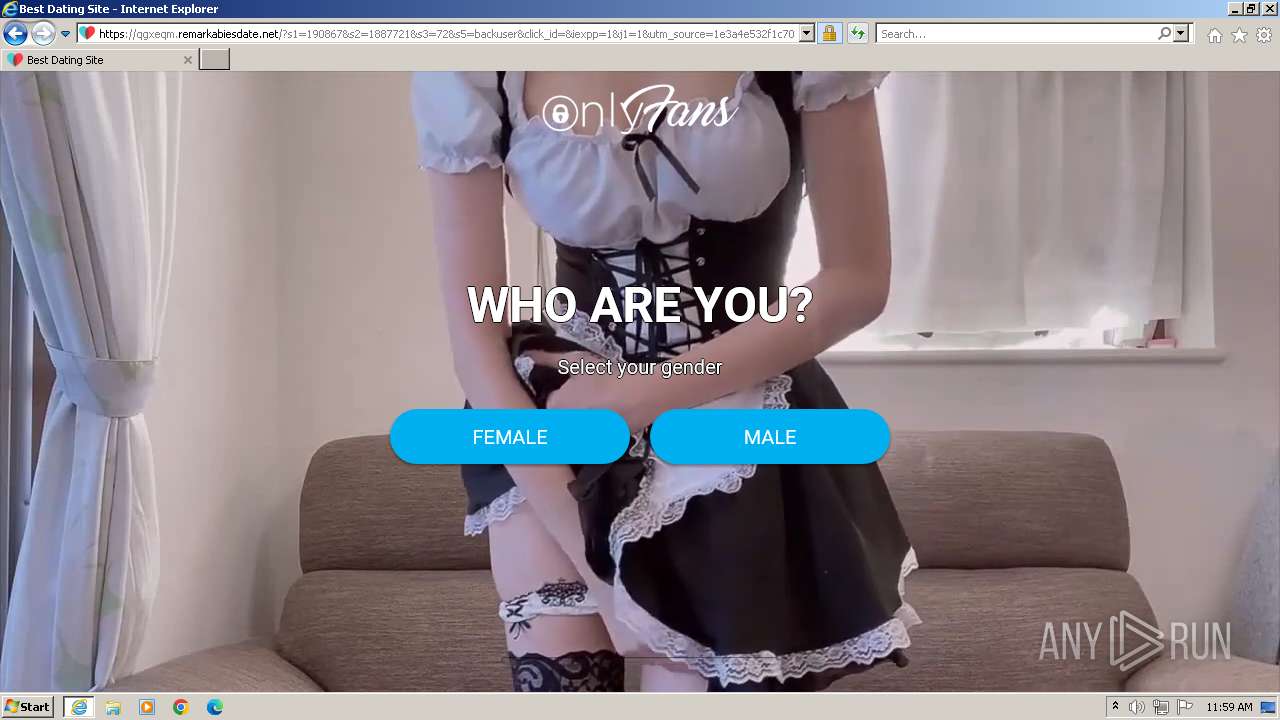
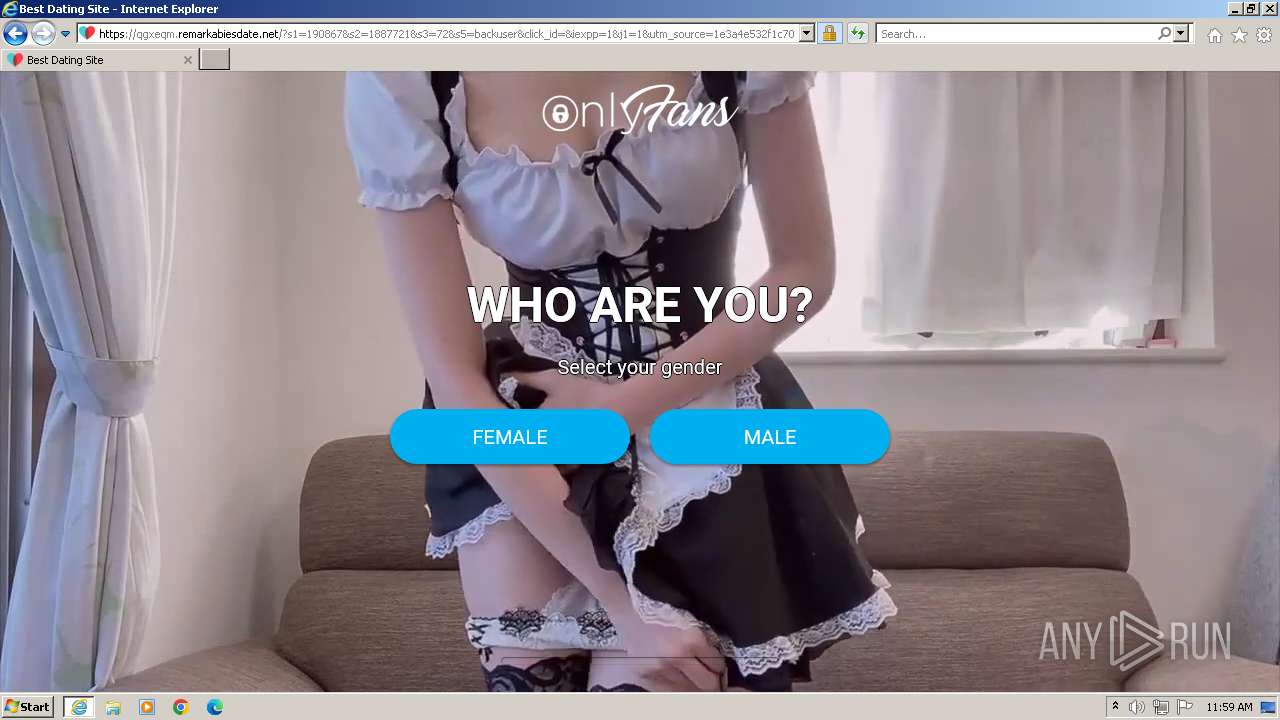
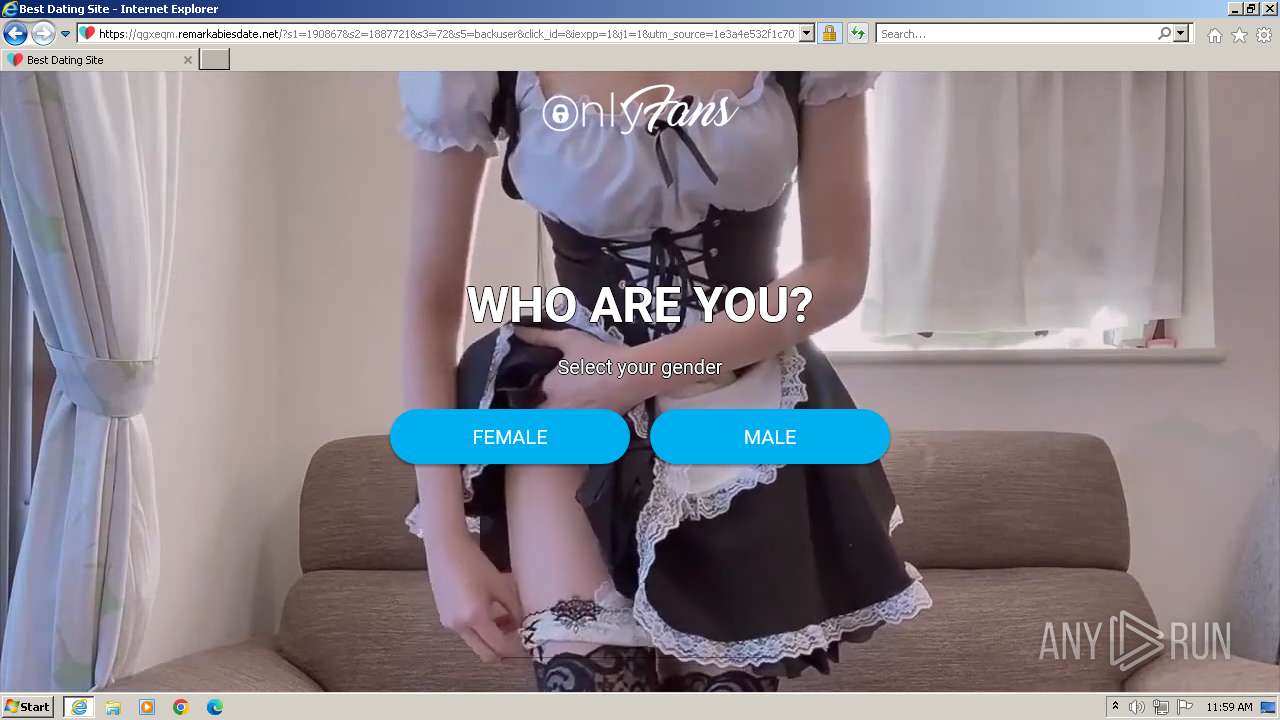
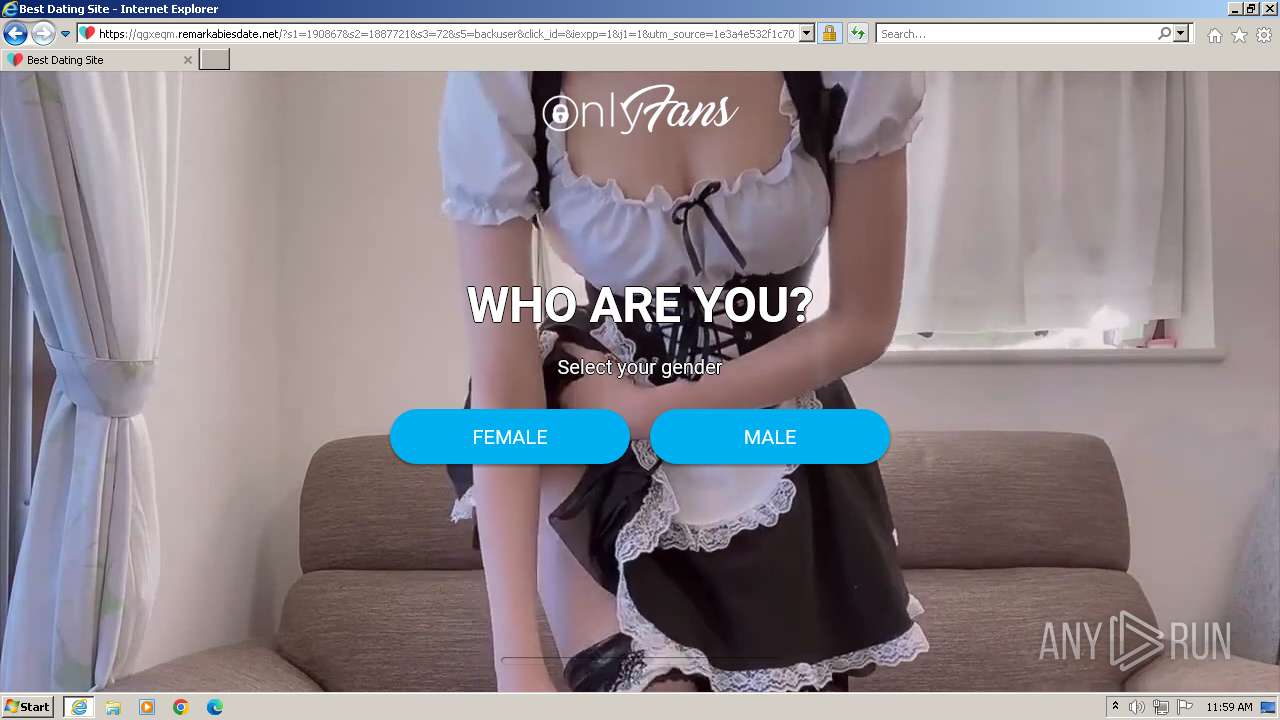
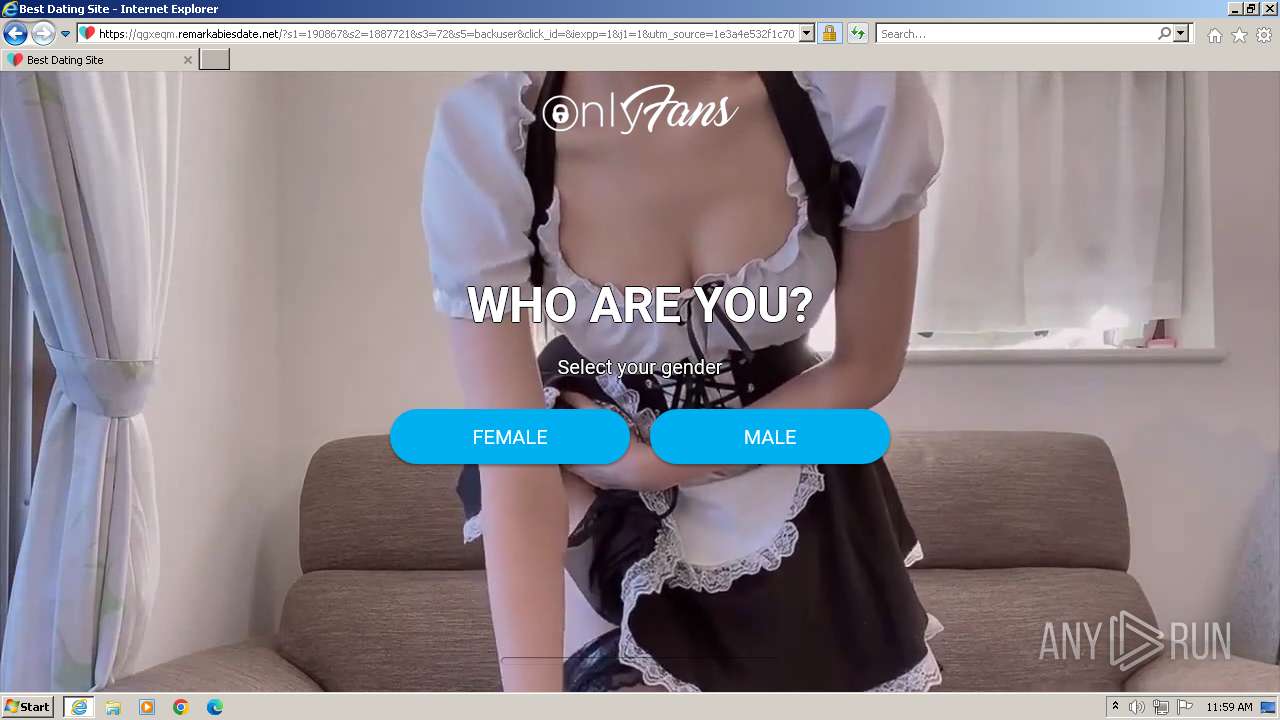
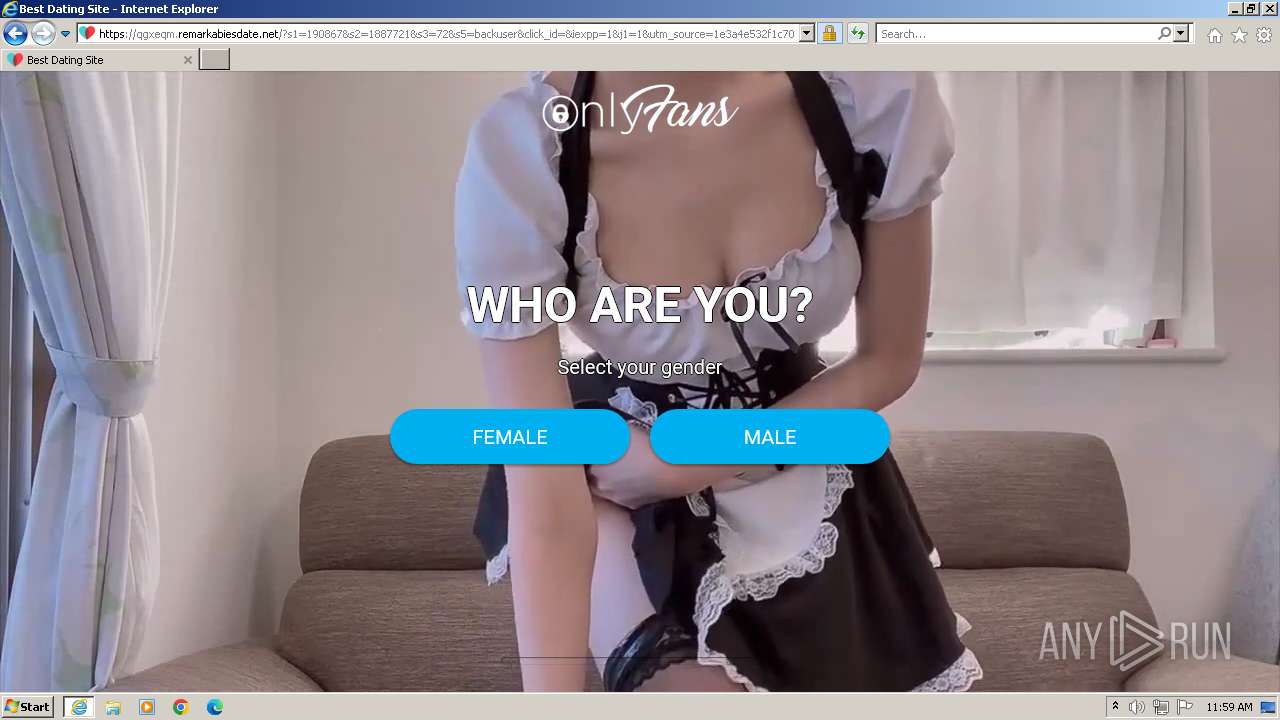
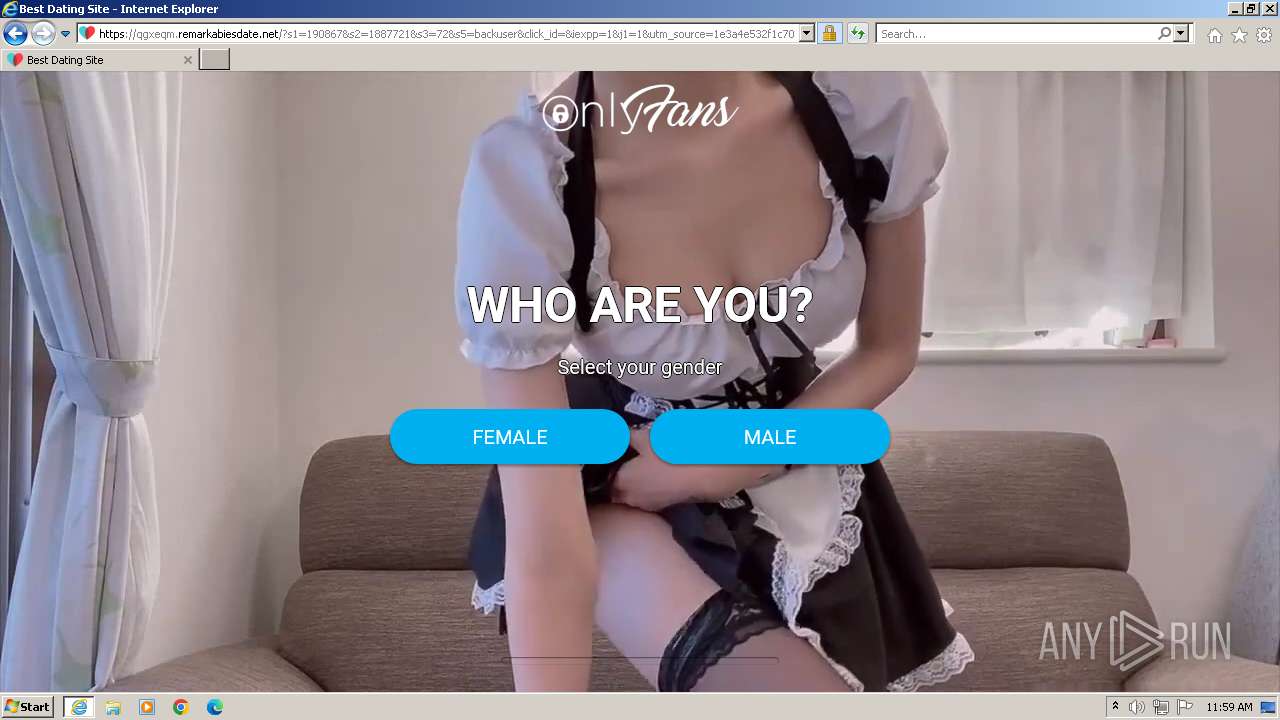
| URL: | https://security.thelist.tas.gov.au/cas/login?gateway=true&service=http://pais.su/vr72mw9q50.htm |
| Full analysis: | https://app.any.run/tasks/3874beea-c4bd-4cfd-859c-332de55f9d9a |
| Verdict: | Malicious activity |
| Analysis date: | November 09, 2023, 11:59:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| SHA1: | C373A1B1713BDCA757ECA80D895C903368F28053 |
| SHA256: | CEC0F7DCAD1515C085CEF4CDFA73227D4F3CEC4B9FA9B934387E63E7A972DD43 |
| SSDEEP: | 3:N8N3QlRl/2IlGNJXRZAbXAk3EMMWf2NCu:2ZQlRl/HGbXRZAbxlMa2d |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Reads the computer name
- wmpnscfg.exe (PID: 3488)
Application launched itself
- iexplore.exe (PID: 3416)
Checks supported languages
- wmpnscfg.exe (PID: 3488)
Manual execution by a user
- wmpnscfg.exe (PID: 3488)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 3488)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
39
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3216 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3416 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3416 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://security.thelist.tas.gov.au/cas/login?gateway=true&service=http://pais.su/vr72mw9q50.htm" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3488 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
19 394
Read events
19 335
Write events
54
Delete events
5
Modification events
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
40
Text files
43
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3216 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:76397A39606827DBC2AB11B4EE3BC19C | SHA256:9975F3548DC5D127FECCA135474E1AFC14F392DA6D544606198C88EFA57EEF48 | |||
| 3216 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B3D66B8F592816E4D56A9F94798E8770 | binary | |
MD5:F611699CDB31993C4D883C8C970F827F | SHA256:50060DAC4E04884E4542CD9BF0DF27C80BD325601FC40464175C5B4CCBCF3004 | |||
| 3216 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 3216 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | binary | |
MD5:E5B7592F0C9812B9640AD5C97E867091 | SHA256:E625667213E66A4A91DBF64F48246EF6A3D1D1C7867FB8392AE560F65D057C03 | |||
| 3216 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B3D66B8F592816E4D56A9F94798E8770 | binary | |
MD5:13F79D1C0339B3BCA52B067D00A56FAF | SHA256:EAC5CBEEC9B0315682C73D87E19D21EA7A54B73E984300B1488A2C8BA92FBA23 | |||
| 3216 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\VDL98GLH.txt | text | |
MD5:D9FFE9517C24C29EED645E945AA7E6A6 | SHA256:3B3F9FC4B2A4C410106E1B742324C03C91EADE763AB7327B3A5B5F3F28088902 | |||
| 3216 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\38WRF5N8.txt | text | |
MD5:8B25A6515656471AD65D816A5E4C04E7 | SHA256:32CB6551946BAE09B1DCBBA0963DBF9198208C6F10DA6101616657C7649E871B | |||
| 3216 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\07CEF2F654E3ED6050FFC9B6EB844250_34D61B4A2A4AE0D3DDAB879224BCA77B | binary | |
MD5:00F73E502F5327988926DDBD88021452 | SHA256:24C6A597A3531966C043494F2D7D2565EE155AEEB9FE705A067F67D9D99EBACF | |||
| 3216 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | binary | |
MD5:8121F9891EE6B85BADA16947785DA332 | SHA256:76CE48D70D1C35276BFB63843517A14AF4C4CC6B0201964E34C8BBAE0090CE85 | |||
| 3216 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\07CEF2F654E3ED6050FFC9B6EB844250_34D61B4A2A4AE0D3DDAB879224BCA77B | binary | |
MD5:E9B5CC0BEA2E134DD2F4E22D5F0B0ADF | SHA256:32AEE11901762A0EDDB7C692A329EB83E8EDFB69212616768A843572E5123EB4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
22
TCP/UDP connections
42
DNS requests
23
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3216 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | binary | 1.42 Kb | unknown |
3416 | iexplore.exe | GET | 200 | 185.238.171.72:80 | http://pais.su/favicon.ico | unknown | html | 6.00 Kb | unknown |
3216 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?24ee352ddd3d4dea | unknown | compressed | 4.66 Kb | unknown |
3216 | iexplore.exe | GET | 200 | 23.201.254.55:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
3216 | iexplore.exe | GET | 200 | 67.27.235.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?4a555302fa74f79f | unknown | compressed | 61.6 Kb | unknown |
3216 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://ocsp.globalsign.com/alphasslcasha256g4/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBSPdwLcDiHQXlVfp8h37hrpMerTggQUT8usqMLvq92Db2u%2Fzpg9XFgldhUCDF8UEFuKOsZS4YsffA%3D%3D | unknown | binary | 1.40 Kb | unknown |
3216 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?55c2195bf7146c10 | unknown | compressed | 61.6 Kb | unknown |
3216 | iexplore.exe | GET | 200 | 67.27.235.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d6bb2ad0af14907d | unknown | compressed | 4.66 Kb | unknown |
3216 | iexplore.exe | GET | 200 | 2.16.202.121:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgQ6C7qlIy8RfCLZmp4eOFaQCA%3D%3D | unknown | binary | 503 b | unknown |
3216 | iexplore.exe | GET | 200 | 172.64.149.23:80 | http://zerossl.ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBQILj%2F5BYz%2BinwYvRPv3x0WYHB6awQUyNl4aKLZGWjVPXLeXwo%2B3LWGhqYCEQCT1sTTIPJzidpW808lzd83 | unknown | binary | 728 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1080 | svchost.exe | 192.168.100.2:53 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | iexplore.exe | 147.109.255.201:443 | — | Networking Tasmania | AU | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3216 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
3216 | iexplore.exe | 67.27.235.126:80 | ctldl.windowsupdate.com | LEVEL3 | US | unknown |
3216 | iexplore.exe | 104.18.38.233:80 | ocsp.comodoca.com | CLOUDFLARENET | — | shared |
3216 | iexplore.exe | 172.64.149.23:80 | ocsp.comodoca.com | CLOUDFLARENET | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
security.thelist.tas.gov.au |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
zerossl.ocsp.sectigo.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
pais.su |
| malicious |
stackpath.bootstrapcdn.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3216 | iexplore.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
3216 | iexplore.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .su TLD (Soviet Union) Often Malware Related |
3216 | iexplore.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
3416 | iexplore.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
3216 | iexplore.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
3216 | iexplore.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |