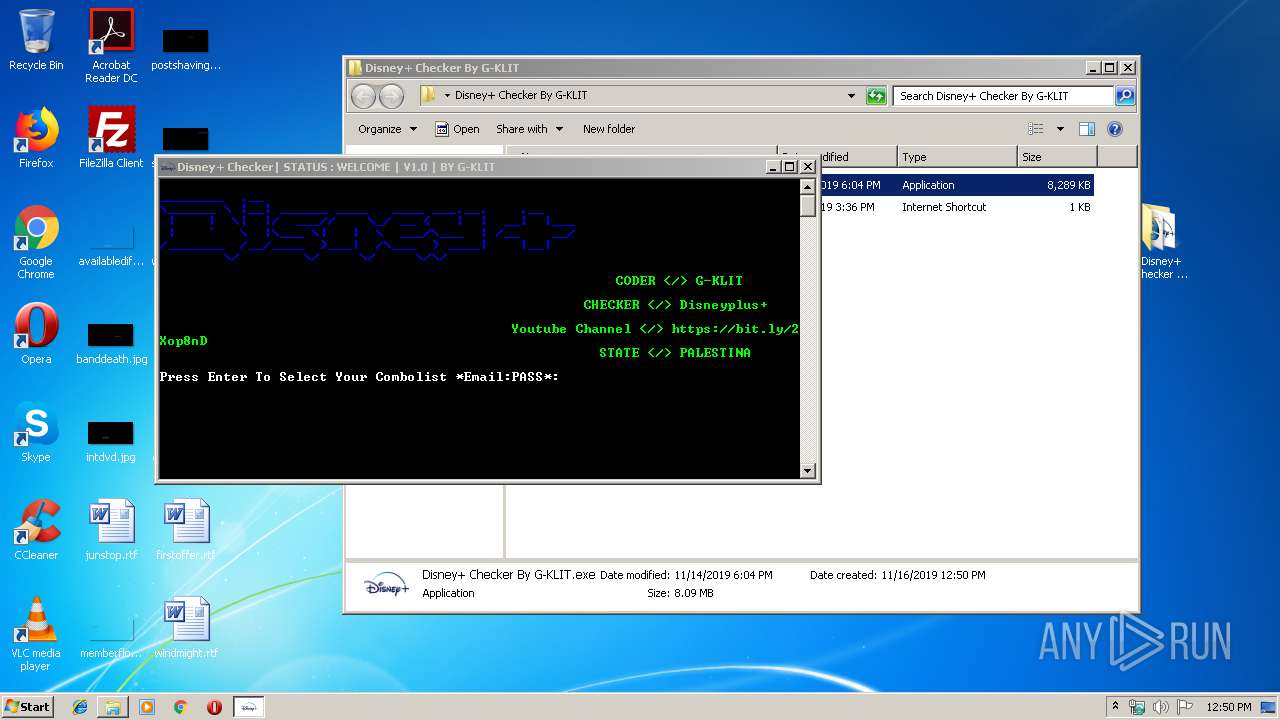
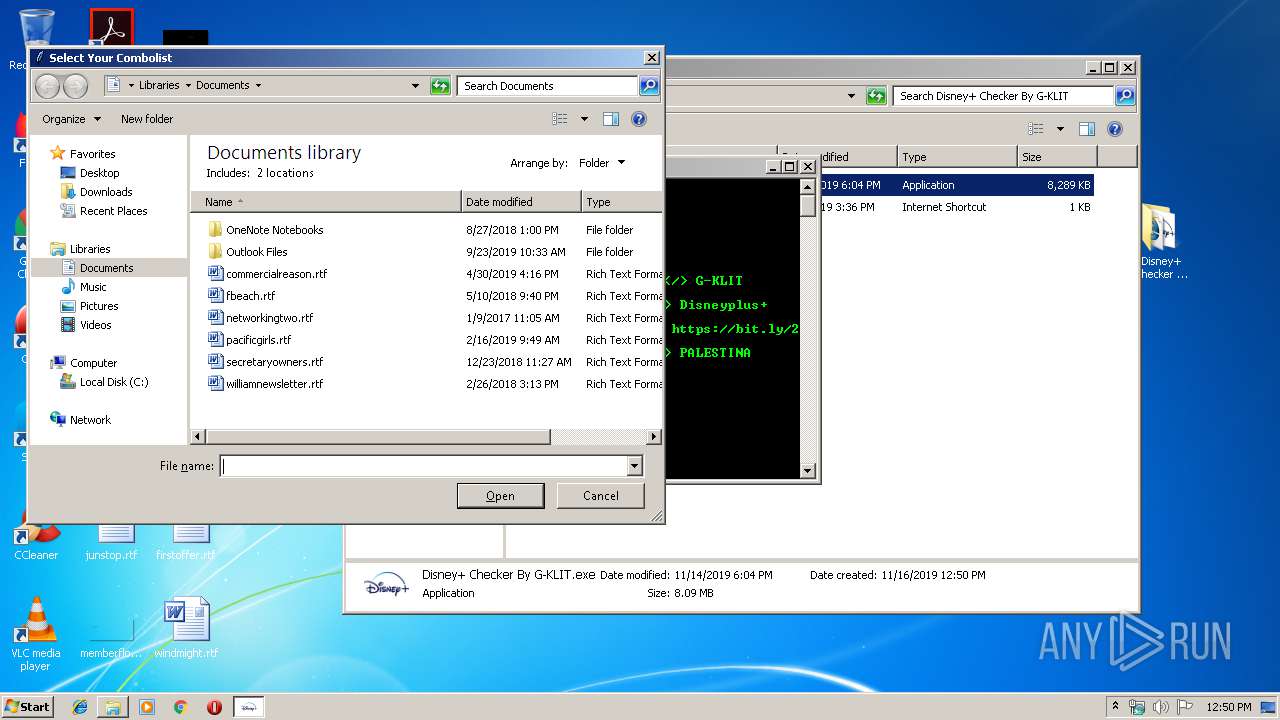
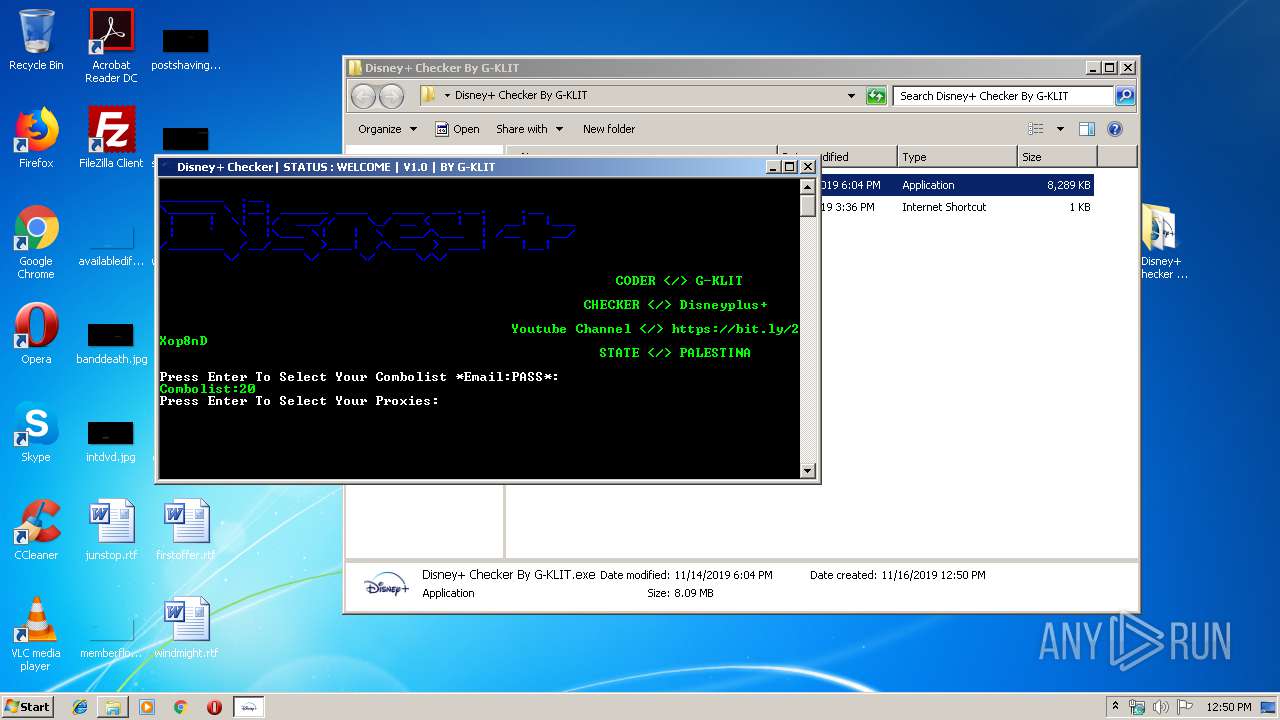
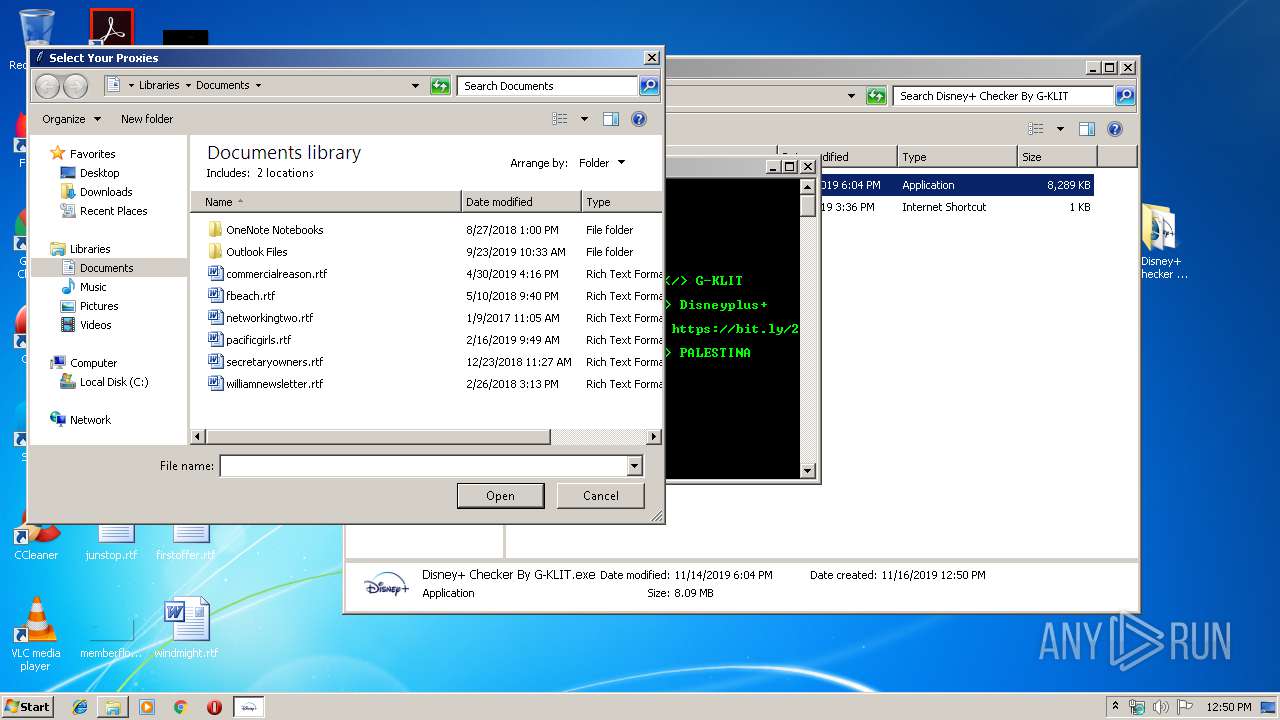
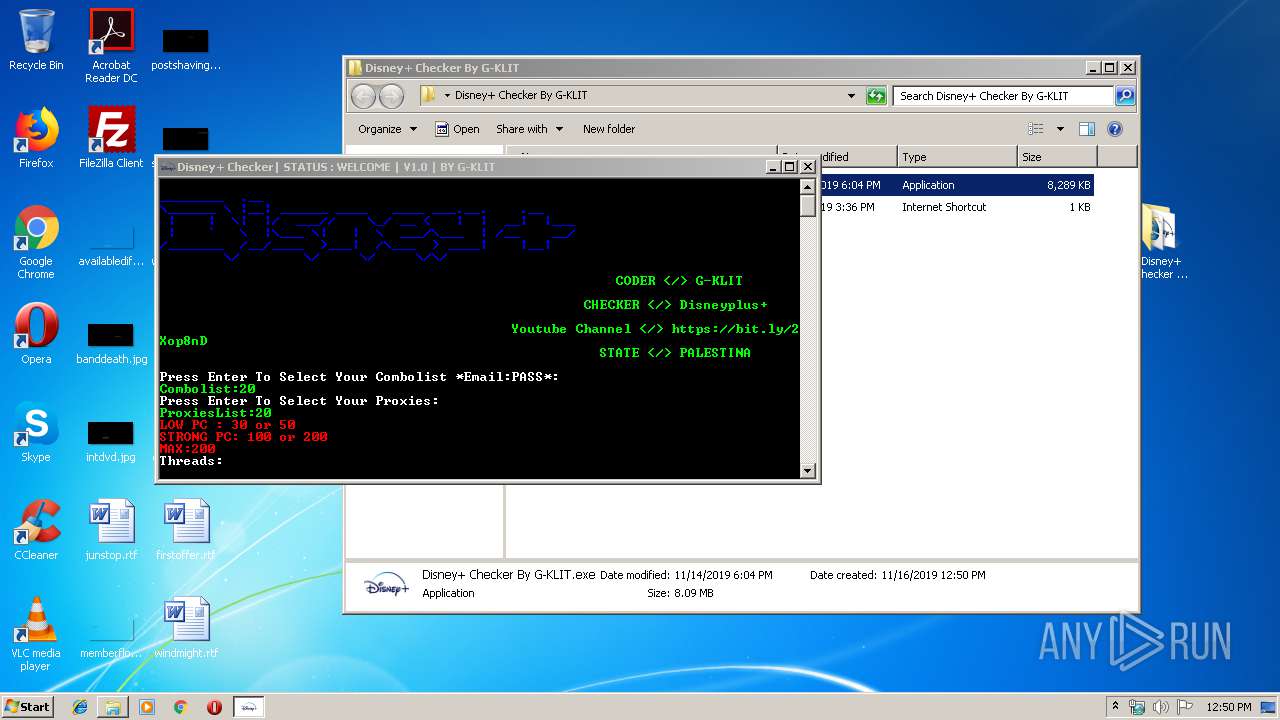
| File name: | Disney+ Checker By G-KLIT.rar |
| Full analysis: | https://app.any.run/tasks/5876b25a-e2f2-4414-a923-efa81ce9ad9e |
| Verdict: | Malicious activity |
| Analysis date: | November 16, 2019, 12:50:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 83DFC5FEA42F82C0C1A51A7BE8E6FB35 |
| SHA1: | 8D4D21A94F6EF2F7FF9BC105875F86ECB548CCC2 |
| SHA256: | CEB47DC2962F1FEE9AA971BCDEF2F5AF5F6B570372371279E8CB5830F24E6BA8 |
| SSDEEP: | 196608:Th7DNutBY1p3hYSk0nN7FkGOEH1SZ+3iGnq/sefsB/:T5hutgHkGUTwRte2/ |
MALICIOUS
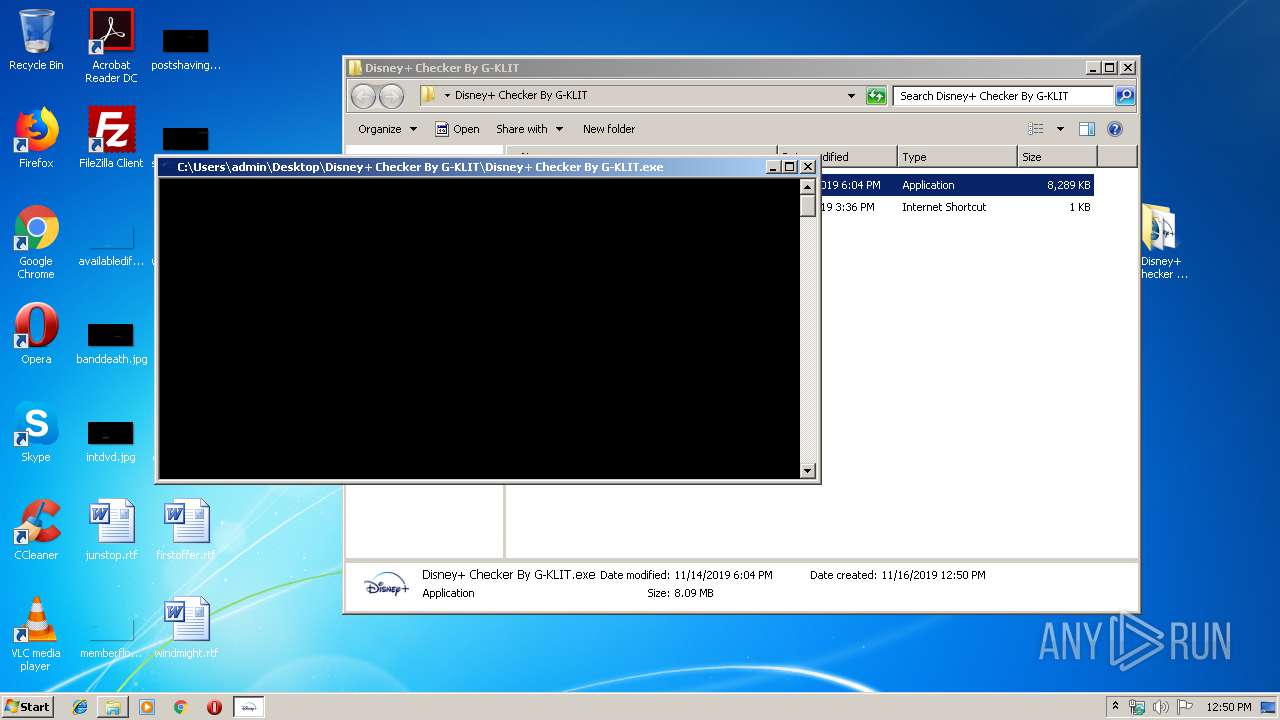
Loads dropped or rewritten executable
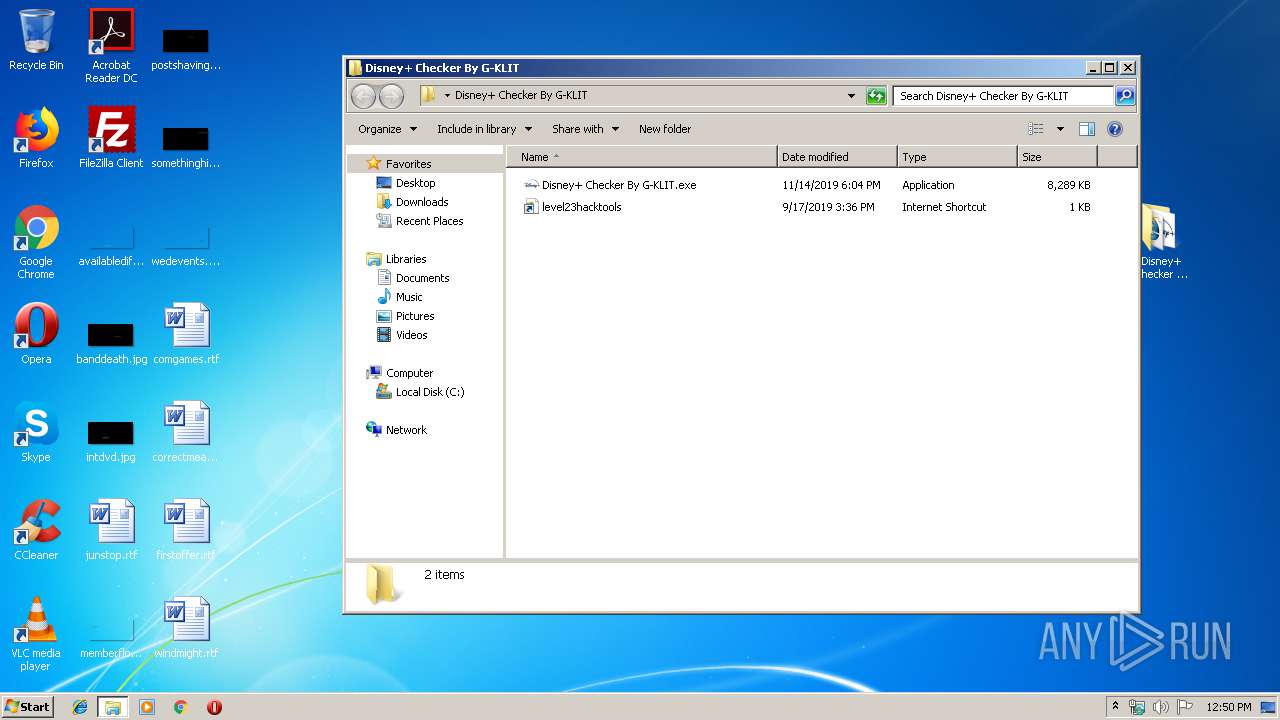
- Disney+ Checker By G-KLIT.exe (PID: 3112)
- Disney+ Checker By G-KLIT.exe (PID: 1584)
- Disney+ Checker By G-KLIT.exe (PID: 928)
SUSPICIOUS
Executable content was dropped or overwritten
- Disney+ Checker By G-KLIT.exe (PID: 4064)
Loads Python modules
- Disney+ Checker By G-KLIT.exe (PID: 3112)
- Disney+ Checker By G-KLIT.exe (PID: 1584)
- Disney+ Checker By G-KLIT.exe (PID: 928)
Application launched itself
- Disney+ Checker By G-KLIT.exe (PID: 4064)
- Disney+ Checker By G-KLIT.exe (PID: 3112)
Starts CMD.EXE for commands execution
- Disney+ Checker By G-KLIT.exe (PID: 3112)
Reads Internet Cache Settings
- Disney+ Checker By G-KLIT.exe (PID: 3112)
INFO
Manual execution by user
- Disney+ Checker By G-KLIT.exe (PID: 4064)
Dropped object may contain Bitcoin addresses
- Disney+ Checker By G-KLIT.exe (PID: 4064)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
41
Monitored processes
6
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 928 | "C:\Users\admin\Desktop\Disney+ Checker By G-KLIT\Disney+ Checker By G-KLIT.exe" "--multiprocessing-fork" "parent_pid=3112" "pipe_handle=1708" | C:\Users\admin\Desktop\Disney+ Checker By G-KLIT\Disney+ Checker By G-KLIT.exe | — | Disney+ Checker By G-KLIT.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1584 | "C:\Users\admin\Desktop\Disney+ Checker By G-KLIT\Disney+ Checker By G-KLIT.exe" "--multiprocessing-fork" "parent_pid=3112" "pipe_handle=1156" | C:\Users\admin\Desktop\Disney+ Checker By G-KLIT\Disney+ Checker By G-KLIT.exe | — | Disney+ Checker By G-KLIT.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2872 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Disney+ Checker By G-KLIT.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3112 | "C:\Users\admin\Desktop\Disney+ Checker By G-KLIT\Disney+ Checker By G-KLIT.exe" | C:\Users\admin\Desktop\Disney+ Checker By G-KLIT\Disney+ Checker By G-KLIT.exe | — | Disney+ Checker By G-KLIT.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3864 | C:\Windows\system32\cmd.exe /c cls | C:\Windows\system32\cmd.exe | — | Disney+ Checker By G-KLIT.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 4064 | "C:\Users\admin\Desktop\Disney+ Checker By G-KLIT\Disney+ Checker By G-KLIT.exe" | C:\Users\admin\Desktop\Disney+ Checker By G-KLIT\Disney+ Checker By G-KLIT.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
1 407
Read events
1 324
Write events
79
Delete events
4
Modification events
| (PID) Process: | (2872) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2872) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2872) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2872) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Disney+ Checker By G-KLIT.rar | |||
| (PID) Process: | (2872) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2872) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2872) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2872) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2872) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (2872) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
19
Suspicious files
1
Text files
912
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2872 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2872.14405\Disney+ Checker By G-KLIT\Disney+ Checker By G-KLIT.exe | — | |
MD5:— | SHA256:— | |||
| 2872 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2872.14405\Disney+ Checker By G-KLIT\level23hacktools.url | — | |
MD5:— | SHA256:— | |||
| 4064 | Disney+ Checker By G-KLIT.exe | C:\Users\admin\AppData\Local\Temp\_MEI40642\Disney+.exe.manifest | xml | |
MD5:— | SHA256:— | |||
| 4064 | Disney+ Checker By G-KLIT.exe | C:\Users\admin\AppData\Local\Temp\_MEI40642\VCRUNTIME140.dll | executable | |
MD5:AE96651CFBD18991D186A029CBECB30C | SHA256:1B372F064EACB455A0351863706E6326CA31B08E779A70DE5DE986B5BE8069A1 | |||
| 4064 | Disney+ Checker By G-KLIT.exe | C:\Users\admin\AppData\Local\Temp\_MEI40642\libcrypto-1_1.dll | executable | |
MD5:C0E55A25DD5C5447F15EED0CA6552AB7 | SHA256:9FEFBA93FA3300732B7E68FB3B4DBB57BF2726889772A1D0D6694A71820D71F3 | |||
| 4064 | Disney+ Checker By G-KLIT.exe | C:\Users\admin\AppData\Local\Temp\_MEI40642\_decimal.pyd | executable | |
MD5:E4292AD50769F592F34BC63F62A5E428 | SHA256:0240F15B44E2D3E37EBEFBB221D3D6017BE5EF99806EC4E36C3521F284CB8043 | |||
| 4064 | Disney+ Checker By G-KLIT.exe | C:\Users\admin\AppData\Local\Temp\_MEI40642\_ssl.pyd | executable | |
MD5:CC5C8EB32ACB2261C42A7285D436CCA9 | SHA256:07EA50E536886F68473635FFEFCFCAA7266E63C478EF039BA100DDF02F88CE61 | |||
| 4064 | Disney+ Checker By G-KLIT.exe | C:\Users\admin\AppData\Local\Temp\_MEI40642\_hashlib.pyd | executable | |
MD5:E84E1BA269371E439C2D52024ACA6535 | SHA256:2FCB297733E6080480AC24CF073FF5E239FB02A1CE9694313C5047F9C58D781B | |||
| 4064 | Disney+ Checker By G-KLIT.exe | C:\Users\admin\AppData\Local\Temp\_MEI40642\unicodedata.pyd | executable | |
MD5:E176F984D22F031098D700B7F1892378 | SHA256:46876FC52F1529C2633372D8E2CEA5B08B5A8582F8645CFAD8F5FF8128A7F575 | |||
| 4064 | Disney+ Checker By G-KLIT.exe | C:\Users\admin\AppData\Local\Temp\_MEI40642\_tkinter.pyd | executable | |
MD5:E46970E8EB0061DF01347A3723140E77 | SHA256:71C4545CEE713F26CF2F910A08340DD519C4713B8416479F74B0B9E2683C85D5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report